diff --git a/.github/sync.yml b/.github/sync.yml
new file mode 100644
index 00000000..3b2680ea
--- /dev/null
+++ b/.github/sync.yml
@@ -0,0 +1,19 @@
+Permify/permify-pro:
+ - source: go.mod
+ dest: go.mod
+ - source: go.sum
+ dest: go.sum
+ - source: cmd/
+ dest: cmd/
+ - source: integration-test/
+ dest: integration-test/
+ - source: internal/
+ dest: internal/
+ exclude: |
+ info.go
+ - source: pkg/
+ dest: pkg/
+ - source: proto/
+ dest: proto/
+ - source: tools/
+ dest: tools/
\ No newline at end of file
diff --git a/.github/workflows/codeql-analysis.yml b/.github/workflows/codeql-analysis.yml
index bd1549da..a12f9f35 100644
--- a/.github/workflows/codeql-analysis.yml
+++ b/.github/workflows/codeql-analysis.yml
@@ -50,7 +50,7 @@ jobs:
# Initializes the CodeQL tools for scanning.
- name: Initialize CodeQL
- uses: github/codeql-action/init@e8893c57a1f3a2b659b6b55564fdfdbbd2982911 # v3.24.0
+ uses: github/codeql-action/init@05963f47d870e2cb19a537396c1f668a348c7d8f # v3.24.8
with:
languages: ${{ matrix.language }}
# If you wish to specify custom queries, you can do so here or in a config file.
@@ -64,7 +64,7 @@ jobs:
# Autobuild attempts to build any compiled languages (C/C++, C#, or Java).
# If this step fails, then you should remove it and run the build manually (see below)
- name: Autobuild
- uses: github/codeql-action/autobuild@e8893c57a1f3a2b659b6b55564fdfdbbd2982911 # v3.24.0
+ uses: github/codeql-action/autobuild@05963f47d870e2cb19a537396c1f668a348c7d8f # v3.24.8
# ℹ️ Command-line programs to run using the OS shell.
# 📚 See https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions#jobsjob_idstepsrun
@@ -77,6 +77,6 @@ jobs:
# ./location_of_script_within_repo/buildscript.sh
- name: Perform CodeQL Analysis
- uses: github/codeql-action/analyze@e8893c57a1f3a2b659b6b55564fdfdbbd2982911 # v3.24.0
+ uses: github/codeql-action/analyze@05963f47d870e2cb19a537396c1f668a348c7d8f # v3.24.8
with:
category: "/language:${{matrix.language}}"
diff --git a/.github/workflows/dependency-review.yml b/.github/workflows/dependency-review.yml
index fc3a42df..8ae22531 100644
--- a/.github/workflows/dependency-review.yml
+++ b/.github/workflows/dependency-review.yml
@@ -24,4 +24,4 @@ jobs:
- name: 'Checkout Repository'
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
- name: 'Dependency Review'
- uses: actions/dependency-review-action@4901385134134e04cec5fbe5ddfe3b2c5bd5d976 # v4.0.0
+ uses: actions/dependency-review-action@0fa40c3c10055986a88de3baa0d6ec17c5a894b3 # v4.2.3
diff --git a/.github/workflows/docs.yaml b/.github/workflows/docs.yaml
deleted file mode 100644
index 056c145d..00000000
--- a/.github/workflows/docs.yaml
+++ /dev/null
@@ -1,58 +0,0 @@
-name: Publish Docs
-
-on:
- push:
- branches:
- - master
- paths:
- - 'docs/**'
- workflow_dispatch:
-
-jobs:
- build-and-deploy:
- runs-on: ubuntu-latest
-
- steps:
- - name: Harden Runner
- uses: step-security/harden-runner@63c24ba6bd7ba022e95695ff85de572c04a18142 # v2.7.0
- with:
- egress-policy: audit
-
- - name: Checkout Repository
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
-
- - name: Set up Node.js
- uses: actions/setup-node@60edb5dd545a775178f52524783378180af0d1f8 # v4.0.2
- with:
- node-version: '16'
-
- - name: Install Dependencies
- run: |
- cd docs
- yarn install
-
- - name: Build Project
- run: |
- cd docs
- yarn build
-
- - name: Deploy to S3
- uses: jakejarvis/s3-sync-action@7ed8b112447abb09f1da74f3466e4194fc7a6311 # master
- with:
- args: --acl public-read --follow-symlinks --delete
- env:
- AWS_S3_BUCKET: ${{ secrets.AWS_DOCS_S3_BUCKET }}
- AWS_ACCESS_KEY_ID: ${{ secrets.AWS_ACCESS_KEY_ID }}
- AWS_SECRET_ACCESS_KEY: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
- AWS_REGION: 'us-east-1'
- SOURCE_DIR: 'docs/build/'
- DEST_DIR: ''
-
- - name: Invalidate CloudFront Distribution
- uses: chetan/invalidate-cloudfront-action@fce6f6f546fae2e9fe55f3bd1411063a908f2557 # master
- env:
- DISTRIBUTION: ${{ secrets.DISTRIBUTION }}
- PATHS: '/*'
- AWS_REGION: 'us-east-1'
- AWS_ACCESS_KEY_ID: ${{ secrets.AWS_ACCESS_KEY_ID }}
- AWS_SECRET_ACCESS_KEY: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
diff --git a/.github/workflows/nightly.yaml b/.github/workflows/nightly.yaml
index 200224b7..96e6575a 100644
--- a/.github/workflows/nightly.yaml
+++ b/.github/workflows/nightly.yaml
@@ -25,20 +25,20 @@ jobs:
with:
go-version: ~1.21.3
- name: Log in to GHCR
- uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
+ uses: docker/login-action@e92390c5fb421da1463c202d546fed0ec5c39f20 # v3.1.0
with:
registry: ghcr.io
username: ${{ github.actor }}
password: ${{ secrets.GH_TOKEN }}
- name: Login to dockerhub
- uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
+ uses: docker/login-action@e92390c5fb421da1463c202d546fed0ec5c39f20 # v3.1.0
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Set up QEMU
uses: docker/setup-qemu-action@68827325e0b33c7199eb31dd4e31fbe9023e06e3 # v3.0.0
- name : Set up Docker Buildx
- uses: docker/setup-buildx-action@f95db51fddba0c2d1ec667646a06c2ce06100226 # v3.0.0
+ uses: docker/setup-buildx-action@2b51285047da1547ffb1b2203d8be4c0af6b1f20 # v3.2.0
- name: Run GoReleaser
uses: goreleaser/goreleaser-action@7ec5c2b0c6cdda6e8bbb49444bc797dd33d74dd8 # v5.0.0
with:
diff --git a/.github/workflows/release.yml b/.github/workflows/release.yml
index c4f45f58..61cc6a35 100644
--- a/.github/workflows/release.yml
+++ b/.github/workflows/release.yml
@@ -25,20 +25,20 @@ jobs:
with:
go-version: ~1.21.3
- name: Log in to GHCR
- uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
+ uses: docker/login-action@e92390c5fb421da1463c202d546fed0ec5c39f20 # v3.1.0
with:
registry: ghcr.io
username: ${{ github.actor }}
password: ${{ secrets.GH_TOKEN }}
- name: Login to dockerhub
- uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
+ uses: docker/login-action@e92390c5fb421da1463c202d546fed0ec5c39f20 # v3.1.0
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Set up QEMU
uses: docker/setup-qemu-action@68827325e0b33c7199eb31dd4e31fbe9023e06e3 # v3.0.0
- name: Set up Docker Buildx
- uses: docker/setup-buildx-action@f95db51fddba0c2d1ec667646a06c2ce06100226 # v3.0.0
+ uses: docker/setup-buildx-action@2b51285047da1547ffb1b2203d8be4c0af6b1f20 # v3.2.0
- name: Run GoReleaser
uses: goreleaser/goreleaser-action@7ec5c2b0c6cdda6e8bbb49444bc797dd33d74dd8 # v5.0.0
with:
diff --git a/.github/workflows/scorecard.yml b/.github/workflows/scorecard.yml
index e4f1134d..8890c1e4 100644
--- a/.github/workflows/scorecard.yml
+++ b/.github/workflows/scorecard.yml
@@ -73,6 +73,6 @@ jobs:
# Upload the results to GitHub's code scanning dashboard.
- name: "Upload to code-scanning"
- uses: github/codeql-action/upload-sarif@e8893c57a1f3a2b659b6b55564fdfdbbd2982911 # v3.24.0
+ uses: github/codeql-action/upload-sarif@05963f47d870e2cb19a537396c1f668a348c7d8f # v3.24.8
with:
sarif_file: results.sarif
diff --git a/.github/workflows/sdk-generator.yml b/.github/workflows/sdk-generator.yml
new file mode 100644
index 00000000..25579a0a
--- /dev/null
+++ b/.github/workflows/sdk-generator.yml
@@ -0,0 +1,50 @@
+name: Generate Client SDKs from OpenAPI
+
+on:
+ push:
+ branches:
+ - master
+ pull_request:
+ branches:
+ - master
+ workflow_dispatch:
+
+jobs:
+ build:
+ runs-on: ubuntu-latest
+ env:
+ GITHUB_TOKEN: ${{ secrets.SDK_GH_TOKEN }}
+ ORG_NAME: permify
+ SWAGGER_PATH: docs/api-reference/apidocs.swagger.json
+
+ strategy:
+ matrix:
+ language: [python, javascript]
+
+ steps:
+ - name: Harden Runner
+ uses: step-security/harden-runner@63c24ba6bd7ba022e95695ff85de572c04a18142 # v2.7.0
+ with:
+ egress-policy: audit
+
+ - name: Checkout repository
+ uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
+
+ - name: Generate Python Client
+ uses: openapi-generators/openapitools-generator-action@d27bd4385276f24d23ea92157dfdf4c47be4bbca # v1
+ with:
+ generator: ${{ matrix.language }}
+ openapi-file: ${SWAGGER_PATH}
+ command-args: -o permify-client --git-user-id ${ORG_NAME} --git-repo-id permify-${{ matrix.language }} --api-package permify --package-name permify
+
+ - name: Push SDK to GitHub
+ run: |
+ git config --global user.name 'GitHub Actions Bot'
+ git config --global user.email '<>'
+ git clone https://${GITHUB_TOKEN}@github.com/${ORG_NAME}/permify-${{ matrix.language }}.git temp
+ cp -r permify-client/* temp/
+ cd temp
+ git add .
+ git diff-index --quiet HEAD || git commit -m "Update ${{ matrix.language }} SDK from OpenAPI changes"
+ git push https://${GITHUB_TOKEN}@github.com/${ORG_NAME}/permify-${{ matrix.language }}.git main --force
+ rm -rf permify-client
diff --git a/.github/workflows/sync.yml b/.github/workflows/sync.yml
new file mode 100644
index 00000000..9d5b3b4d
--- /dev/null
+++ b/.github/workflows/sync.yml
@@ -0,0 +1,21 @@
+name: Sync to Permify Pro
+on:
+ push:
+ branches:
+ - master
+ workflow_dispatch:
+jobs:
+ sync:
+ runs-on: ubuntu-latest
+ steps:
+ - name: Harden Runner
+ uses: step-security/harden-runner@63c24ba6bd7ba022e95695ff85de572c04a18142 # v2.7.0
+ with:
+ egress-policy: audit
+
+ - name: Checkout Repository
+ uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # master
+ - name: Run GitHub File Sync
+ uses: BetaHuhn/repo-file-sync-action@3023dac7ce66c18b119e2012348437eadeaea116 # v1.21.0
+ with:
+ GH_PAT: ${{ secrets.GH_TOKEN }}
\ No newline at end of file
diff --git a/Dockerfile b/Dockerfile
index fe8a9886..ec32b3a2 100644
--- a/Dockerfile
+++ b/Dockerfile
@@ -1,12 +1,12 @@
# Step 1: Builder
-FROM golang:1.21-alpine3.18@sha256:d8b99943fb0587b79658af03d4d4e8b57769b21dcf08a8401352a9f2a7228754 as permify-builder
+FROM golang:1.22-alpine3.18@sha256:2745a45f77ae2e7be569934fa9a111f067d04c767f54577e251d9b101250e46b as permify-builder
WORKDIR /go/src/app
RUN apk update && apk add --no-cache git
COPY . .
RUN --mount=type=cache,target=/root/.cache/go-build --mount=type=cache,target=/go/pkg/mod CGO_ENABLED=0 go build -v ./cmd/permify/
# Step 2: Final
-FROM cgr.dev/chainguard/static:latest@sha256:fd59d10894f38ce93eb6e587595ccdd8570bfd9c8f6fde7df4c589a5cefd82e2
+FROM cgr.dev/chainguard/static:latest@sha256:17c46078cc3a08fa218189d8446f88990361e8fd9e2cb6f6f535a7496c389e8e
COPY --from=ghcr.io/grpc-ecosystem/grpc-health-probe:v0.4.19 /ko-app/grpc-health-probe /usr/local/bin/grpc_health_probe
COPY --from=permify-builder /go/src/app/permify /usr/local/bin/permify
ENV PATH="$PATH:/usr/local/bin"
diff --git a/Dockerfile.local b/Dockerfile.local
index 2b6759c8..6ffc1709 100644
--- a/Dockerfile.local
+++ b/Dockerfile.local
@@ -1,4 +1,4 @@
-FROM golang:1.21-alpine
+FROM golang:1.22-alpine
RUN apk --no-cache add curl
# Install the air binary so we get live code-reloading when we save files
diff --git a/Makefile b/Makefile
index 9449ed1f..69742733 100644
--- a/Makefile
+++ b/Makefile
@@ -86,8 +86,4 @@ serve: build
.PHONY: serve-playground
serve-playground:
- cd ./playground && yarn start
-
-.PHONY: serve-docs
-serve-docs:
- cd ./docs && yarn start
\ No newline at end of file
+ cd ./playground && yarn start
\ No newline at end of file
diff --git a/README.md b/README.md
index 8a179865..5bbae064 100644
--- a/README.md
+++ b/README.md
@@ -36,15 +36,15 @@ Our goal is to make Google's Zanzibar available to everyone and help them build
### With Permify, you can:
-🔮 Create permissions and policies using [Permify's flexible authorization language](https://docs.permify.co/docs/getting-started/modeling) that is compatible with traditional roles and permissions (RBAC), arbitrary relations between users and objects (ReBAC), and attributes (ABAC).
+🔮 Create permissions and policies using [Permify's flexible authorization language](https://docs.permify.co/getting-started/modeling) that is compatible with traditional roles and permissions (RBAC), arbitrary relations between users and objects (ReBAC), and attributes (ABAC).
-🔐 [Manage and store authorization data](https://docs.permify.co/docs/getting-started/sync-data) in your preferred database with high availability and consistency.
+🔐 [Manage and store authorization data](https://docs.permify.co/getting-started/sync-data) in your preferred database with high availability and consistency.
-✅ [Interact with the Permify API](https://docs.permify.co/docs/getting-started/enforcement) to perform access checks, filter your resources with specific permissions, perform bulk permission checks for various resources, and more.
+✅ [Interact with the Permify API](https://docs.permify.co/getting-started/enforcement) to perform access checks, filter your resources with specific permissions, perform bulk permission checks for various resources, and more.
-🧪 Test your authorization logic with [Permify's schema testing](https://docs.permify.co/docs/getting-started/testing). You can conduct scenario-based testing, policy coverage analysis, and IDL parser integration to achieve end-to-end validations for your desired authorization schema.
+🧪 Test your authorization logic with [Permify's schema testing](https://docs.permify.co/getting-started/testing). You can conduct scenario-based testing, policy coverage analysis, and IDL parser integration to achieve end-to-end validations for your desired authorization schema.
-⚙️ Create custom and isolated authorization models for different applications using Permify [Multi-Tenancy](https://docs.permify.co/docs/use-cases/multi-tenancy) support, all managed within a single place, Permify instance.
+⚙️ Create custom and isolated authorization models for different applications using Permify [Multi-Tenancy](https://docs.permify.co/use-cases/multi-tenancy) support, all managed within a single place, Permify instance.
## Getting Started
@@ -53,9 +53,9 @@ Our goal is to make Google's Zanzibar available to everyone and help them build
- Explore overview of [Permify API] and learn how to interact with it.
- See [our article] to examine [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf) in a nutshell.
-[Permify's Authorization Language]: https://docs.permify.co/docs/getting-started/modeling
+[Permify's Authorization Language]: https://docs.permify.co/getting-started/modeling
[playground]: https://play.permify.co/
-[Permify API]: https://docs.permify.co/docs/api-overview
+[Permify API]: https://docs.permify.co/api-reference
[our article]: https://permify.co/post/google-zanzibar-in-a-nutshell
### QuickStart
@@ -73,7 +73,7 @@ This will start Permify with the default configuration options:
See [all of the options] that you can use to set up and deploy Permify in your servers.
-[all of the options]: https://docs.permify.co/docs/installation
+[all of the options]: https://docs.permify.co/setting-up
#### Test your connection
diff --git a/buf.gen.yaml b/buf.gen.yaml
index 62b9dd70..defc4465 100644
--- a/buf.gen.yaml
+++ b/buf.gen.yaml
@@ -28,7 +28,7 @@ plugins:
- paths=source_relative
- logtostderr=true
- plugin: buf.build/grpc-ecosystem/openapiv2:v2.16.2
- out: docs
+ out: docs/api-reference
opt:
- openapi_naming_strategy=simple
- allow_merge=true
diff --git a/docs/.DS_Store b/docs/.DS_Store
new file mode 100644
index 00000000..5832fb72
Binary files /dev/null and b/docs/.DS_Store differ
diff --git a/docs/.gitignore b/docs/.gitignore
deleted file mode 100644
index 3d94332c..00000000
--- a/docs/.gitignore
+++ /dev/null
@@ -1,21 +0,0 @@
-# Dependencies
-/node_modules
-
-# Production
-/build
-
-
-# Generated files
-.docusaurus
-.cache-loader
-
-# Misc
-.DS_Store
-.env.local
-.env.development.local
-.env.test.local
-.env.production.local
-
-npm-debug.log*
-yarn-debug.log*
-yarn-error.log*
\ No newline at end of file
diff --git a/docs/LICENSE b/docs/LICENSE
deleted file mode 100644
index 261eeb9e..00000000
--- a/docs/LICENSE
+++ /dev/null
@@ -1,201 +0,0 @@
- Apache License
- Version 2.0, January 2004
- http://www.apache.org/licenses/
-
- TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
-
- 1. Definitions.
-
- "License" shall mean the terms and conditions for use, reproduction,
- and distribution as defined by Sections 1 through 9 of this document.
-
- "Licensor" shall mean the copyright owner or entity authorized by
- the copyright owner that is granting the License.
-
- "Legal Entity" shall mean the union of the acting entity and all
- other entities that control, are controlled by, or are under common
- control with that entity. For the purposes of this definition,
- "control" means (i) the power, direct or indirect, to cause the
- direction or management of such entity, whether by contract or
- otherwise, or (ii) ownership of fifty percent (50%) or more of the
- outstanding shares, or (iii) beneficial ownership of such entity.
-
- "You" (or "Your") shall mean an individual or Legal Entity
- exercising permissions granted by this License.
-
- "Source" form shall mean the preferred form for making modifications,
- including but not limited to software source code, documentation
- source, and configuration files.
-
- "Object" form shall mean any form resulting from mechanical
- transformation or translation of a Source form, including but
- not limited to compiled object code, generated documentation,
- and conversions to other media types.
-
- "Work" shall mean the work of authorship, whether in Source or
- Object form, made available under the License, as indicated by a
- copyright notice that is included in or attached to the work
- (an example is provided in the Appendix below).
-
- "Derivative Works" shall mean any work, whether in Source or Object
- form, that is based on (or derived from) the Work and for which the
- editorial revisions, annotations, elaborations, or other modifications
- represent, as a whole, an original work of authorship. For the purposes
- of this License, Derivative Works shall not include works that remain
- separable from, or merely link (or bind by name) to the interfaces of,
- the Work and Derivative Works thereof.
-
- "Contribution" shall mean any work of authorship, including
- the original version of the Work and any modifications or additions
- to that Work or Derivative Works thereof, that is intentionally
- submitted to Licensor for inclusion in the Work by the copyright owner
- or by an individual or Legal Entity authorized to submit on behalf of
- the copyright owner. For the purposes of this definition, "submitted"
- means any form of electronic, verbal, or written communication sent
- to the Licensor or its representatives, including but not limited to
- communication on electronic mailing lists, source code control systems,
- and issue tracking systems that are managed by, or on behalf of, the
- Licensor for the purpose of discussing and improving the Work, but
- excluding communication that is conspicuously marked or otherwise
- designated in writing by the copyright owner as "Not a Contribution."
-
- "Contributor" shall mean Licensor and any individual or Legal Entity
- on behalf of whom a Contribution has been received by Licensor and
- subsequently incorporated within the Work.
-
- 2. Grant of Copyright License. Subject to the terms and conditions of
- this License, each Contributor hereby grants to You a perpetual,
- worldwide, non-exclusive, no-charge, royalty-free, irrevocable
- copyright license to reproduce, prepare Derivative Works of,
- publicly display, publicly perform, sublicense, and distribute the
- Work and such Derivative Works in Source or Object form.
-
- 3. Grant of Patent License. Subject to the terms and conditions of
- this License, each Contributor hereby grants to You a perpetual,
- worldwide, non-exclusive, no-charge, royalty-free, irrevocable
- (except as stated in this section) patent license to make, have made,
- use, offer to sell, sell, import, and otherwise transfer the Work,
- where such license applies only to those patent claims licensable
- by such Contributor that are necessarily infringed by their
- Contribution(s) alone or by combination of their Contribution(s)
- with the Work to which such Contribution(s) was submitted. If You
- institute patent litigation against any entity (including a
- cross-claim or counterclaim in a lawsuit) alleging that the Work
- or a Contribution incorporated within the Work constitutes direct
- or contributory patent infringement, then any patent licenses
- granted to You under this License for that Work shall terminate
- as of the date such litigation is filed.
-
- 4. Redistribution. You may reproduce and distribute copies of the
- Work or Derivative Works thereof in any medium, with or without
- modifications, and in Source or Object form, provided that You
- meet the following conditions:
-
- (a) You must give any other recipients of the Work or
- Derivative Works a copy of this License; and
-
- (b) You must cause any modified files to carry prominent notices
- stating that You changed the files; and
-
- (c) You must retain, in the Source form of any Derivative Works
- that You distribute, all copyright, patent, trademark, and
- attribution notices from the Source form of the Work,
- excluding those notices that do not pertain to any part of
- the Derivative Works; and
-
- (d) If the Work includes a "NOTICE" text file as part of its
- distribution, then any Derivative Works that You distribute must
- include a readable copy of the attribution notices contained
- within such NOTICE file, excluding those notices that do not
- pertain to any part of the Derivative Works, in at least one
- of the following places: within a NOTICE text file distributed
- as part of the Derivative Works; within the Source form or
- documentation, if provided along with the Derivative Works; or,
- within a display generated by the Derivative Works, if and
- wherever such third-party notices normally appear. The contents
- of the NOTICE file are for informational purposes only and
- do not modify the License. You may add Your own attribution
- notices within Derivative Works that You distribute, alongside
- or as an addendum to the NOTICE text from the Work, provided
- that such additional attribution notices cannot be construed
- as modifying the License.
-
- You may add Your own copyright statement to Your modifications and
- may provide additional or different license terms and conditions
- for use, reproduction, or distribution of Your modifications, or
- for any such Derivative Works as a whole, provided Your use,
- reproduction, and distribution of the Work otherwise complies with
- the conditions stated in this License.
-
- 5. Submission of Contributions. Unless You explicitly state otherwise,
- any Contribution intentionally submitted for inclusion in the Work
- by You to the Licensor shall be under the terms and conditions of
- this License, without any additional terms or conditions.
- Notwithstanding the above, nothing herein shall supersede or modify
- the terms of any separate license agreement you may have executed
- with Licensor regarding such Contributions.
-
- 6. Trademarks. This License does not grant permission to use the trade
- names, trademarks, service marks, or product names of the Licensor,
- except as required for reasonable and customary use in describing the
- origin of the Work and reproducing the content of the NOTICE file.
-
- 7. Disclaimer of Warranty. Unless required by applicable law or
- agreed to in writing, Licensor provides the Work (and each
- Contributor provides its Contributions) on an "AS IS" BASIS,
- WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
- implied, including, without limitation, any warranties or conditions
- of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
- PARTICULAR PURPOSE. You are solely responsible for determining the
- appropriateness of using or redistributing the Work and assume any
- risks associated with Your exercise of permissions under this License.
-
- 8. Limitation of Liability. In no event and under no legal theory,
- whether in tort (including negligence), contract, or otherwise,
- unless required by applicable law (such as deliberate and grossly
- negligent acts) or agreed to in writing, shall any Contributor be
- liable to You for damages, including any direct, indirect, special,
- incidental, or consequential damages of any character arising as a
- result of this License or out of the use or inability to use the
- Work (including but not limited to damages for loss of goodwill,
- work stoppage, computer failure or malfunction, or any and all
- other commercial damages or losses), even if such Contributor
- has been advised of the possibility of such damages.
-
- 9. Accepting Warranty or Additional Liability. While redistributing
- the Work or Derivative Works thereof, You may choose to offer,
- and charge a fee for, acceptance of support, warranty, indemnity,
- or other liability obligations and/or rights consistent with this
- License. However, in accepting such obligations, You may act only
- on Your own behalf and on Your sole responsibility, not on behalf
- of any other Contributor, and only if You agree to indemnify,
- defend, and hold each Contributor harmless for any liability
- incurred by, or claims asserted against, such Contributor by reason
- of your accepting any such warranty or additional liability.
-
- END OF TERMS AND CONDITIONS
-
- APPENDIX: How to apply the Apache License to your work.
-
- To apply the Apache License to your work, attach the following
- boilerplate notice, with the fields enclosed by brackets "[]"
- replaced with your own identifying information. (Don't include
- the brackets!) The text should be enclosed in the appropriate
- comment syntax for the file format. We also recommend that a
- file or class name and description of purpose be included on the
- same "printed page" as the copyright notice for easier
- identification within third-party archives.
-
- Copyright [yyyy] [name of copyright owner]
-
- Licensed under the Apache License, Version 2.0 (the "License");
- you may not use this file except in compliance with the License.
- You may obtain a copy of the License at
-
- http://www.apache.org/licenses/LICENSE-2.0
-
- Unless required by applicable law or agreed to in writing, software
- distributed under the License is distributed on an "AS IS" BASIS,
- WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- See the License for the specific language governing permissions and
- limitations under the License.
diff --git a/docs/README.md b/docs/README.md
index 5bffd7d6..c89c478d 100644
--- a/docs/README.md
+++ b/docs/README.md
@@ -1,10 +1,32 @@
-# Permify Documentation
+# Mintlify Starter Kit
-Documentation for [Permify], open source authorization service.
+Click on `Use this template` to copy the Mintlify starter kit. The starter kit contains examples including
-[Permify]: https://github.com/Permify/permify
+- Guide pages
+- Navigation
+- Customizations
+- API Reference pages
+- Use of popular components
-
-
-
-
\ No newline at end of file
+### Development
+
+Install the [Mintlify CLI](https://www.npmjs.com/package/mintlify) to preview the documentation changes locally. To install, use the following command
+
+```
+npm i -g mintlify
+```
+
+Run the following command at the root of your documentation (where mint.json is)
+
+```
+mintlify dev
+```
+
+### Publishing Changes
+
+Install our Github App to autopropagate changes from youre repo to your deployment. Changes will be deployed to production automatically after pushing to the default branch. Find the link to install on your dashboard.
+
+#### Troubleshooting
+
+- Mintlify dev isn't running - Run `mintlify install` it'll re-install dependencies.
+- Page loads as a 404 - Make sure you are running in a folder with `mint.json`
diff --git a/docs/api-reference/.DS_Store b/docs/api-reference/.DS_Store
new file mode 100644
index 00000000..bd22b593
Binary files /dev/null and b/docs/api-reference/.DS_Store differ
diff --git a/docs/apidocs.swagger.json b/docs/api-reference/apidocs.swagger.json
similarity index 73%
rename from docs/apidocs.swagger.json
rename to docs/api-reference/apidocs.swagger.json
index ac38c267..bdf04722 100644
--- a/docs/apidocs.swagger.json
+++ b/docs/api-reference/apidocs.swagger.json
@@ -3,7 +3,7 @@
"info": {
"title": "Permify API",
"description": "Permify is an open source authorization service for creating fine-grained and scalable authorization systems.",
- "version": "v0.7.6",
+ "version": "v0.7.8",
"contact": {
"name": "API Support",
"url": "https://github.com/Permify/permify/issues",
@@ -46,7 +46,7 @@
"paths": {
"/v1/tenants/create": {
"post": {
- "summary": "create new tenant",
+ "summary": "create tenant",
"operationId": "tenants.create",
"responses": {
"200": {
@@ -75,6 +75,23 @@
],
"tags": [
"Tenancy"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Tenancy.Create(context.Background(), \u0026v1.TenantCreateRequest {\n Id: \"\"\n Name: \"\"\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.tenancy.create({\n id: \"\",\n name: \"\"\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'http://localhost:3476/v1/tenants/create' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"id\": \"\",\n \"name\": \"\"\n}'"
+ }
]
}
},
@@ -109,6 +126,23 @@
],
"tags": [
"Tenancy"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Tenancy.List(context.Background(), \u0026v1.TenantListRequest{\n PageSize: 20,\n ContinuousToken: \"\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.tenancy.list({\n pageSize: 20,\n continuousToken: \"\",\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/list' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"page_size\": \"10\",\n \"continuous_token\": \"\"\n}'"
+ }
]
}
},
@@ -141,6 +175,23 @@
],
"tags": [
"Tenancy"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Tenancy.Delete(context.Background(), \u0026v1.TenantDeleteRequest {\n Id: \"\"\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.tenancy.delete({\n id: \"\",\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'"
+ }
]
}
},
@@ -165,6 +216,7 @@
"parameters": [
{
"name": "tenant_id",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -187,6 +239,23 @@
],
"tags": [
"Bundle"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Bundle.Delete(context.Background(), \u0026v1.BundleDeleteRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.delete({\n tenantId: \"t1\",\n name: \"organization_created\",\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/delete' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n}'"
+ }
]
}
},
@@ -211,6 +280,7 @@
"parameters": [
{
"name": "tenant_id",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -231,6 +301,23 @@
],
"tags": [
"Bundle"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Bundle.Read(context.Background(), \u0026v1.BundleReadRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.read({\n tenantId: \"t1\",\n name: \"organization_created\",\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n}'"
+ }
]
}
},
@@ -255,6 +342,7 @@
"parameters": [
{
"name": "tenant_id",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -281,12 +369,29 @@
],
"tags": [
"Bundle"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err := client.Bundle.Write(context.Background(), \u0026v1.BundleWriteRequest{\n TenantId: \"t1\",\n Bundles: []*v1.DataBundle{\n {\n Name: \"organization_created\",\n Arguments: []string{\n \"creatorID\",\n \"organizationID\",\n },\n Operations: []*v1.Operation{\n {\n RelationshipsWrite: []string{\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n },\n AttributesWrite: []string{\n \"organization:{{.organizationID}}$public|boolean:false\",\n },\n },\n },\n },\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.write({\n tenantId: \"t1\",\n bundles: [\n {\n name: \"organization_created\",\n arguments: [\n \"creatorID\",\n \"organizationID\",\n ],\n operations: [\n {\n relationships_write: [\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n ],\n attributes_write: [\n \"organization:{{.organizationID}}$public|boolean:false\",\n ]\n }\n ]\n }\n ]\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"bundles\": [\n {\n \"name\": \"organization_created\"\n \"arguments\": [\n \"creatorID\",\n \"organizationID\"\n ],\n \"operations\": [\n {\n \"relationships_write\": [\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n ],\n \"attributes_write\": [\n \"organization:{{.organizationID}}$public|boolean:false\",\n ],\n },\n ],\n },\n ],\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/data/attributes/read": {
"post": {
- "summary": "read attribute(s)",
+ "summary": "read attributes",
"operationId": "data.attributes.read",
"responses": {
"200": {
@@ -305,7 +410,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id represents the unique identifier of the tenant from which the attributes are being read.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -341,6 +446,23 @@
],
"tags": [
"Data"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.ReadAttributes(context.Background(), \u0026 v1.Data.AttributeReadRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.Data.AttributeReadRequestMetadata {\n SnapToken: \"\"\n },\n Filter: \u0026v1.AttributeFilter {\n Entity: \u0026v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Attributes: []string {\"private\"},\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.readAttributes({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n attributes: [\n \"private\"\n ],\n }\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/attributes/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n attributes: [\n \"private\"\n ],\n }\n}'"
+ }
]
}
},
@@ -365,7 +487,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id represents the unique identifier of the tenant from which the data will be deleted.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -392,12 +514,29 @@
],
"tags": [
"Data"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.Delete(context.Background(), \u0026 v1.DataDeleteRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.DataDeleteRequestMetadata {\n SnapToken: \"\"\n },\n TupleFilter: \u0026v1.TupleFilter {\n Entity: \u0026v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Relation: \"admin\",\n Subject: \u0026v1.SubjectFilter {\n Type: \"user\",\n Id: []string {\"1\"},\n Relation: \"\"\n }}\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.delete({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n tupleFilter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"admin\",\n subject: {\n type: \"user\",\n ids: [\n \"1\"\n ],\n relation: \"\"\n }\n }\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/delete' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"tupleFilter\": {\n \"entity\": {\n \"type\": \"organization\",\n \"ids\": [\n \"1\"\n ]\n },\n \"relation\": \"admin\",\n \"subject\": {\n \"type\": \"user\",\n \"ids\": [\n \"1\"\n ],\n \"relation\": \"\"\n }\n },\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/data/relationships/read": {
"post": {
- "summary": "read relation tuple(s)",
+ "summary": "read relationships",
"operationId": "data.relationships.read",
"responses": {
"200": {
@@ -416,7 +555,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id represents the unique identifier of the tenant for which relationships are read.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -452,6 +591,23 @@
],
"tags": [
"Data"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.ReadRelationships(context.Background(), \u0026 v1.Data.RelationshipReadRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.Data.RelationshipReadRequestMetadata {\n SnapToken: \"\"\n },\n Filter: \u0026v1.TupleFilter {\n Entity: \u0026v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Relation: \"member\",\n Subject: \u0026v1.SubjectFilter {\n Type: \"\",\n Id: []string {\"\"},\n Relation: \"\"\n }}\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.readRelationships({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"member\",\n subject: {\n type: \"\",\n ids: [],\n relation: \"\"\n }\n }\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/relationships/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"member\",\n subject: {\n type: \"\",\n ids: [],\n relation: \"\"\n }\n }\n}'"
+ }
]
}
},
@@ -476,6 +632,7 @@
"parameters": [
{
"name": "tenant_id",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -505,12 +662,29 @@
],
"tags": [
"Data"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.RunBundle(context.Background(), \u0026v1.BundleRunRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n Arguments: map[string]string{\n \"creatorID\": \"564\",\n \"organizationID\": \"789\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.runBundle({\n tenantId: \"t1\",\n name: \"organization_created\",\n arguments: {\n creatorID: \"564\",\n organizationID: \"789\",\n }\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/run-bundle' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n \"arguments\": {\n \"creatorID\": \"564\",\n \"organizationID\": \"789\",\n }\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/data/write": {
"post": {
- "summary": "create data",
+ "summary": "write data",
"operationId": "data.write",
"responses": {
"200": {
@@ -529,7 +703,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id represents the unique identifier of the tenant for which data is written.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -568,12 +742,29 @@
],
"tags": [
"Data"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "// Convert the wrapped attribute value into Any proto message\nvalue, err := anypb.New(\u0026v1.BooleanValue{\n Data: true,\n})\nif err != nil {\n // Handle error\n}\n\ncr, err := client.Data.Write(context.Background(), \u0026v1.DataWriteRequest{\n TenantId: \"t1\",,\n Metadata: \u0026v1.DataWriteRequestMetadata{\n SchemaVersion: \"\",\n },\n Tuples: []*v1.Attribute{\n {\n Entity: \u0026v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Relation: \"editor\",\n Subject: \u0026v1.Subject{\n Type: \"user\",\n Id: \"1\",\n Relation: \"\",\n },\n },\n },\n Attributes: []*v1.Attribute{\n {\n Entity: \u0026v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Attribute: \"is_private\",\n Value: value,\n },\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const booleanValue = BooleanValue.fromJSON({ data: true });\n\nconst value = Any.fromJSON({\n typeUrl: 'type.googleapis.com/base.v1.BooleanValue',\n value: BooleanValue.encode(booleanValue).finish()\n});\n\nclient.data.write({\n tenantId: \"t1\",\n metadata: {\n schemaVersion: \"\"\n },\n tuples: [{\n entity: {\n type: \"document\",\n id: \"1\"\n },\n relation: \"editor\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n }],\n attributes: [{\n entity: {\n type: \"document\",\n id: \"1\"\n },\n attribute: \"is_private\",\n value: value,\n }]\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n{\n \"metadata\": {\n \"schema_version\": \"\"\n },\n \"tuples\": [\n {\n \"entity\": {\n \"type\": \"document\",\n \"id\": \"1\"\n },\n \"relation\": \"editor\",\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\"\n }\n }\n ],\n \"attributes\": [\n {\n \"entity\": {\n \"type\": \"document\",\n \"id\": \"1\"\n },\n \"attribute\": \"is_private\",\n \"value\": {\n \"@type\": \"type.googleapis.com/base.v1.BooleanValue\",\n \"data\": true\n }\n }\n ]\n}\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/check": {
"post": {
- "summary": "This method returns a decision about whether user can perform an permission on a certain resource.",
+ "summary": "check api",
"operationId": "permissions.check",
"responses": {
"200": {
@@ -592,7 +783,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -610,11 +801,12 @@
},
"entity": {
"$ref": "#/definitions/Entity",
+ "example": "repository:1",
"description": "Entity on which the permission needs to be checked, required."
},
"permission": {
"type": "string",
- "description": "Name of the permission or relation, required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ "description": "The action the user wants to perform on the resource"
},
"subject": {
"$ref": "#/definitions/Subject",
@@ -622,7 +814,7 @@
},
"context": {
"$ref": "#/definitions/Context",
- "description": "Context associated with this request."
+ "description": "Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../operations/contextual-tuples)"
},
"arguments": {
"type": "array",
@@ -639,12 +831,29 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Permission.Check(context.Background(), \u0026v1.PermissionCheckRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.PermissionCheckRequestMetadata {\n SnapToken: \"\",\n SchemaVersion: \"\",\n Depth: 20,\n },\n Entity: \u0026v1.Entity {\n Type: \"repository\",\n Id: \"1\",\n },\n Permission: \"edit\",\n Subject: \u0026v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n\n if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {\n // RESULT_ALLOWED\n } else {\n // RESULT_DENIED\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.check({\n tenantId: \"t1\", \n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n permission: \"edit\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) =\u003e {\n if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {\n console.log(\"RESULT_ALLOWED\")\n } else {\n console.log(\"RESULT_DENIED\")\n }\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"depth\": 20\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"permission\": \"edit\",\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\",\n \"relation\": \"\"\n },\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/expand": {
"post": {
- "summary": "expand relationships according to schema",
+ "summary": "expand api",
"operationId": "permissions.expand",
"responses": {
"200": {
@@ -663,7 +872,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -706,12 +915,29 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.Expand(context.Background(), \u0026v1.PermissionExpandRequest{\n TenantId: \"t1\",\n Metadata: \u0026v1.PermissionExpandRequestMetadata{\n SnapToken: \"\",\n SchemaVersion: \"\",\n },\n Entity: \u0026v1.Entity{\n Type: \"repository\",\n Id: \"1\",\n },\n Permission: \"push\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.expand({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\"\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n permission: \"push\",\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\": {\n \"schema_version\": \"\",\n \"snap_token\": \"\"\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"permission\": \"push\"\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/lookup-entity": {
"post": {
- "summary": "Retrieve an entity by its identifier.",
+ "summary": "lookup entity",
"operationId": "permissions.lookupEntity",
"responses": {
"200": {
@@ -730,7 +956,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -769,12 +995,29 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.LookupEntity(context.Background(), \u0026 v1.PermissionLookupEntityRequest {\n TenantId: \"t1\",\n Metadata: \u0026 v1.PermissionLookupEntityRequestMetadata {\n SnapToken: \"\"\n SchemaVersion: \"\"\n Depth: 20,\n },\n EntityType: \"document\",\n Permission: \"edit\",\n Subject: \u0026 v1.Subject {\n Type: \"user\",\n Id: \"1\",\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.lookupEntity({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entity_type: \"document\",\n permission: \"edit\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) =\u003e {\n console.log(response.entity_ids)\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"depth\": 20\n },\n \"entity_type\": \"document\",\n \"permission\": \"edit\",\n \"subject\": {\n \"type\":\"user\",\n \"id\":\"1\"\n }\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/lookup-entity-stream": {
"post": {
- "summary": "Stream entities by their identifiers.",
+ "summary": "lookup entity stream",
"operationId": "permissions.lookupEntityStream",
"responses": {
"200": {
@@ -802,7 +1045,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -841,12 +1084,24 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "str, err: = client.Permission.LookupEntityStream(context.Background(), \u0026v1.PermissionLookupEntityRequest {\n Metadata: \u0026v1.PermissionLookupEntityRequestMetadata {\n SnapToken: \"\", \n SchemaVersion: \"\" \n Depth: 50,\n },\n EntityType: \"document\",\n Permission: \"view\",\n Subject: \u0026v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n})\n\n// handle stream response\nfor {\n res, err: = str.Recv()\n\n if err == io.EOF {\n break\n }\n\n // res.EntityId\n}"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const permify = require(\"@permify/permify-node\");\nconst {PermissionLookupEntityStreamResponse} = require(\"@permify/permify-node/dist/src/grpc/generated/base/v1/service\");\n\nfunction main() {\n const client = new permify.grpc.newClient({\n endpoint: \"localhost:3478\",\n })\n\n let res = client.permission.lookupEntityStream({\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entityType: \"document\",\n permission: \"view\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n })\n\n handle(res)\n}\n\nasync function handle(res: AsyncIterable\u003cPermissionLookupEntityStreamResponse\u003e) {\n for await (const response of res) {\n // response.entityId\n }\n}"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/lookup-subject": {
"post": {
- "summary": "Retrieve a subject by its identifier.",
+ "summary": "lookup-subject",
"operationId": "permissions.lookupSubject",
"responses": {
"200": {
@@ -865,7 +1120,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -904,12 +1159,29 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.LookupSubject(context.Background(), \u0026v1.PermissionLookupSubjectRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.PermissionLookupSubjectRequestMetadata{\n SnapToken: \"\",\n SchemaVersion: \"\",\n Depth: 20,\n },\n Entity: \u0026v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Permission: \"edit\",\n SubjectReference: \u0026v1.RelationReference{\n Type: \"user\",\n Relation: \"\",\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.lookupSubject({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\"\n depth: 20,\n },\n Entity: {\n Type: \"document\",\n Id: \"1\",\n },\n permission: \"edit\",\n subject_reference: {\n type: \"user\",\n relation: \"\"\n }\n}).then((response) =\u003e {\n console.log(response.subject_ids)\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\"\n \"depth\": 20,\n },\n \"entity\": {\n type: \"document\",\n id: \"1'\n },\n \"permission\": \"edit\",\n \"subject_reference\": {\n \"type\": \"user\",\n \"relation\": \"\"\n }\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/permissions/subject-permission": {
"post": {
- "summary": "Retrieve permissions related to a specific subject.",
+ "summary": "subject permission",
"operationId": "permissions.subjectPermission",
"responses": {
"200": {
@@ -928,7 +1200,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -963,6 +1235,23 @@
],
"tags": [
"Permission"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.SubjectPermission(context.Background(), \u0026v1.PermissionSubjectPermissionRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.PermissionSubjectPermissionRequestMetadata {\n SnapToken: \"\",\n SchemaVersion: \"\",\n OnlyPermission: false,\n Depth: 20,\n },\n Entity: \u0026v1.Entity {\n Type: \"repository\",\n Id: \"1\",\n },\n Subject: \u0026v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.subjectPermission({\n tenantId: \"t1\", \n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n onlyPermission: true,\n depth: 20\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) =\u003e {\n console.log(response);\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"only_permission\": true,\n \"depth\": 20\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\",\n \"relation\": \"\"\n },\n}'"
+ }
]
}
},
@@ -987,6 +1276,7 @@
"parameters": [
{
"name": "tenant_id",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1013,7 +1303,7 @@
},
"/v1/tenants/{tenant_id}/relationships/write": {
"post": {
- "summary": "create new relationships",
+ "summary": "write relationships",
"operationId": "relationships.write",
"responses": {
"200": {
@@ -1032,7 +1322,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Unique identifier for the tenant with specific constraints.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1068,7 +1358,7 @@
},
"/v1/tenants/{tenant_id}/schemas/list": {
"post": {
- "summary": "list all authorization models",
+ "summary": "list schema",
"operationId": "schemas.list",
"responses": {
"200": {
@@ -1087,7 +1377,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id is a string that identifies the tenant. It must match the pattern \"[a-zA-Z0-9-,]+\",\nbe a maximum of 64 bytes, and must not be empty.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1115,12 +1405,29 @@
],
"tags": [
"Schema"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.List(context.Background(), \u0026v1.SchemaListRequest {\n TenantId: \"t1\",\n PageSize: \"10\",\n ContinuousToken: \"\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.schema.list({\n tenantId: \"t1\",\n continuousToken: \"\"\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"page_size\": \"10\",\n \"continuous_token\": \"\"\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/schemas/read": {
"post": {
- "summary": "read your authorization model",
+ "summary": "read schema",
"operationId": "schemas.read",
"responses": {
"200": {
@@ -1139,7 +1446,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id is a string that identifies the tenant. It must match the pattern \"[a-zA-Z0-9-,]+\",\nbe a maximum of 64 bytes, and must not be empty.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1162,12 +1469,29 @@
],
"tags": [
"Schema"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.Read(context.Background(), \u0026v1.SchemaReadRequest {\n TenantId: \"t1\",\n Metadata: \u0026v1.SchemaReadRequestMetadata{\n SchemaVersion: \"cnbe6se5fmal18gpc66g\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.schema.read({\n tenantId: \"t1\",\n metadata: {\n schemaVersion: swResponse.schemaVersion,\n },\n })"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\": {\n \"schema_version\": \"cnbe6se5fmal18gpc66g\"\n }\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/schemas/write": {
"post": {
- "summary": "write your authorization model",
+ "summary": "write schema",
"operationId": "schemas.write",
"responses": {
"200": {
@@ -1186,7 +1510,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "tenant_id is a string that identifies the tenant. It must match the pattern \"[a-zA-Z0-9-,]+\",\nbe a maximum of 64 bytes, and must not be empty.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1209,11 +1533,29 @@
],
"tags": [
"Schema"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.Write(context.Background(), \u0026v1.SchemaWriteRequest {\n TenantId: \"t1\",\n Schema: `\n \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n `,\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.schema.write({\n tenantId: \"t1\",\n schema: `\n \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n `\n}).then((response) =\u003e {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"schema\": \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n}'"
+ }
]
}
},
"/v1/tenants/{tenant_id}/watch": {
"post": {
+ "summary": "watch changes",
"operationId": "watch.watch",
"responses": {
"200": {
@@ -1241,7 +1583,7 @@
"parameters": [
{
"name": "tenant_id",
- "description": "Identifier of the tenant, required, and must match the pattern \"[a-zA-Z0-9-,]+\", max 64 bytes.",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant \u003ccode\u003et1\u003c/code\u003e for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
"in": "path",
"required": true,
"type": "string"
@@ -1255,7 +1597,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "Snap token to be used for watching."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
}
},
"description": "WatchRequest is the request message for the Watch RPC. It contains the\ndetails needed to establish a watch stream."
@@ -1264,6 +1606,18 @@
],
"tags": [
"Watch"
+ ],
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Watch.Watch(context.Background(), \u0026v1.WatchRequest{\n TenantId: \"t1\",\n SnapToken: \"\",\n})\n// handle stream response\nfor {\n res, err := cr.Recv()\n\n if err == io.EOF {\n break\n }\n\n // res.Changes\n}\n"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const permify = require(\"@permify/permify-node\");\nconst {WatchResponse} = require(\"@permify/permify-node/dist/src/grpc/generated/base/v1/service\");\n\nfunction main() {\n const client = new permify.grpc.newClient({\n endpoint: \"localhost:3478\",\n })\n\n let res = client.watch.watch({\n tenantId: \"t1\",\n snapToken: \"\"\n })\n\n handle(res)\n}\n\nasync function handle(res: AsyncIterable\u003cWatchResponse\u003e) {\n for await (const response of res) {\n // response.changes\n }\n}\n"
+ }
]
}
}
@@ -1361,7 +1715,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "snap_token represents a specific state or \"snapshot\" of the database."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"description": "AttributeReadRequestMetadata defines the structure for the metadata of an attribute read request.\nIt includes the snap_token associated with a particular state of the database."
@@ -1421,7 +1775,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "Token related to the bundle execution."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"description": "BundleRunResponse is the response for a BundleRunRequest.\nIt includes a snap_token, which may be used for tracking the execution or its results."
@@ -1748,7 +2102,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "snap_token represents the state of the database after the requested deletions."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"description": "DataDeleteResponse defines the structure of the response to a data delete request.\nIt includes a snap_token representing the state of the database after the deletion."
@@ -1768,7 +2122,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "snap_token is the token generated after the data write operation, representing a snapshot of the data."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
}
},
"description": "DataWriteResponse defines the structure of the response after writing data.\nIt contains the snap_token generated after the write operation."
@@ -2107,15 +2461,15 @@
},
"snap_token": {
"type": "string",
- "description": "Token associated with the snap."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
},
"depth": {
"type": "integer",
"format": "int32",
- "description": "Depth of the check, must be greater than or equal to 3."
+ "description": "Query limit when if recursive database queries got in loop"
}
},
- "description": "PermissionCheckRequestMetadata is the metadata associated with a PermissionCheckRequest."
+ "description": "PermissionCheckRequestMetadata metadata for the PermissionCheckRequest."
},
"PermissionCheckResponse": {
"type": "object",
@@ -2140,7 +2494,7 @@
"description": "The count of the checks performed."
}
},
- "description": "PermissionCheckResponseMetadata is the metadata associated with a PermissionCheckResponse."
+ "description": "PermissionCheckResponseMetadata metadata for the PermissionCheckResponse."
},
"PermissionDefinition": {
"type": "object",
@@ -2165,10 +2519,10 @@
},
"snap_token": {
"type": "string",
- "description": "Token associated with the snap."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
}
},
- "description": "PermissionExpandRequestMetadata is the metadata associated with a PermissionExpandRequest."
+ "description": "PermissionExpandRequestMetadata metadata for the PermissionExpandRequest."
},
"PermissionExpandResponse": {
"type": "object",
@@ -2189,15 +2543,15 @@
},
"snap_token": {
"type": "string",
- "description": "Token associated with the snap."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
},
"depth": {
"type": "integer",
"format": "int32",
- "description": "Depth of lookup, required, must be greater or equal to 3."
+ "description": "Query limit when if recursive database queries got in loop."
}
},
- "description": "PermissionLookupEntityRequestMetadata is the metadata associated with a PermissionLookupEntityRequest."
+ "description": "PermissionLookupEntityRequestMetadata metadata for the PermissionLookupEntityRequest."
},
"PermissionLookupEntityResponse": {
"type": "object",
@@ -2231,15 +2585,15 @@
},
"snap_token": {
"type": "string",
- "description": "Token associated with the snap."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
},
"depth": {
"type": "integer",
"format": "int32",
- "description": "Depth of the check, must be greater than or equal to 3."
+ "description": "Query limit when if recursive database queries got in loop."
}
},
- "description": "PermissionLookupSubjectRequestMetadata is the metadata associated with a PermissionLookupSubjectRequest."
+ "description": "PermissionLookupSubjectRequestMetadata metadata for the PermissionLookupSubjectRequest."
},
"PermissionLookupSubjectResponse": {
"type": "object",
@@ -2263,7 +2617,7 @@
},
"snap_token": {
"type": "string",
- "description": "Token associated with the snap."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
},
"only_permission": {
"type": "boolean",
@@ -2272,10 +2626,10 @@
"depth": {
"type": "integer",
"format": "int32",
- "description": "Depth of the check, must be greater than or equal to 3."
+ "description": "Query limit when if recursive database queries got in loop."
}
},
- "description": "PermissionSubjectPermissionRequestMetadata is the metadata associated with a PermissionSubjectPermissionRequest."
+ "description": "PermissionSubjectPermissionRequestMetadata metadata for the PermissionSubjectPermissionRequest."
},
"PermissionSubjectPermissionResponse": {
"type": "object",
@@ -2340,7 +2694,8 @@
"type": "object",
"properties": {
"snap_token": {
- "type": "string"
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"title": "RelationshipDeleteResponse"
@@ -2350,7 +2705,7 @@
"properties": {
"snap_token": {
"type": "string",
- "description": "snap_token represents a specific state or \"snapshot\" of the database."
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"description": "RelationshipReadRequestMetadata defines the structure of the metadata for a read request focused on relationships.\nIt includes the snap_token associated with a particular state of the database."
@@ -2386,7 +2741,8 @@
"type": "object",
"properties": {
"snap_token": {
- "type": "string"
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
}
},
"title": "RelationshipWriteResponse"
diff --git a/docs/api-reference/bundle/delete-bundle.mdx b/docs/api-reference/bundle/delete-bundle.mdx
new file mode 100644
index 00000000..21fe3193
--- /dev/null
+++ b/docs/api-reference/bundle/delete-bundle.mdx
@@ -0,0 +1,10 @@
+---
+title: Delete Bundle
+openapi: post /v1/tenants/{tenant_id}/bundle/delete
+---
+
+The "Delete Bundle" API is designed for removing specific data bundles within a multi-tenant application environment. This API facilitates the deletion of a bundle, identified by its unique name, from a designated tenant's environment.
+
+
+To see what Data Bundles are and how they work, check out the [Data Bundles](../../operations/bundle) section.
+
\ No newline at end of file
diff --git a/docs/api-reference/bundle/read-bundle.mdx b/docs/api-reference/bundle/read-bundle.mdx
new file mode 100644
index 00000000..e6870100
--- /dev/null
+++ b/docs/api-reference/bundle/read-bundle.mdx
@@ -0,0 +1,10 @@
+---
+title: Read Bundle
+openapi: post /v1/tenants/{tenant_id}/bundle/read
+---
+
+The "Read Bundle" API is a crucial tool for retrieving details of specific data bundles in a multi-tenant application setup. It is designed to access information about a bundle, uniquely identified by its name, within the specified tenant's environment.
+
+
+To see what Data Bundles are and how they work, check out the [Data Bundles](../../operations/bundle) section.
+
\ No newline at end of file
diff --git a/docs/docs/bundle.md b/docs/api-reference/bundle/write-bundle.mdx
similarity index 76%
rename from docs/docs/bundle.md
rename to docs/api-reference/bundle/write-bundle.mdx
index ca7db9ec..9688a7e6 100644
--- a/docs/docs/bundle.md
+++ b/docs/api-reference/bundle/write-bundle.mdx
@@ -1,15 +1,13 @@
---
-id: bundle
-title: Bundle Service
-sidebar_label: Data Bundles
-slug: /api-overview/bundle
+title: Write Bundle
+openapi: post /v1/tenants/{tenant_id}/bundle/write
---
-## What is Data Bundles
+## What is Data Bundles?
Ensuring that authorization data remains in sync with the business model is an important practice when using Permify.
-Prior to Data Bundles, it was the responsibility of the services (such as [WriteData](./api-overview/data/write-data.md) API) to structure how relations are created and deleted when actions occur on resources.
+Prior to Data Bundles, it was the responsibility of the services (such as [WriteData API](../data/write-data)) to structure how relations are created and deleted when actions occur on resources.
With the Data Bundles, you be able to bundle and model the creation and deletion of relations and attributes when specific actions occur on resources in your applications.
@@ -19,7 +17,7 @@ We believe this functionality will streamline managing authorization data as wel
Let's examine how Bundles operates with basic example.
-Let's say you want to model how data will be created when an organization created in your application. For this purpose, you can utilize the [WriteBundle](./api-overview/bundle/write-bundle.md) API endpoint. This API enables users to define or update data bundles, each distinguished by a unique name.
+Let's say you want to model how data will be created when an organization created in your application. For this purpose, you can utilize the WriteBundle API endpoint. This API enables users to define or update data bundles, each distinguished by a unique name.
Here's an example body for WriteBundle in this scenario:
@@ -78,7 +76,11 @@ This will result in the creation of the following data in Permify:
## Endpoints
-- [WriteBundle](./api-overview/bundle/write-bundle.md)
-- [RunBundle](./api-overview/data/run-bundle.md)
-- [DeleteBundle](./api-overview/bundle/delete-bundle.md)
-- [ReadBundle](./api-overview/bundle/read-bundle.md)
+- [WriteBundle](./write-bundle)
+- [RunBundle](../data/run-bundle)
+- [DeleteBundle](./delete-bundle)
+- [ReadBundle](./read-bundle)
+
+## Write Bundles Request
+
+The "Write Bundle" API is designed for handling data in a multi-tenant application environment. Its primary function is to write and delete data according to predefined structures. This API allows users to define or update data bundles, each distinguished by a unique name.
\ No newline at end of file
diff --git a/docs/api-reference/data/delete-data.mdx b/docs/api-reference/data/delete-data.mdx
new file mode 100644
index 00000000..c3e7f79a
--- /dev/null
+++ b/docs/api-reference/data/delete-data.mdx
@@ -0,0 +1,4 @@
+---
+title: Delete Data
+openapi: post /v1/tenants/{tenant_id}/data/delete
+---
\ No newline at end of file
diff --git a/docs/api-reference/data/delete-relationships.mdx b/docs/api-reference/data/delete-relationships.mdx
new file mode 100644
index 00000000..d0a6f57f
--- /dev/null
+++ b/docs/api-reference/data/delete-relationships.mdx
@@ -0,0 +1,4 @@
+---
+title: Delete Relationships
+openapi: post /v1/tenants/{tenant_id}/relationships/delete
+---
\ No newline at end of file
diff --git a/docs/api-reference/data/read-attributes.mdx b/docs/api-reference/data/read-attributes.mdx
new file mode 100644
index 00000000..c070820b
--- /dev/null
+++ b/docs/api-reference/data/read-attributes.mdx
@@ -0,0 +1,6 @@
+---
+title: Read Attributes
+openapi: post /v1/tenants/{tenant_id}/data/attributes/read
+---
+
+Read API allows for directly querying the stored graph data to display and filter stored attributes.
diff --git a/docs/api-reference/data/read-relationships.mdx b/docs/api-reference/data/read-relationships.mdx
new file mode 100644
index 00000000..316d1e63
--- /dev/null
+++ b/docs/api-reference/data/read-relationships.mdx
@@ -0,0 +1,6 @@
+---
+title: Read Relationships
+openapi: post /v1/tenants/{tenant_id}/data/relationships/read
+---
+
+Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
diff --git a/docs/api-reference/data/run-bundle.mdx b/docs/api-reference/data/run-bundle.mdx
new file mode 100644
index 00000000..3b095823
--- /dev/null
+++ b/docs/api-reference/data/run-bundle.mdx
@@ -0,0 +1,10 @@
+---
+title: Run Bundle
+openapi: post /v1/tenants/{tenant_id}/data/run-bundle
+---
+
+The "Run Bundle" API provides a straightforward way to execute predefined bundles within your application's tenant environment. By sending a POST request to this endpoint, you can activate specific functionalities or processes encapsulated in a bundle.
+
+
+To see what Data Bundles are and how they work, check out the [Data Bundles](../../operations/bundle) section.
+
\ No newline at end of file
diff --git a/docs/docs/api-overview/data/write-data.md b/docs/api-reference/data/write-data.mdx
similarity index 70%
rename from docs/docs/api-overview/data/write-data.md
rename to docs/api-reference/data/write-data.mdx
index 67e87027..7be26346 100644
--- a/docs/docs/api-overview/data/write-data.md
+++ b/docs/api-reference/data/write-data.mdx
@@ -1,57 +1,41 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
+---
+title: Write Authorization Data
+openapi: post /v1/tenants/{tenant_id}/data/write
+---
-# Write Authorization Data
-
-In Permify, attributes and relations between your entities, objects and users represents your authorization data. These data stored as tuples in a [preferred database].
+In Permify, attributes and relations between your entities, objects and users represents your authorization data. These data stored as tuples in a preferred database.
Since these attributes and relations are live instances, meaning they can be affected by specific user actions within the application, they can be created/deleted with a simple Permify API call at runtime.
More specifically, the application client should update preferred database about the changes happening in entities or resources that are related to the authorization structure.
-If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [preferred database] up-to-date. Besides, each attribute or relationship should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as tuples and store in [preferred database].
-
-
+If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write tuples to keep preferred database up-to-date. Besides, each attribute or relationship should be created according to its authorization model, Permify Schema.
-[relational tuples]: ../../../getting-started/sync-data
-[preferred database]: ../../../getting-started/sync-data#where-relational-tuples-used
+Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as tuples and store in preferred database.
-## Write Request
-
-:::info
-You can use the **/v1/tenants/{tenant_id}/data/write** endpoint for both creating **relation tuples** and for creating **attribute data**.
-:::
+
+You can use the `/v1/tenants/{tenant_id}/data/write` endpoint for both creating **relation tuples** and for creating **attribute data**.
+
**Path:**
```javascript
POST /v1/tenants/{tenant_id}/data/write
```
-[](https://permify.github.io/permify-swagger/#/Data/data.write)
-
-#### Glossary for parameters & payload objects:
-
-| Required | Argument | Type | Default | Description |
-| -------- | -------------- | ------ | ------- | ----------------------------------------------------------------------------------------------------------------------------------------------------- |
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this parameter. |
-| [ ] | schema_version | string | 8 | Version of the schema. |
-| [x] | tuples | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **relation**, and **subject** arguments.|
-| [x] | attributes | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **attribute**, and **value** arguments. |
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1” |
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc. |
-| [x] | attribute | string | - | Custom attribute name. |
-| [x] | value | object | - | Represents value and type of the attribute data. |
+## Content
+- [Example Relationship Creation](#example-relationship-creation)
+- [Example Attributes Creation](#example-attribute-creation)
+- [Creating Attributes and Relationship In Single Request](#creating-attributes-relationships-in-singe-request)
+- [Suggested Workflow](#suggested-workflow)
+- [Parameters & Properties](#parameters-and-properties)
-### Creating Relational Tuple
+### Example Relationship Creation
Let's create an example relation tuple. If user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` should be created as follows:
-
+
```go
rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
@@ -75,9 +59,9 @@ rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
})
```
-
+
-
+
```javascript
client.data
@@ -105,8 +89,30 @@ client.data
});
```
-
-
+
+
+```python
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.DataApi(api_client)
+
+ body = permify.DataWriteRequest(
+ tenant_id='t1',
+ metadata={"schemaVersion": ""},
+ tuples=[{
+ "entity": {
+ "type": "organization",
+ "id": "1",
+ },
+ "relation": "admin",
+ "subject": {
+ "type": "user",
+ "id": "3",
+ },
+ }]
+ )
+```
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -132,22 +138,22 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
}'
```
-
+
-### Creating Attribute Data
+### Example Attribute Creation
You can use `attributes` argument to create attribute/attributes with a single API call, similarly creating a `relational tuple`.
Let's say **document:1** is a **private (boolean)** document, that only specific users have view access - `document:1$is_private|boolean:true`.
-:::info Attribute Data Syntax
+
As you noticed, the attribute tuple syntax differs from the relationship syntax, structured similarly as:
`entity $ attribute | value`
-:::
+
-
+
```go
// Convert the wrapped attribute value into Any proto message
@@ -176,9 +182,9 @@ cr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{
})
```
-
+
-
+
```javascript
const booleanValue = BooleanValue.fromJSON({ data: true });
@@ -206,8 +212,35 @@ client.data.write({
})
```
-
-
+
+
+```
+boolean_value = BooleanValue.from_json({"data": True})
+
+value = Any.from_json({
+ "typeUrl": 'type.googleapis.com/base.v1.BooleanValue',
+ "value": BooleanValue.encode(boolean_value).finish()
+})
+
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.DataApi(api_client)
+ tenant_id = 't1'
+
+ body = permify.DataWriteRequest(
+ tenant_id=tenant_id,
+ metadata={"schemaVersion": ""},
+ attributes=[{
+ "entity": {
+ "type": "document",
+ "id": "1"
+ },
+ "attribute": "is_private",
+ "value": value,
+ }]
+ )
+```
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -234,11 +267,11 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
}'
```
-
+
-:::warning Attribute **value** field
-**value** field is mandatory on attribute data creation.
+
+**value** field is mandatory on attribute data creation!
Here are the available attribute value types:
@@ -250,9 +283,9 @@ Here are the available attribute value types:
- **type.googleapis.com/base.v1.BooleanArrayValue**
- **type.googleapis.com/base.v1.IntegerArrayValue**
- **type.googleapis.com/base.v1.DoubleArrayValue**
-:::
+
-#### Creating Attributes and Relations In Single Request
+### Creating Attributes and Relationship In Single Request
Assume we want to both create relational tuple and attribute within in single request. Specifically we want to create following tuples,
@@ -261,7 +294,7 @@ Assume we want to both create relational tuple and attribute within in single re
-
+
```go
// Convert the wrapped attribute value into Any proto message
@@ -304,9 +337,9 @@ cr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{
})
```
-
+
-
+
```javascript
const booleanValue = BooleanValue.fromJSON({ data: true });
@@ -345,8 +378,47 @@ client.data.write({
})
```
-
-
+
+
+
+```
+boolean_value = BooleanValue.from_json({"data": True})
+
+value = Any.from_json({
+ "typeUrl": 'type.googleapis.com/base.v1.BooleanValue',
+ "value": BooleanValue.encode(boolean_value).finish()
+})
+
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.DataApi(api_client)
+ tenant_id = 't1'
+
+ body = permify.DataWriteRequest(
+ tenant_id=tenant_id,
+ metadata={"schemaVersion": ""},
+ tuples=[{
+ "entity": {
+ "type": "document",
+ "id": "1"
+ },
+ "relation": "editor",
+ "subject": {
+ "type": "user",
+ "id": "1"
+ },
+ }],
+ attributes=[{
+ "entity": {
+ "type": "document",
+ "id": "1"
+ },
+ "attribute": "is_private",
+ "value": value,
+ }]
+ )
+
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -386,26 +458,14 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
}'
```
-
+
-## Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../reference/snap-tokens) and how its avoiding stale cache.
-
-## Suggested Workflow
+### Suggested Workflow
The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-### Two Phase Commit Approach
+#### Two Phase Commit Approach
In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
@@ -443,7 +503,7 @@ func CreateDocuments(db *gorm.DB) error {
The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-### Data That Not Stored In Application Database
+#### Data That Not Stored In Application Database
Although ownership generally stored in application databases, there are some data that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
@@ -472,6 +532,4 @@ entity project {
This **team member** relation won't need to be stored in the application database. Storing it only in Permify - preferred database - is enough. In that situation, `WriteData` can be performed in any logical place in your stack.
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
+### Parameters & Properties
diff --git a/docs/api-reference/data/write-relationships.mdx b/docs/api-reference/data/write-relationships.mdx
new file mode 100644
index 00000000..b511a3fa
--- /dev/null
+++ b/docs/api-reference/data/write-relationships.mdx
@@ -0,0 +1,4 @@
+---
+title: Write Relationships
+openapi: post /v1/tenants/{tenant_id}/relationships/write
+---
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/enforcement.md b/docs/api-reference/introduction.mdx
similarity index 63%
rename from docs/versioned_docs/version-0.6.x/getting-started/enforcement.md
rename to docs/api-reference/introduction.mdx
index df4c80f5..d6773ccb 100644
--- a/docs/versioned_docs/version-0.6.x/getting-started/enforcement.md
+++ b/docs/api-reference/introduction.mdx
@@ -1,9 +1,8 @@
---
-sidebar_position: 4
+title: 'Introduction'
+description: 'Example section for showcasing API endpoints'
---
-# Interacting With The API
-
Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
We structured Permify API in 4 core parts:
@@ -13,43 +12,76 @@ We structured Permify API in 4 core parts:
- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ../../api-overview/permission
-[DataService]: ../../api-overview/data
-[SchemaService]: ../../api-overview/schema
-[TenancyService]: ../../api-overview/tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
+Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) and [REST](https://restfulapi.net/).
+
+[PermissionService]: ./permission/check-api
+[DataService]: ./data/write-data
+[SchemaService]: ./schema/write-schema
+[TenancyService]: ./tenancy/create-tenant
+
+**SDKs:**
+
+- [Golang](https://github.com/Permify/permify-go)
+- [NodeJS](https://github.com/Permify/permify-node)
+- [Python](https://github.com/Permify/permify-python)
+- [Javascript](https://github.com/Permify/permify-javascript)
+
+
+
+Our software does not include built-in support for service meshes (eg. Istio).
However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
+
+
## Core Paths
-- Configure your authorization model with [Schema Write](../api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](../api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](../api-overview/data/read-relationships.md)
-- Check access with [Check API](../api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](../api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](../api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](../api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](../api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](../api-overview/watch/watch-changes.md)
+- Configure your authorization model with [Schema Write](./schema/write-schema)
+- Write relational tuples with [Write Data](./data/write-data)
+- Read relation tuples and filter them with [Read Relationships](./data/read-relationships)
+- Check access with [Check API](./permission/check-api)
+- Check entities permissions with [Lookup Entity](./permission/lookup-entity)
+- Check subject permissions with [Lookup Subject](./permission/lookup-subject)
+- Delete relation tuples with [Delete Tuple](./data/delete-data)
+- Expand schema actions with [Expand API](./permission/expand-api)
+- Watch changes in the relation tuples in real-time with [Watch API](./watch/watch-changes)
## Authentication
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../../reference/configuration)
+You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../../setting-up/configuration)
To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
+## Latency & Performance
+
+With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
+
+Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../operations/cache)
+
## Availability of the Service
For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
@@ -78,3 +110,4 @@ Default rate limit is set to 100 requests per second. However, users can adjust
## Need any help ?
Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
+
diff --git a/docs/api-reference/openapi.json b/docs/api-reference/openapi.json
new file mode 100644
index 00000000..941caf0a
--- /dev/null
+++ b/docs/api-reference/openapi.json
@@ -0,0 +1,3510 @@
+{
+ "openapi": "3.0.1",
+ "info": {
+ "title": "Permify API",
+ "description": "Permify is an open source authorization service for creating fine-grained and scalable authorization systems.",
+ "contact": {
+ "name": "API Support",
+ "url": "https://github.com/Permify/permify/issues",
+ "email": "hello@permify.co"
+ },
+ "license": {
+ "name": "Apache-2.0 license",
+ "url": "https://github.com/Permify/permify/blob/master/LICENSE"
+ },
+ "version": "v0.7.7"
+ },
+ "servers": [
+ {
+ "url": "/"
+ }
+ ],
+ "tags": [
+ {
+ "name": "Permission"
+ },
+ {
+ "name": "Watch"
+ },
+ {
+ "name": "Schema"
+ },
+ {
+ "name": "Data"
+ },
+ {
+ "name": "Bundle"
+ },
+ {
+ "name": "Tenancy"
+ }
+ ],
+ "paths": {
+ "/v1/tenants/create": {
+ "post": {
+ "tags": [
+ "Tenancy"
+ ],
+ "summary": "create tenant",
+ "operationId": "tenants.create",
+ "requestBody": {
+ "description": "TenantCreateRequest is the message used for the request to create a tenant.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/TenantCreateRequest"
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/TenantCreateResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Tenancy.Create(context.Background(), &v1.TenantCreateRequest {\n Id: \"\"\n Name: \"\"\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.tenancy.create({\n id: \"\",\n name: \"\"\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'http://localhost:3476/v1/tenants/create' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"id\": \"\",\n \"name\": \"\"\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/list": {
+ "post": {
+ "tags": [
+ "Tenancy"
+ ],
+ "summary": "list tenants",
+ "operationId": "tenants.list",
+ "requestBody": {
+ "description": "TenantListRequest is the message used for the request to list all tenants.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/TenantListRequest"
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/TenantListResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Tenancy.List(context.Background(), &v1.TenantListRequest{\n PageSize: 20,\n ContinuousToken: \"\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.tenancy.list({\n pageSize: 20,\n continuousToken: \"\",\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/list' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"page_size\": \"10\",\n \"continuous_token\": \"\"\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{id}": {
+ "delete": {
+ "tags": [
+ "Tenancy"
+ ],
+ "summary": "delete tenant",
+ "operationId": "tenants.delete",
+ "parameters": [
+ {
+ "name": "id",
+ "in": "path",
+ "description": "id is the unique identifier of the tenant to be deleted.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/TenantDeleteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Tenancy.Delete(context.Background(), &v1.TenantDeleteRequest {\n Id: \"\"\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.tenancy.delete({\n id: \"\",\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'"
+ }
+ ]
+ }
+ },
+ "/v1/tenants/{tenant_id}/bundle/delete": {
+ "post": {
+ "tags": [
+ "Bundle"
+ ],
+ "summary": "delete bundle",
+ "operationId": "bundle.delete",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "Name of the bundle to be deleted."
+ }
+ },
+ "description": "BundleDeleteRequest is used to request the deletion of a bundle.\nIt contains the tenant_id to specify the tenant and the name of the bundle to be deleted."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/BundleDeleteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Bundle.Delete(context.Background(), &v1.BundleDeleteRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.delete({\n tenantId: \"t1\",\n name: \"organization_created\",\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/delete' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/bundle/read": {
+ "post": {
+ "tags": [
+ "Bundle"
+ ],
+ "summary": "read bundle",
+ "operationId": "bundle.read",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string"
+ }
+ }
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/BundleReadResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Bundle.Read(context.Background(), &v1.BundleReadRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.read({\n tenantId: \"t1\",\n name: \"organization_created\",\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/bundle/write": {
+ "post": {
+ "tags": [
+ "Bundle"
+ ],
+ "summary": "write bundle",
+ "operationId": "bundle.write",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "bundles": {
+ "type": "array",
+ "description": "Contains the bundle data to be written.",
+ "items": {
+ "$ref": "#/components/schemas/DataBundle"
+ }
+ }
+ },
+ "description": "BundleWriteRequest is used to request the writing of a bundle.\nIt contains the tenant_id to identify the tenant and the Bundles object."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/BundleWriteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err := client.Bundle.Write(context.Background(), &v1.BundleWriteRequest{\n TenantId: \"t1\",\n Bundles: []*v1.DataBundle{\n {\n Name: \"organization_created\",\n Arguments: []string{\n \"creatorID\",\n \"organizationID\",\n },\n Operations: []*v1.Operation{\n {\n RelationshipsWrite: []string{\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n },\n AttributesWrite: []string{\n \"organization:{{.organizationID}}$public|boolean:false\",\n },\n },\n },\n },\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.bundle.write({\n tenantId: \"t1\",\n bundles: [\n {\n name: \"organization_created\",\n arguments: [\n \"creatorID\",\n \"organizationID\",\n ],\n operations: [\n {\n relationships_write: [\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n ],\n attributes_write: [\n \"organization:{{.organizationID}}$public|boolean:false\",\n ]\n }\n ]\n }\n ]\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"bundles\": [\n {\n \"name\": \"organization_created\"\n \"arguments\": [\n \"creatorID\",\n \"organizationID\"\n ],\n \"operations\": [\n {\n \"relationships_write\": [\n \"organization:{{.organizationID}}#admin@user:{{.creatorID}}\",\n \"organization:{{.organizationID}}#manager@user:{{.creatorID}}\",\n ],\n \"attributes_write\": [\n \"organization:{{.organizationID}}$public|boolean:false\",\n ],\n },\n ],\n },\n ],\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/data/attributes/read": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "read attributes",
+ "operationId": "data.attributes.read",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/AttributeReadRequestMetadata"
+ },
+ "filter": {
+ "$ref": "#/components/schemas/AttributeFilter"
+ },
+ "page_size": {
+ "type": "integer",
+ "description": "page_size specifies the number of results to return in a single page.\nIf more results are available, a continuous_token is included in the response.",
+ "format": "int64"
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is used in case of paginated reads to get the next page of results."
+ }
+ },
+ "description": "AttributeReadRequest defines the structure of a request for reading attributes.\nIt includes the tenant_id, metadata, attribute filter, page size for pagination, and a continuous token for multi-page results."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/AttributeReadResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.ReadAttributes(context.Background(), & v1.Data.AttributeReadRequest {\n TenantId: \"t1\",\n Metadata: &v1.Data.AttributeReadRequestMetadata {\n SnapToken: \"\"\n },\n Filter: &v1.AttributeFilter {\n Entity: &v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Attributes: []string {\"private\"},\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.readAttributes({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n attributes: [\n \"private\"\n ],\n }\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/attributes/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n attributes: [\n \"private\"\n ],\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/data/delete": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "delete data",
+ "operationId": "data.delete",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "tuple_filter": {
+ "$ref": "#/components/schemas/TupleFilter"
+ },
+ "attribute_filter": {
+ "$ref": "#/components/schemas/AttributeFilter"
+ }
+ },
+ "description": "DataDeleteRequest defines the structure of a request to delete data.\nIt includes the tenant_id and filters for selecting tuples and attributes to be deleted."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/DataDeleteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.Delete(context.Background(), & v1.DataDeleteRequest {\n TenantId: \"t1\",\n Metadata: &v1.DataDeleteRequestMetadata {\n SnapToken: \"\"\n },\n TupleFilter: &v1.TupleFilter {\n Entity: &v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Relation: \"admin\",\n Subject: &v1.SubjectFilter {\n Type: \"user\",\n Id: []string {\"1\"},\n Relation: \"\"\n }}\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.delete({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n tupleFilter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"admin\",\n subject: {\n type: \"user\",\n ids: [\n \"1\"\n ],\n relation: \"\"\n }\n }\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/delete' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"tupleFilter\": {\n \"entity\": {\n \"type\": \"organization\",\n \"ids\": [\n \"1\"\n ]\n },\n \"relation\": \"admin\",\n \"subject\": {\n \"type\": \"user\",\n \"ids\": [\n \"1\"\n ],\n \"relation\": \"\"\n }\n },\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/data/relationships/read": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "read relationships",
+ "operationId": "data.relationships.read",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/RelationshipReadRequestMetadata"
+ },
+ "filter": {
+ "$ref": "#/components/schemas/TupleFilter"
+ },
+ "page_size": {
+ "type": "integer",
+ "description": "page_size specifies the number of results to return in a single page.\nIf more results are available, a continuous_token is included in the response.",
+ "format": "int64"
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is used in case of paginated reads to get the next page of results."
+ }
+ },
+ "description": "RelationshipReadRequest defines the structure of a request for reading relationships.\nIt contains the necessary information such as tenant_id, metadata, and filter for the read operation."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/RelationshipReadResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.ReadRelationships(context.Background(), & v1.Data.RelationshipReadRequest {\n TenantId: \"t1\",\n Metadata: &v1.Data.RelationshipReadRequestMetadata {\n SnapToken: \"\"\n },\n Filter: &v1.TupleFilter {\n Entity: &v1.EntityFilter {\n Type: \"organization\",\n Ids: []string {\"1\"} ,\n },\n Relation: \"member\",\n Subject: &v1.SubjectFilter {\n Type: \"\",\n Id: []string {\"\"},\n Relation: \"\"\n }}\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.readRelationships({\n tenantId: \"t1\",\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"member\",\n subject: {\n type: \"\",\n ids: [],\n relation: \"\"\n }\n }\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/relationships/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n metadata: {\n snap_token: \"\",\n },\n filter: {\n entity: {\n type: \"organization\",\n ids: [\n \"1\"\n ]\n },\n relation: \"member\",\n subject: {\n type: \"\",\n ids: [],\n relation: \"\"\n }\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/data/run-bundle": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "run bundle",
+ "operationId": "bundle.run",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "Name of the bundle to be executed."
+ },
+ "arguments": {
+ "type": "object",
+ "additionalProperties": {
+ "type": "string"
+ },
+ "description": "Additional key-value pairs for execution arguments."
+ }
+ },
+ "description": "BundleRunRequest is used to request the execution of a bundle.\nIt includes tenant_id, the name of the bundle, and additional arguments for execution."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/BundleRunResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "rr, err: = client.Data.RunBundle(context.Background(), &v1.BundleRunRequest{\n TenantId: \"t1\",\n Name: \"organization_created\",\n Arguments: map[string]string{\n \"creatorID\": \"564\",\n \"organizationID\": \"789\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.data.runBundle({\n tenantId: \"t1\",\n name: \"organization_created\",\n arguments: {\n creatorID: \"564\",\n organizationID: \"789\",\n }\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/run-bundle' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"name\": \"organization_created\",\n \"arguments\": {\n \"creatorID\": \"564\",\n \"organizationID\": \"789\",\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/data/write": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "write data",
+ "operationId": "data.write",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/DataWriteRequestMetadata"
+ },
+ "tuples": {
+ "type": "array",
+ "description": "tuples contains the list of tuples (entity-relation-entity triples) that need to be written.",
+ "items": {
+ "$ref": "#/components/schemas/Tuple"
+ }
+ },
+ "attributes": {
+ "type": "array",
+ "description": "attributes contains the list of attributes (entity-attribute-value triples) that need to be written.",
+ "items": {
+ "$ref": "#/components/schemas/Attribute"
+ }
+ }
+ },
+ "description": "DataWriteRequest defines the structure of a request for writing data.\nIt contains the necessary information such as tenant_id, metadata,\ntuples and attributes for the write operation."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/DataWriteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "// Convert the wrapped attribute value into Any proto message\nvalue, err := anypb.New(&v1.BooleanValue{\n Data: true,\n})\nif err != nil {\n // Handle error\n}\n\ncr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{\n TenantId: \"t1\",,\n Metadata: &v1.DataWriteRequestMetadata{\n SchemaVersion: \"\",\n },\n Tuples: []*v1.Attribute{\n {\n Entity: &v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Relation: \"editor\",\n Subject: &v1.Subject{\n Type: \"user\",\n Id: \"1\",\n Relation: \"\",\n },\n },\n },\n Attributes: []*v1.Attribute{\n {\n Entity: &v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Attribute: \"is_private\",\n Value: value,\n },\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const booleanValue = BooleanValue.fromJSON({ data: true });\n\nconst value = Any.fromJSON({\n typeUrl: 'type.googleapis.com/base.v1.BooleanValue',\n value: BooleanValue.encode(booleanValue).finish()\n});\n\nclient.data.write({\n tenantId: \"t1\",\n metadata: {\n schemaVersion: \"\"\n },\n tuples: [{\n entity: {\n type: \"document\",\n id: \"1\"\n },\n relation: \"editor\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n }],\n attributes: [{\n entity: {\n type: \"document\",\n id: \"1\"\n },\n attribute: \"is_private\",\n value: value,\n }]\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n{\n \"metadata\": {\n \"schema_version\": \"\"\n },\n \"tuples\": [\n {\n \"entity\": {\n \"type\": \"document\",\n \"id\": \"1\"\n },\n \"relation\": \"editor\",\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\"\n }\n }\n ],\n \"attributes\": [\n {\n \"entity\": {\n \"type\": \"document\",\n \"id\": \"1\"\n },\n \"attribute\": \"is_private\",\n \"value\": {\n \"@type\": \"type.googleapis.com/base.v1.BooleanValue\",\n \"data\": true\n }\n }\n ]\n}\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/check": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "check api",
+ "operationId": "permissions.check",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionCheckRequestMetadata"
+ },
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "permission": {
+ "type": "string",
+ "description": "The action the user wants to perform on the resource"
+ },
+ "subject": {
+ "$ref": "#/components/schemas/Subject"
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ },
+ "arguments": {
+ "type": "array",
+ "description": "Additional arguments associated with this request.",
+ "items": {
+ "$ref": "#/components/schemas/Argument"
+ }
+ }
+ },
+ "description": "PermissionCheckRequest is the request message for the Check method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/PermissionCheckResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {\n TenantId: \"t1\",\n Metadata: &v1.PermissionCheckRequestMetadata {\n SnapToken: \"\",\n SchemaVersion: \"\",\n Depth: 20,\n },\n Entity: &v1.Entity {\n Type: \"repository\",\n Id: \"1\",\n },\n Permission: \"edit\",\n Subject: &v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n\n if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {\n // RESULT_ALLOWED\n } else {\n // RESULT_DENIED\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.check({\n tenantId: \"t1\", \n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n permission: \"edit\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) => {\n if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {\n console.log(\"RESULT_ALLOWED\")\n } else {\n console.log(\"RESULT_DENIED\")\n }\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"depth\": 20\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"permission\": \"edit\",\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\",\n \"relation\": \"\"\n },\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/expand": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "expand api",
+ "operationId": "permissions.expand",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionExpandRequestMetadata"
+ },
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "permission": {
+ "type": "string",
+ "description": "Name of the permission to be expanded, not required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ },
+ "arguments": {
+ "type": "array",
+ "description": "Additional arguments associated with this request.",
+ "items": {
+ "$ref": "#/components/schemas/Argument"
+ }
+ }
+ },
+ "description": "PermissionExpandRequest is the request message for the Expand method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/PermissionExpandResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.Expand(context.Background(), &v1.PermissionExpandRequest{\n TenantId: \"t1\",\n Metadata: &v1.PermissionExpandRequestMetadata{\n SnapToken: \"\",\n SchemaVersion: \"\",\n },\n Entity: &v1.Entity{\n Type: \"repository\",\n Id: \"1\",\n },\n Permission: \"push\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.expand({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\"\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n permission: \"push\",\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\": {\n \"schema_version\": \"\",\n \"snap_token\": \"\"\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"permission\": \"push\"\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/lookup-entity": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "lookup entity",
+ "operationId": "permissions.lookupEntity",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionLookupEntityRequestMetadata"
+ },
+ "entity_type": {
+ "type": "string",
+ "description": "Type of the entity to lookup, required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ },
+ "permission": {
+ "type": "string",
+ "description": "Name of the permission to check, required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ },
+ "subject": {
+ "$ref": "#/components/schemas/Subject"
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ }
+ },
+ "description": "PermissionLookupEntityRequest is the request message for the LookupEntity method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/PermissionLookupEntityResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {\n TenantId: \"t1\",\n Metadata: & v1.PermissionLookupEntityRequestMetadata {\n SnapToken: \"\"\n SchemaVersion: \"\"\n Depth: 20,\n },\n EntityType: \"document\",\n Permission: \"edit\",\n Subject: & v1.Subject {\n Type: \"user\",\n Id: \"1\",\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.lookupEntity({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entity_type: \"document\",\n permission: \"edit\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) => {\n console.log(response.entity_ids)\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"depth\": 20\n },\n \"entity_type\": \"document\",\n \"permission\": \"edit\",\n \"subject\": {\n \"type\":\"user\",\n \"id\":\"1\"\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/lookup-entity-stream": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "lookup entity stream",
+ "operationId": "permissions.lookupEntityStream",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionLookupEntityRequestMetadata"
+ },
+ "entity_type": {
+ "type": "string",
+ "description": "Type of the entity to lookup, required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ },
+ "permission": {
+ "type": "string",
+ "description": "Name of the permission to check, required, must start with a letter and can include alphanumeric and underscore, max 64 bytes."
+ },
+ "subject": {
+ "$ref": "#/components/schemas/Subject"
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ }
+ },
+ "description": "PermissionLookupEntityRequest is the request message for the LookupEntity method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.(streaming responses)",
+ "content": {
+ "application/json": {
+ "schema": {
+ "title": "Stream result of PermissionLookupEntityStreamResponse",
+ "type": "object",
+ "properties": {
+ "result": {
+ "$ref": "#/components/schemas/PermissionLookupEntityStreamResponse"
+ },
+ "error": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "str, err: = client.Permission.LookupEntityStream(context.Background(), &v1.PermissionLookupEntityRequest {\n Metadata: &v1.PermissionLookupEntityRequestMetadata {\n SnapToken: \"\", \n SchemaVersion: \"\" \n Depth: 50,\n },\n EntityType: \"document\",\n Permission: \"view\",\n Subject: &v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n})\n\n// handle stream response\nfor {\n res, err: = str.Recv()\n\n if err == io.EOF {\n break\n }\n\n // res.EntityId\n}"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const permify = require(\"@permify/permify-node\");\nconst {PermissionLookupEntityStreamResponse} = require(\"@permify/permify-node/dist/src/grpc/generated/base/v1/service\");\n\nfunction main() {\n const client = new permify.grpc.newClient({\n endpoint: \"localhost:3478\",\n })\n\n let res = client.permission.lookupEntityStream({\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n depth: 20\n },\n entityType: \"document\",\n permission: \"view\",\n subject: {\n type: \"user\",\n id: \"1\"\n }\n })\n\n handle(res)\n}\n\nasync function handle(res: AsyncIterable) {\n for await (const response of res) {\n // response.entityId\n }\n}"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/lookup-subject": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "lookup-subject",
+ "operationId": "permissions.lookupSubject",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionLookupSubjectRequestMetadata"
+ },
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "permission": {
+ "type": "string",
+ "description": "Permission to be checked, can be a permission or relation. Required, and must match the pattern \"^([a-zA-Z][a-zA-Z0-9_]{1,62}[a-zA-Z0-9])$\", max 64 bytes."
+ },
+ "subject_reference": {
+ "$ref": "#/components/schemas/RelationReference"
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ }
+ },
+ "description": "PermissionLookupSubjectRequest is the request message for the LookupSubject method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/PermissionLookupSubjectResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.LookupSubject(context.Background(), &v1.PermissionLookupSubjectRequest {\n TenantId: \"t1\",\n Metadata: &v1.PermissionLookupSubjectRequestMetadata{\n SnapToken: \"\",\n SchemaVersion: \"\",\n Depth: 20,\n },\n Entity: &v1.Entity{\n Type: \"document\",\n Id: \"1\",\n },\n Permission: \"edit\",\n SubjectReference: &v1.RelationReference{\n Type: \"user\",\n Relation: \"\",\n }\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.lookupSubject({\n tenantId: \"t1\",\n metadata: {\n snapToken: \"\",\n schemaVersion: \"\"\n depth: 20,\n },\n Entity: {\n Type: \"document\",\n Id: \"1\",\n },\n permission: \"edit\",\n subject_reference: {\n type: \"user\",\n relation: \"\"\n }\n}).then((response) => {\n console.log(response.subject_ids)\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\"\n \"depth\": 20,\n },\n \"entity\": {\n type: \"document\",\n id: \"1'\n },\n \"permission\": \"edit\",\n \"subject_reference\": {\n \"type\": \"user\",\n \"relation\": \"\"\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/permissions/subject-permission": {
+ "post": {
+ "tags": [
+ "Permission"
+ ],
+ "summary": "subject permission",
+ "operationId": "permissions.subjectPermission",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionSubjectPermissionRequestMetadata"
+ },
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "subject": {
+ "$ref": "#/components/schemas/Subject"
+ },
+ "context": {
+ "$ref": "#/components/schemas/Context"
+ }
+ },
+ "description": "PermissionSubjectPermissionRequest is the request message for the SubjectPermission method in the Permission service."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/PermissionSubjectPermissionResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err: = client.Permission.SubjectPermission(context.Background(), &v1.PermissionSubjectPermissionRequest {\n TenantId: \"t1\",\n Metadata: &v1.PermissionSubjectPermissionRequestMetadata {\n SnapToken: \"\",\n SchemaVersion: \"\",\n OnlyPermission: false,\n Depth: 20,\n },\n Entity: &v1.Entity {\n Type: \"repository\",\n Id: \"1\",\n },\n Subject: &v1.Subject {\n Type: \"user\",\n Id: \"1\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.permission.subjectPermission({\n tenantId: \"t1\", \n metadata: {\n snapToken: \"\",\n schemaVersion: \"\",\n onlyPermission: true,\n depth: 20\n },\n entity: {\n type: \"repository\",\n id: \"1\"\n },\n subject: {\n type: \"user\",\n id: \"1\"\n }\n}).then((response) => {\n console.log(response);\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\":{\n \"snap_token\": \"\",\n \"schema_version\": \"\",\n \"only_permission\": true,\n \"depth\": 20\n },\n \"entity\": {\n \"type\": \"repository\",\n \"id\": \"1\"\n },\n \"subject\": {\n \"type\": \"user\",\n \"id\": \"1\",\n \"relation\": \"\"\n },\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/relationships/delete": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "delete relationships",
+ "operationId": "relationships.delete",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "title": "RelationshipDeleteRequest",
+ "type": "object",
+ "properties": {
+ "filter": {
+ "$ref": "#/components/schemas/TupleFilter"
+ }
+ }
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/RelationshipDeleteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/relationships/write": {
+ "post": {
+ "tags": [
+ "Data"
+ ],
+ "summary": "write relationships",
+ "operationId": "relationships.write",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/RelationshipWriteRequestMetadata"
+ },
+ "tuples": {
+ "type": "array",
+ "description": "List of tuples for the request. Must have between 1 and 100 items.",
+ "items": {
+ "$ref": "#/components/schemas/Tuple"
+ }
+ }
+ },
+ "description": "Represents a request to write relationship data."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/RelationshipWriteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/schemas/list": {
+ "post": {
+ "tags": [
+ "Schema"
+ ],
+ "summary": "list schema",
+ "operationId": "schemas.list",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "page_size": {
+ "type": "integer",
+ "description": "page_size is the number of tenants to be returned in the response.\nThe value should be between 1 and 100.",
+ "format": "int64"
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is an optional parameter used for pagination.\nIt should be the value received in the previous response."
+ }
+ },
+ "description": "SchemaListRequest is the request message for the List method in the Schema service.\nIt contains tenant_id for which the schemas are to be listed."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/SchemaListResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.List(context.Background(), &v1.SchemaListRequest {\n TenantId: \"t1\",\n PageSize: \"10\",\n ContinuousToken: \"\",\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.schema.list({\n tenantId: \"t1\",\n continuousToken: \"\"\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"page_size\": \"10\",\n \"continuous_token\": \"\"\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/schemas/read": {
+ "post": {
+ "tags": [
+ "Schema"
+ ],
+ "summary": "read schema",
+ "operationId": "schemas.read",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "metadata": {
+ "$ref": "#/components/schemas/SchemaReadRequestMetadata"
+ }
+ },
+ "description": "SchemaReadRequest is the request message for the Read method in the Schema service.\nIt contains tenant_id and metadata about the schema to be read."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": ""
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.Read(context.Background(), &v1.SchemaReadRequest {\n TenantId: \"t1\",\n Metadata: &v1.SchemaReadRequestMetadata{\n SchemaVersion: \"cnbe6se5fmal18gpc66g\",\n },\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "let res = client.schema.read({\n tenantId: \"t1\",\n metadata: {\n schemaVersion: swResponse.schemaVersion,\n },\n })"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"metadata\": {\n \"schema_version\": \"cnbe6se5fmal18gpc66g\"\n }\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/schemas/write": {
+ "post": {
+ "tags": [
+ "Schema"
+ ],
+ "summary": "write schema",
+ "operationId": "schemas.write",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "schema": {
+ "type": "string",
+ "description": "schema is the string representation of the schema to be written."
+ }
+ },
+ "description": "SchemaWriteRequest is the request message for the Write method in the Schema service.\nIt contains tenant_id and the schema to be written."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/SchemaWriteResponse"
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {\n TenantId: \"t1\",\n Schema: `\n \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n `,\n})"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "client.schema.write({\n tenantId: \"t1\",\n schema: `\n \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n `\n}).then((response) => {\n // handle response\n})"
+ },
+ {
+ "label": "cURL",
+ "lang": "curl",
+ "source": "curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \\\n--header 'Content-Type: application/json' \\\n--data-raw '{\n \"schema\": \"entity user {}\\n\\n entity organization {\\n\\n relation admin @user\\n relation member @user\\n\\n action create_repository = (admin or member)\\n action delete = admin\\n }\\n\\n entity repository {\\n\\n relation owner @user\\n relation parent @organization\\n\\n action push = owner\\n action read = (owner and (parent.admin and parent.member))\\n action delete = (parent.member and (parent.admin or owner))\\n }\"\n}'"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ },
+ "/v1/tenants/{tenant_id}/watch": {
+ "post": {
+ "tags": [
+ "Watch"
+ ],
+ "summary": "watch changes",
+ "operationId": "watch.watch",
+ "parameters": [
+ {
+ "name": "tenant_id",
+ "in": "path",
+ "description": "Identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant t1 for this field. Required, and must match the pattern \\“[a-zA-Z0-9-,]+\\“, max 64 bytes.",
+ "required": true,
+ "schema": {
+ "type": "string"
+ }
+ }
+ ],
+ "requestBody": {
+ "content": {
+ "application/json": {
+ "schema": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ }
+ },
+ "description": "WatchRequest is the request message for the Watch RPC. It contains the\ndetails needed to establish a watch stream."
+ }
+ }
+ },
+ "required": true
+ },
+ "responses": {
+ "200": {
+ "description": "A successful response.(streaming responses)",
+ "content": {
+ "application/json": {
+ "schema": {
+ "title": "Stream result of WatchResponse",
+ "type": "object",
+ "properties": {
+ "result": {
+ "$ref": "#/components/schemas/WatchResponse"
+ },
+ "error": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ }
+ },
+ "default": {
+ "description": "An unexpected error response.",
+ "content": {
+ "application/json": {
+ "schema": {
+ "$ref": "#/components/schemas/Status"
+ }
+ }
+ }
+ }
+ },
+ "x-codeSamples": [
+ {
+ "label": "go",
+ "lang": "go",
+ "source": "cr, err := client.Watch.Watch(context.Background(), &v1.WatchRequest{\n TenantId: \"t1\",\n SnapToken: \"\",\n})\n// handle stream response\nfor {\n res, err := cr.Recv()\n\n if err == io.EOF {\n break\n }\n\n // res.Changes\n}\n"
+ },
+ {
+ "label": "node",
+ "lang": "javascript",
+ "source": "const permify = require(\"@permify/permify-node\");\nconst {WatchResponse} = require(\"@permify/permify-node/dist/src/grpc/generated/base/v1/service\");\n\nfunction main() {\n const client = new permify.grpc.newClient({\n endpoint: \"localhost:3478\",\n })\n\n let res = client.watch.watch({\n tenantId: \"t1\",\n snapToken: \"\"\n })\n\n handle(res)\n}\n\nasync function handle(res: AsyncIterable) {\n for await (const response of res) {\n // response.changes\n }\n}\n"
+ }
+ ],
+ "x-codegen-request-body-name": "body"
+ }
+ }
+ },
+ "components": {
+ "schemas": {
+ "AbstractType": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The fully qualified name of this abstract type."
+ },
+ "parameterTypes": {
+ "type": "array",
+ "description": "Parameter types for this abstract type.",
+ "items": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ }
+ }
+ },
+ "description": "Application defined abstract type."
+ },
+ "Any": {
+ "type": "object",
+ "properties": {
+ "@type": {
+ "type": "string",
+ "description": "A URL/resource name that uniquely identifies the type of the serialized\nprotocol buffer message. This string must contain at least\none \"/\" character. The last segment of the URL's path must represent\nthe fully qualified name of the type (as in\n`path/google.protobuf.Duration`). The name should be in a canonical form\n(e.g., leading \".\" is not accepted).\n\nIn practice, teams usually precompile into the binary all types that they\nexpect it to use in the context of Any. However, for URLs which use the\nscheme `http`, `https`, or no scheme, one can optionally set up a type\nserver that maps type URLs to message definitions as follows:\n\n* If no scheme is provided, `https` is assumed.\n* An HTTP GET on the URL must yield a [google.protobuf.Type][]\n value in binary format, or produce an error.\n* Applications are allowed to cache lookup results based on the\n URL, or have them precompiled into a binary to avoid any\n lookup. Therefore, binary compatibility needs to be preserved\n on changes to types. (Use versioned type names to manage\n breaking changes.)\n\nNote: this functionality is not currently available in the official\nprotobuf release, and it is not used for type URLs beginning with\ntype.googleapis.com.\n\nSchemes other than `http`, `https` (or the empty scheme) might be\nused with implementation specific semantics."
+ }
+ },
+ "additionalProperties": {
+ "type": "object"
+ },
+ "description": "`Any` contains an arbitrary serialized protocol buffer message along with a\nURL that describes the type of the serialized message.\n\nProtobuf library provides support to pack/unpack Any values in the form\nof utility functions or additional generated methods of the Any type.\n\nExample 1: Pack and unpack a message in C++.\n\n Foo foo = ...;\n Any any;\n any.PackFrom(foo);\n ...\n if (any.UnpackTo(&foo)) {\n ...\n }\n\nExample 2: Pack and unpack a message in Java.\n\n Foo foo = ...;\n Any any = Any.pack(foo);\n ...\n if (any.is(Foo.class)) {\n foo = any.unpack(Foo.class);\n }\n\nExample 3: Pack and unpack a message in Python.\n\n foo = Foo(...)\n any = Any()\n any.Pack(foo)\n ...\n if any.Is(Foo.DESCRIPTOR):\n any.Unpack(foo)\n ...\n\nExample 4: Pack and unpack a message in Go\n\n foo := &pb.Foo{...}\n any, err := anypb.New(foo)\n if err != nil {\n ...\n }\n ...\n foo := &pb.Foo{}\n if err := any.UnmarshalTo(foo); err != nil {\n ...\n }\n\nThe pack methods provided by protobuf library will by default use\n'type.googleapis.com/full.type.name' as the type URL and the unpack\nmethods only use the fully qualified type name after the last '/'\nin the type URL, for example \"foo.bar.com/x/y.z\" will yield type\nname \"y.z\".\n\n\nJSON\n\nThe JSON representation of an `Any` value uses the regular\nrepresentation of the deserialized, embedded message, with an\nadditional field `@type` which contains the type URL. Example:\n\n package google.profile;\n message Person {\n string first_name = 1;\n string last_name = 2;\n }\n\n {\n \"@type\": \"type.googleapis.com/google.profile.Person\",\n \"firstName\": ,\n \"lastName\": \n }\n\nIf the embedded message type is well-known and has a custom JSON\nrepresentation, that representation will be embedded adding a field\n`value` which holds the custom JSON in addition to the `@type`\nfield. Example (for message [google.protobuf.Duration][]):\n\n {\n \"@type\": \"type.googleapis.com/google.protobuf.Duration\",\n \"value\": \"1.212s\"\n }"
+ },
+ "Argument": {
+ "type": "object",
+ "properties": {
+ "computedAttribute": {
+ "$ref": "#/components/schemas/ComputedAttribute"
+ },
+ "contextAttribute": {
+ "$ref": "#/components/schemas/ContextAttribute"
+ }
+ },
+ "description": "Argument defines the type of argument in a Call. It can be either a ComputedAttribute or a ContextAttribute."
+ },
+ "Attribute": {
+ "type": "object",
+ "properties": {
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "attribute": {
+ "title": "Name of the attribute",
+ "type": "string"
+ },
+ "value": {
+ "$ref": "#/components/schemas/Any"
+ }
+ },
+ "description": "Attribute represents an attribute of an entity with a specific type and value."
+ },
+ "AttributeDefinition": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The name of the attribute, which follows a specific string pattern and has a maximum byte size."
+ },
+ "type": {
+ "$ref": "#/components/schemas/AttributeType"
+ }
+ },
+ "description": "The AttributeDefinition message provides detailed information about a specific attribute."
+ },
+ "AttributeFilter": {
+ "type": "object",
+ "properties": {
+ "entity": {
+ "$ref": "#/components/schemas/EntityFilter"
+ },
+ "attributes": {
+ "title": "Names of the attributes to be filtered",
+ "type": "array",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "AttributeFilter is used to filter attributes based on the entity and attribute names."
+ },
+ "AttributeReadRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ },
+ "description": "AttributeReadRequestMetadata defines the structure for the metadata of an attribute read request.\nIt includes the snap_token associated with a particular state of the database."
+ },
+ "AttributeReadResponse": {
+ "type": "object",
+ "properties": {
+ "attributes": {
+ "type": "array",
+ "description": "attributes is a list of the attributes retrieved in the read operation.",
+ "items": {
+ "$ref": "#/components/schemas/Attribute"
+ }
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is used in the case of paginated reads to retrieve the next page of results."
+ }
+ },
+ "description": "AttributeReadResponse defines the structure of the response to an attribute read request.\nIt includes the attributes retrieved and a continuous token for handling result pagination."
+ },
+ "AttributeType": {
+ "type": "string",
+ "description": "Enumerates the types of attribute.\n\n - ATTRIBUTE_TYPE_UNSPECIFIED: Not specified attribute type. This is the default value.\n - ATTRIBUTE_TYPE_BOOLEAN: A boolean attribute type.\n - ATTRIBUTE_TYPE_BOOLEAN_ARRAY: A boolean array attribute type.\n - ATTRIBUTE_TYPE_STRING: A string attribute type.\n - ATTRIBUTE_TYPE_STRING_ARRAY: A string array attribute type.\n - ATTRIBUTE_TYPE_INTEGER: An integer attribute type.\n - ATTRIBUTE_TYPE_INTEGER_ARRAY: An integer array attribute type.\n - ATTRIBUTE_TYPE_DOUBLE: A double attribute type.\n - ATTRIBUTE_TYPE_DOUBLE_ARRAY: A double array attribute type.",
+ "default": "ATTRIBUTE_TYPE_UNSPECIFIED",
+ "enum": [
+ "ATTRIBUTE_TYPE_UNSPECIFIED",
+ "ATTRIBUTE_TYPE_BOOLEAN",
+ "ATTRIBUTE_TYPE_BOOLEAN_ARRAY",
+ "ATTRIBUTE_TYPE_STRING",
+ "ATTRIBUTE_TYPE_STRING_ARRAY",
+ "ATTRIBUTE_TYPE_INTEGER",
+ "ATTRIBUTE_TYPE_INTEGER_ARRAY",
+ "ATTRIBUTE_TYPE_DOUBLE",
+ "ATTRIBUTE_TYPE_DOUBLE_ARRAY"
+ ]
+ },
+ "BundleDeleteResponse": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string"
+ }
+ }
+ },
+ "BundleReadResponse": {
+ "type": "object",
+ "properties": {
+ "bundle": {
+ "$ref": "#/components/schemas/DataBundle"
+ }
+ }
+ },
+ "BundleRunResponse": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ },
+ "description": "BundleRunResponse is the response for a BundleRunRequest.\nIt includes a snap_token, which may be used for tracking the execution or its results."
+ },
+ "BundleWriteResponse": {
+ "type": "object",
+ "properties": {
+ "names": {
+ "type": "array",
+ "description": "Identifier or acknowledgment of the written bundle.",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "BundleWriteResponse is the response for a BundleWriteRequest.\nIt includes a name which could be used as an identifier or acknowledgment."
+ },
+ "CheckResult": {
+ "type": "string",
+ "description": "Enumerates results of a check operation.\n\n - CHECK_RESULT_UNSPECIFIED: Not specified check result. This is the default value.\n - CHECK_RESULT_ALLOWED: Represents a successful check (the check allowed the operation).\n - CHECK_RESULT_DENIED: Represents a failed check (the check denied the operation).",
+ "default": "CHECK_RESULT_UNSPECIFIED",
+ "enum": [
+ "CHECK_RESULT_UNSPECIFIED",
+ "CHECK_RESULT_ALLOWED",
+ "CHECK_RESULT_DENIED"
+ ]
+ },
+ "CheckedExpr": {
+ "type": "object",
+ "properties": {
+ "referenceMap": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/v1alpha1.Reference"
+ },
+ "description": "A map from expression ids to resolved references.\n\nThe following entries are in this table:\n\n- An Ident or Select expression is represented here if it resolves to a\n declaration. For instance, if `a.b.c` is represented by\n `select(select(id(a), b), c)`, and `a.b` resolves to a declaration,\n while `c` is a field selection, then the reference is attached to the\n nested select expression (but not to the id or or the outer select).\n In turn, if `a` resolves to a declaration and `b.c` are field selections,\n the reference is attached to the ident expression.\n- Every Call expression has an entry here, identifying the function being\n called.\n- Every CreateStruct expression for a message has an entry, identifying\n the message."
+ },
+ "typeMap": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ },
+ "description": "A map from expression ids to types.\n\nEvery expression node which has a type different than DYN has a mapping\nhere. If an expression has type DYN, it is omitted from this map to save\nspace."
+ },
+ "sourceInfo": {
+ "$ref": "#/components/schemas/SourceInfo"
+ },
+ "exprVersion": {
+ "type": "string",
+ "description": "The expr version indicates the major / minor version number of the `expr`\nrepresentation.\n\nThe most common reason for a version change will be to indicate to the CEL\nruntimes that transformations have been performed on the expr during static\nanalysis. In some cases, this will save the runtime the work of applying\nthe same or similar transformations prior to evaluation."
+ },
+ "expr": {
+ "$ref": "#/components/schemas/Expr"
+ }
+ },
+ "description": "A CEL expression which has been successfully type checked."
+ },
+ "Child": {
+ "type": "object",
+ "properties": {
+ "leaf": {
+ "$ref": "#/components/schemas/Leaf"
+ },
+ "rewrite": {
+ "$ref": "#/components/schemas/Rewrite"
+ }
+ },
+ "description": "Child represents a node in the permission tree."
+ },
+ "Comprehension": {
+ "type": "object",
+ "properties": {
+ "iterVar": {
+ "type": "string",
+ "description": "The name of the iteration variable."
+ },
+ "iterRange": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "accuVar": {
+ "type": "string",
+ "description": "The name of the variable used for accumulation of the result."
+ },
+ "accuInit": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "loopCondition": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "loopStep": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "result": {
+ "$ref": "#/components/schemas/Expr"
+ }
+ },
+ "description": "A comprehension expression applied to a list or map.\n\nComprehensions are not part of the core syntax, but enabled with macros.\nA macro matches a specific call signature within a parsed AST and replaces\nthe call with an alternate AST block. Macro expansion happens at parse\ntime.\n\nThe following macros are supported within CEL:\n\nAggregate type macros may be applied to all elements in a list or all keys\nin a map:\n\n* `all`, `exists`, `exists_one` - test a predicate expression against\n the inputs and return `true` if the predicate is satisfied for all,\n any, or only one value `list.all(x, x < 10)`.\n* `filter` - test a predicate expression against the inputs and return\n the subset of elements which satisfy the predicate:\n `payments.filter(p, p > 1000)`.\n* `map` - apply an expression to all elements in the input and return the\n output aggregate type: `[1, 2, 3].map(i, i * i)`.\n\nThe `has(m.x)` macro tests whether the property `x` is present in struct\n`m`. The semantics of this macro depend on the type of `m`. For proto2\nmessages `has(m.x)` is defined as 'defined, but not set`. For proto3, the\nmacro tests whether the property is set to its default. For map and struct\ntypes, the macro tests whether the property `x` is defined on `m`."
+ },
+ "ComputedAttribute": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "title": "Name of the computed attribute",
+ "type": "string"
+ }
+ },
+ "description": "ComputedAttribute defines a computed attribute which includes its name."
+ },
+ "ComputedUserSet": {
+ "type": "object",
+ "properties": {
+ "relation": {
+ "title": "Relation name",
+ "type": "string"
+ }
+ },
+ "description": "ComputedUserSet defines a set of computed users which includes the relation name."
+ },
+ "Constant": {
+ "type": "object",
+ "properties": {
+ "nullValue": {
+ "type": "string",
+ "description": "null value."
+ },
+ "boolValue": {
+ "type": "boolean",
+ "description": "boolean value."
+ },
+ "int64Value": {
+ "type": "string",
+ "description": "int64 value.",
+ "format": "int64"
+ },
+ "uint64Value": {
+ "type": "string",
+ "description": "uint64 value.",
+ "format": "uint64"
+ },
+ "doubleValue": {
+ "type": "number",
+ "description": "double value.",
+ "format": "double"
+ },
+ "stringValue": {
+ "type": "string",
+ "description": "string value."
+ },
+ "bytesValue": {
+ "pattern": "^(?:[A-Za-z0-9+/]{4})*(?:[A-Za-z0-9+/]{2}==|[A-Za-z0-9+/]{3}=)?$",
+ "type": "string",
+ "description": "bytes value.",
+ "format": "byte"
+ },
+ "durationValue": {
+ "type": "string",
+ "description": "protobuf.Duration value.\n\nDeprecated: duration is no longer considered a builtin cel type."
+ },
+ "timestampValue": {
+ "type": "string",
+ "description": "protobuf.Timestamp value.\n\nDeprecated: timestamp is no longer considered a builtin cel type.",
+ "format": "date-time"
+ }
+ },
+ "description": "Represents a primitive literal.\n\nNamed 'Constant' here for backwards compatibility.\n\nThis is similar as the primitives supported in the well-known type\n`google.protobuf.Value`, but richer so it can represent CEL's full range of\nprimitives.\n\nLists and structs are not included as constants as these aggregate types may\ncontain [Expr][google.api.expr.v1alpha1.Expr] elements which require evaluation and are thus not constant.\n\nExamples of literals include: `\"hello\"`, `b'bytes'`, `1u`, `4.2`, `-2`,\n`true`, `null`."
+ },
+ "Context": {
+ "type": "object",
+ "properties": {
+ "tuples": {
+ "type": "array",
+ "description": "A repeated field of tuples involved in the operation.",
+ "items": {
+ "$ref": "#/components/schemas/Tuple"
+ }
+ },
+ "attributes": {
+ "type": "array",
+ "description": "A repeated field of attributes associated with the operation.",
+ "items": {
+ "$ref": "#/components/schemas/Attribute"
+ }
+ },
+ "data": {
+ "type": "object",
+ "properties": {},
+ "description": "Additional data associated with the context."
+ }
+ },
+ "description": "Context encapsulates the information related to a single operation,\nincluding the tuples involved and the associated attributes."
+ },
+ "ContextAttribute": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "title": "Name of the context attribute",
+ "type": "string"
+ }
+ },
+ "description": "ContextAttribute defines a context attribute which includes its name."
+ },
+ "CreateList": {
+ "type": "object",
+ "properties": {
+ "elements": {
+ "type": "array",
+ "description": "The elements part of the list.",
+ "items": {
+ "$ref": "#/components/schemas/Expr"
+ }
+ },
+ "optionalIndices": {
+ "type": "array",
+ "description": "The indices within the elements list which are marked as optional\nelements.\n\nWhen an optional-typed value is present, the value it contains\nis included in the list. If the optional-typed value is absent, the list\nelement is omitted from the CreateList result.",
+ "items": {
+ "type": "integer",
+ "format": "int32"
+ }
+ }
+ },
+ "description": "A list creation expression.\n\nLists may either be homogenous, e.g. `[1, 2, 3]`, or heterogeneous, e.g.\n`dyn([1, 'hello', 2.0])`"
+ },
+ "CreateStruct": {
+ "type": "object",
+ "properties": {
+ "messageName": {
+ "type": "string",
+ "description": "The type name of the message to be created, empty when creating map\nliterals."
+ },
+ "entries": {
+ "type": "array",
+ "description": "The entries in the creation expression.",
+ "items": {
+ "$ref": "#/components/schemas/Entry"
+ }
+ }
+ },
+ "description": "A map or message creation expression.\n\nMaps are constructed as `{'key_name': 'value'}`. Message construction is\nsimilar, but prefixed with a type name and composed of field ids:\n`types.MyType{field_id: 'value'}`."
+ },
+ "DataBundle": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "'name' is a simple string field representing the name of the DataBundle."
+ },
+ "arguments": {
+ "type": "array",
+ "description": "'arguments' is a repeated field, which means it can contain multiple strings.\nThese are used to store a list of arguments related to the DataBundle.",
+ "items": {
+ "type": "string"
+ }
+ },
+ "operations": {
+ "type": "array",
+ "description": "'operations' is a repeated field containing multiple Operation messages.\nEach Operation represents a specific action or set of actions to be performed.",
+ "items": {
+ "$ref": "#/components/schemas/v1.Operation"
+ }
+ }
+ },
+ "description": "DataBundle is a message representing a bundle of data, which includes a name,\na list of arguments, and a series of operations."
+ },
+ "DataChange": {
+ "type": "object",
+ "properties": {
+ "operation": {
+ "$ref": "#/components/schemas/DataChange.Operation"
+ },
+ "tuple": {
+ "$ref": "#/components/schemas/Tuple"
+ },
+ "attribute": {
+ "$ref": "#/components/schemas/Attribute"
+ }
+ },
+ "description": "DataChange represents a single change in data, with an operation type and the actual change which could be a tuple or an attribute."
+ },
+ "DataChange.Operation": {
+ "type": "string",
+ "description": " - OPERATION_UNSPECIFIED: Default operation, not specified.\n - OPERATION_CREATE: Creation operation.\n - OPERATION_DELETE: Deletion operation.",
+ "default": "OPERATION_UNSPECIFIED",
+ "enum": [
+ "OPERATION_UNSPECIFIED",
+ "OPERATION_CREATE",
+ "OPERATION_DELETE"
+ ]
+ },
+ "DataChanges": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snapshot token."
+ },
+ "data_changes": {
+ "type": "array",
+ "description": "The list of data changes.",
+ "items": {
+ "$ref": "#/components/schemas/DataChange"
+ }
+ }
+ },
+ "description": "DataChanges represent changes in data with a snap token and a list of data change objects."
+ },
+ "DataDeleteResponse": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ },
+ "description": "DataDeleteResponse defines the structure of the response to a data delete request.\nIt includes a snap_token representing the state of the database after the deletion."
+ },
+ "DataWriteRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "schema_version represents the version of the schema for the data being written."
+ }
+ },
+ "description": "DataWriteRequestMetadata defines the structure of metadata for a write request.\nIt includes the schema version of the data to be written."
+ },
+ "DataWriteResponse": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ }
+ },
+ "description": "DataWriteResponse defines the structure of the response after writing data.\nIt contains the snap_token generated after the write operation."
+ },
+ "Entity": {
+ "type": "object",
+ "properties": {
+ "type": {
+ "type": "string"
+ },
+ "id": {
+ "type": "string"
+ }
+ },
+ "description": "Entity represents an entity with a type and an identifier."
+ },
+ "EntityDefinition": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The name of the entity, which follows a specific string pattern and has a maximum byte size."
+ },
+ "relations": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/RelationDefinition"
+ },
+ "description": "Map of relation definitions within this entity. The key is the relation name, and the value is the RelationDefinition."
+ },
+ "permissions": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/PermissionDefinition"
+ },
+ "description": "Map of permission definitions within this entity. The key is the permission name, and the value is the PermissionDefinition."
+ },
+ "attributes": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/AttributeDefinition"
+ },
+ "description": "Map of attribute definitions within this entity. The key is the attribute name, and the value is the AttributeDefinition."
+ },
+ "references": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/EntityDefinition.Reference"
+ },
+ "description": "Map of references indicating whether a string pertains to a relation, permission, or attribute."
+ }
+ },
+ "description": "The EntityDefinition message provides detailed information about a specific entity."
+ },
+ "EntityDefinition.Reference": {
+ "type": "string",
+ "description": "The Reference enum specifies whether a name pertains to a relation, permission, or attribute.\n\n - REFERENCE_UNSPECIFIED: Default, unspecified reference.\n - REFERENCE_RELATION: Indicates that the name refers to a relation.\n - REFERENCE_PERMISSION: Indicates that the name refers to a permission.\n - REFERENCE_ATTRIBUTE: Indicates that the name refers to an attribute.",
+ "default": "REFERENCE_UNSPECIFIED",
+ "enum": [
+ "REFERENCE_UNSPECIFIED",
+ "REFERENCE_RELATION",
+ "REFERENCE_PERMISSION",
+ "REFERENCE_ATTRIBUTE"
+ ]
+ },
+ "EntityFilter": {
+ "type": "object",
+ "properties": {
+ "type": {
+ "title": "Type of the entity",
+ "type": "string"
+ },
+ "ids": {
+ "title": "List of entity IDs",
+ "type": "array",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "EntityFilter is used to filter entities based on the type and ids."
+ },
+ "Entry": {
+ "type": "object",
+ "properties": {
+ "id": {
+ "type": "string",
+ "description": "Required. An id assigned to this node by the parser which is unique\nin a given expression tree. This is used to associate type\ninformation and other attributes to the node.",
+ "format": "int64"
+ },
+ "fieldKey": {
+ "type": "string",
+ "description": "The field key for a message creator statement."
+ },
+ "mapKey": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "value": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "optionalEntry": {
+ "type": "boolean",
+ "description": "Whether the key-value pair is optional."
+ }
+ },
+ "description": "Represents an entry."
+ },
+ "Expand": {
+ "type": "object",
+ "properties": {
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "permission": {
+ "type": "string",
+ "description": "permission is the permission applied to the entity."
+ },
+ "arguments": {
+ "type": "array",
+ "description": "arguments are the additional information or context used to evaluate permissions.",
+ "items": {
+ "$ref": "#/components/schemas/Argument"
+ }
+ },
+ "expand": {
+ "$ref": "#/components/schemas/ExpandTreeNode"
+ },
+ "leaf": {
+ "$ref": "#/components/schemas/ExpandLeaf"
+ }
+ },
+ "description": "Expand is used to define a hierarchical structure for permissions.\nIt has an entity, permission, and arguments. The node can be either another hierarchical structure or a set of subjects."
+ },
+ "ExpandLeaf": {
+ "type": "object",
+ "properties": {
+ "subjects": {
+ "$ref": "#/components/schemas/Subjects"
+ },
+ "values": {
+ "$ref": "#/components/schemas/Values"
+ },
+ "value": {
+ "$ref": "#/components/schemas/Any"
+ }
+ },
+ "description": "ExpandLeaf is the leaf node of an Expand tree and can be either a set of Subjects or a set of Values."
+ },
+ "ExpandTreeNode": {
+ "type": "object",
+ "properties": {
+ "operation": {
+ "$ref": "#/components/schemas/ExpandTreeNode.Operation"
+ },
+ "children": {
+ "title": "The children of this tree node",
+ "type": "array",
+ "items": {
+ "$ref": "#/components/schemas/Expand"
+ }
+ }
+ },
+ "description": "ExpandTreeNode represents a node in an expansion tree with a specific operation and its children."
+ },
+ "ExpandTreeNode.Operation": {
+ "type": "string",
+ "description": "Operation is an enum representing the type of operation to be applied on the tree node.",
+ "default": "OPERATION_UNSPECIFIED",
+ "enum": [
+ "OPERATION_UNSPECIFIED",
+ "OPERATION_UNION",
+ "OPERATION_INTERSECTION",
+ "OPERATION_EXCLUSION"
+ ]
+ },
+ "Expr": {
+ "type": "object",
+ "properties": {
+ "id": {
+ "type": "string",
+ "description": "Required. An id assigned to this node by the parser which is unique in a\ngiven expression tree. This is used to associate type information and other\nattributes to a node in the parse tree.",
+ "format": "int64"
+ },
+ "constExpr": {
+ "$ref": "#/components/schemas/Constant"
+ },
+ "identExpr": {
+ "$ref": "#/components/schemas/Ident"
+ },
+ "selectExpr": {
+ "$ref": "#/components/schemas/Select"
+ },
+ "callExpr": {
+ "$ref": "#/components/schemas/Expr.Call"
+ },
+ "listExpr": {
+ "$ref": "#/components/schemas/CreateList"
+ },
+ "structExpr": {
+ "$ref": "#/components/schemas/CreateStruct"
+ },
+ "comprehensionExpr": {
+ "$ref": "#/components/schemas/Comprehension"
+ }
+ },
+ "description": "An abstract representation of a common expression.\n\nExpressions are abstractly represented as a collection of identifiers,\nselect statements, function calls, literals, and comprehensions. All\noperators with the exception of the '.' operator are modelled as function\ncalls. This makes it easy to represent new operators into the existing AST.\n\nAll references within expressions must resolve to a [Decl][google.api.expr.v1alpha1.Decl] provided at\ntype-check for an expression to be valid. A reference may either be a bare\nidentifier `name` or a qualified identifier `google.api.name`. References\nmay either refer to a value or a function declaration.\n\nFor example, the expression `google.api.name.startsWith('expr')` references\nthe declaration `google.api.name` within a [Expr.Select][google.api.expr.v1alpha1.Expr.Select] expression, and\nthe function declaration `startsWith`."
+ },
+ "Expr.Call": {
+ "type": "object",
+ "properties": {
+ "target": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "function": {
+ "type": "string",
+ "description": "Required. The name of the function or method being called."
+ },
+ "args": {
+ "type": "array",
+ "description": "The arguments.",
+ "items": {
+ "$ref": "#/components/schemas/Expr"
+ }
+ }
+ },
+ "description": "A call expression, including calls to predefined functions and operators.\n\nFor example, `value == 10`, `size(map_value)`."
+ },
+ "FunctionType": {
+ "type": "object",
+ "properties": {
+ "resultType": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ },
+ "argTypes": {
+ "type": "array",
+ "description": "Argument types of the function.",
+ "items": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ }
+ }
+ },
+ "description": "Function type with result and arg types."
+ },
+ "Ident": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "Required. Holds a single, unqualified identifier, possibly preceded by a\n'.'.\n\nQualified names are represented by the [Expr.Select][google.api.expr.v1alpha1.Expr.Select] expression."
+ }
+ },
+ "description": "An identifier expression. e.g. `request`."
+ },
+ "Leaf": {
+ "type": "object",
+ "properties": {
+ "computedUserSet": {
+ "$ref": "#/components/schemas/ComputedUserSet"
+ },
+ "tupleToUserSet": {
+ "$ref": "#/components/schemas/TupleToUserSet"
+ },
+ "computedAttribute": {
+ "$ref": "#/components/schemas/ComputedAttribute"
+ },
+ "call": {
+ "$ref": "#/components/schemas/v1.Call"
+ }
+ },
+ "description": "Leaf represents a leaf node in the permission tree."
+ },
+ "ListType": {
+ "type": "object",
+ "properties": {
+ "elemType": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ }
+ },
+ "description": "List type with typed elements, e.g. `list`."
+ },
+ "MapType": {
+ "type": "object",
+ "properties": {
+ "keyType": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ },
+ "valueType": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ }
+ },
+ "description": "Map type with parameterized key and value types, e.g. `map`."
+ },
+ "NullValue": {
+ "type": "string",
+ "description": "`NullValue` is a singleton enumeration to represent the null value for the\n`Value` type union.\n\n The JSON representation for `NullValue` is JSON `null`.\n\n - NULL_VALUE: Null value.",
+ "default": "NULL_VALUE",
+ "enum": [
+ "NULL_VALUE"
+ ]
+ },
+ "PermissionCheckRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "Version of the schema."
+ },
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ },
+ "depth": {
+ "type": "integer",
+ "description": "Query limit when if recursive database queries got in loop",
+ "format": "int32"
+ }
+ },
+ "description": "PermissionCheckRequestMetadata metadata for the PermissionCheckRequest."
+ },
+ "PermissionCheckResponse": {
+ "type": "object",
+ "properties": {
+ "can": {
+ "$ref": "#/components/schemas/CheckResult"
+ },
+ "metadata": {
+ "$ref": "#/components/schemas/PermissionCheckResponseMetadata"
+ }
+ },
+ "description": "PermissionCheckResponse is the response message for the Check method in the Permission service."
+ },
+ "PermissionCheckResponseMetadata": {
+ "type": "object",
+ "properties": {
+ "check_count": {
+ "type": "integer",
+ "description": "The count of the checks performed.",
+ "format": "int32"
+ }
+ },
+ "description": "PermissionCheckResponseMetadata metadata for the PermissionCheckResponse."
+ },
+ "PermissionDefinition": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The name of the permission, which follows a specific string pattern and has a maximum byte size."
+ },
+ "child": {
+ "$ref": "#/components/schemas/Child"
+ }
+ },
+ "description": "The PermissionDefinition message provides detailed information about a specific permission."
+ },
+ "PermissionExpandRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "Version of the schema."
+ },
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ }
+ },
+ "description": "PermissionExpandRequestMetadata metadata for the PermissionExpandRequest."
+ },
+ "PermissionExpandResponse": {
+ "type": "object",
+ "properties": {
+ "tree": {
+ "$ref": "#/components/schemas/Expand"
+ }
+ },
+ "description": "PermissionExpandResponse is the response message for the Expand method in the Permission service."
+ },
+ "PermissionLookupEntityRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "Version of the schema."
+ },
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ },
+ "depth": {
+ "type": "integer",
+ "description": "Query limit when if recursive database queries got in loop.",
+ "format": "int32"
+ }
+ },
+ "description": "PermissionLookupEntityRequestMetadata metadata for the PermissionLookupEntityRequest."
+ },
+ "PermissionLookupEntityResponse": {
+ "type": "object",
+ "properties": {
+ "entity_ids": {
+ "type": "array",
+ "description": "List of identifiers for entities that match the lookup.",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "PermissionLookupEntityResponse is the response message for the LookupEntity method in the Permission service."
+ },
+ "PermissionLookupEntityStreamResponse": {
+ "type": "object",
+ "properties": {
+ "entity_id": {
+ "type": "string",
+ "description": "Identifier for an entity that matches the lookup."
+ }
+ },
+ "description": "PermissionLookupEntityStreamResponse is the response message for the LookupEntityStream method in the Permission service."
+ },
+ "PermissionLookupSubjectRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "Version of the schema."
+ },
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ },
+ "depth": {
+ "type": "integer",
+ "description": "Query limit when if recursive database queries got in loop.",
+ "format": "int32"
+ }
+ },
+ "description": "PermissionLookupSubjectRequestMetadata metadata for the PermissionLookupSubjectRequest."
+ },
+ "PermissionLookupSubjectResponse": {
+ "type": "object",
+ "properties": {
+ "subject_ids": {
+ "type": "array",
+ "description": "List of identifiers for subjects that match the lookup.",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "PermissionLookupSubjectResponse is the response message for the LookupSubject method in the Permission service."
+ },
+ "PermissionSubjectPermissionRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "Version of the schema."
+ },
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)."
+ },
+ "only_permission": {
+ "type": "boolean",
+ "description": "Whether to only check permissions."
+ },
+ "depth": {
+ "type": "integer",
+ "description": "Query limit when if recursive database queries got in loop.",
+ "format": "int32"
+ }
+ },
+ "description": "PermissionSubjectPermissionRequestMetadata metadata for the PermissionSubjectPermissionRequest."
+ },
+ "PermissionSubjectPermissionResponse": {
+ "type": "object",
+ "properties": {
+ "results": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/CheckResult"
+ },
+ "description": "Map of results for each permission check."
+ }
+ },
+ "description": "PermissionSubjectPermissionResponse is the response message for the SubjectPermission method in the Permission service."
+ },
+ "PrimitiveType": {
+ "type": "string",
+ "description": "CEL primitive types.\n\n - PRIMITIVE_TYPE_UNSPECIFIED: Unspecified type.\n - BOOL: Boolean type.\n - INT64: Int64 type.\n\nProto-based integer values are widened to int64.\n - UINT64: Uint64 type.\n\nProto-based unsigned integer values are widened to uint64.\n - DOUBLE: Double type.\n\nProto-based float values are widened to double values.\n - STRING: String type.\n - BYTES: Bytes type.",
+ "default": "PRIMITIVE_TYPE_UNSPECIFIED",
+ "enum": [
+ "PRIMITIVE_TYPE_UNSPECIFIED",
+ "BOOL",
+ "INT64",
+ "UINT64",
+ "DOUBLE",
+ "STRING",
+ "BYTES"
+ ]
+ },
+ "RelationDefinition": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The name of the relation, which follows a specific string pattern and has a maximum byte size."
+ },
+ "relationReferences": {
+ "type": "array",
+ "description": "A list of references to other relations.",
+ "items": {
+ "$ref": "#/components/schemas/RelationReference"
+ }
+ }
+ },
+ "description": "The RelationDefinition message provides detailed information about a specific relation."
+ },
+ "RelationReference": {
+ "type": "object",
+ "properties": {
+ "type": {
+ "type": "string",
+ "description": "The type of the referenced entity, which follows a specific string pattern and has a maximum byte size."
+ },
+ "relation": {
+ "type": "string",
+ "description": "The name of the referenced relation, which follows a specific string pattern and has a maximum byte size."
+ }
+ },
+ "description": "The RelationReference message provides a reference to a specific relation."
+ },
+ "RelationshipDeleteResponse": {
+ "title": "RelationshipDeleteResponse",
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ }
+ },
+ "RelationshipReadRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ },
+ "description": "RelationshipReadRequestMetadata defines the structure of the metadata for a read request focused on relationships.\nIt includes the snap_token associated with a particular state of the database."
+ },
+ "RelationshipReadResponse": {
+ "type": "object",
+ "properties": {
+ "tuples": {
+ "type": "array",
+ "description": "tuples is a list of the relationships retrieved in the read operation, represented as entity-relation-entity triples.",
+ "items": {
+ "$ref": "#/components/schemas/Tuple"
+ }
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is used in the case of paginated reads to retrieve the next page of results."
+ }
+ },
+ "description": "RelationshipReadResponse defines the structure of the response after reading relationships.\nIt includes the tuples representing the relationships and a continuous token for handling result pagination."
+ },
+ "RelationshipWriteRequestMetadata": {
+ "title": "RelationshipWriteRequestMetadata",
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string"
+ }
+ }
+ },
+ "RelationshipWriteResponse": {
+ "title": "RelationshipWriteResponse",
+ "type": "object",
+ "properties": {
+ "snap_token": {
+ "type": "string",
+ "description": "The snap token to avoid stale cache, see more details on [Snap Tokens](../../operations/snap-tokens)"
+ }
+ }
+ },
+ "Rewrite": {
+ "type": "object",
+ "properties": {
+ "rewriteOperation": {
+ "$ref": "#/components/schemas/Rewrite.Operation"
+ },
+ "children": {
+ "type": "array",
+ "description": "A list of children that are operated upon by the rewrite operation.",
+ "items": {
+ "$ref": "#/components/schemas/Child"
+ }
+ }
+ },
+ "description": "The Rewrite message represents a specific rewrite operation.\nThis operation could be one of the following: union, intersection, or exclusion."
+ },
+ "Rewrite.Operation": {
+ "type": "string",
+ "description": "Operation enum includes potential rewrite operations.\nOPERATION_UNION: Represents a union operation.\nOPERATION_INTERSECTION: Represents an intersection operation.\nOPERATION_EXCLUSION: Represents an exclusion operation.\n\n - OPERATION_UNSPECIFIED: Default, unspecified operation.\n - OPERATION_UNION: Represents a union operation.\n - OPERATION_INTERSECTION: Represents an intersection operation.\n - OPERATION_EXCLUSION: Represents an exclusion operation.",
+ "default": "OPERATION_UNSPECIFIED",
+ "enum": [
+ "OPERATION_UNSPECIFIED",
+ "OPERATION_UNION",
+ "OPERATION_INTERSECTION",
+ "OPERATION_EXCLUSION"
+ ]
+ },
+ "RuleDefinition": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The name of the rule, which follows a specific string pattern and has a maximum byte size."
+ },
+ "arguments": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/AttributeType"
+ },
+ "description": "Map of arguments for this rule. The key is the attribute name, and the value is the AttributeType."
+ },
+ "expression": {
+ "$ref": "#/components/schemas/CheckedExpr"
+ }
+ },
+ "description": "The RuleDefinition message provides detailed information about a specific rule."
+ },
+ "SchemaDefinition": {
+ "type": "object",
+ "properties": {
+ "entityDefinitions": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/EntityDefinition"
+ },
+ "description": "Map of entity definitions. The key is the entity name, and the value is the corresponding EntityDefinition."
+ },
+ "ruleDefinitions": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/RuleDefinition"
+ },
+ "description": "Map of rule definitions. The key is the rule name, and the value is the corresponding RuleDefinition."
+ },
+ "references": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/SchemaDefinition.Reference"
+ },
+ "description": "Map of references to signify whether a string refers to an entity or a rule."
+ }
+ },
+ "description": "The SchemaDefinition message provides definitions for entities and rules,\nand includes references to clarify whether a name refers to an entity or a rule."
+ },
+ "SchemaDefinition.Reference": {
+ "type": "string",
+ "description": "The Reference enum helps distinguish whether a name corresponds to an entity or a rule.\n\n - REFERENCE_UNSPECIFIED: Default, unspecified reference.\n - REFERENCE_ENTITY: Indicates that the name refers to an entity.\n - REFERENCE_RULE: Indicates that the name refers to a rule.",
+ "default": "REFERENCE_UNSPECIFIED",
+ "enum": [
+ "REFERENCE_UNSPECIFIED",
+ "REFERENCE_ENTITY",
+ "REFERENCE_RULE"
+ ]
+ },
+ "SchemaList": {
+ "title": "SchemaList provides a list of schema versions with their corresponding creation timestamps",
+ "type": "object",
+ "properties": {
+ "version": {
+ "type": "string"
+ },
+ "created_at": {
+ "type": "string"
+ }
+ }
+ },
+ "SchemaListResponse": {
+ "title": "SchemaListResponse is the response message for the List method in the Schema service.\nIt returns a paginated list of schemas",
+ "type": "object",
+ "properties": {
+ "head": {
+ "title": "head of the schemas is the latest version available for the tenant",
+ "type": "string"
+ },
+ "schemas": {
+ "title": "list of schema versions with creation timestamps",
+ "type": "array",
+ "items": {
+ "$ref": "#/components/schemas/SchemaList"
+ }
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is a string that can be used to paginate and retrieve the next set of results."
+ }
+ }
+ },
+ "SchemaReadRequestMetadata": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "schema_version is the string that identifies the version of the schema to be read."
+ }
+ },
+ "description": "SchemaReadRequestMetadata provides additional information for the Schema Read request.\nIt contains schema_version to specify which version of the schema should be read."
+ },
+ "SchemaReadResponse": {
+ "type": "object",
+ "properties": {
+ "schema": {
+ "$ref": "#/components/schemas/SchemaDefinition"
+ }
+ },
+ "description": "SchemaReadResponse is the response message for the Read method in the Schema service.\nIt returns the requested schema."
+ },
+ "SchemaWriteResponse": {
+ "type": "object",
+ "properties": {
+ "schema_version": {
+ "type": "string",
+ "description": "schema_version is the string that identifies the version of the written schema."
+ }
+ },
+ "description": "SchemaWriteResponse is the response message for the Write method in the Schema service.\nIt returns the version of the written schema."
+ },
+ "Select": {
+ "type": "object",
+ "properties": {
+ "operand": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "field": {
+ "type": "string",
+ "description": "Required. The name of the field to select.\n\nFor example, in the select expression `request.auth`, the `auth` portion\nof the expression would be the `field`."
+ },
+ "testOnly": {
+ "type": "boolean",
+ "description": "Whether the select is to be interpreted as a field presence test.\n\nThis results from the macro `has(request.auth)`."
+ }
+ },
+ "description": "A field selection expression. e.g. `request.auth`."
+ },
+ "SourceInfo": {
+ "type": "object",
+ "properties": {
+ "syntaxVersion": {
+ "type": "string",
+ "description": "The syntax version of the source, e.g. `cel1`."
+ },
+ "location": {
+ "type": "string",
+ "description": "The location name. All position information attached to an expression is\nrelative to this location.\n\nThe location could be a file, UI element, or similar. For example,\n`acme/app/AnvilPolicy.cel`."
+ },
+ "lineOffsets": {
+ "type": "array",
+ "description": "Monotonically increasing list of code point offsets where newlines\n`\\n` appear.\n\nThe line number of a given position is the index `i` where for a given\n`id` the `line_offsets[i] < id_positions[id] < line_offsets[i+1]`. The\ncolumn may be derivd from `id_positions[id] - line_offsets[i]`.",
+ "items": {
+ "type": "integer",
+ "format": "int32"
+ }
+ },
+ "positions": {
+ "type": "object",
+ "additionalProperties": {
+ "type": "integer",
+ "format": "int32"
+ },
+ "description": "A map from the parse node id (e.g. `Expr.id`) to the code point offset\nwithin the source."
+ },
+ "macroCalls": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/Expr"
+ },
+ "description": "A map from the parse node id where a macro replacement was made to the\ncall `Expr` that resulted in a macro expansion.\n\nFor example, `has(value.field)` is a function call that is replaced by a\n`test_only` field selection in the AST. Likewise, the call\n`list.exists(e, e > 10)` translates to a comprehension expression. The key\nin the map corresponds to the expression id of the expanded macro, and the\nvalue is the call `Expr` that was replaced."
+ }
+ },
+ "description": "Source information collected at parse time."
+ },
+ "Status": {
+ "type": "object",
+ "properties": {
+ "code": {
+ "type": "integer",
+ "format": "int32"
+ },
+ "message": {
+ "type": "string"
+ },
+ "details": {
+ "type": "array",
+ "items": {
+ "$ref": "#/components/schemas/Any"
+ }
+ }
+ }
+ },
+ "Subject": {
+ "type": "object",
+ "properties": {
+ "type": {
+ "type": "string"
+ },
+ "id": {
+ "type": "string"
+ },
+ "relation": {
+ "type": "string"
+ }
+ },
+ "description": "Subject represents an entity subject with a type, an identifier, and a relation."
+ },
+ "SubjectFilter": {
+ "type": "object",
+ "properties": {
+ "type": {
+ "title": "Type of the subject",
+ "type": "string"
+ },
+ "ids": {
+ "title": "List of subject IDs",
+ "type": "array",
+ "items": {
+ "type": "string"
+ }
+ },
+ "relation": {
+ "type": "string"
+ }
+ },
+ "description": "SubjectFilter is used to filter subjects based on the type, ids and relation."
+ },
+ "Subjects": {
+ "type": "object",
+ "properties": {
+ "subjects": {
+ "type": "array",
+ "description": "A list of subjects.",
+ "items": {
+ "$ref": "#/components/schemas/Subject"
+ }
+ }
+ },
+ "description": "Subjects holds a repeated field of Subject type."
+ },
+ "Tenant": {
+ "type": "object",
+ "properties": {
+ "id": {
+ "type": "string",
+ "description": "The ID of the tenant."
+ },
+ "name": {
+ "type": "string",
+ "description": "The name of the tenant."
+ },
+ "created_at": {
+ "type": "string",
+ "description": "The time at which the tenant was created.",
+ "format": "date-time"
+ }
+ },
+ "description": "Tenant represents a tenant with an id, a name, and a timestamp indicating when it was created."
+ },
+ "TenantCreateRequest": {
+ "type": "object",
+ "properties": {
+ "id": {
+ "type": "string",
+ "description": "id is a unique identifier for the tenant."
+ },
+ "name": {
+ "type": "string",
+ "description": "name is the name of the tenant."
+ }
+ },
+ "description": "TenantCreateRequest is the message used for the request to create a tenant."
+ },
+ "TenantCreateResponse": {
+ "type": "object",
+ "properties": {
+ "tenant": {
+ "$ref": "#/components/schemas/Tenant"
+ }
+ },
+ "description": "TenantCreateResponse is the message returned from the request to create a tenant."
+ },
+ "TenantDeleteResponse": {
+ "type": "object",
+ "properties": {
+ "tenant": {
+ "$ref": "#/components/schemas/Tenant"
+ }
+ },
+ "description": "TenantDeleteResponse is the message returned from the request to delete a tenant."
+ },
+ "TenantListRequest": {
+ "type": "object",
+ "properties": {
+ "page_size": {
+ "type": "integer",
+ "description": "page_size is the number of tenants to be returned in the response.\nThe value should be between 1 and 100.",
+ "format": "int64"
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is an optional parameter used for pagination.\nIt should be the value received in the previous response."
+ }
+ },
+ "description": "TenantListRequest is the message used for the request to list all tenants."
+ },
+ "TenantListResponse": {
+ "type": "object",
+ "properties": {
+ "tenants": {
+ "type": "array",
+ "description": "tenants is a list of tenants.",
+ "items": {
+ "$ref": "#/components/schemas/Tenant"
+ }
+ },
+ "continuous_token": {
+ "type": "string",
+ "description": "continuous_token is a string that can be used to paginate and retrieve the next set of results."
+ }
+ },
+ "description": "TenantListResponse is the message returned from the request to list all tenants."
+ },
+ "Tuple": {
+ "type": "object",
+ "properties": {
+ "entity": {
+ "$ref": "#/components/schemas/Entity"
+ },
+ "relation": {
+ "type": "string"
+ },
+ "subject": {
+ "$ref": "#/components/schemas/Subject"
+ }
+ },
+ "description": "Tuple is a structure that includes an entity, a relation, and a subject."
+ },
+ "TupleFilter": {
+ "type": "object",
+ "properties": {
+ "entity": {
+ "$ref": "#/components/schemas/EntityFilter"
+ },
+ "relation": {
+ "type": "string"
+ },
+ "subject": {
+ "$ref": "#/components/schemas/SubjectFilter"
+ }
+ },
+ "description": "TupleFilter is used to filter tuples based on the entity, relation and the subject."
+ },
+ "TupleSet": {
+ "type": "object",
+ "properties": {
+ "relation": {
+ "type": "string"
+ }
+ },
+ "description": "TupleSet represents a set of tuples associated with a specific relation."
+ },
+ "TupleToUserSet": {
+ "type": "object",
+ "properties": {
+ "tupleSet": {
+ "$ref": "#/components/schemas/TupleSet"
+ },
+ "computed": {
+ "$ref": "#/components/schemas/ComputedUserSet"
+ }
+ },
+ "description": "TupleToUserSet defines a mapping from tuple sets to computed user sets."
+ },
+ "Values": {
+ "type": "object",
+ "properties": {
+ "values": {
+ "type": "object",
+ "additionalProperties": {
+ "$ref": "#/components/schemas/Any"
+ }
+ }
+ }
+ },
+ "WatchResponse": {
+ "type": "object",
+ "properties": {
+ "changes": {
+ "$ref": "#/components/schemas/DataChanges"
+ }
+ },
+ "description": "WatchResponse is the response message for the Watch RPC. It contains the\nchanges in the data that are being watched."
+ },
+ "WellKnownType": {
+ "type": "string",
+ "description": "Well-known protobuf types treated with first-class support in CEL.\n\n - WELL_KNOWN_TYPE_UNSPECIFIED: Unspecified type.\n - ANY: Well-known protobuf.Any type.\n\nAny types are a polymorphic message type. During type-checking they are\ntreated like `DYN` types, but at runtime they are resolved to a specific\nmessage type specified at evaluation time.\n - TIMESTAMP: Well-known protobuf.Timestamp type, internally referenced as `timestamp`.\n - DURATION: Well-known protobuf.Duration type, internally referenced as `duration`.",
+ "default": "WELL_KNOWN_TYPE_UNSPECIFIED",
+ "enum": [
+ "WELL_KNOWN_TYPE_UNSPECIFIED",
+ "ANY",
+ "TIMESTAMP",
+ "DURATION"
+ ]
+ },
+ "v1.Call": {
+ "type": "object",
+ "properties": {
+ "ruleName": {
+ "title": "Name of the rule",
+ "type": "string"
+ },
+ "arguments": {
+ "title": "Arguments passed to the rule",
+ "type": "array",
+ "items": {
+ "$ref": "#/components/schemas/Argument"
+ }
+ }
+ },
+ "description": "Call represents a call to a rule. It includes the name of the rule and the arguments passed to it."
+ },
+ "v1.Operation": {
+ "type": "object",
+ "properties": {
+ "relationships_write": {
+ "type": "array",
+ "description": "'relationships_write' is a repeated string field for storing relationship keys\nthat are to be written or created.",
+ "items": {
+ "type": "string"
+ }
+ },
+ "relationships_delete": {
+ "type": "array",
+ "description": "'relationships_delete' is a repeated string field for storing relationship keys\nthat are to be deleted or removed.",
+ "items": {
+ "type": "string"
+ }
+ },
+ "attributes_write": {
+ "type": "array",
+ "description": "'attributes_write' is a repeated string field for storing attribute keys\nthat are to be written or created.",
+ "items": {
+ "type": "string"
+ }
+ },
+ "attributes_delete": {
+ "type": "array",
+ "description": "'attributes_delete' is a repeated string field for storing attribute keys\nthat are to be deleted or removed.",
+ "items": {
+ "type": "string"
+ }
+ }
+ },
+ "description": "Operation is a message representing a series of operations that can be performed.\nIt includes fields for writing and deleting relationships and attributes."
+ },
+ "v1alpha1.Reference": {
+ "type": "object",
+ "properties": {
+ "name": {
+ "type": "string",
+ "description": "The fully qualified name of the declaration."
+ },
+ "overloadId": {
+ "type": "array",
+ "description": "For references to functions, this is a list of `Overload.overload_id`\nvalues which match according to typing rules.\n\nIf the list has more than one element, overload resolution among the\npresented candidates must happen at runtime because of dynamic types. The\ntype checker attempts to narrow down this list as much as possible.\n\nEmpty if this is not a reference to a\n[Decl.FunctionDecl][google.api.expr.v1alpha1.Decl.FunctionDecl].",
+ "items": {
+ "type": "string"
+ }
+ },
+ "value": {
+ "$ref": "#/components/schemas/Constant"
+ }
+ },
+ "description": "Describes a resolved reference to a declaration."
+ },
+ "v1alpha1.Type": {
+ "type": "object",
+ "properties": {
+ "dyn": {
+ "type": "object",
+ "properties": {},
+ "description": "Dynamic type."
+ },
+ "null": {
+ "type": "string",
+ "description": "Null value."
+ },
+ "primitive": {
+ "$ref": "#/components/schemas/PrimitiveType"
+ },
+ "wrapper": {
+ "$ref": "#/components/schemas/PrimitiveType"
+ },
+ "wellKnown": {
+ "$ref": "#/components/schemas/WellKnownType"
+ },
+ "listType": {
+ "$ref": "#/components/schemas/ListType"
+ },
+ "mapType": {
+ "$ref": "#/components/schemas/MapType"
+ },
+ "function": {
+ "$ref": "#/components/schemas/FunctionType"
+ },
+ "messageType": {
+ "type": "string",
+ "description": "Protocol buffer message type.\n\nThe `message_type` string specifies the qualified message type name. For\nexample, `google.plus.Profile`."
+ },
+ "typeParam": {
+ "type": "string",
+ "description": "Type param type.\n\nThe `type_param` string specifies the type parameter name, e.g. `list`\nwould be a `list_type` whose element type was a `type_param` type\nnamed `E`."
+ },
+ "type": {
+ "$ref": "#/components/schemas/v1alpha1.Type"
+ },
+ "error": {
+ "type": "object",
+ "properties": {},
+ "description": "Error type.\n\nDuring type-checking if an expression is an error, its type is propagated\nas the `ERROR` type. This permits the type-checker to discover other\nerrors present in the expression."
+ },
+ "abstractType": {
+ "$ref": "#/components/schemas/AbstractType"
+ }
+ },
+ "description": "Represents a CEL type."
+ }
+ },
+ "securitySchemes": {
+ "ApiKeyAuth": {
+ "type": "apiKey",
+ "name": "Authorization",
+ "in": "header"
+ }
+ }
+ },
+ "x-original-swagger-version": "2.0"
+}
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/check-api.md b/docs/api-reference/permission/check-api.mdx
similarity index 54%
rename from docs/versioned_docs/version-0.6.x/api-overview/permission/check-api.md
rename to docs/api-reference/permission/check-api.mdx
index c6bfed58..5cb9da79 100644
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/check-api.md
+++ b/docs/api-reference/permission/check-api.mdx
@@ -1,39 +1,34 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
+---
+title: Check Access Control
+openapi: post /v1/tenants/{tenant_id}/permissions/check
+---
In Permify, you can perform two different types access checks,
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **subject based** authorization checks, in form of `Which resources can user U edit ?`
+- **resource based** authorization checks, structured in the following form: `Can user U perform action Y in resource Z ?`
+- **subject based** authorization checks, structured in the following form: `Which resources can user U edit ?`
+
+In this section we'll look at the resource based check request of Permify.
+
+You can find subject based access checks in [Entity (Data) Filtering] section.
+
+[Entity (Data) Filtering]: ./lookup-entity
-In this section we'll look at the resource based check request of Permify. You can find subject based access checks in [Entity (Data) Filtering] section.
+## Content
-[Entity (Data) Filtering]: ../lookup-entity
+- [Example Check Request](#example-check-request)
+- [How Access Decisions Evaluated?](#how-access-decisions-evaluated)
+- [Latency & Performance](#latency-and-performance)
+- [Parameters & Properties](#parameters-and-properties)
-## Request
+## Example Check Request
-**Path:**
```javascript
POST /v1/permissions/check
```
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.check)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
+
```go
cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
@@ -61,8 +56,8 @@ cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequ
})
```
-
-
+
+
```javascript
client.permission.check({
@@ -90,9 +85,43 @@ client.permission.check({
})
```
-
-
+
+
+```python
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.PermissionApi(api_client)
+ tenant_id = 't1'
+
+ body = PermissionsCheckRequest(
+ tenant_id=tenant_id,
+ metadata={
+ "snapToken": "",
+ "schemaVersion": "",
+ "depth": 20
+ },
+ entity={
+ "type": "repository",
+ "id": "1"
+ },
+ permission="edit",
+ subject={
+ "type": "user",
+ "id": "1"
+ }
+ )
+
+ try:
+ api_response = api_instance.permissions_check(tenant_id, body)
+ if api_response.can == PermissionCheckResponse.Result.RESULT_ALLOWED:
+ print("RESULT_ALLOWED")
+ else:
+ print("RESULT_DENIED")
+ except ApiException as e:
+ print(f"Exception permissions_check: {e}")
+```
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
--header 'Content-Type: application/json' \
@@ -114,20 +143,9 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permission
},
}'
```
-
+
-## Response
-
-```json
-{
- "can": "RESULT_ALLOWED",
- "remaining_depth": 0
-}
-```
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism.
-
## How Access Decisions Evaluated?
Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
@@ -187,11 +205,6 @@ Rather than **or**, if we had an **and** relation then Permify Engine waits the
With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../reference/cache.md)
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
+Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../operations/cache)
+## Parameters & Properties
\ No newline at end of file
diff --git a/docs/api-reference/permission/expand-api.mdx b/docs/api-reference/permission/expand-api.mdx
new file mode 100644
index 00000000..e3fbf538
--- /dev/null
+++ b/docs/api-reference/permission/expand-api.mdx
@@ -0,0 +1,14 @@
+---
+title: Expand API
+openapi: post /v1/tenants/{tenant_id}/permissions/expand
+---
+
+Retrieve all subjects (users and user sets) that have a relationship or attribute with given entity and permission
+
+Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
+
+
+Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
+
+It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
+
\ No newline at end of file
diff --git a/docs/api-reference/permission/lookup-entity-stream.mdx b/docs/api-reference/permission/lookup-entity-stream.mdx
new file mode 100644
index 00000000..51313643
--- /dev/null
+++ b/docs/api-reference/permission/lookup-entity-stream.mdx
@@ -0,0 +1,6 @@
+---
+title: Lookup Entity (Streaming)
+openapi: post /v1/tenants/{tenant_id}/permissions/lookup-entity-stream
+---
+
+The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
diff --git a/docs/api-reference/permission/lookup-entity.mdx b/docs/api-reference/permission/lookup-entity.mdx
new file mode 100644
index 00000000..82decbf6
--- /dev/null
+++ b/docs/api-reference/permission/lookup-entity.mdx
@@ -0,0 +1,50 @@
+---
+title: Lookup Entity (Data Filtering)
+openapi: post /v1/tenants/{tenant_id}/permissions/lookup-entity
+---
+
+Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
+
+So, we provide 2 separate endpoints for data filtering check request,
+
+- Lookup Entity
+- [Lookup Entity Streaming](./lookup-entity-stream)
+
+In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
+
+### How Lookup Operations Evaluated
+
+We explicitly designed reverse lookup to be more performant with changing its evaluation pattern. We do not query all the documents in bulk to get response, instead of this Permify first finds the necessary relations with given subject and the permission/action in the API call. Then query these relations with the subject id this way we reduce lots of additional queries.
+
+To give an example,
+
+```jsx
+entity user {}
+
+entity organization {
+ relation admin @user
+}
+
+entity container {
+ relation parent @organization
+ relation container_admin @user
+ action admin = parent.admin or container_admin
+}
+
+entity document {
+ relation container @container
+ relation viewer @user
+ relation owner @user
+ action view = viewer or owner or container.admin
+}
+```
+
+Lets say we called (reverse) lookup API to find the documents that user:1 can view. Permify first finds the relations that linked with view action, these are
+
+- `document#viewer`
+- `document#owner`
+- `organization#admin`
+- `container#``container_admin`
+
+Then queries each of them with `user:1.`
+
diff --git a/docs/api-reference/permission/lookup-subject.mdx b/docs/api-reference/permission/lookup-subject.mdx
new file mode 100644
index 00000000..aa81a943
--- /dev/null
+++ b/docs/api-reference/permission/lookup-subject.mdx
@@ -0,0 +1,8 @@
+---
+title: Subject Filtering
+openapi: post /v1/tenants/{tenant_id}/permissions/lookup-subject
+---
+
+Lookup Subject endpoint lets you ask questions in form of **“Which subjects can do action Y on entity:X?”**. As a response of this you’ll get a subject results in a format of string array.
+
+In this endpoint you'll get directly the IDs' of the subjects that are authorized in an array.
\ No newline at end of file
diff --git a/docs/api-reference/permission/subject-permission.mdx b/docs/api-reference/permission/subject-permission.mdx
new file mode 100644
index 00000000..48d6b1ae
--- /dev/null
+++ b/docs/api-reference/permission/subject-permission.mdx
@@ -0,0 +1,8 @@
+---
+title: Subject Permission List
+openapi: post /v1/tenants/{tenant_id}/permissions/subject-permission
+---
+
+The Subject Permission List endpoint allows you to inquire in the form of **“Which permissions user:x can perform on entity:y?”**. In response, you'll receive a list of permissions specific to the user for the given entity, returned in the format of a map.
+
+In this endpoint, you'll receive a map of permissions and their statuses directly. The structure is map[string]CheckResult, such as "sample-permission" -> "ALLOWED". This represents the permissions and their associated states in a key-value pair format.
diff --git a/docs/api-reference/schema/list-schema.mdx b/docs/api-reference/schema/list-schema.mdx
new file mode 100644
index 00000000..85c5af9c
--- /dev/null
+++ b/docs/api-reference/schema/list-schema.mdx
@@ -0,0 +1,13 @@
+---
+title: List Schema
+openapi: post /v1/tenants/{tenant_id}/schemas/list
+---
+
+Models written to Permify using the [write schema API](./write-schema) can be listed using this API with the timestamps at which the models were created.
+
+Request needs to be made to the API endpoint **/v1/schemas/list** to list all the models.
+
+### Example Request on Postman
+**POST** `/v1/tenants/{tenant_id}/schemas/list`
+
+
diff --git a/docs/api-reference/schema/read-schema.mdx b/docs/api-reference/schema/read-schema.mdx
new file mode 100644
index 00000000..3a5ea98c
--- /dev/null
+++ b/docs/api-reference/schema/read-schema.mdx
@@ -0,0 +1,13 @@
+---
+title: Read Schema
+openapi: post /v1/tenants/{tenant_id}/schemas/read
+---
+
+When a model is written to Permify using the [write schema API](./write-schema) a schema version will be returned by the API. That schema version can be used to inspect the schema.
+
+Permify Schema needed to be send to API endpoint **/v1/schemas/read** for configuration of your authorization model on Permify API.
+
+### Example Request on Postman
+**POST** `/v1/tenants/{tenant_id}/schemas/read"`
+
+
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/write-schema.md b/docs/api-reference/schema/write-schema.mdx
similarity index 53%
rename from docs/versioned_docs/version-0.2.x/api-overview/write-schema.md
rename to docs/api-reference/schema/write-schema.mdx
index f97a9f84..cdac796e 100644
--- a/docs/versioned_docs/version-0.2.x/api-overview/write-schema.md
+++ b/docs/api-reference/schema/write-schema.mdx
@@ -1,72 +1,25 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
+---
+title: Write Schema
+openapi: post /v1/tenants/{tenant_id}/schemas/write
+---
Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-:::caution Use Playground For Testing
+
If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.

-:::
+
Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-### Path : ** POST "/v1/schemas/write"**
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | schema | string | - | Permify Schema as string|
-
-**Example Request on Postman:**
+### Example Request on Postman
+**POST** `/v1/tenants/{tenant_id}/schemas/write`

-### Using gRPC Clients
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- Schema: `
- entity user {}
-
- entity document {
- relation viewer @user
-
- action view = viewer
- }
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- schema: `
- entity user {}
-
- entity document {
- relation viewer @user
-
- action view = viewer
- }
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
+See the following FAQ page to refer to the suggested workflow for: [Managing Schema Changes](../../introduction/faqs#how-to-manage-schema-changes).
\ No newline at end of file
diff --git a/docs/api-reference/tenancy/create-tenant.mdx b/docs/api-reference/tenancy/create-tenant.mdx
new file mode 100644
index 00000000..08817c23
--- /dev/null
+++ b/docs/api-reference/tenancy/create-tenant.mdx
@@ -0,0 +1,10 @@
+---
+title: Create Tenant
+openapi: post /v1/tenants/create
+---
+
+Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
+
+
+We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
+
diff --git a/docs/api-reference/tenancy/delete-tenant.mdx b/docs/api-reference/tenancy/delete-tenant.mdx
new file mode 100644
index 00000000..611625ad
--- /dev/null
+++ b/docs/api-reference/tenancy/delete-tenant.mdx
@@ -0,0 +1,4 @@
+---
+title: Delete Tenant
+openapi: delete /v1/tenants/{id}
+---
\ No newline at end of file
diff --git a/docs/api-reference/tenancy/list-tenants.mdx b/docs/api-reference/tenancy/list-tenants.mdx
new file mode 100644
index 00000000..f3355b67
--- /dev/null
+++ b/docs/api-reference/tenancy/list-tenants.mdx
@@ -0,0 +1,4 @@
+---
+title: List Tenants
+openapi: post /v1/tenants/list
+---
\ No newline at end of file
diff --git a/docs/api-reference/watch/watch-changes.mdx b/docs/api-reference/watch/watch-changes.mdx
new file mode 100644
index 00000000..b77dfbc9
--- /dev/null
+++ b/docs/api-reference/watch/watch-changes.mdx
@@ -0,0 +1,70 @@
+---
+title: Watch API
+openapi: post /v1/tenants/{tenant_id}/watch
+---
+
+The Permify Watch API acts as a real-time broadcaster that shows changes in the relation tuples.
+
+The Watch API exclusively supports gRPC and works with PostgreSQL, given the track_commit_timestamp option is enabled. Please note, it doesn't support in-memory databases or HTTP communication.
+
+## Requirements
+
+- PostgreSQL database set up with track_commit_timestamp option enabled
+
+## Enabling track_commit_timestamp on PostgreSQL
+
+To ensure data consistency and synchronization between your application and Permify, enable track_commit_timestamp on
+your PostgreSQL server. This can be done by executing the following options in your PostgreSQL:
+
+### Option 1: SQL Command
+
+1. Open your PostgreSQL command line interface.
+2. Execute the following command:
+
+ ```sql
+ ALTER SYSTEM SET track_commit_timestamp = ON;
+ ```
+
+3. Reload the configuration with the following command:
+
+ ```sql
+ SELECT pg_reload_conf();
+ ```
+
+### Option 2: Editing postgresql.conf
+
+1. Find and open the postgresql.conf file in a text editor. Its location depends on your PostgreSQL installation. Common
+ locations are:
+ - Debian-based systems: /etc/postgresql/[version]/main/postgresql.conf
+ - Red Hat-based systems: /var/lib/pgsql/data/postgresql.conf
+
+2. Add or modify the following line in the postgresql.conf file:
+ ```
+ track_commit_timestamp = on
+ ```
+
+3. Save and close the postgresql.conf file.
+4. Reload the PostgreSQL configuration for the changes to take effect. This can be done via the PostgreSQL console:
+ ```sql
+ SELECT pg_reload_conf();
+ ```
+
+ Or if you have command line access, use:
+
+ ```bash
+ sudo service postgresql reload
+ ```
+
+Please ensure you have the necessary permissions to execute these commands or modify the postgresql.conf file. Also, remember that changes in the postgresql.conf file will persist across restarts, while the SQL method may need to be reapplied depending on your PostgreSQL version and setup.
+
+
+Important Configuration Requirement: To use the Watch API, it must be enabled in your configuration file. Add or modify the following lines:
+
+```yaml
+service:
+ watch:
+ enabled: true
+```
+
+
+
diff --git a/docs/babel.config.js b/docs/babel.config.js
deleted file mode 100644
index e00595da..00000000
--- a/docs/babel.config.js
+++ /dev/null
@@ -1,3 +0,0 @@
-module.exports = {
- presets: [require.resolve('@docusaurus/core/lib/babel/preset')],
-};
diff --git a/docs/client-development-en/0.pack b/docs/client-development-en/0.pack
deleted file mode 100644
index aa55caba..00000000
Binary files a/docs/client-development-en/0.pack and /dev/null differ
diff --git a/docs/client-development-en/index.pack b/docs/client-development-en/index.pack
deleted file mode 100644
index 26728a8d..00000000
Binary files a/docs/client-development-en/index.pack and /dev/null differ
diff --git a/docs/development.mdx b/docs/development.mdx
new file mode 100644
index 00000000..87830089
--- /dev/null
+++ b/docs/development.mdx
@@ -0,0 +1,98 @@
+---
+title: 'Development'
+description: 'Learn how to preview changes locally'
+---
+
+
+ **Prerequisite** You should have installed Node.js (version 18.10.0 or
+ higher).
+
+
+Step 1. Install Mintlify on your OS:
+
+
+
+```bash npm
+npm i -g mintlify
+```
+
+```bash yarn
+yarn global add mintlify
+```
+
+
+
+Step 2. Go to the docs are located (where you can find `mint.json`) and run the following command:
+
+```bash
+mintlify dev
+```
+
+The documentation website is now available at `http://localhost:3000`.
+
+### Custom Ports
+
+Mintlify uses port 3000 by default. You can use the `--port` flag to customize the port Mintlify runs on. For example, use this command to run in port 3333:
+
+```bash
+mintlify dev --port 3333
+```
+
+You will see an error like this if you try to run Mintlify in a port that's already taken:
+
+```md
+Error: listen EADDRINUSE: address already in use :::3000
+```
+
+## Mintlify Versions
+
+Each CLI is linked to a specific version of Mintlify. Please update the CLI if your local website looks different than production.
+
+
+
+```bash npm
+npm i -g mintlify@latest
+```
+
+```bash yarn
+yarn global upgrade mintlify
+```
+
+
+
+## Deployment
+
+
+ Unlimited editors available under the [Startup
+ Plan](https://mintlify.com/pricing)
+
+
+You should see the following if the deploy successfully went through:
+
+
+
+
+
+## Troubleshooting
+
+Here's how to solve some common problems when working with the CLI.
+
+
+
+ Update to Node v18. Run `mintlify install` and try again.
+
+
+Go to the `C:/Users/Username/.mintlify/` directory and remove the `mint`
+folder. Then Open the Git Bash in this location and run `git clone
+https://github.com/mintlify/mint.git`.
+
+Repeat step 3.
+
+
+
+ Try navigating to the root of your device and delete the ~/.mintlify folder.
+ Then run `mintlify dev` again.
+
+
+
+Curious about what changed in a CLI version? [Check out the CLI changelog.](/changelog/command-line)
diff --git a/docs/docs/api-overview.md b/docs/docs/api-overview.md
deleted file mode 100644
index d505b336..00000000
--- a/docs/docs/api-overview.md
+++ /dev/null
@@ -1,93 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Using the Permify API
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [DataService]: Authorization data operations such as creating, deleting and reading relational tuples and attributes.
-- [BundleService]: Facilitates the creation and execution of bundles that perform predefined operations, establishing relationships and attributes based on provided arguments.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permifyco/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ./permission
-[DataService]: ./data
-[BundleService]: ./bundle
-[SchemaService]: ./schema
-[TenancyService]: ./tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](./api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](./api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](./api-overview/data/read-relationships.md)
-- Check access with [Check API](./api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](./api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](./api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](./api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](./api-overview/watch/watch-changes.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our [documentation](https://docs.permify.co/docs/reference/configuration). We used [Token bucket](https://en.wikipedia.org/wiki/Token_bucket) algorithm for rate limiting.
-
-## Error Handling
-
-Permify API uses a set of defined error codes to indicate various types of failures or issues.
-Understanding these error codes and their implications is vital for effective error handling and troubleshooting within the Permify API.
-Each error code is designed to provide clear insights into what went wrong and how to resolve it, ensuring a smoother integration and operation of the API in your applications
-Refer to the [Error Codes](https://github.com/Permify/permify/blob/master/proto/base/v1/errors.proto) documentation for detailed descriptions and resolution steps for each error code.
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/_category_.json b/docs/docs/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/docs/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/docs/api-overview/bundle/_category_.json b/docs/docs/api-overview/bundle/_category_.json
deleted file mode 100644
index d8d37140..00000000
--- a/docs/docs/api-overview/bundle/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Bundle Service",
- "position": 4,
- "collapsed": true
-}
diff --git a/docs/docs/api-overview/bundle/delete-bundle.md b/docs/docs/api-overview/bundle/delete-bundle.md
deleted file mode 100644
index d175eda8..00000000
--- a/docs/docs/api-overview/bundle/delete-bundle.md
+++ /dev/null
@@ -1,58 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Bundle [Beta]
-
-The "Delete Bundle" API is designed for removing specific data bundles within a multi-tenant application environment. This API facilitates the deletion of a bundle, identified by its unique name, from a designated tenant's environment.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/delete
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.delete)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-
-
-
-
-```go
-rr, err: = client.Bundle.Delete(context.Background(), &v1.BundleDeleteRequest{
- TenantId: "t1",
- Name: "organization_created",
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.delete({
- tenantId: "t1",
- name: "organization_created",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/bundle/read-bundle.md b/docs/docs/api-overview/bundle/read-bundle.md
deleted file mode 100644
index f96a54ce..00000000
--- a/docs/docs/api-overview/bundle/read-bundle.md
+++ /dev/null
@@ -1,58 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Bundle [Beta]
-
-The "Read Bundle" API is a crucial tool for retrieving details of specific data bundles in a multi-tenant application setup. It is designed to access information about a bundle, uniquely identified by its name, within the specified tenant's environment.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/read
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.read)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-
-
-
-
-```go
-rr, err: = client.Bundle.Read(context.Background(), &v1.BundleReadRequest{
- TenantId: "t1",
- Name: "organization_created",
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.read({
- tenantId: "t1",
- name: "organization_created",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/bundle/write-bundle.md b/docs/docs/api-overview/bundle/write-bundle.md
deleted file mode 100644
index 9ee9d653..00000000
--- a/docs/docs/api-overview/bundle/write-bundle.md
+++ /dev/null
@@ -1,117 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Bundle [Beta]
-
-The "Write Bundle" API is designed for handling data in a multi-tenant application environment. Its primary function is to write and delete data according to predefined structures. This API allows users to define or update data bundles, each distinguished by a unique name.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/write
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.write)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-| [x] | operations | object | Represent actions that can be performed on data, such as adding or deleting relationships or attributes when certain events occur. |
-| [x] | arguments | string[] | Parameters that will be used in the operations |
-
-
-
-
-```go
-rr, err := client.Bundle.Write(context.Background(), &v1.BundleWriteRequest{
- TenantId: "t1",
- Bundles: []*v1.DataBundle{
- {
- Name: "organization_created",
- Arguments: []string{
- "creatorID",
- "organizationID",
- },
- Operations: []*v1.Operation{
- {
- RelationshipsWrite: []string{
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- },
- AttributesWrite: []string{
- "organization:{{.organizationID}}$public|boolean:false",
- },
- },
- },
- },
- },
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.write({
- tenantId: "t1",
- bundles: [
- {
- name: "organization_created",
- arguments: [
- "creatorID",
- "organizationID",
- ],
- operations: [
- {
- relationships_write: [
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- ],
- attributes_write: [
- "organization:{{.organizationID}}$public|boolean:false",
- ]
- }
- ]
- }
- ]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "bundles": [
- {
- "name": "organization_created"
- "arguments": [
- "creatorID",
- "organizationID"
- ],
- "operations": [
- {
- "relationships_write": [
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- ],
- "attributes_write": [
- "organization:{{.organizationID}}$public|boolean:false",
- ],
- },
- ],
- },
- ],
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/data/_category_.json b/docs/docs/api-overview/data/_category_.json
deleted file mode 100644
index 1a2612e1..00000000
--- a/docs/docs/api-overview/data/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Data Service",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/docs/api-overview/data/delete-data.md b/docs/docs/api-overview/data/delete-data.md
deleted file mode 100644
index b8d09e33..00000000
--- a/docs/docs/api-overview/data/delete-data.md
+++ /dev/null
@@ -1,111 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Data
-
-You can delete any stored relation tuples or attributes with following API
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/tenants/{tenant_id}/data/delete
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.delete)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | tuples_filter | object |filter to delete relational tuples. Contains **entity**, **relation** and **subject**.
-| [x] | attribute_filter | object | filter to delete attributes. Contains **entity** and **attributes**.
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | relation of the given entity |
-| [x] | attribute | string array | attributes to be deleted |
-| [ ] | subject | object | the user or user set. It contains type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.Delete(context.Background(), & v1.DataDeleteRequest {
- TenantId: "t1",
- Metadata: &v1.DataDeleteRequestMetadata {
- SnapToken: ""
- },
- TupleFilter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.delete({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- tupleFilter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "tupleFilter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- },
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/api-overview/data/read-attributes.md b/docs/docs/api-overview/data/read-attributes.md
deleted file mode 100644
index 86b4af1b..00000000
--- a/docs/docs/api-overview/data/read-attributes.md
+++ /dev/null
@@ -1,95 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Attributes
-
-Read API allows for directly querying the stored graph data to display and filter stored attributes.
-
-## Request
-```javascript
-POST /v1/tenants/{tenant_id}/data/attributes/read
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.attributes.read)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | attributes | string array | attributes of the given entity |
-
-
-
-
-
-```go
-rr, err: = client.Data.ReadAttributes(context.Background(), & v1.Data.AttributeReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.AttributeReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.AttributeFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Attributes: []string {"private"},
-})
-```
-
-
-
-
-
-```javascript
-client.data.readAttributes({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/attributes/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/data/read-relationships.md b/docs/docs/api-overview/data/read-relationships.md
deleted file mode 100644
index f59a3d57..00000000
--- a/docs/docs/api-overview/data/read-relationships.md
+++ /dev/null
@@ -1,106 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-## Request
-```javascript
-POST /v1/tenants/{tenant_id}/data/relationships/read
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.relationships.read)
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.ReadRelationships(context.Background(), & v1.Data.RelationshipReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.readRelationships({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/relationships/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/data/run-bundle.md b/docs/docs/api-overview/data/run-bundle.md
deleted file mode 100644
index a86d53ea..00000000
--- a/docs/docs/api-overview/data/run-bundle.md
+++ /dev/null
@@ -1,75 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Run Bundle [Beta]
-
-The "Run Bundle" API provides a straightforward way to execute predefined bundles within your application's tenant
-environment. By sending a POST request to this endpoint, you can activate specific functionalities or processes
-encapsulated in a bundle.
-
-## Request
-
-```javascript
- POST /v1/tenants/{tenant_id}/data/run-bundle
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/bundle.run)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-| [ ] | arguments | map | parameters for the bundle in key-value format. |
-
-
-
-
-```go
-rr, err: = client.Data.RunBundle(context.Background(), &v1.BundleRunRequest{
- TenantId: "t1",
- Name: "organization_created",
- Arguments: map[string]string{
- "creatorID": "564",
- "organizationID": "789",
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.runBundle({
- tenantId: "t1",
- name: "organization_created",
- arguments: {
- creatorID: "564",
- organizationID: "789",
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/run-bundle' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
- "arguments": {
- "creatorID": "564",
- "organizationID": "789",
- }
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/permission/_category_.json b/docs/docs/api-overview/permission/_category_.json
deleted file mode 100644
index e810c587..00000000
--- a/docs/docs/api-overview/permission/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Permission Service",
- "position": 2,
- "collapsed": true
-}
diff --git a/docs/docs/api-overview/permission/check-api.md b/docs/docs/api-overview/permission/check-api.md
deleted file mode 100644
index c6bfed58..00000000
--- a/docs/docs/api-overview/permission/check-api.md
+++ /dev/null
@@ -1,197 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
-
-In Permify, you can perform two different types access checks,
-
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **subject based** authorization checks, in form of `Which resources can user U edit ?`
-
-In this section we'll look at the resource based check request of Permify. You can find subject based access checks in [Entity (Data) Filtering] section.
-
-[Entity (Data) Filtering]: ../lookup-entity
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/permissions/check
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.check)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionCheckRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "can": "RESULT_ALLOWED",
- "remaining_depth": 0
-}
-```
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism.
-
-## How Access Decisions Evaluated?
-
-Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
-
-In high level, access of an subject related with the relationships or attributes created between the subject and the resource. You can define this data in Permify Schema then create and store them as relational tuples and attributes, which is basically forms your authorization data.
-
-Permify Engine to compute access decision in 2 steps,
-1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
-2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
-
-Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
-
-[relational tuples]: ../../getting-started/sync-data.md
-[Permify Schema]: ../../getting-started/modeling.md
-
-When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity document {
-
- // represents documents parent organization
- relation parent @organization
-
- // represents owner of this document
- relation owner @user
-
- // permissions
- action edit = parent.admin or owner
- action delete = owner
-}
-```
-
-Which has a directed graph as follows:
-
-
-
-As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
-
-**Q1:** Get the owners of the `document:12`.
-
-**Q2:** Get admins of the organization where `document:12` belongs to.
-
-Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
-
-Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
-
-## Latency & Performance
-
-With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
-
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../reference/cache.md)
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
diff --git a/docs/docs/api-overview/permission/expand-api.md b/docs/docs/api-overview/permission/expand-api.md
deleted file mode 100644
index 998955c1..00000000
--- a/docs/docs/api-overview/permission/expand-api.md
+++ /dev/null
@@ -1,319 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-
-Retrieve all subjects (users and user sets) that have a relationship or attribute with given entity and permission
-
-Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
-
-:::caution When To Use ?
-Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
-
-It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
-:::
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.expand)
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), &v1.PermissionExpandRequest{
- TenantId: "t1",
- Metadata: &v1.PermissionExpandRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "",
- "snap_token": ""
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "push"
-}'
-```
-
-
-
-## Example Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:**
-```javascript
-POST /v1/tenants/{tenant_id}/permissions/expand
-```
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”. |
-| [x] | permission | string | - | The permission the user wants to perform on the resource |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-### Expand Push Action
-
-Request
-
-
-
diff --git a/docs/docs/api-overview/permission/lookup-entity.md b/docs/docs/api-overview/permission/lookup-entity.md
deleted file mode 100644
index b87d77a4..00000000
--- a/docs/docs/api-overview/permission/lookup-entity.md
+++ /dev/null
@@ -1,228 +0,0 @@
----
-title: Entity (Data) Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Entity Filtering
-
-Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So, we provide 2 separate endpoints for data filtering check request,
-
-- [Lookup Entity](#lookup-entity)
-- [Lookup Entity (Streaming)](#lookup-entity-streaming)
-
-## Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
-
-**Path**
-```javascript
- POST /v1/permissions/lookup-entity
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntity)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens) |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- EntityType: "document",
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupEntity({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity_type: "document",
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response.entity_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type":"user",
- "id":"1"
- }
-}'
-```
-
-
-
-## How Lookup Operations Evaluated
-
-We explicitly designed reverse lookup to be more performant with changing its evaluation pattern. We do not query all the documents in bulk to get response, instead of this Permify first finds the necessary relations with given subject and the permission/action in the API call. Then query these relations with the subject id this way we reduce lots of additional queries.
-
-To give an example,
-
-```jsx
-entity user {}
-
-entity organization {
- relation admin @user
-}
-
-entity container {
- relation parent @organization
- relation container_admin @user
- action admin = parent.admin or container_admin
-}
-
-entity document {
- relation container @container
- relation viewer @user
- relation owner @user
- action view = viewer or owner or container.admin
-}
-```
-
-Lets say we called (reverse) lookup API to find the documents that user:1 can view. Permify first finds the relations that linked with view action, these are
-
-- `document#viewer`
-- `document#owner`
-- `organization#admin`
-- `container#``container_admin`
-
-Then queries each of them with `user:1.`
-
-## Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-**Path**
-```javascript
- POST /v1/permissions/lookup-entity-stream
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntityStream)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md) |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-str, err: = client.Permission.LookupEntityStream(context.Background(), &v1.PermissionLookupEntityRequest {
- Metadata: &v1.PermissionLookupEntityRequestMetadata {
- SnapToken: "",
- SchemaVersion: ""
- Depth: 50,
- },
- EntityType: "document",
- Permission: "view",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-
-// handle stream response
-for {
- res, err: = str.Recv()
-
- if err == io.EOF {
- break
- }
-
- // res.EntityId
-}
-```
-
-
-
-
-```javascript
-const permify = require("@permify/permify-node");
-const {PermissionLookupEntityStreamResponse} = require("@permify/permify-node/dist/src/grpc/generated/base/v1/service");
-
-function main() {
- const client = new permify.grpc.newClient({
- endpoint: "localhost:3478",
- })
-
- let res = client.permission.lookupEntityStream({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entityType: "document",
- permission: "view",
- subject: {
- type: "user",
- id: "1"
- }
- })
-
- handle(res)
-}
-
-async function handle(res: AsyncIterable) {
- for await (const response of res) {
- // response.entityId
- }
-}
-```
-
-
-
\ No newline at end of file
diff --git a/docs/docs/api-overview/permission/lookup-subject.md b/docs/docs/api-overview/permission/lookup-subject.md
deleted file mode 100644
index 0d0e17ff..00000000
--- a/docs/docs/api-overview/permission/lookup-subject.md
+++ /dev/null
@@ -1,116 +0,0 @@
----
-title: Subject Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Filtering
-
-Lookup Subject endpoint lets you ask questions in form of **“Which subjects can do action Y on entity:X?”**. As a response of this you’ll get a subject results in a format of string array.
-
-So, we provide 1 endpoint for subject filtering request,
-
-- [/v1/permissions/lookup-subject](#lookup-subject)
-
-## Lookup Subject
-
-In this endpoint you'll get directly the IDs' of the subjects that are authorized in an array.
-
-**POST**
-```javascript
-/v1/permissions/lookup-subject
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupSubject)
-
-| Required | Argument | Type | Default | Description |
-|----------|---------------------|----------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1 |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject_reference | object | - | the subject or subject reference who wants to take the action. It contains type and relation of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSubject(context.Background(), &v1.PermissionLookupSubjectRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionLookupSubjectRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- Depth: 20,
- },
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Permission: "edit",
- SubjectReference: &v1.RelationReference{
- Type: "user",
- Relation: "",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupSubject({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- depth: 20,
- },
- Entity: {
- Type: "document",
- Id: "1",
- },
- permission: "edit",
- subject_reference: {
- type: "user",
- relation: ""
- }
-}).then((response) => {
- console.log(response.subject_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": ""
- "depth": 20,
- },
- "entity": {
- type: "document",
- id: "1'
- },
- "permission": "edit",
- "subject_reference": {
- "type": "user",
- "relation": ""
- }
-}'
-```
-
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/api-overview/permission/subject-permission.md b/docs/docs/api-overview/permission/subject-permission.md
deleted file mode 100644
index 8157f3dc..00000000
--- a/docs/docs/api-overview/permission/subject-permission.md
+++ /dev/null
@@ -1,133 +0,0 @@
----
-title: Subject Permission List
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Permission List
-
-The Subject Permission List endpoint allows you to inquire in the form of **“Which permissions user:x can perform on entity:y?”**. In response, you'll receive a list of permissions specific to the user for the given entity, returned in the format of a map.
-
-So, we provide 1 endpoint for subject permission list,
-
-- [/v1/permissions/subject-permission](#subject-permission)
-
-In this endpoint, you'll receive a map of permissions and their statuses directly. The structure is map[string]CheckResult, such as "sample-permission" -> "ALLOWED". This represents the permissions and their associated states in a key-value pair format.
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/permissions/subject-permission
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.subjectPermission)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | only_permission | bool | false | By default, the endpoint returns both permissions and relations associated with the user and entity. However, when the "only_permission" parameter is set to true, it returns only the permissions. | |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.SubjectPermission(context.Background(), &v1.PermissionSubjectPermissionRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionSubjectPermissionRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- OnlyPermission: false,
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-```
-
-
-
-
-```javascript
-client.permission.subjectPermission({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- onlyPermission: true,
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response);
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "only_permission": true,
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "results": [
- {
- "key": "delete",
- "value": "RESULT_ALLOWED"
- },
- {
- "key": "edit",
- "value": "RESULT_ALLOWED"
- }
- ]
-}
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/docs/api-overview/schema/_category_.json b/docs/docs/api-overview/schema/_category_.json
deleted file mode 100644
index 8fd1e959..00000000
--- a/docs/docs/api-overview/schema/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Schema Service",
- "position": 1,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/docs/api-overview/schema/list-schema.md b/docs/docs/api-overview/schema/list-schema.md
deleted file mode 100644
index 6a3248e2..00000000
--- a/docs/docs/api-overview/schema/list-schema.md
+++ /dev/null
@@ -1,54 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# List Schema
-
-Models written to Permify using the [write schema API](./write-schema.md) can be listed using this API with the timestamps at which the models were created.
-
-Request needs to be made to the API endpoint **/v1/schemas/list** to list all the models.
-
-## Request
-
-```javascript
-POST /v1/tenants/{tenant_id}/schemas/list
-```
-
-[](https://permify.github.io/permify-swagger/#/Schema/schemas.list)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | page_size | string | - | Number of schema versions to be fetched |
-| [ ] | continuous_token | string | - | Continuation token for subsequent pages to be fetched |
-
-
-
-
-```go
-sr, err: = client.Schema.List(context.Background(), &v1.SchemaListRequest {
- TenantId: "t1",
- PageSize: "10",
- ContinuousToken: "",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- "page_size": "10",
- "continuous_token": ""
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/list"
-
-**Example Request on Postman:**
-
-
diff --git a/docs/docs/api-overview/schema/read-schema.md b/docs/docs/api-overview/schema/read-schema.md
deleted file mode 100644
index 7a0587d3..00000000
--- a/docs/docs/api-overview/schema/read-schema.md
+++ /dev/null
@@ -1,55 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Schema
-
-When a model is written to Permify using the [write schema API](./write-schema.md) a schema version will be returned by the API. That schema version can be used to inspect the schema.
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/read** for configuration of your authorization model on Permify API.
-
-## Request
-
-```javascript
-POST /v1/tenants/{tenant_id}/schemas/read
-```
-
-[](https://permify.github.io/permify-swagger/#/Schema/schemas.read)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | schema_version | string | - | Permify Schema version to read|
-
-
-
-
-```go
-sr, err: = client.Schema.Read(context.Background(), &v1.SchemaReadRequest {
- TenantId: "t1",
- Metadata: &v1.SchemaReadRequestMetadata{
- SchemaVersion: "cnbe6se5fmal18gpc66g",
- },
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "cnbe6se5fmal18gpc66g"
- }
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/read"**
-
-**Example Request on Postman:**
-
-
diff --git a/docs/docs/api-overview/schema/write-schema.md b/docs/docs/api-overview/schema/write-schema.md
deleted file mode 100644
index 4ae10d83..00000000
--- a/docs/docs/api-overview/schema/write-schema.md
+++ /dev/null
@@ -1,97 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
-
-Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
-
-We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-:::
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-## Request
-
-```javascript
-POST /v1/tenants/{tenant_id}/schemas/write
-```
-
-[](https://permify.github.io/permify-swagger/#/Schema/schemas.write)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- TenantId: "t1",
- Schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- tenantId: "t1",
- schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "schema": "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/write"**
-
-**Example Request on Postman:**
-
-
-
-
-## Suggested Workflow For Schema Changes
-
-It's expected that your initial schema will eventually change as your product or system evolves
-
-As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
-
-A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database unless you delete them with the [delete API](../data/delete-data.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
-
-We recommend applying the following pattern to safely handle schema changes:
-
-- Set up a central git repository that includes the schema.
-- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
-- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
-
-## Need any help ?
-
-Depending on the frequency and the type of the changes that you made on the schemas, this method may not be optimal for you - In such cases, we are open to exploring alternative solutions. Please feel free to [schedule a call with one of our engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/api-overview/tenancy/_category_.json b/docs/docs/api-overview/tenancy/_category_.json
deleted file mode 100644
index e1ebce3c..00000000
--- a/docs/docs/api-overview/tenancy/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Tenancy Service",
- "position": 5,
- "collapsed": true
-}
diff --git a/docs/docs/api-overview/tenancy/create-tenant.md b/docs/docs/api-overview/tenancy/create-tenant.md
deleted file mode 100644
index 20a35d7e..00000000
--- a/docs/docs/api-overview/tenancy/create-tenant.md
+++ /dev/null
@@ -1,59 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Create Tenant
-
-Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
-
-:::caution
-We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
-:::
-
-## Request
-
-```javascript
-POST /v1/tenants/create
-```
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.create)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Create(context.Background(), & v1.TenantCreateRequest {
- Id: ""
- Name: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.create({
- id: "",
- name: ""
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'http://localhost:3476/v1/tenants/create' \
---header 'Content-Type: application/json' \
---data-raw '{
- "id": "",
- "name": ""
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/api-overview/tenancy/delete-tenant.md b/docs/docs/api-overview/tenancy/delete-tenant.md
deleted file mode 100644
index aca60ef7..00000000
--- a/docs/docs/api-overview/tenancy/delete-tenant.md
+++ /dev/null
@@ -1,47 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Tenant
-
-You can delete a tenant with following API.
-
-## Request
-```javascript
-DELETE /v1/tenants/{id}
-```
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.delete)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Delete(context.Background(), & v1.TenantDeleteRequest {
- Id: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.delete({
- id: "",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/api-overview/watch/_category_.json b/docs/docs/api-overview/watch/_category_.json
deleted file mode 100644
index bb0c647b..00000000
--- a/docs/docs/api-overview/watch/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Watch Service",
- "position": 6,
- "collapsed": true
-}
diff --git a/docs/docs/api-overview/watch/watch-changes.md b/docs/docs/api-overview/watch/watch-changes.md
deleted file mode 100644
index aabc7416..00000000
--- a/docs/docs/api-overview/watch/watch-changes.md
+++ /dev/null
@@ -1,145 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Watch
-
-The Permify Watch API acts as a real-time broadcaster that shows changes in the relation tuples.
-
-The Watch API exclusively supports gRPC and works with PostgreSQL, given the track_commit_timestamp option is enabled. Please note, it doesn't support in-memory databases or HTTP communication.
-
-# Requirements
-
-- PostgreSQL database set up with track_commit_timestamp option enabled
-
-## Enabling track_commit_timestamp on PostgreSQL
-
-To ensure data consistency and synchronization between your application and Permify, enable track_commit_timestamp on
-your PostgreSQL server. This can be done by executing the following options in your PostgreSQL:
-
-### Option 1: SQL Command
-
-1. Open your PostgreSQL command line interface.
-2. Execute the following command:
-
- ```sql
- ALTER SYSTEM SET track_commit_timestamp = ON;
- ```
-
-3. Reload the configuration with the following command:
-
- ```sql
- SELECT pg_reload_conf();
- ```
-
-### Option 2: Editing postgresql.conf
-
-1. Find and open the postgresql.conf file in a text editor. Its location depends on your PostgreSQL installation. Common
- locations are:
- - Debian-based systems: /etc/postgresql/[version]/main/postgresql.conf
- - Red Hat-based systems: /var/lib/pgsql/data/postgresql.conf
-
-2. Add or modify the following line in the postgresql.conf file:
- ```
- track_commit_timestamp = on
- ```
-
-3. Save and close the postgresql.conf file.
-4. Reload the PostgreSQL configuration for the changes to take effect. This can be done via the PostgreSQL console:
- ```sql
- SELECT pg_reload_conf();
- ```
-
- Or if you have command line access, use:
-
- ```bash
- sudo service postgresql reload
- ```
-
-Please ensure you have the necessary permissions to execute these commands or modify the postgresql.conf file. Also, remember that changes in the postgresql.conf file will persist across restarts, while the SQL method may need to be reapplied depending on your PostgreSQL version and setup.
-
-:::info
-Important Configuration Requirement: To use the Watch API, it must be enabled in your configuration file. Add or modify the following lines:
-
-```yaml
-service:
- watch:
- enabled: true
-```
-
-:::
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/watch/watch
-```
-
-[](https://permify.github.io/permify-swagger/#/Watch/watch.watch)
-
-| Required | Argument | Type | Default | Description |
-|----------|------------|--------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | snap_token | string | - | specifies the starting point for broadcasting changes. If a snap_token is provided, all changes following that specific snapshot will be broadcasted. If a snap_token is not provided, the Watch API will broadcast all changes that occur after the Watch API is initiated., see more details on [Snap Tokens](../../../reference/snap-tokens). |
-
-
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```go)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```javascript)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-## Response
-
-```json
-{
- "changes": {
- "tuple_changes": [
- {
- "operation": "OPERATION_CREATE",
- "tuple": {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "56",
- "relation": ""
- }
- }
- }
- ],
- "snap_token": "MgMAAAAAAAA="
- }
-}
-```
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or
-have any questions about this
-example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/docs/comparision.md b/docs/docs/comparision.md
deleted file mode 100644
index 75fb39c4..00000000
--- a/docs/docs/comparision.md
+++ /dev/null
@@ -1,38 +0,0 @@
----
-id: comparison
-title: Comparison Between Other Zanzibar implementations
----
-
-:::caution Note
-This comparison table shows the differentiation between authorization solutions based or inspired by Google Zanzibar paper. If you use any of these solutions and feel the information could be improved, feel free to reach out.
-:::
-
-## General Aspects
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|---------------------------------|------------|------------|-----------|-----------|
-| **Zanzibar Paper Faithfulness** | Medium | High | High | High |
-| **Scalability** | Medium | Medium | High | High |
-| **Consistency & Cache** | No Zookies | No Zookies | Supported | Supported |
-| **Dev UX** | Average | Average | High | High |
-
-## Feature Set
-
-- ✅ Supported, and ready to use with no added configuration or code
-- 🟡 Limited support and requires extra user-code to implement.
-- ⛔ Not officially supported or documented.
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|--------------------------|----------|---------|---------|---------|
-| **Check API** | ✅ | ✅ | ✅ | ✅ |
-| **Write API** | ✅ | ✅ | ✅ | ✅ |
-| **Read API** | ✅ | ✅ | ✅ | ✅ |
-| **Expand API** | ✅ | ✅ | ✅ | ✅ |
-| **Watch API** | ✅ | ✅ | ✅ | ✅ |
-| **RBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ReBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ABAC** | ⛔ | 🟡 | ✅ | ✅ |
-| **Data Filtering** | ⛔ | ✅ | ✅ | ✅ |
-| **Multi Tenancy** | ⛔ | ✅ | ⛔ | ✅ |
-| **Testing & Validation** | ⛔ | 🟡 | ✅ | ✅ |
-| **Logging & Tracing** | 🟡 | ✅ | ✅ | ✅ |
diff --git a/docs/docs/examples.md b/docs/docs/examples.md
deleted file mode 100644
index ecc4d10a..00000000
--- a/docs/docs/examples.md
+++ /dev/null
@@ -1,18 +0,0 @@
----
-id: examples
-title: Real World Examples
-sidebar_label: Real World Examples
-slug: /getting-started/examples
----
-
-* [Google Docs]: Explore how users can gain direct access to a document through **organizational roles** or through **inherited/nested permissions**.
-* [Facebook Groups]: Explore how users can perform various actions based on the **roles and permissions within the groups** they belong.
-* [Notion]: Explore how **one global entity (workspace) can manage access rights** in the child entities that belong to it.
-* [Instagram]: Explore how **public/private attributes** play role in granting access to specific users.
-* [Mercury]: Explore how **attributes and rules interact within the hierarchical relationships**.
-
-[Google Docs]:./getting-started/examples/google-docs.md
-[Facebook Groups]:./getting-started/examples/facebook-groups.md
-[Notion]:./getting-started/examples/notion.md
-[Instagram]:./getting-started/examples/instagram.md
-[Mercury]:./getting-started/examples/mercury.md
\ No newline at end of file
diff --git a/docs/docs/getting-started/_category_.json b/docs/docs/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/docs/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/docs/getting-started/examples/_category_.json b/docs/docs/getting-started/examples/_category_.json
deleted file mode 100644
index b3e4f801..00000000
--- a/docs/docs/getting-started/examples/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Example Permission Structures",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/docs/getting-started/examples/facebook-groups.md b/docs/docs/getting-started/examples/facebook-groups.md
deleted file mode 100644
index 1b918630..00000000
--- a/docs/docs/getting-started/examples/facebook-groups.md
+++ /dev/null
@@ -1,546 +0,0 @@
-# Facebook Groups
-
-This example demonstrate the authorization structure for Facebook groups, which enables users to perform various actions based on their roles and permissions within the group.
-
-### Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
-
-```perm
-// Represents a user
-entity user {}
-
-// Represents a Facebook group
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
-}
-
-// Represents a post in a Facebook group
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
-}
-
-// Represents a comment like on a post in a Facebook group
-entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
-}
-
-// Definition of poll entity
-entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
-}
-
-// Definition of file entity
-entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
-}
-
-// Definition of event entity
-entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities and relations, as well as actions and permissions that can be taken by users within the group. Let's examine them shortly;
-
-### Entities & Relations
-
-* **`user`** entity represents a user in the Facebook.
-
-* **`group`** entity represents the Facebook group, and it has several relations including member, admin, and moderator to represent the members, admins, and moderators of the group. Additionally, there are relations to represent the posts and comments in the group.
-
-* **`post`** entity represents a post in the Facebook group, and it has relations to represent the owner of the post and the group that the post belongs to.
-
-* **`comment`** entity represents a comment on a post in the Facebook group, and it has relations to represent the owner of the comment, the post that the comment belongs to, and the comment itself.
-
-* **`like`** entity represents a like on a post in the Facebook group, and it has relations to represent the owner of the like and the post that the like belongs to.
-
-* **`poll`** entity represents a poll in the Facebook group, and it has relations to represent the owner of the poll and the group that the poll belongs to.
-
-* **`file`** entity represents a file in the Facebook group, and it has relations to represent the owner of the file and the group that the file belongs to.
-
-* **`event`** entity represents an event in the Facebook group, and it has relations to represent the owner of the event and the group that the event belongs to.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions.
-
-For example, the `create_group` action can only be performed by a `member`, as follows:
-
-#### Creating a group permission
-
-```perm
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
-
- ..
-
- // Create group permission
- action create_group = member
-
- ..
- ..
-}
-```
-
-Another example would be given from the `edit_post` action in the post entity, which specifies the permissions required to edit a post in a Facebook group.
-
-#### Editing a post permission
-
-```perm
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- ..
-
- action edit_post = owner or group.admin
-
- ..
- ..
-}
-```
-
-An **owner** of a post can always edit their own post. In addition, members who are defined as **admin** of the group - which the post belongs to - can also edit the post.
-
-Since most entities are deeply nested together, we also have multiple hierarchical permissions.
-
-#### Nested Hierarchies
-
-For example, we can define a permission "view_comment" if only user is owner of that comment or user is a member of the group which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-//group relationships
-group:1#member@user:1
-group:1#admin@user:2
-group:2#moderator@user:3
-group:2#member@user:4
-group:1#member@user:5
-
-//post relationships
-post:1#owner@user:1
-post:1#group@group:1
-post:2#owner@user:4
-post:2#group@group:1
-
-//comment relationships
-comment:1#owner@user:2
-comment:1#post@post:1
-comment:2#owner@user:5
-comment:2#post@post:2
-
-//like relationships
-like:1#owner@user:3
-like:1#post@post:1
-like:2#owner@user:4
-like:2#post@post:2
-
-//poll relationships
-poll:1#owner@user:2
-poll:1#group@group:1
-poll:2#owner@user:5
-poll:2#group@group:1
-
-//like relationships
-file:1#owner@user:1
-file:1#group@group:1
-
-//event relationships
-event:1#owner@user:3
-event:1#group@group:1
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:4 RSVP_to_event event:1 ?
-
-
-```perm
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
-
- ..
- ..
-
- action RSVP_to_event = owner or group.member
- }
-```
-
-According to what we have defined for the **'RSVP_to_event'** action, users who are either the owner of `event:1` or a member of the group that belongs to `event:1` can grant access to RSVP to the event.
-
-According to the relation tuples we created, `user:4` is not the **owner** of the event. Furthermore, when we check whether `user:4` is a **member** of the only group (`group:1`) that `event:1` is part of (`event:1#group@group:1`), we see that there is no **member** relation for `user:4` in that group.
-
-Therefore, the `user:4 RSVP_to_event event:1` check request should yield a **'false'** response.
-
-
-
-
-can user:5 view_comment comment:1 ?
-
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-According to the relation tuples we created, `user:5` is not the **owner** of the comment. But member of the `group:1` and thats grant `user:5` (`group:1#member@user:5`) access to perform view the comment:1. In particularly, `comment:1` is part of the `post:1` (`comment:1#post@post:1`) and `post:1` is part of the group:1 (`post:1#group@group:1`). And from the action definition on above model group:1 members can view the `comment:1`.
-
-Therefore, the `user:5 view_comment comment:1` check request should yield a **'true'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
- }
-
- entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
- }
-
- entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
- }
-
- entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
- }
-
- entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
- }
-
- entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
- }
-
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
- }
-
-relationships:
- - group:1#member@user:1
- - group:1#admin@user:2
- - group:2#moderator@user:3
- - group:2#member@user:4
- - group:1#member@user:5
- - post:1#owner@user:1
- - post:1#group@group:1
- - post:2#owner@user:4
- - post:2#group@group:1
- - comment:1#owner@user:2
- - comment:1#post@post:1
- - comment:2#owner@user:5
- - comment:2#post@post:2
- - like:1#owner@user:3
- - like:1#post@post:1
- - like:2#owner@user:4
- - like:2#post@post:2
- - poll:1#owner@user:2
- - poll:1#group@group:1
- - poll:2#owner@user:5
- - poll:2#group@group:1
- - file:1#owner@user:1
- - file:1#group@group:1
- - event:1#owner@user:3
- - event:1#group@group:1
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "event:1"
- subject: "user:4"
- assertions:
- RSVP_to_event : false
- - entity: "comment:1"
- subject: "user:5"
- assertions:
- view_comment : true
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/getting-started/examples/google-docs.md b/docs/docs/getting-started/examples/google-docs.md
deleted file mode 100644
index 3f14e1f7..00000000
--- a/docs/docs/getting-started/examples/google-docs.md
+++ /dev/null
@@ -1,344 +0,0 @@
-# Google Docs Simplified
-
-This example models a simplified version of Google Docs style permission system where users can be granted direct access to a document, or access via organizations and nested groups.
-
-### Schema | [Open in playground](https://play.permify.co/?s=iuRic3nR1HeZJcFyRNKPo)
-
-```perm
-entity user {}
-
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-## Breakdown of the Model
-
-### User
-
-```perm
-entity user {}
-```
-
-Represents a user who can be granted permission to access a documents directly, or through their membership in a group or organization.
-
-### Document
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-Represents a document that users can be granted permission to access. The document entity has two relationships:
-
-#### Relations
-
-**org:** Represents organization that document belongs to.
-
-**manager:** A relationship between users who are authorized to manage the document. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group member and manager relations.
-
-**viewer:** A relationship between users who are authorized to view the document. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager relations.
-
-The document entity has two actions defined:
-
-#### Actions
-
-**manage:**: An action that can be performed by users who are authorized to manage the document, as determined by the manager relationship.
-
-**view:** An action that can be performed by users who are authorized to view the document, as determined by the viewer and manager relationships.
-
-### Group
-
-```perm
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-```
-
-Represents a group of users who can be granted permission to access a document. The group entity has two relationships:
-
-#### Relations
-
-**manager:** A relationship between users who are authorized to manage the group. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are members of the group. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager.
-
-The group entity has one action defined:
-
-### Organization
-
-```perm
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-```
-
-Represents an organization that can contain groups, users, and documents. The organization entity has several relationships:
-
-#### Relations
-
-**group:** A relationship between the organization and its groups. This relationship is defined by the `@group` annotation on the end corresponding to the group entity.
-
-**document:** A relationship between the organization and its document. This relationship is defined by the `@document` annotation on the end corresponding to the group entity.
-
-**administrator:** A relationship between users who are authorized to manage the organization. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are directly members of the organization. This relationship is defined by the `@user` annotation on the end corresponding to the user entity.
-
-The organization entity has two permissions defined:
-
-#### Permissions
-
-**admin:** An permission that can be performed by users who are authorized to manage the organization, as determined by the administrator relationship.
-
-**member:** An permission that can be performed by users who are directly members of the organization, or who have administrator relationship, or who are members of groups that are part of the organization,
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different groups
-group:tech#manager@user:ashley
-group:tech#direct_member@user:david
-group:marketing#manager@user:john
-group:marketing#direct_member@user:jenny
-group:hr#manager@user:josh
-group:hr#direct_member@user:joe
-
-// Assign groups to other groups
-group:tech#direct_member@group:marketing#direct_member
-group:tech#direct_member@group:hr#direct_member
-
-// Connect groups to organization
-organization:acme#group@group:tech
-organization:acme#group@group:marketing
-organization:acme#group@group:hr
-
-// Add some documents under the organization
-organization:acme#document@document:product_database
-organization:acme#document@document:marketing_materials
-organization:acme#document@document:hr_documents
-
-// Assign a user and members of a group as administrators for the organization
-organization:acme#administrator@group:tech#manager
-organization:acme#administrator@user:jenny
-
-// Set the permissions on some documents
-document:product_database#manager@group:tech#manager
-document:product_database#viewer@group:tech#direct_member
-document:marketing_materials#viewer@group:marketing#direct_member
-document:hr_documents#manager@group:hr#manager
-document:hr_documents#viewer@group:hr#direct_member
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:ashley edit document:product_database ?
-
-
-```perm
- entity document {
- relation org @organization
-
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-```
-
-According what we have defined for the edit action managers and admins, of the organization that document belongs, can edit product database. In this context, Permify engine will check does subject `user:ashley` has any direct or indirect manager relation within `document:product_database`. Consecutively it will check does `user:ashley` has admin relation in the Acme Org - `organization:acme#document@document:product_database`.
-
-Ashley doesn't have any administrative relation in Acme Org but she is the manager in group tech (`group:tech#manager@user:ashley`) and we have defined that manager of group tech is manager of product_database with the tuple (`document:product_database#manager@group:tech#manager`). Therefore, the **user:ashley edit document:product_database** check request should yield **true** response.
-
-
-
-
-can user:joe view document:hr_documents ?
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check whether subject `user:joe` has any direct or indirect manager or viewer relation within `document:hr_documents`. Also consecutively it will check does `user:joe` has admin relation in the Acme Org - `organization:acme#document@document:hr_documents`.
-
-Joe doesn't have administrative role/relation in Acme Org.
-
-Also he doesn't have have manager relationship in that document or within any entity.
-
-But he is member in the hr group (`group:hr#member@user:joe`) and we defined hr members have viewer relationship in hr documents (`document:hr_documents#viewer@group:hr#member`). So that, this enforcement should yield **true** response.
-
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check does subject `user:david` has any direct or indirect manager or viewer relation within `document:marketing_materials`. Also consecutively it will check does `user:david` has admin relation in the Acme Org - `organization:acme#document@document:marketing_materials`.
-
-Similar Joe and Ashley, David also doesn't have administrative role/relation in Acme Org.
-
-Also David doesn't have member or manager relationship related with marketing group - `document:marketing_materials`. So that, this enforcement should yield **false** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
- }
-
- entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
- }
-
- entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-
-relationships:
- - group:tech#manager@user:ashley
- - group:tech#direct_member@user:david
- - group:marketing#manager@user:john
- - group:marketing#direct_member@user:jenny
- - group:hr#manager@user:josh
- - group:hr#direct_member@user:joe
-
- - group:tech#direct_member@group:marketing#direct_member
- - group:tech#direct_member@group:hr#direct_member
-
- - organization:acme#group@group:tech
- - organization:acme#group@group:marketing
- - organization:acme#group@group:hr
- - organization:acme#document@document:product_database
- - organization:acme#document@document:marketing_materials
- - organization:acme#document@document:hr_documents
- - organization:acme#administrator@group:tech#manager
- - organization:acme#administrator@user:jenny
-
- - document:product_database#manager@group:tech#manager
- - document:product_database#viewer@group:tech#direct_member
- - document:marketing_materials#viewer@group:marketing#direct_member
- - document:hr_documents#manager@group:hr#manager
- - document:hr_documents#viewer@group:hr#direct_member
-
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "document:product_database"
- subject: "user:ashley"
- assertions:
- edit: true
- - entity: "document:hr_documents"
- subject: "user:joe"
- assertions:
- view: true
- - entity: "document:marketing_materials"
- subject: "user:david"
- assertions:
- view: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of modeling Google Docs style permission system. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/docs/getting-started/examples/instagram.md b/docs/docs/getting-started/examples/instagram.md
deleted file mode 100644
index 9cd83163..00000000
--- a/docs/docs/getting-started/examples/instagram.md
+++ /dev/null
@@ -1,376 +0,0 @@
-# Instagram
-
-This example presents an Instagram Authorization Schema, outlining the intricate relationships between users, accounts, and posts on the platform. It defines user access levels, privacy settings, and interactions, offering insights into how followers, account owners, and post restrictions are managed within the Instagram ecosystem.
-
-## Schema | [Open in playground](https://play.permify.co/?s=instagram&tab=schema)
-
-```perm
-entity user {}
-
-entity account {
- // users have accounts
- relation owner @user
-
- // accounts can follow other users/accounts.
- relation following @user
-
- // other users/accounts can follow account.
- relation follower @user
-
- // accounts can be private or public.
- attribute public boolean
-
- // users can view an account if they're followers, owners, or if the account is not private.
- action view = (owner or follower) or public
-
-}
-
-entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- // users can view the posts, if they have access to view the linked accounts.
- action view = account.view
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
-}
-```
-
-## Brief Examination of the Model
-
-The Instagram Authorization Schema models the relationships between users, accounts, and posts in the Instagram platform.
-
-Users can own accounts, follow other accounts, and be followed by other users. Accounts can have public or private settings, and access to view an account is determined by ownership, followers, and privacy settings. Posts are associated with accounts and can have restricted comments and likes based on account privacy.
-
-### Entities & Relations
-
-- **`User`**: Represents a user on the Instagram platform.
-
-- **`Account`**: Represents a user account on Instagram. Accounts have owners, followers, and can follow other accounts.
-
-- **`Post`**: Represents a post on Instagram. Posts are linked to accounts and can have restricted comments and likes.
-
-### Permissions
-
-Users can view an account if they are the owner, a follower, or if the account is public.
-Users can comment and like posts if they have access to view the linked account and the post is unrestricted.
-
-### Relationships and Attributes
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Relationships
-// Users, Accounts and Posts:
- account:1#owner@user:kevin
- account:2#owner@user:george
- account:1#following@user:george
- account:2#follower@user:kevin
- post:1#account@account:1
- post:2#account@account:2
-
-// Attributes
-// Accounts and Posts:
- account:1$public|boolean:true
- account:2$public|boolean:false
- post:1$restricted|boolean:false
- post:2$restricted|boolean:true
-```
-
-## Test & Validation
-
-To validate our authorization logic, let's run some tests on different scenarios using the Instagram Authorization Schema.
-
-### Test 1: Checking Account Viewing Permissions
-
-
-
- Can user:kevin view account:1?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:kevin` is the owner of `account:1`. Hence, `user:kevin` should be able to view `account:1`. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:kevin view account:2?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:kevin` follows `account:2`. Hence, `user:kevin` should be able to view `account:2` because he is a follower. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:george view account:1?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:george` can view `account:1`, because the account is public. Hence, `user:george` should be able to view `account:1`. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:george view account:2?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:george` is the owner of `account:2`. Hence, `user:george` should be able to view `account:2`. The expected result is `'true'`.
-
-
-
-
-### Test 2: Checking Post Viewing Permissions
-
-Can user:george view post:1?
-
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:1` is linked with `account:1`, and it does not have restricted access. Also, `user:george` is following `account:1`. Hence, `user:george` should be able to view `post:1`. The expected result is `'true'`.
-
-
-
-
-Can user:kevin view post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it has restricted access. Also, `user:george` is not following `account:1`. Hence, `user:kevin` should not be able to view `post:2`. The expected result is `'false'`.
-
-
-
-
-Can user:george view post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it is restricted access. Also, `user:george` can view his own `post:2`. The expected result is `'true'`.
-
-
-
-
-### Test 3: Checking Post Commenting Permissions
-
-Can user:george comment post:1?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action comment = account.following not restricted
-}
-```
-
-According to the schema, `post:1` is linked with `account:1`, and it is not restricted. Also, `user:george` can comment on `post:1`. The expected result is `'true'`.
-
-
-
-
-Can user:kevin comment post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action comment = account.following not restricted
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it is restricted. `user:kevin` cannot comment on `post:2`. The expected result is `'false'`.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: |-
- entity user {}
-
- entity account {
- // users have accounts
- relation owner @user
-
- // accounts can follow other users/accounts.
- relation following @user
-
- // other users/accounts can follow account.
- relation follower @user
-
- // accounts can be private or public.
- attribute public boolean
-
- // users can view an account if they're followers, owners, or if the account is not private.
- action view = (owner or follower) or public
-
- }
-
- entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- // users can view the posts, if they have access to view the linked accounts.
- action view = account.view
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
- }
-relationships:
- - account:1#owner@user:kevin
- - account:2#owner@user:george
- - account:1#following@user:george
- - account:2#follower@user:kevin
- - post:1#account@account:1
- - post:2#account@account:2
-attributes:
- - account:1$public|boolean:true
- - account:2$public|boolean:false
- - post:1$restricted|boolean:false
- - post:2$restricted|boolean:true
-scenarios:
- - name: Account Viewing Permissions
- description: Evaluate account viewing permissions for 'kevin' and 'george'.
- checks:
- - entity: account:1
- subject: user:kevin
- assertions:
- view: true
- - entity: account:2
- subject: user:kevin
- assertions:
- view: true
- - entity: account:1
- subject: user:george
- assertions:
- view: true
- - entity: account:2
- subject: user:george
- assertions:
- view: true
- - name: Post Viewing Permissions
- description: Determine post viewing permissions for 'kevin' and 'george'.
- checks:
- - entity: post:1
- subject: user:george
- assertions:
- view: true
- - entity: post:2
- subject: user:kevin
- assertions:
- view: true
- - entity: post:2
- subject: user:george
- assertions:
- view: true
- - name: Post Commenting Permissions
- description: Evaluate post commenting permissions for 'kevin' and 'george'.
- checks:
- - entity: post:1
- subject: user:george
- assertions:
- comment: true
- - entity: post:2
- subject: user:kevin
- assertions:
- comment: false
-```
-
-## Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
diff --git a/docs/docs/getting-started/testing.md b/docs/docs/getting-started/testing.md
deleted file mode 100644
index 977fcf2d..00000000
--- a/docs/docs/getting-started/testing.md
+++ /dev/null
@@ -1,279 +0,0 @@
----
-sidebar_position: 4
----
-
-# Testing & Validation
-
-Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
-
-Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
-
-We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Adding Validate Action To Your Workflow
-
-After adding [permify-validate-action] to your Github Action workflow, you need to define the schema validation yaml file as,
-
-- **With local file:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "test.yaml"
-```
-
-- **With external url:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
-```
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Schema Validation File
-
-Below you can examine an example schema validation yaml file. It consists 3 parts;
-- `schema` which is the authorization model you want to test,
-- `relationships` sample data to test your model,
-- `scenarios` to test access check queries within created scenarios.
-
-### Defining the Schema:
-
-You can define the `schema` in the YAML file in one of two ways:
-
-1. **Directly in the File:** Define the schema directly within the YAML file.
-
- ```yaml
- schema: >-
- entity user {}
- entity organization {
- ...
- }
-
-2. **Via URL or File Path:** Specify a URL or a file path to an external schema file.
- **Example with URL:**
-
- ```yaml
- schema: https://example.com/path/to/schema.txt
- ```
-
- **Example with File Path:**
- ```yaml
- schema: /path/to/your/schema/file.txt
- ```
-
-Here is an example Schema Validation file,
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = (admin or member)
- action delete = admin
- }
-
- entity repository {
-
- relation owner @user @organization#member
- relation parent @organization
-
- action push = owner
- action read = (owner and (parent.admin and parent.member))
- action delete = (parent.member and (parent.admin or owner))
- action edit = parent.member not owner
- }
-
-relationships:
- - "organization:1#admin@user:1"
- - "organization:1#member@user:1"
- - "repository:1#owner@user:1"
- - "repository:2#owner@user:2"
- - "repository:2#owner@user:3"
- - "repository:1#parent@organization:1#..."
- - "organization:1#member@user:43"
- - "repository:1#owner@user:43"
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "repository:1"
- subject: "user:1"
- assertions:
- push : true
- owner : true
- - entity: "repository:2"
- subject: "user:1"
- assertions:
- push : false
- - entity: "repository:3"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- assertions:
- push : true
- - entity: "repository:1"
- subject: "user:43"
- assertions:
- edit : false
- entity_filters:
- - entity_type: "repository"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- - "repository:4#owner@user:1"
- - "repository:5#owner@user:1"
- assertions:
- push : ["1", "3", "4", "5"]
- edit : []
- subject_filters:
- - subject_reference: "user"
- entity: "repository:1"
- context:
- - "organization:1#member@user:58"
- assertions:
- push : ["1", "43"]
- edit : ["58"]
-```
-
-Assuming that you're well-familiar with the `schema` and `relationships` sections of the above YAML file. If not, please see the previous sections to learn how to create an authorization model (schema) and generate data (relationships) according to it.
-
-We'll continue by examining how to create scenarios.
-
-## Creating Test Scenarios
-
-You can create multiple access checks at once to test whether your authorization logic behaves as expected or not.
-
-Besides simple access checks you can also test subject filtering queries and data (entity) filtering with it.
-
-Let's deconstruct the `scenarios`,
-
-### Scenarios
-
-```js
-scenarios:
- - name: // name of the scenario
- description: // description of the scenario
- checks: // simple access check case/cases
- entity_filters: // entity (data) filtering query/queries
- subject_filters: // subject filtering query/queries
-```
-
-### Access Check
-
-You can create `check` inside `scenarios` to test multiple access check cases,
-
-```js
-checks:
- - entity: "repository:3" // resource/entity that you want to check access for
- subject: "user:1" // subject that performs the access check
- context: // additional data provided during an access check to be evaluated
- - "repository:3#owner@user:1"
- assertions: // expected result/results for specific action/s or an permission/s.
- push : true
-```
-
-Semantics for above check is: whether `user:1` can push to `repository:3`, additional to stored tuples take account that user:1 is owner of repository:3 (`repository:3#owner@user:1`). Expected result for that check it **true** - `push : true`
-
-:::info Contextual Tuples
-We use `context` (Contextual Tuples) with simple relational tuples for simplicity in this example. However, it is primarily used for dynamic access checks, such as those involving time, date, or IP address, etc.
-
-To learn more about how `context` works, see the [Contextual Tuples](../../reference/contextual-tuples) section.
-:::
-
-### Entity Filtering
-
-You can create `entity_filters` within `scenarios` to test your data filtering queries.
-
-```js
-entity_filters:
- - entity_type: "repository" // entity that you want to filter
- subject: "user:1" // subject that you want to perform data filtering
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "3", "4", "5"] // IDs of the resources that we expected to return
- edit : []
-```
-
-The major difference between `check` lies in the assertions part. Since we're performing data filtering with bulk data, instead of a true-false result, we enter the IDs of the resources that we expect to be returned
-
-### Subject Filtering
-
-You can create `subject_filters` within `scenarios` to test your subject filtering queries, a.k.a which users can perform action Y or have permission X on entity:Z?
-
-```js
-- subject_reference: "user"
- entity: "repository:1"
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "43"] // IDs of the users that we expected to return
- edit : ["58"]
-```
-
-:::info API Endpoints
-You can find the related API endpoints for `check`, `entity_filters`, and `subject_filters` in the Permission service in the [Using The API](../../api-overview) section.
-:::
-
-## Coverage Analysis
-
-By using the command `permify coverage {path of your schema validation file}`, you can measure the coverage for your schema.
-
-The coverage is calculated by analyzing the relationships and assertions in your created model, identifying any missing elements.
-
-The output of the example provided above is as follows.
-
-
-
-## Testing in Local
-
-You can also test your new authorization model in your local (Permify clone) without using [permify-validate-action] at all.
-
-For that open up a new file and add a schema yaml file inside. Then build your project with, run `make build` command and run `./permify validate {path of your schema validation file}`.
-
-If we use the above example schema validation file, after running `./permify validate {path of your schema validation file}` it gives a result on the terminal as:
-
-
-
-[permify-validate-action]: https://github.com/Permify/permify-validate-action
-
-## AST Conversion
-
-By utilizing the command `permify ast {path of your schema validation file}`, you can effortlessly convert your model into an Abstract Syntax Tree (AST) representation.
-
-The conversion to AST provides a structured representation of your model, making it easier to navigate, modify, and analyze. This process ensures that your model is syntactically correct and can be processed by other tools without issues.
-
-The output after running the above example command is illustrated below.
-
-
-
-
-## Unit Tests For Schema Changes
-
-We recommend leveraging Permify's in-memory databases for a simplified and isolated testing environment. These in-memory databases can be easily created and disposed of for each individual unit test, ensuring that your tests do not interfere with each other and each one starts with a clean slate.
-
-For managing permission/relation changes, we suggest storing schema in an abstracted place such as a git repo and centrally checking and approving every change before deploying it via the CI pipeline that utilizes the **Write Schema API**.
-
-We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-
-You can find more details about our suggested workflow to handle schema changes in [Write Schema](../../api-overview/schema/write-schema#suggested-workflow-for-schema-changes) section.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
-
diff --git a/docs/docs/installation.md b/docs/docs/installation.md
deleted file mode 100644
index d76986e1..00000000
--- a/docs/docs/installation.md
+++ /dev/null
@@ -1,17 +0,0 @@
----
-id: installation
-title: Setup Permify
-slug: /installation
----
-
-# Setup Permify
-
-Here is some options that you can use to set up and deploy Permify in your servers.
-
-```mdx-code-block
-import {CardList} from '../src/components/Card';
-
-
-```
-
-If options your deployment preference is not listed below please let us know Also if you have any questions join our [Discord community](https://discord.gg/n6KfzYxhPp) or send us an email at support@permify.co.
\ No newline at end of file
diff --git a/docs/docs/installation/_category_.json b/docs/docs/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/docs/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/docs/installation/aws.md b/docs/docs/installation/aws.md
deleted file mode 100644
index c1c204d9..00000000
--- a/docs/docs/installation/aws.md
+++ /dev/null
@@ -1,187 +0,0 @@
----
-title: AWS ECS, ECR & EC2
----
-
-# Deploy on AWS ECS, ECR & EC2
-
-AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
-
-There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
-
-ECS is a container management service. You can run your containers as task definitions, and It’s one of the easiest ways to deploy containers.
-
-If you’d like to watch this tutorial rather than reading. Here’s the video version.
-
-
-
-There is no prerequisite in this tutorial. You can simply deploy permify by following this step-by-step guide. However, if you want to integrate more advanced AWS security & networking features, we’ll follow up with a new tutorial guideline.
-
-At the end of this tutorial you’ll be able to;
-
-1. [Create a security group](#create-an-ec2-security-group)
-2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
-3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
-4. [Running our task definition](#4-running-our-task-definition)
-
-## 1. Create an EC2 Security Group
-
-So first thing first, let’s go over into security groups and create our security group. We’ll need this security group while creating our cluster.
-
-
-
-Search for “Security Groups” in the search bar. And go to the EC2 security groups feature.
-
-
-
-Then start creating a new security group.
-
-
-
-You have to name your security group, and give a description. Also, you need to choose the same VPC that you’ll going to use in EC2. So, I choose the default one. And I’m going to use same one while creating the ECS cluster.
-
-The next step is to configure our inbound rules. Here’s the configuration;
-
-```json
-//for mapping HTTP request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for mapping RPC request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3478",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for using SSH for connecting from your local computer.
-type = "Custom TCP", protocol = "TCP", port_range = "22",source = "Anywhere", 0.0.0.0/0
-```
-
-We have configured the HTTP and RPC ports for Permify. Also, we added port “22” for SSH connection. So, we can connect to EC2 through our local terminal.
-
-Now, we’re good to go. You can create the security group. And it’s ready to use in our ECS.
-
-## 2. Creating an ECS cluster
-
-
-
-The next step is to create an ECS cluster. From your AWS console search for Elastic Container Service or ECS for short.
-
-
-
-Then go over the clusters. As you can see there are 2 types of clusters. One is for ECS and another for EKS. We need to use ECS, EKS stands for Elastic Kubernetes Service. Today we’re not going to cover Kubernetes.
-
-Click **“Create Cluster”**
-
-
-
-Let’s create our first Cluster. Simply you have 3 options; Serverless(Network Only), Linux, and Windows. We’re going to cover EC2 Linux + Networking option.
-
-
-
-The next step is to configure our Cluster, starting with your Cluster name. Since we’re deploying Permify, I’ll call it “permify”.
-
-Then choose your instance type. You can take a look at different instances and pricing from [here](https://aws.amazon.com/ec2/pricing/on-demand/). I’m going with the t4 large. For cost purposes, you can choose t2.micro if you’re just trying out. It’s free tier eligible.
-
-Also, if you want to connect this EC2 instance from your local computer. You need to use SSH. Thus choose a key pair. If you have no such intention, leave it “none”.
-
-
-
-Now, we need to configure networking. First, choose your VPC, we use the default VPC as we did in the security groups. And choose any subnet on that VPC.
-
-You want to enable auto-assigned IP to make your app reachable from the internet.
-
-Choose the security group we have created previously.
-
-And voila, you can create your cluster. Now, we need to run our container in this cluster. To do that, let’s go over task definitions. And create our container definition.
-
-## 3. Creating and running task definitions
-
-Go over to ECS, and click the task definitions.
-
-
-
-And create a new task definition.
-
-
-
-Again, you’re going to ask to choose between; FARGATE, EC2, and EXTERNAL (On-premise). We’ll continue with EC2.
-
-Leave everything in default under the “Configure task and container definitions” section.
-
-
-
-Under the IAM role section you can choose “ecsTaskExecutionRole” if you want to use Cloud Watch later.
-
-You can leave task size in default since it’s optional for EC2.
-
-The critical part over here is to add our container. Click on the “Add Container” button.
-
-
-
-Then we need to add our container details. First, give a name. And then the most important part is our image URI. Permify is registered on the Github Registry so our image is;
-
-```yaml
-ghcr.io/permify/permify:latest
-```
-
-Then we need to define memory limit for the container, I went with 1024. You can define as much as your instance allows.
-
-Next step is to mapping our ports. As we mentioned in security groups, Permify by default listens;
-
-- `3476 for HTTP port`
-- `3478 for RPC port`
-
-
-
-Then we need to define command under the environment section. So, in order to start permify we first need to add “serve” command.
-
-For using properly we need a few other. Here’s the commands we need.
-
-```yaml
-serve, --database-engine=postgres, --database-uri=postgres://:@:/, --database-pool-max=20
-```
-
-- `serve` ⇒ for starting the Permify.
-- `--database-engine=postgres` ⇒ for defining the db we use.
-- `--database-uri=postgres://:password@:/` ⇒ for connecting your database with URI.
-- `--database-pool-max=20` ⇒ the depth for running in graph.
-
-We’re nice and clear, add the container and then just create your task definition. We’ll use this definition to run in our cluster.
-
-So, let’s go over and run our task definition.
-
-## 4. Running our task definition
-
-
-
-Let’s go to ECS and enter into our cluster. And go over into the tasks to run our task.
-
-
-
-Click to “Run new Task”
-
-
-
-Choose EC2 as a launch type. Then pick the task definition we just created. And leave everything else in the default. You can run your task now.
-
-We have just deployed our container into EC2 instance with ECS. Let’s test it.
-
-Now you can go over into EC2, and click on the running instances. Find the instance named `ECS Instance - EC2ContainerService-` in the running instances.
-
-
-
-Copy the Public IPv4 DNS from the right corner, and paste it into your browser. But you need to add `:3476` to access our http endpoint. So it should be like this;
-
-`:3476`
-
-and if you add healthz at the end like this;
-
-`:3476/healthz`
-
-you should get Serving status :)
-
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/docs/installation/azure.md b/docs/docs/installation/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/docs/installation/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/docs/installation/kubernetes.md b/docs/docs/installation/kubernetes.md
deleted file mode 100644
index f2a1e21b..00000000
--- a/docs/docs/installation/kubernetes.md
+++ /dev/null
@@ -1,173 +0,0 @@
----
-title: Kubernetes Cluster
----
-
-# Deploy on Kubernetes Cluster
-
-In this section we’re going to deploy Permify in AWS EKS which is Amazon Elastic Kubernetes Service. EKS is a managed service that you can easily run Kubernetes in AWS.
-
-Here’s what we’re going to do step-by-step;
-
-1. [Configure our AWS IAM credentials](#configure-aws-cli-with-your-iam-account)
-3. [Create EKS cluster and configure nodes](#creating-an-aws-eks-cluster)
-4. [Deploy Permify to nodes](#deploying--running-permify-in-nodes)
-
-There are a couple of small prerequisites for this tutorial.
-
-### Pre-requisites
-
-- An AWS account.
-- The AWS Command Line Interface (CLI) is installed and configured on your local machine. — [Click here](https://us-east-1.console.aws.amazon.com/iamv2/home?region=us-east-1#/home) to go to IAM
-- The AWS IAM Authenticator for Kubernetes is installed and configured on your local machine.
-
-## Configure AWS CLI with your IAM account.
-
-The first step is to configure our AWS IAM account into our local terminal so that we can run commands. Most of you probably have a configured AWS account if you ever set up anything into AWS programmatically, so you can skip this. If you don’t follow these steps.
-
-### Create an AWS IAM Programmatic Access Account
-
-First, let’s create IAM credentials for ourselves. Search IAM from the AWS console. You need to write down the account ID if you want to log in AWS console with this account as well. Let’s go over users and start creating our credentials.
-
-
-
-At Users screen click to “Add users” — and you’ll end up in your first screen creating user credentials. Here you can define the name of the user. Also there 2 options that you can choose simultaneously.
-
-But you must choose “Access key - Programmatic access” option. It’ll allow us to configure our AWS CLI on our local machine.
-
-You can also choose “Password - AWS Management Console access” if you want to log in to this account through the console. But you’ll need the Account ID that I mentioned in the IAM console screen.
-
-In the next screen, you’ll be asked to create or copy the user-set permissions. For this tutorial, you’ll only need to access EKS resources and features. So lets create group by clicking the “Create group” — and then at pop-up screen search for EKS.
-
-
-
-I’ll choose all EKS permissions but if you have certain policies internally, just stick with them. You’ll only need following permission to;
-
-- `AmazonEKSClusterPolicy`
-- `AmazonEKSServicePolicy`
-- `AmazonEKSVPCResourceController`
-- `AmazonEKSWorkerNodePolicy`
-
-Then simply you can review and create the user.
-
-
-
-Once you created the credentials you’ll prompt the “Access key ID” and “Secret access key”, you should save this down somewhere. We’re going the use these to configure our local machine with AWS CLI.
-
-### **Configure AWS CLI with your IAM account**
-
-Let’s open our local terminal
-
-```jsx
-aws configure
-```
-
-Next you’ll ask for the following credentials;
-
-- `AWS Access Key ID`
-- `AWS Secret Access Key`
-- `Default region name`
-- `Default output format` (leave it empty)
-
-## Creating an AWS EKS Cluster
-
-For the first step, we need to install [eksctl](https://eksctl.io/) — which is like kubectl but for AWS EKS. It helps us to set up and deploy our cluster and nodes within a fraction of the time.
-
-Let’s download eksctl using brew.
-
-
-```jsx
-brew tap weaveworks/tap
-```
-
-While installing the eksctl, we’ll end up getting kubectl and other dependencies.
-
-```jsx
-brew install weaveworks/tap/eksctl
-```
-
-Now, we’re ready to create our EKS cluster. You can define certain things while deploying standard the cluster beside the name and version like; the region you want to deploy, the EC2 instance type of each node, and the number of nodes you want to run.
-
-```bash
-eksctl create cluster \
---name \
---version 1.24 \
---region \
---nodegroup-name permify \
---node-type t2.small \
---nodes 2
-```
-
-## Deploying & Running Permify in Nodes
-
-The next stop is applying our manifests which will help us to deploy and configure our container/Permify.
-
-Let’s create our deployment manifest first.
-
-```yaml
-apiVersion: apps/v1
-kind: Deployment
-metadata:
- labels:
- app: permify
- name: permify
-spec:
- replicas: 2
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://postgres:nOcodeSTIAnLAba@permify-test.ceuo5kqsxyea.us-east-1.rds.amazonaws.com:5432/demo"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
-status: {}
-```
-
-Now let’s apply our deployment manifest
-
-```jsx
-kubectl apply -f deployment.yaml
-```
-
-The next step is to create a service manifest, this will allow us to configure our container app.
-
-```jsx
-apiVersion: v1
-kind: Service
-metadata:
- name: permify
-spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
-status:
- loadBalancer: {}
-```
-
-Let’s apply service.yaml to our nodes.
-
-```jsx
-kubectl apply -f service.yaml
-```
-
-Last but not least, we can check our pods & nodes. And we can start using the container with load balancer
\ No newline at end of file
diff --git a/docs/docs/installation/overview.md b/docs/docs/installation/overview.md
deleted file mode 100644
index 76fb8a56..00000000
--- a/docs/docs/installation/overview.md
+++ /dev/null
@@ -1,259 +0,0 @@
----
-sidebar_position: 1
----
-
-# Guide
-
-This guide shows you how to set up Permify in your servers and use it across your applications.
-
-:::info Minimum Requirements
-PostgreSQL: Version 13.8 or higher
-:::
-
-Please ensure your system meets these requirements before proceeding with the following steps:
-
-1. [Set Up & Run Permify Service](#set-up-permify-service)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Manage and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
-4. [Perform Access Check](#perform-access-check)
-
-:::info Talk to an Permify Engineer
-Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-## Set Up Permify Service
-
-You can run Permify Service with various options but in that tutorial we'll run it via docker container.
-
-### Run From Docker Container
-
-Production usage of Permify needs some configurations such as defining running options, selecting datastore to store authorization data and more.
-
-However, for the sake of this tutorial we'll not do any configurations and quickly start Permify on your local with running the docker command below:
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-:::info
-You can examine [Deploy using Docker] section to get more about the configuration options and learn the full integration to run Permify Service from docker container.
-
-[Deploy using Docker]: ../container
-:::
-
-### Test your connection
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core endpoints.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-## Model your Authorization with Permify Schema
-
-After installation completed and Permify server is running, next step is modeling authorization with Permify authorization language - [Permify Schema]- and configure it to Permify API.
-
-You can define your entities, relations between them and access control decisions of each actions with using [Permify Schema].
-
-### Creating your authorization model
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-
-:::
-
-Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action view_files = admin or member
- action edit_files = admin
-
-}
-```
-
-We have 2 entities these are **"user"** and **"organization"**. Entities represents your main tables. We strongly advise naming entities the same as your original database entities.
-
-Lets roll back our example,
-
-- The `user` entity represents users. This entity is empty because it's only responsible for referencing users.
-
-- The `organization` entity has its own relations (`admin` and `member`) which related with user entity. This entity also has 2 actions, respectively:
- - Organization member and admin can view files.
- - Only admins can edit files.
-
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
-
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../use-cases/simple-rbac
-:::
-
-### Configuring Schema via API
-
-After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../api-overview/schema/write-schema.md) for configuration of your authorization model on Permify authorization service.
-
-:::caution Before Continue on Writing Schema
-You'll see **tenant_id** parameter almost all Permify APIs including Write Schema. With version 0.3.x Permify became a tenancy based authorization infrastructure, and supports multi-tenancy by default so its a mandatory parameter when doing any operations.
-
-We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
-:::
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-**POST /v1/tenants/{tenant_id}/schemas/write**
-
-
-
-## Store Authorization Data as Relational Tuples
-
-After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action.
-
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules by using [Write Data API](../api-overview/data/write-data.md)
-
-For our guide let's grant one of the team members (Ashley) an admin role.
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-**POST /v1/tenants/{tenant_id}/data/write**
-
-```json
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1" //Organization identifier
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1", //Ashley's identifier
- "relation": ""
- }
- }
- ]
-}
-```
-
-
-
-**Created relational tuple:** organization:1#admin@user:1
-
-**Semantics:** User 1 (Ashley) has admin role on organization 1.
-
-:::tip
-In ideal production usage Permify stores your authorization data in a database you prefer. You can configure the database with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) or CLI flag options.
-
-But in this tutorial Permify Service running default configurations on local, so authorization data will be stored in memory. You can find more detailed explanation how Permify stores authorization data in [Managing Authorization Data] section.
-
-[Managing Authorization Data]: ../../getting-started/sync-data
-:::
-
-## Perform Access Check
-
-Finally we're ready to control authorization. Access decision results computed according to relational tuples and the stored model, [Permify Schema] action conditions.
-
-Lets get back to our example and perform an example access check via [Check API]. We want to check whether an specific user has an access to view files in a organization.
-
-[Check API]: ../../api-overview/permission/check-api
-[Permify Schema]: ../../getting-started/modeling
-
-#### Example HTTP Request:
-
-***Can the user 45 view files on organization 1 ?***
-
-**POST /v1/tenants/{tenant_id}/permissions/check**
-
-| Required | Argument | Type | Default | Description |
-|----------|----------------|----------|---------|---------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field. |
-| [x] | entity | object | - | name and id of the entity. Example: organization:1. |
-| [x] | action | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action |
-| [ ] | schema_version | string | - | get results according to given schema version |
-| [ ] | depth | integer | 8 | - |
-
-### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_files",
- "subject": {
- "type": "user",
- "id": "45",
- "relation": ""
- },
-}
-```
-
-### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "metadata": {
- "check_count": 0
- }
-}
-```
-
-See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-
-[Access Control Check]: ../api-overview/permission/check-api.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you struggle with installation or have any questions, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/docs/permify-overview/_category_.json b/docs/docs/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/docs/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/docs/permify-overview/infrastructure.md b/docs/docs/permify-overview/infrastructure.md
deleted file mode 100644
index 0f29223d..00000000
--- a/docs/docs/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,79 +0,0 @@
-
-# Architecture & Deployment
-
-Permify is a infrastructure for ease the process of creating and managing scalable authorization systems in your environment.
-
-This section shows where and how does Permify fit into your environment with examining Permify's high level design, internal architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## High Level Design
-
-You can model your authorization logic with **Permify's domain specific language** and your applications can interpolate with Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data and more!
-
-Permify stores access control relations in a **database of your choice**, and each API request evaluates and takes into account access decisions based on the stored relations.
-
-So this preferred database behaves as a **centralized data source** for your authorization system.
-
-
-
-### Permify vs Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Architecture
-
-Permify supports both HTTP and GRPC. HTTP requests are converted to GRPC and then transferred to Permify servers.
-
-There are 4 servers in a Permify Instance: Permission, Relationship, Schema, and Watch.
-
-- **Permission Server:** The permission server forwards the request to the invoker. The invoker checks for any missing parts of the query, let’s say if no snapshot is provided, it finds the head snapshot. It then hashes the request (with snapshot and schema version) and forwards it to the most convenient Permify instance. If the hash matches its own, it directs it to the local cache. If the cache does not contain the request, it proceeds to the engine. The engine breaks down the query into sub-queries and returns it to the invoker. This process continues until a final decision is made.
-- **Relationship Server:** After validating the request, it passes it to the database access layer.
-- **Schema Server:** After validating the request, it passes it to the database access layer.
-- **Watch Server:** It broadcasts changes in relationships based on their snapshots.
-
-
-
-Database abstractions for the reader and writer can use a database like Aurora Postgres.
-
-When deploying, separate hosts can be used in the Permify config for the reader and writer. This way, different Permify instances can read from different read replicas.
-
-**Note:** we are using serf (https://github.com/hashicorp/serf) agent for node discovery on hashring.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization.
-
-Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications.
-
-See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important.
-
-As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/docs/permify-overview/intro.md b/docs/docs/permify-overview/intro.md
deleted file mode 100644
index 69c135f2..00000000
--- a/docs/docs/permify-overview/intro.md
+++ /dev/null
@@ -1,117 +0,0 @@
----
-sidebar_position: 1
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is an **open source authorization service** for creating fine-grained and scalable authorization systems.
-
-With Permify, you can easily structure your authorization model, store authorization data in your preferred database, and interact with the Permify API to handle all authorization queries from your applications or services.
-
-Permify is inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://permify.co/post/google-zanzibar-in-a-nutshell/).
-
-### Motivation
-
-Our goal is to make **Google's Zanzibar** available to everyone and help them to build robust, flexible, and easily auditable authorization system that establishes a [natural linkage between permissions](https://permify.co/post/relationship-based-access-control-rebac/) across the business units, functions, and entities of an organization.
-
-## Key Features
-
-🛡️ **Production ready** authorization API that serve as **gRPC** and **REST**.
-
-🔮 Domain Specific Authorization Language to **easily model** your authorization. Supporting RBAC, ReBAC, ABAC and more.
-
-🔐 Database Configuration to store your permissions with **high availability** and **low latency**.
-
-✅ Perform access control checks and get answers **down to 10ms** with our various cache mechanisms that we operate.
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-⚙️ Create custom permissions for your **tenants**, and manage them in a single place with **Multi Tenancy**.
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin].
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Getting Started
-
-In Permify, authorization is divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify will [Store Authorization Data] as relations.
-- Perform [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../../getting-started/modeling
-[Store Authorization Data]: ../../getting-started/sync-data
-[Access Checks]: ../../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want to try it out and examine it instantly,
-
-
-
-## Community & Support
-
-We would love to hear from you :heart:
-
-You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
-
-For feature requests, bugs, or any improvements you can always open an [issue](https://github.com/permify/permify/issues).
-
-### Want to Contribute? Here are the ways to contribute to Permify
-
-* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
-* **Improve documentation:** Alongside our codebase, documentation is an important part of our open-source journey. We're trying to give the best DX possible to explain ourselves and Permify. And you can help with that by importing resources or adding new ones.
-* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
-
-You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
-
-## Communication Channels
-
-If you like Permify, please consider giving us a :star: on [github](https://github.com/permify/permify)
-
-
+
+Our software does not include built-in support for service meshes (eg. Istio).
However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
+
+
## Core Paths
-- Configure your authorization model with [Schema Write](../api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](../api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](../api-overview/data/read-relationships.md)
-- Check access with [Check API](../api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](../api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](../api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](../api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](../api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](../api-overview/watch/watch-changes.md)
+- Configure your authorization model with [Schema Write](../../api-reference/schema/write-schema)
+- Write relational tuples with [Write Data](../../api-reference/data/write-data)
+- Read relation tuples and filter them with [Read Relationships](../../api-reference/data/read-relationships)
+- Check access with [Check API](../../api-reference/permission/check-api)
+- Check entities permissions with [Lookup Entity](../../api-reference/permission/lookup-entity)
+- Check subject permissions with [Lookup Subject](../../api-reference/permission/lookup-subject)
+- Delete relation tuples with [Delete Tuple](../../api-reference/data/delete-data)
+- Expand schema actions with [Expand API](../../api-reference/permission/expand-api)
+- Watch changes in the relation tuples in real-time with [Watch API](../../api-reference/watch/watch-changes)
## Authentication
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../../reference/configuration)
+You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../../setting-up/configuration)
To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
+## Latency & Performance
+
+With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
+
+Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../operations/cache)
+
## Availability of the Service
For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/examples/facebook-groups.md b/docs/getting-started/examples/facebook-groups.mdx
similarity index 98%
rename from docs/versioned_docs/version-0.4.x/getting-started/examples/facebook-groups.md
rename to docs/getting-started/examples/facebook-groups.mdx
index 1b918630..61fe94e1 100644
--- a/docs/versioned_docs/version-0.4.x/getting-started/examples/facebook-groups.md
+++ b/docs/getting-started/examples/facebook-groups.mdx
@@ -1,8 +1,6 @@
-# Facebook Groups
-
This example demonstrate the authorization structure for Facebook groups, which enables users to perform various actions based on their roles and permissions within the group.
-### Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
+## Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
```perm
// Represents a user
@@ -296,9 +294,7 @@ event:1#group@group:1
Finally, let's check some permissions and test our authorization logic.
-can user:4 RSVP_to_event event:1 ?
-
-
+
```perm
entity event {
@@ -321,14 +317,10 @@ According to what we have defined for the **'RSVP_to_event'** action, users who
According to the relation tuples we created, `user:4` is not the **owner** of the event. Furthermore, when we check whether `user:4` is a **member** of the only group (`group:1`) that `event:1` is part of (`event:1#group@group:1`), we see that there is no **member** relation for `user:4` in that group.
Therefore, the `user:4 RSVP_to_event event:1` check request should yield a **'false'** response.
+
-
-
-
-can user:5 view_comment comment:1 ?
-
-
-```perm
+
+ ```perm
// Represents a post in a Facebook group
entity post {
@@ -369,9 +361,7 @@ entity comment {
According to the relation tuples we created, `user:5` is not the **owner** of the comment. But member of the `group:1` and thats grant `user:5` (`group:1#member@user:5`) access to perform view the comment:1. In particularly, `comment:1` is part of the `post:1` (`comment:1#post@post:1`) and `post:1` is part of the group:1 (`post:1#group@group:1`). And from the action definition on above model group:1 members can view the `comment:1`.
Therefore, the `user:5 view_comment comment:1` check request should yield a **'true'** response.
-
-
-
+
Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/examples/google-docs.md b/docs/getting-started/examples/google-docs.mdx
similarity index 97%
rename from docs/versioned_docs/version-0.4.x/getting-started/examples/google-docs.md
rename to docs/getting-started/examples/google-docs.mdx
index 3f14e1f7..12db3e00 100644
--- a/docs/versioned_docs/version-0.4.x/getting-started/examples/google-docs.md
+++ b/docs/getting-started/examples/google-docs.mdx
@@ -1,5 +1,3 @@
-# Google Docs Simplified
-
This example models a simplified version of Google Docs style permission system where users can be granted direct access to a document, or access via organizations and nested groups.
### Schema | [Open in playground](https://play.permify.co/?s=iuRic3nR1HeZJcFyRNKPo)
@@ -175,10 +173,8 @@ document:hr_documents#viewer@group:hr#direct_member
Finally, let's check some permissions and test our authorization logic.
-can user:ashley edit document:product_database ?
-
-
-```perm
+
+ ```perm
entity document {
relation org @organization
@@ -193,14 +189,10 @@ Finally, let's check some permissions and test our authorization logic.
According what we have defined for the edit action managers and admins, of the organization that document belongs, can edit product database. In this context, Permify engine will check does subject `user:ashley` has any direct or indirect manager relation within `document:product_database`. Consecutively it will check does `user:ashley` has admin relation in the Acme Org - `organization:acme#document@document:product_database`.
Ashley doesn't have any administrative relation in Acme Org but she is the manager in group tech (`group:tech#manager@user:ashley`) and we have defined that manager of group tech is manager of product_database with the tuple (`document:product_database#manager@group:tech#manager`). Therefore, the **user:ashley edit document:product_database** check request should yield **true** response.
+
-
-
-
-can user:joe view document:hr_documents ?
-
-
-```perm
+
+ ```perm
entity document {
relation org @organization
@@ -219,14 +211,10 @@ Joe doesn't have administrative role/relation in Acme Org.
Also he doesn't have have manager relationship in that document or within any entity.
But he is member in the hr group (`group:hr#member@user:joe`) and we defined hr members have viewer relationship in hr documents (`document:hr_documents#viewer@group:hr#member`). So that, this enforcement should yield **true** response.
+
-
-
-```perm
+
+ ```perm
entity document {
relation org @organization
@@ -243,9 +231,7 @@ According what we have defined for the view action viewers or managers or org.ad
Similar Joe and Ashley, David also doesn't have administrative role/relation in Acme Org.
Also David doesn't have member or manager relationship related with marketing group - `document:marketing_materials`. So that, this enforcement should yield **false** response.
-
-
-
+
Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/instagram.md b/docs/getting-started/examples/instagram.mdx
similarity index 89%
rename from docs/versioned_docs/version-0.5.x/getting-started/examples/instagram.md
rename to docs/getting-started/examples/instagram.mdx
index 9cd83163..5353424f 100644
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/instagram.md
+++ b/docs/getting-started/examples/instagram.mdx
@@ -1,5 +1,3 @@
-# Instagram
-
This example presents an Instagram Authorization Schema, outlining the intricate relationships between users, accounts, and posts on the platform. It defines user access levels, privacy settings, and interactions, offering insights into how followers, account owners, and post restrictions are managed within the Instagram ecosystem.
## Schema | [Open in playground](https://play.permify.co/?s=instagram&tab=schema)
@@ -88,13 +86,9 @@ To validate our authorization logic, let's run some tests on different scenarios
### Test 1: Checking Account Viewing Permissions
-
-
- Can user:kevin view account:1?
-
-
-
+
+
```perm
entity account {
relation owner @user
@@ -106,18 +100,10 @@ To validate our authorization logic, let's run some tests on different scenarios
```
According to the schema, `user:kevin` is the owner of `account:1`. Hence, `user:kevin` should be able to view `account:1`. The expected result is `'true'`.
+
-
-
-
-
-
- Can user:kevin view account:2?
-
-
-
-
-```perm
+
+ ```perm
entity account {
relation owner @user
relation following @user
@@ -128,17 +114,10 @@ According to the schema, `user:kevin` is the owner of `account:1`. Hence, `user:
```
According to the schema, `user:kevin` follows `account:2`. Hence, `user:kevin` should be able to view `account:2` because he is a follower. The expected result is `'true'`.
+
-
-
-
-
-
- Can user:george view account:1?
-
-
-
-
+
+
```perm
entity account {
relation owner @user
@@ -150,18 +129,10 @@ According to the schema, `user:kevin` follows `account:2`. Hence, `user:kevin` s
```
According to the schema, `user:george` can view `account:1`, because the account is public. Hence, `user:george` should be able to view `account:1`. The expected result is `'true'`.
+
-
-
-
-
-
- Can user:george view account:2?
-
-
-
-
-```perm
+
+ ```perm
entity account {
relation owner @user
relation following @user
@@ -172,17 +143,12 @@ According to the schema, `user:george` can view `account:1`, because the account
```
According to the schema, `user:george` is the owner of `account:2`. Hence, `user:george` should be able to view `account:2`. The expected result is `'true'`.
-
-
-
+
### Test 2: Checking Post Viewing Permissions
-Can user:george view post:1?
-
-
-
-```perm
+
+ ```perm
entity post {
relation account @account
attribute restricted boolean
@@ -191,13 +157,9 @@ entity post {
```
According to the schema, `post:1` is linked with `account:1`, and it does not have restricted access. Also, `user:george` is following `account:1`. Hence, `user:george` should be able to view `post:1`. The expected result is `'true'`.
+
-
-
-
-Can user:kevin view post:2?
-
-
+
```perm
entity post {
relation account @account
@@ -207,14 +169,10 @@ entity post {
```
According to the schema, `post:2` is linked with `account:2`, and it has restricted access. Also, `user:george` is not following `account:1`. Hence, `user:kevin` should not be able to view `post:2`. The expected result is `'false'`.
+
-
-
-
-Can user:george view post:2?
-
-
-```perm
+
+ ```perm
entity post {
relation account @account
attribute restricted boolean
@@ -223,15 +181,11 @@ entity post {
```
According to the schema, `post:2` is linked with `account:2`, and it is restricted access. Also, `user:george` can view his own `post:2`. The expected result is `'true'`.
-
-
-
+
### Test 3: Checking Post Commenting Permissions
-Can user:george comment post:1?
-
-
+
```perm
entity post {
relation account @account
@@ -241,14 +195,10 @@ entity post {
```
According to the schema, `post:1` is linked with `account:1`, and it is not restricted. Also, `user:george` can comment on `post:1`. The expected result is `'true'`.
+
-
-
-
-Can user:kevin comment post:2?
-
-
-```perm
+
+ ```perm
entity post {
relation account @account
attribute restricted boolean
@@ -257,9 +207,7 @@ entity post {
```
According to the schema, `post:2` is linked with `account:2`, and it is restricted. `user:kevin` cannot comment on `post:2`. The expected result is `'false'`.
-
-
-
+
Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
diff --git a/docs/versioned_docs/version-0.6.x/examples.md b/docs/getting-started/examples/intro.mdx
similarity index 67%
rename from docs/versioned_docs/version-0.6.x/examples.md
rename to docs/getting-started/examples/intro.mdx
index ecc4d10a..2b76a3c6 100644
--- a/docs/versioned_docs/version-0.6.x/examples.md
+++ b/docs/getting-started/examples/intro.mdx
@@ -1,8 +1,7 @@
---
id: examples
-title: Real World Examples
+title: Introduction
sidebar_label: Real World Examples
-slug: /getting-started/examples
---
* [Google Docs]: Explore how users can gain direct access to a document through **organizational roles** or through **inherited/nested permissions**.
@@ -11,8 +10,8 @@ slug: /getting-started/examples
* [Instagram]: Explore how **public/private attributes** play role in granting access to specific users.
* [Mercury]: Explore how **attributes and rules interact within the hierarchical relationships**.
-[Google Docs]:./getting-started/examples/google-docs.md
-[Facebook Groups]:./getting-started/examples/facebook-groups.md
-[Notion]:./getting-started/examples/notion.md
-[Instagram]:./getting-started/examples/instagram.md
-[Mercury]:./getting-started/examples/mercury.md
\ No newline at end of file
+[Google Docs]:./google-docs
+[Facebook Groups]:./facebook-groups
+[Notion]:./notion
+[Instagram]:./instagram
+[Mercury]:./mercury
\ No newline at end of file
diff --git a/docs/docs/getting-started/examples/mercury.md b/docs/getting-started/examples/mercury.mdx
similarity index 94%
rename from docs/docs/getting-started/examples/mercury.md
rename to docs/getting-started/examples/mercury.mdx
index 796c6211..85b88b13 100644
--- a/docs/docs/getting-started/examples/mercury.md
+++ b/docs/getting-started/examples/mercury.mdx
@@ -1,12 +1,12 @@
-# Mercury
-
Explore **Mercury's Authorization Schema** in this example, delving into the intricate interplay among **users**, **organizations**, and **accounts**. Uncover the defined user roles, approval workflows, and limits, providing a snapshot of the dynamic relationships within the Mercury ecosystem.
For those who don’t know, Mercury is a bank offering both checking and savings accounts, complete with debit and credit card features. Given the delicate nature of financial transactions, Mercury has built-in access control features to ensure security.
But today we’re going to focus on approvals. Mercury allows it’s users to set a number amount for multiple user approval for any action.
-For instance, an admin can decide that withdrawals above $1000 by members require approval from two designated approvers. This means, if a member wants to withdraw more than $1000, they need a green light from two admin. And if an admin tries to withdraw they need an approval form another admin.
+For instance, an admin can decide that withdrawals above $1000 by members require approval from two designated approvers.
+
+This means, if a member wants to withdraw more than $1000, they need a green light from two admin. And if an admin tries to withdraw they need an approval form another admin.
- Admin → Withdraw $1000 → needs an approver
- Member → Withdraw $1000 → needs 2 approvers.
diff --git a/docs/docs/getting-started/examples/notion.md b/docs/getting-started/examples/notion.mdx
similarity index 98%
rename from docs/docs/getting-started/examples/notion.md
rename to docs/getting-started/examples/notion.mdx
index 9095d464..d21851ce 100644
--- a/docs/docs/getting-started/examples/notion.md
+++ b/docs/getting-started/examples/notion.mdx
@@ -1,5 +1,3 @@
-# Notion
-
This is a schema definition of the authorization model for Notion, a popular productivity and organization tool.
### Schema | [Open in playground](https://play.permify.co/?s=BsCvLmd4g81sB20XJZI5p)
@@ -261,10 +259,8 @@ comment:task_list_2_comment_2#author@user:charlie
Since we have our schema and the sample relation tuples, let's check some permissions and test our authorization logic.
-can user:alice write database:task_list ?
-
-
-```perm
+
+ ```perm
entity database {
// The workspace associated with the database
relation workspace @workspace
@@ -316,13 +312,10 @@ entity workspace {
And as we mentioned the engineering team workspace is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`). Therefore, the `user:alice write database:task_list` check request should yield a **'true'** response.
-
-
+
-can user:charlie write page:product_spec ?
-
-
-```perm
+
+ ```perm
entity page {
// The workspace associated with the page
relation workspace @workspace
@@ -355,9 +348,7 @@ entity workspace {
```
So that, `user:charlie` doesn't have a write relationship in the workspace. And ultimately, the `user:charlie write page:product_spec` check request should yield a **'false'** response.
-
-
-
+
Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
diff --git a/docs/docs/getting-started/modeling.md b/docs/getting-started/modeling.mdx
similarity index 89%
rename from docs/docs/getting-started/modeling.md
rename to docs/getting-started/modeling.mdx
index 2a5fbc60..06d45927 100644
--- a/docs/docs/getting-started/modeling.md
+++ b/docs/getting-started/modeling.mdx
@@ -1,12 +1,11 @@
---
-sidebar_position: 1
+icon: "code"
+title: "Modeling Authorization"
---
-# Modeling Authorization
+Permify was designed and structured as a true ReBAC solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-Permify was designed and structured as a true ReBAC solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-
-With Permify, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group.
+With Permify, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group.
This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
@@ -28,9 +27,9 @@ Permify Schema can be created on our [playground](https://play.permify.co/) as w
This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-We'll follow a simplified version of the GitHub access control system, where teams and organizations have control over the viewing, editing, or deleting access rights of repositories.
+We'll follow a simplified version of the GitHub access control system, where teams and organizations have control over the viewing, editing, or deleting access rights of repositories.
-Before start I want to share the full implementation of simple Github access control example with using Permify Schema.
+Before start I want to share the full implementation of simple Github access control example with using Permify Schema.
```perm
entity user {}
@@ -68,14 +67,14 @@ entity repository {
}
```
-:::info
+
You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-:::
+
-## Defining Entities
+## Defining Entities
The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
@@ -100,7 +99,7 @@ Entities has 2 different attributes. These are;
## Defining Relations
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions.
+Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions.
Keyword **_relation_** need to used to create a entity relation with name and type attributes.
@@ -117,7 +116,7 @@ relation [name] @[type]
Lets turn back to our example and define our relations inside our entities:
-#### User Entity
+### User Entity
→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
@@ -127,7 +126,7 @@ entity user {}
### Roles and User Types
-You can define user types and roles within the entity. If you specifically want to define a global role, such as `admin`, we advise defining it at the entity with the most global hierarchy, such as an organization. Then, spread it to the rest of the entities to include it within permissions.
+You can define user types and roles within the entity. If you specifically want to define a global role, such as `admin`, we advise defining it at the entity with the most global hierarchy, such as an organization. Then, spread it to the rest of the entities to include it within permissions.
For the sake of simplicity, let's define only 2 user types in an organization, these are administrators and direct members of the organization.
@@ -189,7 +188,7 @@ As you can see we have new syntax above,
When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-:::info
+
You can use **#** to reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
Actual purpose of feature locking is to giving ability to specify the sets of users that can be assigned.
@@ -217,19 +216,19 @@ You will then be able to specify not only individual users but also members of a
- organization:1#viewer@user:U2
- organization:1#viewer@organization:O1#member
-
With `organization:1#viewer@organization:O1#member` all members of the organization O1 will have the right to perform the relevant action.
In other words, all members in O1 now end up having the relevant `viewer` relation.
You can think of these definitions as a precaution taken against creating undesired user set relationships.
-:::
+
+
Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
## Defining Actions and Permissions
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances.
+Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances.
The basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
@@ -260,7 +259,7 @@ entity repository {
→ If we examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-:::info Permission Keyword
+
The same `read` can also be defined using the **permission** keyword, as follows:
```perm
@@ -268,15 +267,16 @@ The same `read` can also be defined using the **permission** keyword, as follows
```
Using `action` and `permission` will yield the same result for defining permissions in your authorization logic. See why we have 2 keywords for defining an permission from the [Nested Hierarchies](#nested-hierarchies) section.
-:::
+
+
#### Exclusion
-After this point, we'll move beyond the GitHub example and explore more advanced abilities of Permify DSL.
+After this point, we'll move beyond the GitHub example and explore more advanced abilities of Permify DSL.
Before delving into details, let's examine the **`not`** operator and conclude [Intersection and Exclusion](#intersection-and-exclusion) section.
-Here is the **post** entity from our sample [Instagram Authorization Structure](./examples/google-docs.md)example,
+Here is the **post** entity from our sample [Instagram Authorization Structure](./examples/instagram) example,
```perm
entity post {
@@ -301,7 +301,7 @@ This is a simple example to demonstrate how you can exclude users, resources, or
### Permission Union
-Permify allows you to set permissions that are effectively the union of multiple permission sets.
+Permify allows you to set permissions that are effectively the union of multiple permission sets.
You can define permissions as relations to union all rules that permissions have. Here is an simple demonstration how to achieve permission union in our DSL, you can use actions (or permissions) when defining another action (or permission) like relations,
@@ -314,20 +314,20 @@ The `delete` action inherits the rules from the `edit` action. By doing that, we
Permission union is super beneficial in scenarios where a user needs to have varied access across different departments or roles.
-### Nested Hierarchies
+### Nested Hierarchies
The reason we have two keywords for defining permissions (`action` and `permission`) is that while most permissions are based on actions (such as view, read, edit, etc.), there are still cases where we need to define permissions based on roles or user types, such as admin or member.
-Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
+Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
Here is a simple example to demonstrate inherited permissions.
-Let's examine a small snippet from our [Facebook Groups](./examples/google-docs.md) real world example. Let's create a permission called 'view' in the comment entity (which represents the comments of the post in Facebook Groups)
+Let's examine a small snippet from our [Facebook Groups](./examples/google-docs) real world example. Let's create a permission called 'view' in the comment entity (which represents the comments of the post in Facebook Groups)
Users can only view a comment if:
-- The user is the owner of that comment
-**or**
+- The user is the owner of that comment
+ **or**
- The user is a member of the group to which the comment's post belongs.
```perm
@@ -341,7 +341,7 @@ entity post {
relation group @group
// Permissions for the post entity
-
+
..
..
permission group_member = group.member
@@ -360,7 +360,7 @@ entity comment {
..
..
- // Permissions
+ // Permissions
action view = owner or post.group_member
..
@@ -374,7 +374,7 @@ The `post.group_member` refers to the members of the group to which the post bel
permission group_member = group.member
```
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
+Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
@@ -384,7 +384,7 @@ With Permify DSL, you can define recursive relationship-based permissions within
As an example, consider a system where there are multiple organizations within a company, some of which may have a parent-child relationship between them.
-As expected, organization members are also granted permission to view their organization details. You can model that as follows:
+As expected, organization members are also granted permission to view their organization details. You can model that as follows:
```perm
entity user {}
@@ -401,9 +401,9 @@ Let's extend the scenario by adding a rule allowing parent organization members

-First authorization schema that we provide won't solve this issue because `parent.member` accommodate single upward traversal in a hierarchy.
+First authorization schema that we provide won't solve this issue because `parent.member` accommodate single upward traversal in a hierarchy.
-Instead of `parent.member` we can call the parent view permission on the same entity - `parent.view` to achieve multiple levels of upward traversal, as follows:
+Instead of `parent.member` we can call the parent view permission on the same entity - `parent.view` to achieve multiple levels of upward traversal, as follows:
```perm
entity user {}
@@ -418,9 +418,10 @@ entity organization {
This way, we achieve a recursive relationship between parent-child organizations.
-:::note
-*Credits to [Léo](https://github.com/LeoFVO) for the illustration and for [highlighting](https://github.com/Permify/permify/issues/790) this use case.*
-:::
+
+ *Credits to [Léo](https://github.com/LeoFVO) for the illustration and for
+ [highlighting](https://github.com/Permify/permify/issues/790) this use case.*
+
## Attribute Based Permissions (ABAC)
@@ -450,7 +451,7 @@ string
string[]
// An integer attribute type.
-integer
+integer
// An integer array attribute type.
integer[]
@@ -472,7 +473,7 @@ In the following example schema, a rule could be used to check if a given IP add
entity user {}
entity organization {
-
+
relation admin @user
attribute ip_range string[]
@@ -485,11 +486,12 @@ rule check_ip_range(ip string, ip_range string[]) {
}
```
-:::info Syntax
-We design our schema language based on [Common Expression Language (CEL)](https://github.com/google/cel-go). So the syntax looks nearly identical to equivalent expressions in C++, Go, Java, and TypeScript.
+
+We design our schema language based on [Common Expression Language (CEL)](https://github.com/google/cel-go). So the syntax looks nearly identical to equivalent expressions in C++, Go, Java, and TypeScript.
Please let us know via our [Discord channel](https://discord.gg/n6KfzYxhPp) if you have questions regarding syntax, definitions or any operator you identify not working as expected.
-:::
+
+
Let's examine some of common usage of ABAC with small schema examples.
@@ -500,14 +502,15 @@ For attributes that represent a binary choice or state, such as a yes/no questio
```perm
entity post {
attribute is_public boolean
-
+
permission view = is_public
}
```
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
-:::
+
+ ⛔ If you don’t create the related attribute data, Permify accounts boolean as
+ `FALSE`
+
### Text & Object Based Conditions
@@ -522,7 +525,7 @@ String can be used as attribute data type in a variety of scenarios where text-b
entity user {}
entity organization {
-
+
relation admin @user
attribute location string[]
@@ -535,15 +538,16 @@ rule check_location(current_location string, location string[]) {
}
```
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts string as `""`
-:::
+
+ ⛔ If you don’t create the related attribute data, Permify accounts string as
+ `""`
+
### Numerical Conditions
#### Integers
-Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
+Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
@@ -560,9 +564,10 @@ rule check_age(age integer) {
}
```
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts integer as `0`
-:::
+
+ ⛔ If you don’t create the related attribute data, Permify accounts integer as
+ `0`
+
#### Double - Precise numerical information
@@ -588,9 +593,10 @@ rule check_balance(amount double, balance double) {
}
```
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts double as `0.0`
-:::
+
+ ⛔ If you don’t create the related attribute data, Permify accounts double as
+ `0.0`
+
See more details on [Attribute Based Access Control](#attribute-based-permissions-abac) section to learn our approach on ABAC as well as how it operates in Permify. you can see more comprehensive ABAC examples in the [Example ABAC Use Cases](../use-cases/abac/#example-use-cases) section in related page.
@@ -600,14 +606,14 @@ You can check out more comprehensive schema examples from the [Real World Exampl
Here is what each example focuses on,
-* [Google Docs]: how users can gain direct access to a document through **organizational roles** or through **inherited/nested permissions**.
-* [Facebook Groups]: how users can perform various actions based on the **roles and permissions within the groups** they belong.
-* [Notion]: how **one global entity (workspace) can manage access rights** in the child entities that belong to it.
-* [Instagram]: how **public/private attributes** play role in granting access to specific users.
-* [Mercury]: how **attributes and rules interact within the hierarchical relationships**.
-
-[Google Docs]:./examples/google-docs.md
-[Facebook Groups]:./examples/facebook-groups.md
-[Notion]:./examples/notion.md
-[Instagram]:./examples/instagram.md
-[Mercury]:./examples/mercury.md
\ No newline at end of file
+- [Google Docs]: how users can gain direct access to a document through **organizational roles** or through **inherited/nested permissions**.
+- [Facebook Groups]: how users can perform various actions based on the **roles and permissions within the groups** they belong.
+- [Notion]: how **one global entity (workspace) can manage access rights** in the child entities that belong to it.
+- [Instagram]: how **public/private attributes** play role in granting access to specific users.
+- [Mercury]: how **attributes and rules interact within the hierarchical relationships**.
+
+[Google Docs]: ./examples/google-docs
+[Facebook Groups]: ./examples/facebook-groups
+[Notion]: ./examples/notion
+[Instagram]: ./examples/instagram
+[Mercury]: ./examples/mercury
diff --git a/docs/versioned_docs/version-0.6.x/installation/overview.md b/docs/getting-started/quickstart.mdx
similarity index 81%
rename from docs/versioned_docs/version-0.6.x/installation/overview.md
rename to docs/getting-started/quickstart.mdx
index 76fb8a56..b05c6674 100644
--- a/docs/versioned_docs/version-0.6.x/installation/overview.md
+++ b/docs/getting-started/quickstart.mdx
@@ -1,25 +1,23 @@
---
-sidebar_position: 1
+icon: "rocket"
+title: Quickstart
---
-# Guide
-
This guide shows you how to set up Permify in your servers and use it across your applications.
-:::info Minimum Requirements
+## Minimum Requirements
PostgreSQL: Version 13.8 or higher
-:::
Please ensure your system meets these requirements before proceeding with the following steps:
1. [Set Up & Run Permify Service](#set-up-permify-service)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Manage and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
+2. [Model your Authorization with Permify Schema](#model-your-authorization-with-permify-schema)
+3. [Store Authorization Data & Schema](#store-authorization-data)
4. [Perform Access Check](#perform-access-check)
-:::info Talk to an Permify Engineer
+
Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
+
## Set Up Permify Service
@@ -40,11 +38,11 @@ This will start Permify with the default configuration options:
* Port 3478 is used to serve the GRPC Service.
* Authorization data stored in memory.
-:::info
+
You can examine [Deploy using Docker] section to get more about the configuration options and learn the full integration to run Permify Service from docker container.
-[Deploy using Docker]: ../container
-:::
+[Deploy using Docker]: ../setting-up/installation/container
+
### Test your connection
@@ -56,10 +54,30 @@ localhost:3476/healthz
You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core endpoints.
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
+[Using the API]: ../getting-started/enforcement
+
+
## Model your Authorization with Permify Schema
@@ -71,14 +89,13 @@ You can define your entities, relations between them and access control decision
Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-:::caution Use Playground For Testing
+
If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.

-
-:::
+
Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
@@ -106,45 +123,44 @@ Lets roll back our example,
- Organization member and admin can view files.
- Only admins can edit files.
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
+
+For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also you can check out [Real World Examples] section to better understand some familiar use cases modeled with Permify Schema.
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../use-cases/simple-rbac
-:::
+[Modeling Authorization with Permify]: ../getting-started/modeling
+[Real World Examples]: ../getting-started/examples/intro
+
### Configuring Schema via API
-After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../api-overview/schema/write-schema.md) for configuration of your authorization model on Permify authorization service.
+After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../../api-reference/schema/write-schema) for configuration of your authorization model on Permify authorization service.
-:::caution Before Continue on Writing Schema
+
You'll see **tenant_id** parameter almost all Permify APIs including Write Schema. With version 0.3.x Permify became a tenancy based authorization infrastructure, and supports multi-tenancy by default so its a mandatory parameter when doing any operations.
-We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
-:::
+We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
+
-#### Example HTTP Request on Postman:
+
+**Example HTTP Request on Postman:**
| Required | Argument | Type | Default | Description |
|----------|-------------------|--------|---------|-------------|
| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
| [x] | schema | string | - | Permify Schema as string|
-**POST /v1/tenants/{tenant_id}/schemas/write**
+**POST** `/v1/tenants/{tenant_id}/schemas/write`

-## Store Authorization Data as Relational Tuples
+## Store Authorization Data
After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action.
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules by using [Write Data API](../api-overview/data/write-data.md)
+You can write relationships and attributes as ACLs by using [Write Data API](../../api-reference/data/write-data)
For our guide let's grant one of the team members (Ashley) an admin role.
-#### Example HTTP Request on Postman:
+**Example HTTP Request on Postman:**
| Required | Argument | Type | Default | Description |
|----------|-------------------|--------|---------|-------------|
@@ -155,7 +171,7 @@ For our guide let's grant one of the team members (Ashley) an admin role.
| [x] | subject | string | - | User or user set who wants to take the action. |
| [ ] | schema_version | string | 8 | Version of the schema |
-**POST /v1/tenants/{tenant_id}/data/write**
+**POST** `/v1/tenants/{tenant_id}/data/write`
```json
{
@@ -181,17 +197,17 @@ For our guide let's grant one of the team members (Ashley) an admin role.

-**Created relational tuple:** organization:1#admin@user:1
+**Created relationship:** organization:1#admin@user:1
**Semantics:** User 1 (Ashley) has admin role on organization 1.
-:::tip
+
In ideal production usage Permify stores your authorization data in a database you prefer. You can configure the database with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) or CLI flag options.
But in this tutorial Permify Service running default configurations on local, so authorization data will be stored in memory. You can find more detailed explanation how Permify stores authorization data in [Managing Authorization Data] section.
-[Managing Authorization Data]: ../../getting-started/sync-data
-:::
+[Managing Authorization Data]: ../getting-started/sync-data
+
## Perform Access Check
@@ -199,14 +215,12 @@ Finally we're ready to control authorization. Access decision results computed a
Lets get back to our example and perform an example access check via [Check API]. We want to check whether an specific user has an access to view files in a organization.
-[Check API]: ../../api-overview/permission/check-api
-[Permify Schema]: ../../getting-started/modeling
-
-#### Example HTTP Request:
+[Check API]: ../../../api-reference/permission/check-api
+[Permify Schema]: ../getting-started/modeling
***Can the user 45 view files on organization 1 ?***
-**POST /v1/tenants/{tenant_id}/permissions/check**
+**POST** `/v1/tenants/{tenant_id}/permissions/check`
| Required | Argument | Type | Default | Description |
|----------|----------------|----------|---------|---------------------------------------------------------------------------------------------------------------------------------------------------|
@@ -217,7 +231,7 @@ Lets get back to our example and perform an example access check via [Check API]
| [ ] | schema_version | string | - | get results according to given schema version |
| [ ] | depth | integer | 8 | - |
-### Request
+**Request:**
```json
{
@@ -239,7 +253,7 @@ Lets get back to our example and perform an example access check via [Check API]
}
```
-### Response
+**Response**
```json
{
@@ -252,7 +266,7 @@ Lets get back to our example and perform an example access check via [Check API]
See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-[Access Control Check]: ../api-overview/permission/check-api.md
+[Access Control Check]: ../../api-reference/permission/check-api
## Need any help ?
diff --git a/docs/docs/getting-started/sync-data.md b/docs/getting-started/sync-data.mdx
similarity index 89%
rename from docs/docs/getting-started/sync-data.md
rename to docs/getting-started/sync-data.mdx
index 07f0759f..1fde3de0 100644
--- a/docs/docs/getting-started/sync-data.md
+++ b/docs/getting-started/sync-data.mdx
@@ -1,19 +1,16 @@
---
sidebar_position: 2
+title: Storing Data & Schema
+icon: 'database'
---
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Managing Authorization Data
-
-Permify unifies your authorization data in a database of your preference, which serves as the single source of truth for all authorization queries and requests via the Permify API.
+Permify unifies your authorization data and the authorization schemas you have in a database of your preference, which serves as the single source of truth for all authorization queries and requests via the Permify API.
In Permify, you can store authorization data in two different forms: as **relationships** and as **attributes**.
Let's examine relationships first.
-## Access Control as Relationships
+## Relationships
In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
@@ -45,7 +42,7 @@ Here are some attributes with semantics,
These relational tuples and attributes represents your authorization data.
-Permify stores your these data in a database you prefer. You can configure the database when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
+Permify stores your these data in a database you prefer. You can configure the database when running Permify Service with using [configuration options](../setting-up/configuration).
Stored data are queried and utilized in Permify APIs, including the check API, which is an access control check request used to determine whether a user's action is authorized.
@@ -57,7 +54,7 @@ Relationships and attributes can be created with an simple API call, Since these
Each relational tuple or attribute should be created according to its authorization model, [Permify Schema].
-[Permify Schema]: ../modeling
+[Permify Schema]: ./modeling

@@ -94,7 +91,7 @@ According to the schema above; when a user creates a document in an organization
You can create relational tuples by using `Write Data API`.
-
+
```go
rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
@@ -117,10 +114,9 @@ rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
},
})
```
+
-
-
-
+
```javascript
client.data.write({
@@ -144,8 +140,8 @@ client.data.write({
})
```
-
-
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -170,7 +166,7 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
]
}'
```
-
+
### Snap Tokens
@@ -183,7 +179,7 @@ In Write Data API response you'll get a snap token of the operation.
}
```
-This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../reference/snap-tokens.md)
+This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../operations/snap-tokens)
## More Examples
@@ -196,7 +192,7 @@ Let's create more example data according to the schema we defined above.
**Semantics:** User 3 is administrator in organization 1.
-
+
```go
rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
@@ -220,9 +216,9 @@ rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
})
```
-
+
-
+
```javascript
client.data.write({
@@ -246,8 +242,8 @@ client.data.write({
})
```
-
-
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -272,7 +268,7 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
]
}'
```
-
+
### Parent Organization
@@ -282,7 +278,7 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
**Semantics:** Organization 1 is parent of document 1.
-
+
```go
rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
@@ -307,9 +303,9 @@ rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
})
```
-
+
-
+
```javascript
client.data.write({
@@ -334,8 +330,8 @@ client.data.write({
})
```
-
-
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -360,14 +356,14 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
]
}'
```
-
+
-:::info
+
Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
Simply, the usage of ... is straightforward: if you're use user entity as an subject, you should not be using the `...` If you're using another subject rather than user entity then you need to use the `...`
-:::
+
### Organization Members Are Maintainers in specific Doc
@@ -376,7 +372,7 @@ Simply, the usage of ... is straightforward: if you're use user entity as an sub
**Definition:** Members of organization 2 are maintainers in document 1.
-
+
```go
rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
@@ -401,9 +397,9 @@ rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
})
```
-
+
-
+
```javascript
client.data.write({
@@ -428,8 +424,8 @@ client.data.write({
})
```
-
-
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
@@ -454,10 +450,10 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write
]
}'
```
-
+
-#### Test this Example on [Playground](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_)
+**Test this Example on [Playground](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_)**
## Audit Logs For Permission Changes
@@ -473,8 +469,4 @@ We have a strong foundation for permission baselining and review, thanks to MVCC
**Current State Review:** You can review the current state of permissions by examining the latest versions of each permission setting.
-**Cleanup:** Your system incorporates a garbage collector for managing old data, which helps keep your permissions structure clean and optimized.
-
-## Next
-
-Let's now head over to the **Access Control Check** section and learn how to perform access control in Permify to ensure that only authorized users have the right level of access to our resources.
+**Cleanup:** Your system incorporates a garbage collector for managing old data, which helps keep your permissions structure clean and optimized.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/testing.md b/docs/getting-started/testing.mdx
similarity index 97%
rename from docs/versioned_docs/version-0.5.x/getting-started/testing.md
rename to docs/getting-started/testing.mdx
index 977fcf2d..6cad8524 100644
--- a/docs/versioned_docs/version-0.5.x/getting-started/testing.md
+++ b/docs/getting-started/testing.mdx
@@ -1,18 +1,18 @@
---
sidebar_position: 4
+icon: 'vial'
+title: 'Testing & Validation'
---
-# Testing & Validation
-
Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-:::info
+
If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
+
## Adding Validate Action To Your Workflow
@@ -34,9 +34,9 @@ steps:
validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
```
-:::info
+
If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
+
## Schema Validation File
@@ -188,11 +188,11 @@ checks:
Semantics for above check is: whether `user:1` can push to `repository:3`, additional to stored tuples take account that user:1 is owner of repository:3 (`repository:3#owner@user:1`). Expected result for that check it **true** - `push : true`
-:::info Contextual Tuples
+
We use `context` (Contextual Tuples) with simple relational tuples for simplicity in this example. However, it is primarily used for dynamic access checks, such as those involving time, date, or IP address, etc.
-To learn more about how `context` works, see the [Contextual Tuples](../../reference/contextual-tuples) section.
-:::
+To learn more about how `context` works, see the [Contextual Tuples](../operations/contextual-tuples) section.
+
### Entity Filtering
@@ -223,9 +223,9 @@ You can create `subject_filters` within `scenarios` to test your subject filteri
edit : ["58"]
```
-:::info API Endpoints
-You can find the related API endpoints for `check`, `entity_filters`, and `subject_filters` in the Permission service in the [Using The API](../../api-overview) section.
-:::
+
+You can find the related API endpoints for `check`, `entity_filters`, and `subject_filters` in the Permission service in the [Using The API](../getting-started/enforcement) section.
+
## Coverage Analysis
@@ -268,7 +268,7 @@ For managing permission/relation changes, we suggest storing schema in an abstra
We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-You can find more details about our suggested workflow to handle schema changes in [Write Schema](../../api-overview/schema/write-schema#suggested-workflow-for-schema-changes) section.
+You can find more details about our suggested workflow to handle schema changes in following [FAQS page](../introduction/faqs#how-to-manage-schema-changes).
## Need any help ?
diff --git a/docs/images/checks-passed.png b/docs/images/checks-passed.png
new file mode 100644
index 00000000..3303c773
Binary files /dev/null and b/docs/images/checks-passed.png differ
diff --git a/docs/images/hero-dark.svg b/docs/images/hero-dark.svg
new file mode 100644
index 00000000..c6a30e88
--- /dev/null
+++ b/docs/images/hero-dark.svg
@@ -0,0 +1,161 @@
+
diff --git a/docs/images/hero-light.svg b/docs/images/hero-light.svg
new file mode 100644
index 00000000..297d68fb
--- /dev/null
+++ b/docs/images/hero-light.svg
@@ -0,0 +1,155 @@
+
diff --git a/docs/logo/.DS_Store b/docs/logo/.DS_Store
new file mode 100644
index 00000000..5008ddfc
Binary files /dev/null and b/docs/logo/.DS_Store differ
diff --git a/docs/logo/dark.svg b/docs/logo/dark.svg
new file mode 100644
index 00000000..a784a21f
--- /dev/null
+++ b/docs/logo/dark.svg
@@ -0,0 +1,9 @@
+
diff --git a/docs/logo/light.svg b/docs/logo/light.svg
new file mode 100644
index 00000000..c4158bf8
--- /dev/null
+++ b/docs/logo/light.svg
@@ -0,0 +1,9 @@
+
diff --git a/docs/mint.json b/docs/mint.json
new file mode 100644
index 00000000..4c5bbe79
--- /dev/null
+++ b/docs/mint.json
@@ -0,0 +1,189 @@
+{
+ "$schema": "https://mintlify.com/schema.json",
+ "name": "Permify Docs",
+ "logo": {
+ "dark": "/logo/dark.svg",
+ "light": "/logo/light.svg"
+ },
+ "favicon": "/favicon.svg",
+ "colors": {
+ "primary": "#8246FF",
+ "light": "#8246FF",
+ "dark": "#6318FF",
+ "anchors": {
+ "from": "#8246FF",
+ "to": "#8246FF"
+ }
+ },
+ "openapi": ["./api-reference/openapi.json"],
+ "topbarLinks": [
+ {
+ "name": "Support",
+ "url": "https://discord.com/invite/n6KfzYxhPp"
+ }
+ ],
+ "modeToggle": {
+ "default": "dark"
+ },
+ "analytics": {
+ "plausible": {
+ "domain": "docs.permify.co"
+ }
+ },
+ "topbarCtaButton": {
+ "name": "Playground",
+ "url": "https://play.permify.co/?s=organizations-hierarchies"
+ },
+ "tabs": [
+ {
+ "name": "API Reference",
+ "url": "api-reference"
+ }
+ ],
+ "anchors": [
+ {
+ "name": "Community",
+ "icon": "discord",
+ "url": "https://discord.com/invite/n6KfzYxhPp"
+ },
+ {
+ "name": "Open Source",
+ "icon": "github",
+ "url": "https://github.com/Permify/permify"
+ }
+ ],
+ "navigation": [
+ {
+ "group": "Introduction",
+ "pages": [
+ "permify-overview/intro",
+ "permify-overview/authorization-service",
+ "permify-overview/faqs"
+ ]
+ },
+ {
+ "group": "Getting Started",
+ "pages": [
+ "getting-started/quickstart",
+ "getting-started/modeling",
+ "getting-started/sync-data",
+ "getting-started/enforcement",
+ "getting-started/testing",
+ {
+ "group": "Real World Examples",
+ "icon": "globe",
+ "pages": [
+ "getting-started/examples/intro",
+ "getting-started/examples/facebook-groups",
+ "getting-started/examples/google-docs",
+ "getting-started/examples/instagram",
+ "getting-started/examples/mercury",
+ "getting-started/examples/notion"
+ ]
+ }
+ ]
+ },
+ {
+ "group": "Setting Up",
+ "icon": "cloud-arrow-up",
+ "pages": [
+ "setting-up/configuration",
+ {
+ "group": "Deployment",
+ "icon": "cloud-arrow-up",
+ "pages": [
+ "setting-up/installation/intro",
+ "setting-up/installation/aws",
+ "setting-up/installation/brew",
+ "setting-up/installation/container",
+ "setting-up/installation/google",
+ "setting-up/installation/helm",
+ "setting-up/installation/kubernetes"
+ ]
+ }
+ ]
+ },
+ {
+ "group": "Operations",
+ "pages": [
+ "operations/bundle",
+ "operations/cache",
+ "operations/contextual-tuples",
+ "operations/tracing",
+ "operations/snap-tokens"
+ ]
+ },
+ {
+ "group": "Use Cases",
+ "pages": [
+ "use-cases/rbac",
+ "use-cases/rebac",
+ "use-cases/abac",
+ "use-cases/custom-roles",
+ "use-cases/multi-tenancy"
+ ]
+ },
+ {
+ "group": "API Documentation",
+ "pages": [
+ "api-reference/introduction"
+ ]
+ },
+ {
+ "group": "Schema Service",
+ "pages": [
+ "api-reference/schema/write-schema",
+ "api-reference/schema/list-schema",
+ "api-reference/schema/read-schema"
+ ]
+ },
+ {
+ "group": "Data Service",
+ "pages": [
+ "api-reference/data/write-data",
+ "api-reference/data/read-relationships",
+ "api-reference/data/read-attributes",
+ "api-reference/data/run-bundle",
+ "api-reference/data/delete-data"
+ ]
+ },
+ {
+ "group": "Permission Service",
+ "pages": [
+ "api-reference/permission/check-api",
+ "api-reference/permission/expand-api",
+ "api-reference/permission/lookup-subject",
+ "api-reference/permission/lookup-entity",
+ "api-reference/permission/lookup-entity-stream",
+ "api-reference/permission/subject-permission"
+ ]
+ },
+ {
+ "group": "Tenancy Service",
+ "pages": [
+ "api-reference/tenancy/list-tenants",
+ "api-reference/tenancy/create-tenant",
+ "api-reference/tenancy/delete-tenant"
+ ]
+ },
+ {
+ "group": "Bundle Service",
+ "pages": [
+ "api-reference/bundle/write-bundle",
+ "api-reference/bundle/read-bundle",
+ "api-reference/bundle/delete-bundle"
+ ]
+ },
+ {
+ "group": "Watch Service",
+ "pages": [
+ "api-reference/watch/watch-changes"
+ ]
+ }
+ ],
+ "footerSocials": {
+ "twitter": "https://twitter.com/getPermify",
+ "github": "https://github.com/Permify/permify",
+ "linkedin": "https://www.linkedin.com/company/permifyco"
+ }
+}
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/bundle.md b/docs/operations/bundle.mdx
similarity index 71%
rename from docs/versioned_docs/version-0.6.x/bundle.md
rename to docs/operations/bundle.mdx
index ca7db9ec..fd23cb77 100644
--- a/docs/versioned_docs/version-0.6.x/bundle.md
+++ b/docs/operations/bundle.mdx
@@ -1,15 +1,13 @@
---
-id: bundle
-title: Bundle Service
-sidebar_label: Data Bundles
-slug: /api-overview/bundle
+icon: cube
+title: Data Bundles
---
## What is Data Bundles
Ensuring that authorization data remains in sync with the business model is an important practice when using Permify.
-Prior to Data Bundles, it was the responsibility of the services (such as [WriteData](./api-overview/data/write-data.md) API) to structure how relations are created and deleted when actions occur on resources.
+Prior to Data Bundles, it was the responsibility of the services (such as [WriteData](../api-reference/data/write-data) API) to structure how relations are created and deleted when actions occur on resources.
With the Data Bundles, you be able to bundle and model the creation and deletion of relations and attributes when specific actions occur on resources in your applications.
@@ -19,7 +17,7 @@ We believe this functionality will streamline managing authorization data as wel
Let's examine how Bundles operates with basic example.
-Let's say you want to model how data will be created when an organization created in your application. For this purpose, you can utilize the [WriteBundle](./api-overview/bundle/write-bundle.md) API endpoint. This API enables users to define or update data bundles, each distinguished by a unique name.
+Let's say you want to model how data will be created when an organization created in your application. For this purpose, you can utilize the [WriteBundle](../../api-reference/bundle/write-bundle) API endpoint. This API enables users to define or update data bundles, each distinguished by a unique name.
Here's an example body for WriteBundle in this scenario:
@@ -54,9 +52,9 @@ Let's say user:564 creates an organization:789 in your application. According to
- organization:789#manager@user:564
- organization:789$public|boolean:false
-Instead of using the [WriteData](./api-overview/data/write-data.md) endpoint, you can utilize [RunBundle](./api-overview/data/run-bundle.md) to create this data by simply providing specific identifiers.
+Instead of using the [WriteData](../../api-reference/data/write-data) endpoint, you can utilize [RunBundle](../../api-reference/data/run-bundle) to create this data by simply providing specific identifiers.
-An example request of [RunBundle](./api-overview/data/run-bundle.md) for this scenario:
+An example request of [RunBundle](../../api-reference/data/run-bundle) for this scenario:
```json
POST /bundle
@@ -78,7 +76,7 @@ This will result in the creation of the following data in Permify:
## Endpoints
-- [WriteBundle](./api-overview/bundle/write-bundle.md)
-- [RunBundle](./api-overview/data/run-bundle.md)
-- [DeleteBundle](./api-overview/bundle/delete-bundle.md)
-- [ReadBundle](./api-overview/bundle/read-bundle.md)
+- [WriteBundle](../../api-reference/bundle/write-bundle)
+- [RunBundle](../../api-reference/data/run-bundle)
+- [DeleteBundle](../../api-reference/bundle/delete-bundle)
+- [ReadBundle](../../api-reference/bundle/read-bundle)
diff --git a/docs/versioned_docs/version-0.5.x/reference/cache.md b/docs/operations/cache.mdx
similarity index 90%
rename from docs/versioned_docs/version-0.5.x/reference/cache.md
rename to docs/operations/cache.mdx
index 1910705a..f97af926 100644
--- a/docs/versioned_docs/version-0.5.x/reference/cache.md
+++ b/docs/operations/cache.mdx
@@ -1,4 +1,7 @@
-# Cache Mechanisms
+---
+icon: hard-drive
+title: Cache Mechanisms
+---
This section showcases the cache mechanisms that Permify uses.
@@ -9,14 +12,14 @@ Schemas are stored in an in-memory cache based on their versions. If a version i
The size of this can be determined through the Permify configuration. Here is an example configuration:
service:
-```yaml
+```yaml
…
schema:
cache:
number_of_counters: 1_000
max_cost: 10MiB
…
-```
+```
The cache library used is: https://github.com/dgraph-io/ristretto
@@ -25,14 +28,14 @@ The cache library used is: https://github.com/dgraph-io/ristretto
Permify applies the MVCC (Multi Version Concurrency Control) pattern for Postgres, creating a separate database snapshot for each write and delete operation. This both enhances performance and provides a consistent cache.
An example of a cache key is:
-check_{tenant_id}_{schema_version}:{snapshot_token}:{check_request}
+`check_{tenant_id}_{schema_version}:{snapshot_token}:{check_request}`
Permify hashes each request and searches for the same key. If it cannot find it, it runs the check engine and writes to the cache, thus creating a consistently working hash.
The size of this can also be determined via the Permify configuration. Here’s an example:
service:
-```yaml
+```yaml
…
permission:
bulk_limit: 100
@@ -41,7 +44,7 @@ service:
number_of_counters: 10_000
max_cost: 10MiB
…
-```
+```
The cache library used is: https://github.com/dgraph-io/ristretto
@@ -49,7 +52,7 @@ Note: Another advantage of the MVCC pattern is the ability to historically store
## Distributed Cache
-Permify does provide a distributed cache across availability zones (within an AWS region) via **Consistent Hashing**. Permify uses Consistent Hashing across its distributed instances for more efficient use of their individual caches.
+Permify does provide a distributed cache across availability zones (within an AWS region) via **Consistent Hashing**. Permify uses Consistent Hashing across its distributed instances for more efficient use of their individual caches.
This would allow for high availability and resilience in the face of individual nodes or even entire availability zone failure, as well as improved performance due to data locality benefits.
@@ -65,13 +68,16 @@ Using this consistent hashing approach, we can effectively utilize individual ca
You can learn more about consistent hashing from the following blog post: [Introducing Consistent Hashing](https://itnext.io/introducing-consistent-hashing-9a289769052e)
-:::info
-Note, however, that while the consistent hashing approach will distribute keys evenly across the cache nodes, it's up to the application logic to ensure the cache is used effectively (i.e., that it reads from and writes to the cache appropriately).
-:::
+
+ Note that while the consistent hashing approach will distribute keys evenly
+ across the cache nodes, it's up to the application logic to ensure the cache
+ is used effectively (i.e., that it reads from and writes to the cache
+ appropriately).
+
Here is an example configuration:
-```yaml
+```yaml
distributed:
# Indicates whether the distributed mode is enabled or not
enabled: true
@@ -83,13 +89,10 @@ distributed:
# The port on which the service is exposed
port: "5000"
-```
+```
Additional to that we’re using a [circuit breaker](https://blog.bitsrc.io/circuit-breaker-pattern-in-microservices-26bf6e5b21ff) pattern to detect and handle failures when the underlying database is unavailable. It prevents unnecessary calls when the database is down and handles the process on the rebooting phase.
## Need any help ?
Our team is happy help you to structure right architecture for your permission system. Feel free to [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
diff --git a/docs/versioned_docs/version-0.6.x/reference/contextual-tuples.md b/docs/operations/contextual-tuples.mdx
similarity index 74%
rename from docs/versioned_docs/version-0.6.x/reference/contextual-tuples.md
rename to docs/operations/contextual-tuples.mdx
index 3765e967..eea6415b 100644
--- a/docs/versioned_docs/version-0.6.x/reference/contextual-tuples.md
+++ b/docs/operations/contextual-tuples.mdx
@@ -1,7 +1,7 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Contextual Data (Dynamic Permissions)
+---
+icon: tags
+title: Contextual Permissions
+---
Contextual tuples are relations that can be dynamically added to permission request operations. When you send these relations along with your requests, they get processed alongside existing relations in the database and will return a result.
@@ -76,7 +76,7 @@ So let's say user Ashley trying to view employee X. And lets assume that,
- She connected to VPN which connected to network 192.158.1.38 - which is Branch's internal network.
-
+
```go
data, err := structpb.NewStruct(map[string]interface{}{
@@ -111,8 +111,8 @@ cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequ
})
```
-
-
+
+
```javascript
client.permission
@@ -147,8 +147,57 @@ client.permission
});
```
-
-
+
+
+
+```python
+import permify
+from permify.models.permission_check_request import PermissionCheckRequest
+from permify.models.permission_check_response import PermissionCheckResponse
+from permify.rest import ApiException
+from pprint import pprint
+
+configuration = permify.Configuration(host="http://localhost")
+
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.PermissionApi(api_client)
+ tenant_id = 't1'
+
+ body = PermissionCheckRequest(
+ tenant_id=tenant_id,
+ metadata={
+ "snapToken": "",
+ "schemaVersion": "",
+ "depth": 20
+ },
+ entity={
+ "type": "organization",
+ "id": "1",
+ },
+ permission="hr_manager",
+ subject={
+ "type": "user",
+ "id": "1",
+ },
+ context={
+ "data": {
+ "ip_address": "192.158.1.38",
+ },
+ },
+ )
+
+ try:
+ api_response = api_instance.permissions_check(tenant_id, body)
+ if api_response.can == PermissionCheckResponse.Result.RESULT_ALLOWED:
+ print("RESULT_ALLOWED")
+ else:
+ print("RESULT_DENIED")
+ except ApiException as e:
+ print(f"Exception when calling PermissionApi->permissions_check: {e}")
+```
+
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
@@ -177,12 +226,16 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permission
}'
```
-
+
-:::info
-Besides data, you can also provide relational tuples and attributes alongside the access check using contextual tuples. You can view the full parameters for the [permission check in our swagger docs](https://permify.github.io/permify-swagger/#/Permission/permissions.check).
-:::
+
+ Besides data, you can also provide relational tuples and attributes alongside
+ the access check using contextual tuples. You can view the full parameters for
+ the [permission check in our swagger
+ docs](https://permify.github.io/permify-swagger/#/Permission/permissions.check).
+
+
## Need any help ?
diff --git a/docs/versioned_docs/version-0.6.x/reference/snap-tokens.md b/docs/operations/snap-tokens.mdx
similarity index 93%
rename from docs/versioned_docs/version-0.6.x/reference/snap-tokens.md
rename to docs/operations/snap-tokens.mdx
index 95eec606..b4ed3e7e 100644
--- a/docs/versioned_docs/version-0.6.x/reference/snap-tokens.md
+++ b/docs/operations/snap-tokens.mdx
@@ -1,5 +1,7 @@
-
-# Snap Tokens & Zookies
+---
+icon: equals
+title: Consistency (Snap Tokens)
+---
A Snap Token is a token that consists of an encoded timestamp, which is used to ensure fresh results in access control checks.
@@ -39,10 +41,10 @@ Then this snap token can be used in endpoints. For example it can be used in acc
}
```
-[Write API]: ../../api-overview/data/write-data/
-[Check API]: ../../api-overview/permission/check-api
+[Write API]: ../../api-reference/data/write-data
+[Check API]: ../../api-reference/permission/check-api
-### When Snap Token is NOT Provided
+## When Snap Token is NOT Provided
In Permify, every transaction is recorded in the 'transactions' table, and when a Snap Token is not provided, it retrieves the ID of the latest transaction from this table. This ID represents the most current snapshot of the database. After a query is executed with this ID, the results are then cached using this ID.
@@ -56,4 +58,4 @@ When the second request arrives, since a transaction ID was not provided, the la
## More on Cache Mechanism
-Permify implements several cache mecnanisims in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](./cache.md)
\ No newline at end of file
+Permify implements several cache mecnanisims in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisms](./cache)
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/reference/tracing.md b/docs/operations/tracing.mdx
similarity index 97%
rename from docs/versioned_docs/version-0.6.x/reference/tracing.md
rename to docs/operations/tracing.mdx
index 13fb142d..46224c7a 100644
--- a/docs/versioned_docs/version-0.6.x/reference/tracing.md
+++ b/docs/operations/tracing.mdx
@@ -1,5 +1,7 @@
-
-# Tracing Tools
+---
+icon: magnifying-glass
+title: Observability
+---
Permify has integrations with some of popular tracing tools to analyze performance and behavior of your authorization. These are:
diff --git a/docs/package.json b/docs/package.json
deleted file mode 100644
index 4284b6d9..00000000
--- a/docs/package.json
+++ /dev/null
@@ -1,91 +0,0 @@
-{
- "name": "docs",
- "version": "0.0.0",
- "private": true,
- "scripts": {
- "docusaurus": "docusaurus",
- "start": "docusaurus start",
- "build": "docusaurus build",
- "swizzle": "docusaurus swizzle",
- "deploy": "docusaurus deploy",
- "clear": "docusaurus clear",
- "serve": "docusaurus serve",
- "write-translations": "docusaurus write-translations",
- "write-heading-ids": "docusaurus write-heading-ids",
- "typecheck": "tsc"
- },
- "dependencies": {
- "@cmfcmf/docusaurus-search-local": "^1.1.0",
- "@docusaurus/core": "^2.4.3",
- "@docusaurus/plugin-client-redirects": "^2.4.3",
- "@docusaurus/plugin-google-analytics": "^2.4.3",
- "@docusaurus/plugin-google-gtag": "^2.4.3",
- "@docusaurus/preset-classic": "^2.4.3",
- "@glidejs/glide": "^3.6.0",
- "@reach/accordion": "^0.18.0",
- "@redq/reuse-modal": "^2.0.0",
- "@styled-system/theme-get": "^5.1.2",
- "animate.css": "^4.1.1",
- "clsx": "^1.1.1",
- "polished": "^4.2.2",
- "prism-react-renderer": "^1.2.1",
- "prop-types": "^15.8.1",
- "query-string": "^8.1.0",
- "rc-collapse": "^3.5.2",
- "rc-drawer": "^6.1.3",
- "rc-progress": "^3.4.1",
- "rc-tabs": "12.5.7",
- "react": "^17.0.1",
- "react-accessible-accordion": "5.0.0",
- "react-anchor-link-smooth-scroll": "^1.0.12",
- "react-aria-menubutton": "^7.0.3",
- "react-collapser": "^1.5.10",
- "react-content-loader": "^6.2.0",
- "react-countdown-now": "^2.1.2",
- "react-countup": "^6.4.1",
- "react-dom": "^17.0.1",
- "react-github-btn": "^1.4.0",
- "react-icons": "^4.7.1",
- "react-icons-kit": "^2.0.0",
- "react-id-swiper": "^4.0.0",
- "react-image": "^4.0.3",
- "react-image-gallery": "1.2.11",
- "react-loader-spinner": "^5.3.4",
- "react-masonry-component": "^6.3.0",
- "react-parallax": "^3.5.1",
- "react-parallax-component": "^1.0.6",
- "react-phone-number-input": "^3.2.18",
- "react-responsive": "^9.0.0",
- "react-reveal": "^1.2.2",
- "react-rnd": "^10.3.7",
- "react-scroll-motion": "^0.3.0",
- "react-scroll-parallax": "^3.3.1",
- "react-scrollspy": "^3.4.3",
- "react-select": "^5.6.0",
- "react-slick": "^0.29.0",
- "react-stickynode": "^4.1.0",
- "react-tabs": "^6.0.0",
- "react-tsparticles": "^2.9.3",
- "react-waypoint": "10.3.0",
- "styled-components": "^5.3.6",
- "styled-system": "5.1.5",
- "swiper": "^9.1.0"
- },
- "devDependencies": {
- "@docusaurus/module-type-aliases": "^2.4.0",
- "@tsconfig/docusaurus": "^1.0.4",
- "typescript": "^4.9.5"
- },
- "browserslist": {
- "production": [
- ">0.5%",
- "not dead",
- "not op_mini all"
- ],
- "development": [
- "last 1 chrome version",
- "last 1 firefox version",
- "last 1 safari version"
- ]
- }
-}
diff --git a/docs/docs/permify-overview/authorization-service.md b/docs/permify-overview/authorization-service.mdx
similarity index 82%
rename from docs/docs/permify-overview/authorization-service.md
rename to docs/permify-overview/authorization-service.mdx
index 91d0dc7f..9daa4247 100644
--- a/docs/docs/permify-overview/authorization-service.md
+++ b/docs/permify-overview/authorization-service.mdx
@@ -1,7 +1,9 @@
+---
+sidebar_position: 1
+title: Authorization As A Service
+---
-# Authorization As A Service
-
-Getting authorization right is tough, no matter how you've set up your architecture. You're gonna need a solid plan to handle permissions between services, all while keeping it separate from your applications main code.
+Getting authorization right is tough, no matter how you've set up your architecture. You're gonna need a solid plan to handle permissions between services, all while keeping it separate from your applications main code.
In a monolithic app, you can abstract authorization from your app using libraries. This involves building a permission system for each individual application or service that is directly connected with the database.
@@ -9,7 +11,7 @@ This approach works well until you have several applications with many services.
So due to this, at some point, most companies tend to design these systems as abstract entities, such as a centralized engine, that cater apps that has many services. But its not an easy process for [several reasons](#building-an-authorization-service-is-hard).
-Authorization as a service means outsourcing your app's permission management to streamline authorization in your applications. Beyond the clear advantage of saving valuable development time, [it also significantly enhances visibility, scalability, and flexibility](#benefits-of-using-an-authorization-service) within your authorization journey.
+Authorization as a service means outsourcing your app's permission management to streamline authorization in your applications. Beyond the clear advantage of saving valuable development time, [it also significantly enhances visibility, scalability, and flexibility](#benefits-of-using-an-authorization-service-permify) within your authorization journey.
[Permify] is an **centralized authorization service** that offers a variety of binding and crafting options to secure your applications. It works in run time and respond to all authorization questions from any of your apps.
@@ -27,54 +29,61 @@ For instance; in order to make an access check and compute a decision, you need
Loading and processing authorization data is especially painful for access checks which come from different environments and services. Also, the authorization service which will be accessed by nearly every other service must be at least as available as the rest of your stack.
-So for a centralized authorization service to operate smoothly, this systems needs to have to be fast, consistent, and available all times.
+So for a centralized authorization service to operate smoothly, this systems needs to have to be fast, consistent, and available all times.
Another point is, you probably need to have an additional service to to store your authorization data model, which generally includes saving and updating essential permissions like roles, attributes or relationships. This service should manage the entirety of authorization policies, providing administrators the flexibility to adjust these policies when necessary.
## Benefits of using an Authorization Service - Permify
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch.
+### Move & Iterate Faster
-You can get started quickly with a [simple API](../api-overview.md) that you can easily integrate into your application to move and iterate faster.
+Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch.
-### Scale As You Wish
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
+You can get started quickly with a [simple API](../getting-started/enforcement) that you can easily integrate into your application to move and iterate faster.
+### Scale As You Wish
+Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
-Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period.
+Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period.
Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services
-:::success Metrics
-Currently, Permify can achieve response times of up to **10ms** for access control checks, with handling up to **1 trillion access requests** per second. Thanks to our state-of-the-art [parallel graph engine](https://docs.permify.co/docs/api-overview/permission/check-api/#how-access-decisions-evaluated) and various [cache mechanisms](https://docs.permify.co/docs/reference/cache/) that we operate.
-:::
+
+ Currently, Permify can achieve response times of up to **10ms** for access
+ control checks, with handling up to **1 trillion access requests** per second.
+ Thanks to our state-of-the-art [parallel graph
+ engine](./faqs#how-access-decisions-evaluated)
+ and various [cache mechanisms](../operations/cache)
+ that we operate.
+
[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell
### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group.
-Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time.
+Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group.
+
+Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time.
-Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
+Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road.
-Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product.
+Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road.
-Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production.
+Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product.
+
+Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production.
After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security.
+
+Protect your data, prevent unauthorized access and ensure your customers security.
Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
## Need any help on Authorization ?
Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify or how it might fit into your authorization workflow, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/permify-overview/faqs.mdx b/docs/permify-overview/faqs.mdx
new file mode 100644
index 00000000..224ec304
--- /dev/null
+++ b/docs/permify-overview/faqs.mdx
@@ -0,0 +1,129 @@
+---
+title: Permify FAQs
+---
+
+### Does Permify Supports Authentication?
+
+Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
+
+To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data.
+
+Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
+
+### How Access Decisions Evaluated?
+
+Access decisions are evaluated by stored authorization data and your authorization model, Permify Schema.
+
+In high level, access of an subject related with the relationships or attributes created between the subject and the resource. You can define this data in Permify Schema then create and store them as relational tuples and attributes, which is basically forms your authorization data.
+
+Permify Engine to compute access decision in 2 steps,
+1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
+2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
+
+Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
+
+[relational tuples]: ../../getting-started/sync-data.md
+[Permify Schema]: ../../getting-started/modeling.md
+
+When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
+
+```perm
+entity user {}
+
+entity organization {
+
+ // organizational roles
+ relation admin @user
+ relation member @user
+}
+
+entity document {
+
+ // represents documents parent organization
+ relation parent @organization
+
+ // represents owner of this document
+ relation owner @user
+
+ // permissions
+ action edit = parent.admin or owner
+ action delete = owner
+}
+```
+
+Which has a directed graph as follows:
+
+
+
+As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
+
+**Q1:** Get the owners of the `document:12`.
+
+**Q2:** Get admins of the organization where `document:12` belongs to.
+
+Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
+
+Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
+
+### How To Manage Schema Changes ?
+
+It's expected that your initial schema will eventually change as your product or system evolves
+
+As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
+
+A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database unless you delete them with the [delete API](../data/delete-data.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
+
+We recommend applying the following pattern to safely handle schema changes:
+
+- Set up a central git repository that includes the schema.
+- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
+- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
+- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
+
+
+### What is Preferred Deployment Pattern For Permify?
+
+Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization.
+
+Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications.
+
+See the [What is Authorization Service] Section for a detailed explanation of those advantages.
+
+[What is Authorization Service]: ../authorization-service
+
+
+
+Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important.
+
+As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
+
+
+### Why should I use Permify instead of IAM solutions such as Cognito, Firebase Auth or Keycloak to handle authorization?
+
+There are some major differences between authorization-specific solutions and identity providers, or I might say IAMs
+
+While IAMs often offer some level of authorization capabilities, they are not as flexible or fine-grained as dedicated authorization systems like Permify. Therefore, customizing complex permission logic (such as hierarchical relationships, user groups, dynamic attributes, etc.) can be challenging in IAMs.
+
+Another point is that authorization as a service solutions are focused entirely on authorization. This means they provide not only fine-grained permissions but also tooling and functionality to ease testing and observability of the authorization system.
+
+Also Permify leveraging Google’s Zanzibar scalable data model and unified ACL (Access Control List) approach, enables the creation of a centralized authorization service capable of handling high volumes of data and access checks across your microservices stack.
+
+Still its worth mention that if you have a basic authorization system or need, it totally makes sense to use the solutions you mentioned for handling the authorization part as well.
+
+### How Permify Works With Identity Providers (IAMs)?
+
+Identity providers help you store and control your users’ and employees’ identities in a single place.
+
+Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have.
+
+But as a maker of this project management app. You need to build the permissions and then map to Okta.
+
+What we do is, help you build these permissions and eventually map anywhere you want.
+
+### Is Permify a true ReBAC solution?
+
+Permify was designed and structured as a true ReBAC solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
+
+With Permify, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group.
+
+This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
\ No newline at end of file
diff --git a/docs/permify-overview/intro.mdx b/docs/permify-overview/intro.mdx
new file mode 100644
index 00000000..0616bec0
--- /dev/null
+++ b/docs/permify-overview/intro.mdx
@@ -0,0 +1,109 @@
+---
+title: Explore Permify
+description: 'Start building scalable authorization systems in mere minutes'
+---
+
+
+
+
+## What is Permify ?
+
+[Permify](https://github.com/Permify/permify) is an **open source authorization service** for creating fine-grained and scalable authorization systems.
+
+With Permify, you can easily structure your authorization model, store authorization data in your preferred database, and interact with the Permify API to handle all authorization queries from your applications or services.
+
+Permify is inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://permify.co/post/google-zanzibar-in-a-nutshell/).
+
+## Motivation
+
+Building scalable authorization systems is hard and time-consuming, and we're here to overcome this!
+
+Our goal is to make Google’s Zanzibar available to everyone and help engineering teams build a robust, flexible, and easily auditable authorization system, which will centrally position itself in your environment, taking responsibility for access control among your applications and services.
+
+See the [Authorization As A Service](./authorization-service) section to learn why building authorization is challenging and how our approach significantly reduces engineering efforts and secures future-proof access control systems.
+
+## With Permify, you can:
+
+🔮 Create permissions and policies using [Permify's flexible authorization language](../getting-started/modeling) that is compatible with traditional roles and permissions (RBAC), arbitrary relations between users and objects (ReBAC), and attributes (ABAC).
+
+🔐 [Manage and store authorization data](../getting-started/sync-data) in your preferred database with high availability and consistency.
+
+✅ [Interact with the Permify API](../getting-started/enforcement) to perform access checks, filter your resources with specific permissions, perform bulk permission checks for various resources, and more.
+
+🧪 Test your authorization logic with [Permify's schema testing](../getting-started/testing). You can conduct scenario-based testing, policy coverage analysis, and IDL parser integration to achieve end-to-end validations for your desired authorization schema.
+
+⚙️ Create custom and isolated authorization models for different applications using Permify [Multi-Tenancy](../use-cases/multi-tenancy) support, all managed within a single place, Permify instance.
+
+## Getting Started
+
+In Permify, authorization is divided into 3 core aspects; **modeling**, **storing authorization data** and **interacting with the APIs**.
+
+- See how to [Model your Authorization] using Permify Schema.
+- Learn how Permify will [Store Authorization Data] as relations.
+- Perform [Access Checks] anywhere in your stack.
+
+[Model your Authorization]: ../getting-started/modeling
+[Store Authorization Data]: ../getting-started/sync-data
+[Access Checks]: ../getting-started/enforcement
+
+This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications.
+
+For the ones that want to try it out and examine it instantly, use [Permify Playground](https://play.permify.co/) to get started!
+
+
+
+
+
+## Community & Support
+
+We would love to hear from you!
+
+You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
+
+For feature requests, bugs, or any improvements you can always open an [issue](https://github.com/permify/permify/issues).
+
+### Want to Contribute? Here are the ways to contribute to Permify
+
+* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
+* **Improve documentation:** Alongside our codebase, documentation is an important part of our open-source journey. We're trying to give the best DX possible to explain ourselves and Permify. And you can help with that by importing resources or adding new ones.
+* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
+
+You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
+
+## Communication Channels
+
+If you like Permify, please consider giving us a star on [github](https://github.com/permify/permify)
+
+
+
+
+## Roadmap
+
+You can find Permify's Public Roadmap [here](https://github.com/orgs/Permify/projects/1)!
+
+## Need any help on Authorization ?
+
+Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify or how it might fit into your authorization workflow, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
+
diff --git a/docs/quickstart.mdx b/docs/quickstart.mdx
new file mode 100644
index 00000000..d7f34867
--- /dev/null
+++ b/docs/quickstart.mdx
@@ -0,0 +1,86 @@
+---
+title: 'Quickstart'
+description: 'Start building awesome documentation in under 5 minutes'
+---
+
+## Setup your development
+
+Learn how to update your docs locally and and deploy them to the public.
+
+### Edit and preview
+
+
+
+ During the onboarding process, we created a repository on your Github with
+ your docs content. You can find this repository on our
+ [dashboard](https://dashboard.mintlify.com). To clone the repository
+ locally, follow these
+ [instructions](https://docs.github.com/en/repositories/creating-and-managing-repositories/cloning-a-repository)
+ in your terminal.
+
+
+ Previewing helps you make sure your changes look as intended. We built a
+ command line interface to render these changes locally. 1. Install the
+ [Mintlify CLI](https://www.npmjs.com/package/mintlify) to preview the
+ documentation changes locally with this command: ``` npm i -g mintlify ```
+ 2. Run the following command at the root of your documentation (where
+ `mint.json` is): ``` mintlify dev ```
+
+
+
+### Deploy your changes
+
+
+
+
+ Our Github app automatically deploys your changes to your docs site, so you
+ don't need to manage deployments yourself. You can find the link to install on
+ your [dashboard](https://dashboard.mintlify.com). Once the bot has been
+ successfully installed, there should be a check mark next to the commit hash
+ of the repo.
+
+
+ [Commit and push your changes to
+ Git](https://docs.github.com/en/get-started/using-git/pushing-commits-to-a-remote-repository#about-git-push)
+ for your changes to update in your docs site. If you push and don't see that
+ the Github app successfully deployed your changes, you can also manually
+ update your docs through our [dashboard](https://dashboard.mintlify.com).
+
+
+
+
+## Update your docs
+
+Add content directly in your files with MDX syntax and React components. You can use any of our components, or even build your own.
+
+
+
+
+ Add flair to your docs with personalized branding.
+
+
+
+ Implement your OpenAPI spec and enable API user interaction.
+
+
+
+ Draw insights from user interactions with your documentation.
+
+
+
+ Keep your docs on your own website's subdomain.
+
+
+
diff --git a/docs/docs/reference/configuration.md b/docs/setting-up/configuration.mdx
similarity index 94%
rename from docs/docs/reference/configuration.md
rename to docs/setting-up/configuration.mdx
index e7f01746..d577170d 100644
--- a/docs/docs/reference/configuration.md
+++ b/docs/setting-up/configuration.mdx
@@ -1,11 +1,22 @@
-# Configuration File
+---
+title: Configuration
+icon: gear
+---
-Permify offers various options for configuring your Permify API Server.
+Permify offers various options for configuring your Permify Server. Here is the example configuration YAML file with glossary below.
-Here is the example configuration YAML file with glossary below. You can also find
+You can also find
this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-***Example config.yaml file***
+### Configure Using Flags
+
+Alternatively, you can set configuration options using flags when running the command. See all the configuration flags by running,
+
+```shell
+docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve -help
+```
+
+### Configuration Using YAML File
```yaml
# The server section specifies the HTTP and gRPC server settings,
@@ -108,10 +119,9 @@ distributed:
```
-## Options
+## Configuration Glossary
-server | Server Configurations
-
+
#### Definition
@@ -142,7 +152,7 @@ Server options to run Permify. (`grpc` and `http` available for now.)
| [x] | tls | - | transport layer security options. |
| [ ] | enabled (for tls) | false | switch option for tls |
| [ ] | cert | - | tls certificate path. |
-| [ ] | key | - | tls key pat |
+| [ ] | key | - | tls key path |
#### ENV
@@ -160,11 +170,9 @@ Server options to run Permify. (`grpc` and `http` available for now.)
| http-cors-allowed-origins | PERMIFY_HTTP_CORS_ALLOWED_ORIGINS | string array |
| http-cors-allowed-headers | PERMIFY_HTTP_CORS_ALLOWED_HEADERS | string array |
-
-
+
-logger | Logging Options
-
+
#### Definition
@@ -193,11 +201,9 @@ Real time logs of authorization. Permify uses [zerolog] as a logger.
| log-level | PERMIFY_LOG_LEVEL | string |
| log-output | PERMIFY_LOG_OUTPUT | string |
-
-
+
-authn | Server Authentication
-
+
#### Definition
@@ -205,8 +211,8 @@ You can choose to authenticate users to interact with Permify API.
There are 2 authentication method you can choose:
-* [Pre Shared Keys](#pre-shared-keys)
-* [OpenID Connect](#openid-connect)
+* Pre Shared Keys
+* OpenID Connect
#### Pre Shared Keys
@@ -276,12 +282,9 @@ authentication.
| authn-oidc-issuer | PERMIFY_AUTHN_OIDC_ISSUER | string |
| authn-oidc-audience | PERMIFY_AUTHN_OIDC_AUDIENCE | string |
-
-
+
[jaeger]: https://www.jaegertracing.io/
diff --git a/docs/setting-up/installation/.DS_Store b/docs/setting-up/installation/.DS_Store
new file mode 100644
index 00000000..5008ddfc
Binary files /dev/null and b/docs/setting-up/installation/.DS_Store differ
diff --git a/docs/versioned_docs/version-0.4.x/installation/aws.md b/docs/setting-up/installation/aws.mdx
similarity index 98%
rename from docs/versioned_docs/version-0.4.x/installation/aws.md
rename to docs/setting-up/installation/aws.mdx
index c1c204d9..a689cd97 100644
--- a/docs/versioned_docs/version-0.4.x/installation/aws.md
+++ b/docs/setting-up/installation/aws.mdx
@@ -1,9 +1,7 @@
---
-title: AWS ECS, ECR & EC2
+title: Deploy on AWS ECS, ECR & EC2
---
-# Deploy on AWS ECS, ECR & EC2
-
AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
@@ -18,7 +16,7 @@ There is no prerequisite in this tutorial. You can simply deploy permify by foll
At the end of this tutorial you’ll be able to;
-1. [Create a security group](#create-an-ec2-security-group)
+1. [Create a security group](#1-create-an-ec2-security-group)
2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
4. [Running our task definition](#4-running-our-task-definition)
diff --git a/docs/docs/installation/brew.md b/docs/setting-up/installation/brew.mdx
similarity index 66%
rename from docs/docs/installation/brew.md
rename to docs/setting-up/installation/brew.mdx
index 0212df8b..de2cb0c5 100644
--- a/docs/docs/installation/brew.md
+++ b/docs/setting-up/installation/brew.mdx
@@ -1,9 +1,7 @@
---
-title: "Install with Brew"
+title: Install with Brew
---
-# Brew With Configurations
-
This section shows how to install and run Permify Service using brew.
### Install Permify
@@ -28,9 +26,10 @@ See all the configuration flags by running,
permify serve --help
```
-:::info Environment Variables
+
In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
+
+
### Configure With Using Config File
@@ -46,7 +45,7 @@ or
permify serve --config=config.yaml
```
-### Test your connection.
+### Test your connection
You can test your connection by making an HTTP GET request,
@@ -56,10 +55,30 @@ localhost:3476/healthz
You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-[Using the API]: ../../api-overview/
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
+[Using the API]: ../../getting-started/enforcement
+
+
### Need any help ?
diff --git a/docs/docs/installation/container.md b/docs/setting-up/installation/container.mdx
similarity index 53%
rename from docs/docs/installation/container.md
rename to docs/setting-up/installation/container.mdx
index aa0b7686..7cbea8fa 100644
--- a/docs/docs/installation/container.md
+++ b/docs/setting-up/installation/container.mdx
@@ -1,9 +1,7 @@
---
-title: "Docker Container"
+title: Run using Docker
---
-# Run using Docker
-
This section shows how to run Permify using our docker container. You can run Permify using Docker with following command.
## Run in a terminal
@@ -12,15 +10,15 @@ This section shows how to run Permify using our docker container. You can run Pe
docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
```
-This will start a Permify server with the configuration that is in **{YOUR-CONFIG-PATH}**.
+This will start a Permify server with the configuration that is in `{YOUR-CONFIG-PATH}`.
### Configure with a YAML file
-This config path - `{YOUR-CONFIG-PATH}` - should contain the [config yaml file](../reference/configuration.md), where you can configure the Permify Server as well as define the ***database*** to store your authorization related data in.
+This config path - `{YOUR-CONFIG-PATH}` - should contain the [config yaml file](../configuration), where you can configure the Permify Server as well as define the ***database*** to store your authorization related data in.
-:::info Talk to an Permify Engineer
+
By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database.
-:::
+
### Configure Using Flags
@@ -30,9 +28,11 @@ Alternatively, you can set configuration options using flags when running the co
docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve -help
```
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
+
+In addition to CLI flags, Permify also supports configuration via environment variables.
+
+You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
+
### Test your connection.
@@ -44,11 +44,30 @@ localhost:3476/healthz
You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
+[Using the API]: ../../getting-started/enforcement
+
+
### Need any help ?
diff --git a/docs/docs/installation/google.md b/docs/setting-up/installation/google.mdx
similarity index 100%
rename from docs/docs/installation/google.md
rename to docs/setting-up/installation/google.mdx
diff --git a/docs/docs/installation/helm.md b/docs/setting-up/installation/helm.mdx
similarity index 97%
rename from docs/docs/installation/helm.md
rename to docs/setting-up/installation/helm.mdx
index 5345d05d..421b366b 100644
--- a/docs/docs/installation/helm.md
+++ b/docs/setting-up/installation/helm.mdx
@@ -1,11 +1,7 @@
---
-title: Helm Chart
+title: Deploying Permify with Helm Charts
---
-# Deploying Permify with Helm Charts
-
-## Introduction to Helm
-
Helm is a package manager for Kubernetes applications that simplifies the deployment and management of applications in a Kubernetes cluster. Using Helm, you can package and release your applications as charts, which are pre-configured Kubernetes resources.
You can learn more about helm [here](https://helm.sh/docs/)
diff --git a/docs/setting-up/installation/intro.mdx b/docs/setting-up/installation/intro.mdx
new file mode 100644
index 00000000..5b48761f
--- /dev/null
+++ b/docs/setting-up/installation/intro.mdx
@@ -0,0 +1,58 @@
+---
+id: examples
+title: Deployment
+sidebar_label: Installation
+---
+
+
+
+ Set up Permify instance a with single docker command in your local.
+
+
+
+## Deployment Guides
+
+Here is some options that you can use to set up and deploy Permify in your servers.
+If options your deployment preference is not listed below please let us know.
+
+
+
+
+ Deploy Permify on a server using a configuration yaml file.
+
+
+
+
+ Deploying Docker Container & Permify to AWS EC2 using ECS.
+
+
+
+
+ Deploy Permify on a EKS Kubernetes cluster.
+
+
+
+
+ Install and run Permify with Homebrew package manager.
+
+
+
+
+ Deploy Permify with using Google Compute Engine.
+
+
-
- );
-}
diff --git a/docs/src/css/custom.css b/docs/src/css/custom.css
deleted file mode 100644
index 64fc6e37..00000000
--- a/docs/src/css/custom.css
+++ /dev/null
@@ -1,187 +0,0 @@
-/**
- * Any CSS included here will be global. The classic template
- * bundles Infima by default. Infima is a CSS framework designed to
- * work well for content-centric websites.
- */
-
-/* You can override the default Infima variables here. */
-:root {
- --ifm-color-primary: #8246FF;
- --ifm-color-primary-dark: #736986;
- --ifm-color-primary-darker: #291A47;
- --ifm-color-primary-darkest: #0C0025;
- --ifm-color-primary-light: #A274FF;
- --ifm-color-primary-lighter: #C1A2FF;
- --ifm-color-primary-lightest: #E0D1FF;
- --ifm-code-font-size: 95%;
- --ifm-pagination-nav-border-radius: 2px;
- --ifm-pagination-border-radius: 2px;
- --ifm-pre-border-radius: 2px;
- --ifm-alert-border-radius: 2px;
- --ifm-badge-border-radius: 2px;
- --ifm-breadcrumb-border-radius: 2px;
-}
-
-.footer--dark {
- --ifm-footer-background-color: #141517 !important;
-}
-
-html[data-theme='dark'] {
- --ifm-background-color: black !important;
- --ifm-navbar-background-color: #141517 !important;
-}
-
-html[data-theme='dark'] .card {
- background-color: #141517;
- border: 1px solid #303030 !important;
-}
-
-html[data-theme='dark'] pre {
- background-color: #141517 !important;
-}
-
-html[data-theme='dark'] code {
- background-color: #141517 !important;
-}
-
-.card {
- border-radius: 2px !important;
-}
-
-html[data-theme='dark'] .card-body_src-components-Card-Card-module {
- background-color: #141517 !important;
-}
-
-html[data-theme='dark'] .card_src-components-Case-Case-module {
- background-color: #141517 !important;
-}
-
-html {
- font-size: 16px;
-}
-
-.aa-DetachedSearchButton {
- width: 170px !important;
- height: 2rem !important;
- font-size: 14px !important;
-}
-
-
-/* For readability concerns, you should choose a lighter palette in dark mode. */
-html[data-theme='dark'] {
- --ifm-color-primary: #A274FF;
- --ifm-color-primary-dark: #A274FF;
- --ifm-color-primary-darker: #A274FF;
- --ifm-color-primary-darkest: #A274FF;
- --ifm-color-primary-light: #A274FF;
- --ifm-color-primary-lighter: #E0D1FF;
- --ifm-color-primary-lightest: #E0D1FF;
-}
-
-.docusaurus-highlight-code-line {
- background-color: rgba(0, 0, 0, 0.1);
- display: block;
- margin: 0 calc(-1 * var(--ifm-pre-padding));
- padding: 0 var(--ifm-pre-padding);
-}
-
-html[data-theme='dark'] .docusaurus-highlight-code-line {
- background-color: rgba(0, 0, 0, 0.3);
-}
-
-.header-discord-link:hover {
- opacity: 0.6;
-}
-
-.header-discord-link:before {
- background: url("data:image/svg+xml,%3Csvg width='25px' height='20px' viewBox='0 0 256 199' xmlns='http://www.w3.org/2000/svg' xmlns:xlink='http://www.w3.org/1999/xlink' preserveAspectRatio='xMidYMid'%3E%3Cg%3E%3Cpath d='M216.856339,16.5966031 C200.285002,8.84328665 182.566144,3.2084988 164.041564,0 C161.766523,4.11318106 159.108624,9.64549908 157.276099,14.0464379 C137.583995,11.0849896 118.072967,11.0849896 98.7430163,14.0464379 C96.9108417,9.64549908 94.1925838,4.11318106 91.8971895,0 C73.3526068,3.2084988 55.6133949,8.86399117 39.0420583,16.6376612 C5.61752293,67.146514 -3.4433191,116.400813 1.08711069,164.955721 C23.2560196,181.510915 44.7403634,191.567697 65.8621325,198.148576 C71.0772151,190.971126 75.7283628,183.341335 79.7352139,175.300261 C72.104019,172.400575 64.7949724,168.822202 57.8887866,164.667963 C59.7209612,163.310589 61.5131304,161.891452 63.2445898,160.431257 C105.36741,180.133187 151.134928,180.133187 192.754523,160.431257 C194.506336,161.891452 196.298154,163.310589 198.110326,164.667963 C191.183787,168.842556 183.854737,172.420929 176.223542,175.320965 C180.230393,183.341335 184.861538,190.991831 190.096624,198.16893 C211.238746,191.588051 232.743023,181.531619 254.911949,164.955721 C260.227747,108.668201 245.831087,59.8662432 216.856339,16.5966031 Z M85.4738752,135.09489 C72.8290281,135.09489 62.4592217,123.290155 62.4592217,108.914901 C62.4592217,94.5396472 72.607595,82.7145587 85.4738752,82.7145587 C98.3405064,82.7145587 108.709962,94.5189427 108.488529,108.914901 C108.508531,123.290155 98.3405064,135.09489 85.4738752,135.09489 Z M170.525237,135.09489 C157.88039,135.09489 147.510584,123.290155 147.510584,108.914901 C147.510584,94.5396472 157.658606,82.7145587 170.525237,82.7145587 C183.391518,82.7145587 193.761324,94.5189427 193.539891,108.914901 C193.539891,123.290155 183.391518,135.09489 170.525237,135.09489 Z' fill-rule='nonzero'%3E%3C/path%3E%3C/g%3E%3C/svg%3E") no-repeat;
- content: "";
- display: flex;
- height: 20px;
- width: 25px;
-}
-
-html[data-theme='dark'] .header-discord-link:before {
- background: url("data:image/svg+xml,%3Csvg width='25px' height='20px' viewBox='0 0 256 199' xmlns='http://www.w3.org/2000/svg' xmlns:xlink='http://www.w3.org/1999/xlink' preserveAspectRatio='xMidYMid'%3E%3Cg%3E%3Cpath d='M216.856339,16.5966031 C200.285002,8.84328665 182.566144,3.2084988 164.041564,0 C161.766523,4.11318106 159.108624,9.64549908 157.276099,14.0464379 C137.583995,11.0849896 118.072967,11.0849896 98.7430163,14.0464379 C96.9108417,9.64549908 94.1925838,4.11318106 91.8971895,0 C73.3526068,3.2084988 55.6133949,8.86399117 39.0420583,16.6376612 C5.61752293,67.146514 -3.4433191,116.400813 1.08711069,164.955721 C23.2560196,181.510915 44.7403634,191.567697 65.8621325,198.148576 C71.0772151,190.971126 75.7283628,183.341335 79.7352139,175.300261 C72.104019,172.400575 64.7949724,168.822202 57.8887866,164.667963 C59.7209612,163.310589 61.5131304,161.891452 63.2445898,160.431257 C105.36741,180.133187 151.134928,180.133187 192.754523,160.431257 C194.506336,161.891452 196.298154,163.310589 198.110326,164.667963 C191.183787,168.842556 183.854737,172.420929 176.223542,175.320965 C180.230393,183.341335 184.861538,190.991831 190.096624,198.16893 C211.238746,191.588051 232.743023,181.531619 254.911949,164.955721 C260.227747,108.668201 245.831087,59.8662432 216.856339,16.5966031 Z M85.4738752,135.09489 C72.8290281,135.09489 62.4592217,123.290155 62.4592217,108.914901 C62.4592217,94.5396472 72.607595,82.7145587 85.4738752,82.7145587 C98.3405064,82.7145587 108.709962,94.5189427 108.488529,108.914901 C108.508531,123.290155 98.3405064,135.09489 85.4738752,135.09489 Z M170.525237,135.09489 C157.88039,135.09489 147.510584,123.290155 147.510584,108.914901 C147.510584,94.5396472 157.658606,82.7145587 170.525237,82.7145587 C183.391518,82.7145587 193.761324,94.5189427 193.539891,108.914901 C193.539891,123.290155 183.391518,135.09489 170.525237,135.09489 Z' fill='%23FFF' fill-rule='nonzero'%3E%3C/path%3E%3C/g%3E%3C/svg%3E") no-repeat;
-}
-
-.header-twitter-link:hover {
- opacity: 0.6;
-}
-
-.header-twitter-link:before {
- background: url("data:image/svg+xml,%3Csvg width='25px' height='20px' viewBox='0 0 256 209' xmlns='http://www.w3.org/2000/svg' xmlns:xlink='http://www.w3.org/1999/xlink' preserveAspectRatio='xMidYMid'%3E%3Cg%3E%3Cpath d='M256,25.4500259 C246.580841,29.6272672 236.458451,32.4504868 225.834156,33.7202333 C236.678503,27.2198053 245.00583,16.9269929 248.927437,4.66307685 C238.779765,10.6812633 227.539325,15.0523376 215.57599,17.408298 C205.994835,7.2006971 192.34506,0.822 177.239197,0.822 C148.232605,0.822 124.716076,24.3375931 124.716076,53.3423116 C124.716076,57.4586875 125.181462,61.4673784 126.076652,65.3112644 C82.4258385,63.1210453 43.7257252,42.211429 17.821398,10.4359288 C13.3005011,18.1929938 10.710443,27.2151234 10.710443,36.8402889 C10.710443,55.061526 19.9835254,71.1374907 34.0762135,80.5557137 C25.4660961,80.2832239 17.3681846,77.9207088 10.2862577,73.9869292 C10.2825122,74.2060448 10.2825122,74.4260967 10.2825122,74.647085 C10.2825122,100.094453 28.3867003,121.322443 52.413563,126.14673 C48.0059695,127.347184 43.3661509,127.988612 38.5755734,127.988612 C35.1914554,127.988612 31.9009766,127.659938 28.694773,127.046602 C35.3777973,147.913145 54.7742053,163.097665 77.7569918,163.52185 C59.7820257,177.607983 37.1354036,186.004604 12.5289147,186.004604 C8.28987161,186.004604 4.10888474,185.75646 0,185.271409 C23.2431033,200.173139 50.8507261,208.867532 80.5109185,208.867532 C177.116529,208.867532 229.943977,128.836982 229.943977,59.4326002 C229.943977,57.1552968 229.893412,54.8901664 229.792282,52.6381454 C240.053257,45.2331635 248.958338,35.9825545 256,25.4500259' %3E%3C/path%3E%3C/g%3E%3C/svg%3E") no-repeat;
- content: "";
- display: flex;
- height: 20px;
- width: 27px;
-}
-
-html[data-theme='dark'] .header-twitter-link:before {
- background: url("data:image/svg+xml,%3Csvg width='25px' height='20px' viewBox='0 0 256 209' xmlns='http://www.w3.org/2000/svg' xmlns:xlink='http://www.w3.org/1999/xlink' preserveAspectRatio='xMidYMid'%3E%3Cg%3E%3Cpath d='M256,25.4500259 C246.580841,29.6272672 236.458451,32.4504868 225.834156,33.7202333 C236.678503,27.2198053 245.00583,16.9269929 248.927437,4.66307685 C238.779765,10.6812633 227.539325,15.0523376 215.57599,17.408298 C205.994835,7.2006971 192.34506,0.822 177.239197,0.822 C148.232605,0.822 124.716076,24.3375931 124.716076,53.3423116 C124.716076,57.4586875 125.181462,61.4673784 126.076652,65.3112644 C82.4258385,63.1210453 43.7257252,42.211429 17.821398,10.4359288 C13.3005011,18.1929938 10.710443,27.2151234 10.710443,36.8402889 C10.710443,55.061526 19.9835254,71.1374907 34.0762135,80.5557137 C25.4660961,80.2832239 17.3681846,77.9207088 10.2862577,73.9869292 C10.2825122,74.2060448 10.2825122,74.4260967 10.2825122,74.647085 C10.2825122,100.094453 28.3867003,121.322443 52.413563,126.14673 C48.0059695,127.347184 43.3661509,127.988612 38.5755734,127.988612 C35.1914554,127.988612 31.9009766,127.659938 28.694773,127.046602 C35.3777973,147.913145 54.7742053,163.097665 77.7569918,163.52185 C59.7820257,177.607983 37.1354036,186.004604 12.5289147,186.004604 C8.28987161,186.004604 4.10888474,185.75646 0,185.271409 C23.2431033,200.173139 50.8507261,208.867532 80.5109185,208.867532 C177.116529,208.867532 229.943977,128.836982 229.943977,59.4326002 C229.943977,57.1552968 229.893412,54.8901664 229.792282,52.6381454 C240.053257,45.2331635 248.958338,35.9825545 256,25.4500259' fill='%23fff'%3E%3C/path%3E%3C/g%3E%3C/svg%3E") no-repeat;
-}
-
-.header-github-link:hover {
- opacity: 0.6;
-}
-
-.header-github-link:before {
- background: url("data:image/svg+xml;charset=utf-8, %3Csvg viewBox='0 0 24 24' xmlns='http://www.w3.org/2000/svg'%3E%3Cpath d='M12 .297c-6.63 0-12 5.373-12 12 0 5.303 3.438 9.8 8.205 11.385.6.113.82-.258.82-.577 0-.285-.01-1.04-.015-2.04-3.338.724-4.042-1.61-4.042-1.61C4.422 18.07 3.633 17.7 3.633 17.7c-1.087-.744.084-.729.084-.729 1.205.084 1.838 1.236 1.838 1.236 1.07 1.835 2.809 1.305 3.495.998.108-.776.417-1.305.76-1.605-2.665-.3-5.466-1.332-5.466-5.93 0-1.31.465-2.38 1.235-3.22-.135-.303-.54-1.523.105-3.176 0 0 1.005-.322 3.3 1.23.96-.267 1.98-.399 3-.405 1.02.006 2.04.138 3 .405 2.28-1.552 3.285-1.23 3.285-1.23.645 1.653.24 2.873.12 3.176.765.84 1.23 1.91 1.23 3.22 0 4.61-2.805 5.625-5.475 5.92.42.36.81 1.096.81 2.22 0 1.606-.015 2.896-.015 3.286 0 .315.21.69.825.57C20.565 22.092 24 17.592 24 12.297c0-6.627-5.373-12-12-12'/%3E%3C/svg%3E") no-repeat;
- content: "";
- display: flex;
- height: 24px;
- width: 24px;
-}
-
-html[data-theme='dark'] .header-github-link:before {
- background: url("data:image/svg+xml;charset=utf-8,%3Csvg viewBox='0 0 24 24' xmlns='http://www.w3.org/2000/svg'%3E%3Cpath d='M12 .297c-6.63 0-12 5.373-12 12 0 5.303 3.438 9.8 8.205 11.385.6.113.82-.258.82-.577 0-.285-.01-1.04-.015-2.04-3.338.724-4.042-1.61-4.042-1.61C4.422 18.07 3.633 17.7 3.633 17.7c-1.087-.744.084-.729.084-.729 1.205.084 1.838 1.236 1.838 1.236 1.07 1.835 2.809 1.305 3.495.998.108-.776.417-1.305.76-1.605-2.665-.3-5.466-1.332-5.466-5.93 0-1.31.465-2.38 1.235-3.22-.135-.303-.54-1.523.105-3.176 0 0 1.005-.322 3.3 1.23.96-.267 1.98-.399 3-.405 1.02.006 2.04.138 3 .405 2.28-1.552 3.285-1.23 3.285-1.23.645 1.653.24 2.873.12 3.176.765.84 1.23 1.91 1.23 3.22 0 4.61-2.805 5.625-5.475 5.92.42.36.81 1.096.81 2.22 0 1.606-.015 2.896-.015 3.286 0 .315.21.69.825.57C20.565 22.092 24 17.592 24 12.297c0-6.627-5.373-12-12-12' fill='%23fff'/%3E%3C/svg%3E") no-repeat;
-}
-
-.getting-started-grid {
- display: inline-grid;
- align-items: center;
- grid-template-columns: 1fr 1fr 1fr;
- column-gap: 10px;
- row-gap: 10px;
-}
-
-.btn:hover {
- cursor: pointer;
-}
-
-.btn-thumb {
- display: flex;
- flex-direction: column;
- height: 100%;
- padding: 0 0 10px 0 ;
- align-items: center;
- text-align: center;
-
- background-color: #291A47;
- border-radius: 2px;
- color: #ffffff;
- vertical-align: middle;
-}
-
-.btn-thumb .thumbnail {
- height: 160px;
- width: 100%;
- margin-bottom: 10px;
- position: relative;
- border-radius: 0 !important;
-}
-
-.btn-thumb .thumb-txt {
- display: flex;
- align-items: center;
- height: inherit;
- padding: 0 5px;
-}
-
-
-.btn-thumb img {
- height: 160px;
- width: 100%;
- object-fit: cover;
- border-radius: 2px 2px 0 0;
-}
\ No newline at end of file
diff --git a/docs/src/pages/index.js b/docs/src/pages/index.js
deleted file mode 100644
index 9243d1cc..00000000
--- a/docs/src/pages/index.js
+++ /dev/null
@@ -1,6 +0,0 @@
-import React from 'react';
-import { Redirect } from 'react-router-dom';
-
-export default function Home() {
- return ;
-}
diff --git a/docs/src/pages/index.module.css b/docs/src/pages/index.module.css
deleted file mode 100644
index 666feb6a..00000000
--- a/docs/src/pages/index.module.css
+++ /dev/null
@@ -1,23 +0,0 @@
-/**
- * CSS files with the .module.css suffix will be treated as CSS modules
- * and scoped locally.
- */
-
-.heroBanner {
- padding: 4rem 0;
- text-align: center;
- position: relative;
- overflow: hidden;
-}
-
-@media screen and (max-width: 966px) {
- .heroBanner {
- padding: 2rem;
- }
-}
-
-.buttons {
- display: flex;
- align-items: center;
- justify-content: center;
-}
diff --git a/docs/src/theme/prism-include-languages.js b/docs/src/theme/prism-include-languages.js
deleted file mode 100644
index e20261f4..00000000
--- a/docs/src/theme/prism-include-languages.js
+++ /dev/null
@@ -1,28 +0,0 @@
-/**
- * Copyright (c) Facebook, Inc. and its affiliates.
- *
- * This source code is licensed under the MIT license found in the
- * LICENSE file in the root directory of this source tree.
- */
-import siteConfig from '@generated/docusaurus.config';
-export default function prismIncludeLanguages(PrismObject) {
- const {
- themeConfig: {prism},
- } = siteConfig;
- const {additionalLanguages} = prism; // Prism components work on the Prism instance on the window, while prism-
- // react-renderer uses its own Prism instance. We temporarily mount the
- // instance onto window, import components to enhance it, then remove it to
- // avoid polluting global namespace.
- // You can mutate PrismObject: registering plugins, deleting languages... As
- // long as you don't re-assign it
-
- globalThis.Prism = PrismObject;
- additionalLanguages.forEach((lang) => {
- // eslint-disable-next-line global-require, import/no-dynamic-require
- require(`prismjs/components/prism-${lang}`);
- });
-
- require('./prism-perm-lang.js');
-
- delete globalThis.Prism;
-}
diff --git a/docs/src/theme/prism-perm-lang.js b/docs/src/theme/prism-perm-lang.js
deleted file mode 100644
index 1ecb8ee9..00000000
--- a/docs/src/theme/prism-perm-lang.js
+++ /dev/null
@@ -1,14 +0,0 @@
-(function (Prism) {
- Prism.languages.perm = Prism.languages.extend('clike', {
-
- 'comment': {
- pattern: /\/\/.*|\/\*[\s\S]*?(?:\*\/|$)/,
- greedy: true
- },
- 'number':{
- pattern: /\\B@\\w+#?\\w+/,
- greedy: true
- },
- 'keyword': /\b(?:entity|permission|attribute|rule|relation|action|or|not|and)\b(?!\s*=\s*\d)/,
- });
-}(Prism));
diff --git a/docs/static/.nojekyll b/docs/static/.nojekyll
deleted file mode 100644
index e69de29b..00000000
diff --git a/docs/static/img/docusaurus.png b/docs/static/img/docusaurus.png
deleted file mode 100644
index f458149e..00000000
Binary files a/docs/static/img/docusaurus.png and /dev/null differ
diff --git a/docs/static/img/favicon.ico b/docs/static/img/favicon.ico
deleted file mode 100644
index 9b582bdd..00000000
Binary files a/docs/static/img/favicon.ico and /dev/null differ
diff --git a/docs/static/img/logo.svg b/docs/static/img/logo.svg
deleted file mode 100644
index faff98f9..00000000
--- a/docs/static/img/logo.svg
+++ /dev/null
@@ -1,3 +0,0 @@
-
diff --git a/docs/static/img/tutorial/docsVersionDropdown.png b/docs/static/img/tutorial/docsVersionDropdown.png
deleted file mode 100644
index ff1cbe68..00000000
Binary files a/docs/static/img/tutorial/docsVersionDropdown.png and /dev/null differ
diff --git a/docs/static/img/tutorial/localeDropdown.png b/docs/static/img/tutorial/localeDropdown.png
deleted file mode 100644
index d7163f96..00000000
Binary files a/docs/static/img/tutorial/localeDropdown.png and /dev/null differ
diff --git a/docs/static/img/undraw_docusaurus_mountain.svg b/docs/static/img/undraw_docusaurus_mountain.svg
deleted file mode 100644
index 431cef2f..00000000
--- a/docs/static/img/undraw_docusaurus_mountain.svg
+++ /dev/null
@@ -1,170 +0,0 @@
-
diff --git a/docs/static/img/undraw_docusaurus_react.svg b/docs/static/img/undraw_docusaurus_react.svg
deleted file mode 100644
index e4170504..00000000
--- a/docs/static/img/undraw_docusaurus_react.svg
+++ /dev/null
@@ -1,169 +0,0 @@
-
diff --git a/docs/static/img/undraw_docusaurus_tree.svg b/docs/static/img/undraw_docusaurus_tree.svg
deleted file mode 100644
index a05cc03d..00000000
--- a/docs/static/img/undraw_docusaurus_tree.svg
+++ /dev/null
@@ -1 +0,0 @@
-
\ No newline at end of file
diff --git a/docs/tsconfig.json b/docs/tsconfig.json
deleted file mode 100644
index 6f475698..00000000
--- a/docs/tsconfig.json
+++ /dev/null
@@ -1,7 +0,0 @@
-{
- // This file is not used in compilation. It is here just for a nice editor experience.
