You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
I have modified the static configuration file /etc/traefik/traefik.yml with the following, and yes, the traefik user can read the file. Logs don't show anything interesting.
I keep getting 500 internal server error on all my https backends. http ones work regularly
I'm using a single service for my backend, I just changed the url: http -> https. The 500 was coming from traefik 100%, I can curl the service directly.
Nothing is even reaching the backend service, the request fails when it reaches traefik. (I checked the backend service logs)
It seems that the rootCAs rule is not honored for some reason, because when setting:
serversTransport:
insecureSkipVerify: true
Everything works as it should, except the above flag is not production approved.
providers:
file:
filename: /etc/traefik/config.ymlwatch: trueserversTransport:
rootCAs:
- /etc/traefik/certs/self-signedCA.pem # also in system trust store and readable by traefik userinsecureSkipVerify: falseentryPoints:
web:
address: :80http:
redirections:
entryPoint:
to: web-securescheme: httpspermanent: trueweb-secure:
address: :443certificatesResolvers:
le:
...
redacted
...
If applicable, please paste the log output in DEBUG level
No response
The text was updated successfully, but these errors were encountered:
Welcome!
What did you do?
Trying to configure TLS on my backends by following this guide:
https://doc.traefik.io/traefik/routing/overview/#rootcas
I'm running traefik on debian 11 with systemd.
I have modified the static configuration file
/etc/traefik/traefik.ymlwith the following, and yes, the traefik user can read the file. Logs don't show anything interesting.I keep getting 500 internal server error on all my https backends. http ones work regularly
I'm using a single service for my backend, I just changed the url: http -> https. The 500 was coming from traefik 100%, I can curl the service directly.
Nothing is even reaching the backend service, the request fails when it reaches traefik. (I checked the backend service logs)
It seems that the rootCAs rule is not honored for some reason, because when setting:
Everything works as it should, except the above flag is not production approved.
Any thoughts? This seems like a bug...
What did you see instead?
My Desktop -> Traefik
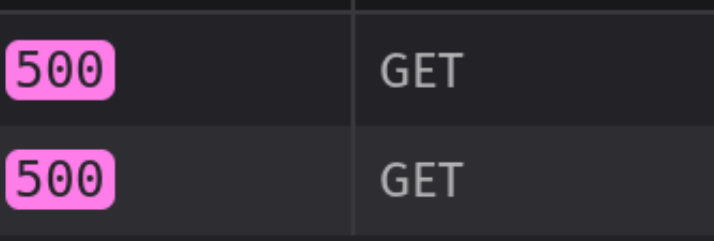
Traefik -> backend service:
What version of Traefik are you using?
Version: 2.9.5
Codename: banon
Go version: go1.19.3
Built: 2022-11-17T15:04:26Z
OS/Arch: linux/amd64
What is your environment & configuration?
config.yml:
traefik.yml:
If applicable, please paste the log output in DEBUG level
No response
The text was updated successfully, but these errors were encountered: