Lazywarden is a Python automation tool designed to Backup and Restore data from your vault, including Bitwarden attachments. It allows you to upload backups to multiple cloud storage services and receive notifications across multiple platforms. It also offers AES encrypted backups and uses key derivation with Argon2, ensuring maximum security for your data.
- 🔒 Maximum Security: Data protection with AES-256 encryption and Argon2 key derivation.
- 🔄 Automated Backups and Imports: Keep your Bitwarden vault up to date and secure.
- ✅ Integrity Verification: SHA-256 hash to ensure data integrity on every backup.
- ☁️ Multi-Cloud Support: Store backups to services such as Dropbox, Google Drive, pCloud, MEGA, NextCloud, Seafile, Storj, Cloudflare R2, Filebase (IPFS) and via SMTP.
- 🖥️ Local Storage: Save backups to a local path for greater control.
- 🔔 Real-Time Alerts: Instant notifications on Discord, Telegram and Slack.
- 🗓️ Schedule Management: Integration with CalDAV, Todoist and Vikunja to manage your schedule.
- 🐳 Easy Deployment: Quick setup with Docker Compose.
- 🤖 Full Automation and Custom Scheduling: Automatic backups with flexible scheduling options (daily, weekly, monthly, yearly). Integration with CalDAV, Todoist and Vikunja for complete tracking and email notifications.
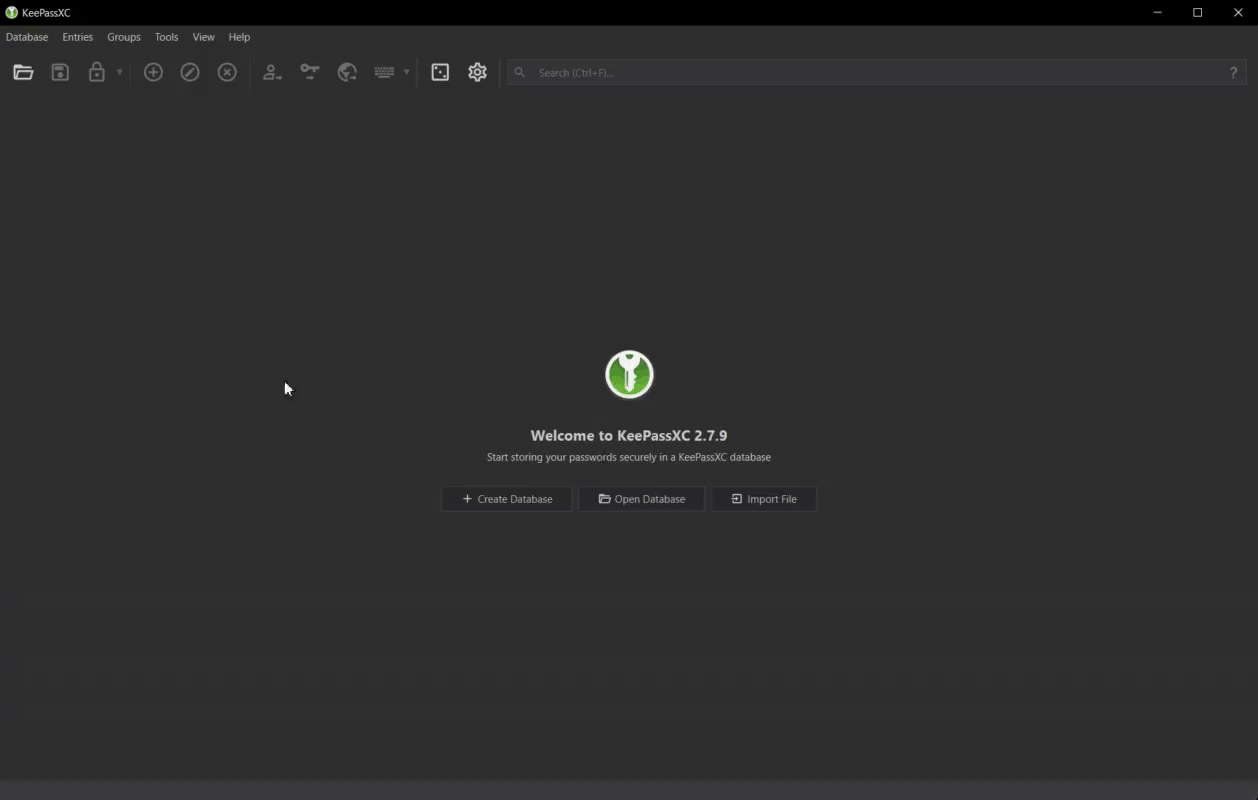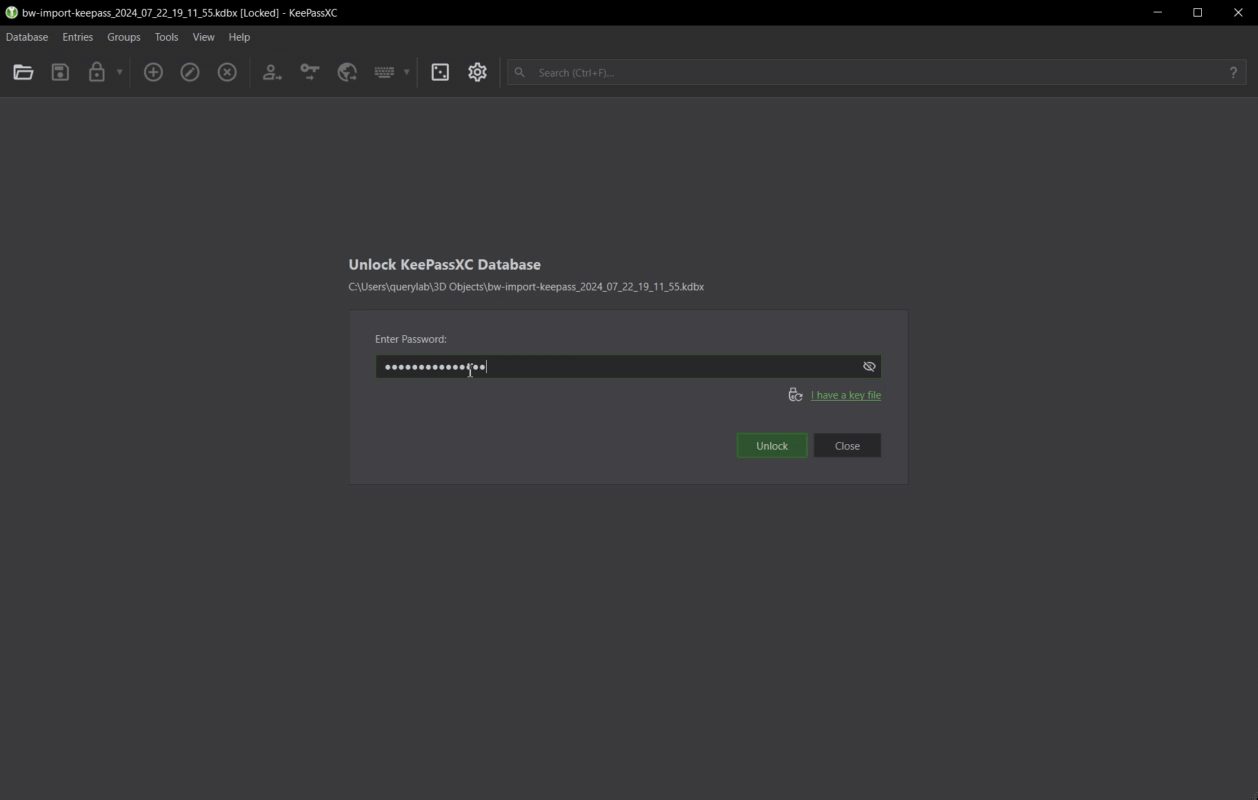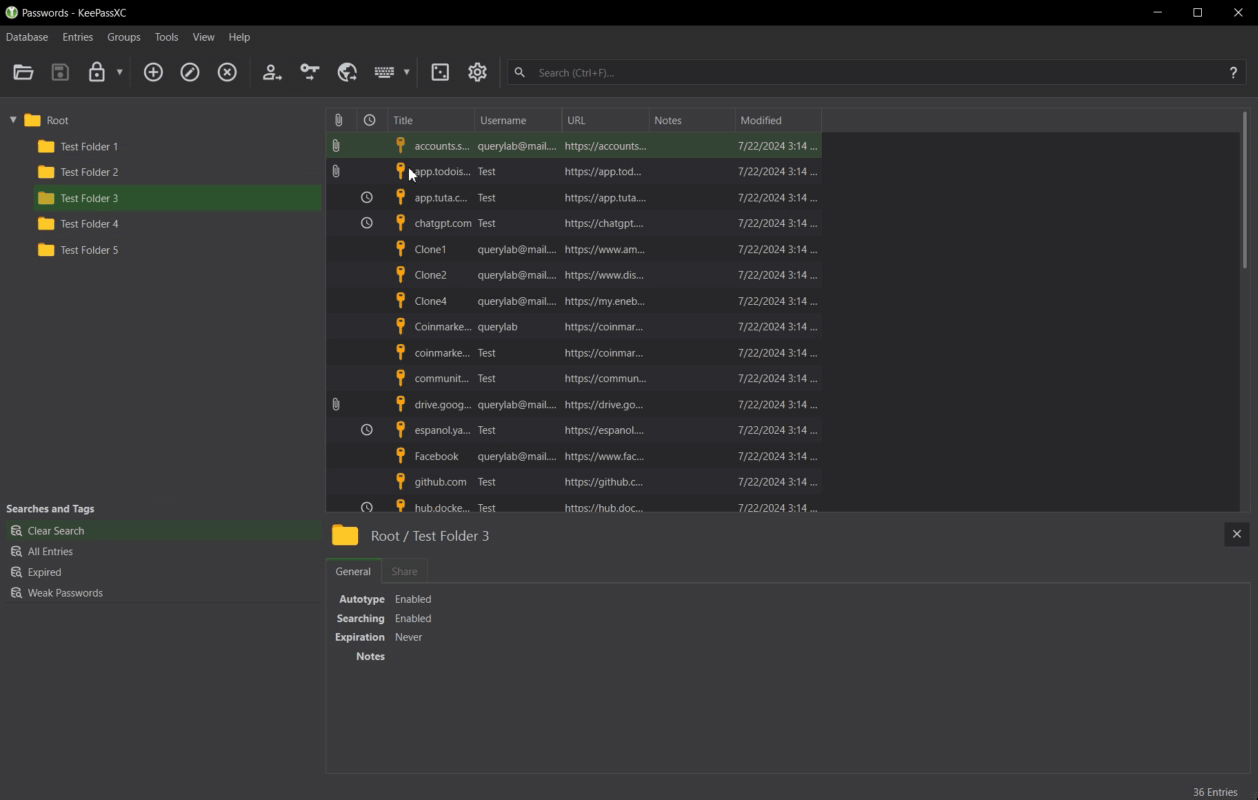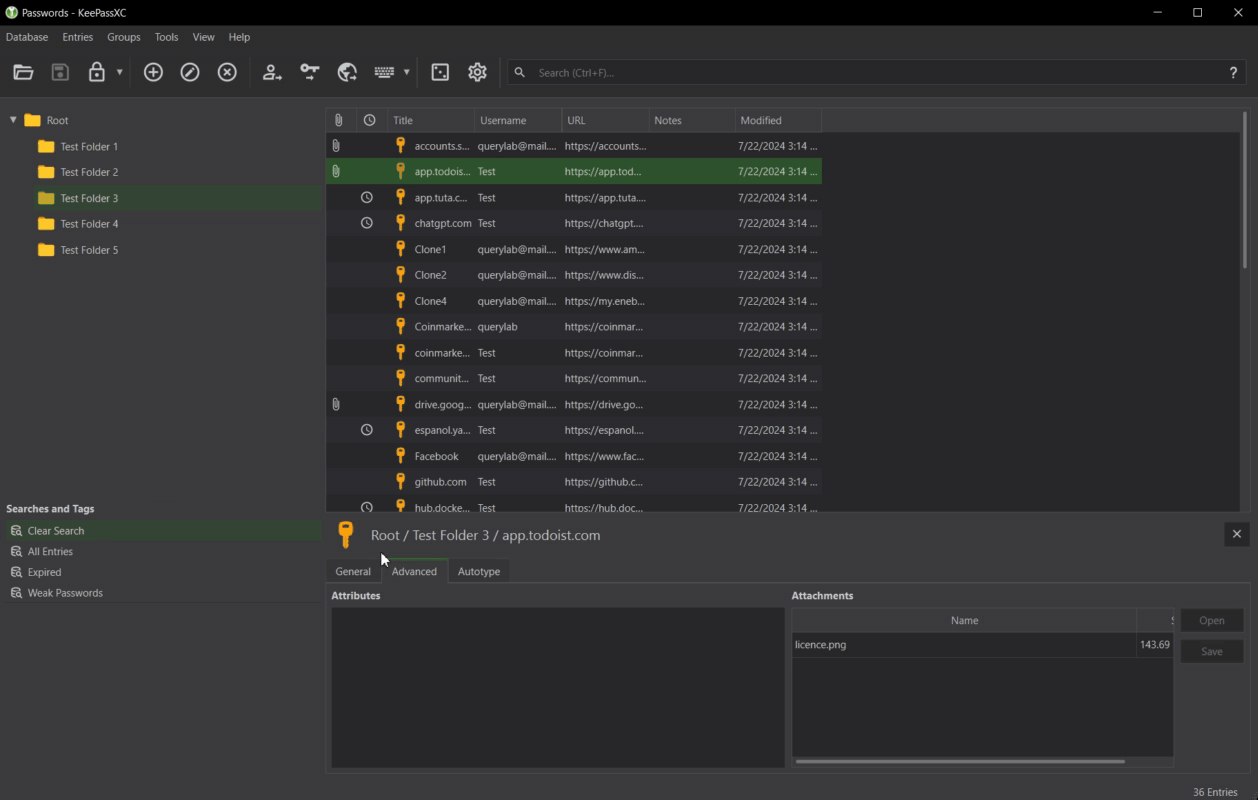
- 🔑 Bitwarden Export to KeePass: Export Bitwarden items to a KeePass database (kdbx), including TOTP-seeded logins, URI, custom fields, card, identity attachments and secure notes.

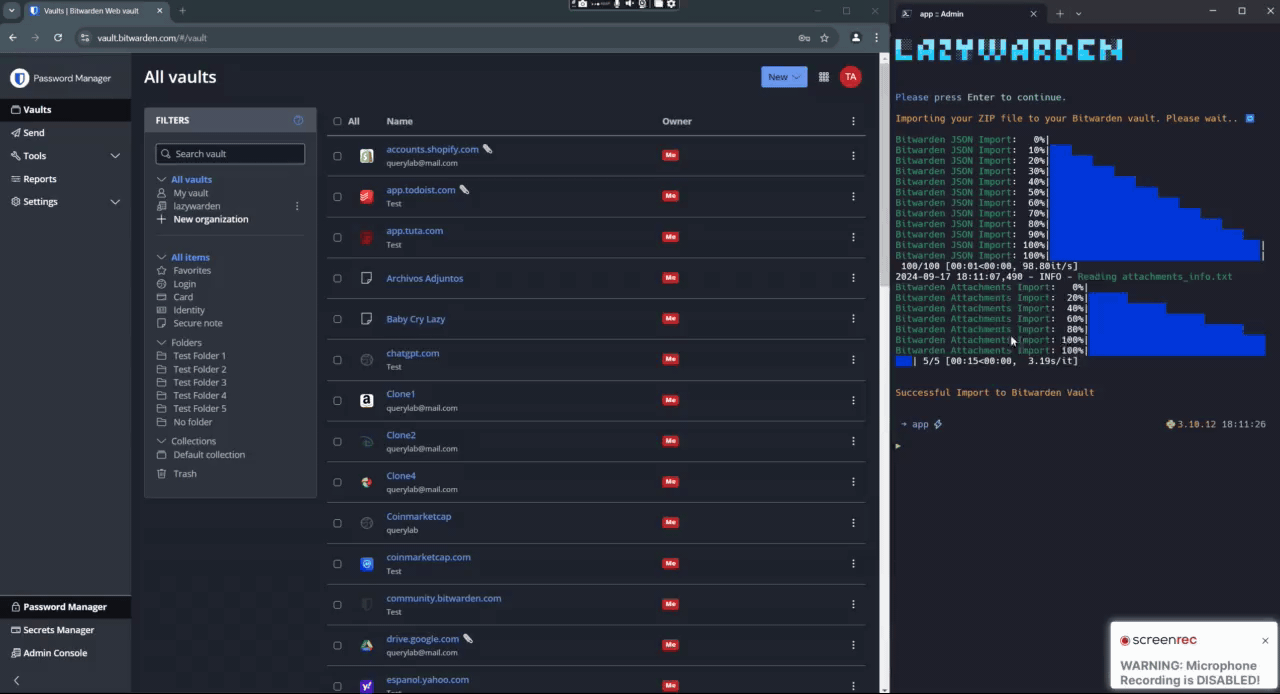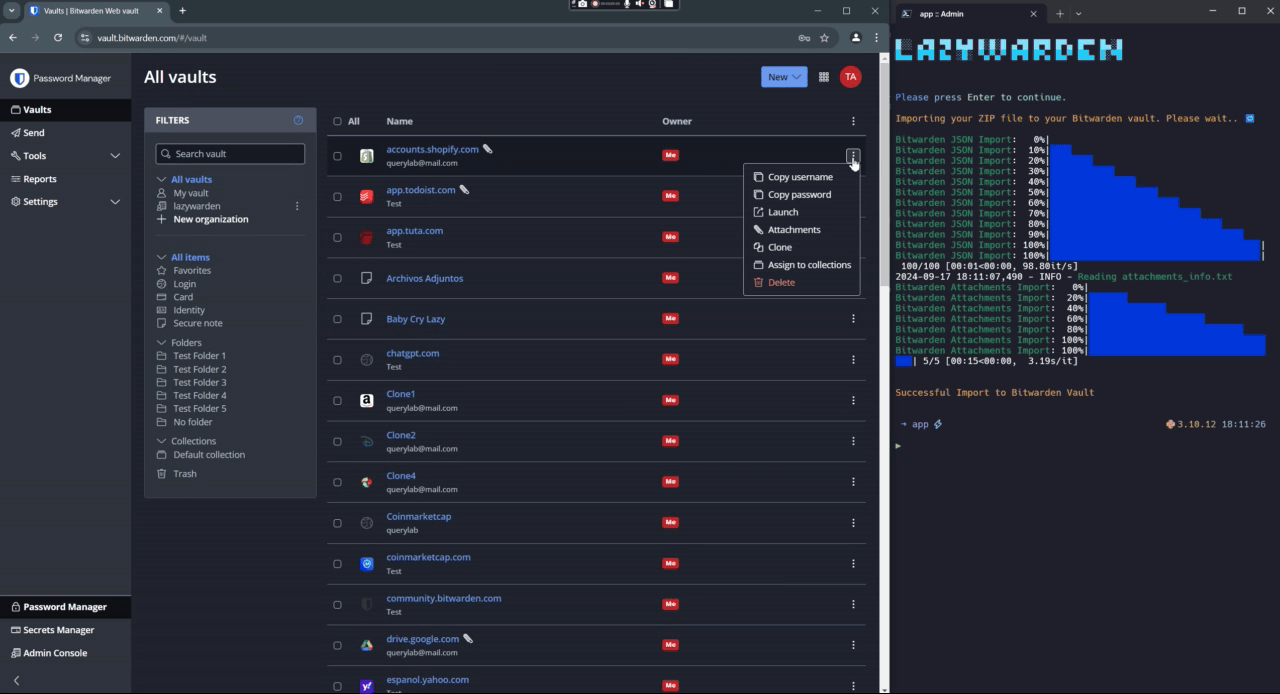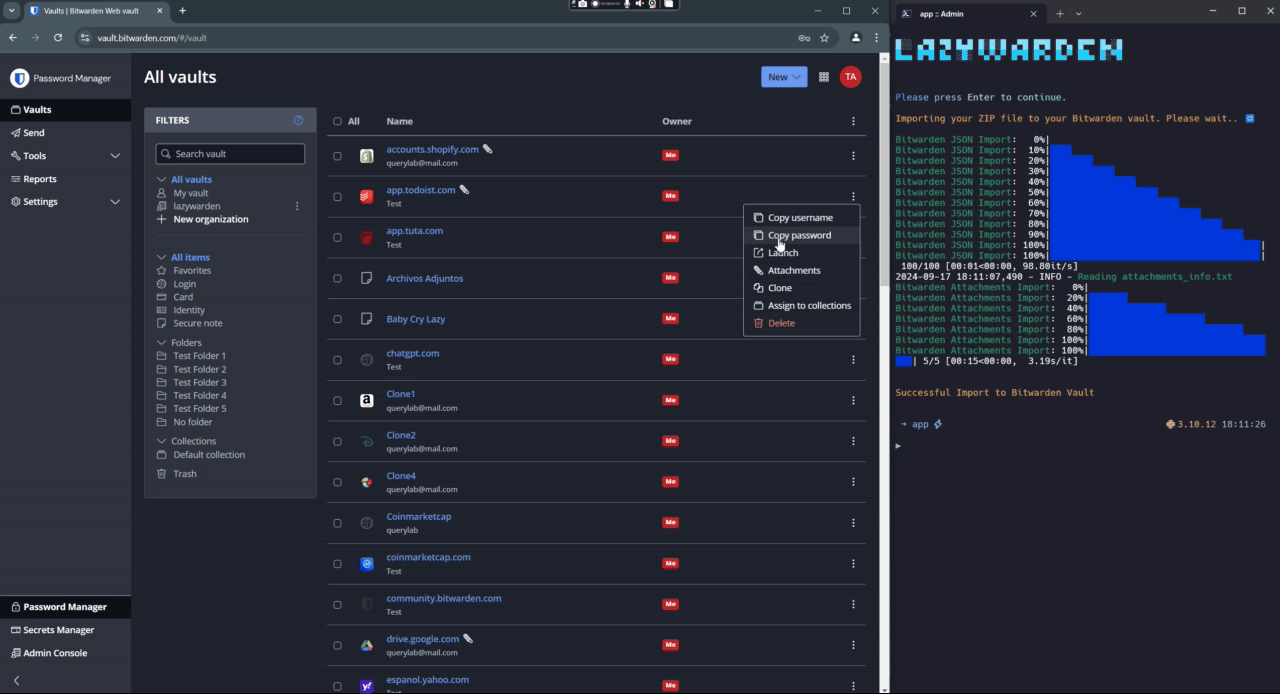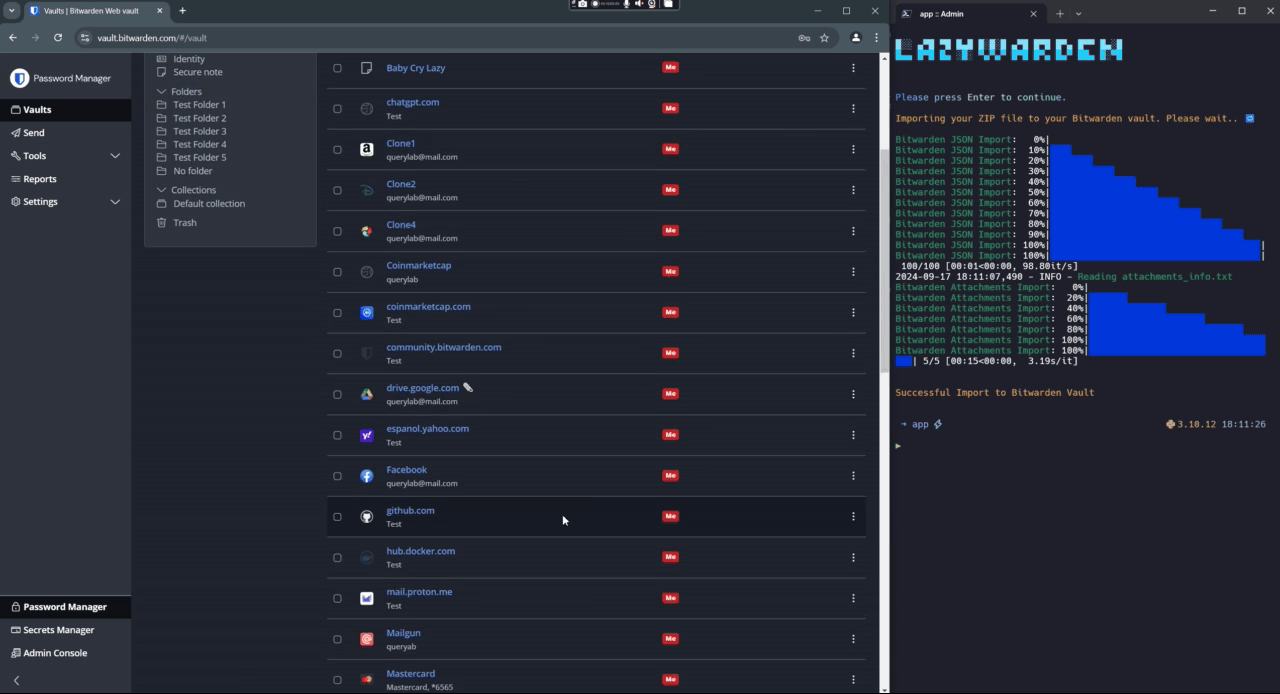



-
Operating System: Compatible with major Linux distributions
- ✅ Ubuntu
- ✅ Debian
git clone https://github.com/querylab/lazywarden.git
cd lazywarden- Create a
.envfile based on the on this.env.sampleexample file and fill in the necessary variables.
# Bitwarden Secrets
BW_URL=80607bef-1153-4eb6-1111-b1a0013ebdd1
BW_USERNAME=c6a5fc4d-6d36-1111-820a-a1dae99e2f43
BW_PASSWORD=0de9c3be-253d-1111-be10-de0607329ffa
BW_TOTP_SECRET=01726d37-0df7-1111-a78d-96fdc8efd59b
ENCRYPTION_PASSWORD=588b0643-1111-4a78-ba3e-9467ad9c81a7
ZIP_PASSWORD=3bcadf27-446d-47f0-1111-b1469fa58546
ZIP_ATTACHMENT_PASSWORD=89d458e7-9ac4-1111-9f23-95cb4b8cff86
# pCloud Credentials
PCLOUD_USERNAME=8d5f981b-705a-1111-a25d-a2abe925f4e4
PCLOUD_PASSWORD=23351280-0184-1111-99b0-2b6a1bc921ae
# Mega Credentials
MEGA_EMAIL=1dafc95a-63c2-4b66-1111-bd7cd5a2ea5e
MEGA_PASSWORD=51bec27b-7c79-1111-9cef-1be72675a47f
# Dropbox Credentials
DROPBOX_ACCESS_TOKEN=647ff022-1111-47d9-a54f-fef635b23eff
DROPBOX_REFRESH_TOKEN=873e5430-1111-4d62-8bf2-acce1e915a9d
DROPBOX_APP_KEY=81f259ae-d6e4-47b1-1111-6bec568ddc85
DROPBOX_APP_SECRET=0b407a02-ded5-1111-b953-caf8fc79af99
# Todoist Credentials
TODOIST_TOKEN=667321ac-2229-42a1-1111-3c568c9d73e6
# CalDAV Credentials
CALDAV_URL=049c9267-bdb0-4266-1111-b19a00e9b626
CALDAV_USERNAME=6eff84c9-fbeb-1111-ad30-b19a00e9cc09
CALDAV_PASSWORD=492c37fd-46df-1111-abe7-b19a00e9e601
# Nextcloud Credentials
NEXTCLOUD_URL=e375df76-d3b2-1111-83ba-b19a0158fe08
# Example http://192.175.88.112:8400
NEXTCLOUD_USERNAME=a267c8cd-9d13-1111-8729-b19a0159276a
NEXTCLOUD_PASSWORD=7036175d-046b-1111-9797-b19a01594308
# Seafile Credentials
SEAFILE_SERVER_URL=20060dfc-4fa0-1111-8b41-b19b000857e7
# Example http://192.175.88.212:8200
SEAFILE_USERNAME=9959dabb-ae4c-1111-9fc1-b19b00087d64
SEAFILE_PASSWORD=94e5f170-aedb-1111-b1b9-b19b00088ccd
# Filebase Credentials
FILEBASE_ACCESS_KEY=53ec784f-4b18-1111-9a47-b1a00136efc5
FILEBASE_SECRET_KEY=f99d8d83-57b9-1111-9ace-b1a001370117
# KeePass Password
KEEPASS_PASSWORD=95512b36-32e9-1111-9c15-b1ae0171b2f9
# Storj Credentials
STORJ_ACCESS_KEY=a7d85af3-ad63-1111-b039-b208012c381a
STORJ_SECRET_KEY=1303faf7-b34e-1111-ac43-b208012c4f05
STORJ_ENDPOINT=fb787806-a3f4-1111-8523-b208012c6543
# R2 Credentials
R2_ACCESS_KEY_ID=ffb0d6ed-1111-46ad-8fdf-b2080132c9dd
R2_SECRET_ACCESS_KEY=083b5344-1111-4dd8-909e-b2080132dc52
R2_ENDPOINT_URL=31510979-b5b1-1111-8957-b2080132f436
# Vikunja Credentials
VIKUNJA_API_TOKEN=7e67437c-1489-1111-8fbb-b20801880db2
VIKUNJA_URL=d3b7a73f-ebb9-1111-8dc2-b208018843a6
#Example for Bitwarden Secret Manager http://192.175.88.227:3456/api/v1
# Google Drive Settings
GOOGLE_SERVICE_ACCOUNT_FILE=/root/lazywarden/config/bitwarden-drive-backup-google.json
