New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
fs: bring back macos-specific copyfile(3) #2578
Conversation
This reverts commit 5bc4d77.
|
We need to do an For the record, this one is possibly due to this part in For clonefileat it should fail correctly, since |
63f4cf5
to
b3b3c43
Compare
We can do our own open!
b3b3c43
to
f2b9cfd
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@cjihrig You probably want to take a look at this?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
MacOS does not have faccess(2) in case you are wondering why I did this. There is only access(2) with the "real UID" shenanigans that will bite us in the future.
Is using fstat() an option? At least we wouldn't be creating and unlinking the file.
src/unix/fs.c
Outdated
| int result; | ||
| int err; | ||
| size_t bytes_to_send; | ||
| int64_t in_offset; | ||
| ssize_t bytes_written; | ||
|
|
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Can you add this line back.
|
fstat is not the best idea because ACL is a thing on macOS. The correct way to do so is via the access(2) family of APIs, but macOS does not have a faccess(2) / faccessat(2) that does EUID instead of the UID with AT_EACCESS. A quick Google search I did yesterday finds CarbonStdCLib.o, apparently a C library polyfill, doing something similar for faccess. Unlinking is what the OS X cp(1) command does for Gonna fix the branch thing later today (UTC+8). |
|
Hmm, looks like there is faccessat(2) on macOS >= 10.10. What's the OS support policy for libuv and nodejs? (Looks like I can do that for node, which only supports macOS >= 10.11.) |
|
libuv supports macOS >= 10.7. See the list of supported platforms here. |
|
A good-ish polyfill for our desired functionality is found in gnulib euidaccess(3) (GPL!!). It gives two implementations: the correct but non-reentrant one using a setre{u,g}id-access-setre{u,g}id pattern and the traditional stat thing which is incorrect with ACL. So which one is more evil here, changing a global state or being incorrect in a case not yet tested? Since faccessat(2) is a syscall, I can possibly get away with doing a version check like the clone part and syscall(2) the whole thing away on 10.10+. I still need to pick a way to polyfill this feature for [10.7, 10.10), so please do give your suggestion on that. It should look like: #if defined(__APPLE__) && !TARGET_OS_IPHONE
/** @returns 1: writeable. 2: does not exist. */
static int fs__mac_canwrite(const char* path, int darwin_kern_maj) {
int res = 0;
// 10.7+
if (darwin_kern_maj >= 11) {
// TODO: rewrite to use syscall(2) and sys/syscall.h!
res = faccessat(AT_FDCWD, path, W_OK | R_OK, AT_EACCESS) == 0;
goto test_exist;
}
/* polyfill here */
test_exist: // should be reused by stat or access polyfills
if (res == 0 && errorno == ENOENT)
return 2;
return res;
}
static bool fs__mac_can_copy(const char* path, int darwin_kern_maj, int excl) {
int res;
res = fs__mac_canwrite(path, darwin_kern_maj);
if (res != 2)
return ! excl;
// Apple manpage says their dirname does not modify the input. Trust it for now.
return !! fs__mac_canwrite(dirname(path), darwin_kern_maj);
}
#endif |
|
I presume the gnulib implementation will be GPL and therefore cannot be used in libuv. |
|
Yeah, someone will need to wipe their brain with only the phrase "implement an access check based on stat() or setuid and access(2)" left if they decided to implement it here. Should possibly add a click warning on the gnulib link. |
6e117ff
to
2d2f929
Compare
* remove a stat dependency retained from copying the non-Darwin open() codepath. We don't need to make it super right here since it's deleted soon afterwards, so just a 0700 will do. * retain whatever copyfile tries to say in the errno, instead of the generic error -1.
|
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions. |
|
This issue has been automatically marked as stale because it has not had recent activity. It will be closed if no further activity occurs. Thank you for your contributions. |
|
With this change, the macOS implementation has more overlap with the Unix implementation than it previously did. The overlap is more prone to getting out of sync - for example, the Unix implementation no longer opens the destination with Maybe we should look into using |
|
ping |
|
I opened #3406 earlier this week to raise the baseline to macOS 10.15. When accepted and merged, I think that would unblock this PR. |
That's good, but I thought the main issue here was that APFS Copy on Write is not supported. When it is supported, the speedup should be closer to infinity than 2x. |
|
This wasn’t with the COPYFILE_FICLONE flag, so whether or not it used copy
on write is up to the implementation of copyfile()
…On Fri, Jan 14, 2022 at 5:09 AM Petter Uvesten ***@***.***> wrote:
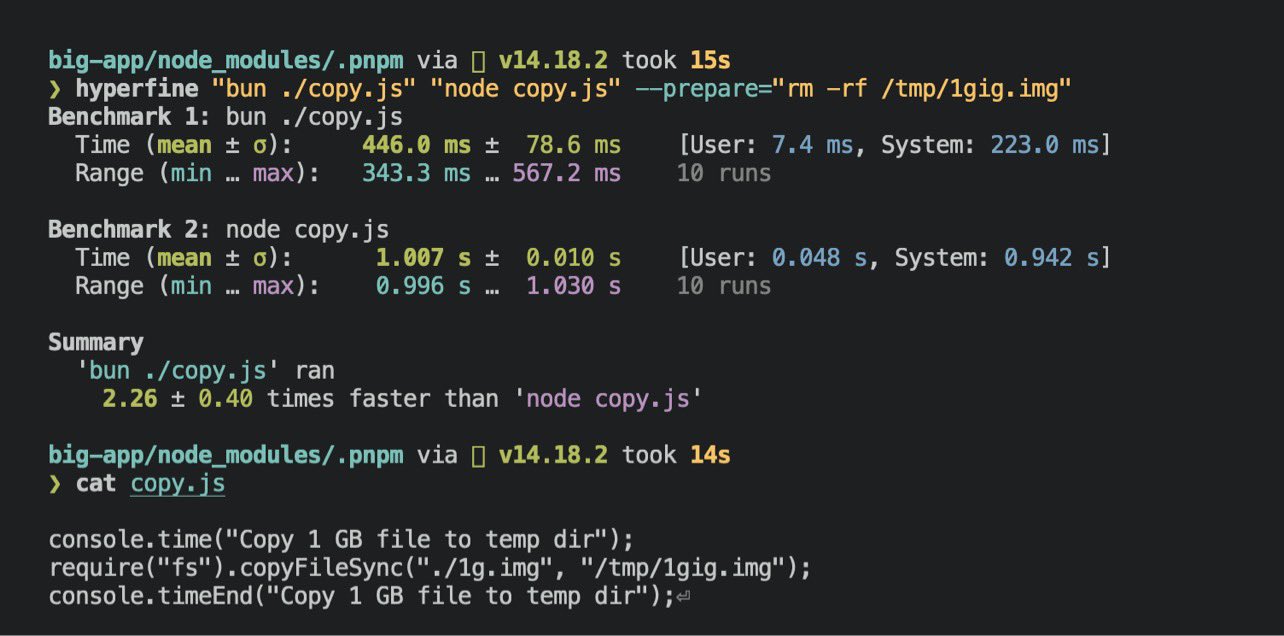
To give you a sense of the impact here — bun’s implementation of
fs.copyFileSync which uses copyfile() on macOS performs 2x faster than
node’s fs.copyFileSync when copying a 1 GB file.
That's good, but I thought the main issue here was that APFS Copy on Write
is not supported. When it is supported, the speedup should be closer to
infinity than 2x.
—
Reply to this email directly, view it on GitHub
<#2578 (comment)>, or
unsubscribe
<https://github.com/notifications/unsubscribe-auth/AAFNGS7IQTIBOXES67KGINLUWAN7NANCNFSM4J3JET2A>
.
You are receiving this because you commented.Message ID:
***@***.***>
|
|
The baseline is now macos 10.15. There's one remaining comment from @cjihrig so I defer to him on whether it's ready for merging. Let me know if I should also review. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM if the tests pass.
|
|
||
| /* Check OS version. Cloning is only supported on macOS >= 10.12. */ | ||
| if (req->flags & UV_FS_COPYFILE_FICLONE_FORCE) { | ||
| if (can_clone == 0) { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| if (can_clone == 0) { | |
| if (0 == uv__load_relaxed(&can_clone)) { |
| if (1 != sscanf(buf, "%d", &major)) | ||
| abort(); | ||
|
|
||
| can_clone = -1 + 2 * (major >= 16); /* macOS >= 10.12 */ |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| can_clone = -1 + 2 * (major >= 16); /* macOS >= 10.12 */ | |
| /* macOS >= 10.12 */ | |
| uv__store_relaxed(&can_clone, -1 + 2 * (major >= 16)); |
| can_clone = -1 + 2 * (major >= 16); /* macOS >= 10.12 */ | ||
| } | ||
|
|
||
| if (can_clone < 0) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| if (can_clone < 0) | |
| if (0 > uv__load_relaxed(&can_clone)) |
| /* Copyfile(2) tries to chmod the file when a rw open fails. This causes | ||
| * nodejs/node#26936. | ||
| * Make it behave by doing our own open-test, because faccessat(2) is not | ||
| * present on OS X < 10.10. */ | ||
| dstfd = uv_fs_open(NULL, | ||
| &fs_req, | ||
| req->new_path, | ||
| dst_flags, | ||
| S_IRWXU, | ||
| NULL); | ||
| uv_fs_req_cleanup(&fs_req); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
With 10.15 as the baseline, it's presumably okay to use faccessat() now?
| if (dstfd < 0) { | ||
| return dstfd; | ||
| } else { | ||
| err = uv__close_nocheckstdio(dstfd); | ||
| if (err) { | ||
| return err; | ||
| } | ||
| /* We might have created it. We also don't want clone to fail without | ||
| * UV_FS_COPYFILE_EXCL. */ | ||
| unlink(req->new_path); | ||
| } | ||
|
|
||
| if (copyfile(req->path, req->new_path, NULL, flags)) { | ||
| return UV__ERR(errno); | ||
| } | ||
| return 0; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Stylistic:
| if (dstfd < 0) { | |
| return dstfd; | |
| } else { | |
| err = uv__close_nocheckstdio(dstfd); | |
| if (err) { | |
| return err; | |
| } | |
| /* We might have created it. We also don't want clone to fail without | |
| * UV_FS_COPYFILE_EXCL. */ | |
| unlink(req->new_path); | |
| } | |
| if (copyfile(req->path, req->new_path, NULL, flags)) { | |
| return UV__ERR(errno); | |
| } | |
| return 0; | |
| if (dstfd < 0) | |
| return dstfd; | |
| err = uv__close_nocheckstdio(dstfd); | |
| if (err) | |
| return err; | |
| /* We might have created it. We also don't want clone to fail without | |
| * UV_FS_COPYFILE_EXCL. */ | |
| unlink(req->new_path); | |
| if (copyfile(req->path, req->new_path, NULL, flags)) | |
| return UV__ERR(errno); | |
| return 0; |
| return UV__ERR(errno); | ||
| } | ||
| return 0; | ||
| #else |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| #else | |
| #else /* defined(__APPLE__) && !TARGET_OS_IPHONE */ |
| @@ -1287,6 +1359,7 @@ static ssize_t uv__fs_copyfile(uv_fs_t* req) { | |||
|
|
|||
| errno = UV__ERR(result); | |||
| return -1; | |||
| #endif | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| #endif | |
| #endif /* defined(__APPLE__) && !TARGET_OS_IPHONE */ |
Makes it easier to keep track of what else/endif belongs to what ifdef.
|
This issue has been automatically marked as stale because it has not had recent activity. Thank you for your contributions. |
|
Never Gonna Give You Up |
|
Adding my comment so my anti stale bot will take care of this pr from now on |
|
There's some unaddressed feedback I left in February. Most is stylistic but the faccessat() question needs an answer before this can go in. Also, a gentle reminder that bots and their owners are likely to meet with swift and permanent bans. |
|
This issue has been automatically marked as stale because it has not had recent activity. Thank you for your contributions. |
|
Where is the anti stale bot? |
|
I've added the not-stale label. Hopefully that will keep stale bot away. |
|
@Artoria2e5 Do you plan on picking up this pull request again? If not, maybe someone else wants to step up and get this over the finish line? |
I've tried to incorporate your feedback: #3654 |
|
In light of an updated PR being available I am closing this one. Just don't have time for code when I am all stuck at McD, I am afraid. |
Go check out #3654 instead. @mischnic is awesome.
copyfile(3) does not always do its own open according to permission rules. We can solve that by guarding it with one of our own opens. This way we can keep the cool clonefile thing for huge node_modules and still have sensible results.
MacOS does not have faccess(2) in case you are wondering why I did this. There is only access(2) with the "real UID" shenanigans that will bite us in the future.
This PR partially reverts #2233. Tests in the said PR are kept, and they should pass.