New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Certificate is invalid on Chrome #3535
Comments
|
You might need to restart your browser; in any case, just make sure Caddy's root certificate is installed into the trust store used by Chrome / Brave. Caddy's auto-installation is a best-effort but still needs some improvement. We use functions based on: https://github.com/FiloSottile/mkcert |
|
@mholt, just encountered the same issue with caddy 2.1.1, Chrome 83.0.4103.116. Chrome has the caddy CA on the trusted list, I checked. To me, it looks like Chrome doesn't like the fact that the certificate from the internal issuer doesn't have the subject commonName set. |
|
Indeed, when I made a small change to csr.Subject.CommonName = "hardcoded.name"and rm -rf ~/.local/share/caddysuddenly the issue went away, and Chrome accepted the certificate, no problem. I would love to create a PR of this, but I'm completely ignorant of the Go language, and can't really figure out where I'd get the name for the CSR. I could give it a shot, if you point me in the right direction. |
|
@mikaelhg Can you post the full output of the certificate viewer in Chrome with the problematic cert? |
diff --git a/modules/caddytls/internalissuer.go b/modules/caddytls/internalissuer.go
index ca43bf8f..1c69bbe2 100644
--- a/modules/caddytls/internalissuer.go
+++ b/modules/caddytls/internalissuer.go
@@ -119,6 +119,8 @@ func (li InternalIssuer) Issue(ctx context.Context, csr *x509.CertificateRequest
lifetime = issuerCert.NotAfter.Sub(time.Now())
}
+ csr.Subject.CommonName = "baddy.caddy.daddy"
+
certChain, err := auth.Sign(csr, provisioner.Options{},
profileDefaultDuration(li.Lifetime),
) |
|
Oh, maybe you meant the exports... I had to reproduce the process to get those, so these aren't exactly identical to the first ones, but they behave identically. Working: Broken: |
|
Should I open a new issue, or will you reopen this one? |
|
Thanks, the full PEM dump was helpful. It appears to be because the SAN extension is not marked as critical, which Chrome requires when there is not a CommonName (subject). |
|
This was a combination of behaviors in both smallstep and Chrome. Upgrading to the latest smallstep release (v0.14.6) seems to fix the problem for me. (/cc @maraino) With the latest update, Key Usage Key Encipherment is gone is gone, and SAN extension has "Critical: Yes" which I believe is the correct behavior. |
|
I can confirm that the current master fixed the issue for me. Thank you. |
|
Building from master seems to fix the issue with chrome and chromium but the subject is still missing in the issued certificate, is this case for you too @mikaelhg ? |
|
@aduzsardi , it is, and Edit: Nevermind, it's just Chrome marking the default 404 as untrusted because the content comes from an internal source. With an actual 404 document Chrome still shows the page as trusted. |
|
@aduzsardi As I said in the other issue, CommonName has been deprecated for 20 years. It is intentional that CommonName is not set in Caddy certificates. Even Chrome has not accepted it for years now. |
|
The subject is not required when (as of somewhat recently) the SAN extension is critical, which is what was fixed upstream. You can think that field should be used out all you want, but there's good reasons it was deprecated 20 years ago. I imagine CAs today only fill it out for backwards compatibility with really old software (that, and a bug in macOS until 10.13) which isn't something Caddy cares about (in fact it's contrary to the goals of this project). |
|
I'm ok with this too even if it will be tagged as "Won't fix/not a bug" , but when looking at the Certificate hierarchy tree view for the certificate it just looks very silly |
|
@aduzsardi The issue was fixed, see above. Just not in the way that you want (for no reason other than "looks silly" -- if that's your gripe, please file an issue with the certificate viewing software instead). |
|
@mholt I just updated to latest Docker tag from 6 hours ago. This is still 2.1.1, so perhaps not? I have imported the root.crt and intermediate.crt into my local OS trust store (where they've been converted to caddy PEM files), as well as used Chrome settings UI for security to import the authority (not sure if intermediate import was required but did that as well). Still fails to be recognized as secure. Firefox accepts it. Providing leaf cert I generate from While I don't know if it's any different with the fix, I also agree it's not great for Firefox or Chrome UI detail cert view, as the leaf cert is literally an invisible/blank field(in Firefox it's indicated via tabs, in Chrome it's a tree view of the cert chain). CommonName might not be required but at least provides a better UX for humans inspecting the certificate chain via browsers UI. |
|
We don't publish beta and RC versions to Docker. You can build the latest from source though, with xcaddy and the golang image as a base. |
|
I am fine using |
|
Is this supposed to be fixed in v2.2.0-rc.3? I just tried this version, and I still experience the same issue in Chromium ( |
|
If you do |
Thank you for putting this in a better argument that i could , just because something is not required per say , doesn't mean it has no value. :) |
|
@aduzsardi Using the CommonName field after it has been deprecated is incorrect software; if it looks weird in the cert viewer, the cert viewer will need to fix that. Please focus these complaints in the proper projects where it can be fixed. |
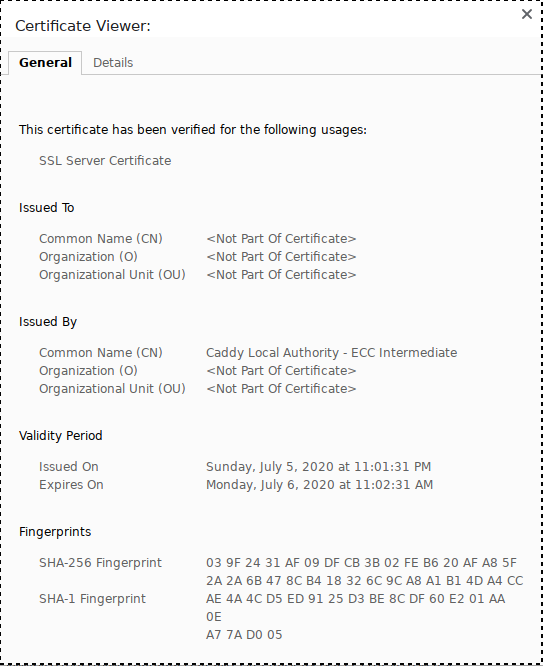



If I start a reverse proxy like this
sudo caddy reverse-proxy --to 127.0.0.1:1234where under :1234 there's a server running, it works perfectly on Firefox when I visit
https://localhost. If I visit the same on chromium-based browsers (Chrome, Brave) I get anNET::ERR_CERT_INVALIDerror.On the command line I get this error:
http: TLS handshake error from [::1]:43216: remote error: tls: unknown certificateCaddy version is
v2.1.0 h1:MC4d65RCVaEKy1iOFjsD51mybOwS8qdEVBi7ESDhUfE=The text was updated successfully, but these errors were encountered: