- Windows 10, macOS or any Linux distro
- At least 8 GB RAM (16GB recommended)
- Understand how virtual machines work
- Learn how to create a basic virtual environment for pentesting purpose
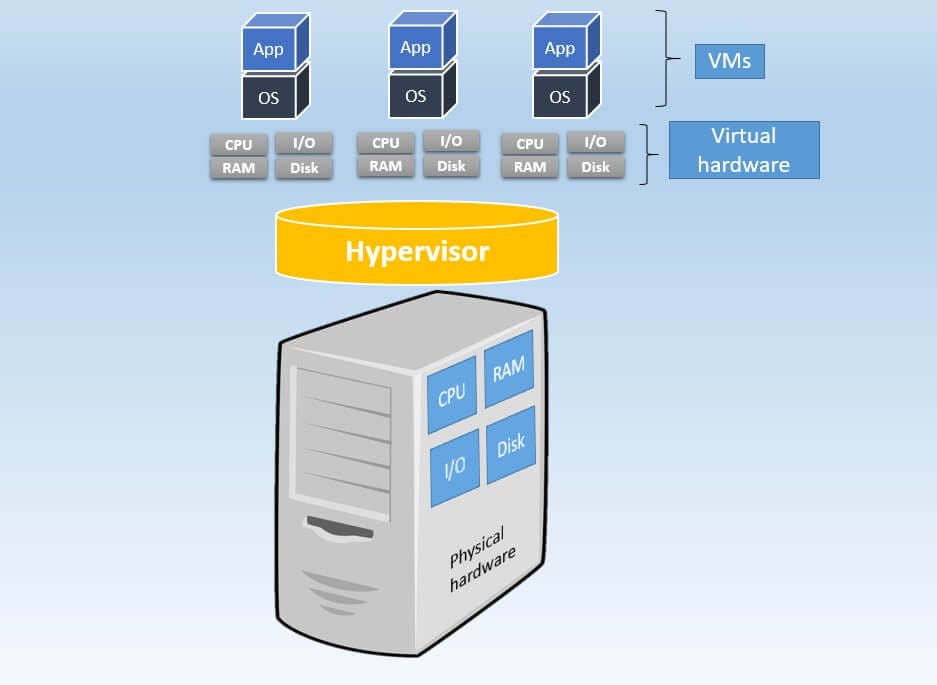
For simplicity, think of a virtual machine (VM) as a "computer made of software" which you can use to run any software you'd run on a real, physical computer. Like a physical machine, a virtual machine has its own operating system (Windows, Linux, etc.), storage, networking, configuration settings, and software, and it is fully isolated from other virtual machines running on that host.
Security benefits — Because virtual machines run in multiple operating systems, using a guest operating system on a VM allows you to run apps of questionable security and protects your host operating system. VMs also allow for better security forensics, pentesting and are often used to safely study computer viruses, isolating the viruses to avoid risking their host computer.
There are two main hypervisor types, referred to as “Type 1” (or “bare metal”) and “Type 2” (or “hosted”).
- Type 1 hypervisor acts like a lightweight operating system and runs directly on the host’s hardware.
- Type 2 hypervisor runs as a software layer on an operating system, like other computer programs.
- This tutorial use Oracle VM VirtualBox, the most popular free and open-source hosted hypervisor for x86 virtualization, developed by Oracle.
- There are other options from different vendors to achieve the same result:
- Make sure your PC support hardware virtualization (Windows)
- Reboot your computer
- Right when the computer is coming up from the black screen, press Delete, Esc, F1, F2, or F4. Each computer manufacturer uses a different key but it may show a brief message at boot telling you which one to press. If you miss it the first time, reboot and try again. It helps to tap the key about twice a second when the computer is coming up. If you are not able to enter the BIOS via this method, consult your computer’s manual.
- In the BIOS settings, find the configuration items related to the CPU. These can be in under the headings Processor, Chipset, or Northbridge.
- Enable virtualization; the setting may be called VT-x, AMD-V, SVM, or Vanderpool. Enable Intel VT-d or AMD IOMMU if the options are available.
- Save your changes and reboot.
⚠️ If you are unable to find the Virtualization settings in your BIOS it may mean that your computer does not support it.
-
Download the latest version of Virtual Box
-
Install Virtual Box and Extension Pack
- There is no special configuration on the Virtual Box installation process, just point, click and install.
- Once the installation is done, install the Extension Pack by double clicking it; The file extension is
.vbox-extpack. Don't worry about the warning prompts.
The next steps will cover how to create a NAT network on VirtualBox. In simple words Virtual Machines needs a virtual network adapter, to access the internet and segragete your Host IP(main OS) and Guest IP(VM).
- Launch VirtualBox and open the
Preferencespane
- Go to the
Network tabon the left pane, and then click thegreen plus buttonon the right
- By the default, VirtualBox automatically creates a NatNetwork. Click the
OKbutton and save this configuration
- Next part we will download the latest Kali Linux version and boot it up into Virtual box software
⚠️ Kali Linux Tutorial will be covered on the next module [Linux for Hackers].md
Kali Linux (formerly known as BackTrack Linux) is an open-source, Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. [+]
Kali Linux contains several hundred tools targeted towards various information security tasks, such as:
- Penetration Testing
- Security Research
- Computer Forensics
- Reverse Engineering
- Go to Offensive Security website:
- Download the Kali Linux VirtualBox image, make sure to select the
Virtual Box image (OVA)
Once you have installed VirtualBox and downloaded the Kali Linux image, you just need to import it to VirtualBox in order to make it work.
- Launch VirtualBox and click the
Import Buttonon the top center menu
- Next, browse the Kali Linux image (OVA) you just downloaded and choose it to be imported (as you can see in the image below).
- Next, you will be shown the settings for the virtual machine you are about to import. So, you can customize them or not – that is your choice based on your hardware capacity.
- If you have a computer with 8GB RAM and at least 2 cores available, leave the default settings.
- If your computer have 16GB RAM or more, I recommend to use 4GB RAM on Kali Linux, to do that, scroll down the configuration list and change the
RAM valueto4096MB
- You will now see the Kali box listed. So, just hit Start to launch it.
- Type the default credentials: username:
kali, password:kali.- Tip: On Linux, you can change the default password of the current user by typing
passwdon terminal.
- Tip: On Linux, you can change the default password of the current user by typing
- Done!
⚠️ Next module you'll learn some techniques of Kali distro and how to operate on Linux itself.