- "extends": "@tsconfig/docusaurus/tsconfig.json",
- "compilerOptions": {
- "baseUrl": "."
- }
-}
diff --git a/docs/use-cases/.DS_Store b/docs/use-cases/.DS_Store
new file mode 100644
index 00000000..5008ddfc
Binary files /dev/null and b/docs/use-cases/.DS_Store differ
diff --git a/docs/docs/use-cases/abac.md b/docs/use-cases/abac.mdx
similarity index 92%
rename from docs/docs/use-cases/abac.md
rename to docs/use-cases/abac.mdx
index 23a6cb4d..a005a3ef 100644
--- a/docs/docs/use-cases/abac.md
+++ b/docs/use-cases/abac.mdx
@@ -1,4 +1,6 @@
-# Attribute Based Access Control
+---
+title: Attribute Based Access Control (ABAC)
+---
This page explains the design approach of Permify's ABAC support as well as demonstrates how to create and use attribute based permissions in Permify.
@@ -93,11 +95,11 @@ rule check_ip_range(ip string, ip_range string[]) {
}
```
-:::info Syntax
+
We design our schema language based on [Common Expression Language (CEL)](https://github.com/google/cel-go). So the syntax looks nearly identical to equivalent expressions in C++, Go, Java, and TypeScript.
Please let us know via our [Discord channel](https://discord.gg/n6KfzYxhPp) if you have questions regarding syntax, definitions or any operator you identify not working as expected.
-:::
+
Let's examine some of common usage of ABAC with small schema examples.
@@ -112,10 +114,7 @@ entity post {
permission view = is_public
}
```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
-:::
+If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
### Text & Object Based Conditions
@@ -143,9 +142,8 @@ rule check_location(current_location string, location string[]) {
}
```
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts string as `""`
-:::
+If you don’t create the related attribute data, Permify accounts string as `""`
+
### Numerical Conditions
@@ -167,10 +165,7 @@ rule check_age(age integer) {
age >= 18
}
```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts integer as `0`
-:::
+If you don’t create the related attribute data, Permify accounts integer as `0`
#### Double - Precise numerical information
@@ -195,10 +190,7 @@ rule check_balance(amount double, balance double) {
(balance >= amount) && (amount <= 5000)
}
```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts double as `0.0`
-:::
+If you don’t create the related attribute data, Permify accounts double as `0.0`
## Example Use Cases
@@ -242,8 +234,8 @@ This means that the 'view' permission is granted if either the repository is pub
**Request keys before hash**
-- check*{snapshot}*{schema*version}*{context}\_post:1$is_public → true
-- check*{snapshot}*{schema*version}*{context}\_post:1#admin@user:1 → true
+- `check*{snapshot}*{schema*version}*{context}\_post:1$is_public` → true
+- `check*{snapshot}*{schema*version}*{context}\_post:1#admin@user:1` → true
### Example of Weekday
@@ -283,8 +275,8 @@ The permissions in this model state that to 'view' the repository, the user must
**Request keys before hash**
-- check*{snapshot}*{schema*version}*{context}\_organization:1$is_weekday(context.day_of_week) → true
-- check*{snapshot}*{schema*version}*{context}\_post:1#member@user:1 → true
+- `check*{snapshot}*{schema*version}*{context}\_organization:1$is_weekday(context.day_of_week)` → true
+- `check*{snapshot}*{schema*version}*{context}\_post:1#member@user:1` → true
### Example of Banking System
@@ -327,8 +319,8 @@ Both of these conditions need to be true for the **`withdraw`** permission to be
**Request keys before hash**
-- check*{snapshot}*{schema*version}*{context}\_account:1$check_balance(context.amount,balance) → true
-- check*{snapshot}*{schema*version}*{context}\_account:1#owner@user:1 → true
+- `check*{snapshot}*{schema*version}*{context}\_account:1$check_balance(context.amount,balance)` → true
+- `check*{snapshot}*{schema*version}*{context}\_account:1#owner@user:1` → true
### Hierarchical Usage
@@ -376,16 +368,19 @@ rule check_budget(budget double) {
- organization:1$organization|integer:2021
**Check Evolution Sub Queries For Department View**
+
→ department:1$check_budget(budget) → true
+
→ department:1#organization@user:1 → true
→ organization:2$check_founding_year(founding_year) → false
+
→ organization:1$check_founding_year(founding_year) → true
**Request keys before hash**
-- check*{snapshot}*{schema*version}*{context}\_department:1$check_budget(budget) → true
-- check*{snapshot}*{schema*version}*{context}\_organization:2$check_founding_year(founding_year) → false
-- check*{snapshot}*{schema*version}*{context}\_organization:1$check_founding_year(founding_year) → true
+- `check*{snapshot}*{schema*version}*{context}\_department:1$check_budget(budget)` → true
+- `check*{snapshot}*{schema*version}*{context}\_organization:2$check_founding_year(founding_year)` → false
+- `check*{snapshot}*{schema*version}*{context}\_organization:1$check_founding_year(founding_year)` → true
## Evaluation of ABAC Access Checks
@@ -459,8 +454,8 @@ The cache mechanism works by hashing the snapshot of the database, schema versio
**Request keys before hash**
-- check*{snapshot}*{schema*version}*{context}\_organization:1#admin@user:1 → true
-- check*{snapshot}*{schema*version}*{context}\_organization:1$check_ip_range(ip_range) → true
+- `check*{snapshot}*{schema*version}*{context}\_organization:1#admin@user:1` → true
+- `check*{snapshot}*{schema*version}*{context}\_organization:1$check_ip_range(ip_range)` → true
## How To Use ABAC
diff --git a/docs/docs/use-cases/custom-roles.md b/docs/use-cases/custom-roles.mdx
similarity index 99%
rename from docs/docs/use-cases/custom-roles.md
rename to docs/use-cases/custom-roles.mdx
index 4ddf1658..95a620df 100644
--- a/docs/docs/use-cases/custom-roles.md
+++ b/docs/use-cases/custom-roles.mdx
@@ -1,5 +1,6 @@
-
-# Custom Roles
+---
+title: Custom Roles
+---
This document highlights a solution for custom roles with the [Permify Schema]. In this tutorial, we will create custom **admin** and **member** roles in a project. Then set the permissions of these roles according to their capabilities on the dashboard and tasks.
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/multi-tenancy.md b/docs/use-cases/multi-tenancy.mdx
similarity index 63%
rename from docs/versioned_docs/version-0.5.x/use-cases/multi-tenancy.md
rename to docs/use-cases/multi-tenancy.mdx
index c8e5be9a..4f319113 100644
--- a/docs/versioned_docs/version-0.5.x/use-cases/multi-tenancy.md
+++ b/docs/use-cases/multi-tenancy.mdx
@@ -1,39 +1,21 @@
---
-title: "Multi Tenancy"
+title: Multi Tenancy
---
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-With version 0.3.x Permify moved to a tenancy-based infrastructure, which affects almost all of the API operations.
-
-## Multi Tenancy on Permify
-
Multi-tenancy in Permify refers to an authorization architecture where a single Permify authorization service serves multiple applications/organizations (tenants).
-This allows customization of the authorization for each tenant's specific needs. With Multi-Tenancy support, you can create a custom authorization schema and relation tuples for the different tenants and manage them in a single place.
+This allows customization of the authorization for each tenant's specific needs. With Multi-Tenancy support, you can create a custom authorization schema and authorization data for the different tenants and manage them in a single place.
For the users that don't have/need multi-tenancy in their authorization structure, we created a pre-inserted tenant (id: **t1**) that comes default when you serve a Permify service.
-Several things changed when we moved to tenant based infrastructure, these are:
-
-- [Multi Tenancy on Permify](#multi-tenancy-on-permify)
- - [API endpoints now have Tenant ID field](#api-endpoints-now-have-tenant-id-field)
- - [Check API](#check-api)
- - [Added Tenancy Service](#added-tenancy-service)
- - [Permission Database Tenancy Table and Tenant Id column](#permission-database-tenancy-table-and-tenant-id-column)
- - [Tenant Table](#tenant-table)
- - [Tenant ID Column](#tenant-id-column)
-- [Need any help ?](#need-any-help-)
+### Tenancy Based APIs
-### API endpoints now have Tenant ID field
-
-All API endpoints now have a `tenant_id` mandatory field. Let's examine a check request below,
+Almost all Permify API endpoints have a `tenant_id` mandatory field. Let's examine a check request below,
#### Check API
-
+
```go
cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckRequest {
@@ -61,8 +43,8 @@ cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckReq
})
```
-
-
+
+
```javascript
client.permission.check({
@@ -90,8 +72,51 @@ client.permission.check({
})
```
-
-
+
+
+
+```python
+import permify
+from permify.models.permission_check_request import PermissionCheckRequest
+from permify.rest import ApiException
+from pprint import pprint
+
+configuration = permify.Configuration(host="http://localhost")
+
+with permify.ApiClient(configuration) as api_client:
+ api_instance = permify.PermissionApi(api_client)
+ tenant_id = 't1'
+
+ body = PermissionCheckRequest(
+ tenant_id=tenant_id,
+ metadata={
+ "snapToken": "",
+ "schemaVersion": "",
+ "depth": 20
+ },
+ entity={
+ "type": "repository",
+ "id": "1",
+ },
+ permission="edit",
+ subject={
+ "type": "user",
+ "id": "1",
+ }
+ )
+
+ try:
+ api_response = api_instance.permissions_check(tenant_id, body)
+ if api_response.can == PermissionCheckResponse.Result.RESULT_ALLOWED:
+ print("RESULT_ALLOWED")
+ else:
+ print("RESULT_DENIED")
+ except ApiException as e:
+ print(f"Exception when calling PermissionApi->permissions_check: {e}")
+```
+
+
+
```curl
curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
@@ -114,20 +139,21 @@ curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permission
},
}'
```
-
+
-Users that come from version 0.2.x and users that have a single tenant can enter **t1** as tenant id. See changes on the other endpoints from [API Overview Section](../api-overview.md).
+Users that come from version 0.2.x and users that have a single tenant can enter **t1** as tenant id. See changes on the other endpoints from [API Overview Section](../getting-started/enforcement).
-### Added Tenancy Service
+### Tenancy Service
-To manage tenants we have added a Tenancy service; you can create, delete and list tenants. See the [Tenancy Service](../../api-overview/tenancy) in Using The API section.
+To manage tenants we have added a Tenancy service; you can create, delete and list tenants. See the [Tenancy Service](../../api-reference/tenancy/create-tenant) in Using The API section.
-### Permission Database Tenancy Table and Tenant Id column
+### Permission Database
#### Tenant Table
-A tenants table has been added to the Permission database to store tenant's details. The new folder structure changed as follows:
+A tenants table has been added to the Permissions database to store tenants' details.
+
```
tables
├── migrations
@@ -139,7 +165,7 @@ tables
#### Tenant ID Column
-Relation tuples and schema definition tables now have a tenant_id column, which stores the id of the tenant that the data belongs.
+Authorization DATA and schema definition tables now have a tenant_id column, which stores the id of the tenant that the data belongs.
Let's take a look at a snapshot of the demo table on an example Permission Database.
diff --git a/docs/versioned_docs/version-0.6.x/use-cases/simple-rbac.md b/docs/use-cases/rbac.mdx
similarity index 97%
rename from docs/versioned_docs/version-0.6.x/use-cases/simple-rbac.md
rename to docs/use-cases/rbac.mdx
index 85d70b6b..9835ac40 100644
--- a/docs/versioned_docs/version-0.6.x/use-cases/simple-rbac.md
+++ b/docs/use-cases/rbac.mdx
@@ -1,9 +1,7 @@
---
-sidebar_position: 1
+title: Role Based Access Control (RBAC)
---
-# Role Based Access Control
-
Want to implement roles and permissions in your application? Permify fully covers you at that point. The example below shows how to model simple role based access controls for organizational roles and permissions with our authorization language, [Permify Schema].
[Permify Schema]: ../../getting-started/modeling
@@ -120,7 +118,7 @@ organization:21#agent@user:ege
For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-[Relational Tuples]: ../getting-started/sync-data.md
+[Relational Tuples]: ../getting-started/sync-data
## Need any help ?
diff --git a/docs/versioned_docs/version-0.6.x/use-cases/rebac.md b/docs/use-cases/rebac.mdx
similarity index 96%
rename from docs/versioned_docs/version-0.6.x/use-cases/rebac.md
rename to docs/use-cases/rebac.mdx
index 561b500e..f33c98b6 100644
--- a/docs/versioned_docs/version-0.6.x/use-cases/rebac.md
+++ b/docs/use-cases/rebac.mdx
@@ -1,5 +1,6 @@
-
-# Relationship Based Access Control
+---
+title: Relationship Based Access Control (ReBAC)
+---
Permify was designed and structured as a true [Relationship Based Access Control(ReBAC)](https://permify.co/post/relationship-based-access-control-rebac/) solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
@@ -7,7 +8,7 @@ Here are some common use cases where you can benefit from using ReBAC models in
- [Protecting Organizational-Wide Resources](#protecting-organizational-wide-resources)
- [Deeply Nested Hierarchies](#deeply-nested-hierarchies)
-- [User Groups & Team Permissions](#user-groups--team-permissions)
+- [User Groups & Team Permissions](#user-groups-and-team-permissions)
## Protecting Organizational-Wide Resources
@@ -208,9 +209,7 @@ team:1#org@organization:1#...
project:1#team@team:1#...
-Lets assume we created the above [relational tuples]. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** since the `user:1` is an admin of the `organization:1` and `project:1` belongs to `team:1`, which belongs to `organization:1`.
-
-[relational tuples]: ../getting-started/sync-data.md
+Lets assume we created the above tuples. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** since the `user:1` is an admin of the `organization:1` and `project:1` belongs to `team:1`, which belongs to `organization:1`.
Let's break down this case,
diff --git a/docs/versioned_docs/version-0.2.x/api-overview.md b/docs/versioned_docs/version-0.2.x/api-overview.md
deleted file mode 100644
index 762d98a5..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview.md
+++ /dev/null
@@ -1,36 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Overview
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 3 core parts; ***modeling authorization***, ***storing authorization data*** and ***enforcement***. Therefore, Permify API has sections that represent the functionalities of these core parts.
-
-- **Permission Section**: Consist enforcement requests and options.
-- **Relationship Section**: Authorization data operations such as creating, deleting and reading relational tuples.
-- **Schema Section**: Modeling and Permify Schema related functionalities including configuration and auditing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) and [REST](https://restfulapi.net/).
-
-[](https://god.gw.postman.com/run-collection/16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de?action=collection%2Ffork&collection-url=entityId%3D16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de%26entityType%3Dcollection%26workspaceId%3Dd3a8746c-fa57-49c0-83a5-6fcf25a7fc05)
-[](https://app.swaggerhub.com/apis-docs/permify/permify/latest)
-
-## Core Paths
-
-- Check access with [Check API](./api-overview/check-api.md)
-- Configure your authorization model with [Schema Write](./api-overview/write-schema.md)
-- Write relational tuples with [Write API](./api-overview/write-relationships.md)
-- Read relation tuples and filter them with [Read API](./api-overview/read-api.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/delete-relationships.md)
-- Expand schema actions with [Expand API](./api-overview/expand-api.md)
-- Get permissions of your resources with [Schema Lookup](./api-overview/schema-lookup.md)
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/_category_.json b/docs/versioned_docs/version-0.2.x/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/check-api.md b/docs/versioned_docs/version-0.2.x/api-overview/check-api.md
deleted file mode 100644
index b9d9b56c..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/check-api.md
+++ /dev/null
@@ -1,122 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
-
-In Permify, you can perform two different types access checks,
-
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **data filtering (coming soon)** authorization checks , in form of `Which records can user U edit ?`
-
-In this section we'll investigate proior check request of Permify: **resource based** authorization checks. You can find subject based access checks in [data filtering] section.
-
-**Path:** POST /v1/permissions/check
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It containes type and id of the subject. |
-| [ ] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop|
-
-#### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}
-```
-
-#### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "remaining_depth": 0
-}
-```
-
-### Using gRPC Clients
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckRequest {
- Metadata: & v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism. See how [access decisions evaluated] in Permify.
-
-[access decisions evaluated]: ../../getting-started/enforcement#how-access-decisions-are-evaluated
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/delete-relationships.md b/docs/versioned_docs/version-0.2.x/api-overview/delete-relationships.md
deleted file mode 100644
index 17474d7e..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/delete-relationships.md
+++ /dev/null
@@ -1,98 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Relational Tuples
-
-You can delete any stored relation tuples with following path
-
-**Path:** POST /v1/relationships/delete
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-#### Request
-
-```json
-{
- "filter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- }
-}
-```
-
-### Using gRPC Clients
-
-
-
-
-```go
-rr, err: = client.Relationship.Delete(context.Background(), & v1.RelationshipDeleteRequest {
- Metadata: &v1.RelationshipDeleteRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.delete({
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/expand-api.md b/docs/versioned_docs/version-0.2.x/api-overview/expand-api.md
deleted file mode 100644
index ff4c9086..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/expand-api.md
+++ /dev/null
@@ -1,308 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-We developed a expand API to see Permify Schema actions in a tree structure to improve observability and reasonability of access permissions.
-
-Expand API is represented by a user set tree whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs, and intermediate nodes represent union, intersection, or exclusion operators.
-
-Expand is crucial for our users to reason about the complete set of users and groups that have access to their objects, which allows them to build efficient search indices for access-controlled content. Unlike the Read API, Expand follows indirect references expressed through user set rewrite rules.
-
-## Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify's DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:** POST /v1/permissions/expand
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../reference/snap-tokens) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”.
-| [x] | action | string | - | The action the user wants to perform on the resource |
-
-### Expand Push Action
-
-Request
-
-
-
-### Using gRPC Clients
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), & v1.PermissionExpandRequest {
- Metadata: & v1.PermissionExpandRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-#### **Graph Representation of Expanding Read Action**
-
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/read-api.md b/docs/versioned_docs/version-0.2.x/api-overview/read-api.md
deleted file mode 100644
index 2044a616..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/read-api.md
+++ /dev/null
@@ -1,131 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-**Path:** POST /v1/relationship/read
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-#### Request
-
-```json
-{
- "metadata": {
- "snap_token": "",
- },
- "filter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "member",
- "subject": {
- "type": "",
- "ids": [
- ""
- ],
- "relation": ""
- }
- }
-}
-```
-
-#### Response
-
-```json
-[
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "member",
- "subject": {
- "type": "user",
- "id": "1"
- }
- },
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "member",
- "subject": {
- "type": "user",
- "id": "2"
- }
- }
-]
-```
-
-### Using gRPC Clients
-
-
-
-
-```go
-rr, err: = client.Relationship.Read(context.Background(), & v1.RelationshipReadRequest {
- Metadata: &v1.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.read({
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [
- ""
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/schema-lookup.md b/docs/versioned_docs/version-0.2.x/api-overview/schema-lookup.md
deleted file mode 100644
index 96b75d1a..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/schema-lookup.md
+++ /dev/null
@@ -1,90 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Schema Lookup
-
-You can use schema lookup API endpoint to retrieve all permissions associated with a resource relation. Basically, you can perform enforcement without checking stored authorization data. For example in given a Permify Schema like:
-
-```
-entity user {}
-
-entity document {
-
- relation assignee @user
- relation manager @user
-
- action view = assignee or manager
- action edit = manager
-
-}
-
-```
-
-Let's say you have a user X with a manager role. If you want to check what user X can do on a documents ? You can use the schema lookup endpoint as follows,
-
-**Path:** POST /v1/permissions/lookup-schema
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [x] | entity_type | string | - | type of the entity.
-| [x] | relation_names | string[] | - | string array that holds entity relations |
-
-#### Request
-
-```json
-{
- "metadata": {
- "schema_version": ""
- },
- "entity_type": "document",
- "relation_names": [ "manager" ]
-}
-```
-
-#### Response
-
-```json
-{
- "data": {
- "action_names": [
- "view",
- "edit"
- ]
- }
-}
-```
-
-
-### Using gRPC Clients
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSchema(context.Background(), & v1.PermissionLookupSchemaRequest {
- Metadata: & v1.PermissionLookupSchemaRequestMetadata {
- SchemaVersion: ""
- },
- EntityType: "document",
- RelationNames: []string {"manager"},
-})
-```
-
-
-
-
-```javascript
-client.permission.LookupSchema({
- metadata: {
- schema_version: ""
- },
- entity_type: "document",
- relation_names: [ "manager" ]
-})
-```
-
-
-
-
-The response will return all the possible actions that manager can perform on documents. Also you can extend relation lookup as much as you want by adding relations to the **"relation_names"** array.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/api-overview/write-relationships.md b/docs/versioned_docs/version-0.2.x/api-overview/write-relationships.md
deleted file mode 100644
index 37eb812f..00000000
--- a/docs/versioned_docs/version-0.2.x/api-overview/write-relationships.md
+++ /dev/null
@@ -1,190 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Relationships
-
-In Permify, relations between your entities, objects and users stored as [relational tuples] in [writeDB]. Since relations and authorization data's are live instances these relational tuples can be created with an simple API call in runtime.
-
-When using Permify, the application client should update writeDB about the changes happening in entities or resources that are related to the authorization structure. If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [writeDB] up-to-date. Besides, each relational tuple should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as relation tuples and store in [writeDB].
-
-
-
-[relational tuples]: ../../getting-started/sync-data
-[writeDB]: ../../getting-started/sync-data#where-relational-tuples-used-
-
-## Example Request
-
-So if user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` must be created by using **/v1/relationships/write** endpoint.
-
-**Path:** POST /v1/relationships/write
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-### Request
-
-```json
-{
- "schema_version": "",
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}
-```
-
-### Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../reference/snap-tokens) and how its avoiding stale cache.
-
-### Using gRPC Clients
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "admin",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-## Suggested Workflow
-
-The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-
-### Two Phase Commit Approach
-In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
-
-To give more concurrent example of this action, let's take a look at below createDocument function
-
-```go
-func CreateDocuments(db *gorm.DB) error {
-
- tx := db.Begin()
- defer func() {
- if r := recover(); r != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- }
- }()
-
- if err := tx.Error; err != nil {
- return err
- }
-
- if err := tx.Create(docs).Error; err != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- return err
- }
-
- // if transaction successful, write relation tuple to Permify
- permify.WriteRelationships(...)
-
- return tx.Commit().Error
-}
-```
-The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-
-### Relationships that not stored in application database
-
-Although ownership generally stored in application databases, there are some relations that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
-
-For example, you can model a simple project management authorization in Permify as follows,
-
-```perm
-entity user {}
-
-entity team {
-
- relation owner @user
- relation member @user
-}
-
-entity project {
-
- relation team @team
- relation owner @user
-
- action view = team.member or team.owner or project.owner
- action edit = project.owner or team.owner
- action delete = project.owner or team.owner
-
-}
-```
-
-This **team member** relation won't need to be stored in the application database. Storing it only in Permify - WriteDB - is enough. In that situation, `WriteRelationships` can be performed in any logical place in your stack.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/deployment/_category_.json b/docs/versioned_docs/version-0.2.x/deployment/_category_.json
deleted file mode 100644
index 3bbc347f..00000000
--- a/docs/versioned_docs/version-0.2.x/deployment/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Deployment",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/deployment/aws.md b/docs/versioned_docs/version-0.2.x/deployment/aws.md
deleted file mode 100644
index a1f5560d..00000000
--- a/docs/versioned_docs/version-0.2.x/deployment/aws.md
+++ /dev/null
@@ -1,188 +0,0 @@
----
-title: AWS ECS, ECR & EC2
----
-
-# Deploy on AWS ECS, ECR & EC2
-
-AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
-
-There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
-
-ECS is a container management service. You can run your containers as task definitions, and It’s one of the easiest ways to deploy containers.
-
-If you’d like to watch this tutorial rather than reading. Here’s the video version.
-
-
-
-There is no prerequisite in this tutorial. You can simply deploy permify by following this step-by-step guide. However, if you want to integrate more advanced AWS security & networking features, we’ll follow up with a new tutorial guideline.
-
-At the end of this tutorial you’ll be able to;
-
-1. [Create a security group](#create-an-ec2-security-group)
-2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
-3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
-4. [Running our task definition](#4-running-our-task-definition)
-
-## 1. Create an EC2 Security Group
-
-So first thing first, let’s go over into security groups and create our security group. We’ll need this security group while creating our cluster.
-
-
-
-Search for “Security Groups” in the search bar. And go to the EC2 security groups feature.
-
-
-
-Then start creating a new security group.
-
-
-
-You have to name your security group, and give a description. Also, you need to choose the same VPC that you’ll going to use in EC2. So, I choose the default one. And I’m going to use same one while creating the ECS cluster.
-
-The next step is to configure our inbound rules. Here’s the configuration;
-
-```json
-//for mapping HTTP request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for mapping RPC request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3478",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for using SSH for connecting from your local computer.
-type = "Custom TCP", protocol = "TCP", port_range = "22",source = "Anywhere", 0.0.0.0/0
-```
-
-We have configured the HTTP and RPC ports for Permify. Also, we added port “22” for SSH connection. So, we can connect to EC2 through our local terminal.
-
-Now, we’re good to go. You can create the security group. And it’s ready to use in our ECS.
-
-## 2. Creating an ECS cluster
-
-
-
-The next step is to create an ECS cluster. From your AWS console search for Elastic Container Service or ECS for short.
-
-
-
-Then go over the clusters. As you can see there are 2 types of clusters. One is for ECS and another for EKS. We need to use ECS, EKS stands for Elastic Kubernetes Service. Today we’re not going to cover Kubernetes.
-
-Click **“Create Cluster”**
-
-
-
-Let’s create our first Cluster. Simply you have 3 options; Serverless(Network Only), Linux, and Windows. We’re going to cover EC2 Linux + Networking option.
-
-
-
-The next step is to configure our Cluster, starting with your Cluster name. Since we’re deploying Permify, I’ll call it “permify”.
-
-Then choose your instance type. You can take a look at different instances and pricing from [here](https://aws.amazon.com/ec2/pricing/on-demand/). I’m going with the t4 large. For cost purposes, you can choose t2.micro if you’re just trying out. It’s free tier eligible.
-
-Also, if you want to connect this EC2 instance from your local computer. You need to use SSH. Thus choose a key pair. If you have no such intention, leave it “none”.
-
-
-
-Now, we need to configure networking. First, choose your VPC, we use the default VPC as we did in the security groups. And choose any subnet on that VPC.
-
-You want to enable auto-assigned IP to make your app reachable from the internet.
-
-Choose the security group we have created previously.
-
-And voila, you can create your cluster. Now, we need to run our container in this cluster. To do that, let’s go over task definitions. And create our container definition.
-
-## 3. Creating and running task definitions
-
-Go over to ECS, and click the task definitions.
-
-
-
-And create a new task definition.
-
-
-
-Again, you’re going to ask to choose between; FARGATE, EC2, and EXTERNAL (On-premise). We’ll continue with EC2.
-
-Leave everything in default under the “Configure task and container definitions” section.
-
-
-
-Under the IAM role section you can choose “ecsTaskExecutionRole” if you want to use Cloud Watch later.
-
-You can leave task size in default since it’s optional for EC2.
-
-The critical part over here is to add our container. Click on the “Add Container” button.
-
-
-
-Then we need to add our container details. First, give a name. And then the most important part is our image URI. Permify is registered on the Github Registry so our image is;
-
-```yaml
-ghcr.io/permify/permify:latest
-```
-
-Then we need to define memory limit for the container, I went with 1024. You can define as much as your instance allows.
-
-Next step is to mapping our ports. As we mentioned in security groups, Permify by default listens;
-
-- `3476 for HTTP port`
-- `3478 for RPC port`
-
-
-
-Then we need to define command under the environment section. So, in order to start permify we first need to add “serve” command.
-
-For using properly we need a few other. Here’s the commands we need.
-
-```yaml
-serve, --database-engine=postgres, --database-name=, --database-uri=postgres://:@:, --database-pool-max=20
-```
-
-- `serve` ⇒ for starting the Permify.
-- `--database-engine=postgres` ⇒ for defining the db we use.
-- `--database-name=` ⇒ name of the database you use.
-- `--database-uri=postgres://:password@:` ⇒ for connecting your database with URI.
-- `--database-pool-max=20` ⇒ the depth for running in graph.
-
-We’re nice and clear, add the container and then just create your task definition. We’ll use this definition to run in our cluster.
-
-So, let’s go over and run our task definition.
-
-## 4. Running our task definition
-
-
-
-Let’s go to ECS and enter into our cluster. And go over into the tasks to run our task.
-
-
-
-Click to “Run new Task”
-
-
-
-Choose EC2 as a launch type. Then pick the task definition we just created. And leave everything else in the default. You can run your task now.
-
-We have just deployed our container into EC2 instance with ECS. Let’s test it.
-
-Now you can go over into EC2, and click on the running instances. Find the instance named `ECS Instance - EC2ContainerService-` in the running instances.
-
-
-
-Copy the Public IPv4 DNS from the right corner, and paste it into your browser. But you need to add `:3476` to access our http endpoint. So it should be like this;
-
-`:3476`
-
-and if you add healthz at the end like this;
-
-`:3476/healthz`
-
-you should get Serving status :)
-
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/deployment/azure.md b/docs/versioned_docs/version-0.2.x/deployment/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/versioned_docs/version-0.2.x/deployment/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/deployment/google.md b/docs/versioned_docs/version-0.2.x/deployment/google.md
deleted file mode 100644
index dcb3614a..00000000
--- a/docs/versioned_docs/version-0.2.x/deployment/google.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Google Compute Engine
----
-
-# Deploy on Google Compute Engine
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/deployment/kubernetes.md b/docs/versioned_docs/version-0.2.x/deployment/kubernetes.md
deleted file mode 100644
index 997c8942..00000000
--- a/docs/versioned_docs/version-0.2.x/deployment/kubernetes.md
+++ /dev/null
@@ -1,174 +0,0 @@
----
-title: Deploy on Kubernetes Cluster
----
-
-# Deploy on Kubernetes Cluster
-
-In this section we’re going to deploy Permify in AWS EKS which is Amazon Elastic Kubernetes Service. EKS is a managed service that you can easily run Kubernetes in AWS.
-
-Here’s what we’re going to do step-by-step;
-
-1. [Configure our AWS IAM credentials](#configure-aws-cli-with-your-iam-account)
-3. [Create EKS cluster and configure nodes](#creating-an-aws-eks-cluster)
-4. [Deploy Permify to nodes](#deploying--running-permify-in-nodes)
-
-There are a couple of small prerequisites for this tutorial.
-
-### Pre-requisites
-
-- An AWS account.
-- The AWS Command Line Interface (CLI) is installed and configured on your local machine. — [Click here](https://us-east-1.console.aws.amazon.com/iamv2/home?region=us-east-1#/home) to go to IAM
-- The AWS IAM Authenticator for Kubernetes is installed and configured on your local machine.
-
-## Configure AWS CLI with your IAM account.
-
-The first step is to configure our AWS IAM account into our local terminal so that we can run commands. Most of you probably have a configured AWS account if you ever set up anything into AWS programmatically, so you can skip this. If you don’t follow these steps.
-
-### Create an AWS IAM Programmatic Access Account
-
-First, let’s create IAM credentials for ourselves. Search IAM from the AWS console. You need to write down the account ID if you want to log in AWS console with this account as well. Let’s go over users and start creating our credentials.
-
-
-
-At Users screen click to “Add users” — and you’ll end up in your first screen creating user credentials. Here you can define the name of the user. Also there 2 options that you can choose simultaneously.
-
-But you must choose “Access key - Programmatic access” option. It’ll allow us to configure our AWS CLI on our local machine.
-
-You can also choose “Password - AWS Management Console access” if you want to log in to this account through the console. But you’ll need the Account ID that I mentioned in the IAM console screen.
-
-In the next screen, you’ll be asked to create or copy the user-set permissions. For this tutorial, you’ll only need to access EKS resources and features. So lets create group by clicking the “Create group” — and then at pop-up screen search for EKS.
-
-
-
-I’ll choose all EKS permissions but if you have certain policies internally, just stick with them. You’ll only need following permission to;
-
-- `AmazonEKSClusterPolicy`
-- `AmazonEKSServicePolicy`
-- `AmazonEKSVPCResourceController`
-- `AmazonEKSWorkerNodePolicy`
-
-Then simply you can review and create the user.
-
-
-
-Once you created the credentials you’ll prompt the “Access key ID” and “Secret access key”, you should save this down somewhere. We’re going the use these to configure our local machine with AWS CLI.
-
-### **Configure AWS CLI with your IAM account**
-
-Let’s open our local terminal
-
-```jsx
-aws configure
-```
-
-Next you’ll ask for the following credentials;
-
-- `AWS Access Key ID`
-- `AWS Secret Access Key`
-- `Default region name`
-- `Default output format` (leave it empty)
-
-## Creating an AWS EKS Cluster
-
-For the first step, we need to install [eksctl](https://eksctl.io/) — which is like kubectl but for AWS EKS. It helps us to set up and deploy our cluster and nodes within a fraction of the time.
-
-Let’s download eksctl using brew.
-
-
-```jsx
-brew tap weaveworks/tap
-```
-
-While installing the eksctl, we’ll end up getting kubectl and other dependencies.
-
-```jsx
-brew install weaveworks/tap/eksctl
-```
-
-Now, we’re ready to create our EKS cluster. You can define certain things while deploying standard the cluster beside the name and version like; the region you want to deploy, the EC2 instance type of each node, and the number of nodes you want to run.
-
-```bash
-eksctl create cluster \
---name \
---version 1.24 \
---region \
---nodegroup-name permify \
---node-type t2.small \
---nodes 2
-```
-
-## Deploying & Running Permify in Nodes
-
-The next stop is applying our manifests which will help us to deploy and configure our container/Permify.
-
-Let’s create our deployment manifest first.
-
-```yaml
-apiVersion: apps/v1
-kind: Deployment
-metadata:
- labels:
- app: permify
- name: permify
-spec:
- replicas: 2
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-name=demo"
- - "--database-uri=postgres://postgres:nOcodeSTIAnLAba@permify-test.ceuo5kqsxyea.us-east-1.rds.amazonaws.com:5432"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
-status: {}
-```
-
-Now let’s apply our deployment manifest
-
-```jsx
-kubectl apply -f deployment.yaml
-```
-
-The next step is to create a service manifest, this will allow us to configure our container app.
-
-```jsx
-apiVersion: v1
-kind: Service
-metadata:
- name: permify
-spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
-status:
- loadBalancer: {}
-```
-
-Let’s apply service.yaml to our nodes.
-
-```jsx
-kubectl apply -f service.yaml
-```
-
-Last but not least, we can check our pods & nodes. And we can start using the container with load balancer
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/_category_.json b/docs/versioned_docs/version-0.2.x/example-use-cases/_category_.json
deleted file mode 100644
index 9f9db2d4..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Common Use Cases",
- "position": 8,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/organizational.md b/docs/versioned_docs/version-0.2.x/example-use-cases/organizational.md
deleted file mode 100644
index 7c4f94df..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/organizational.md
+++ /dev/null
@@ -1,151 +0,0 @@
-
-
-# Organizations & Hierarchies
-
-Group your users by organization with giving them access organzational-wide resources. In this use case we'll follow a simplified version of Github's access control that shows how to model basic repository push, read and delete permissions with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
--------
-
-## Full Schema
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents user of this repository
- relation owner @user
-
- // permissions
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 3 entities,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that user and repositories belongs.
-
-- `repository`, represents a repository in a github.
-
-### Relations
-
-To define relation, **relations** needed to be created as entity attributes.
-
-#### organization entity
-
-In our schema we defined 2 relation in organization entity, respectively; ``admin`` and ``member``
-
-```perm
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-``admin`` indicates that the user got an administrative role in that organization and with the same logic ``member`` represents the default user that belongs to that organization.
-
-#### repository entity
-
-Repository entities have 2 relations, these are ``parent`` and ``owner``. Both of these relations represents actual database relations with other entities rather than a role-based approach likewise to the **organization** entity above.
-
-```perm
-entity repository {
-
- relation parent @organization
- relation owner @user
-
-}
-```
-
-``parent`` relation represents the parent organization with a repository. And ``owner`` represents the specific user, the repository's owner.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### repository actions
-
-In our schema, we examined one of the main functionalities can the user make on any GitHub repository. These are pushing to the repo, reading & viewing the repo, and deleting that repo.
-
-We can say only,
-
-- Repository owners can ``push`` to that repo.
-- Repository owners, who also need to have an administrative role or be an owner of the parent organization, can ``read``.
-- Repository owners or administrative roles in an organization can ``delete`` the repository.
-
-```
-entity repository {
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-Since ``parent` represents the parent organization of repository. It can reach repositories parent organization relations with comma. So,
-
-- ``parent.admin``
-indicates admin role on organization
-
-- ``parent.member``
-indicates member of that organization.
-
-## Example Relational Tuples
-
-organization:2#admin@user:daniel
-
-organization:54#member@user:ege
-
-organization:12#member@user:jack
-
-repository:34#parent@organization:54
-
-repository:68#owner@user:12
-
-repository:12#owner@user:46
-
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/ownership.md b/docs/versioned_docs/version-0.2.x/example-use-cases/ownership.md
deleted file mode 100644
index 0891e84b..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/ownership.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# Ownership
-
-Granting privileges to the owner of the resource is a common pattern that many applications follow. Generally we want creators of the resource - document, post, comment etc - have superior power on that resource. Check out the below model see how ownership can be modeled with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
--------
-
-```perm
-entity user {}
-
-entity comment {
-
- // represents comment's owner
- relation owner @user
-
- // permissions
- action edit = owner
- action delete = owner
-}
-
-```
-
-## Sample Relational Tuples
-
-comment:2#owner@user:1
-
-comment:3#owner@user:51
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/parent-child.md b/docs/versioned_docs/version-0.2.x/example-use-cases/parent-child.md
deleted file mode 100644
index 88ecd8b0..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/parent-child.md
+++ /dev/null
@@ -1,141 +0,0 @@
-
-# Parent Child Relationships
-
-See how parent child relations can model in Permify. In this use case we'll follow a simple student-calendar management system with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
--------
-
-## Full Schema
-
-```perm
-entity user {}
-
-entity student {
-
- // refers student itself
- relation self @user
-
- // teacher of the student
- relation teacher @user
-}
-
-entity class {
-
- // refers class member
- relation member @student
-
- // calender view permission
- action view_calendar = member.self or member.teacher
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 3 entity,
-
-- `user`, represents users. This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `student`, representing students. student and class entities have many to many relation.
-
-- `class`, representing class that students belongs.
-
-### Relations
-
-To define relation, **relations** needed to be created as entity attributes.
-
-#### student entity
-
-In our schema above, we defined 2 relation in user entity, respectively; ``self`` and ``student``
-
-```perm
-entity student {
-
- relation self @user
- relation teacher @user
-
-}
-
-```
-
-**self** describes student itself, and **teacher** represents the teacher that students take a class from.
-
-#### class entity
-
-The class entity has only one relation, which is ``member``. It represents the member of the class. Basically, students whom taking that specific class.
-
-```perm
-entity class {
-
- relation member @student
-
-}
-```
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### class actions
-
-Think each class has a calendar that shows necessary times and dates of lectures, deadlines etc.
-
-We want only,
-
-- Students that take that class
-- Teachers, whom is teacher of the student that takes that specific class (class member).
-
-can access to calendar of that spesific class.
-
-```perm
-entity class {
-
- action view_calendar = member.self or member.teacher
-
-}
-```
-
-Since ``member` represents the relation with student entitiy. It can reach its relations with comma. So,
-
-- ``member.self``
-indicates student itself, whom takes that class.
-
-- ``member.teacher``
-indicates teacher of student, whom takes that class.
-
-## Example Relational Tuples
-
-student:2#self@user:daniel
-
-student:54#self@user:daniel
-
-student:12#teacher@user:jack
-
-student:34#teacher@user:jack
-
-class:68#member@student:54
-
-class:12#member@student:34
-
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/sharing.md b/docs/versioned_docs/version-0.2.x/example-use-cases/sharing.md
deleted file mode 100644
index 0850cbc6..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/sharing.md
+++ /dev/null
@@ -1,40 +0,0 @@
-
-# Sharing & Collaboration
-
-Inviting a team member to a document, project or repository should be hassle free to model. In Permify you can achieve this with simply defining a invite action. Check out the below model block see how sharing can be modeled with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
--------
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
- relation manager @user
-
-}
-
-entity project {
-
- // represents project's parent organization
- relation org @organization
-
- // represents owner of this project
- relation owner @user
-
- // invite permission
- action invite = org.admin or owner
-
-}
-
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/simple-rbac.md b/docs/versioned_docs/version-0.2.x/example-use-cases/simple-rbac.md
deleted file mode 100644
index 17933ead..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/simple-rbac.md
+++ /dev/null
@@ -1,130 +0,0 @@
----
-sidebar_position: 1
----
-
-# Role Based Access Control
-
-Want to implement role and permissions to your application ? Permify fully covers you at that point. Below example shows how to model simple role based access control for organizational roles and permissions with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
--------
-
-## Full Schema
-
-```perm
-entity user {}
-
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
- //organization files access permissions
- action view_files = admin or manager or (member and not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 2 entities,
-
-- `user`, represents users (maybe corresponds as employees). This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, representing the organization the user (employees) belongs. It has several roles and permissions related to the specific resources such as organization files and vendor files.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles. In this example, we have 4 organizational wide roles, respectively; admin, manager, member, and agent.
-
-```perm
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
-}
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### organization actions
-
-In our schema, we define several actions for controlling access permissions on organization files and organization vendor's files.
-
-```perm
-entity organization {
-
- //organization files access permissions
- action view_files = admin or manager or (member and not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-let's take a look at some of the actions:
-
-- ``action edit_files = admin or manager``
-indicates that only the admin or manager has permission to edit files in the organization.
-
-- ``action view_files = admin or manager or (member and not agent)``
-indicates that the admin, manager, or members (without having the agent role) can view organization files.
-
-
-
-## Example Relational Tuples for this case
-
-organization:2#admin@user:daniel
-
-organization:5#member@user:ashley
-
-organization:17#manager@user:mert
-
-organization:21#agent@user:ege
-
-.
-.
-.
-
-For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/example-use-cases/user-groups.md b/docs/versioned_docs/version-0.2.x/example-use-cases/user-groups.md
deleted file mode 100644
index ed259649..00000000
--- a/docs/versioned_docs/version-0.2.x/example-use-cases/user-groups.md
+++ /dev/null
@@ -1,203 +0,0 @@
-
-# User Groups
-
-This use case shows how to organize permissions based on groupings of users or resources. In this use case we'll follow a simple project management app with Permify's DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
--------
-
-## Full Schema
-
-```perm
-entity user {}
-
-entity organization {
-
- //organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- // represents owner or creator of the team
- relation owner @user
-
- // represents direct member of the team
- relation member @user
-
- // reference for organization that team belong
- relation org @organization
-
- // organization admins or owners can edit, delete the team details
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- // to invite someone you need to be admin and either owner or member of this team
- action invite = org.admin and (owner or member)
-
- // only owners can remove users
- action remove_user = owner
-
-}
-
-entity project {
-
- // references for team and organization that project belongs
- relation team @team
- relation org @organization
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 4 entity,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that contain teams.
-
-- `team`, represents teams, which belongs to a organization.
-
-- `project`, represents projects that belongs teams.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles.
-
-The organization entity has 2 relations ``admin`` and ``member`` users. Think of these as organizational-wide roles.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-#### team entity
-
-The eeam entity has its own relations respectively, ``owner``, ``member`` and ``org``
-
-```perm
-entity team {
-
- relation owner @user
- relation member @user
- relation org @organization
-
-}
-```
-
-#### project entity
-
-Project entity has ``team`` and ``org`` relations. Both these relations represents parent relationship with other entites, parent team and parent organization.
-
-```perm
-entity project {
-
- relation team @team
- relation org @organization
-
-}
-```
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### team actions
-
-- Only organization ***admin (admin role)*** and ***team owner*** can perform editing and deleting team spesific resources.
-
-- Moreover, for inviting a colleague to a team you must have ***admin role*** and either be a ***owner*** or ***member*** on that team.
-
-- To remove users in team you must be a ***owner*** of that team.
-
-And these rules reflects Permify Schema as:
-
-```perm
-entity team {
-
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- action invite = org.admin and (owner or member)
- action remove_user = owner
-
-}
-```
-
-#### project actions
-
-And there are the project actions below. It consists of checking access for basic operations such as viewing, editing, or deleting project resources.
-
-```perm
-entity project {
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Example Relational Tuples
-
-team:2#member@user:daniel
-
-team:54#owner@user:daniel
-
-organization:12#admin@user:jack
-
-organization:51#member@user:jack
-
-organiation:41#member@team:42#member
-
-project:35#team@team:34#....
-
-
-.
-.
-.
-.
-.
-
-
-organization:41#member@team:42#member
-
-**--> represents members of team 42 also members in organization 41**
-
-project:35#team@team:34#....
-
-**--> represents project 54 is in team 34**
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/getting-started/_category_.json b/docs/versioned_docs/version-0.2.x/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/versioned_docs/version-0.2.x/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.2.x/getting-started/enforcement.md b/docs/versioned_docs/version-0.2.x/getting-started/enforcement.md
deleted file mode 100644
index c2f807ac..00000000
--- a/docs/versioned_docs/version-0.2.x/getting-started/enforcement.md
+++ /dev/null
@@ -1,239 +0,0 @@
----
-sidebar_position: 4
----
-
-# Access Control Check
-
-In Permify, you can perform access control checks as both [resource specific] and [subject specific] (data filtering) with single API calls.
-
-A simple [resource specific] access check takes form of ***Can the subject U perform action X on a resource Y ?***. A real world example would be: can user:1 edit document:2 where the right side of the ":" represents identifier of the entity.
-
-On the other hand [subject specific] access check takes form of ***Which resources does subject U perform an action X ?*** This option is best for filtering data or bulk permission checks.
-
-[resource specific]: #resource-specific-check-request
-[subject specific]: #subject-specific-data-filtering-check-request
-
-## Performance & Availability
-
-Permify designed to answer these authorization questions efficiently and with minimal complexity while providing low latency with:
-- Using its parallel graph engine.
-- Storing the relationships between resources beforehand in Permify data store: [writeDB], rather than providing these relationships at “check” time.
-- Implementing permission caching to not recompute repeated permission checks, and in memory cache to store authorization schema.
-- Using [Snap Tokens](../../reference/snap-tokens) to achieve consistency and high performance in cache.
-
-Performance and availability of the API calls - especially access checks - are crucial for us and we're ongoingly improving and testing it with various methods.
-
-:::info
-We would love to create a test environment for you in order to test Permify API and see performance and availability of it. [Schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-[writeDB]: ../getting-started/sync-data.md
-
-## Resource Specific Check Request
-
-Let's follow an simplified access control decision for examining the resource specific [check] request.
-
-[check]: ../api-overview/check-api.md
-
-***Can the user 3 edit document 12 ?***
-
-#### Path:
-
-POST /v1/permissions/check
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop|
-
-#### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- },
- "entity": {
- "type": "document",
- "id": "12"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}
-```
-
-#### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "remaining_depth": 0
-}
-```
-
-### How Access Decisions Evaluated?
-
-Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
-
-In high level, access of an subject related with the relationships created between the subject and the resource. You can define this relationships in Permify Schema then create and store them as relational tuples, which is basically your authorization data.
-
-Permify Engine to compute access decision in 2 steps,
-1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
-2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
-
-Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
-
-[relational tuples]: ../../getting-started/sync-data
-[Permify Schema]: ../../getting-started/modeling
-
-When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity document {
-
- // represents documents parent organization
- relation parent @organization
-
- // represents owner of this document
- relation owner @user
-
- // permissions
- action edit = parent.admin or owner
- action delete = owner
-}
-```
-
-Which has a directed graph as follows:
-
-
-
-As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
-
-**Q1:** Get the owners of the `document:12`.
-
-**Q2:** Get admins of the organization where `document:12` belongs to.
-
-Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
-
-Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
-
-## Subject Specific (Data Filtering) Check Request
-
-For this access check you can ask questions in form of “Which resources can user:X do action Y?” And you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So we have a 2 seperate endpoints for data filtering check request,
-
-- [/v1/permissions/lookup-entity](#lookup-entity)
-- [/v1/permissions/lookup-entity-stream](#lookup-entity-streaming)
-
-### Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array
-
-#### Path:
-
-POST /v1/permissions/lookup-entity
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-
-#### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- }
-}
-```
-
-#### Response
-
-```json
-{
- "entity_ids": [
- "15","142","93214","312","612"
- ]
-}
-```
-
-### Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-#### Path:
-
-POST /v1/permissions/lookup-entity-stream
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-
-#### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- }
-}
-```
-
-#### Response
-
-```json
-{
- "(streaming entity IDs')"
-}
-```
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/getting-started/modeling.md b/docs/versioned_docs/version-0.2.x/getting-started/modeling.md
deleted file mode 100644
index 4be6f25d..00000000
--- a/docs/versioned_docs/version-0.2.x/getting-started/modeling.md
+++ /dev/null
@@ -1,241 +0,0 @@
----
-sidebar_position: 1
----
-
-# Modeling Authorization
-
-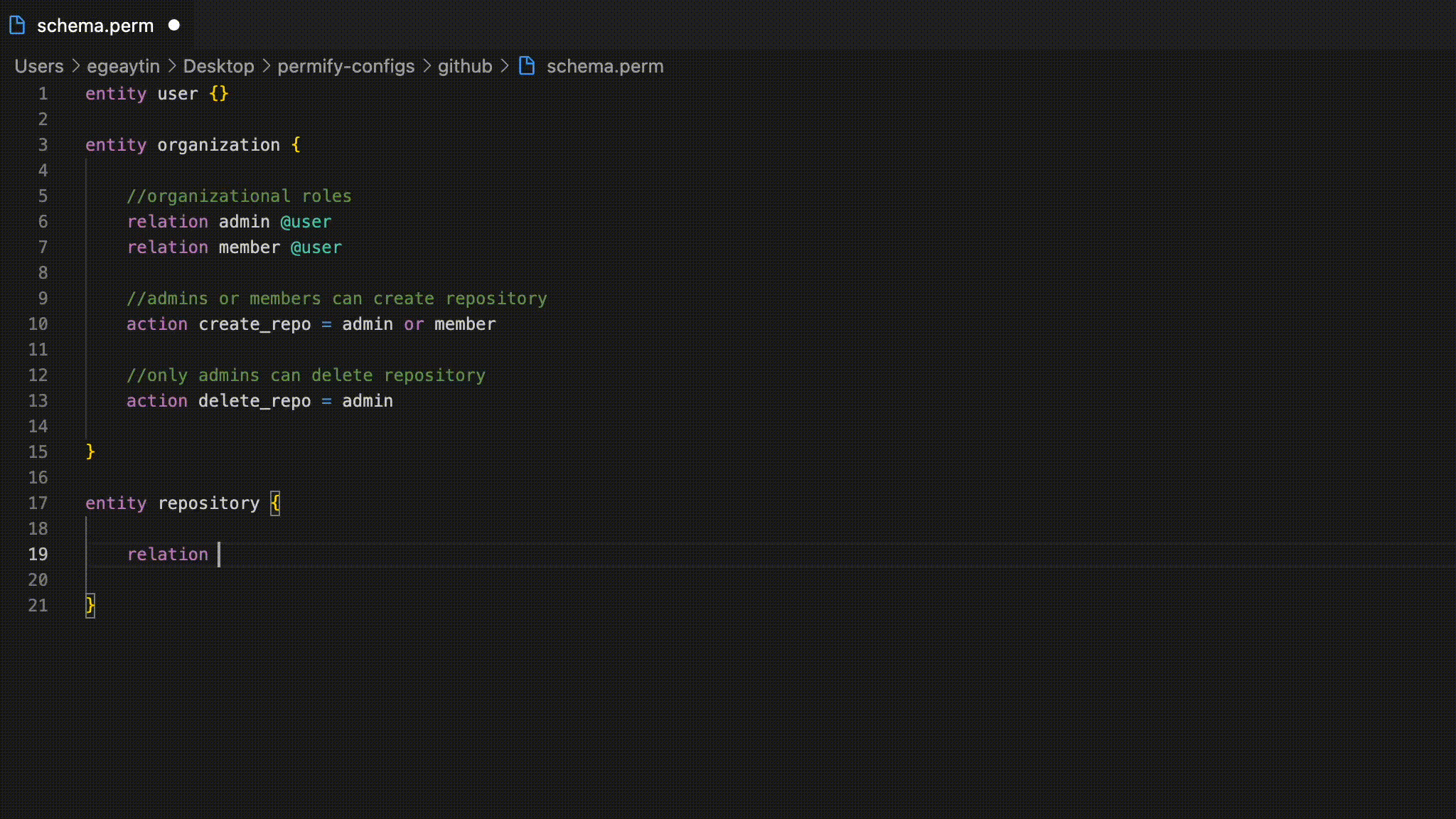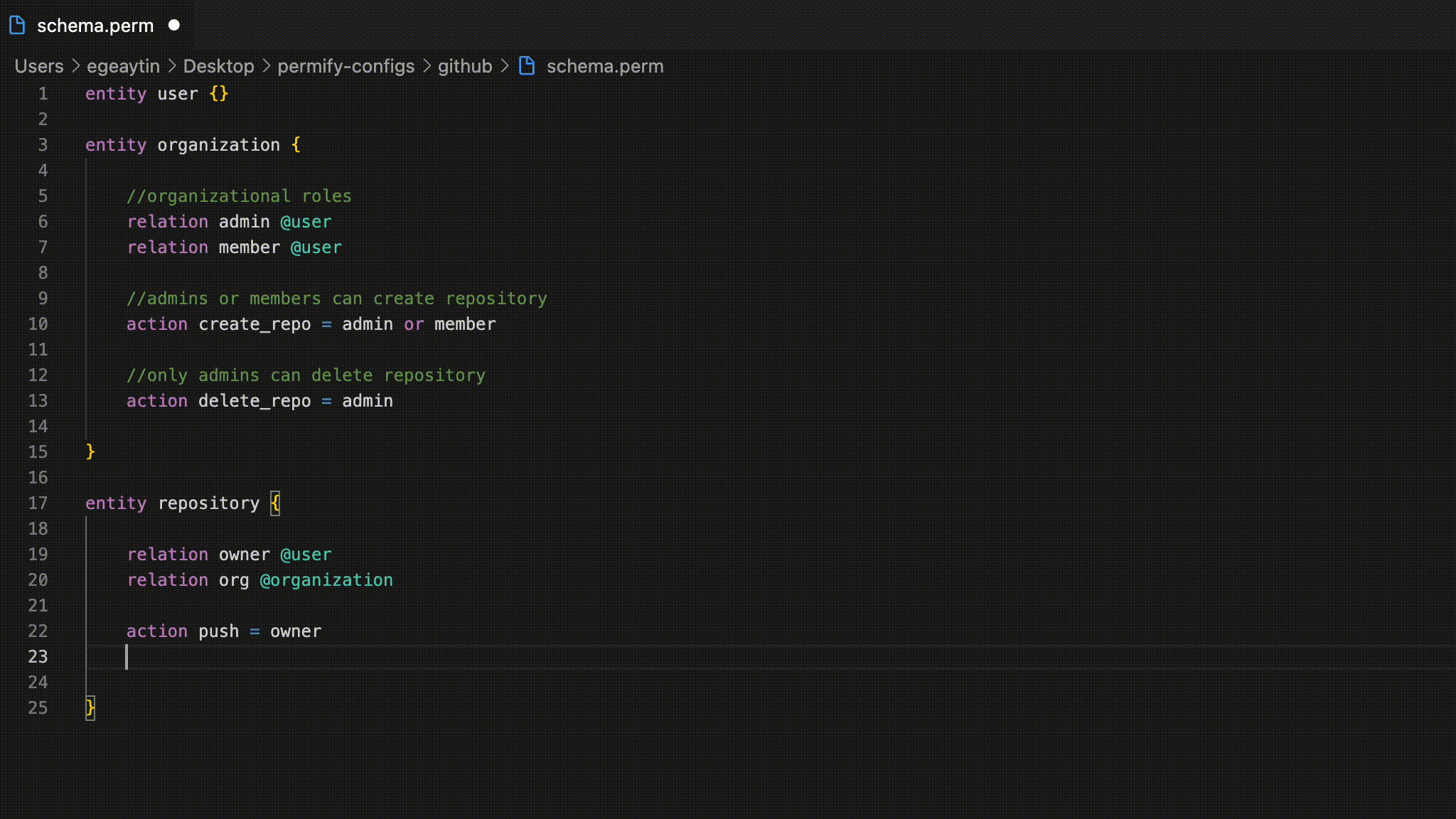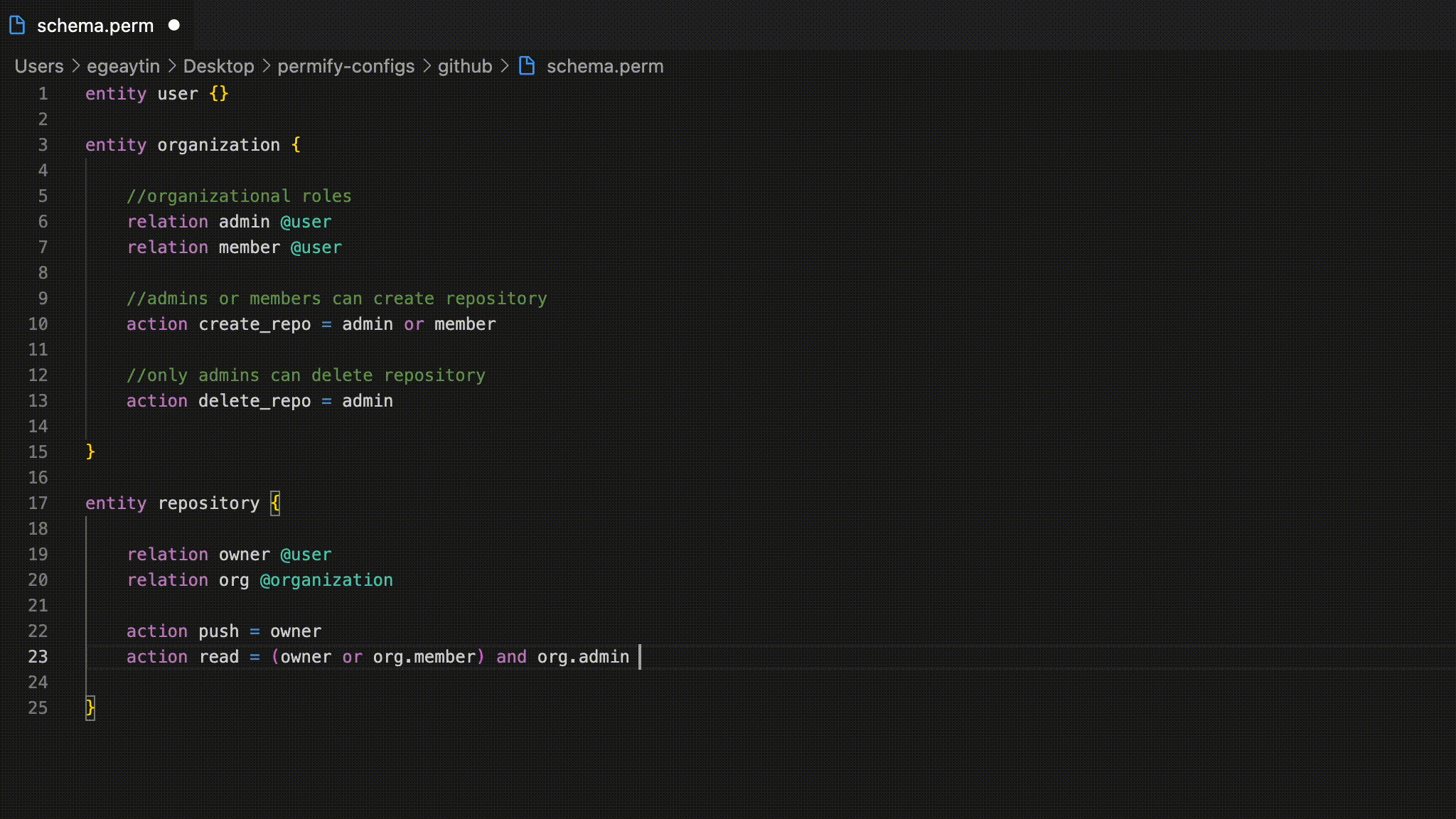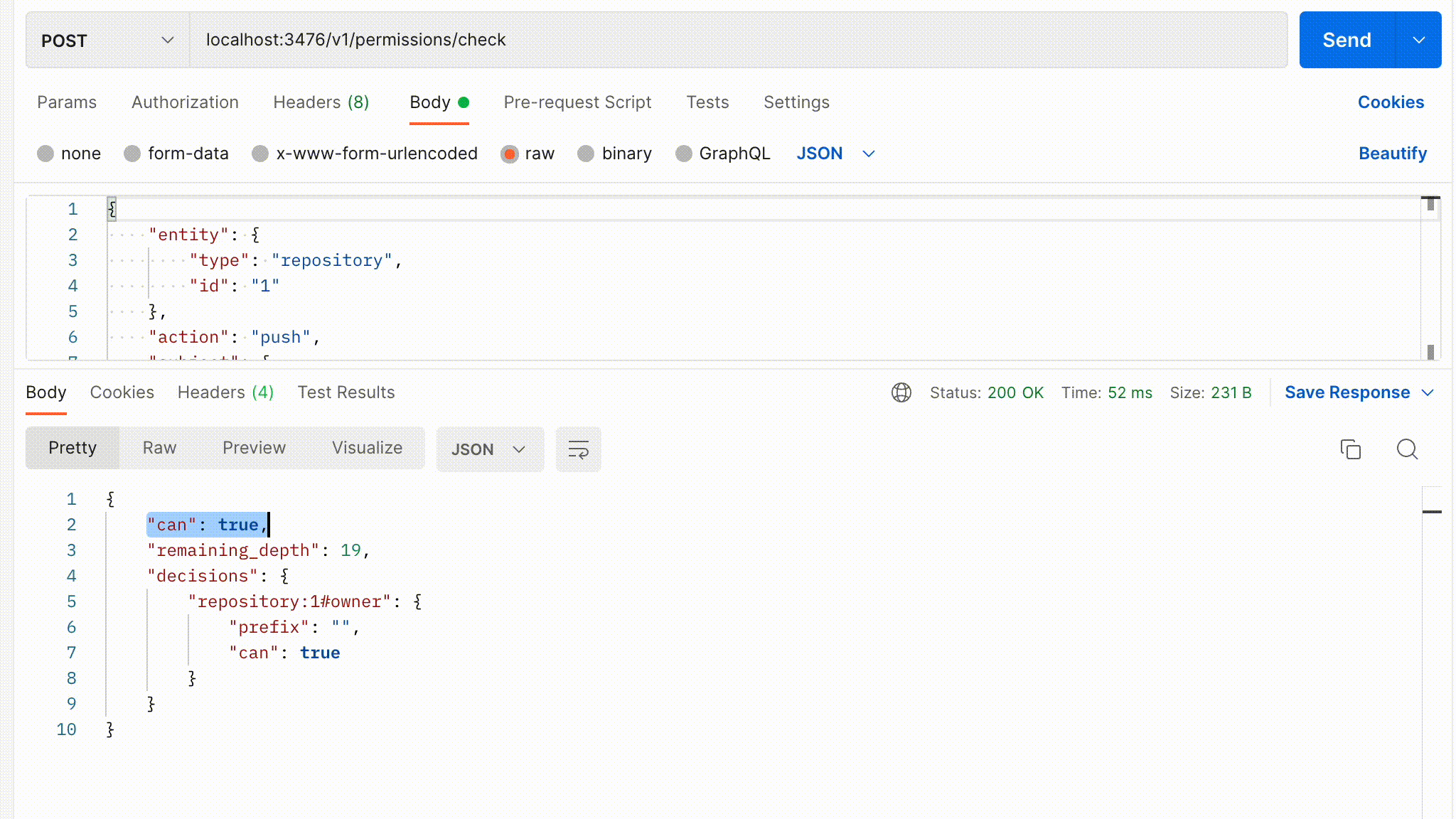
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it, we called it Permify Schema. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like user types such as admin, manager, member, etc.
