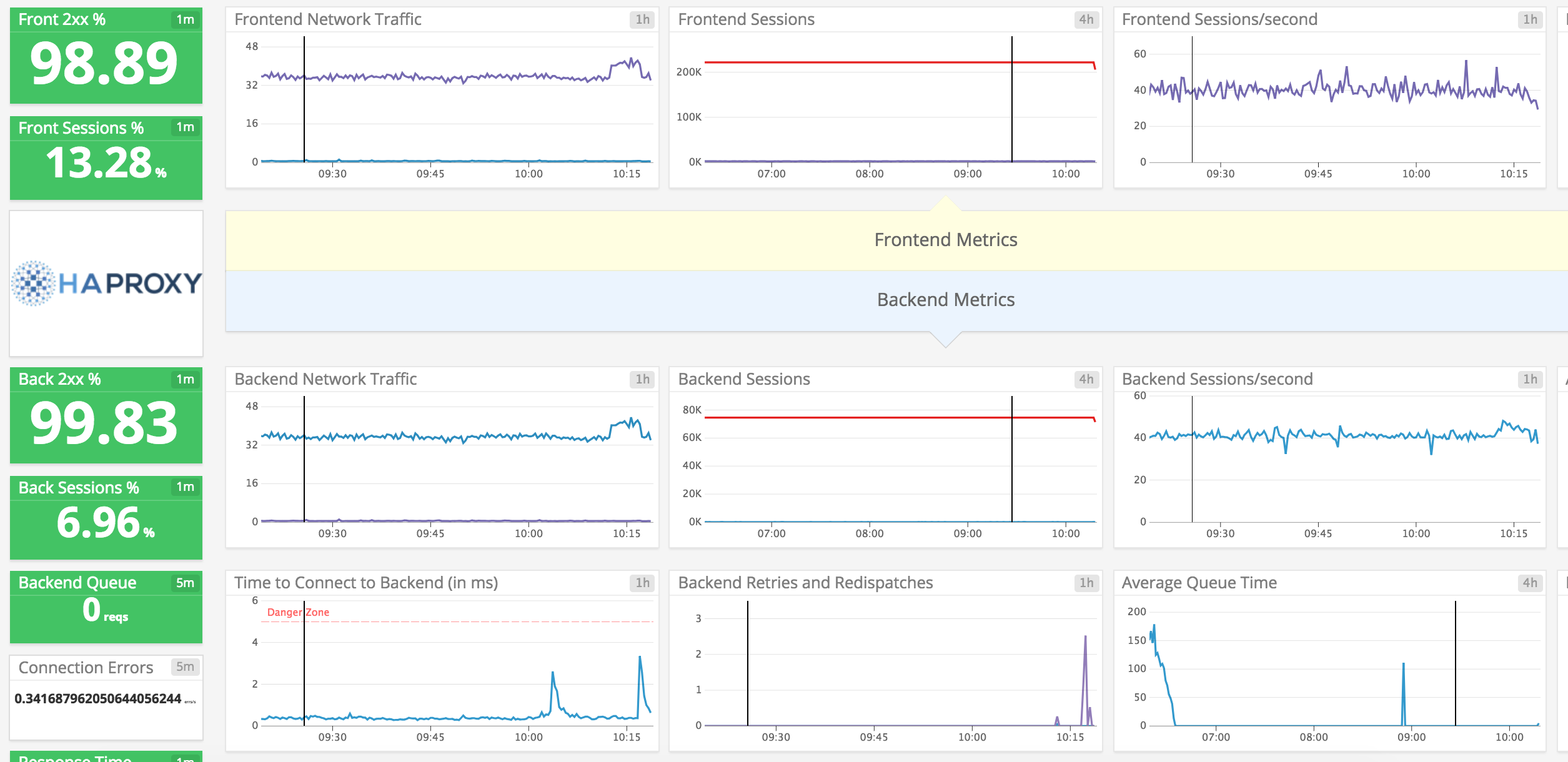
Capture HAProxy activity in Datadog to:
- Visualize HAProxy load-balancing performance.
- Know when a server goes down.
- Correlate the performance of HAProxy with the rest of your applications.
This integration can collect metrics from a Prometheus endpoint (recommended) or from a socket-based integration through the stats endpoint (deprecated). Using the Prometheus endpoint requires HAProxy version 2 (enterprise version 1.9rc1) or later.
When using the Prometheus endpoint, starting with version 4.0.0, this OpenMetrics-based integration has a latest mode (use_openmetrics: true) and a legacy mode (use_openmetrics: false and use_prometheus: true). To get all the most up-to-date features, Datadog recommends enabling the latest mode. For more information, see Latest and Legacy Versioning For OpenMetrics-based Integrations.
To use the socket-based integration, set both use_openmetrics and use_prometheus to false and follow the corresponding instructions on the Configuration section.
