New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Unable to access iframe contentDocument when webSecurity disabled. #18214
Comments
|
Thanks for reaching out! We require the template to be filled out on all new issues and pull requests. We do this so that we can be certain we have all the information we need to address your submission efficiently. This allows the maintainers to spend more time fixing bugs, implementing enhancements, and reviewing and merging pull requests. Thanks for understanding and meeting us half way 😀 In particular here, things like OS, Electron Version, etc. are critical for anyone to look into this. |
|
updatd it above... thx |
|
Can you confirm this is possible if you launch Chrome itself with |
|
@MarshallOfSound ahah! It did not. And good point about --disable-web-security. I didn't realize this was the exact same thing as electron disabled web security. ... but at least I can try to track down why this isn't working by taking another path. |
|
Oh wow.. I figured it out! It IS chrome + electron specific and is a bug in Electron. We need to add "--disable-site-isolation-trials" cypress-io/cypress#1951 (comment) While this is concerning I think Electron might want to opt out of these 'trials'.... Maybe this trial is turned on for everyone though? It would be really unfortunate for bugs to leak in non-deterministically due to these A/B trials. |
|
Note this works with chromium but I do not have a workaround for electron. |
|
This worked, thx. app.commandLine.appendSwitch('disable-site-isolation-trials') |
|
With Related: #18940 |
|
Thank you for taking the time to report this issue and helping to make Electron better. The version of Electron you reported this on has been superseded by newer releases. If you're still experiencing this issue in Electron 6.x.y or later, please add a comment specifying the version you're testing with and any other new information that a maintainer trying to reproduce the issue should know. I'm setting the Thanks in advance! Your help is appreciated. |
|
Thank you for your issue! We haven't gotten a response to our questions in our comment above. With only the information that is currently in the issue, we don't have enough information to take action. I'm going to close this but don't hesitate to reach out if you have or find the answers we need, we'll be happy to reopen the issue. |


I have read the Contributing Guidelines for this project.
I agree to follow the Code of Conduct that this project adheres to.
I have searched the issue tracker for an issue that matches the one I want to file, without success.
Electron Version:
5.0.1
Operating System:
Ubuntu 19.04
Last Known Working Electron version::
unknown
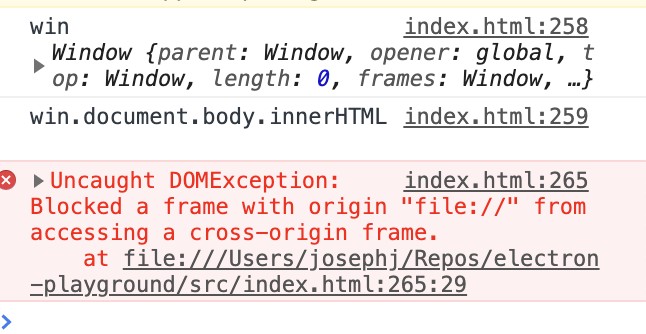
If web security is enabled a script should be able to access the contentDocument of a host iframe even if it's in a different origin.
That doesn't seem to be the case and I think this is a regression a few Electron versions back but I can verify.
I verified this by creating a simple test which sets webSecurity: false (and I verified this part)....
I then load two URLs. One with an iframe in the same origin and another in a different origin.
With the same origin I can see the iframe.contentDocument just fine.
However, with a different origin it's null.
I just wrote a simple script to verify this.
The text was updated successfully, but these errors were encountered: