+
+
+
+
+
+
+ Login
+
+
+
+ {linkToRender()}
+ {formToRender()}
+  +
+We'll refer to whatever biometric device that's used as simply a "device" below. The WebAuthn flow includes two "phases":
+
+1. **Registration**: the first time a new device is added for a user (a user can have multiple devices registered)
+2. **Authentication**: the device is recognized and can be used to login on subsequent visits
+
+### User Experience
+
+The `LoginPage` generated by Redwood includes two new prompts on the login page, depending on the state of the user and whether they have registered their device yet or not:
+
+**Registration**
+
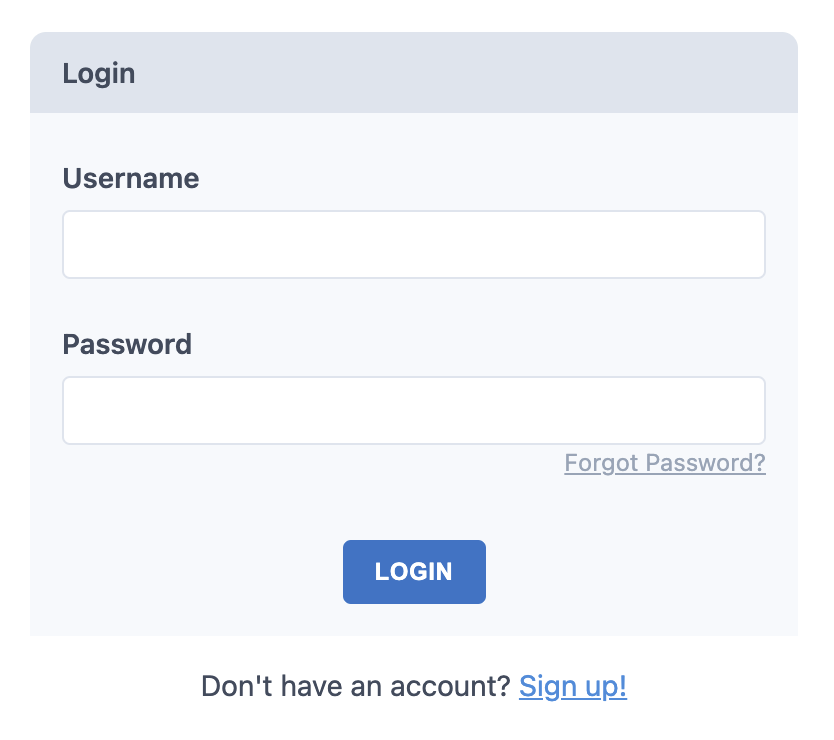
+The user is prompt to login with username/password:
+
+
+
+We'll refer to whatever biometric device that's used as simply a "device" below. The WebAuthn flow includes two "phases":
+
+1. **Registration**: the first time a new device is added for a user (a user can have multiple devices registered)
+2. **Authentication**: the device is recognized and can be used to login on subsequent visits
+
+### User Experience
+
+The `LoginPage` generated by Redwood includes two new prompts on the login page, depending on the state of the user and whether they have registered their device yet or not:
+
+**Registration**
+
+The user is prompt to login with username/password:
+
+ +
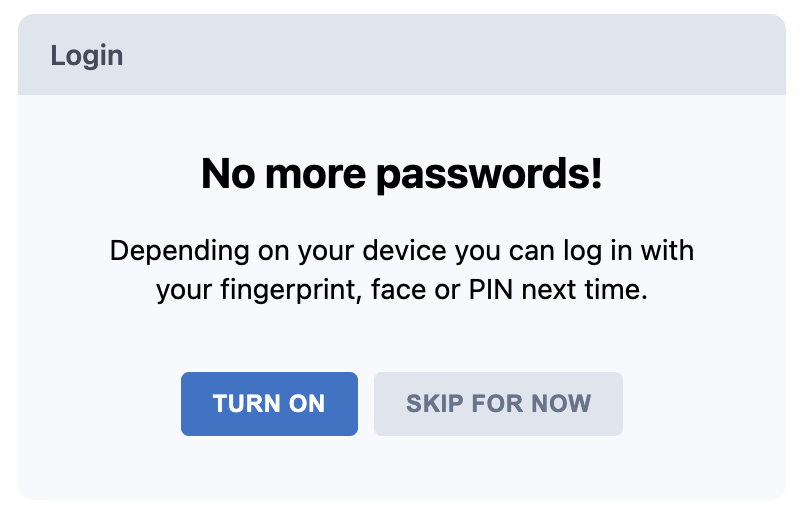
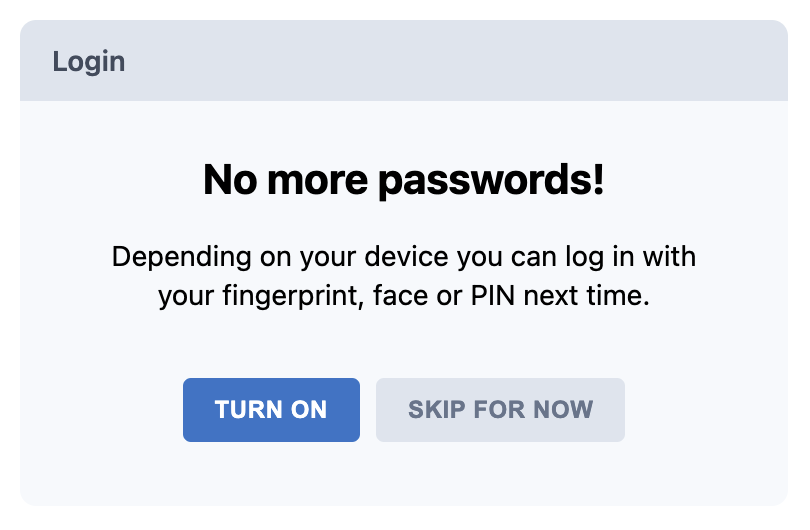
+Then asked if they want to enable WebAuthn:
+
+
+
+Then asked if they want to enable WebAuthn:
+
+ +
+If so, they are shown the browser's prompt to scan:
+
+
+
+If so, they are shown the browser's prompt to scan:
+
+ +
+If they skip, they just proceed into the site as usual. If they log out and back in, they will be prompted to enable WebAuthn again.
+
+**Authentication**
+
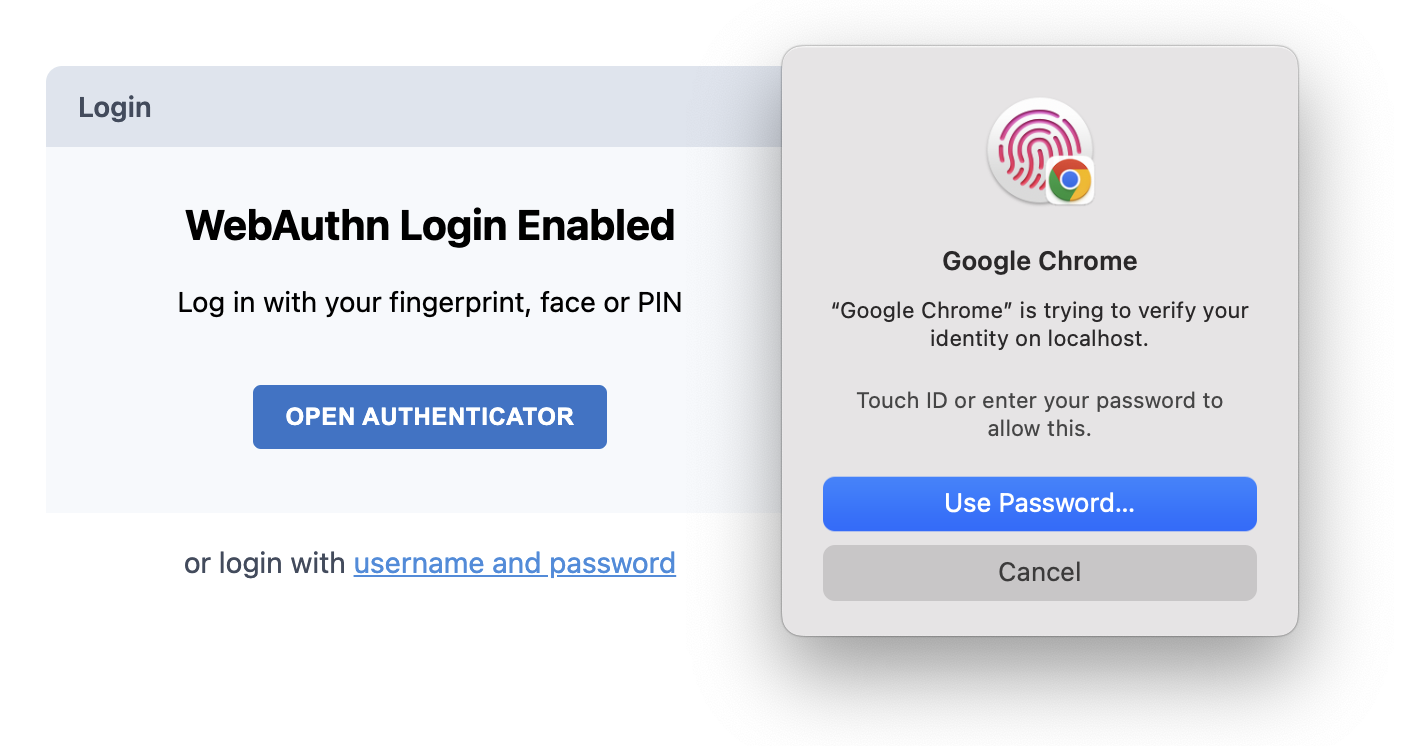
+When a device is already registered then it can be used to skip username/password login. The user is immediately shown the prompt to scan when they land on the login page (if the prompt doesn't show, or they mistakenly cancel it, they can click "Open Authenticator" to show the prompt again)
+
+
+
+If they skip, they just proceed into the site as usual. If they log out and back in, they will be prompted to enable WebAuthn again.
+
+**Authentication**
+
+When a device is already registered then it can be used to skip username/password login. The user is immediately shown the prompt to scan when they land on the login page (if the prompt doesn't show, or they mistakenly cancel it, they can click "Open Authenticator" to show the prompt again)
+
+ +
+They can also choose to go to use username/password credentials instead of their registered device.
+
+### How it Works
+
+The back and forth between the web and api sides works like this:
+
+**Registration**
+
+1. If the user selects to enable their device, a request is made to the server for "registration options" which is a JSON object containing details about the server and user (domain, username).
+2. Your app receives that data and then makes a browser API call that says to start the biometric reader with the received options
+3. The user scans their fingerprint/face and the browser API returns an ID representing this device, a public key and a few other fields for validation on the server
+4. The ID, public key, and additional details are sent to the server to be verified. Assuming the are, the device is saved to the database in a `UserCredential` table (you can change the name if you want). The server responds by placing a cookie on the user's browser with the device ID (a random string of letters and numbers)
+
+A similar process takes place when authenticating:
+
+**Authentication**
+
+1. If the cookie from the previous process is present, the web side knows that the user has a registered device so a request is made to the server to get "authentication options"
+2. The server looks up user who's credential ID is in the cookie and gets a list of all of the devices they have registered in the past. This is included along with the domain and username
+3. The web side receives the options from the server and a browser API call is made. The browser first checks to see if the list of devices from the server includes the current device. If so, it prompts the user to scan their fingerprint/face (if the device is not in the list, the user will directed back to username/password signup)
+4. The ID, public key, user details and a signature are sent to the server and checked to make sure the signature contains the expected data encrypted with the public key. If so, the regular login cookie is set (the same as if the user had used username/password login)
+
+In both cases, actual scanning and matching of devices is handled by the operating system: all we care about is that we are given a credential ID and a public key back from the device.
+
+### Browser Support
+
+WebAuthn is supported in the following browsers (as of July 2022):
+
+| OS | Browser | Authenticator |
+| ------- | ------- | ------------- |
+| macOS | Firefox | Yubikey Security Key NFC (USB), Yubikey 5Ci, SoloKey |
+| macOS | Chrome | Touch ID, Yubikey Security Key NFC (USB), Yubikey 5Ci, SoloKey |
+| iOS | All | Face ID, Touch ID, Yubikey Security Key NFC (NFC), Yubikey 5Ci |
+| Android | Chrome | Fingerprint Scanner, caBLE |
+| Android | Firefox | Screen PIN |
+
+#### iOS WebKit Browsers
+
+iOS Safari (and other iOS WebKit-based browsers) currently has a limitation where only a single `async` event can occur before asking to prompt the user for a WebAuthn interaction. In React, there are lots of `async` events floating around as you browse a site, which means the chances that the WebAuthn request is the first one is pretty slim.
+
+This means that if the login page is not the first page you land on, trying to authenticate will raise an error. Redwood catches this error and responds with the following prompt (which we know is not ideal, but better than the default message of "No available authenticator recognized any of the available credentials"):
+
+
+
+They can also choose to go to use username/password credentials instead of their registered device.
+
+### How it Works
+
+The back and forth between the web and api sides works like this:
+
+**Registration**
+
+1. If the user selects to enable their device, a request is made to the server for "registration options" which is a JSON object containing details about the server and user (domain, username).
+2. Your app receives that data and then makes a browser API call that says to start the biometric reader with the received options
+3. The user scans their fingerprint/face and the browser API returns an ID representing this device, a public key and a few other fields for validation on the server
+4. The ID, public key, and additional details are sent to the server to be verified. Assuming the are, the device is saved to the database in a `UserCredential` table (you can change the name if you want). The server responds by placing a cookie on the user's browser with the device ID (a random string of letters and numbers)
+
+A similar process takes place when authenticating:
+
+**Authentication**
+
+1. If the cookie from the previous process is present, the web side knows that the user has a registered device so a request is made to the server to get "authentication options"
+2. The server looks up user who's credential ID is in the cookie and gets a list of all of the devices they have registered in the past. This is included along with the domain and username
+3. The web side receives the options from the server and a browser API call is made. The browser first checks to see if the list of devices from the server includes the current device. If so, it prompts the user to scan their fingerprint/face (if the device is not in the list, the user will directed back to username/password signup)
+4. The ID, public key, user details and a signature are sent to the server and checked to make sure the signature contains the expected data encrypted with the public key. If so, the regular login cookie is set (the same as if the user had used username/password login)
+
+In both cases, actual scanning and matching of devices is handled by the operating system: all we care about is that we are given a credential ID and a public key back from the device.
+
+### Browser Support
+
+WebAuthn is supported in the following browsers (as of July 2022):
+
+| OS | Browser | Authenticator |
+| ------- | ------- | ------------- |
+| macOS | Firefox | Yubikey Security Key NFC (USB), Yubikey 5Ci, SoloKey |
+| macOS | Chrome | Touch ID, Yubikey Security Key NFC (USB), Yubikey 5Ci, SoloKey |
+| iOS | All | Face ID, Touch ID, Yubikey Security Key NFC (NFC), Yubikey 5Ci |
+| Android | Chrome | Fingerprint Scanner, caBLE |
+| Android | Firefox | Screen PIN |
+
+#### iOS WebKit Browsers
+
+iOS Safari (and other iOS WebKit-based browsers) currently has a limitation where only a single `async` event can occur before asking to prompt the user for a WebAuthn interaction. In React, there are lots of `async` events floating around as you browse a site, which means the chances that the WebAuthn request is the first one is pretty slim.
+
+This means that if the login page is not the first page you land on, trying to authenticate will raise an error. Redwood catches this error and responds with the following prompt (which we know is not ideal, but better than the default message of "No available authenticator recognized any of the available credentials"):
+
+ +
+You could catch this error on your login page and display your own custom error message, of course.
+
+So the workaround is to simply reload the page (guaranteeing that the WebAuthn request will be the first event fired off on the page) then the user is prompted and can login like normal. However, this reload needs to initiated by the user, it can't happen automatically in React (trust us, we already tried).
+
+:::caution Will it be fixed?
