diff --git a/docs/reference/modules/terraform-aws-vpc/network-acl-inbound/network-acl-inbound.md b/docs/reference/modules/terraform-aws-vpc/network-acl-inbound/network-acl-inbound.md
index 4cb2d6bc81..599572a62e 100644
--- a/docs/reference/modules/terraform-aws-vpc/network-acl-inbound/network-acl-inbound.md
+++ b/docs/reference/modules/terraform-aws-vpc/network-acl-inbound/network-acl-inbound.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# Network ACL Inbound Terraform Module
-View Source
+View Source
Release Notes
@@ -24,7 +24,7 @@ with because they are stateless, which means that opening an inbound port is oft
which your services use to respond. This can be very easy to forget, so this module adds not only the inbound ports to
an ACL, but also the ephemeral outbound ports for return traffic.
-See the [network-acl-outbound](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/network-acl-outbound) module for the analogous version of this module, but for opening
+See the [network-acl-outbound](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/network-acl-outbound) module for the analogous version of this module, but for opening
outbound ports.
## What's a Network ACL?
@@ -47,7 +47,7 @@ EC2 instance), a network ACL controls what inbound and outbound traffic is allow
module "network_acl_inbound" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-inbound?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-inbound?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -134,7 +134,7 @@ module "network_acl_inbound" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-inbound?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-inbound?ref=v0.26.2"
}
inputs = {
@@ -221,11 +221,11 @@ inputs = {
diff --git a/docs/reference/modules/terraform-aws-vpc/network-acl-outbound/network-acl-outbound.md b/docs/reference/modules/terraform-aws-vpc/network-acl-outbound/network-acl-outbound.md
index c0035fced7..9958c1e736 100644
--- a/docs/reference/modules/terraform-aws-vpc/network-acl-outbound/network-acl-outbound.md
+++ b/docs/reference/modules/terraform-aws-vpc/network-acl-outbound/network-acl-outbound.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# Network ACL Outbound Terraform Module
-View Source
+View Source
Release Notes
@@ -24,7 +24,7 @@ because they are stateless, which means that opening an outbound port is often n
which the remote services can use to respond. This can be very easy to forget, so this module adds not only the
outbound to an ACL, but also the ephemeral inbound ports for return traffic.
-See the [network-acl-inbound](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/network-acl-inbound) module for the analogous version of this module, but for opening
+See the [network-acl-inbound](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/network-acl-inbound) module for the analogous version of this module, but for opening
inbound ports.
## What's a Network ACL?
@@ -47,7 +47,7 @@ EC2 instance), a network ACL controls what inbound and outbound traffic is allow
module "network_acl_outbound" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-outbound?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-outbound?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -134,7 +134,7 @@ module "network_acl_outbound" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-outbound?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/network-acl-outbound?ref=v0.26.2"
}
inputs = {
@@ -221,11 +221,11 @@ inputs = {
diff --git a/docs/reference/modules/terraform-aws-vpc/port-range-calculator/port-range-calculator.md b/docs/reference/modules/terraform-aws-vpc/port-range-calculator/port-range-calculator.md
index b0e0935ab3..0060ada595 100644
--- a/docs/reference/modules/terraform-aws-vpc/port-range-calculator/port-range-calculator.md
+++ b/docs/reference/modules/terraform-aws-vpc/port-range-calculator/port-range-calculator.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# Port Calculator Module
-View Source
+View Source
Release Notes
@@ -50,7 +50,7 @@ just those ports:
module "port_range_calculator" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/port-range-calculator?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/port-range-calculator?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -84,7 +84,7 @@ module "port_range_calculator" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/port-range-calculator?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/port-range-calculator?ref=v0.26.2"
}
inputs = {
@@ -178,11 +178,11 @@ Map of port ranges to the ranges to allow. This is provided as a convenience out
diff --git a/docs/reference/modules/terraform-aws-vpc/transit-gateway-attachment/transit-gateway-attachment.md b/docs/reference/modules/terraform-aws-vpc/transit-gateway-attachment/transit-gateway-attachment.md
new file mode 100644
index 0000000000..ea043f0606
--- /dev/null
+++ b/docs/reference/modules/terraform-aws-vpc/transit-gateway-attachment/transit-gateway-attachment.md
@@ -0,0 +1,339 @@
+---
+title: "Transit Gateway Attachment Terraform Module"
+hide_title: true
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
+import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
+import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
+
+
+
+# Transit Gateway Attachment Terraform Module
+
+View Source
+
+Release Notes
+
+This module creates a transit gateway attachment resource. A transit gateway attachment, attaches the transit gateway to a VPC. This module can be used to attach a transit gateway to multiple VPCs. Attaching a transit gateway to one or more VPCs creates a HUB and spoke routing topology, allowing traffic from one VPC to reach other VPCs or from a VPC to reach on-premises networks.
+
+The module accepts a map of VPCs for attachment to the transit gateway. See the examples below for the structure of the map.
+
+See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+
+## What is a Transit Gateway Attachment?
+
+A transit gateway attachment is a way to connect a transit gateway (virtual router) to a VPC. You can think of a VPC attachment just like a cat5e or cat6 network cable. By attaching the transit gateway, you're connecting the cable between the virtual router and a VPC. By attaching the transit gateway and then either configuring a route or enabling route propagation, you can route traffic between VPCs.
+
+## Usage
+
+For usage examples, check out the [examples folder](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/examples/transit-gateway-attachment/).
+
+
+
+## Requirements
+
+| Name | Version |
+|------|---------|
+| [terraform](#requirement_terraform) | >= 1.0.0 |
+| [aws](#requirement_aws) | >= 4.5.0 |
+
+## Providers
+
+| Name | Version |
+|------|---------|
+| [aws](#provider_aws) | >= 4.5.0 |
+
+## Modules
+
+No modules.
+
+## Resources
+
+| Name | Type |
+|------|------|
+| [aws_ec2\_transit_gateway_vpc_attachment.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/ec2\_transit_gateway_vpc_attachment) | resource |
+
+## Inputs
+
+| Name | Description | Type | Default | Required |
+|------|-------------|------|---------|:--------:|
+| [custom_tags](#input_custom_tags) | A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable. | `map(string)` | `{}` | no |
+| [enable_appliance_mode_support](#input_enable_appliance_mode_support) | Whether Appliance Mode support is enabled. If enabled, a traffic flow between a source and destination uses the same Availability Zone for the VPC attachment for the lifetime of that flow. The default is false. | `bool` | `false` | no |
+| [enable_dns_support](#input_enable_dns_support) | Whether DNS resolution is enabled for this VPC attachment. The default is false. | `bool` | `false` | no |
+| [enable_ipv6\_support](#input_enable_ipv6\_support) | Whether IPv6 support is enabled. If enabled, a private IPv6 address from the Amazon pool of IPv6 addresses is assigned to the Elastic Network Interface (ENI) for a VPC attachment. The default is false. | `bool` | `false` | no |
+| [enable_transit_gateway_default_route_table_association](#input_enable_transit_gateway_default_route_table_association) | Whether the VPC attachment should be associated with the Transit Gateway association default route table. The default is true. | `bool` | `true` | no |
+| [enable_transit_gateway_default_route_table_propagation](#input_enable_transit_gateway_default_route_table_propagation) | Whether the VPC attachment should propagate routes with the Transit Gateway propagation default route table. The default is true. | `bool` | `true` | no |
+| [transit_gateway_id](#input_transit_gateway_id) | EC2 Transit Gateway identifier | `string` | n/a | yes |
+| [vpcs](#input_vpcs) | A map of vpcs with their name and the subnet ids that the transit gateway will attach to. The subnet IDs configured here are the attachment point for the transit gateway. I.E. The transit gateway will have an IP on these subnets. | `map(object({
vpc_id = string
vpc_name = string
subnet_ids = list(string)
}))` | n/a | yes |
+
+## Outputs
+
+| Name | Description |
+|------|-------------|
+| [id](#output_id) | EC2 Transit Gateway Attachment identifier. |
+
+
+
+## Sample Usage
+
+
+
+
+```hcl title="main.tf"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-ATTACHMENT MODULE
+# ------------------------------------------------------------------------------------------------------
+
+module "transit_gateway_attachment" {
+
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-attachment?ref=v0.26.2"
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # EC2 Transit Gateway identifier
+ transit_gateway_id =
+
+ # A map of vpcs with their name and the subnet ids that the transit gateway
+ # will attach to. The subnet IDs configured here are the attachment point for
+ # the transit gateway. I.E. The transit gateway will have an IP on these
+ # subnets.
+ vpcs =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # Whether Appliance Mode support is enabled. If enabled, a traffic flow
+ # between a source and destination uses the same Availability Zone for the VPC
+ # attachment for the lifetime of that flow. The default is false.
+ enable_appliance_mode_support = false
+
+ # Whether DNS resolution is enabled for this VPC attachment. The default is
+ # false.
+ enable_dns_support = false
+
+ # Whether IPv6 support is enabled. If enabled, a private IPv6 address from the
+ # Amazon pool of IPv6 addresses is assigned to the Elastic Network Interface
+ # (ENI) for a VPC attachment. The default is false.
+ enable_ipv6_support = false
+
+ # Whether the VPC attachment should be associated with the Transit Gateway
+ # association default route table. The default is true.
+ enable_transit_gateway_default_route_table_association = true
+
+ # Whether the VPC attachment should propagate routes with the Transit Gateway
+ # propagation default route table. The default is true.
+ enable_transit_gateway_default_route_table_propagation = true
+
+}
+
+
+```
+
+
+
+
+```hcl title="terragrunt.hcl"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-ATTACHMENT MODULE
+# ------------------------------------------------------------------------------------------------------
+
+terraform {
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-attachment?ref=v0.26.2"
+}
+
+inputs = {
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # EC2 Transit Gateway identifier
+ transit_gateway_id =
+
+ # A map of vpcs with their name and the subnet ids that the transit gateway
+ # will attach to. The subnet IDs configured here are the attachment point for
+ # the transit gateway. I.E. The transit gateway will have an IP on these
+ # subnets.
+ vpcs =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # Whether Appliance Mode support is enabled. If enabled, a traffic flow
+ # between a source and destination uses the same Availability Zone for the VPC
+ # attachment for the lifetime of that flow. The default is false.
+ enable_appliance_mode_support = false
+
+ # Whether DNS resolution is enabled for this VPC attachment. The default is
+ # false.
+ enable_dns_support = false
+
+ # Whether IPv6 support is enabled. If enabled, a private IPv6 address from the
+ # Amazon pool of IPv6 addresses is assigned to the Elastic Network Interface
+ # (ENI) for a VPC attachment. The default is false.
+ enable_ipv6_support = false
+
+ # Whether the VPC attachment should be associated with the Transit Gateway
+ # association default route table. The default is true.
+ enable_transit_gateway_default_route_table_association = true
+
+ # Whether the VPC attachment should propagate routes with the Transit Gateway
+ # propagation default route table. The default is true.
+ enable_transit_gateway_default_route_table_propagation = true
+
+}
+
+
+```
+
+
+
+
+
+
+
+## Reference
+
+
+
+
+### Required
+
+
+
+
+EC2 Transit Gateway identifier
+
+
+
+
+
+
+
+A map of vpcs with their name and the subnet ids that the transit gateway will attach to. The subnet IDs configured here are the attachment point for the transit gateway. I.E. The transit gateway will have an IP on these subnets.
+
+
+
+
+```hcl
+map(object({
+ vpc_id = string
+ vpc_name = string
+ subnet_ids = list(string)
+ }))
+```
+
+
+
+
+### Optional
+
+
+
+
+A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable.
+
+
+
+
+
+
+
+
+Whether Appliance Mode support is enabled. If enabled, a traffic flow between a source and destination uses the same Availability Zone for the VPC attachment for the lifetime of that flow. The default is false.
+
+
+
+
+
+
+
+
+Whether DNS resolution is enabled for this VPC attachment. The default is false.
+
+
+
+
+
+
+
+
+Whether IPv6 support is enabled. If enabled, a private IPv6 address from the Amazon pool of IPv6 addresses is assigned to the Elastic Network Interface (ENI) for a VPC attachment. The default is false.
+
+
+
+
+
+
+
+
+Whether the VPC attachment should be associated with the Transit Gateway association default route table. The default is true.
+
+
+
+
+
+
+
+
+Whether the VPC attachment should propagate routes with the Transit Gateway propagation default route table. The default is true.
+
+
+
+
+
+
+
+
+
+
+
+EC2 Transit Gateway Attachment identifier.
+
+
+
+
+
+
+
+
+
diff --git a/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment-accepter/transit-gateway-peering-attachment-accepter.md b/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment-accepter/transit-gateway-peering-attachment-accepter.md
new file mode 100644
index 0000000000..2b4a4d705a
--- /dev/null
+++ b/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment-accepter/transit-gateway-peering-attachment-accepter.md
@@ -0,0 +1,269 @@
+---
+title: "Transit Gateway Peering Attachment Accepter Accepter Terraform Module"
+hide_title: true
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
+import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
+import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
+
+
+
+# Transit Gateway Peering Attachment Accepter Accepter Terraform Module
+
+View Source
+
+Release Notes
+
+This Terraform Module creates Transit Gateway peering resources for the `accepter` side of the connection. This allows for connectivity between multiple regions or multiple AWS accounts. Transit Gateway peering is a one-to-one relationship between two transit gateways. If you need to peer multiple transit gateways, you will need to create multiple transit gateway peering attachments.
+
+See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+
+## What is a Transit Gateway Peering Attachment Accepter?
+
+A transit gateway peering attachment accepter is a way to connect two transit gateways to each other. Much like the VPC attachment, this can be thought of as a network cable. By attaching them, you 'plug' the two transit gateways together. This allows you to route traffic between the two transit gateways. Unlike VPC attachments, peering attachments have two components to the attachment a `requester` and an `accepter`. This is important because each attachment must be accepted prior to the attachment being completed. This is a security measure to ensure a malicious attachment from a random account does not gain network access to your environment. The `accepter` is the side of the peering attachment that accepts the request from the `requester`.
+
+For usage examples, check out the [examples folder](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/examples/transit-gateway-peering-attachment).
+
+
+
+## Requirements
+
+| Name | Version |
+|------|---------|
+| [terraform](#requirement_terraform) | >= 1.0.0 |
+| [aws](#requirement_aws) | >= 4.5.0 |
+
+## Providers
+
+| Name | Version |
+|------|---------|
+| [aws](#provider_aws) | >= 4.5.0 |
+
+## Modules
+
+No modules.
+
+## Resources
+
+| Name | Type |
+|------|------|
+| [aws_ec2\_transit_gateway_peering_attachment_accepter.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/ec2\_transit_gateway_peering_attachment_accepter) | resource |
+| [aws_ec2\_transit_gateway_peering_attachment.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/ec2\_transit_gateway_peering_attachment) | data source |
+
+## Inputs
+
+| Name | Description | Type | Default | Required |
+|------|-------------|------|---------|:--------:|
+| [custom_tags](#input_custom_tags) | A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable. | `map(string)` | `{}` | no |
+| [name](#input_name) | The name of the transit gateway peering attachment. If not set, a default name will be used. | `string` | `null` | no |
+| [transit_gateway_attachment_id](#input_transit_gateway_attachment_id) | The transit gateway peering attachment ID to accept. If none is set, the module will attempt to look this up. | `string` | `null` | no |
+| [transit_gateway_id](#input_transit_gateway_id) | Transit gateway ID of which to accept the peering attachments from. This will be the accepter side transit gateway (your side) of the peering attachment | `string` | n/a | yes |
+
+## Outputs
+
+| Name | Description |
+|------|-------------|
+| [ids](#output_ids) | The transit gateway peering attachment identifier. |
+| [peer_account_ids](#output_peer_account_ids) | The identifers for the peer account. |
+| [peer_transit_gateway_ids](#output_peer_transit_gateway_ids) | The identifier of the peer transit gateway. |
+| [transit_gateway_ids](#output_transit_gateway_ids) | The identifer of the transit gateway for the accepter resources. |
+
+
+
+## Sample Usage
+
+
+
+
+```hcl title="main.tf"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-PEERING-ATTACHMENT-ACCEPTER MODULE
+# ------------------------------------------------------------------------------------------------------
+
+module "transit_gateway_peering_attachment_accepter" {
+
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-peering-attachment-accepter?ref=v0.26.2"
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Transit gateway ID of which to accept the peering attachments from. This
+ # will be the accepter side transit gateway (your side) of the peering
+ # attachment
+ transit_gateway_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # The name of the transit gateway peering attachment. If not set, a default
+ # name will be used.
+ name = null
+
+ # The transit gateway peering attachment ID to accept. If none is set, the
+ # module will attempt to look this up.
+ transit_gateway_attachment_id = null
+
+}
+
+
+```
+
+
+
+
+```hcl title="terragrunt.hcl"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-PEERING-ATTACHMENT-ACCEPTER MODULE
+# ------------------------------------------------------------------------------------------------------
+
+terraform {
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-peering-attachment-accepter?ref=v0.26.2"
+}
+
+inputs = {
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Transit gateway ID of which to accept the peering attachments from. This
+ # will be the accepter side transit gateway (your side) of the peering
+ # attachment
+ transit_gateway_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # The name of the transit gateway peering attachment. If not set, a default
+ # name will be used.
+ name = null
+
+ # The transit gateway peering attachment ID to accept. If none is set, the
+ # module will attempt to look this up.
+ transit_gateway_attachment_id = null
+
+}
+
+
+```
+
+
+
+
+
+
+
+## Reference
+
+
+
+
+### Required
+
+
+
+
+Transit gateway ID of which to accept the peering attachments from. This will be the accepter side transit gateway (your side) of the peering attachment
+
+
+
+
+### Optional
+
+
+
+
+A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable.
+
+
+
+
+
+
+
+
+The name of the transit gateway peering attachment. If not set, a default name will be used.
+
+
+
+
+
+
+
+
+The transit gateway peering attachment ID to accept. If none is set, the module will attempt to look this up.
+
+
+
+
+
+
+
+
+
+
+
+The transit gateway peering attachment identifier.
+
+
+
+
+
+
+
+The identifers for the peer account.
+
+
+
+
+
+
+
+The identifier of the peer transit gateway.
+
+
+
+
+
+
+
+The identifer of the transit gateway for the accepter resources.
+
+
+
+
+
+
+
+
+
diff --git a/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment/transit-gateway-peering-attachment.md b/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment/transit-gateway-peering-attachment.md
new file mode 100644
index 0000000000..bb8a36c0da
--- /dev/null
+++ b/docs/reference/modules/terraform-aws-vpc/transit-gateway-peering-attachment/transit-gateway-peering-attachment.md
@@ -0,0 +1,271 @@
+---
+title: "Transit Gateway Peering Attachment Module"
+hide_title: true
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
+import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
+import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
+
+
+
+# Transit Gateway Peering Attachment Module
+
+View Source
+
+Release Notes
+
+This Terraform Module creates transit gateway peering resources for the `requester` side of the connection to another transit gateway. The transit gateway can be in this account or in another account. Transit gateway peering is a one-to-one relationship between two transit gateways. If you need to peer multiple transit gateways, you will need to create multiple transit gateway peering attachments.
+
+See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+
+## What is a Transit Gateway Peering Attachment?
+
+A transit gateway peering attachment is a way to connect two transit gateways to each other. Much like the VPC attachment, this can be thought of as a network cable. By attaching them, you 'plug' the two transit gateways together. This allows you to route traffic between the two transit gateways. Unlike VPC attachments, peering attachments have two components to the attachment a `requester` and an `accepter`. This is important because each attachment must be accepted prior to the attachment being completed. This is a security measure to ensure a malicious attachment from a random account does not gain network access to your environment.
+
+## Usage
+
+For usage examples, check out the [examples folder](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/examples/transit-gateway-peering-attachment/).
+
+
+
+## Requirements
+
+| Name | Version |
+|------|---------|
+| [terraform](#requirement_terraform) | >= 1.0.0 |
+| [aws](#requirement_aws) | >= 4.5.0 |
+
+## Providers
+
+| Name | Version |
+|------|---------|
+| [aws](#provider_aws) | >= 4.5.0 |
+
+## Modules
+
+No modules.
+
+## Resources
+
+| Name | Type |
+|------|------|
+| [aws_ec2\_transit_gateway_peering_attachment.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/ec2\_transit_gateway_peering_attachment) | resource |
+
+## Inputs
+
+| Name | Description | Type | Default | Required |
+|------|-------------|------|---------|:--------:|
+| [custom_tags](#input_custom_tags) | A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable. | `map(string)` | `{}` | no |
+| [name](#input_name) | The name of the transit gateway peering attachment. If not set, a default name will be used. | `string` | `null` | no |
+| [peer_account_id](#input_peer_account_id) | The AWS account ID of the peer transit gateway. This is only required when the peer transit gateway is owned by a different AWS account. Defaults to the current account ID. | `string` | `null` | no |
+| [peer_region](#input_peer_region) | The AWS region where the peer transit gateway resides. | `string` | n/a | yes |
+| [peer_transit_gateway_id](#input_peer_transit_gateway_id) | The ID of the peer transit gateway. | `string` | n/a | yes |
+| [transit_gateway_id](#input_transit_gateway_id) | The ID of the transit gateway. This should be your transit gateway. | `string` | n/a | yes |
+
+## Outputs
+
+| Name | Description |
+|------|-------------|
+| [id](#output_id) | Transit Gateway Peering Attachment identifier |
+
+
+
+## Sample Usage
+
+
+
+
+```hcl title="main.tf"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-PEERING-ATTACHMENT MODULE
+# ------------------------------------------------------------------------------------------------------
+
+module "transit_gateway_peering_attachment" {
+
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-peering-attachment?ref=v0.26.2"
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # The AWS region where the peer transit gateway resides.
+ peer_region =
+
+ # The ID of the peer transit gateway.
+ peer_transit_gateway_id =
+
+ # The ID of the transit gateway. This should be your transit gateway.
+ transit_gateway_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # The name of the transit gateway peering attachment. If not set, a default
+ # name will be used.
+ name = null
+
+ # The AWS account ID of the peer transit gateway. This is only required when
+ # the peer transit gateway is owned by a different AWS account. Defaults to
+ # the current account ID.
+ peer_account_id = null
+
+}
+
+
+```
+
+
+
+
+```hcl title="terragrunt.hcl"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-PEERING-ATTACHMENT MODULE
+# ------------------------------------------------------------------------------------------------------
+
+terraform {
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-peering-attachment?ref=v0.26.2"
+}
+
+inputs = {
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # The AWS region where the peer transit gateway resides.
+ peer_region =
+
+ # The ID of the peer transit gateway.
+ peer_transit_gateway_id =
+
+ # The ID of the transit gateway. This should be your transit gateway.
+ transit_gateway_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A map of tags to apply to all resources when applicable. The key is the tag
+ # name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # The name of the transit gateway peering attachment. If not set, a default
+ # name will be used.
+ name = null
+
+ # The AWS account ID of the peer transit gateway. This is only required when
+ # the peer transit gateway is owned by a different AWS account. Defaults to
+ # the current account ID.
+ peer_account_id = null
+
+}
+
+
+```
+
+
+
+
+
+
+
+## Reference
+
+
+
+
+### Required
+
+
+
+
+The AWS region where the peer transit gateway resides.
+
+
+
+
+
+
+
+The ID of the peer transit gateway.
+
+
+
+
+
+
+
+The ID of the transit gateway. This should be your transit gateway.
+
+
+
+
+### Optional
+
+
+
+
+A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable.
+
+
+
+
+
+
+
+
+The name of the transit gateway peering attachment. If not set, a default name will be used.
+
+
+
+
+
+
+
+
+The AWS account ID of the peer transit gateway. This is only required when the peer transit gateway is owned by a different AWS account. Defaults to the current account ID.
+
+
+
+
+
+
+
+
+
+
+
+Transit Gateway Peering Attachment identifier
+
+
+
+
+
+
+
+
+
diff --git a/docs/reference/modules/terraform-aws-vpc/transit-gateway-route/transit-gateway-route.md b/docs/reference/modules/terraform-aws-vpc/transit-gateway-route/transit-gateway-route.md
new file mode 100644
index 0000000000..2a54edcb7b
--- /dev/null
+++ b/docs/reference/modules/terraform-aws-vpc/transit-gateway-route/transit-gateway-route.md
@@ -0,0 +1,234 @@
+---
+title: "Transit Gateway Route Module"
+hide_title: true
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
+import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
+import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
+
+
+
+# Transit Gateway Route Module
+
+View Source
+
+Release Notes
+
+This module creates a route for each CIDR block in a list `cidr_blocks` to a transit gateway route table. The route can be directed to any attachment within the transit gateway or can be configured as a blackhole route. A blackhole route is useful to drop traffic to a given CIDR block, or can be utilized to flush downstream route tables of ephemeral routes.
+
+See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+
+## What is a Transit Gateway Route?
+
+A transit gateway route is a way to route traffic between VPCs, peers, VPNs, and other transit gateway attachments. You can think of a transit gateway route just like a route on a router. By creating a route, you're telling the transit gateway how to route traffic to a given CIDR block. By creating a route and then attaching the transit gateway to a VPC, you can route traffic between VPCs. Where possible, we recommend utilizing dynamic routing either by way of propagation or BGP. This simplifies the management of routes and ensures that routes are automatically updated when attachments are added or removed.
+
+## Usage
+
+For usage examples, check out the [examples folder](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/examples/transit-gateway-route/).
+
+
+
+## Requirements
+
+| Name | Version |
+|------|---------|
+| [terraform](#requirement_terraform) | >= 1.0.0 |
+| [aws](#requirement_aws) | >= 4.5.0 |
+
+## Providers
+
+| Name | Version |
+|------|---------|
+| [aws](#provider_aws) | >= 4.5.0 |
+
+## Modules
+
+No modules.
+
+## Resources
+
+| Name | Type |
+|------|------|
+| [aws_ec2\_transit_gateway_route.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/ec2\_transit_gateway_route) | resource |
+
+## Inputs
+
+| Name | Description | Type | Default | Required |
+|------|-------------|------|---------|:--------:|
+| [cidr_blocks](#input_cidr_blocks) | A list of IPv4 or IPv6 CIDR blocks used for destination matches. Routing decisions are based on the most specific match. | `list(string)` | n/a | yes |
+| [enable_blackhole](#input_enable_blackhole) | Indicates whether to drop traffic that matches this route (blackhole). Cannot use with 'transit_gateway_attachment_id' Defaults to false. | `bool` | `false` | no |
+| [transit_gateway_attachment_id](#input_transit_gateway_attachment_id) | Identifier of Transit Gateway Attachment (required for propagation). Cannot use with 'enable_blackhole'. Default is null. | `string` | `null` | no |
+| [transit_gateway_route_table_id](#input_transit_gateway_route_table_id) | Identifier of Transit Gateway Route Table | `string` | n/a | yes |
+
+## Outputs
+
+| Name | Description |
+|------|-------------|
+| [id](#output_id) | Map of ids of the transit gateway routes. |
+
+
+
+## Sample Usage
+
+
+
+
+```hcl title="main.tf"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-ROUTE MODULE
+# ------------------------------------------------------------------------------------------------------
+
+module "transit_gateway_route" {
+
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-route?ref=v0.26.2"
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A list of IPv4 or IPv6 CIDR blocks used for destination matches. Routing
+ # decisions are based on the most specific match.
+ cidr_blocks =
+
+ # Identifier of Transit Gateway Route Table
+ transit_gateway_route_table_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Indicates whether to drop traffic that matches this route (blackhole).
+ # Cannot use with 'transit_gateway_attachment_id' Defaults to false.
+ enable_blackhole = false
+
+ # Identifier of Transit Gateway Attachment (required for propagation). Cannot
+ # use with 'enable_blackhole'. Default is null.
+ transit_gateway_attachment_id = null
+
+}
+
+
+```
+
+
+
+
+```hcl title="terragrunt.hcl"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY-ROUTE MODULE
+# ------------------------------------------------------------------------------------------------------
+
+terraform {
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway-route?ref=v0.26.2"
+}
+
+inputs = {
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # A list of IPv4 or IPv6 CIDR blocks used for destination matches. Routing
+ # decisions are based on the most specific match.
+ cidr_blocks =
+
+ # Identifier of Transit Gateway Route Table
+ transit_gateway_route_table_id =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Indicates whether to drop traffic that matches this route (blackhole).
+ # Cannot use with 'transit_gateway_attachment_id' Defaults to false.
+ enable_blackhole = false
+
+ # Identifier of Transit Gateway Attachment (required for propagation). Cannot
+ # use with 'enable_blackhole'. Default is null.
+ transit_gateway_attachment_id = null
+
+}
+
+
+```
+
+
+
+
+
+
+
+## Reference
+
+
+
+
+### Required
+
+
+
+
+A list of IPv4 or IPv6 CIDR blocks used for destination matches. Routing decisions are based on the most specific match.
+
+
+
+
+
+
+
+Identifier of Transit Gateway Route Table
+
+
+
+
+### Optional
+
+
+
+
+Indicates whether to drop traffic that matches this route (blackhole). Cannot use with 'transit_gateway_attachment_id' Defaults to false.
+
+
+
+
+
+
+
+
+Identifier of Transit Gateway Attachment (required for propagation). Cannot use with 'enable_blackhole'. Default is null.
+
+
+
+
+
+
+
+
+
+
+
+Map of ids of the transit gateway routes.
+
+
+
+
+
+
+
+
+
diff --git a/docs/reference/modules/terraform-aws-vpc/transit-gateway/transit-gateway.md b/docs/reference/modules/terraform-aws-vpc/transit-gateway/transit-gateway.md
new file mode 100644
index 0000000000..bdd0a1317a
--- /dev/null
+++ b/docs/reference/modules/terraform-aws-vpc/transit-gateway/transit-gateway.md
@@ -0,0 +1,412 @@
+---
+title: "Transit Gateway Terraform Module"
+hide_title: true
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
+import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
+import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
+
+
+
+# Transit Gateway Terraform Module
+
+View Source
+
+Release Notes
+
+This Terraform module creates a transit gateway resource. A transit gateway is an effective method of connecting multiple VPCs, Direct Connects, VPNs, and other networks. Transit gateways are also a good way to connect VPCs to shared services, such as NAT gateways, firewalls, and other security appliances. By using a transit gateway, the number of connections to and from VPCs can be reduced, which reduces the number of routes that need to be managed.
+
+See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+
+## Usage
+
+For usage examples, check out the [examples folder](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/examples/transit-gateway/).
+
+## What's a Transit Gateway?
+
+A [Transit Gateway](https://aws.amazon.com/transit-gateway/) acts as a **Regional** virtual router for traffic flowing between your Virtual Private Clouds (VPCs) and on-premises networks. Transit Gateway simplifies how customers interconnect their networks to scale their AWS workloads. Transit Gateway reduces the number of connections needed to connect many VPCs, AWS accounts, and on-premises networks. Transit Gateway can also be used to isolate workloads by attaching VPCs and on-premises networks to different route tables which can send traffic to security appliances, such as virtual firewalls.
+
+## Transit Gateway vs VPC peering
+
+Transit Gateway solves the complexity involved with creating and managing multiple VPC peering connections at scale. Transit Gateway's should be utilized whenever connectivity is required with more than two VPCs. Transit Gateway's allow for far more flexibility in future networking decisions and are much easier to manage.
+
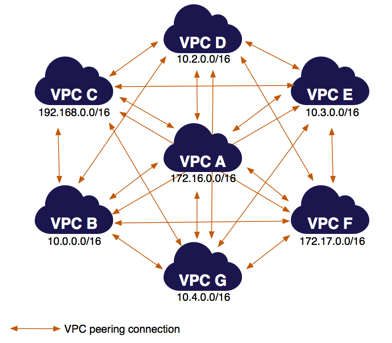
+### VPC Peering
+
+
+
+Credits [many-vpcs-full-access](https://docs.aws.amazon.com/vpc/latest/peering/peering-configurations-full-access.html#many-vpcs-full-access)
+
+### Transit Gateway
+
+A network without AWS Transit Gateway will often look like
+
+
+However, with AWS Transit Gateway it will be more like
+
+
+
+Credits [Transit Gateway](https://aws.amazon.com/transit-gateway)
+
+## How To
+
+What follows are the steps required to configure Transit Gateway resources within your environment(s).
+
+### Create a Network Between Same Region/Same Account
+
+* Create the Transit Gateway
+* Attach your VPCs to your Transit Gateway
+* Add routes between the Transit Gateway and your VPCs
+
+### Create a Network Between Different Regions or Different Accounts
+
+* Create the Transit Gateway in the first region/account
+* Create the Transit Gateway in the second region/account
+* Create a Transit Gateway Peering Connection between the two Transit Gateways
+ * The peering option can be implemented using this module along with [transit-gateway-peering-attachment](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/transit-gateway-peering-attachment/) & [transit-gateway-peering-attachment-accepter](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/transit-gateway-peering-attachment-accepter/) modules. See [VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) for more information on the core networking components and topologies.
+* Attach your VPCs to your Transit Gateway
+* Add routes between the Transit Gateways and your VPCs
+
+
+
+## Requirements
+
+| Name | Version |
+|------|---------|
+| [terraform](#requirement_terraform) | >= 1.0.0 |
+| [aws](#requirement_aws) | >= 4.5.0 |
+
+## Providers
+
+| Name | Version |
+|------|---------|
+| [aws](#provider_aws) | >= 4.5.0 |
+
+## Modules
+
+No modules.
+
+## Resources
+
+| Name | Type |
+|------|------|
+| [aws_ec2\_transit_gateway.this](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/ec2\_transit_gateway) | resource |
+
+## Inputs
+
+| Name | Description | Type | Default | Required |
+|------|-------------|------|---------|:--------:|
+| [amazon_side_asn](#input_amazon_side_asn) | Private Autonomous System Number (ASN) for the Amazon side of a BGP session. The range is 64512 to 65534 for 16-bit ASNs and 4200000000 to 4294967294 for 32-bit ASNs. The default is 64512. | `number` | `64512` | no |
+| [custom_tags](#input_custom_tags) | (Optional) A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable. | `map(string)` | `{}` | no |
+| [description](#input_description) | Description of the EC2 Transit Gateway | `string` | `null` | no |
+| [enable_auto_accept_shared_attachments](#input_enable_auto_accept_shared_attachments) | Whether resource attachment requests are automatically accepted. Default is false. | `bool` | `false` | no |
+| [enable_default_route_table_association](#input_enable_default_route_table_association) | Whether resource attachments are automatically associated with the default route table. Default is true. | `bool` | `true` | no |
+| [enable_default_route_table_propagation](#input_enable_default_route_table_propagation) | Whether transit gateway attachments automatically propagate routes to the default route table. Default is true. | `bool` | `true` | no |
+| [enable_dns_support](#input_enable_dns_support) | Whether DNS support is enabled on the transit gateway. Default to true. | `bool` | `true` | no |
+| [enable_multicast_support](#input_enable_multicast_support) | Whether multicast is enabled on the transit gateway. Default is false. | `bool` | `false` | no |
+| [enable_vpn_ecmp_support](#input_enable_vpn_ecmp_support) | Whether VPN Equal Cost Multipath Protocol support is enabled on the transit gateway. Default is true. | `bool` | `true` | no |
+| [name](#input_name) | The name of the Transit Gateway | `string` | n/a | yes |
+| [transit_gateway_cidr_blocks](#input_transit_gateway_cidr_blocks) | List of IPv4 or IPv6 CIDR blocks to use for the transit gateway. Must be a size /24 CIDR block or larger for IPv4, or a size /64 CIDR block or larger for IPv6. | `list(string)` | `null` | no |
+
+## Outputs
+
+| Name | Description |
+|------|-------------|
+| [default_route_table_id](#output_default_route_table_id) | Transit Gateway default route table identifier. |
+| [id](#output_id) | Transit Gateway identifier. |
+
+
+
+## Sample Usage
+
+
+
+
+```hcl title="main.tf"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY MODULE
+# ------------------------------------------------------------------------------------------------------
+
+module "transit_gateway" {
+
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway?ref=v0.26.2"
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # The name of the Transit Gateway
+ name =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Private Autonomous System Number (ASN) for the Amazon side of a BGP session.
+ # The range is 64512 to 65534 for 16-bit ASNs and 4200000000 to 4294967294 for
+ # 32-bit ASNs. The default is 64512.
+ amazon_side_asn = 64512
+
+ # (Optional) A map of tags to apply to all resources when applicable. The key
+ # is the tag name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # Description of the EC2 Transit Gateway
+ description = null
+
+ # Whether resource attachment requests are automatically accepted. Default is
+ # false.
+ enable_auto_accept_shared_attachments = false
+
+ # Whether resource attachments are automatically associated with the default
+ # route table. Default is true.
+ enable_default_route_table_association = true
+
+ # Whether transit gateway attachments automatically propagate routes to the
+ # default route table. Default is true.
+ enable_default_route_table_propagation = true
+
+ # Whether DNS support is enabled on the transit gateway. Default to true.
+ enable_dns_support = true
+
+ # Whether multicast is enabled on the transit gateway. Default is false.
+ enable_multicast_support = false
+
+ # Whether VPN Equal Cost Multipath Protocol support is enabled on the transit
+ # gateway. Default is true.
+ enable_vpn_ecmp_support = true
+
+ # List of IPv4 or IPv6 CIDR blocks to use for the transit gateway. Must be a
+ # size /24 CIDR block or larger for IPv4, or a size /64 CIDR block or larger
+ # for IPv6.
+ transit_gateway_cidr_blocks = null
+
+}
+
+
+```
+
+
+
+
+```hcl title="terragrunt.hcl"
+
+# ------------------------------------------------------------------------------------------------------
+# DEPLOY GRUNTWORK'S TRANSIT-GATEWAY MODULE
+# ------------------------------------------------------------------------------------------------------
+
+terraform {
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/transit-gateway?ref=v0.26.2"
+}
+
+inputs = {
+
+ # ----------------------------------------------------------------------------------------------------
+ # REQUIRED VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # The name of the Transit Gateway
+ name =
+
+ # ----------------------------------------------------------------------------------------------------
+ # OPTIONAL VARIABLES
+ # ----------------------------------------------------------------------------------------------------
+
+ # Private Autonomous System Number (ASN) for the Amazon side of a BGP session.
+ # The range is 64512 to 65534 for 16-bit ASNs and 4200000000 to 4294967294 for
+ # 32-bit ASNs. The default is 64512.
+ amazon_side_asn = 64512
+
+ # (Optional) A map of tags to apply to all resources when applicable. The key
+ # is the tag name and the value is the tag value. Note that the tag 'Name' is
+ # automatically added by this module but may be optionally overwritten by this
+ # variable.
+ custom_tags = {}
+
+ # Description of the EC2 Transit Gateway
+ description = null
+
+ # Whether resource attachment requests are automatically accepted. Default is
+ # false.
+ enable_auto_accept_shared_attachments = false
+
+ # Whether resource attachments are automatically associated with the default
+ # route table. Default is true.
+ enable_default_route_table_association = true
+
+ # Whether transit gateway attachments automatically propagate routes to the
+ # default route table. Default is true.
+ enable_default_route_table_propagation = true
+
+ # Whether DNS support is enabled on the transit gateway. Default to true.
+ enable_dns_support = true
+
+ # Whether multicast is enabled on the transit gateway. Default is false.
+ enable_multicast_support = false
+
+ # Whether VPN Equal Cost Multipath Protocol support is enabled on the transit
+ # gateway. Default is true.
+ enable_vpn_ecmp_support = true
+
+ # List of IPv4 or IPv6 CIDR blocks to use for the transit gateway. Must be a
+ # size /24 CIDR block or larger for IPv4, or a size /64 CIDR block or larger
+ # for IPv6.
+ transit_gateway_cidr_blocks = null
+
+}
+
+
+```
+
+
+
+
+
+
+
+## Reference
+
+
+
+
+### Required
+
+
+
+
+The name of the Transit Gateway
+
+
+
+
+### Optional
+
+
+
+
+Private Autonomous System Number (ASN) for the Amazon side of a BGP session. The range is 64512 to 65534 for 16-bit ASNs and 4200000000 to 4294967294 for 32-bit ASNs. The default is 64512.
+
+
+
+
+
+
+
+
+(Optional) A map of tags to apply to all resources when applicable. The key is the tag name and the value is the tag value. Note that the tag 'Name' is automatically added by this module but may be optionally overwritten by this variable.
+
+
+
+
+
+
+
+
+Description of the EC2 Transit Gateway
+
+
+
+
+
+
+
+
+Whether resource attachment requests are automatically accepted. Default is false.
+
+
+
+
+
+
+
+
+Whether resource attachments are automatically associated with the default route table. Default is true.
+
+
+
+
+
+
+
+
+Whether transit gateway attachments automatically propagate routes to the default route table. Default is true.
+
+
+
+
+
+
+
+
+Whether DNS support is enabled on the transit gateway. Default to true.
+
+
+
+
+
+
+
+
+Whether multicast is enabled on the transit gateway. Default is false.
+
+
+
+
+
+
+
+
+Whether VPN Equal Cost Multipath Protocol support is enabled on the transit gateway. Default is true.
+
+
+
+
+
+
+
+
+List of IPv4 or IPv6 CIDR blocks to use for the transit gateway. Must be a size /24 CIDR block or larger for IPv4, or a size /64 CIDR block or larger for IPv6.
+
+
+
+
+
+
+
+
+
+
+
+Transit Gateway default route table identifier.
+
+
+
+
+
+
+
+Transit Gateway identifier.
+
+
+
+
+
+
+
+
+
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-app-network-acls/vpc-app-network-acls.md b/docs/reference/modules/terraform-aws-vpc/vpc-app-network-acls/vpc-app-network-acls.md
index 5fcf9935b1..4adabe20c7 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-app-network-acls/vpc-app-network-acls.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-app-network-acls/vpc-app-network-acls.md
@@ -9,17 +9,17 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC-App Network ACLs Terraform Module
-View Source
+View Source
Release Notes
This Terraform Module adds a default set of [Network
ACLs](http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_ACLs.html) to a VPC created using the
-[vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-app) module. The ACLs enforce the following security settings (based on [A Reference VPC
+[vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-app) module. The ACLs enforce the following security settings (based on [A Reference VPC
Architecture](https://www.whaletech.co/2014/10/02/reference-vpc-architecture.html)):
* **Public subnet**: Allow all requests.
@@ -92,7 +92,7 @@ module "network_acls" {
module "vpc_app_network_acls" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app-network-acls?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app-network-acls?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -211,7 +211,7 @@ module "vpc_app_network_acls" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app-network-acls?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app-network-acls?ref=v0.26.2"
}
inputs = {
@@ -625,11 +625,11 @@ Use this variable to ensure the Network ACL does not get created until the VPC i
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-app/vpc-app.md b/docs/reference/modules/terraform-aws-vpc/vpc-app/vpc-app.md
index d8de63d026..ac7ba73ae2 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-app/vpc-app.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-app/vpc-app.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# IPv6
-View Source
+View Source
Release Notes
@@ -55,8 +55,8 @@ To summarize:
* In a given subnet tier, there are usually three or four actual subnets, one for each Availability Zone.
* Therefore, if we created a single VPC in the `us-west-2` region, which has Availability Zones `us-west-2a`,`us-west-2b`,
and `us-west-2c`, each subnet tier would have three subnets (one per Availability Zone) for a total of 9 subnets in all.
-* The only way to reach this VPC is from the public Internet via a publicly exposed sevice, or via the [mgmt VPC](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-mgmt),
- which uses [VPC Peering](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-peering) to make this VPC accessible from the mgmt VPC.
+* The only way to reach this VPC is from the public Internet via a publicly exposed sevice, or via the [mgmt VPC](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-mgmt),
+ which uses [VPC Peering](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-peering) to make this VPC accessible from the mgmt VPC.
* Philosophically, everything in a VPC should be isolated from all resources in any other VPC. In particular, we want
to ensure that our stage environment is completely independent from prod. This architecture helps to reinforce that.
@@ -71,7 +71,7 @@ nearly all use-cases, and is consistent with many examples and existing document
## Other VPC Core Concepts
-Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules//_docs/vpc-core-concepts.md) like subnets, NAT Gateways, and VPC Endpoints.
+Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) like subnets, NAT Gateways, and VPC Endpoints.
## IPv6 Design
@@ -109,7 +109,7 @@ module "vpc_app_ipv6_example" {
module "vpc_app" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -500,7 +500,7 @@ module "vpc_app" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.26.2"
}
inputs = {
@@ -1736,11 +1736,11 @@ A map of all public subnets, with the subnet name as the key, and all `aws-subne
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder-rules/vpc-dns-forwarder-rules.md b/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder-rules/vpc-dns-forwarder-rules.md
index 30995417c7..e3a61d8cab 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder-rules/vpc-dns-forwarder-rules.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder-rules/vpc-dns-forwarder-rules.md
@@ -9,23 +9,23 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC DNS Forwarder Rules Terraform Module
-View Source
+View Source
Release Notes
This Terraform Module creates [Route 53 Resolver Forwarding
Rules](https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/resolver-rules-managing.html) for a VPC that will
-utilize Route 53 Resolver Endpoints created with the [vpc-dns-forwarder module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-dns-forwarder). These forwarding
+utilize Route 53 Resolver Endpoints created with the [vpc-dns-forwarder module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-dns-forwarder). These forwarding
rules, combined with Route 53 Resolvers, allow DNS queries for specific domains to be resolved by peered VPCs.
## How do you specify the hostnames that use the forwarder?
By default, no DNS query will be routed through the Route 53 Resolvers created by the [vpc-dns-forwarder
-module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-dns-forwarder). You need to create forwarding rules that specify which specific domains should be
+module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-dns-forwarder). You need to create forwarding rules that specify which specific domains should be
resolved through the Route 53 Resolvers so that they are resolved over the peering connection. You can use this module
to construct the forwarding rules.
@@ -72,7 +72,7 @@ forwarder rule, it will match any domain that ends with `.local` (note the dot),
module "vpc_dns_forwarder_rules" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder-rules?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder-rules?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -126,7 +126,7 @@ module "vpc_dns_forwarder_rules" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder-rules?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder-rules?ref=v0.26.2"
}
inputs = {
@@ -180,11 +180,11 @@ inputs = {
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder/vpc-dns-forwarder.md b/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder/vpc-dns-forwarder.md
index 9cdf421921..da1d7e2019 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder/vpc-dns-forwarder.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-dns-forwarder/vpc-dns-forwarder.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC DNS Forwarder Terraform Module
-View Source
+View Source
Release Notes
@@ -47,7 +47,7 @@ private endpoints internal to the target VPC.
By default, no DNS query will be routed through the Route 53 Resolvers created by this module. You need to create
forwarding rules that specify which specific domains should be resolved through the Route 53 Resolvers created by this
-module. You can use the [vpc-dns-forwarder-rules module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-dns-forwarder-rules) to construct the forwarding rules.
+module. You can use the [vpc-dns-forwarder-rules module](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-dns-forwarder-rules) to construct the forwarding rules.
## Sample Usage
@@ -62,7 +62,7 @@ module. You can use the [vpc-dns-forwarder-rules module](https://github.com/grun
module "vpc_dns_forwarder" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -138,7 +138,7 @@ module "vpc_dns_forwarder" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-dns-forwarder?ref=v0.26.2"
}
inputs = {
@@ -380,11 +380,11 @@ The secondary IP address of the DNS resolver in the origin VPC. This is the IP t
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-flow-logs/vpc-flow-logs.md b/docs/reference/modules/terraform-aws-vpc/vpc-flow-logs/vpc-flow-logs.md
index afd4503c27..56c80afebc 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-flow-logs/vpc-flow-logs.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-flow-logs/vpc-flow-logs.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC Flow Logs Terraform Module
-View Source
+View Source
Release Notes
@@ -86,7 +86,7 @@ TODO: Publish flow logs to an S3 bucket or CloudWatch Logs group in another acco
module "vpc_flow_logs" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-flow-logs?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-flow-logs?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# OPTIONAL VARIABLES
@@ -232,7 +232,7 @@ module "vpc_flow_logs" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-flow-logs?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-flow-logs?ref=v0.26.2"
}
inputs = {
@@ -784,11 +784,11 @@ The name of the S3 bucket where flow logs are published.
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-interface-endpoint/vpc-interface-endpoint.md b/docs/reference/modules/terraform-aws-vpc/vpc-interface-endpoint/vpc-interface-endpoint.md
index 650e175222..756935d2d9 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-interface-endpoint/vpc-interface-endpoint.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-interface-endpoint/vpc-interface-endpoint.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# Interface VPC Endpoint
-View Source
+View Source
Release Notes
@@ -193,7 +193,7 @@ Not specifying a rule allows all traffic.
## Other VPC Core Concepts
-Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules//_docs/vpc-core-concepts.md) like subnets and NAT Gateways.
+Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) like subnets and NAT Gateways.
## Sample Usage
@@ -208,7 +208,7 @@ Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-
module "vpc_interface_endpoint" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-interface-endpoint?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-interface-endpoint?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -2023,7 +2023,7 @@ module "vpc_interface_endpoint" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-interface-endpoint?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-interface-endpoint?ref=v0.26.2"
}
inputs = {
@@ -8331,11 +8331,11 @@ If you have private dns enabled, then your streaming calls would automatically g
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-mgmt-network-acls/vpc-mgmt-network-acls.md b/docs/reference/modules/terraform-aws-vpc/vpc-mgmt-network-acls/vpc-mgmt-network-acls.md
index 96d512ce8a..f6bb02efb3 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-mgmt-network-acls/vpc-mgmt-network-acls.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-mgmt-network-acls/vpc-mgmt-network-acls.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# \[DEPRECATED] VPC-Mgmt Network ACLs Terraform Module
-View Source
+View Source
Release Notes
@@ -28,7 +28,7 @@ aware that, in a future release, once we feel the new functionality in `vpc-app`
This Terraform Module adds a default set of [Network
ACLs](http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_ACLs.html) to a VPC created using the
-[vpc-mgmt](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-mgmt) module. The ACLs enforce the following security settings (based on [A Reference VPC
+[vpc-mgmt](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-mgmt) module. The ACLs enforce the following security settings (based on [A Reference VPC
Architecture](https://www.whaletech.co/2014/10/02/reference-vpc-architecture.html)):
* **Public subnet**: Allow all requests.
@@ -63,7 +63,7 @@ EC2 instance), a network ACL controls what inbound and outbound traffic is allow
module "vpc_mgmt_network_acls" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt-network-acls?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt-network-acls?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -142,7 +142,7 @@ module "vpc_mgmt_network_acls" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt-network-acls?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt-network-acls?ref=v0.26.2"
}
inputs = {
@@ -345,11 +345,11 @@ The number to use for the first rule that is created by this module. All rules i
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-mgmt/vpc-mgmt.md b/docs/reference/modules/terraform-aws-vpc/vpc-mgmt/vpc-mgmt.md
index 2bd24bcc2d..7954092112 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-mgmt/vpc-mgmt.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-mgmt/vpc-mgmt.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# \[DEPRECATED] VPC-Mgmt Terraform Module
-View Source
+View Source
Release Notes
@@ -27,7 +27,7 @@ aware that, in a future release, once we feel the new functionality in `vpc-app`
`vpc-mgmt` entirely.
This Terraform Module launches a single VPC meant to house DevOps and other management services. By contrast, the apps
-that power your business should run in an "app" VPC. (See the [vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-app) module.)
+that power your business should run in an "app" VPC. (See the [vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-app) module.)
## What's a VPC?
@@ -65,7 +65,7 @@ To summarize:
## VPC Peering
-Learn more about VPC Peering in the [vpc-peering](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-peering) module.
+Learn more about VPC Peering in the [vpc-peering](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-peering) module.
## SSH Access via the Bastion Host
@@ -79,7 +79,7 @@ examples](https://github.com/gruntwork-io/terraform-aws-server/tree/main/example
## Other VPC Core Concepts
-Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules//_docs/vpc-core-concepts.md) like subnets, NAT Gateways, and VPC Endpoints.
+Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules//_docs/vpc-core-concepts.md) like subnets, NAT Gateways, and VPC Endpoints.
## Sample Usage
@@ -94,7 +94,7 @@ Learn about [Other VPC Core Concepts](https://github.com/gruntwork-io/terraform-
module "vpc_mgmt" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -301,7 +301,7 @@ module "vpc_mgmt" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-mgmt?ref=v0.26.2"
}
inputs = {
@@ -1011,11 +1011,11 @@ A null_resource that indicates that the VPC is ready, including all of its resou
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-accepter/vpc-peering-cross-accounts-accepter.md b/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-accepter/vpc-peering-cross-accounts-accepter.md
index 88f54a95b9..8d12bc6e7d 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-accepter/vpc-peering-cross-accounts-accepter.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-accepter/vpc-peering-cross-accounts-accepter.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# vpc-peering-cross-accounts-accepter
-View Source
+View Source
Release Notes
@@ -78,7 +78,7 @@ No modules.
module "vpc_peering_cross_accounts_accepter" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-accepter?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-accepter?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -136,7 +136,7 @@ module "vpc_peering_cross_accounts_accepter" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-accepter?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-accepter?ref=v0.26.2"
}
inputs = {
@@ -297,11 +297,11 @@ Peering connection ID.
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-requester/vpc-peering-cross-accounts-requester.md b/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-requester/vpc-peering-cross-accounts-requester.md
index fd745cd948..86a8062a7a 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-requester/vpc-peering-cross-accounts-requester.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-peering-cross-accounts-requester/vpc-peering-cross-accounts-requester.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# vpc-peering-cross-accounts-requester
-View Source
+View Source
Release Notes
@@ -73,7 +73,7 @@ No modules.
module "vpc_peering_cross_accounts_requester" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-requester?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-requester?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -131,7 +131,7 @@ module "vpc_peering_cross_accounts_requester" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-requester?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-cross-accounts-requester?ref=v0.26.2"
}
inputs = {
@@ -299,11 +299,11 @@ Peering connection ID.
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-peering-external/vpc-peering-external.md b/docs/reference/modules/terraform-aws-vpc/vpc-peering-external/vpc-peering-external.md
index a18a2dc4ca..9d5f3ef4c8 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-peering-external/vpc-peering-external.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-peering-external/vpc-peering-external.md
@@ -9,11 +9,11 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC Peering For External VPCs Module
-View Source
+View Source
Release Notes
@@ -87,7 +87,7 @@ EC2 instance), a network ACL controls what inbound and outbound traffic is allow
module "vpc_peering_external" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-external?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-external?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -202,7 +202,7 @@ module "vpc_peering_external" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-external?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering-external?ref=v0.26.2"
}
inputs = {
@@ -317,11 +317,11 @@ inputs = {
diff --git a/docs/reference/modules/terraform-aws-vpc/vpc-peering/vpc-peering.md b/docs/reference/modules/terraform-aws-vpc/vpc-peering/vpc-peering.md
index 2ef03057ae..3758dfe661 100644
--- a/docs/reference/modules/terraform-aws-vpc/vpc-peering/vpc-peering.md
+++ b/docs/reference/modules/terraform-aws-vpc/vpc-peering/vpc-peering.md
@@ -9,19 +9,19 @@ import VersionBadge from '../../../../../src/components/VersionBadge.tsx';
import { HclListItem, HclListItemDescription, HclListItemTypeDetails, HclListItemDefaultValue, HclGeneralListItem } from '../../../../../src/components/HclListItem.tsx';
import { ModuleUsage } from "../../../../../src/components/ModuleUsage";
-
+
# VPC-Peering Terraform Module
-View Source
+View Source
Release Notes
This Terraform Module creates [VPC Peering
Connections](http://docs.aws.amazon.com/AmazonVPC/latest/PeeringGuide/Welcome.html) between VPCs. Normally, VPCs are
completely isolated from each other, but sometimes, you want to allow traffic to flow between them, such as allowing
-DevOps tools running in a Mgmt VPC (see [vpc-mgmt](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-mgmt)) to talk to apps running in a Stage or Prod VPC (see
-[vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.1/modules/vpc-app)). This module can create peering connections and route table entries that make this sort of
+DevOps tools running in a Mgmt VPC (see [vpc-mgmt](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-mgmt)) to talk to apps running in a Stage or Prod VPC (see
+[vpc-app](https://github.com/gruntwork-io/terraform-aws-vpc/tree/v0.26.2/modules/vpc-app)). This module can create peering connections and route table entries that make this sort of
cross-VPC communication possible.
## What's a VPC?
@@ -57,7 +57,7 @@ and production, someone in staging *cannot* access production.
module "vpc_peering" {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering?ref=v0.26.2"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
@@ -141,7 +141,7 @@ module "vpc_peering" {
# ------------------------------------------------------------------------------------------------------
terraform {
- source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering?ref=v0.26.1"
+ source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-peering?ref=v0.26.2"
}
inputs = {
@@ -225,11 +225,11 @@ inputs = {