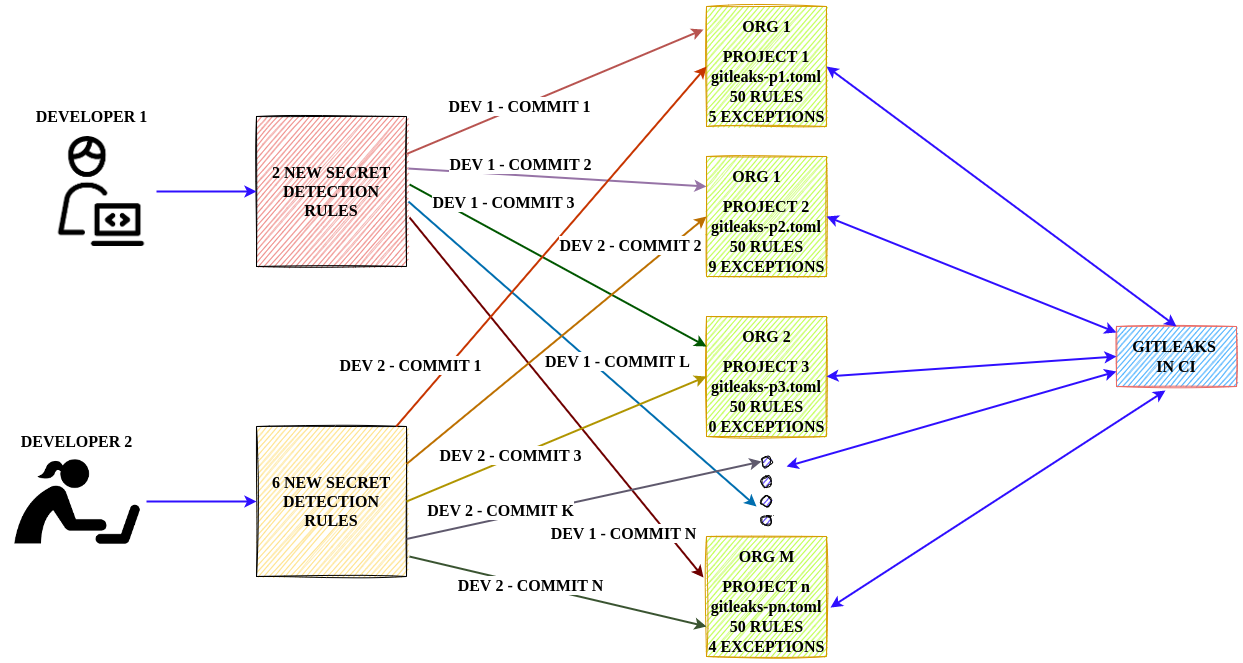
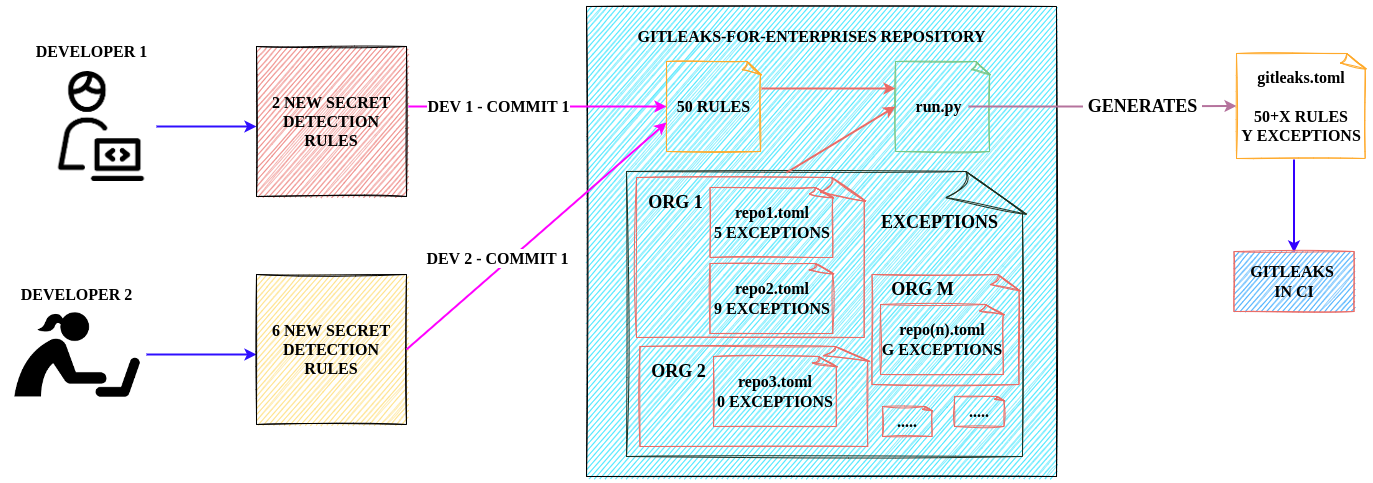
Gitleaks is customized for use across multiple projects/enterprises. This project allows you to have a centralized detection rule management.
When we use Gitleaks with "n" number of projects, the architecture will be similar to below.
- The
descriptionfield inbase.tomlis mandatory & it should start with "Rule: " - The
idfield in[[rules]]inallowlist.tomlis mandatory & it should be an integer - DO NOT edit
idfield inbase.toml. All the whitelisting/allowlist id are dependent on it
# Sample rule structure
[[rules]]
description = "Rule 99: New rule description here"
regex = '''newrule-regex-here'''
tags = ["rule-tag-1", "rule-tag-2"]- Except
commits, all the below fields areregexmatches. - The
idfield in[[rules]]is mandatory & it should be an integer - Folder structure
- rewanthtammana > gitleaks-demo-repo > allowlist.toml
- rewanthtammana > another-repo > allowlist.toml
# Rule specific allow lists
# Sample allowlist structure
[[rules]]
id = "99"
[rules.allowlist]
commits = ["commit-id-here"]
files = ['''keys/eGuardKey.id_dsa$''']- By default all detection rules are in in
base.toml - Save your allowlist rules in
allowlist/$USERNAME/$REPONAME/allowlist.toml python run.py -a <allowlist-file-path> > gitleaks.toml- Combines your repo specificallowlist.toml&base.tomlto generategitleaks.tomlfile- Use the above generated
gitleaks.tomlas gitleaks repo scanning configuration file
python3 run.py -a allowlist/$USERNAME/$REPONAME/allowlist.toml > gitleaks.toml
gitleaks detect -c ./gitleaks.toml --source /path/to/repo -vFor further usage refer to, https://github.com/zricethezav/gitleaks
You can add new rules to base.toml file. It's parent file.
[[rules]]
description = "Rule <id here>: AWS Secret Key"
regex = '''(?i)aws(.{0,20})?(?-i)['\"][0-9a-zA-Z\/+]{40}['\"]'''
tags = ["key", "AWS"]pip install -r requirements.txt
pyinstaller run.py --onefile
./dist/run #This binary can also be used