+
+Safari (and other browsers based on WebKit on iOS) have had this limitation for quite a while (and it used to be even [more harsh](https://groups.google.com/a/fidoalliance.org/g/fido-dev/c/pIs0DIajWVs/m/xeg0WjFkAQAJ) to the point that WebAuthn was functionally unusable) so it may never be rectified. Your best bet may be to just come up with a friendly message that makes it clear this isn't the user's problem, but just a current limitation of the browser ecosystem.
+
+:::
+
+### Configuration
+
+WebAuthn support requires a few updates to your codebase:
+
+1. Adding a `UserCredential` model
+2. Adding configuration options in `api/src/functions/auth.js`
+3. Adding a `client` to the `
+
+You could catch this error on your login page and display your own custom error message, of course.
+
+So the workaround is to simply reload the page (guaranteeing that the WebAuthn request will be the first event fired off on the page) then the user is prompted and can login like normal. However, this reload needs to initiated by the user, it can't happen automatically in React (trust us, we already tried).
+
+:::caution Will it be fixed?
+
+Safari (and other browsers based on WebKit on iOS) have had this limitation for quite a while (and it used to be even [more harsh](https://groups.google.com/a/fidoalliance.org/g/fido-dev/c/pIs0DIajWVs/m/xeg0WjFkAQAJ) to the point that WebAuthn was functionally unusable) so it may never be rectified. Your best bet may be to just come up with a friendly message that makes it clear this isn't the user's problem, but just a current limitation of the browser ecosystem.
+
+:::
+
+### Configuration
+
+WebAuthn support requires a few updates to your codebase:
+
+1. Adding a `UserCredential` model
+2. Adding configuration options in `api/src/functions/auth.js`
+3. Adding a `client` to the `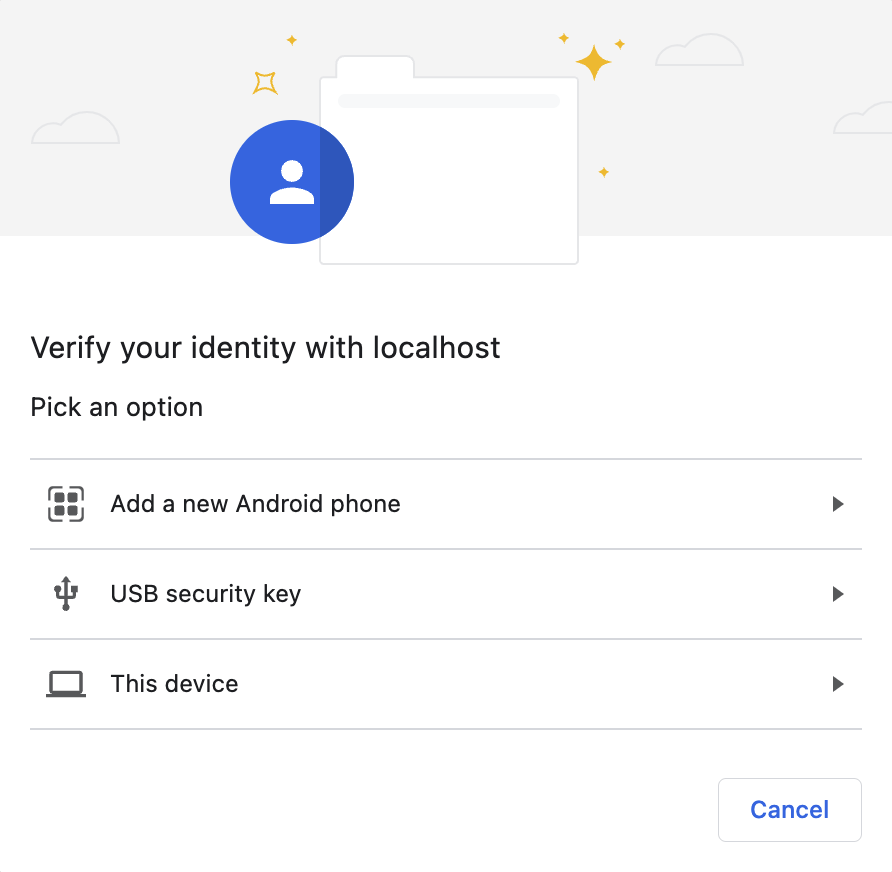 +
+If you pick "Add a new Android Phone" you're presented with a QR code:
+
+
+
+If you pick "Add a new Android Phone" you're presented with a QR code:
+
+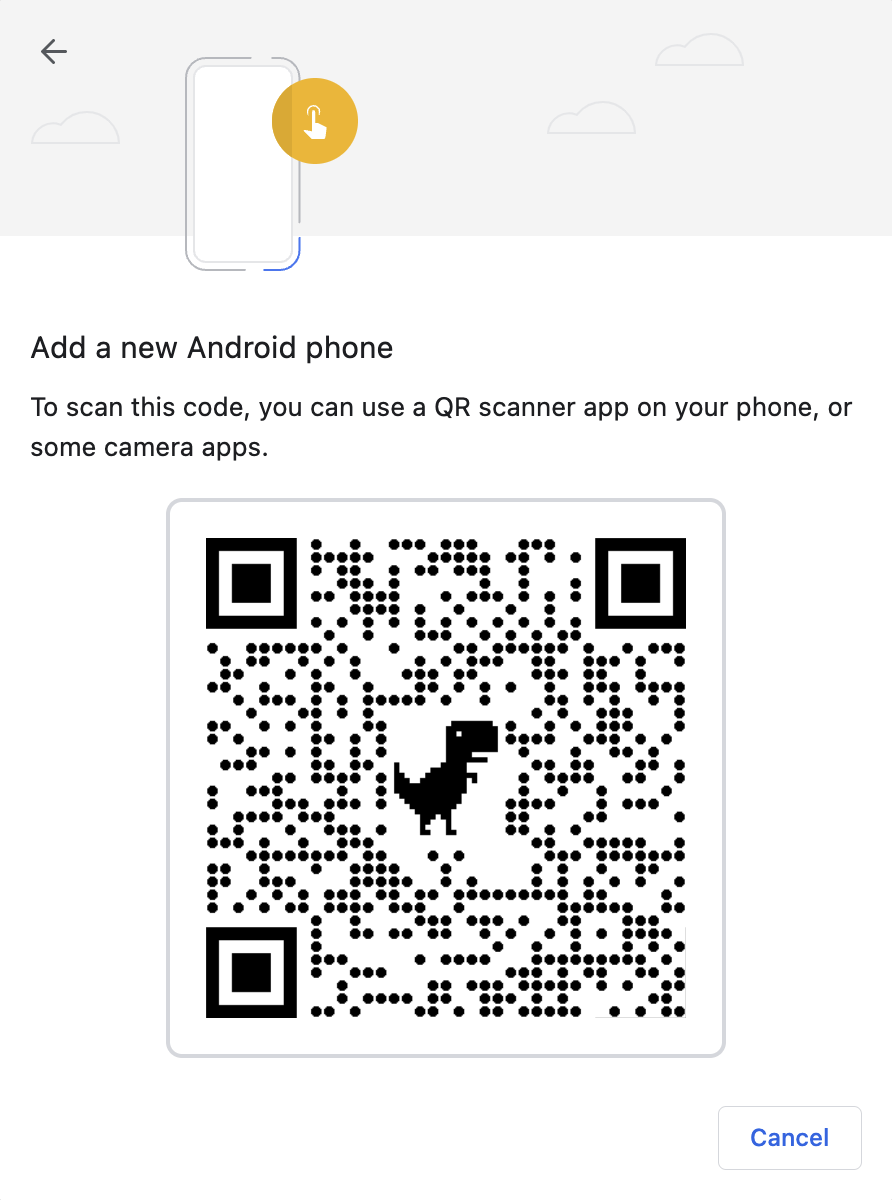 +
+If you pick "USB Security Key" you're given the chance to scan your fingerprint in a 3rd party USB device:
+
+
+
+If you pick "USB Security Key" you're given the chance to scan your fingerprint in a 3rd party USB device:
+
+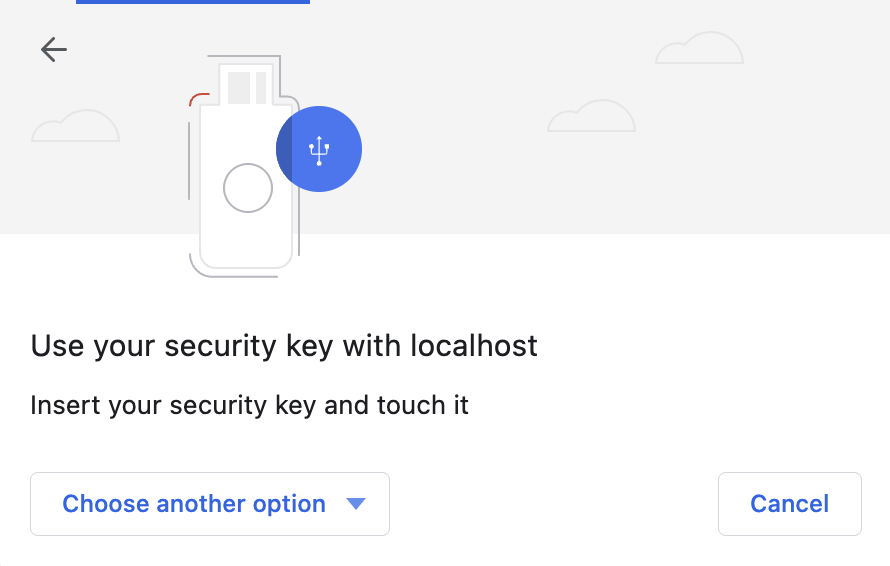 +
+And finally if you pick "This device" you're presented with the standard interface you'd get if used `platform` as your type:
+
+
+
