diff --git a/docs/hub/security-tokens.md b/docs/hub/security-tokens.md
index af4822286..40545aff6 100644
--- a/docs/hub/security-tokens.md
+++ b/docs/hub/security-tokens.md
@@ -5,8 +5,8 @@
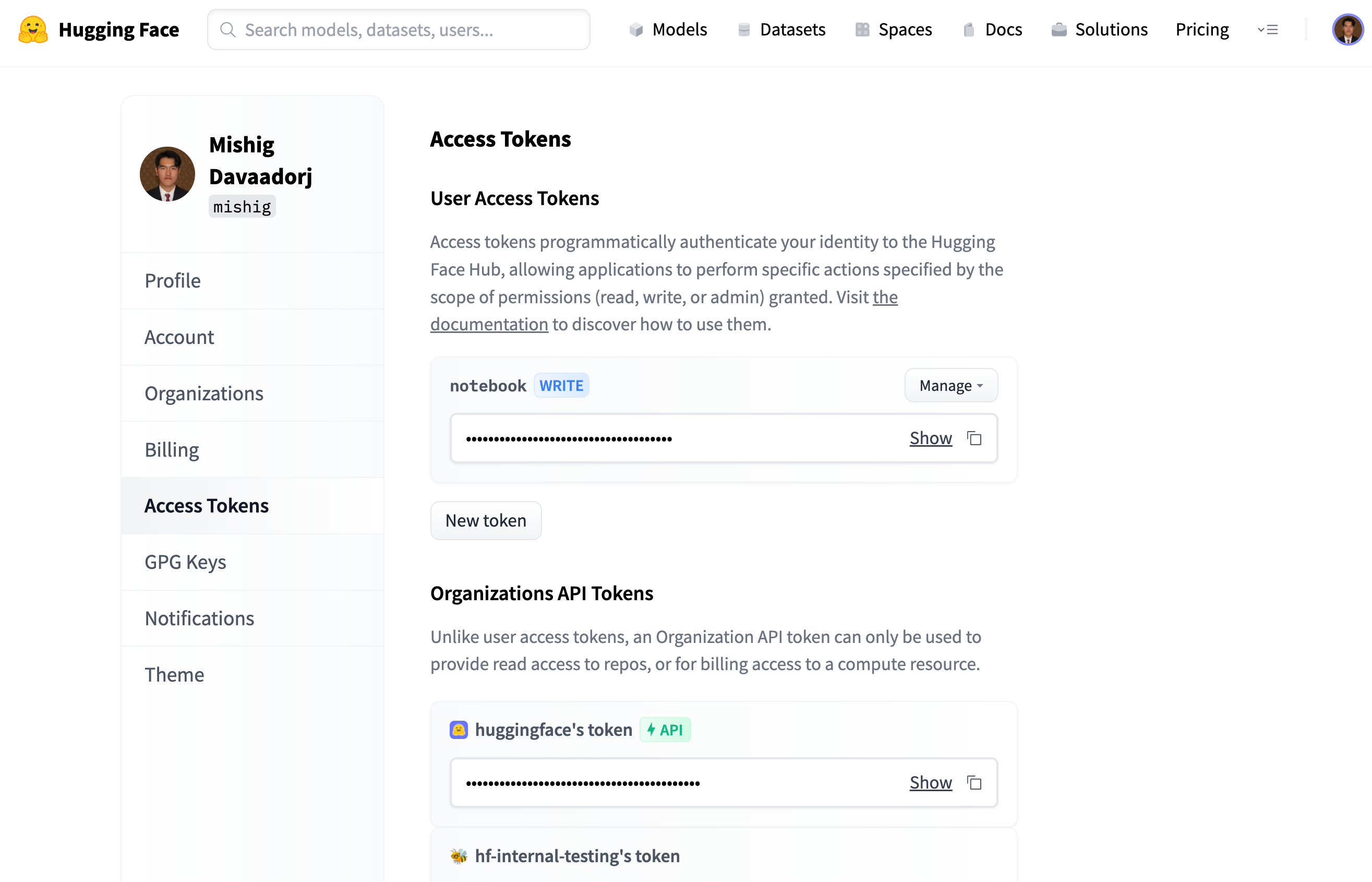
User Access Tokens are the preferred way to authenticate an application or notebook to Hugging Face services. You can manage your access tokens in your [settings](https://huggingface.co/settings/tokens).
Access tokens allow applications and notebooks to perform specific actions specified by the scope of the roles shown in the following:
@@ -15,6 +15,15 @@ Access tokens allow applications and notebooks to perform specific actions speci
- `write`: tokens with this role additionally grant write access to the repositories you have write access to. Use this token if you need to create or push content to a repository (e.g., when training a model or modifying a model card).
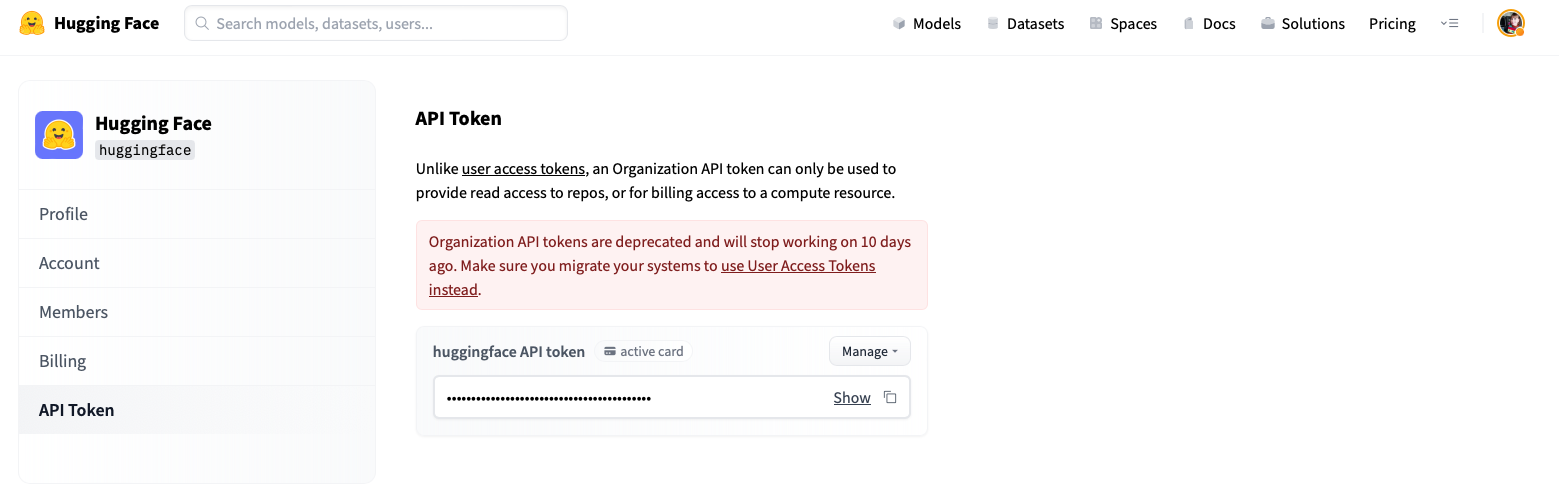
+Note that Organization API Tokens have been deprecated:
+
+
+
+
+
 -
- +
+ +
+
 -
- +
+ +
+
 +
+ +
+