GOOGLE_FOLDER_ID=1oWWis81111Tz5qRA3W4YTtO0LjvXFvoA
# Backup Settings
BACKUP_DIR=/root/lazywarden/backup-drive/
CRON_SCHEDULE="0 0 23 * *"
TIMEZONE=America/New_York
TIMESTAMP=2024_10_18_22_47_46
# API URLs for Bitwarden
API_URL=https://vault.bitwarden.com/api
IDENTITY_URL=https://vault.bitwarden.com/identity
# Organization ID
ORGANIZATION_ID=232c1890-1111-40b4-b769-b195012f78af
# Access Token for Bitwarden Authentication
ACCESS_TOKEN=0.34827757-1111-1111-1111-b20a01647f46.WDp3AUjnle1LqlXvs0Ox9xEWzgY8Hp:CKue3vgWTvIQzEmDlBlqGw==
# Notifications and Alerts
TELEGRAM_TOKEN=
TELEGRAM_CHAT_ID=
DISCORD_WEBHOOK_URL=
SLACK_WEBHOOK_URL=
# SMTP Configuration for Email Notifications
SMTP_SERVER=mail.smtp2go.com
SMTP_PORT=8025
SMTP_USERNAME=
SMTP_PASSWORD=
EMAIL_RECIPIENT=
SENDER_EMAIL=- Run the script to install all system dependencies and requirements
cd lazywarden/scripts
chmod +x setup-ubuntu-env.sh
./setup-ubuntu-env.sh- Run this script to automatically install Docker & Docker-Compose:
chmod +x docker-ubuntu.sh
./docker-ubuntu.sh- First, ensure you are in the root directory of the project
lazywarden/:
cd ..
