The Terraform modules that power the TNT Architecture and Super Router
projects for "scaling" VPCs and TGWs in AWS have been published to the Terraform Cloud public registry at v1.0.0 and are used in this demo! They can be composed together to build a decentralized hub spoke topology with automatic peering and routing for cross-region and intra-region VPC and TGW connectivity.
Related articles:
- Original Blog Post in Super Powered, Super Sharp, Super Router!
- Fresh new decentralized design in $init super refactor.
- New features means new steez in Slappin chrome on the WIP!
Demo:
- Pre-requisite: AWS account, may need to increase your VPC and or TGW quota for each us-east-1 and us-west-2 depending on how many you currently have. This demo will be creating 4 more VPCs in each region (8 total) and 3 TGWs in each region (6 total)
- Super Router module provides both intra-region and cross-region peering and routing for Centralized Routers and Tiered VPCs (same AWS account only, no cross account).
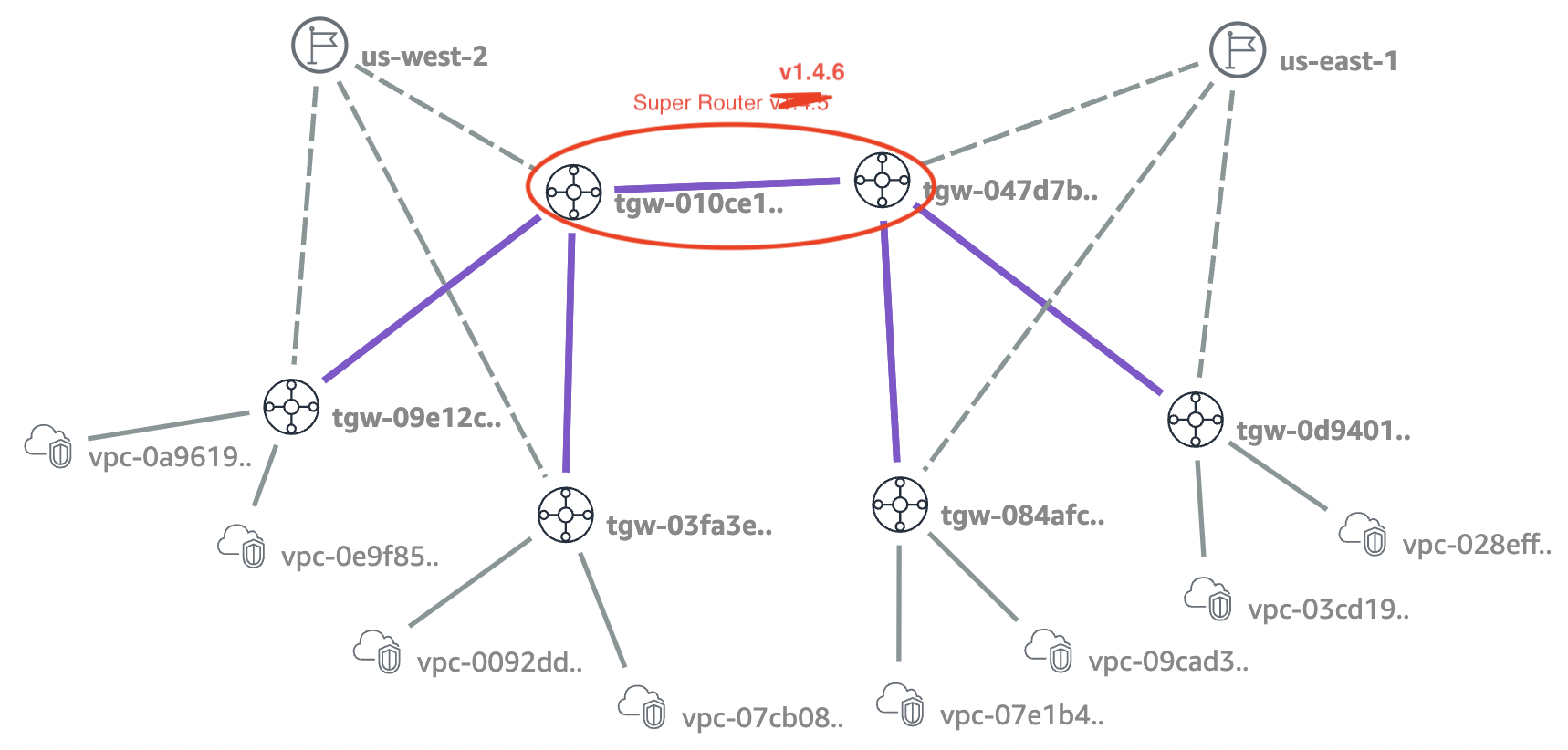
The resulting architecture is a decentralized hub spoke topology:
It begins:
terraform init
Apply Tiered-VPCs (must exist before Centralized Routers):
terraform apply -target module.vpcs_usw2 -target module.vpcs_another_usw2 -target module.vpcs_use1 -target module.vpcs_another_use1
Apply Centralized Routers (must exist before Super Router) and Intra VPC Security Group Rules:
terraform apply -target module.centralized_routers_usw2 -target module.centralized_routers_use1 -target module.intra_vpc_security_group_rules_usw2 -target module.intra_vpc_security_group_rules_use1
Apply Super Router and Super Intra VPC Security Group Rules:
terraform apply -target module.super_router_usw2_to_use1 -target module.super_intra_vpc_security_group_rules_usw2_to_use1
The Super Router is now complete!
Note: If we were using this in Terraform Cloud then it would be best for each of the module applys above to be in their own separate networking workspace with triggers. For example, if a VPC or AZ is added in it's own VPC workspace then apply and trigger the centralized router workspace to build routes, then trigger a workspace to add to Super Router.)
Routing and peering Validation with AWS Route Analyzer:
- Go to AWS Network Manager (free to use)
- Create global network ->
next- UNCHECK
Add core network in your global networkor you will be billed extra ->next
- UNCHECK
- Select new global network -> go to
Transit Gateways->Register Transit Gateway-> Select TGWs ->Register Transit Gateway-> wait until all states sayAvailable - Go to
Transit gateway network->Route Analyzer- Intra-Region Test 1 (usw2c to usw2a)
- Source:
- Transit Gateway: Choose
TEST-centralized-router-thunderbird-usw2 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-general1-usw2 <-> TEST-centralized-router-thunderbird-usw2(VPC) - IP Address:
192.168.16.7(experiment1private subnet)
- Transit Gateway: Choose
- Destination:
- Transit Gateway: Choose
TEST-centralized-router-storm-usw2 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-cicd1-usw2 <-> TEST-centralized-router-storm-usw2(VPC) - IP Address:
172.16.6.9(random1public subnet)
- Transit Gateway: Choose
- Select
Run Route Analysis- Forward and Return Paths should both have a
Connectedstatus.
- Forward and Return Paths should both have a
- Source:
- Intra-Region Test 2 (use1c to use1c)
- Source:
- Transit Gateway: Choose
TEST-centralized-router-bishop-use1 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-infra2-use1 <-> TEST-centralized-router-bishop-use1(VPC) - IP Address:
192.168.32.8(db1private subnet)
- Transit Gateway: Choose
- Destination:
- Transit Gateway: Choose
TEST-centralized-router-wolverine-use1 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-app2-use1 <-> TEST-centralized-router-wolverine-use1(VPC) - IP Address:
10.0.0.4(cluster1private subnet)
- Transit Gateway: Choose
- Select
Run Route Analysis- Forward and Return Paths should both have a
Connectedstatus.
- Forward and Return Paths should both have a
- Source:
- Cross-Region Test 1 (usw2a to use1c)
- Source:
- Transit Gateway: Choose
TEST-centralized-router-thunderbird-usw2 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-app1-usw2 <-> TEST-centralized-router-thunderbird-usw2(VPC) - IP Address:
10.0.19.5(random1public subnet)
- Transit Gateway: Choose
- Destination:
- Transit Gateway: Choose
TEST-centralized-router-wolverine-use1 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-general2-use1 <-> TEST-centralized-router-wolverine-use1(VPC) - IP Address:
192.168.11.6(experiment2private subnet)
- Transit Gateway: Choose
- Select
Run Route Analysis- Forward and Return Paths should both have a
Connectedstatus.
- Forward and Return Paths should both have a
- Source:
- Cross-Region Test 2 (use1a to usw2c)
- Source:
- Transit Gateway: Choose
TEST-centralized-router-bishop-use1 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-cicd2-use1 <-> TEST-centralized-router-bishop-use1(VPC) - IP Address:
10.0.32.3(jenkins1private subnet)
- Transit Gateway: Choose
- Destination:
- Transit Gateway: Choose
TEST-centralized-router-storm-usw2 - Transit Gateway Attachment: Choose
TEST-tiered-vpc-infra1-usw2 <-> TEST-centralized-router-storm-usw2(VPC) - IP Address:
172.16.16.6(jenkins2private subnet)
- Transit Gateway: Choose
- Select
Run Route Analysis- Forward and Return Paths should both have a
Connectedstatus.
- Forward and Return Paths should both have a
- Source:
- Intra-Region Test 1 (usw2c to usw2a)
- Create global network ->
Several other routes can be validated, try them out!
Tear down:
terraform destroy(long delay to get to yes or no prompt, be patient)