diff --git a/blog-service/2025-08-20-apps-extrahop.md b/blog-service/2025-08-20-apps-extrahop.md
new file mode 100644
index 0000000000..b8f12de400
--- /dev/null
+++ b/blog-service/2025-08-20-apps-extrahop.md
@@ -0,0 +1,12 @@
+---
+title: ExtraHop RevealX 360 (Apps)
+image: https://help.sumologic.com/img/reuse/rss-image.jpg
+keywords:
+ - apps
+ - extrahop-revealx-360
+hide_table_of_contents: true
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+
+We're excited to introduce the new ExtraHop RevealX 360 app for Sumo Logic, which enables you to gain real-time visibility into your security hub findings data. This app can help security teams to monitor detection trends, track changes in risk levels, and gain insights into the most frequently observed MITRE techniques, top destination devices, and key targets on the network. [Learn more](/docs/integrations/webhooks/extrahop-revealx-360).
diff --git a/cid-redirects.json b/cid-redirects.json
index 94de56132b..78de4806b0 100644
--- a/cid-redirects.json
+++ b/cid-redirects.json
@@ -1636,6 +1636,7 @@
"/cid/10210": "/docs/integrations/saas-cloud/proofpoint-tap",
"/cid/10202": "/docs/integrations/saas-cloud/mimecast",
"/cid/12222": "/docs/integrations/webhooks/snyk",
+ "/cid/12223": "/docs/integrations/webhooks/extrahop-revealx-360",
"/cid/1119": "/docs/integrations/saas-cloud/druva",
"/cid/10191": "/docs/integrations/saas-cloud/akamai-datastream",
"/cid/10194": "/docs/integrations/saas-cloud/proofpoint-on-demand",
diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 0f6543bafc..8dc6da1e76 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -219,7 +219,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [ESET](https://www.eset.com/us/) | Cloud SIEM integration: [ESET](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/ced86de0-64e4-4e7c-ae25-fb5b3dff3cb8.md) |
|
| [ESET](https://www.eset.com/us/) | Cloud SIEM integration: [ESET](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/ced86de0-64e4-4e7c-ae25-fb5b3dff3cb8.md) |
| }) | [Exabeam](https://www.exabeam.com/) | Cloud SIEM integration: [Exabeam](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/9d2d799d-2d6c-4894-a46f-0cce00641bcb.md) |
|
| [Exabeam](https://www.exabeam.com/) | Cloud SIEM integration: [Exabeam](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/9d2d799d-2d6c-4894-a46f-0cce00641bcb.md) |
| }) | [Exploit Database](https://www.exploit-db.com/) | Automation integration: [Exploit Database](/docs/platform-services/automation-service/app-central/integrations/exploit-database/) |
-|
| [Exploit Database](https://www.exploit-db.com/) | Automation integration: [Exploit Database](/docs/platform-services/automation-service/app-central/integrations/exploit-database/) |
-| }) | [ExtraHop](https://www.extrahop.com/) | Cloud SIEM integration: [Extrahop](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/a8b03e2e-7497-4104-874d-cafd03aeb4c1.md)
| [ExtraHop](https://www.extrahop.com/) | Cloud SIEM integration: [Extrahop](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/a8b03e2e-7497-4104-874d-cafd03aeb4c1.md)
Community app: [Sumo Logic for ExtraHop Reveal(x) 360](https://github.com/SumoLogic/sumologic-content/tree/master/ExtraHop%20Reveal(x)%20360) |
+| }) | [ExtraHop](https://www.extrahop.com/) | App: [ExtraHop RevealX 360](/docs/integrations/webhooks/extrahop-revealx-360)
| [ExtraHop](https://www.extrahop.com/) | App: [ExtraHop RevealX 360](/docs/integrations/webhooks/extrahop-revealx-360)
- Cloud SIEM integration: [ExtraHop](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/a8b03e2e-7497-4104-874d-cafd03aeb4c1.md)
Community app: [Sumo Logic for ExtraHop Reveal(x) 360](https://github.com/SumoLogic/sumologic-content/tree/master/ExtraHop%20Reveal(x)%20360) |
## F
diff --git a/docs/integrations/webhooks/extrahop-revealx-360.md b/docs/integrations/webhooks/extrahop-revealx-360.md
new file mode 100644
index 0000000000..d038688e35
--- /dev/null
+++ b/docs/integrations/webhooks/extrahop-revealx-360.md
@@ -0,0 +1,169 @@
+---
+id: extrahop-revealx-360
+title: ExtraHop RevealX 360
+sidebar_label: ExtraHop RevealX 360
+description: The ExtraHop RevealX 360 app for Sumo Logic provides security analysts with critical visibility into your ExtraHop RevealX 360 environment.
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+
+}) +
+The ExtraHop RevealX 360 app offers powerful network detection and response capabilities, providing organisations with in-depth visibility into security threats throughout their environment. By centralizing detection data such as total detections, average risk scores, MITRE attack techniques, and destination device activity, this app allows security teams to quickly identify, prioritize, and investigate suspicious activities.
+
+By leveraging real-time metrics and contextual threat information, the app highlights patterns of malicious behavior, high-risk destinations, and devices originating from embargoed locations. This insight helps teams monitor evolving risks, identify vulnerable assets, and understand the tactics and techniques targeting their networks.
+
+With its comprehensive detection summaries, geographical breakdowns, and detailed device-level insights, the ExtraHop RevealX 360 app empowers organizations to respond effectively to emerging threats. By maintaining a clear view of their security posture, teams can act swiftly, reduce dwell time, and strengthen defenses to protect critical systems and data.
+
+:::info
+This app includes [built-in monitors](#extrahop-revealx-360-alerts). For details on creating custom monitors, refer to [Create monitors for ExtraHop RevealX 360 app](#create-monitors-for-extrahop-revealx-360-app).
+:::
+
+## Log types
+
+The Sumo Logic app for ExtraHop RevealX 360 ingests [detection events](https://docs.extrahop.com/current/detections-create-notification-rule/) via a webhook.
+
+## Sample log messages
+
+```json title="Detection log"
+{
+ "mitre_techniques": [
+ {
+ "id": "T1021",
+ "name": "Remote Services"
+ },
+ {
+ "id": "T1078",
+ "name": "Valid Accounts"
+ },
+ {
+ "id": "T1570",
+ "name": "Lateral Tool Transfer"
+ }
+ ],
+ "recommended": true,
+ "time": 1755070340426,
+ "dst": {
+ "type": "device",
+ "ipaddr": null,
+ "hostname": null,
+ "role": "victim",
+ "endpoint": "server",
+ "username": null,
+ "device": {
+ "oid": 17550703405,
+ "macaddr": "0E:C9:8B:2C:62:F3",
+ "name": "pc2.i.rx.tours",
+ "ipaddrs": [
+ "109.248.151.179"
+ ]
+ }
+ },
+ "id": 17550703402,
+ "url": "https://envio1206.duckdns.org/extrahop/#/detections/detail/17550703402/?from=1755070340&until=1755070340&interval_type=DT",
+ "risk_score": 65,
+ "recommended_factors": [
+ "top_offender"
+ ],
+ "additional_participants": [],
+ "categories_ids": [
+ "sec",
+ "sec.lateral",
+ "sec.attack"
+ ],
+ "properties": {},
+ "type": "New SMB Executable File Transfer Activity",
+ "description": "pc2.i.rx.tours received an executable file. This is the first time in several weeks ExtraHop observed this activity. Check unexpected files for malware.\nExample of a suspicious transferred file path. View more in investigation steps\n\nADMIN$\\xxFDMxx.exe\n",
+ "src": {
+ "type": "device",
+ "ipaddr": "109.248.151.179",
+ "hostname": null,
+ "role": "offender",
+ "endpoint": "client",
+ "username": null,
+ "device": {
+ "oid": 17550703400,
+ "macaddr": "0E:86:1F:88:60:E9",
+ "name": "pc3.i.rx.tours"
+ }
+ },
+ "title": "New SMB Executable File Transfer Activity"
+}
+```
+
+## Sample queries
+
+```sql title="Total Detections"
+_sourceCategory=Labs/extraHop
+| json "id", "time", "url", "src.username", "risk_score", "mitre_techniques[*].name", "dst.device.name", "dst.device.macaddr", "dst.device.ipaddrs.[*]", "dst.ipaddr", "type", "title", "description", "recommended_factors", "categories_ids", "dst.hostname", "dst.role" as id, time, url, src_username, risk_score, mitre_techniques, dst_device_name, dst_device_mac_address, dst_device_ip_list, dst_device_ip_2, type, title, description, recommended_factors, categories_ids, dst_hostname, dst_role nodrop
+
+| extract field=mitre_techniques "\"?(?[\w\s\-&.,]*)\"?[,\n\]]" multi nodrop
+| extract field=dst_device_ip_list "\"?(?[\w\s\-&.,]*)\"?[,\n\]]" nodrop
+| if (isBlank(dst_device_ip_1), dst_device_ip_2, dst_device_ip_1) as dst_device_ip
+
+| where techniques matches "*"
+
+| count by id, time, url, src_username
+| count
+```
+
+## Setup
+
+### Source configuration
+
+Follow the below steps to configure the Hosted Collector to receive ExtraHop RevealX 360 events:
+
+1. In the Sumo Logic portal, create a new [Hosted Collector](/docs/send-data/hosted-collectors/configure-hosted-collector/) or use an existing one. Then add an [HTTP Logs and Metrics Source](/docs/send-data/hosted-collectors/http-source/logs-metrics/#configure-an-httplogs-and-metrics-source).
+2. Configure **Source Category** in the HTTP source - for example, `webhook/extrahop-revealx` - for the ExtraHop RevealX 360 integration.
+3. Copy and save the endpoint URL of the source.
+
+### Vendor configuration
+
+Configure the webhook integration in ExtraHop RevealX 360 to send events to the Sumo Logic HTTP source. Once configured, it will be triggered each time the events occur within your Extrahop RevealX 360 account.
+
+To configure the ExtraHop RevealX 360 webhook, refer to the [ExtraHop RevealX 360 Documentation](https://docs.extrahop.com/current/detections-create-notification-rule/).
+
+### Installing the ExtraHop RevealX 360 app
+
+import AppInstall2 from '../../reuse/apps/app-install-v2.md';
+
+
+
+## Viewing ExtraHop RevealX 360 dashboards
+
+import ViewDashboards from '../../reuse/apps/view-dashboards.md';
+
+
+
+### Security
+
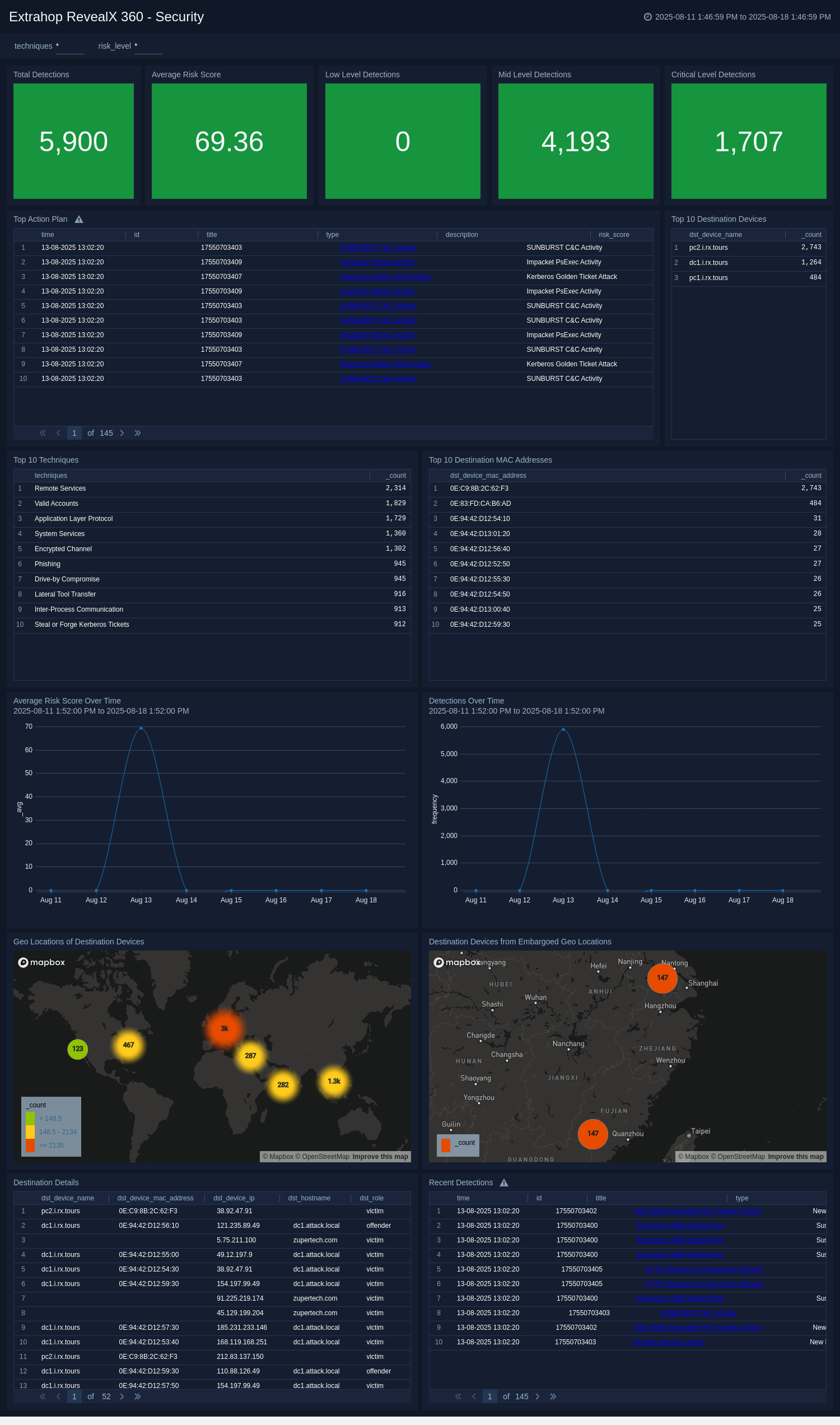
+The **ExtraHop RevealX 360 - Security** dashboard provides a comprehensive overview of network detection activities and the overall security posture of your environment. It offers insights into total detections, average risk scores, and the distribution of techniques over time, allowing teams to quickly identify unusual patterns and potential areas of concern.
+
+This dashboard helps security teams monitor detection trends, track changes in risk levels, and gain insights into the most frequently observed MITRE techniques, top destination devices, and key targets on the network. It also highlights detections linked to high-risk or embargoed geolocations, offering valuable context for prioritizing investigations.
+
+By consolidating these insights into a unified view, the dashboard enhances threat detection, supports more informed response actions, and strengthens defenses against evolving network-based attacks.
+
+The ExtraHop RevealX 360 app offers powerful network detection and response capabilities, providing organisations with in-depth visibility into security threats throughout their environment. By centralizing detection data such as total detections, average risk scores, MITRE attack techniques, and destination device activity, this app allows security teams to quickly identify, prioritize, and investigate suspicious activities.
+
+By leveraging real-time metrics and contextual threat information, the app highlights patterns of malicious behavior, high-risk destinations, and devices originating from embargoed locations. This insight helps teams monitor evolving risks, identify vulnerable assets, and understand the tactics and techniques targeting their networks.
+
+With its comprehensive detection summaries, geographical breakdowns, and detailed device-level insights, the ExtraHop RevealX 360 app empowers organizations to respond effectively to emerging threats. By maintaining a clear view of their security posture, teams can act swiftly, reduce dwell time, and strengthen defenses to protect critical systems and data.
+
+:::info
+This app includes [built-in monitors](#extrahop-revealx-360-alerts). For details on creating custom monitors, refer to [Create monitors for ExtraHop RevealX 360 app](#create-monitors-for-extrahop-revealx-360-app).
+:::
+
+## Log types
+
+The Sumo Logic app for ExtraHop RevealX 360 ingests [detection events](https://docs.extrahop.com/current/detections-create-notification-rule/) via a webhook.
