-
Notifications
You must be signed in to change notification settings - Fork 1k
Description
Please provide us with the following information:
This issue is for a: (mark with an x)
- [x] bug report -> please search issues before submitting
- [ ] feature request
- [ ] documentation issue or request
- [ ] regression (a behavior that used to work and stopped in a new release)
The issue was found for the following scenario:
Please add an 'x' for the scenario(s) where you found an issue
- Web app that signs in users
- with a work and school account in your organization: 1-WebApp-OIDC/1-1-MyOrg
- with any work and school account: /1-WebApp-OIDC/1-2-AnyOrg
- with any work or school account or Microsoft personal account: 1-WebApp-OIDC/1-3-AnyOrgOrPersonal
- with users in National or sovereign clouds 1-WebApp-OIDC/1-4-Sovereign
- with B2C users 1-WebApp-OIDC/1-5-B2C
- Web app that calls Microsoft Graph
- Calling graph with the Microsoft Graph SDK: 2-WebApp-graph-user/2-1-Call-MSGraph
- With specific token caches: 2-WebApp-graph-user/2-2-TokenCache
- Calling Microsoft Graph in national clouds: 2-WebApp-graph-user/2-4-Sovereign-Call-MSGraph
- Web app calling several APIs 3-WebApp-multi-APIs
- Web app calling your own Web API 4-WebApp-your-API
- Web app restricting users
- by Roles: 5-WebApp-AuthZ/5-1-Roles
- by Groups: 5-WebApp-AuthZ/5-2-Groups
- Deployment to Azure
- Other (please describe)
Repro-ing the issue
Repro steps
- Clone sample 1-1 or 2-1.
- Configure appsettings.json with app registration information:
{
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"Domain": "microsoft.onmicrosoft.com",
"TenantId": "72f988bf-86f1-41af-91ab-2d7cd011db47",
"ClientId": "7561a6e5-a4da-43d9-a920-a2194b9086bf",
"CallbackPath": "/signin-oidc",
"SignedOutCallbackPath ": "/signout-oidc"
},
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*"
}- Run sample and attempt to sign out.
Expected behavior
- App signs the user out and suggests closing all browser windows.
Actual behavior
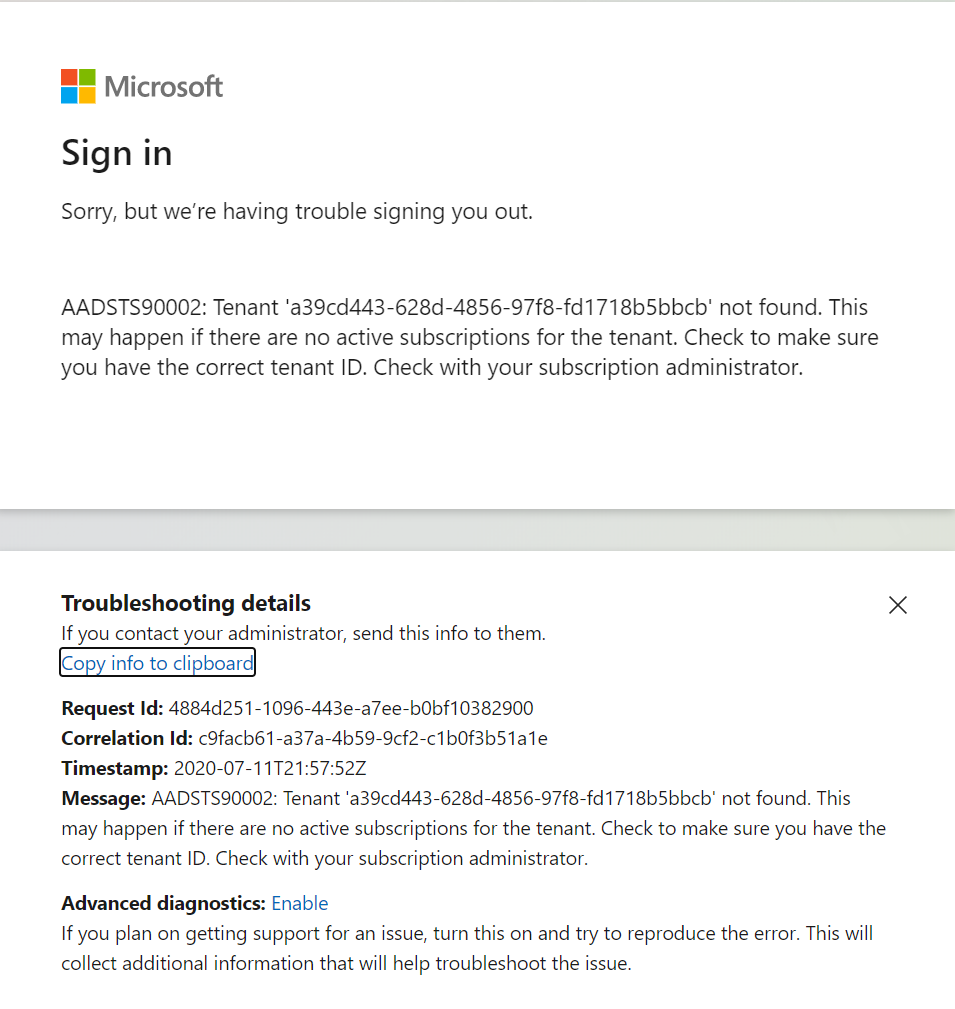
Error AADSTS90002 is displayed with a reference to unknown tenant a39cd443-628d-4856-97f8-fd1718b5bbcb (see screenshot at the bottom).
Not sure if this is related, but I'm also somewhat confused by this setting in appsettings.json, which was originally:
"SignedOutCallbackPath ": "/signout-callback-oidc"
The readme says to use "signout-oidc" as the logout url in the app registration, but changing this in appsettings.json (as shown above) seems to have no effect; the redirect url in all HTTP requests captured in Fiddler is "/signout-callback-oidc" regardless of the values in appsetting.json and the app registration, i.e.:
Request:
GET https://localhost:44321/MicrosoftIdentity/Account/SignOut HTTP/1.1
Host: localhost:44321
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.106 Safari/537.36 Edg/83.0.478.54
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://localhost:44321/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
...
Response:
HTTP/1.1 302 Found
Date: Sat, 11 Jul 2020 22:10:22 GMT
Server: Kestrel
Content-Length: 0
Cache-Control: no-cache
Pragma: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Location: https://login.microsoftonline.com/72f988bf-86f1-41af-91ab-2d7cd011db47/oauth2/v2.0/logout?post_logout_redirect_uri=https%3A%2F%2Flocalhost%3A44321%2Fsignout-callback-oidc&state=CfDJ8Bju3ImRn7xCu7-KQDKKllxMPBQW97WpWZn9bjoUYv-MGegCgWENv5U1DbRHnuCI61vJChvzPQLcel-roF6fbdArKQv4JRsf1TdNPIEbWKJP7vCoPbjVuOF0uNYyfrToR1h7o-SgRbu9FXq1rhl3lvpTjUJVSjvQSAfgUPBXJoMnoFfvKIV5gNPvzuHJyvgDReX6XPyoEvY4rJ0Ax2dlDs0&x-client-SKU=ID_NETSTANDARD2_0&x-client-ver=5.5.0.0
Set-Cookie: .AspNetCore.Cookies=; expires=Thu, 01 Jan 1970 00:00:00 GMT; path=/; secure; samesite=lax; httponly
- You can enable Middleware diagnostics by uncommenting the following lines
- You can enable personally identifiable information in your exceptions to get more information in the open id connect middleware see Seeing [PII is hidden] in log messages
- Logging for MSAL.NET is described at Loggin in MSAL.NET
OS and Version?
Windows 10
Versions
.NET Core: 3.1
Microsoft.Identity.Web: 0.1.5-preview
Attempting to troubleshooting yourself:
- did you go through the README.md in the folder where you found the issue? Yes
- did you go through the documentation:
Thanks! We'll be in touch soon.