+ })
+})
Vectra
+Gain visibility into security threats detected across networks, cloud environments, and endpoints.
+}) | [Varnish](https://www.varnish-software.com/) | Apps:
| [Varnish](https://www.varnish-software.com/) | Apps: }) | [Varonis](https://www.varonis.com/) | Cloud SIEM integration: [Varonis](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/20270f89-127e-4055-96ec-56045e67e163.md) |
-|
| [Varonis](https://www.varonis.com/) | Cloud SIEM integration: [Varonis](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/vendors/20270f89-127e-4055-96ec-56045e67e163.md) |
-| }) | [Vectra](https://www.vectra.ai/) | Automation integration: [Vectra](/docs/platform-services/automation-service/app-central/integrations/vectra/)
| [Vectra](https://www.vectra.ai/) | Automation integration: [Vectra](/docs/platform-services/automation-service/app-central/integrations/vectra/) }) | [Vectra](https://www.vectra.ai/) | App: [Vectra](/docs/integrations/saas-cloud/vectra)
| [Vectra](https://www.vectra.ai/) | App: [Vectra](/docs/integrations/saas-cloud/vectra) }) | [VirusTotal](https://www.virustotal.com/) | Automation integrations:
| [VirusTotal](https://www.virustotal.com/) | Automation integrations: }) | [VMRay](https://www.vmray.com/) | Automation integration: [VMRay](/docs/platform-services/automation-service/app-central/integrations/vmray/) |
|
| [VMRay](https://www.vmray.com/) | Automation integration: [VMRay](/docs/platform-services/automation-service/app-central/integrations/vmray/) |
| }) | [VMware](https://www.vmware.com/) | Apps:
| [VMware](https://www.vmware.com/) | Apps: Analyze authentication events, user activities, and potential security threats.
+})
Gain visibility into security threats detected across networks, cloud environments, and endpoints.
+})
}) +
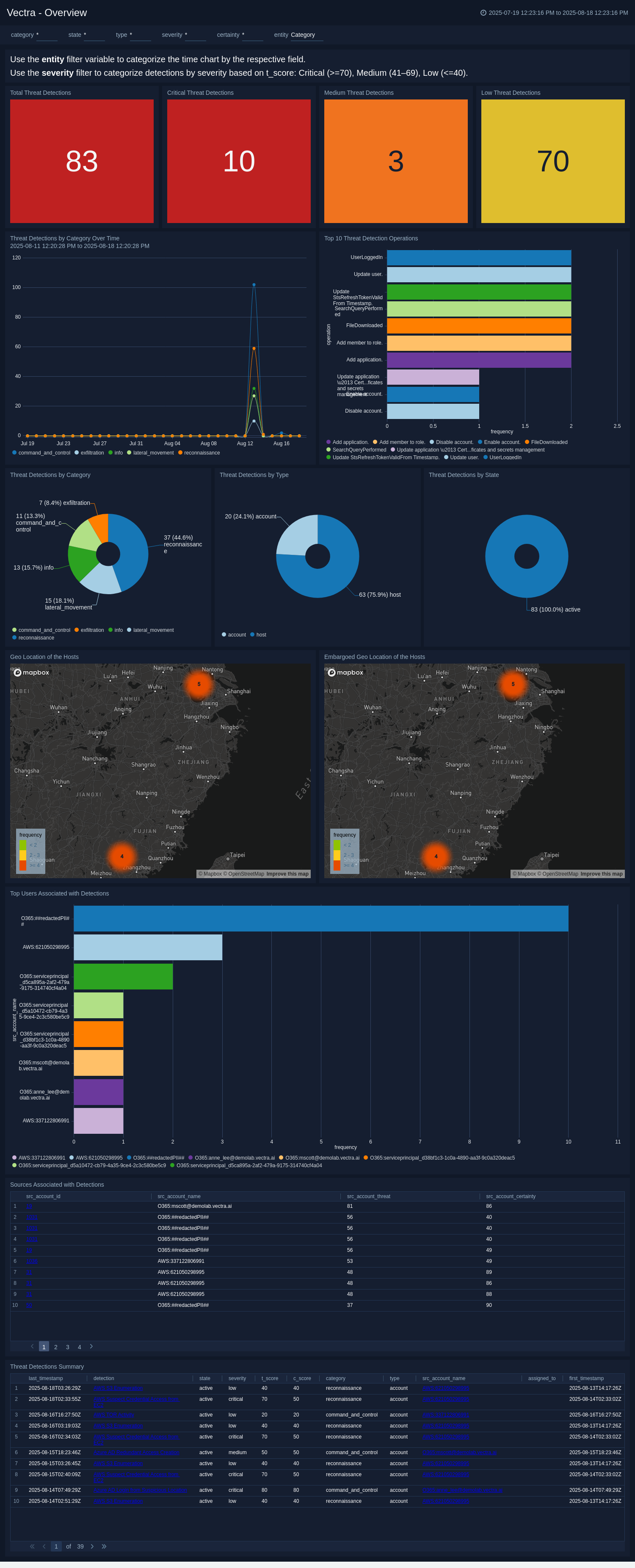
+The Vectra app offers comprehensive visibility into security threats detected across networks, cloud environments, and endpoints. It consolidates threat intelligence from multiple sources, categorizing detections by their severity, type, and behavior, while providing detailed contextual data to accelerate investigations. With interactive dashboards and targeted monitoring tools, security teams can track trends, pinpoint high-risk activities, and measure remediation effectiveness. By combining threat scoring, detection timelines, and enriched metadata, the app empowers proactive threat hunting, rapid incident response, and continuous improvement of security posture.
+
+:::info
+This app includes [built-in monitors](#vectra-alerts). For details on creating custom monitors, refer to the [Create monitors for Vectra app](#create-monitors-for-the-vectra-app).
+:::
+
+## Log types
+
+This app uses Sumo Logic’s [Vectra Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/vectra-source/) to collect detections from the Vectra platform.
+
+### Sample log message
+
+```json title="Detection"
+{
+ "summary": {
+ "user_agents": [
+ "Microsoft Azure CLI",
+ "Microsoft Azure CLI"
+ ],
+ "browser": [
+ "Chrome 138.0.0",
+ "Chrome"
+ ],
+ "operating_system": [
+ "Linux",
+ "Linux"
+ ],
+ "workloads": [
+ "Azure Resource Manager",
+ "AzureActiveDirectory"
+ ],
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "description": "This account was seen using a scripting engine to access services in Azure AD which is unusual for the account. Unusual usage of scripting engines in Azure AD and Microsoft 365 can be indicative of a compromised account."
+ },
+ "data_source": {
+ "type": "o365",
+ "connection_name": "M365-Demo",
+ "connection_id": "s9s9c5cj"
+ },
+ "filtered_by_rule": false,
+ "src_account": {
+ "id": 1034,
+ "name": "O365:demolab.vectra.ai",
+ "url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/accounts/1034",
+ "threat": 30,
+ "certainty": 90,
+ "privilege_level": null,
+ "privilege_category": null
+ },
+ "threat": 70,
+ "last_timestamp": "2025-08-12T18:29:21Z",
+ "is_targeting_key_asset": false,
+ "sensor_name": "Vectra X",
+ "filtered_by_ai": false,
+ "id": 3586,
+ "c_score": 60,
+ "src_ip": null,
+ "assigned_date": null,
+ "filtered_by_user": false,
+ "is_custom_model": false,
+ "assigned_to": null,
+ "detection_category": "lateral_movement",
+ "note_modified_timestamp": null,
+ "created_timestamp": "2025-08-12T18:53:29Z",
+ "note": null,
+ "is_marked_custom": false,
+ "url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
+ "state": "active",
+ "detection": "Azure AD Unusual Scripting Engine Usage",
+ "triage_rule_id": null,
+ "groups": [],
+ "category": "lateral_movement",
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "certainty": 60,
+ "t_score": 70,
+ "tags": [],
+ "note_modified_by": null,
+ "detection_url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
+ "description": null,
+ "notes": [],
+ "detection_type": "Azure AD Unusual Scripting Engine Usage",
+ "custom_detection": null,
+ "sensor": "s9s9c5cj",
+ "targets_key_asset": false,
+ "is_triaged": false,
+ "src_host": null,
+ "type": "account",
+ "grouped_details": [
+ {
+ "workload": "Azure Resource Manager",
+ "user_agent": "Microsoft Azure CLI",
+ "operating_system": "Linux",
+ "browser": "Chrome 138.0.0",
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "operations_count": 1,
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "last_timestamp": "2025-08-12T18:29:21Z"
+ },
+ {
+ "workload": "AzureActiveDirectory",
+ "user_agent": "Microsoft Azure CLI",
+ "operating_system": "Linux",
+ "browser": "Chrome",
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "operations_count": 1,
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "last_timestamp": "2025-08-12T18:29:21Z"
+ }
+ ]
+}
+```
+
+### Sample queries
+
+```sql title="Total Detections"