The use_openmetrics option uses the latest mode of OpenMetrics, which requires Agent v7.35 or later, or for you to enable Python 3 in Agent v6.35 or later for metric collection. For hosts that are unable to use Python 3 or are on Agent v7.34 or earlier, use the legacy mode of OpenMetrics or the socket-based legacy integration.
Metrics marked as [OpenMetrics V1] or [OpenMetrics V2] are only available using the corresponding mode of the HAProxy integration. Metrics marked as [OpenMetrics V1 and V2] are collected by both modes.
The HAProxy check is included in the Datadog Agent package, so you don't need to install anything else on your HAProxy server.
The recommended way to set up this integration is by enabling the Prometheus endpoint on HAProxy. This endpoint is built into HAProxy starting with version 2 (enterprise version 1.9rc1). If you are using an older version, consider setting up the HAProxy Prometheus exporter, or alternatively set up the legacy socket-based integration described in the next section.
To use the legacy OpenMetrics mode instead of the latest one, change the use_openmetrics option to use_prometheus, and change the openmetrics_endpoint option to prometheus_url. For more information, see the Prometheus and OpenMetrics metrics collection from a host documentation.
- Configure your
haproxy.confusing the official guide. - Restart HAProxy to enable the Prometheus endpoint.
To configure this check for an Agent running on a host:
-
Edit the
haproxy.d/conf.yamlfile in theconf.d/folder at the root of your Agent's configuration directory to start collecting your HAProxy metrics. See the sample haproxy.d/conf.yaml for all available configuration options.instances: ## @param use_openmetrics - boolean - optional - default: false ## Enable to preview the new version of the check which supports HAProxy version 2 or later ## or environments using the HAProxy exporter. ## ## OpenMetrics-related options take effect only when this is set to `true`. ## ## Uses the latest OpenMetrics V2 implementation for more features and better performance. ## Note: To see the configuration options for the OpenMetrics V1 implementation (Agent v7.33 or earlier), ## https://github.com/DataDog/integrations-core/blob/7.33.x/haproxy/datadog_checks/haproxy/data/conf.yaml.example # - use_openmetrics: true # Enables OpenMetrics V2 ## @param openmetrics_endpoint - string - optional ## The URL exposing metrics in the OpenMetrics format. # openmetrics_endpoint: http://localhost:<PORT>/metrics
To view configuration options for the legacy implementation, see the sample haproxy.d/conf.yaml file for Agent v7.34 or earlier.
For containerized environments, see the Autodiscovery Integration Templates for guidance on applying the parameters below.
| Parameter | Value |
|---|---|
<INTEGRATION_NAME> |
haproxy |
<INIT_CONFIG> |
blank or {} |
<INSTANCE_CONFIG> |
{"openmetrics_endpoint": "http://%%host%%:<PORT>/metrics", "use_openmetrics": "true"} |
Add pod annotations under .spec.template.metadata for a Deployment:
apiVersion: apps/v1
kind: Deployment
metadata:
name: haproxy
spec:
template:
metadata:
labels:
name: haproxy
annotations:
ad.datadoghq.com/haproxy.check_names: '["haproxy"]'
ad.datadoghq.com/haproxy.init_configs: '[{}]'
ad.datadoghq.com/haproxy.instances: |
[
{
"openmetrics_endpoint": "http://%%host%%:<PORT>/metrics", "use_openmetrics": "true"
}
]
spec:
containers:
- name: haproxyThis configuration strategy is provided as a reference for legacy users. If you are setting up the integration for the first time, consider using the Prometheus-based strategy described in the previous section.
The Agent collects metrics using a stats endpoint:
-
Configure one in your
haproxy.conf:listen stats # Define a listen section called "stats" bind :9000 # Listen on localhost:9000 mode http stats enable # Enable stats page stats hide-version # Hide HAProxy version stats realm Haproxy\ Statistics # Title text for popup window stats uri /haproxy_stats # Stats URI stats auth Username:Password # Authentication credentials
To configure this check for an Agent running on a host:
Edit the haproxy.d/conf.yaml file, in the conf.d/ folder at the root of your Agent's configuration directory to start collecting your HAProxy metrics and logs. See the sample haproxy.d/conf.yaml for all available configuration options.
-
Add this configuration block to your
haproxy.d/conf.yamlfile to start gathering your HAProxy Metrics:init_config: instances: ## @param url - string - required ## Haproxy URL to connect to gather metrics. ## Set the according <USERNAME> and <PASSWORD> or use directly a unix stats ## or admin socket: unix:///var/run/haproxy.sock # - url: http://localhost/admin?stats
By default Haproxy sends logs over UDP to port 514. The Agent can listen for these logs on this port, however, binding to a port number under 1024 requires elevated permissions. Follow the instructions below to set this up. Alternatively, you can use a different port and skip step 3.
-
Collecting logs is disabled by default in the Datadog Agent, enable it in your
datadog.yamlfile:logs_enabled: true
-
Add this configuration block to your
haproxy.d/conf.yamlfile to start collecting your Haproxy Logs:logs: - type: udp port: 514 service: <SERVICE_NAME> source: haproxy
Change the
serviceparameter value and configure it for your environment. See the sample haproxy.d/conf.yaml for all available configuration options. -
Grant access to port 514 using the
setcapcommand:sudo setcap CAP_NET_BIND_SERVICE=+ep /opt/datadog-agent/bin/agent/agent
Verify the setup is correct by running the
getcapcommand:sudo getcap /opt/datadog-agent/bin/agent/agent
With the expected output:
/opt/datadog-agent/bin/agent/agent = cap_net_bind_service+ep
Note: Re-run this
setcapcommand every time you upgrade the Agent.
To configure this check for an Agent running on a container:
Set Autodiscovery Integrations Templates as Docker labels on your application container:
LABEL "com.datadoghq.ad.check_names"='["haproxy"]'
LABEL "com.datadoghq.ad.init_configs"='[{}]'
LABEL "com.datadoghq.ad.instances"='[{"url": "https://%%host%%/admin?stats"}]'Collecting logs is disabled by default in the Datadog Agent. To enable it, see Docker Log Collection.
Then, set Log Integrations as Docker labels:
LABEL "com.datadoghq.ad.logs"='[{"source":"haproxy","service":"<SERVICE_NAME>"}]'To configure this check for an Agent running on Kubernetes:
Set Autodiscovery Integrations Templates as pod annotations on your application container. Aside from this, templates can also be configured with a file, a configmap, or a key-value store.
Annotations v1 (for Datadog Agent v7.36 or earlier)
apiVersion: v1
kind: Pod
metadata:
name: haproxy
annotations:
ad.datadoghq.com/haproxy.check_names: '["haproxy"]'
ad.datadoghq.com/haproxy.init_configs: '[{}]'
ad.datadoghq.com/haproxy.instances: |
[
{
"url": "https://%%host%%/admin?stats"
}
]
spec:
containers:
- name: haproxyAnnotations v2 (for Datadog Agent v7.36 or later)
apiVersion: v1
kind: Pod
metadata:
name: haproxy
annotations:
ad.datadoghq.com/haproxy.checks: |
{
"haproxy": {
"init_config": {},
"instances": [
{
"url": "https://%%host%%/admin?stats"
}
]
}
}
spec:
containers:
- name: haproxyAvailable for Agent versions >6.0
Collecting logs is disabled by default in the Datadog Agent. To enable it, see Kubernetes Log Collection.
Then, set Log Integrations as pod annotations. This can also be configured with a file, a configmap, or a key-value store.
Annotations v1/v2
apiVersion: v1
kind: Pod
metadata:
name: haproxy
annotations:
ad.datadoghq.com/haproxy.logs: '[{"source":"haproxy","service":"<SERVICE_NAME>"}]'
spec:
containers:
- name: haproxyTo configure this check for an Agent running on ECS:
Set Autodiscovery Integrations Templates as Docker labels on your application container:
{
"containerDefinitions": [{
"name": "haproxy",
"image": "haproxy:latest",
"dockerLabels": {
"com.datadoghq.ad.check_names": "[\"haproxy\"]",
"com.datadoghq.ad.init_configs": "[{}]",
"com.datadoghq.ad.instances": "[{\"url\": \"https://%%host%%/admin?stats\"}]"
}
}]
}Available for Agent versions 6.0 or later
Collecting logs is disabled by default in the Datadog Agent. To enable it, see ECS Log Collection.
Then, set Log Integrations as Docker labels:
{
"containerDefinitions": [{
"name": "haproxy",
"image": "haproxy:latest",
"dockerLabels": {
"com.datadoghq.ad.logs": "[{\"source\":\"haproxy\",\"service\":\"<SERVICE_NAME>\"}]"
}
}]
}Run the Agent's status subcommand and look for haproxy under the Checks section.
See metadata.csv for a list of metrics provided by this integration.
The HAProxy check does not include any events.
See service_checks.json for a list of service checks provided by this integration.
On systems with syslog, if the Agent is listening for HAProxy logs on port 514, the following error can appear in the Agent logs:
Can't start UDP forwarder on port 514: listen udp :514: bind: address already in use.
This is happening because, by default, syslog is listening on port 514. To resolve this error, syslog can be disabled, or HAProxy can be configured to forward logs to port 514 and another port the Agent is listening for logs on. The port the Agent listens on can be defined in the haproxy.d/conf.yaml file here.
Need help? Contact Datadog support.