Deploy the same version service in multiple clusters #13327
Labels
area/networking
lifecycle/automatically-closed
Indicates a PR or issue that has been closed automatically.
lifecycle/stale
Indicates a PR or issue hasn't been manipulated by an Istio team member for a while
Milestone
Describe the feature request
Deploy the same version service in multiple clusters using gateway connected feature and make sure they can be accessed
Describe alternatives you've considered
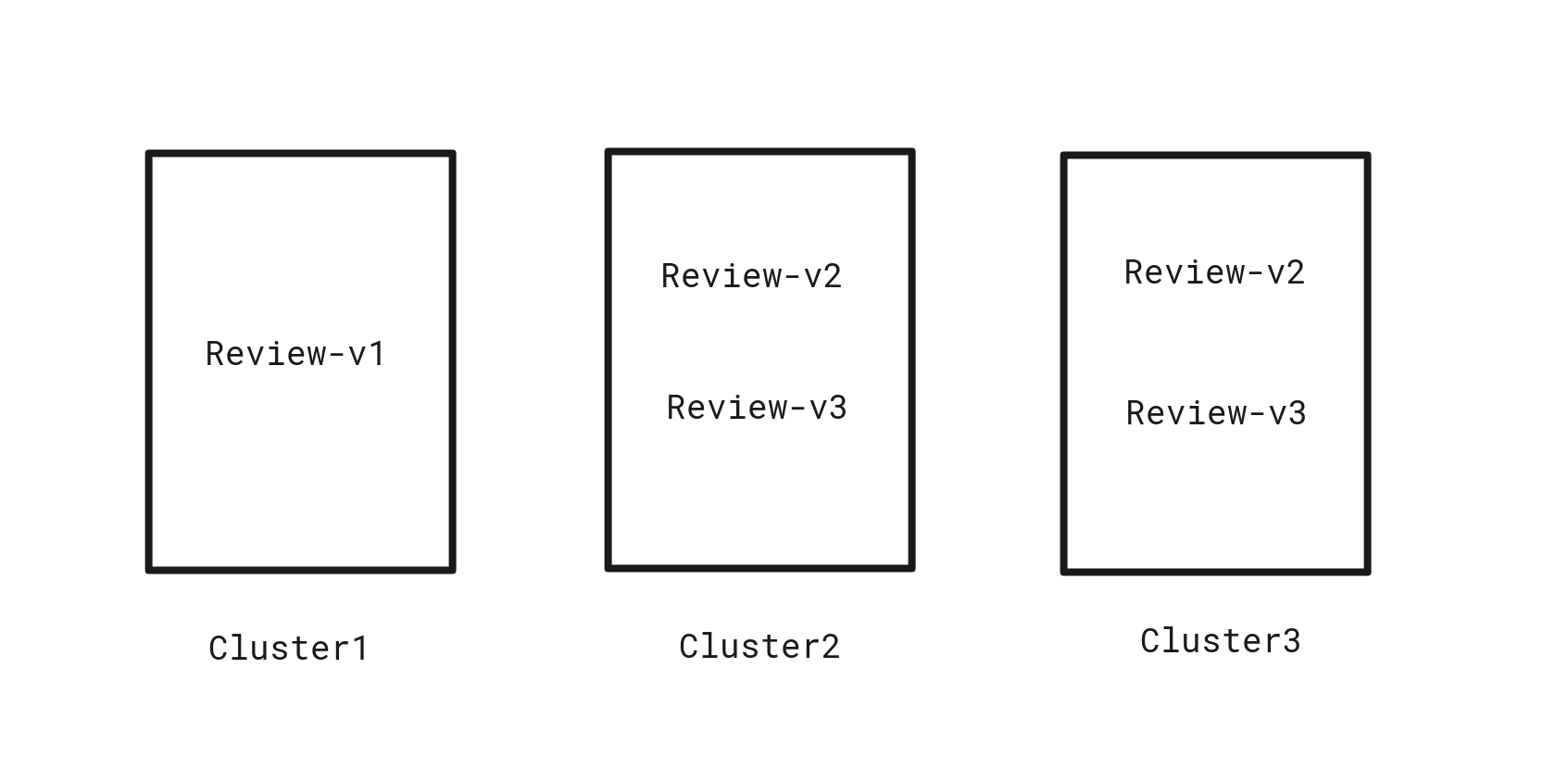
In the Version Routing in a Multicluster Service Mesh tutorial , it deploys two version of review services in the second cluster. I created three Kubernetes clusters and deploy review-v1 in cluster1, review-v2 and review-v3 in cluster2 and cluster 3.
I wonder how can I deploy the same version service like review-v2 in two clusters and make sure both of them can be accessed.
Currently, I have tried to add some lines to the deployment files:
As you can see from the yaml file, I added two endpoints for the ServiceEntry review-default. Since one subsets cannot have two labels, the second label in the configuration file will overwrite the first one. After deployment, v2 subset's corresponding label is cluster2, and v3 subset's corresponding label is cluster3. Therefore, after the deployment, all requests for a certain service will be directed to a cluster instead of two-clusters in a certain order (such as round-robin).
The text was updated successfully, but these errors were encountered: