diff --git a/README.md b/README.md
index f7984baa..a216ec70 100644
--- a/README.md
+++ b/README.md
@@ -61,13 +61,6 @@ Dotenv is a zero-dependency module that loads environment variables from a `.env
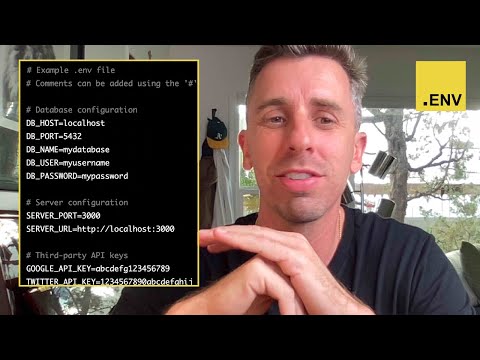
## 🌱 Install
-
-
-
-

-
+

+

+
-
-

-
 -
- -
- +
+ -
-