+
+## Sample log messages
+
+```json title="Detection log"
+{
+ "mitre_techniques": [
+ {
+ "id": "T1021",
+ "name": "Remote Services"
+ },
+ {
+ "id": "T1078",
+ "name": "Valid Accounts"
+ },
+ {
+ "id": "T1570",
+ "name": "Lateral Tool Transfer"
+ }
+ ],
+ "recommended": true,
+ "time": 1755070340426,
+ "dst": {
+ "type": "device",
+ "ipaddr": null,
+ "hostname": null,
+ "role": "victim",
+ "endpoint": "server",
+ "username": null,
+ "device": {
+ "oid": 17550703405,
+ "macaddr": "0E:C9:8B:2C:62:F3",
+ "name": "pc2.i.rx.tours",
+ "ipaddrs": [
+ "109.248.151.179"
+ ]
+ }
+ },
+ "id": 17550703402,
+ "url": "https://envio1206.duckdns.org/extrahop/#/detections/detail/17550703402/?from=1755070340&until=1755070340&interval_type=DT",
+ "risk_score": 65,
+ "recommended_factors": [
+ "top_offender"
+ ],
+ "additional_participants": [],
+ "categories_ids": [
+ "sec",
+ "sec.lateral",
+ "sec.attack"
+ ],
+ "properties": {},
+ "type": "New SMB Executable File Transfer Activity",
+ "description": "pc2.i.rx.tours received an executable file. This is the first time in several weeks ExtraHop observed this activity. Check unexpected files for malware.\nExample of a suspicious transferred file path. View more in investigation steps\n\nADMIN$\\xxFDMxx.exe\n",
+ "src": {
+ "type": "device",
+ "ipaddr": "109.248.151.179",
+ "hostname": null,
+ "role": "offender",
+ "endpoint": "client",
+ "username": null,
+ "device": {
+ "oid": 17550703400,
+ "macaddr": "0E:86:1F:88:60:E9",
+ "name": "pc3.i.rx.tours"
+ }
+ },
+ "title": "New SMB Executable File Transfer Activity"
+}
+```
+
+## Sample queries
+
+```sql title="Total Detections"
+_sourceCategory=Labs/extraHop
+| json "id", "time", "url", "src.username", "risk_score", "mitre_techniques[*].name", "dst.device.name", "dst.device.macaddr", "dst.device.ipaddrs.[*]", "dst.ipaddr", "type", "title", "description", "recommended_factors", "categories_ids", "dst.hostname", "dst.role" as id, time, url, src_username, risk_score, mitre_techniques, dst_device_name, dst_device_mac_address, dst_device_ip_list, dst_device_ip_2, type, title, description, recommended_factors, categories_ids, dst_hostname, dst_role nodrop
+
+| extract field=mitre_techniques "\"?(?[\w\s\-&.,]*)\"?[,\n\]]" multi nodrop
+| extract field=dst_device_ip_list "\"?(?[\w\s\-&.,]*)\"?[,\n\]]" nodrop
+| if (isBlank(dst_device_ip_1), dst_device_ip_2, dst_device_ip_1) as dst_device_ip
+
+| where techniques matches "*"
+
+| count by id, time, url, src_username
+| count
+```
+
+## Setup
+
+### Source configuration
+
+Follow the below steps to configure the Hosted Collector to receive ExtraHop RevealX 360 events:
+
+1. In the Sumo Logic portal, create a new [Hosted Collector](/docs/send-data/hosted-collectors/configure-hosted-collector/) or use an existing one. Then add an [HTTP Logs and Metrics Source](/docs/send-data/hosted-collectors/http-source/logs-metrics/#configure-an-httplogs-and-metrics-source).
+2. Configure **Source Category** in the HTTP source - for example, `webhook/extrahop-revealx` - for the ExtraHop RevealX 360 integration.
+3. Copy and save the endpoint URL of the source.
+
+### Vendor configuration
+
+Configure the webhook integration in ExtraHop RevealX 360 to send events to the Sumo Logic HTTP source. Once configured, it will be triggered each time the events occur within your Extrahop RevealX 360 account.
+
+To configure the ExtraHop RevealX 360 webhook, refer to the [ExtraHop RevealX 360 Documentation](https://docs.extrahop.com/current/detections-create-notification-rule/).
+
+### Installing the ExtraHop RevealX 360 app
+
+import AppInstall2 from '../../reuse/apps/app-install-v2.md';
+
+
+
+## Viewing ExtraHop RevealX 360 dashboards
+
+import ViewDashboards from '../../reuse/apps/view-dashboards.md';
+
+
+
+### Security
+
+The **ExtraHop RevealX 360 - Security** dashboard provides a comprehensive overview of network detection activities and the overall security posture of your environment. It offers insights into total detections, average risk scores, and the distribution of techniques over time, allowing teams to quickly identify unusual patterns and potential areas of concern.
+
+This dashboard helps security teams monitor detection trends, track changes in risk levels, and gain insights into the most frequently observed MITRE techniques, top destination devices, and key targets on the network. It also highlights detections linked to high-risk or embargoed geolocations, offering valuable context for prioritizing investigations.
+
+By consolidating these insights into a unified view, the dashboard enhances threat detection, supports more informed response actions, and strengthens defenses against evolving network-based attacks.
 +
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+### ExtraHop RevealX 360 alerts
+
+| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
+|:--|:--|:--|:--|
+| `ExtraHop RevealX 360 - Destination Devices from Embargoed Geo Locations` | This alert is fired when events originating from embargoed locations are detected, ensuring adherence to security restrictions and protocols. | Critical | Count > 0 |
+| `ExtraHop RevealX 360 - Critical Detections` | This alert is fired when detections are identified with a risk score greater than 70, signaling high-severity threats that require immediate investigation and remediation. | Critical | Count > 0 |
+
+## Upgrade/Downgrade the ExtraHop RevealX 360 app (Optional)
+
+import AppUpdate from '../../reuse/apps/app-update.md';
+
+
+
+## Uninstalling the ExtraHop RevealX 360 app (Optional)
+
+import AppUninstall from '../../reuse/apps/app-uninstall.md';
+
+
diff --git a/sidebars.ts b/sidebars.ts
index 78b170f656..183f94fe85 100644
--- a/sidebars.ts
+++ b/sidebars.ts
@@ -2688,6 +2688,7 @@ integrations: [
'integrations/webhooks/bugsnag',
'integrations/webhooks/configcat',
'integrations/webhooks/emnify',
+ 'integrations/webhooks/extrahop-revealx-360',
'integrations/webhooks/firefly',
'integrations/webhooks/flagsmith',
'integrations/webhooks/grafana-oncall',
diff --git a/static/img/send-data/extrahop-revealx-360-icon.png b/static/img/send-data/extrahop-revealx-360-icon.png
new file mode 100644
index 0000000000..8e2dc56d7d
Binary files /dev/null and b/static/img/send-data/extrahop-revealx-360-icon.png differ
+
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+### ExtraHop RevealX 360 alerts
+
+| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
+|:--|:--|:--|:--|
+| `ExtraHop RevealX 360 - Destination Devices from Embargoed Geo Locations` | This alert is fired when events originating from embargoed locations are detected, ensuring adherence to security restrictions and protocols. | Critical | Count > 0 |
+| `ExtraHop RevealX 360 - Critical Detections` | This alert is fired when detections are identified with a risk score greater than 70, signaling high-severity threats that require immediate investigation and remediation. | Critical | Count > 0 |
+
+## Upgrade/Downgrade the ExtraHop RevealX 360 app (Optional)
+
+import AppUpdate from '../../reuse/apps/app-update.md';
+
+
+
+## Uninstalling the ExtraHop RevealX 360 app (Optional)
+
+import AppUninstall from '../../reuse/apps/app-uninstall.md';
+
+
diff --git a/sidebars.ts b/sidebars.ts
index 78b170f656..183f94fe85 100644
--- a/sidebars.ts
+++ b/sidebars.ts
@@ -2688,6 +2688,7 @@ integrations: [
'integrations/webhooks/bugsnag',
'integrations/webhooks/configcat',
'integrations/webhooks/emnify',
+ 'integrations/webhooks/extrahop-revealx-360',
'integrations/webhooks/firefly',
'integrations/webhooks/flagsmith',
'integrations/webhooks/grafana-oncall',
diff --git a/static/img/send-data/extrahop-revealx-360-icon.png b/static/img/send-data/extrahop-revealx-360-icon.png
new file mode 100644
index 0000000000..8e2dc56d7d
Binary files /dev/null and b/static/img/send-data/extrahop-revealx-360-icon.png differ
 +
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+}) | [ESET](https://www.eset.com/us/) | Cloud SIEM integration: [ESET](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/ced86de0-64e4-4e7c-ae25-fb5b3dff3cb8.md) |
|
| [ESET](https://www.eset.com/us/) | Cloud SIEM integration: [ESET](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/ced86de0-64e4-4e7c-ae25-fb5b3dff3cb8.md) |
| }) | [Exploit Database](https://www.exploit-db.com/) | Automation integration: [Exploit Database](/docs/platform-services/automation-service/app-central/integrations/exploit-database/) |
-|
| [Exploit Database](https://www.exploit-db.com/) | Automation integration: [Exploit Database](/docs/platform-services/automation-service/app-central/integrations/exploit-database/) |
-| }) | [ExtraHop](https://www.extrahop.com/) | Cloud SIEM integration: [Extrahop](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/a8b03e2e-7497-4104-874d-cafd03aeb4c1.md)
| [ExtraHop](https://www.extrahop.com/) | Cloud SIEM integration: [Extrahop](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/a8b03e2e-7497-4104-874d-cafd03aeb4c1.md) }) | [ExtraHop](https://www.extrahop.com/) | App: [ExtraHop RevealX 360](/docs/integrations/webhooks/extrahop-revealx-360)
| [ExtraHop](https://www.extrahop.com/) | App: [ExtraHop RevealX 360](/docs/integrations/webhooks/extrahop-revealx-360)  +
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+## Create monitors for ExtraHop RevealX 360 app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+