+_sourceCategory="Labs/Vectra"
+| json "id","last_timestamp","first_timestamp","state","t_score","c_score","category","type","summary.operations[*]","grouped_details[*].src_ips[*]","detection_url","assigned_to","detection","certainty","src_account.id","src_account.name","src_account.url","src_account.threat","src_account.certainty" as id,last_timestamp,first_timestamp,state,t_score,c_score,category,type,operations,src_ips,detection_url,assigned_to,detection,certainty,src_account_id,src_account_name,src_account_url,src_account_threat,src_account_certainty nodrop
+| if (t_score>=70,"critical",if(t_score>=41 and t_score<=69, "medium", if(t_score<=40,"low","unknown"))) as severity
+
+// global filters
+| where isNull(state) or state matches "{{state}}"
+| where isNull(category) or category matches "{{category}}"
+| where isNull(severity) or severity matches "{{severity}}"
+| where isNull(type) or type matches "{{type}}"
+| where isNull(certainty) or certainty matches "{{certainty}}"
+
+// panel specific
+| count by id
+| count
+```
+
+## Collection configuration and app installation
+
+import CollectionConfiguration from '../../reuse/apps/collection-configuration.md';
+
+
+
+The Vectra app offers comprehensive visibility into security threats detected across networks, cloud environments, and endpoints. It consolidates threat intelligence from multiple sources, categorizing detections by their severity, type, and behavior, while providing detailed contextual data to accelerate investigations. With interactive dashboards and targeted monitoring tools, security teams can track trends, pinpoint high-risk activities, and measure remediation effectiveness. By combining threat scoring, detection timelines, and enriched metadata, the app empowers proactive threat hunting, rapid incident response, and continuous improvement of security posture.
+
+:::info
+This app includes [built-in monitors](#vectra-alerts). For details on creating custom monitors, refer to the [Create monitors for Vectra app](#create-monitors-for-the-vectra-app).
+:::
+
+## Log types
+
+This app uses Sumo Logic’s [Vectra Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/vectra-source/) to collect detections from the Vectra platform.
+
+### Sample log message
+
+```json title="Detection"
+{
+ "summary": {
+ "user_agents": [
+ "Microsoft Azure CLI",
+ "Microsoft Azure CLI"
+ ],
+ "browser": [
+ "Chrome 138.0.0",
+ "Chrome"
+ ],
+ "operating_system": [
+ "Linux",
+ "Linux"
+ ],
+ "workloads": [
+ "Azure Resource Manager",
+ "AzureActiveDirectory"
+ ],
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "description": "This account was seen using a scripting engine to access services in Azure AD which is unusual for the account. Unusual usage of scripting engines in Azure AD and Microsoft 365 can be indicative of a compromised account."
+ },
+ "data_source": {
+ "type": "o365",
+ "connection_name": "M365-Demo",
+ "connection_id": "s9s9c5cj"
+ },
+ "filtered_by_rule": false,
+ "src_account": {
+ "id": 1034,
+ "name": "O365:demolab.vectra.ai",
+ "url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/accounts/1034",
+ "threat": 30,
+ "certainty": 90,
+ "privilege_level": null,
+ "privilege_category": null
+ },
+ "threat": 70,
+ "last_timestamp": "2025-08-12T18:29:21Z",
+ "is_targeting_key_asset": false,
+ "sensor_name": "Vectra X",
+ "filtered_by_ai": false,
+ "id": 3586,
+ "c_score": 60,
+ "src_ip": null,
+ "assigned_date": null,
+ "filtered_by_user": false,
+ "is_custom_model": false,
+ "assigned_to": null,
+ "detection_category": "lateral_movement",
+ "note_modified_timestamp": null,
+ "created_timestamp": "2025-08-12T18:53:29Z",
+ "note": null,
+ "is_marked_custom": false,
+ "url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
+ "state": "active",
+ "detection": "Azure AD Unusual Scripting Engine Usage",
+ "triage_rule_id": null,
+ "groups": [],
+ "category": "lateral_movement",
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "certainty": 60,
+ "t_score": 70,
+ "tags": [],
+ "note_modified_by": null,
+ "detection_url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
+ "description": null,
+ "notes": [],
+ "detection_type": "Azure AD Unusual Scripting Engine Usage",
+ "custom_detection": null,
+ "sensor": "s9s9c5cj",
+ "targets_key_asset": false,
+ "is_triaged": false,
+ "src_host": null,
+ "type": "account",
+ "grouped_details": [
+ {
+ "workload": "Azure Resource Manager",
+ "user_agent": "Microsoft Azure CLI",
+ "operating_system": "Linux",
+ "browser": "Chrome 138.0.0",
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "operations_count": 1,
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "last_timestamp": "2025-08-12T18:29:21Z"
+ },
+ {
+ "workload": "AzureActiveDirectory",
+ "user_agent": "Microsoft Azure CLI",
+ "operating_system": "Linux",
+ "browser": "Chrome",
+ "operations": [
+ "UserLoggedIn"
+ ],
+ "operations_count": 1,
+ "src_ips": [
+ "80.117.40.124"
+ ],
+ "first_timestamp": "2025-08-12T18:29:21Z",
+ "last_timestamp": "2025-08-12T18:29:21Z"
+ }
+ ]
+}
+```
+
+### Sample queries
+
+```sql title="Total Detections"
+_sourceCategory="Labs/Vectra"
+| json "id","last_timestamp","first_timestamp","state","t_score","c_score","category","type","summary.operations[*]","grouped_details[*].src_ips[*]","detection_url","assigned_to","detection","certainty","src_account.id","src_account.name","src_account.url","src_account.threat","src_account.certainty" as id,last_timestamp,first_timestamp,state,t_score,c_score,category,type,operations,src_ips,detection_url,assigned_to,detection,certainty,src_account_id,src_account_name,src_account_url,src_account_threat,src_account_certainty nodrop
+| if (t_score>=70,"critical",if(t_score>=41 and t_score<=69, "medium", if(t_score<=40,"low","unknown"))) as severity
+
+// global filters
+| where isNull(state) or state matches "{{state}}"
+| where isNull(category) or category matches "{{category}}"
+| where isNull(severity) or severity matches "{{severity}}"
+| where isNull(type) or type matches "{{type}}"
+| where isNull(certainty) or certainty matches "{{certainty}}"
+
+// panel specific
+| count by id
+| count
+```
+
+## Collection configuration and app installation
+
+import CollectionConfiguration from '../../reuse/apps/collection-configuration.md';
+
+ +
+### Security
+
+The **Vectra - Security** dashboard focuses on advanced and high-severity threats that require immediate attention. It highlights critical threat detections, command-and-control activities, and account-based privilege escalation attempts, as well as anomalies in Azure AD operations. Persistent threats are tracked with metrics on time-to-remediation, enabling teams to assess response efficiency. Each panels are designed to surface patterns that indicate targeted attacks, lateral movement, or ongoing compromise attempts. By consolidating these high-priority insights, the dashboard helps security analysts quickly isolate urgent incidents, understand attack context, and coordinate effective containment and remediation strategies.
+
+### Security
+
+The **Vectra - Security** dashboard focuses on advanced and high-severity threats that require immediate attention. It highlights critical threat detections, command-and-control activities, and account-based privilege escalation attempts, as well as anomalies in Azure AD operations. Persistent threats are tracked with metrics on time-to-remediation, enabling teams to assess response efficiency. Each panels are designed to surface patterns that indicate targeted attacks, lateral movement, or ongoing compromise attempts. By consolidating these high-priority insights, the dashboard helps security analysts quickly isolate urgent incidents, understand attack context, and coordinate effective containment and remediation strategies.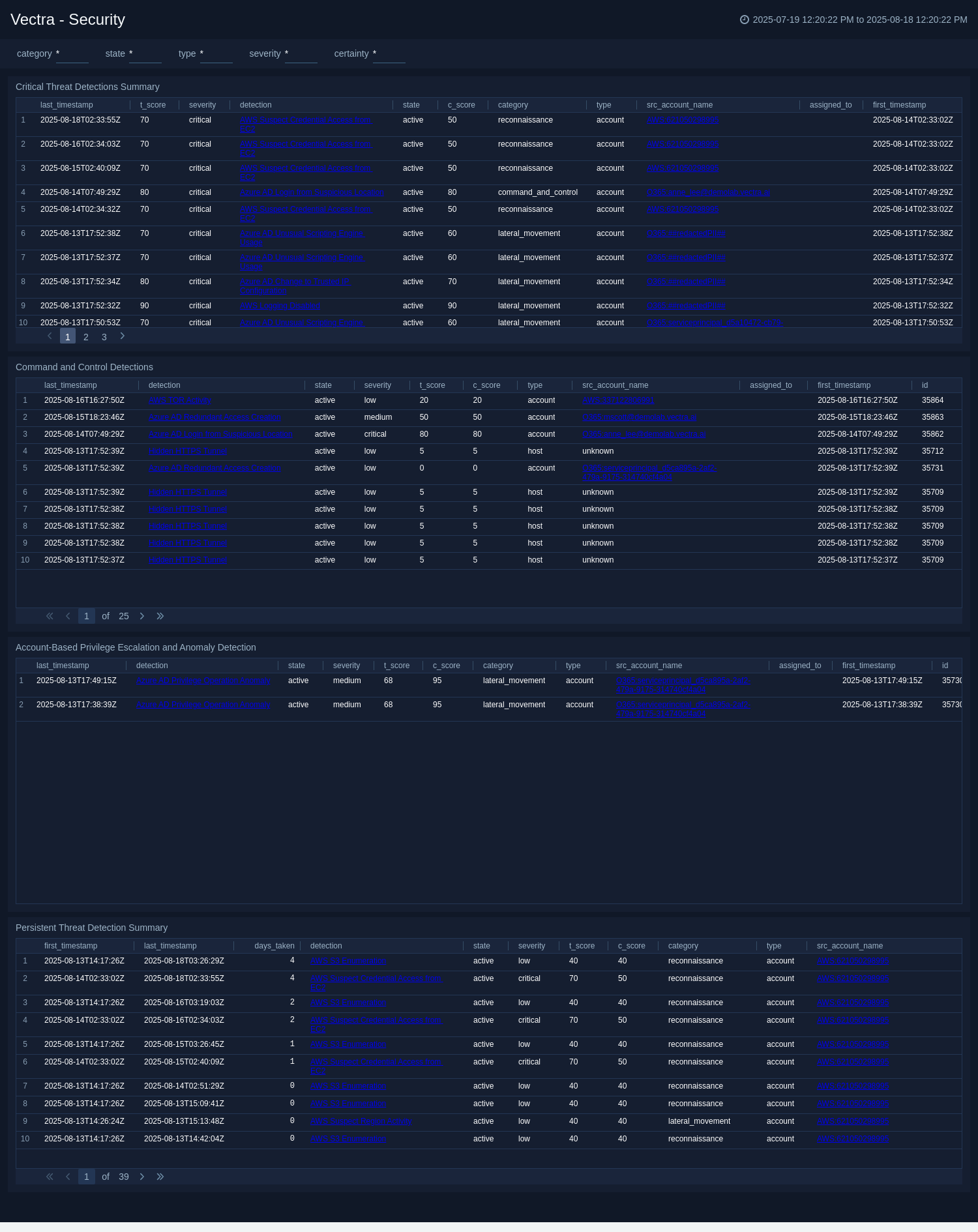 +
+## Create monitors for the Vectra app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+## Create monitors for the Vectra app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+