+ })
+})
Carbon Black Inventory
+Gain insight into endpoint assets and their security status in your environment.
+}) | [Cassandra](https://cassandra.apache.org/) | Apps:
| [Cassandra](https://cassandra.apache.org/) | Apps: }) | [Catchpoint](https://www.catchpoint.com/) | Partner integration: [Catchpoint](https://github.com/catchpoint/Integrations.SumoLogic/blob/main/README.md) |
|
| [Catchpoint](https://www.catchpoint.com/) | Partner integration: [Catchpoint](https://github.com/catchpoint/Integrations.SumoLogic/blob/main/README.md) |
| }) | [Cato Networks](https://www.catonetworks.com/) | App: [Cato Networks](/docs/integrations/saas-cloud/cato-networks/)
| [Cato Networks](https://www.catonetworks.com/) | App: [Cato Networks](/docs/integrations/saas-cloud/cato-networks/) }) | Carbon Black Inventory | App: [Carbon Black Inventory](/docs/integrations/saas-cloud/carbon-black-inventory/)
| Carbon Black Inventory | App: [Carbon Black Inventory](/docs/integrations/saas-cloud/carbon-black-inventory/) }) | [Censys](https://censys.com/) | Automation integrations:
| [Censys](https://censys.com/) | Automation integrations: }) | [Certego](https://www.certego.net/) | Automation integration: [Certego](/docs/platform-services/automation-service/app-central/integrations/certego/) |
|
| [Certego](https://www.certego.net/) | Automation integration: [Certego](/docs/platform-services/automation-service/app-central/integrations/certego/) |
| }) | [ChatGPT Compliance](https://chatgpt.com/) | Collector: [ChatGPT Compliance Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/chatgpt-compliance-source) |
diff --git a/docs/integrations/saas-cloud/carbon-black-inventory.md b/docs/integrations/saas-cloud/carbon-black-inventory.md
new file mode 100644
index 0000000000..12839e95c7
--- /dev/null
+++ b/docs/integrations/saas-cloud/carbon-black-inventory.md
@@ -0,0 +1,137 @@
+---
+id: carbon-black-inventory
+title: Carbon Black Inventory
+sidebar_label: Carbon Black Inventory
+description: The Sumo Logic app for Carbon Black Inventory enables security analysts identify risks and configuration gaps to improve endpoint hygiene, faster response, and stronger overall security.
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+
+
| [ChatGPT Compliance](https://chatgpt.com/) | Collector: [ChatGPT Compliance Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/chatgpt-compliance-source) |
diff --git a/docs/integrations/saas-cloud/carbon-black-inventory.md b/docs/integrations/saas-cloud/carbon-black-inventory.md
new file mode 100644
index 0000000000..12839e95c7
--- /dev/null
+++ b/docs/integrations/saas-cloud/carbon-black-inventory.md
@@ -0,0 +1,137 @@
+---
+id: carbon-black-inventory
+title: Carbon Black Inventory
+sidebar_label: Carbon Black Inventory
+description: The Sumo Logic app for Carbon Black Inventory enables security analysts identify risks and configuration gaps to improve endpoint hygiene, faster response, and stronger overall security.
+---
+
+import useBaseUrl from '@docusaurus/useBaseUrl';
+
+}) +
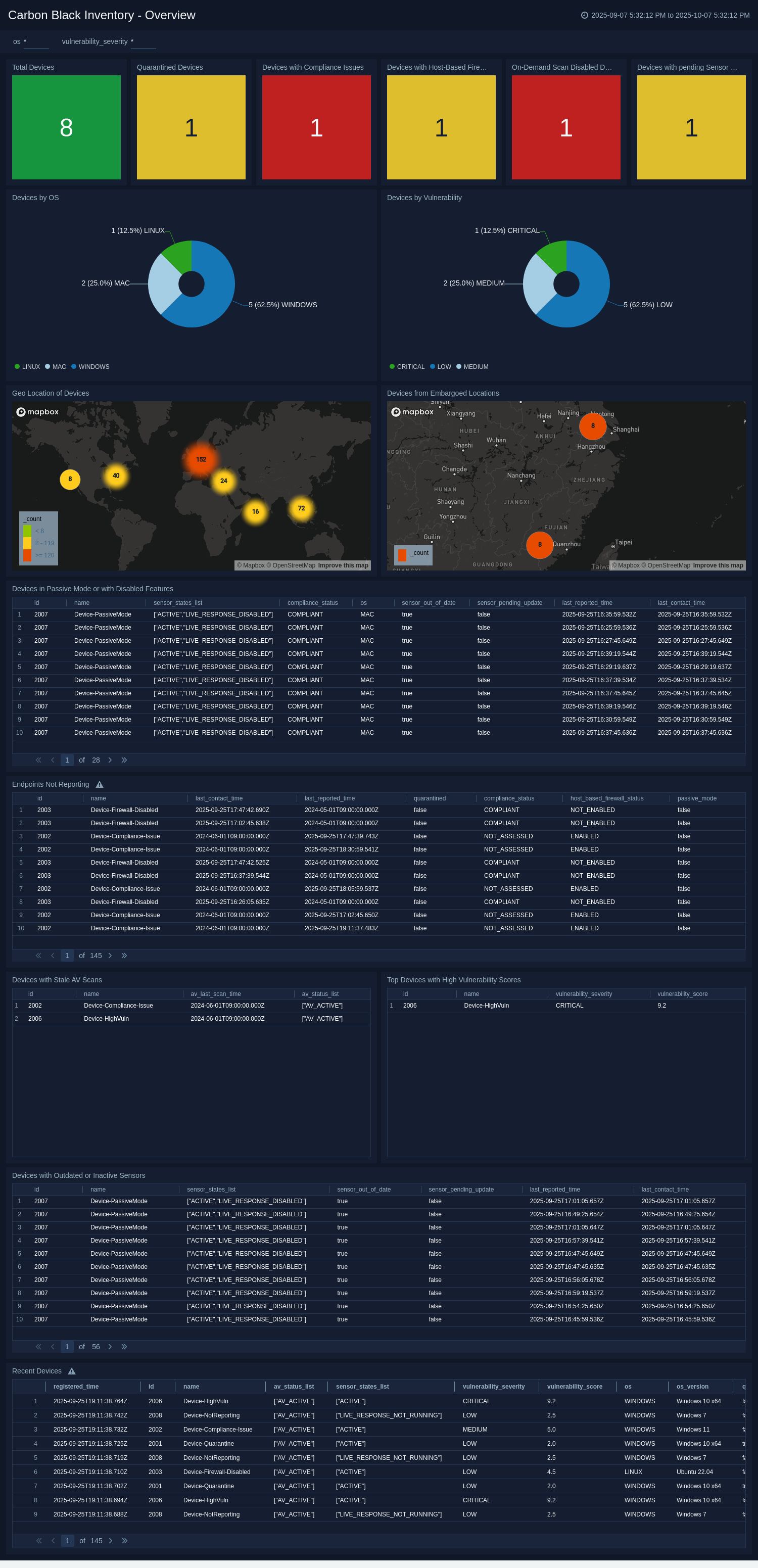
+The Sumo Logic app for Carbon Black Inventory offers comprehensive visibility into endpoint assets and their security posture across your environment. By consolidating key device data, including total device counts, compliance status, antivirus and sensor health, and vulnerability levels, the app enables security teams to quickly identify at-risk endpoints and configuration gaps.
+
+Dedicated panels highlight quarantined devices, non-compliant endpoints, systems with passive or outdated sensors, and devices lacking recent antivirus scans, allowing you to efficiently monitor operational hygiene and security coverage. Visualizations by operating system, vulnerability severity, and geographic location provide valuable context for prioritizing patching and remediation.
+
+By surfacing high-priority issues, such as stale endpoints, disabled firewalls, or devices located in embargoed regions, alongside a complete inventory summary, the Sumo Logic app for Carbon Black Inventory helps you maintain strong endpoint hygiene, reduce risk exposure, and support compliance initiatives. This unified view empowers teams to respond faster, improve device management, and strengthen security across the IT environment.
+
+:::info
+This app includes [built-in monitors](#carbon-black-inventory-alerts). For details on creating custom monitors, refer to [Create monitors for Carbon Black Inventory app](#create-monitors-for-the-carbon-black-inventory-app).
+:::
+
+## Log types
+
+This app uses Sumo Logic’s [Carbon Black Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/carbon-black-inventory-source/) to collect device logs from the Carbon Black Inventory platform.
+
+## Sample log message
+
+
+
+The Sumo Logic app for Carbon Black Inventory offers comprehensive visibility into endpoint assets and their security posture across your environment. By consolidating key device data, including total device counts, compliance status, antivirus and sensor health, and vulnerability levels, the app enables security teams to quickly identify at-risk endpoints and configuration gaps.
+
+Dedicated panels highlight quarantined devices, non-compliant endpoints, systems with passive or outdated sensors, and devices lacking recent antivirus scans, allowing you to efficiently monitor operational hygiene and security coverage. Visualizations by operating system, vulnerability severity, and geographic location provide valuable context for prioritizing patching and remediation.
+
+By surfacing high-priority issues, such as stale endpoints, disabled firewalls, or devices located in embargoed regions, alongside a complete inventory summary, the Sumo Logic app for Carbon Black Inventory helps you maintain strong endpoint hygiene, reduce risk exposure, and support compliance initiatives. This unified view empowers teams to respond faster, improve device management, and strengthen security across the IT environment.
+
+:::info
+This app includes [built-in monitors](#carbon-black-inventory-alerts). For details on creating custom monitors, refer to [Create monitors for Carbon Black Inventory app](#create-monitors-for-the-carbon-black-inventory-app).
+:::
+
+## Log types
+
+This app uses Sumo Logic’s [Carbon Black Inventory Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/carbon-black-inventory-source/) to collect device logs from the Carbon Black Inventory platform.
+
+## Sample log message
+
+ +
+## Create monitors for the Carbon Black Inventory app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+## Create monitors for the Carbon Black Inventory app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+Gain insight into user behavior patterns and resources.
+})
Gain insight into endpoint assets and their security status in your environment.
+})