source venv/bin/activate- Now Install Bitwarden CLI using the
bitwarden-cli-install.pyscript, which will install all CLI dependencies:
python3 scripts/bitwarden-cli-install.py- Change the system timezone using the following command. Replace
Region/Citywith the desired timezone (e.g.,America/New_York):
timedatectl set-timezone Region/City- For example, to set the timezone to
America/New_York, you would run:
timedatectl set-timezone America/New_York- Run the Lazywarden program. Navigate to the
app/folder and executemain.py:
cd app
python3 main.py- In Ubuntu, if you encounter an error when running
main.py, it may be related to missing or outdated libraries. To fix this, I recommend running the following command to install all the necessary dependencies:
pip install -r requirements.txt- Run the script to install all system dependencies and requirements:
cd lazywarden/scripts
chmod +x setup-debian-env.sh
./setup-debian-env.sh- Run this script to automatically install Docker & Docker-Compose:
chmod +x docker-debian.sh
./docker-debian.sh- First, ensure you are in the root directory of the project
lazywarden/:
cd ..
source venv/bin/activate- Install Bitwarden CLI using the
bitwarden-cli-install.pyscript, which will install all CLI dependencies:
python3 scripts/bitwarden-cli-install.py- Change the system timezone using the following command. Replace
Region/Citywith the desired timezone (e.g.,America/New_York):
timedatectl set-timezone Region/City- For example, to set the timezone to
America/New_York, you would run:
timedatectl set-timezone America/New_York- Run the Lazywarden program. Navigate to the
app/folder and executemain.py:
cd app
python3 main.py- In Debian, if you encounter an error when running
main.py, it may be related to missing or outdated libraries. To fix this, I recommend running the following command to install all the necessary dependencies:
pip install -r requirements.txtTo set up Secret Management in Bitwarden, first create a new organization in your account to serve as a container for shared secrets. Next, subscribe to the Secret Manager service, which allows you to securely store an unlimited number of secrets, such as API keys, passwords and certificates. This service provides end-to-end encryption, centralized management and access control.
- After creating your Organization, go to Secret Manager in the tab at the top right.
- Then create your lazywarden Project.
- After creating your lazywarden Project, you need to create the secrets that will be in the lazywarden project. Here are some examples:
- With these secrets added, we can now modify our .env file to contain our secrets.
# Bitwarden Secrets
BW_URL=00000000-0000-0000-0000-000000000000
BW_USERNAME=00000000-0000-0000-0000-000000000000
BW_PASSWORD=00000000-0000-0000-0000-000000000000
BW_TOTP_SECRET=00000000-0000-0000-0000-000000000000
ENCRYPTION_PASSWORD=00000000-0000-0000-0000-000000000000
ZIP_PASSWORD=00000000-0000-0000-0000-000000000000
ZIP_ATTACHMENT_PASSWORD=00000000-0000-0000-0000-000000000000
# pCloud Credentials
PCLOUD_USERNAME=00000000-0000-0000-0000-000000000000
PCLOUD_PASSWORD=00000000-0000-0000-0000-000000000000
# Mega Credentials
MEGA_EMAIL=00000000-0000-0000-0000-000000000000
MEGA_PASSWORD=00000000-0000-0000-0000-000000000000
# Dropbox Credentials
DROPBOX_ACCESS_TOKEN=00000000-0000-0000-0000-000000000000
DROPBOX_REFRESH_TOKEN=00000000-0000-0000-0000-000000000000
DROPBOX_APP_KEY=00000000-0000-0000-0000-000000000000
DROPBOX_APP_SECRET=00000000-0000-0000-0000-000000000000
# Todoist Credentials
TODOIST_TOKEN=00000000-0000-0000-0000-000000000000
# CalDAV Credentials
CALDAV_URL=00000000-0000-0000-0000-000000000000
CALDAV_USERNAME=00000000-0000-0000-0000-000000000000
CALDAV_PASSWORD=00000000-0000-0000-0000-000000000000
# Nextcloud Credentials
NEXTCLOUD_URL=00000000-0000-0000-0000-000000000000
NEXTCLOUD_USERNAME=00000000-0000-0000-0000-000000000000
NEXTCLOUD_PASSWORD=00000000-0000-0000-0000-000000000000
# Seafile Credentials
SEAFILE_SERVER_URL=00000000-0000-0000-0000-000000000000
SEAFILE_USERNAME=00000000-0000-0000-0000-000000000000
SEAFILE_PASSWORD=00000000-0000-0000-0000-000000000000
# Filebase Credentials
FILEBASE_ACCESS_KEY=00000000-0000-0000-0000-000000000000
FILEBASE_SECRET_KEY=00000000-0000-0000-0000-000000000000
# KeePass Password
KEEPASS_PASSWORD=00000000-0000-0000-0000-000000000000
# Storj Credentials
STORJ_ACCESS_KEY=00000000-0000-0000-0000-000000000000
STORJ_SECRET_KEY=00000000-0000-0000-0000-000000000000
STORJ_ENDPOINT=00000000-0000-0000-0000-000000000000
# R2 Credentials
R2_ACCESS_KEY_ID=00000000-0000-0000-0000-000000000000
R2_SECRET_ACCESS_KEY=00000000-0000-0000-0000-000000000000
R2_ENDPOINT_URL=00000000-0000-0000-0000-000000000000
# Vikunja Credentials
VIKUNJA_API_TOKEN=00000000-0000-0000-0000-000000000000
VIKUNJA_URL=00000000-0000-0000-0000-000000000000- If you have TOTP enabled on your Bitwarden account, put the seeds of your TOTP in the BW_TOTP_SECRET variable.
- If you do not have TOTP enabled on your Bitwarden account, just put random characters as shown in the image below.
- Continue filling in the other variables one by one. If you do not have an account, for example for pCloud, MEGA, Filebase, Seafile, NextCloud or Dropbox fill in the variables with some random characters. For example, if you don't have a MEGA account, put the following:
-
As you can see in the images above, I don't have a MEGA account, so I used random strings. You always have to have something in the Secret Variables for the program to work. Now, the backup will only be stored locally in the chosen directory and in Google Drive, Dropbox, pCloud, NextCloud, Seafile and Filebase but not in MEGA as my account is not configured
-
After creating all your secrets, create a Machine Account that will hold our ACCESS_TOKEN.
- Add and save the lazywarden project to your Machine Account.
- Finally, go to Access Tokens and create one to use in our lazywarden project.
- To find the ORGANIZATION_ID variable for our .env you can get it by visiting the URL when you are in your organization or by running the following command:
bw list organizationsORGANIZATION_ID=212A4880-22f9-1114-b00e-12345234278ac
ACCESS_TOKEN=0.345f5e9c-8730-4a4c-917b-b100003312356.Oj4XzcyGFF222212345kwzV:e5mC4d1111111128/3EQ==### These variables contain the passwords for encrypting the backup.
### Change the passwords according to your preferences.
#Contains the encryption password for the JSON file
ENCRYPTION_PASSWORD=p3mTd5SqDqkXQqE!Tpwv27Ecx
#Contains the encryption password for the first ZIP file
ZIP_PASSWORD=ZCGvq@gwS7QhV@&R3k*x*xN72anybyFHW2RWiBTr
# Contains the encryption password for the attached ZIP file.
# Where our files will be stored if Bitwarden Premium is enabled.
# If Bitwarden Premium is not enabled, the attachment folder will be empty.
ZIP_ATTACHMENT_PASSWORD=HBLXL9!grer@Uay2edkwTXeZx!E9DxKphNxsNak1knb3dcfx2o
# Contains the encryption password for KeePass Database (Kdbx).
KEEPASS_PASSWORD=e2zkwTXe21!E9DxKpBy following these steps, your Dropbox Token will remain active and will not expire every 4 hours.
- Create a new project.
- Create Permissions
- Obtain the Authorization Code
- Open a browser and navigate to the following URL, replacing
<App key>with your App Key:
https://www.dropbox.com/oauth2/authorize?token_access_type=offline&response_type=code&client_id=<App key>- Obtain the Authorization Token
Run the following command in the terminal, making sure to replace <received code>, <App key>, and <App secret> with the correct values:
curl https://api.dropbox.com/oauth2/token \
-d code=<received code> \
-d grant_type=authorization_code \
-u <App key>:<App secret>
#Example
curl https://api.dropbox.com/oauth2/token \
-d code=G4sTbrY9DMoAAAAAAAAAQTeLtVHACmv1tVaWYLYCGvA \
-d grant_type=authorization_code \
-u 7on1ofs1236ki:b6bl6jg123lm8iz- When you run the command, you will receive a response like this:
"access_token": "sl.B3hxfHXr123459z8_TS230pcLcLNbJ1234Hj-ccZmG5XCcQrN-Wb6ESMs0PSzwOtROxLb6XRaj6mUzHU1g8G60canTvjkWBBaNzVY1234hH2FEOhlwseaNcnQ9RyPn6vh",
"token_type": "bearer",
"expires_in": 14400,
"refresh_token": "WtG6MI5YdccAAAAAAAAAAcAvu1234nB6skR3BmpgH3x5Reb-ae7FsLuNQ5-mZkk",
"scope": "account_info.read",
"uid": "143786425",
"account_id": "dbid:BBAnJyzGYtm3-WP9a2HkL1TL8FVgPl5s-VM"- Now use this new
refresh_token,access_tokenalong with the previous<App key>, and<App secret>to fill in the secret variables needed in Bitwarden Secret Manager:
#Example
DROPBOX_ACCESS_TOKEN=sl.B3hxfHXrU12345z8_TS230pcLcLNbJj019MyrVHj-ccZmG5XCcQrN-Wb6ESMs0PSzwOtROxLb612345g8G60canTvjkWBBaNzVYP15cx5h12345NcnQ9RyPn6vh
DROPBOX_REFRESH_TOKEN=WtG6MI5Yd1234AAAAAAcAvuFd9usnB6skR3BmpgH3x5Reb-ae7FsLuNQ5-mZkk
DROPBOX_APP_KEY=1on14fs123456ki
DROPBOX_APP_SECRET=b1bl12345m8iz
- Go to this web page https://console.developers.google.com/iam-admin/serviceaccounts
- Create a New Project.
- Then go to "Service Accounts" and create a new service.
- Select the role "Actions Admin".
- Download the key in JSON format. This key will be used in our project to upload the Bitwarden backup to Google Drive. Once you obtain the JSON file, store it in the /config folder of the project. Name the JSON file bitwarden-drive-backup-google.json.
# Place the Google credentials file in the specified path /config
GOOGLE_SERVICE_ACCOUNT_FILE=/home/lazywarden/config/bitwarden-drive-backup-google.json
- Go to the following link and enable the Google Drive API:https://console.cloud.google.com/apis/library
- Now that you have enabled the API, go to your Google Drive and create a folder named "Bitwarden-Backup".
- Share the "Bitwarden-Backup" folder by clicking on "Share" and share it with the email address created in the Service Account when you set up the project.
- After sharing the folder, you need to get the ID of this folder to store it in your .env file. To find the ID of the “Bitwarden-Backup” folder, open the folder and look at the URL in your browser.
GOOGLE_FOLDER_ID=1qtV4vfIjmXyhDdzIzJ6RiCc-b0M22vsFlazywarden/
├── app/ # This directory appears to contain the main application code
│ ├── backup.py # Backup functions
│ ├── bitwarden_client.py # Client to interact with Bitwarden
│ ├── config.py # General application configurations
│ ├── imports.py # Handles common imports
│ ├── main.py # Main entry point of the application
│ ├── notifications.py # Handles notifications
│ ├── secrets_manager.py # Manages secrets
│ ├── import_to_bitwarden.py # Import your bitwarden vault
│ ├── import_to_keepass.py # Create kdbx database
│ ├── schedule_backup.py # For create Schedule Backup
├── config/ # Directory for configuration files
│ ├── bitwarden-drive-backup-google.json # Configuration for Google Drive
├── scripts/ # Directory for installation and setup scripts
│ ├── bitwarden-cli-install.py # Script to install the Bitwarden CLI
│ ├── docker-debian.sh # Setup script for Debian with Docker
│ ├── docker-ubuntu.sh # Setup script for Ubuntu with Docker
│ ├── setup-debian-env.sh # Environment setup for Debian
│ ├── setup-ubuntu-env.sh # Environment setup for Ubuntu
│ ├── alldecrypt-zip.py # Decrypt all zip files
│ ├── json-only-decrypt.py # Decrypt only json files (optional)
├── backup-drive/
│ ├── (This is where the generated backups will be stored local)
├── .env # File for environment variables
├── Dockerfile # Docker configuration file to create an application image
├── docker-compose.yml # Docker Compose Configuration
├── entrypoint.sh # Entrypoint script for Docker
└── requirements.txt # File that lists the project Python dependencies
To automatically run the backup script in the background using cron, every 24 hours follow these steps:
- Open the crontab for editing:
crontab -e- Select an editor if you dont have one configured:
Select an editor. To change later, run 'select-editor'.
1. /bin/nano <---- easiest
2. /usr/bin/vim.basic
3. /usr/bin/vim.tiny
4. /bin/ed
Choose 1-4 [1]: 1
- Add the following line to schedule the
lazywarden.pyscript to run at midnight every day:
0 0 23 * * /root/lazywarden/venv/bin/python3 /root/lazywarden/app/main.py >> /var/log/lazywarden-cron.log 2>&1
- Save & Close and reload the file. Verify that the cron job is set up correctly:
service cron reload
crontab -l
The Docker container will run the main.py script every 24 hours to back up Bitwarden and upload it to the configured cloud services. Notifications will be sent to the specified services in case of success or failure. You can modify the backup frequency according to your needs, such as monthly, daily, or hourly.
services:
lazywarden:
container_name: lazywarden
hostname: lazywarden
image: querylab/lazywarden:latest
env_file:
- .env
environment:
UNLOCK_VAULT: "true"
volumes:
- /root/lazywarden/config:/root/lazywarden/config
- /root/lazywarden/backup-drive:/root/lazywarden/backup-drive/
- /root/lazywarden/.env:/app/.env
restart: unless-stopped- Run the Docker container
docker compose up -d
- The
Dockerfilesets up the environment, installs dependencies, and copies necessary files into the container.
- The
docker-compose.ymlfile defines the lazywarden service and sets up environment variables and volumes for persistent storage.
- For security, run this project only in a local environment within your personal network. This significantly reduces the risk of exposure to external attacks, ensuring that sensitive data and credentials remain protected within a controlled environment.
- Large attachments in your Bitwarden account (e.g., MP4 videos, MP3 files, high-resolution photos) may cause the backup process to take longer. Uploading these larger backups to cloud services will also be slower. Local storage and importing data are much faster in comparison.
- A high number of attachments can significantly extend the total backup time. Upload errors may occur when sending files to Dropbox, Google Drive, pCloud, MEGA, Seafile, Nextcloud, or Filebase. If an error occurs, retrying the backup often resolves the issue.
- Configuring the Bitwarden Secret Manager is required for the program to function correctly. Even if you don't have an account, you must set a random variable to ensure proper operation.
- This program is compatible with both self-hosted Bitwarden and Vaultwarden instances.
- Import functionality for Vaultwarden and self-hosted Bitwarden is not yet implemented in the Bitwarden API.
- CalDAV calendar integration has only been tested with the following providers: Baikal, Fruux, Memotoo, Posteo, and SOGo.
- Rotate the secrets stored in Bitwarden Secret Manager regularly for enhanced security.
- If you switch Bitwarden Accounts, make sure to run the
bw logoutcommand before logging into a new account. - I run the program using the root user.
-
I created Lazywarden to Automate Bitwarden Backups without manual effort or exposing sensitive data. After struggling with complex tools, I leveraged Bitwarden Secret Manager to securely manage secrets. Lazywarden automates backups and uploads them to multiple cloud services (Google Drive, Dropbox, pCloud, MEGA, Seafile, Nextcloud, Filebase), and integrates with Telegram, Discord, Slack, Todoist, and CalDAV for notifications and tracking. Its standout feature is the ability to restore encrypted backups back into Bitwarden, making backup management simple, secure, and efficient.
-
If you like this project, please consider giving it a ⭐