+And finally if you pick "This device" you're presented with the standard interface you'd get if used `platform` as your type:
+
+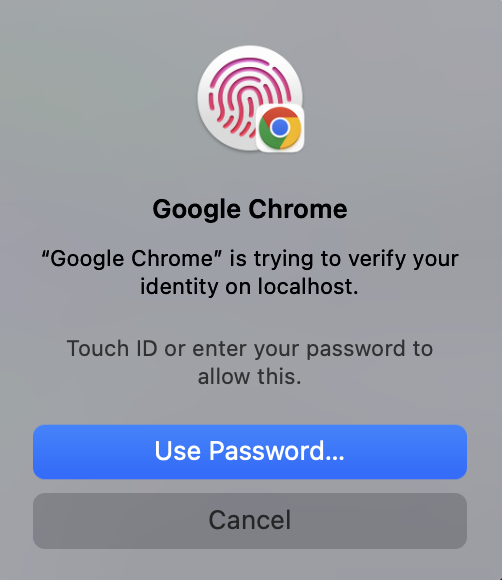 +
+You'll have to decide if this UX tradeoff is worth it for your customers, as it can be pretty confusing when first presented with all of these options when someone is just used to using TouchID or FaceID.
+
+#### **platform**
+
+The `platform` option provides the simplest UI and one that users with a TouchID or FaceID will be immediately familiar with:
+
+
+
+You'll have to decide if this UX tradeoff is worth it for your customers, as it can be pretty confusing when first presented with all of these options when someone is just used to using TouchID or FaceID.
+
+#### **platform**
+
+The `platform` option provides the simplest UI and one that users with a TouchID or FaceID will be immediately familiar with:
+
+ +
+Note that you can also fallback to use your user account password (on the computer itself) in addition to TouchID:
+
+
+
+Note that you can also fallback to use your user account password (on the computer itself) in addition to TouchID:
+
+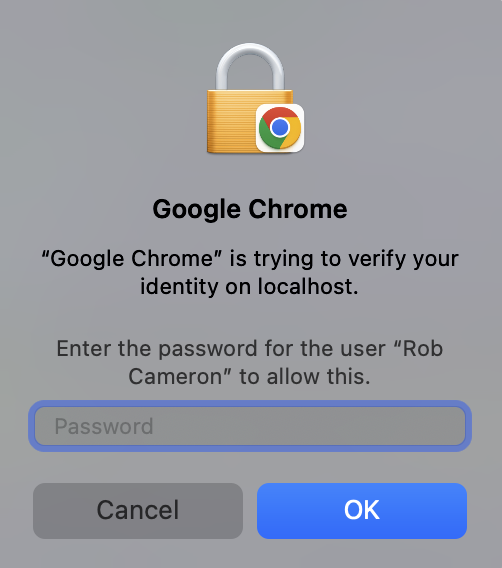 +
+Both the password and TouchID scan will count as the same device, so users can alternate between them if they want.
+
+#### **cross-platform**
+
+This interface is the same as `any`, but without the option to pick "This device":
+
+
+
+Both the password and TouchID scan will count as the same device, so users can alternate between them if they want.
+
+#### **cross-platform**
+
+This interface is the same as `any`, but without the option to pick "This device":
+
+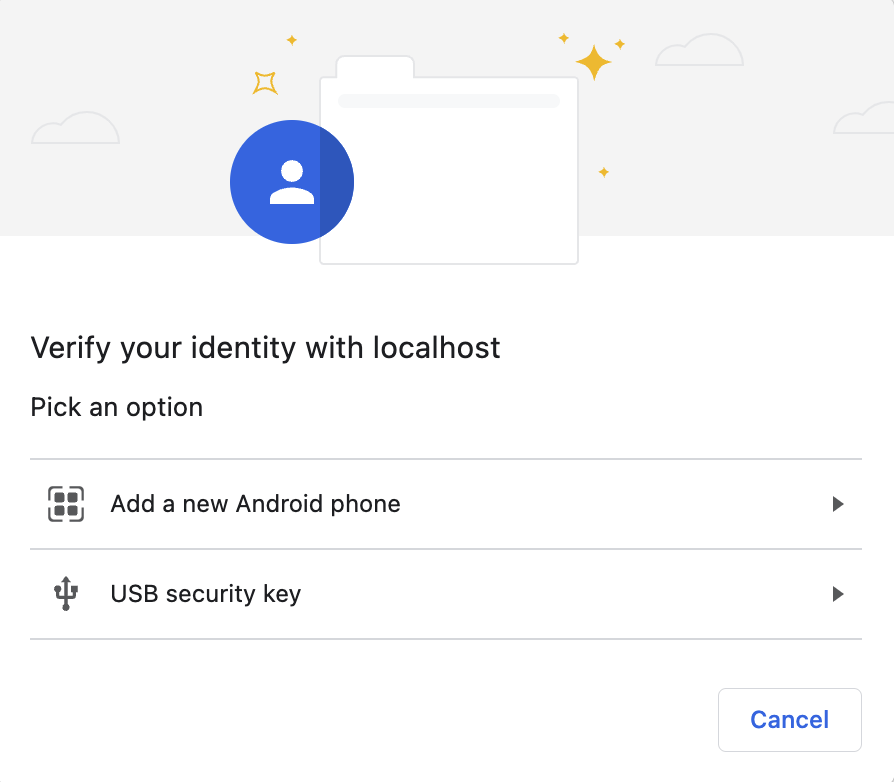 +
+So while the `any` option is the most flexible, it's also the most confusing to users. If you do plan on allowing any device, you may want to do a user-agent check and try to explain to users what the different options actually mean.
+
+The api-side is now ready to go.
+
+### App.js Updates
+
+If you generated your login/signup pages with `yarn rw g dbAuth --webAuthn` then all of these changes are in place and you can start using WebAuthn right away! Otherwise, read on.
+
+First you'll need to import the `WebAuthnClient` and give it to the `
+
+So while the `any` option is the most flexible, it's also the most confusing to users. If you do plan on allowing any device, you may want to do a user-agent check and try to explain to users what the different options actually mean.
+
+The api-side is now ready to go.
+
+### App.js Updates
+
+If you generated your login/signup pages with `yarn rw g dbAuth --webAuthn` then all of these changes are in place and you can start using WebAuthn right away! Otherwise, read on.
+
+First you'll need to import the `WebAuthnClient` and give it to the `Log in with your fingerprint, face or PIN
++ Depending on your device you can log in with your fingerprint, face or + PIN next time. +
+