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. It includes set-algebraic operators such as inter- section and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-Here’s a simple breakdown of our schema.
-
-
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is **_".perm"_**.
-
-## Developing a Schema
-
-This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-
-We'll follow a simplified version of github access control system. To see completed model you can jump directly to [Github Example](#github-example).
-
-:::info
-You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
-
-[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-
-:::
-
-### Entities
-
-The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
-
-Think of entities as tables in your relationship database. We are strongly advice to name entities same as your database table name that its corresponds. In that way you can easily model and reason your authorization as well as eliminating the error possibility.
-
-You can create entities using `entity` keyword. Since we're following example of simplified github access control, lets create some of our entities as follows.
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity team {}
-
-entity repository {}
-```
-
-Entities has 2 different attributes. These are;
-
-- **relations**
-- **actions**
-
-### Relations
-
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions. Keyword **_relation_** need to used to create a entity relation with name and type attributes.
-
-**Relation Attributes:**
-
-- **name:** relation name.
-- **type:** relation type, basically the entity it’s related to (e.g. user, organization, document, etc.)
-
-An example relation takes form of,
-
-```perm
-relation [name] @[type]
-```
-
-Lets turn back to our example and define our relations inside our entities:
-
-#### User Entity
-
-→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
-
-```perm
-entity user {}
-```
-
-#### Organization Entity
-
-→ For the sake of simplicity let's define only 2 user types in an organization, these are administrators and direct members of the organization.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-```
-
-#### Team Entity
-
-→ Let's say teams can belong organizations and can have a member inside of it as follows,
-
-```perm
-entity team {
-
- relation parent @organization
- relation member @user
-
-}
-```
-
-The parent relation is indicating the organization the team belongs to. This way we can achieve **parent-child relationship** inside this entity.
-
-#### Repository Entity
-
-→ Organizations and users can have multiple repositories, so each repository is related with an organization and with users. We can define repository relations as as follows.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-}
-```
-
-The owner relation indicates the creator of the repository, that way we can achieve **ownership** in Permify.
-
-**Defining Multiple Relation Types**
-
-As you can see we have new syntax above,
-
-```perm
- relation maintainer @user @team#member
-```
-
-When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-
-**_Quick note here:_** with using # you can reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
-
-Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances. So, the basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
-
-Permify Schema supports `and`, `or`, `and not` and `or not` operators to define actions. Keyword **_action_** need to used with these operators to form an action.
-
-Lets get back to our github example and create some actions on repository entity,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- ..
- ..
-
- action push = owner
-
-}
-```
-
-→ `action push = owner or maintainer` indicates only the repository owner or maintainers can push to
-repository.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- ..
- ..
-
- action read = (owner or maintainer or org.member) and org.admin
-
-}
-```
-
-→ For more fine grained permission let's examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-
-
-:::info
-You can add actions to another action like relations, see below.
-
-```perm
- action edit = member or manager
- action delete = edit or org.admin
-```
-
-delete action can inherit the edit action rules like above. To sum up, only organization administrators and any relation that can perform edit action (member or manager) can perform delete action.
-
-:::
-
-## Github Example
-
-Here is full implementation of simple Github access control example with using Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
- action edit_team = member or parent.admin
-
-}
-
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- action push = owner or maintainer
- action read = (owner or maintainer or parent.member) and parent.admin
- action delete = parent.admin or owner
-
-}
-```
-
-See more schema examples from the [Example Use Cases](../../use-cases) section with their detailed examination.
diff --git a/docs/versioned_docs/version-0.2.x/getting-started/sync-data.md b/docs/versioned_docs/version-0.2.x/getting-started/sync-data.md
deleted file mode 100644
index 597754dd..00000000
--- a/docs/versioned_docs/version-0.2.x/getting-started/sync-data.md
+++ /dev/null
@@ -1,179 +0,0 @@
----
-sidebar_position: 2
----
-
-# Centralizing Authorization Data
-
-Permify unifies your authorization data in a database you prefer. We named that database as Write Database, shortly **WriteDB**.
-
-Permify API provides various functionalities - checking access, reasoning permissions, etc - to maintain separate access control mechanisms for individual applications. And **WriteDB** stands as a source of truth for these authorization functionalities.
-
-## Access Control as Relations - Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. Each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-In Permify, the simplest form of relational tuple structured as: `entity # relation @ user`. Here are some relational tuples with semantics,
-
-
-
-## Where Relational Tuples Used ?
-
-In Permify, these relational tuples represents your authorization data.
-
-Permify stores your relational tuples (authorization data) in **WriteDB**. You can configure it **WriteDB** when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-Stored relational tuples are queried on access control check requests to decide whether user action is authorized.
-
-As an example; to decide whether a user could view a protected resource, Permify looks up the relations between that specific user and the protected resource. These relation types could be ownership, parent-child relation, or even a role such as an administrator or manager.
-[WriteDB]: #write-database
-
-## Creating Relational Tuples
-
-Relational tuples can be created with an simple API call in runtime, since relations and authorization data's are live instances. Each relational tuple should be created according to its authorization model, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-
-
-Let's follow a real example to see how to create relation tuples. Lets say we have a document management system with the following Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation member @user
-
-}
-
-entity document {
-
- relation owner @user
- relation org @organization
-
- action view = owner or org.member
- action edit = owner
- action delete = owner
-}
-```
-
- According to the schema above; when a user creates a document in an organization, more specifically let's say, when user:1 in organization:2 create a document:4 we need to create the following relational tuple,
-
-- `document:4#owner@user:1`
-
-[WriteDB]: #write-database
-
-### API endpoint
-
-You can create relational tuples by using `/v1/relationships/write` endpoint.
-
-Send a request to POST - `/v1/relationships/write`
-
-**Request**
-
-```json
-{
- "schema_version": "",
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "4"
- },
- "relation": "owner",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- }
- }
- ]
-}
-```
-
-## More Relation Tuple Examples
-
-### Organization Admin
-
-Request
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-**Created relational tuple:** organization:1#admin@1
-
-**Definition:** User 1 has admin role on organization 1.
-
-### Organization Members are Viewer of Repo
-
-Request
-
-```json
-{
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "relation": "viewer",
- "subject": {
- "type": "organization",
- "id": "2",
- "relation": "member"
- }
-}
-```
-
-**Created relational tuple:** repository:1#admin@organization:2#member
-
-**Definition:** Members of organization 2 are viewers of repository 1.
-
-### Parent Organization
-
-Request
-
-```json
-{
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "relation": "parent",
- "subject": {
- "type": "organization",
- "id": "1",
- "relation": "..."
- }
-}
-```
-
-**Relational Tuple:** repository:1#parent@organization:1#…
-
-**Definition:** Organization 1 is parent of repository 1.
-
-:::info
-Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
-:::
-
-## Write Database
-
-But how authorization data stored in WriteDB ? Let's take a look at a snap shot of demo table on example Write Database.
-
-
-
-Each row represents object-user or object-object relations, which we call relational tuples. Each row (tuple) behave as ACL and takes the form of “user U has relation R to object O”
-
-→ Considering table above, semantics of second row (id:8) is **user 1 is owner of repository 1**
-
-Alternatively user U can behave as "set of users".
-More specifically, “set of users S has relation R to object O”, where S is itself specified in terms of another object-relation pair.
-
- → First row in our table (id:7), we can see that **organization 1 (set of users in organization) is parent of repository 1**
-
-:::info
-These relational tuples data form is inspired by Google’s Consistent, Global Authorization System, [Google Zanzibar White Paper](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf)
-:::
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/getting-started/testing.md b/docs/versioned_docs/version-0.2.x/getting-started/testing.md
deleted file mode 100644
index 1d01611a..00000000
--- a/docs/versioned_docs/version-0.2.x/getting-started/testing.md
+++ /dev/null
@@ -1,104 +0,0 @@
----
-sidebar_position: 4
----
-
-# Testing & Validation
-
-Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
-
-Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
-
-We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Usage
-
-### Adding action to your workflow
-
-After adding [permify-validate-action] to your Github Action workflow, you need to define the schema validation yaml file as,
-
-- **With local file:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1"
- with:
- validationFile: "test.yaml"
-```
-
-- **With external url:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1"
- with:
- validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
-```
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-### Creating Schema Validation File
-
-Below you can examine an example schema validation yaml file. It consists 3 parts; `schema` which is your new authorization model, sample `relationships` to test your model and lastly `assertions` which is the test access check questions and expected response - true or false.
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = (admin or member)
- action delete = admin
- }
-
- entity repository {
-
- relation owner @user @organization#member
- relation parent @organization
-
- action push = owner
- action read = (owner and (parent.admin and parent.member))
- action delete = (parent.member and (parent.admin or owner))
- action edit = parent.member and not owner
- }
-
-relationships:
- - "organization:1#admin@user:1"
- - "organization:1#member@user:1"
- - "repository:1#owner@user:1"
- - "repository:2#owner@user:2"
- - "repository:2#owner@user:3"
- - "repository:1#parent@organization:1#..."
- - "organization:1#member@user:43"
- - "repository:1#owner@user:43"
-
-assertions:
- - "can user:1 push repository:1": true
- - "can user:1 push repository:2": false
- - "can user:1 push repository:3": false
- - "can user:43 edit repository:1": false
-```
-
-You can also test your new authorization model in your local (Permify clone) without using [permify-validate-action] at all.
-
-For that open up a new file and add a schema yaml file inside. Then build your project with, run `make run` command and run `./permify validate {path of your schema validation file}`.
-
-If we use the above example schema validation file, after running `./permify validate {path of your schema validation file}` it gives a result on the terminal as:
-
-
-
-[permify-validate-action]: https://github.com/Permify/permify-validate-action
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
-
diff --git a/docs/versioned_docs/version-0.2.x/installation/_category_.json b/docs/versioned_docs/version-0.2.x/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/versioned_docs/version-0.2.x/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.2.x/installation/brew.md b/docs/versioned_docs/version-0.2.x/installation/brew.md
deleted file mode 100644
index 8e81d855..00000000
--- a/docs/versioned_docs/version-0.2.x/installation/brew.md
+++ /dev/null
@@ -1,69 +0,0 @@
----
-title: "Brew (With Conf)"
----
-
-# Brew With Configurations
-
-This section shows how to intall and run Permify Service with using brew.
-
-### Install Permify
-
-Open terminal and run following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-### Run Permify Service
-
-To run the Permify Service, `permify serve` command should be run with configurations.
-
-By default, the service is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather then an actual database. You can override these with running the command with configuration flags. See all configuration options with running `permify serve --help` on terminal.
-
-Check out the [Centralize Authorization Data] section to learn how to organize this config YAML file and get more details about the configuration options.
-
-[Centralize Authorization Data]: ../getting-started/sync-data
-
-### Configuration Flags
-
-| Flag | Description | Default |
-|--------------------------|----------| ----------|
-| --authn-enabled | Enable server authentication | false |
-| --authn-preshared-keys | Preshared key/keys for server authentication. | - |
-| --database-engine | Data source. Permify supports PostgreSQL('postgres') for now. | memory |
-| --database-name | Custom database name | - |
-| --max_open_connections | Max connection pool size | 20 |
-| --database-uri | Uri of your data source to store relation tuples | - |
-| --grpc-port | Port that server run on | 3478 |
-| --grpc-tls-config-cert-path | GRPC tls certificate path | - |
-| --grpc-tls-config-key-path | GRPC tls key path | - |
-| -h or --help | Help for serve | no value |
-| --http-cors-allowed-headers | CORS allowed headers for http gateway | [*] |
-| --http-cors-allowed-origins | CORS allowed origins for http gateway | [*] |
-| --http-enabled | Switch option for HTTP server | true |
-| --http-port | HTTP port address | 3476 |
-| --http-tls-config-cert-path | HTTP tls certificate path | - |
-| --http-tls-config-key-path | HTTP tls key path | - |
-| --log-level | Real time logs of authorization. Permify uses zerolog as a logger | debug|
-| --tracer-enabled | Switch option for tracing | false |
-| --tracer-endpoint | Export uri for tracing data | - |
-| --tracer-exporter | Can be; jaeger, signoz or zipkin. (integrated tracing tools) | - |
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../api-overview/
-
-[](https://god.gw.postman.com/run-collection/16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de?action=collection%2Ffork&collection-url=entityId%3D16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de%26entityType%3Dcollection%26workspaceId%3Dd3a8746c-fa57-49c0-83a5-6fcf25a7fc05)
-[](https://app.swaggerhub.com/apis-docs/permify/permify/latest)
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.2.x/installation/container.md b/docs/versioned_docs/version-0.2.x/installation/container.md
deleted file mode 100644
index 621d67fc..00000000
--- a/docs/versioned_docs/version-0.2.x/installation/container.md
+++ /dev/null
@@ -1,136 +0,0 @@
----
-title: "Container (With Conf)"
----
-
-# Container With Configurations
-
-This section shows how to run Permify Service from a container with configurations. You can run Permify service from a container with following steps.
-
-### Run following line on Terminal
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
-```
-
-This will start an API server with the configuration options that pointed out on the **{YOUR-CONFIG-PATH}**.
-
-This config path - `{YOUR-CONFIG-PATH}:/config` - addresses **config.yaml** file, where you can configure running options of the server as well as define the ***database to store your authorization data***.
-
-By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database. You can override these by creating and and point out a new configuration file when running the command.
-
-Permify designed to be store authorization data in a database you prefer as relation tuples. We called that database **‘writeDB’**. Additional to other configuration options, you can also define (point out) your **‘writeDB’** on the configuration YAML file as well.
-
-### Configuration File
-
-Here is the example configuration YAML file with descriptions below. You can also find this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-
-***Example config.yaml file***
-
-```yaml
-server:
- http:
- enabled: true
- port: 3476
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
- grpc:
- port: 3478
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
-
-logger:
- level: 'debug'
-
-authn:
- enabled: false
- keys: []
-
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://localhost:9411/api/v2/spans'
- enabled: false
-
-meter:
- exporter: 'otlp'
- endpoint: 'localhost:4318'
- enabled: true
-
-service:
- circuit_breaker: false
- concurrency_limit: 100
-
-database:
- engine: 'postgres'
- database: 'db_name'
- uri: 'postgres://user:password@host:5432'
- max_open_connections: 20
-```
-* **server:** Server options to run Permify. (`grpc` and `http` available for now.)
- * **grpc:** example, same configurations for `http` option.
- * **port:** port that server run on.
- * **tls:** transport layer security options.
- * **enabled** switch option for tls, *(default: false)*.
- * **cert** tls certificate path.
- * **key** tls key path.
-
-* **logger**
- * **level:** Real time logs of authorization. Permify uses [zerolog] as a logger.
-
-[zerolog]: https://github.com/rs/zerolog
-
-* **authn**
- * **enabled:** switch option for server authentication, *(default: false)*
- * **keys:** Private key/keys for server authentication. Permify does not provide this key, so it must be generated by the users.
-
-* **tracer** (optional)
- * **exporter:** Permify integrated with [jaeger] , [signoz] and [zipkin] tracing tools. See our [change log] about tracing performance of your authorization.
- * **endpoint:** export uri for tracing data.
- * **enabled:** switch option for tracing. *(default: false)*
-
-* **meter** (optional)
- * **exporter:** [otpl](https://opentelemetry.io/docs/collector/) is default.
- * **endpoint:** export uri to observe metrics; check count, cache check count and session information; Permify version, hostname, os, arch.
- * **enabled:** switch option for meter tracing. *(default: true)*
-
-* **database** : Points out where your want to store your authorization data (relation tuples, audits, decision logs, authorization model )
- * **engine:** Data source. Permify supports **PostgreSQL**(`'postgres'`) for now. Contact with us for your preferred database. *(default: memory)*
- * **database:** Custom database name.
- * **uri:** Uri of your data source.
- * **max_open_connections:** Max connection pool size, *(default: 20)*
-
-[jaeger]: https://www.jaegertracing.io/
-[zipkin]: https://zipkin.io/
-[signoz]: https://signoz.io/
-[change log]: https://permify.co/changelog/
-
-### Configure With Using Flags
-
-Alternatively, you can set configuration options with the respected flags when running the command. See all configuration flags with running,
-
-```shell
-docker run -p 8080:8080 ghcr.io/permify/permify serve -help
-```
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview
-
-[](https://god.gw.postman.com/run-collection/16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de?action=collection%2Ffork&collection-url=entityId%3D16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de%26entityType%3Dcollection%26workspaceId%3Dd3a8746c-fa57-49c0-83a5-6fcf25a7fc05)
-[](https://app.swaggerhub.com/apis-docs/permify/permify/latest)
-
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.2.x/installation/overview.md b/docs/versioned_docs/version-0.2.x/installation/overview.md
deleted file mode 100644
index 194c1247..00000000
--- a/docs/versioned_docs/version-0.2.x/installation/overview.md
+++ /dev/null
@@ -1,266 +0,0 @@
----
-sidebar_position: 1
----
-
-# Guide
-
-Permify is an open-source authorization service that you can run in your environment and works as an API. This guide shows how to set up Permify in your servers and use it accross your applications. Set up and implementation consists of 4 steps,
-
-1. [Set Up & Run Permify Service](#run-permify-api)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Migrate and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
-4. [Perform Access Check](#perform-access-check)
-
-:::info Talk to an Permify Engineer
-Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-## Set Up Permify Service
-
-You can run Permify Service with two options:
-
-- [Run From Container](#run-from-container)
-- [Install With Brew](#install-with-brew).
-
-### Run From Container
-
-Installation needs some configuration such as defining running options, selecting datastore to store authorization data and more.
-
-However, If you want to play around with Permify without doing any configurations, you can quickly start Permify on your local with running the command below:
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-See [Container With Configurations] section to get more details about the configuration options and learn the full integration to run Permify Service from container.
-
-[Container With Configurations]: ../container
-
-### Install With Brew
-
-Firstly, open terminal and run following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-After the brew installation, the `serve` command should be used to run Permify. However, if you want to start Permify without doing any configurations, you can run the command without config flags as follows:
-
-```shell
-permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-You can override these configurations with running the command with configuration flags. See all configuration options with running `permify serve --help` on terminal.
-
-Check out the [Brew With Configurations] section to learn full implementation with configurations.
-
-[Brew With Configurations]: ../brew
-
-### Test your connection
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview
-
-[](https://god.gw.postman.com/run-collection/16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de?action=collection%2Ffork&collection-url=entityId%3D16122080-54b1e316-8105-4440-b5bf-f27a05a8b4de%26entityType%3Dcollection%26workspaceId%3Dd3a8746c-fa57-49c0-83a5-6fcf25a7fc05)
-[](https://app.swaggerhub.com/apis-docs/permify/permify/latest)
-
-
-## Model your Authorization with Permify Schema
-
-After installation completed and Permify server is running, next step is modeling authorization with Permify's authorization language - [Permify Schema]- and condigure it to Permify API.
-
-You can define your entities, relations between them and access control decisions of each actions with using [Permify Schema].
-
-### Creating your authorization model
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-
-:::
-
-Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action view_files = admin or member
- action edit_files = admin
-
-}
-```
-
-We have 2 entities these are **"user"** and **"organization"**. Entities represents your main tables. We strongly advise naming entities the same as your original database entities.
-
-Lets roll back our example,
-
-- The `user` entity represents users. This entity is empty because it's only responsible for referencing users.
-
-- The `organization` entity has its own relations (`admin` and `member`) which related with user entity. This entity also has 2 actions, respectively:
- - Organization member and admin can view files.
- - Only admins can edit files.
-
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
-
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../example-use-cases/simple-rbac
-:::
-
-### Configuring Permify Schema to API
-
-After modeling completed, you need to send Permify Schema - authorization model - to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-#### Path : ** POST "/v1/schemas/write"**
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | schema | string | - | Permify Schema as string|
-
-**Example Request on Postman:**
-
-
-
-## Store Authorization Data as Relational Tuples
-
-After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action. Permify stores your authorization data in a database you prefer. We called that database as WriteDB, and you can configure it when running Permify Service.
-
-:::info
-If your Permify Service running default configurations, authorization data will be stored in memory.
-:::
-
-If you set up Permify Service from container you can both configure WriteDB with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) and configuration flags. On the other hand, If you're using brew to install and run Permify you can only use the configuration flags.
-
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules at this writeDB by using `/v1/relationships/write` endpoint.
-
-For our guide let's grant one of the team members (Ashley) an admin role.
-
-**Request:** POST - `/v1/relationships/write`
-
-```json
-{
- "schema_version": "",
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1" //Organization identifier
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1", //Ashley's identifier
- "relation": ""
- }
- }
- ]
-}
-```
-
-**Created relational tuple:** organization:1#admin@1
-
-**Semantics:** User 1 (Ashley) has admin role on organization 1.
-
-:::info
-You can find more detailed explanation from [Move & Synchronize Authorization Data] section.
-
-[Move & Synchronize Authorization Data]: ../../getting-started/sync-data
-:::
-
-### Performing Access Control Check
-
-You can check authorization with
-single API call. This check request returns a decision about whether user can perform an action on a certain resource.
-
-Access decisions generated according to relational tuples, which stored in your database (writeDB) and [Permify Schema] action conditions.
-
-[Permify Schema]: ../getting-started/modeling
-
-## Perform Access Check
-
-Finally we're ready to control authorization. Lets perform an example access check via [check] API.
-
-[check]: ../../api-overview/check-api
-
-***Can the user 45 view files on organization 1 ?***
-
-### Path:
-
-POST /v1/permissions/check
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | entity | object | - | name and id of the entity. Example: organization:1”.
-| [x] | action | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action |
-| [ ] | schema_version | string | - | get results according to given schema version|
-| [ ] | depth | integer | 8 | |
-
-### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_files",
- "subject": {
- "type": "user",
- "id": "45",
- "relation": ""
- },
-}
-```
-
-### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "metadata": {
- "check_count": 0
- }
-}
-```
-
-See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-
-[Access Control Check]: ../../getting-started/enforcement
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you struggle with installation or have any questions, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/permify-overview/_category_.json b/docs/versioned_docs/version-0.2.x/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/versioned_docs/version-0.2.x/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.2.x/permify-overview/authorization-service.md b/docs/versioned_docs/version-0.2.x/permify-overview/authorization-service.md
deleted file mode 100644
index 0810c6c2..00000000
--- a/docs/versioned_docs/version-0.2.x/permify-overview/authorization-service.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# What is Authorization Service?
-
-Authorization is an important part of software development. There are many different ways to implement authorization, but it's important for all apps to have some form of it in order to protect the user from malicious actors and unauthorized access attempts.
-
-An authorization service is a module that allows you to manage access to your application and ease the development and maintenance of your authorization system. It works in run time and respond to all authorization questions from any of your apps.
-
-
-
-[Permify] is a fully open source authorization service that offers a variety of binding and crafting options to secure your applications.
-
-[Permify]: https://github.com/Permify/permify
-
-## Why should I use Authorization Service instead of doing from scratch?
-
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch. You can started quickly with a simple API that you can easily integrate into your application to move and iterate faster.
-
-### Do Not Reinvent The Wheel
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps. Building a scalable and robust authorization system is hard and needs a quite engineering time. Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period. Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services.
-
-[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-
-### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group. Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time. Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
-
-### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road. Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product. Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production. After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
-
-### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security. Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
-
-## Cases that can benefit from An Authorization Service:
-
-- If you already have an identity/auth solution and want to plug in fine-grained authorization on top of that.
-- If you want to create a unified access control mechanism to use across your individual applications.
-- If you want to make future-proof authorization system and don't want to spend engineering effort for it.
-- If you’re managing authorization for growing micro-service infrastructure.
-- If your authorization logic is cluttering your code base.
-- If your data model is getting too complicated to handle your authorization within the service.
-- If your authorization is growing too complex to handle within code or API gateway.
-
diff --git a/docs/versioned_docs/version-0.2.x/permify-overview/infrastructure.md b/docs/versioned_docs/version-0.2.x/permify-overview/infrastructure.md
deleted file mode 100644
index 9cc9733c..00000000
--- a/docs/versioned_docs/version-0.2.x/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,50 +0,0 @@
-
-# Where does Permify fit into your environment?
-
-Permify is a simply GRPC service that responsible for managing and authorization in your environment. This section shows where and how does Permify fit into your environment with examining Permify's architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## Architecture
-
-Permify stores access control relations on a database you choose and performs authorization checks based on the stored relations. We called that database Write Database - **WriteDB** - and it behaves as a centralized data source for your authorization system.
-
-You can model your authorization with Permify's DSL - Permify Schema and your applications can talk to Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data, or make changes to data stored in WriteDb.
-
-
-
-### Permify with Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization. Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications. See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important. As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/versioned_docs/version-0.2.x/permify-overview/intro.md b/docs/versioned_docs/version-0.2.x/permify-overview/intro.md
deleted file mode 100644
index 3b889d41..00000000
--- a/docs/versioned_docs/version-0.2.x/permify-overview/intro.md
+++ /dev/null
@@ -1,101 +0,0 @@
----
-sidebar_position: 1
-slug: /
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is an **open-source authorization service** for creating and maintaining fine-grained authorizations in your applications.
-
-With Permify you can easily structure your authorization model, store authorization data in your own servers securely, and interact with Permify API to handle all authorization questions from any of your applications.
-
-Permify's data model is inspired by Google’s consistent, global authorization system, [Google Zanzibar Paper](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-## Key Features
-
-⚙️ **Production ready** authorization API that serve as **gRPC** and **REST**
-
-🔮 Domain Specific Authorization Language - Permify Schema - to **easily model** your authorization
-
-🔐 Database Configuration to store your permissions **in house** with **high availability**
-
-✅ Ask authorization questions and get answers **down to 10ms** with **parallel graph engine**
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf)
-
-📝 **Audit & Reason** your access control hassle-free with various functionalities via API
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin]
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Getting Started
-
-In Permify, authorization divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify [Store Authorization Data] as relations.
-- Perform an [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../getting-started/modeling
-[Store Authorization Data]: ../getting-started/sync-data
-[Access Checks]: ../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want trying out and examine it instantly,
-
-
-
-## Community & Support
-
-We love to talk about authorization also we would love to hear from you :heart:
-
-You can get immediate help on our [Discord](https://discord.gg/n6KfzYxhPp) channel. This can be any kind of questions related to Permify, authorization, or even from authentication or identity access control. We'd love to discuss anything related with access control space.
-
-For feature requests, bugs or any improvements you can always open an [issue] on Github. If you like Permify, please consider giving us a :star:️ on [Github](https://github.com/Permify/permify)
-
-[issue]: https://github.com/Permify/permify/issues
-
-
-
-## Need any help on Authorization ?
-
-Our team is happy to help you anything about authorization. Moreover, if you'd like to learn more about using Permify in your app or have any questions, [schedule a call with one of our founders](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/playground.md b/docs/versioned_docs/version-0.2.x/playground.md
deleted file mode 100644
index 00947b27..00000000
--- a/docs/versioned_docs/version-0.2.x/playground.md
+++ /dev/null
@@ -1,74 +0,0 @@
----
-sidebar_position: 6
----
-
-# Using Permify Playground
-
-You can use our [Playground] to create and test your authorization in a browser. Our playground consists 4 sections; Authorization Model, Visualizer, Authorization Data and Enforcement. Let's examine these sections by following a simple example.
-
-[Playground]: https://play.permify.co/
-
-## Authorization Model
-
-You can create your authorization model in this section with using Permify authorization language, Permify Schema. You can define your entities, relations between them and access control decisions with using Permify Schema. We already have a couple of use cases and example that you can choose to see how authorization can be structured with Permify Schema. Also, you can check our docs to learn more about how to model authorization in Permify.
-
-To demonstrate how playground works, let's choose the "empty" option from our dropdown to create a simple authorization model as follows:
-
-
-
-We have 2 permissions these are editing repository and deleting repository. Repository has parent child relation with organizations. Lastly organizations can have organizational wide roles such as admin and member. After completing your authorization model you can just save it with hitting the save button and start testing it.
-
-## Visualizer
-
-We get loads of feedback about the observability and reasonability of the authorization model across teams and colleagues. So we put a simple visualizer that shows how your authorization structure looks at a high level. In particular, you can examine relations between entities and their permissions. Here is a visualization for example model that we created above.
-
-
-
-## Authorization Data
-
-You can create sample authorization data to test your authorization logic. In Permify, authorization data stored as relation tuples and these tuples stored in a database that you preferred. The basic relation tuple takes the form of:
-
-`entity # relation @ user`
-
-So the entity can be any entity that you defined in your model. If we look up our example it can be an organization or repository (since the user is empty). The relation can be one of the defined relations in the selected entity. Lastly, the user is basically the user or user set in our system. Let's say we want make user 1 admin in organization 1 then we need to create an example relational tuple according to our model as follows:
-
-`organization:1#admin@user:1`
-
-To create a relation tuple in playground just hit the "new" button and a pop up will open.
-
-
-
-You can choose entity, relation and the subject (user or user set) with entering identifier to create sample data. Let's create the relation tuple `organization:1#admin@user:1` as follows.
-
-
-
-And this created tuple shown in the Authorization Data section as follows.
-
-
-
-Let's add one more relation tuple to perform a sample access check. I want to add repository:1 into organization:1 as follows:
-
-
-
-Created relational tuple after this will be: "repository:1#parent@organization:1#..." We used “...” when subject type is different from user entity. #… represents a relation that does not affect the semantics of the tuple.
-
-## Enforcement ( Access Checks)
-Finally as we have a sample data lets perform an access check from the right below. Let's check whether user:1 can edit the repository:1. Since organization:1 is parent of repository:1 ( `repository:1#parent@organization:1#...` ) and user:1 has an admin role in organization:1 ( `organization:1#admin@user:1` ) user:1 should allow to edit the repository:1 because the we define rule of the edit permission action as:
-
-`action edit = owner or parent.admin`
-
-which parent.admin indicates admin in the organization that repository belongs to. So let's type **"can user:1 edit repository:1"** and hit the check button to get result.
-
-
-
-
-Let's try to get unauthorized result. Type "can user:1 delete repository:1" on the question input. Since only owners can delete the repository this access check will result as unauthorized.
-
-
-
-As we seen above this is how you can model your authorization and test it with sample data in Permify Playground. Check out our docs for different modeling use cases, creating and storing relational tuples and more.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.2.x/reference/_category_.json b/docs/versioned_docs/version-0.2.x/reference/_category_.json
deleted file mode 100644
index b55d99d8..00000000
--- a/docs/versioned_docs/version-0.2.x/reference/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Reference",
- "position": 8,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.2.x/reference/glossary.md b/docs/versioned_docs/version-0.2.x/reference/glossary.md
deleted file mode 100644
index 58c57b51..00000000
--- a/docs/versioned_docs/version-0.2.x/reference/glossary.md
+++ /dev/null
@@ -1,45 +0,0 @@
----
-sidebar_position: 1
----
-
-# Glossary
-
-This section explains the basic concepts that commonly mentioned in Permify, as well as in this document. You can find the whole context on right menu.
-
-## Google Zanzibar (or just Zanzibar)
-
-[Google Zanzibar] is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
-
-Google published Zanzibar back in 2019, and in a short time it gained attention quickly. In fact some big tech companies started to shift their legacy authorization structure to Zanzibar style systems. Additionaly, Zanzibar based solutions increased over the time. All disclosure; [Permify] is an authorization system based on Zanzibar.
-
-For more about Zanzibar check our blog post, [Google Zanzibar In A Nutshell]
-
-[Google Zanzibar In A Nutshell]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-[Google Zanzibar]: https://research.google/pubs/pub48190/
-[Permify]: https://permify.co/
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it, we called it Permify Schema. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager etc. You can define your entities, relations between them and access control decisions with using Permify Schema.
-
-It includes set-algebraic operators such as inter- section and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-## Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. The simplest form of relational tuple structured as `entity # relation @ user` and each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-## Write Database - WriteDB
-
-Permify stores your relational tuples (authorization data) in **WriteDB**. You can configure it **WriteDB** when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-## Relationship Based Access Control (ReBAC)
-
-ReBAC is an access control model that defines permissions based on the relationships between entities and subjects of your system. Although ReBAC is best known for social networks because its core concept is about the network of relations, it can be applied beyond that.
-
-Check out [Relationship Based Access Control Models](https://permify.co/post/relationship-based-access-control-rebac/) post learn more about ReBAC and its common usage.
-
-## Domain Specific Language (DSL)
-
-Domain Specific Language is a language that specialized to a particular application domain. Permify has its DSL basically an authorization language which you can model and structure your authorization with it. We called it Permify Schema.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/reference/snap-tokens.md b/docs/versioned_docs/version-0.2.x/reference/snap-tokens.md
deleted file mode 100644
index d9d734f5..00000000
--- a/docs/versioned_docs/version-0.2.x/reference/snap-tokens.md
+++ /dev/null
@@ -1,50 +0,0 @@
-
-# Snap Tokens & Zookies
-
-A Snap Token is a token that consists of an encoded timestamp, which is used to ensure fresh results in access control checks.
-
-## Why you should use Snap Tokens ?
-
-Basically, you should use snap tokens both for consistency and performance. The main goal of Permify is to provide an authorization system that ensures excellent performance that can handle millions of requests from different environments while ensuring data consistency.
-
-Performance standards can be achievable with caching. In Permify, the cache mechanism eliminates re-computing of access control checks that once occurred, unless any relationships of resources don't change.
-
-Still, all caches suffer from the risk of becoming stale. If some schema update happens, or relations change then all of the caches should be updated according to it to prevent false positive or false negative results.
-
-Permify avoids this problem with an approach of snapshot reads. Simply, it ensures that access control is evaluated at a consistent point in time to prevent inconsistency.
-
-To achieve this, we developed tokens called Snap Tokens that consist of a timestamp that is compared in access checks to ensure that the snapshot of the access control is at least as fresh as the resource timestamp - basically its stored snap token.
-
-## How to use Snap Tokens
-
-Snap Tokens used in endpoints to represent the snapshot and get fresh results of the API's. It mainly used in [Write API] and [Check API].
-
-The general workflow for using snap token is getting the snap token from the reponse of Write API request - basically when writing a relational tuple - then mapped it with the resource. One way of doing that is storing snap token in the additioanl column in your relational database.
-
-Then this snap token can be used in endpoints. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-```json
-{
- "schema_version": "ce8siqtmmud16etrelag",
- "snap_token": "gp/twGSvLBc=",
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- },
-}
-```
-
-[Write API]: ../../api-overview/write-relationships
-[Check API]: ../../api-overview/check-api
-
-#### All endpoints that used snap token
-
-- [Write API](../../api-overview/write-relationships)
-- [Check API](../../api-overview/check-api)
-- [Expand API](../../api-overview/expand-api)
-- [Schema Lookup](../../api-overview/schema-lookup)
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.2.x/reference/tracing.md b/docs/versioned_docs/version-0.2.x/reference/tracing.md
deleted file mode 100644
index 9f6a3193..00000000
--- a/docs/versioned_docs/version-0.2.x/reference/tracing.md
+++ /dev/null
@@ -1,52 +0,0 @@
-
-# Tracing Tools
-
-Permify has integrations with some of popular tracing tools to analyze performance and behavior of your authorization. These are:
-
-- [Jaeger](https://www.jaegertracing.io/)
-- [Signoz](https://signoz.io/)
-- [Zipkin](https://zipkin.io/)
-
-## Usage
-
-### Set Up
-
-Adding one of these tracing tools to your authorization system is quite simple, you just need to define it in the Permify configuration file as **tracer**.
-
-```yaml
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-```
-- ***exporter***: enter the tool name that you want to use. `jaeger` , `signoz` and `zipkin`.
-- ***endpoint***: export url for tracing data.
-- ***disabled***: switch option for tracing.
-
-**Example YAML configuration file**
-
-```yaml
-app:
- name: ‘permify’
-http:
- port: 3476
-logger:
- log_level: ‘debug’
- rollbar_env: ‘permify’
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-database:
- write:
- connection: 'postgres'
- database: 'morf-health-demo'
- uri: 'postgres://postgres:SphU4Uf3QXNntT@permify.us-east-1.rds.amazonaws.com:5432'
- pool_max: 2
-```
-
-After running Permify in your server, you should run Zipkin as well. If you're using docker here is the docker pull request for Zipkin:
-
-```
-docker run -d -p 9411:9411 openzipkin/zipkin
-```
diff --git a/docs/versioned_docs/version-0.3.x/api-overview.md b/docs/versioned_docs/version-0.3.x/api-overview.md
deleted file mode 100644
index af2094da..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview.md
+++ /dev/null
@@ -1,52 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Overview
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 3 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [RelationshipService]: Authorization data operations such as creating, deleting and reading relational tuples.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ./permission
-[RelationshipService]: ./relationship
-[SchemaService]: ./schema
-[TenancyService]: ./tenancy
-
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](./api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Relationships](./api-overview/relationship/write-relationships.md)
-- Read relation tuples and filter them with [Read API](./api-overview/relationship/read-api.md)
-- Check access with [Check API](./api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](./api-overview/permission/lookup-entity.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/relationship/delete-relationships.md)
-- Expand schema actions with [Expand API](./api-overview/permission/expand-api.md)
-- Get permissions of your resources with [Schema Lookup](./api-overview/permission/schema-lookup.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/_category_.json b/docs/versioned_docs/version-0.3.x/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/permission/_category_.json b/docs/versioned_docs/version-0.3.x/api-overview/permission/_category_.json
deleted file mode 100644
index f91d5b46..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/permission/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Permission Service",
- "position": 3,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/permission/check-api.md b/docs/versioned_docs/version-0.3.x/api-overview/permission/check-api.md
deleted file mode 100644
index fff42fdb..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/permission/check-api.md
+++ /dev/null
@@ -1,130 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
-
-In Permify, you can perform two different types access checks,
-
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **subject based** authorization checks, in form of `Which resources can user U edit ?`
-
-In this section we'll look at the resource based check request of Permify. You can find subject based access checks in [Check Entities' Permissions] section.
-
-[Check Entities' Permissions]: ../lookup-entity
-
-## Request
-
-**Path:** POST /v1/permissions/check
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop|
-
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "remaining_depth": 0
-}
-```
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism. See how [access decisions evaluated] in Permify.
-
-[access decisions evaluated]: ../../../getting-started/enforcement#how-access-decisions-evaluated
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/permission/expand-api.md b/docs/versioned_docs/version-0.3.x/api-overview/permission/expand-api.md
deleted file mode 100644
index df568adb..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/permission/expand-api.md
+++ /dev/null
@@ -1,329 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-
-Retrieve all subjects (users and user sets) that have a relationship with given entity and permission
-
-Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
-
-:::caution When To Use ?
-Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
-
-It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
-:::
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), & v1.PermissionExpandRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionExpandRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "",
- "snap_token": ""
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "push"
-}'
-```
-
-
-
-## Example Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:** POST /v1/tenants/{tenant_id}/permissions/expand
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”.
-| [x] | action | string | - | The action the user wants to perform on the resource |
-
-### Expand Push Action
-
-Request
-
-
-
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/permission/lookup-entity.md b/docs/versioned_docs/version-0.3.x/api-overview/permission/lookup-entity.md
deleted file mode 100644
index 33ed99a8..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/permission/lookup-entity.md
+++ /dev/null
@@ -1,178 +0,0 @@
----
-title: Check Entities' Permissions
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Entities' Permissions (Data Filtering)
-
-Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So, we provide 2 separate endpoints for data filtering check request,
-
-- [/v1/permissions/lookup-entity](#lookup-entity)
-- [/v1/permissions/lookup-entity-stream](#lookup-entity-streaming)
-
-## Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
-
-**POST** /v1/permissions/lookup-entity
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- EntityType: "document",
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupEntity({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity_type: "document",
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response.entity_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type":"user",
- "id":"1"
- }
-}'
-```
-
-
-
-### Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-**POST** /v1/permissions/lookup-entity-stream
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”.
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-
-
-
-
-```go
-str, err: = client.Permission.LookupEntityStream(context.Background(), & v1.PermissionLookupEntityRequest {
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: "",
- SchemaVersion: ""
- Depth: 50,
- },
- EntityType: "document",
- Permission: "view",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-
-// handle stream response
-for {
- res, err: = str.Recv()
-
- if err == io.EOF {
- break
- }
-
- // res.EntityId
-}
-```
-
-
-
-
-```javascript
-const permify = require("@permify/permify-node");
-const {PermissionLookupEntityStreamResponse} = require("@permify/permify-node/dist/src/grpc/generated/base/v1/service");
-
-function main() {
- const client = new permify.grpc.newClient({
- endpoint: "localhost:3478",
- })
-
- let res = client.permission.lookupEntityStream({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entityType: "document",
- permission: "view",
- subject: {
- type: "user",
- id: "1"
- }
- })
-
- handle(res)
-}
-
-async function handle(res: AsyncIterable) {
- for await (const response of res) {
- // response.entityId
- }
-}
-```
-
-
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/permission/schema-lookup.md b/docs/versioned_docs/version-0.3.x/api-overview/permission/schema-lookup.md
deleted file mode 100644
index 5d660117..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/permission/schema-lookup.md
+++ /dev/null
@@ -1,95 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Schema Lookup
-
-You can use schema lookup API endpoint to retrieve all permissions associated with a resource relation. Basically, you can perform enforcement without checking stored authorization data. For example in given a Permify Schema like:
-
-```
-entity user {}
-
-entity document {
-
- relation assignee @user
- relation manager @user
-
- action view = assignee or manager
- action edit = manager
-
-}
-
-```
-
-Let's say you have a user X with a manager role. If you want to check what user X can do on a documents ? You can use the schema lookup endpoint as follows,
-
-## Request
-
-**Path:** POST /v1/permissions/lookup-schema
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [x] | entity_type | string | - | type of the entity.
-| [x] | relation_names | string[] | - | string array that holds entity relations |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSchema(context.Background(), & v1.PermissionLookupSchemaRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupSchemaRequestMetadata {
- SchemaVersion: ""
- },
- EntityType: "document",
- RelationNames: []string {"manager"},
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupSchema({
- tenantId: "t1",
- metadata: {
- schema_version: ""
- },
- entity_type: "document",
- relation_names: [ "manager" ]
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-schema' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "entity_type": "document",
- "relation_names": [ "manager" ]
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "data": {
- "action_names": [
- "view",
- "edit"
- ]
- }
-}
-```
-
-
-The response will return all the possible actions that manager can perform on documents. Also you can extend relation lookup as much as you want by adding relations to the **"relation_names"** array.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/relationship/_category_.json b/docs/versioned_docs/version-0.3.x/api-overview/relationship/_category_.json
deleted file mode 100644
index bca5fd5e..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/relationship/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Relationship Service",
- "position": 2,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/relationship/delete-relationships.md b/docs/versioned_docs/version-0.3.x/api-overview/relationship/delete-relationships.md
deleted file mode 100644
index d63b7e68..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/relationship/delete-relationships.md
+++ /dev/null
@@ -1,103 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Relational Tuples
-
-You can delete any stored relation tuples with following API
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/relationships/delete
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Relationship.Delete(context.Background(), & v1.RelationshipDeleteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipDeleteRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.delete({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "filter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/relationship/read-api.md b/docs/versioned_docs/version-0.3.x/api-overview/relationship/read-api.md
deleted file mode 100644
index eb70b30c..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/relationship/read-api.md
+++ /dev/null
@@ -1,103 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id/relationships/read
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Relationship.Read(context.Background(), & v1.RelationshipReadRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.read({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/relationship/write-relationships.md b/docs/versioned_docs/version-0.3.x/api-overview/relationship/write-relationships.md
deleted file mode 100644
index 0646ff4e..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/relationship/write-relationships.md
+++ /dev/null
@@ -1,196 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Relationships
-
-In Permify, relations between your entities, objects and users stored as [relational tuples] in [writeDB]. Since relations and authorization data's are live instances these relational tuples can be created with an simple API call in runtime.
-
-When using Permify, the application client should update writeDB about the changes happening in entities or resources that are related to the authorization structure. If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [writeDB] up-to-date. Besides, each relational tuple should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as relation tuples and store in [writeDB].
-
-
-
-[relational tuples]: ../../../getting-started/sync-data
-[writeDB]: ../../../getting-started/sync-data#where-relational-tuples-used
-
-## Request
-
-So if user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` must be created by using **/v1/relationships/write** endpoint.
-
-**Path:** POST /v1/tenants/{tenant_id}/relationships/write
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "admin",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../../reference/snap-tokens) and how its avoiding stale cache.
-
-## Suggested Workflow
-
-The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-
-### Two Phase Commit Approach
-In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
-
-To give more concurrent example of this action, let's take a look at below createDocument function
-
-```go
-func CreateDocuments(db *gorm.DB) error {
-
- tx := db.Begin()
- defer func() {
- if r := recover(); r != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- }
- }()
-
- if err := tx.Error; err != nil {
- return err
- }
-
- if err := tx.Create(docs).Error; err != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- return err
- }
-
- // if transaction successful, write relation tuple to Permify
- permify.WriteRelationships(...)
-
- return tx.Commit().Error
-}
-```
-The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-
-### Relationships that not stored in application database
-
-Although ownership generally stored in application databases, there are some relations that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
-
-For example, you can model a simple project management authorization in Permify as follows,
-
-```perm
-entity user {}
-
-entity team {
-
- relation owner @user
- relation member @user
-}
-
-entity project {
-
- relation team @team
- relation owner @user
-
- action view = team.member or team.owner or project.owner
- action edit = project.owner or team.owner
- action delete = project.owner or team.owner
-
-}
-```
-
-This **team member** relation won't need to be stored in the application database. Storing it only in Permify - WriteDB - is enough. In that situation, `WriteRelationships` can be performed in any logical place in your stack.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/schema/_category_.json b/docs/versioned_docs/version-0.3.x/api-overview/schema/_category_.json
deleted file mode 100644
index 8fd1e959..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/schema/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Schema Service",
- "position": 1,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/schema/write-schema.md b/docs/versioned_docs/version-0.3.x/api-overview/schema/write-schema.md
deleted file mode 100644
index 47a0e1ff..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/schema/write-schema.md
+++ /dev/null
@@ -1,93 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
-
-Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
-
-We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-:::
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-## Request
-
-**POST** /v1/tenants/{tenant_id}/schemas/write
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- TenantId: "t1",
- Schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- tenantId: "t1",
- schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "schema": "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/write"**
-
-**Example Request on Postman:**
-
-
-
-
-## Suggested Workflow For Schema Changes
-
-It's expected that your initial schema will eventually change as your product or system evolves
-
-As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
-
-A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database (your writeDB) unless you delete them with the [delete API](../relationship/delete-relationships.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
-
-We recommend applying the following pattern to safely handle schema changes:
-
-- Set up a central git repository that includes the schema.
-- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
-- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
-
-## Need any help ?
-
-Depending on the frequency and the type of the changes that you made on the schemas, this method may not be optimal for you - In such cases, we are open to exploring alternative solutions. Please feel free to [schedule a call with one of our engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/_category_.json b/docs/versioned_docs/version-0.3.x/api-overview/tenancy/_category_.json
deleted file mode 100644
index 9771416d..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Tenancy Service",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/create-tenant.md b/docs/versioned_docs/version-0.3.x/api-overview/tenancy/create-tenant.md
deleted file mode 100644
index 412ddaec..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/create-tenant.md
+++ /dev/null
@@ -1,55 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Create Tenant
-
-Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
-
-:::caution
-We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
-:::
-
-## Request
-
-**POST /v1/tenants/create**
-
-
-
-
-```go
-rr, err: = client.Tenancy.Create(context.Background(), & v1.TenantCreateRequest {
- Id: ""
- Name: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.create({
- id: "",
- name: ""
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'http://localhost:3476/v1/tenants/create' \
---header 'Content-Type: application/json' \
---data-raw '{
- "id": "",
- "name": ""
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/delete-tenant.md b/docs/versioned_docs/version-0.3.x/api-overview/tenancy/delete-tenant.md
deleted file mode 100644
index d8bd4a43..00000000
--- a/docs/versioned_docs/version-0.3.x/api-overview/tenancy/delete-tenant.md
+++ /dev/null
@@ -1,44 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Tenant
-
-You can delete a tenant with following API.
-
-## Request
-
-**DELETE /v1/tenants/{id}**
-
-
-
-
-```go
-rr, err: = client.Tenancy.Delete(context.Background(), & v1.TenantDeleteRequest {
- Id: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.delete({
- id: "",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/comparision.md b/docs/versioned_docs/version-0.3.x/comparision.md
deleted file mode 100644
index 6df7749f..00000000
--- a/docs/versioned_docs/version-0.3.x/comparision.md
+++ /dev/null
@@ -1,38 +0,0 @@
----
-id: comparison
-title: Comparison Between Other Zanzibar implementations
----
-
-:::caution Note
-This comparison table shows the differentiation between authorization solutions based or inspired by Google Zanzibar paper. If you use any of these solutions and feel the information could be improved, feel free to reach out.
-:::
-
-## General Aspects
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify
-|---|---|---|---|---|
-| **Zanzibar Paper Faithfulness** | Medium | High | High | High
-| **Scalability** | Medium | Medium | High | High
-| **Consistency & Cache** | No Zookies | No Zookies | Supported | Supported |
-| **Dev UX** | Average | Average | High | High |
-
-## Feature Set
-
-- ✅ Supported, and ready to use with no added configuration or code
-- 🟡 Limited support and requires extra user-code to implement.
-- ⛔ Not officially supported or documented.
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify
-|---|---|---|---|---|
-| **Check API** |✅ | ✅ | ✅ | ✅ |
-| **Write API** | ✅ | ✅ | ✅ | ✅ |
-| **Read API** | ✅ | ✅ | ✅ | ✅ |
-| **Expand API** | ✅ | ✅ | ✅ | ✅ |
-| **Watch API** | ✅ | ✅ | ✅ | ⛔ |
-| **RBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ReBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ABAC** | ⛔ | 🟡 | ✅ | ⛔ |
-| **Data Filtering** | ⛔ | ✅ | ✅ | ✅ |
-| **Multi Tenancy** | ⛔ | ✅ | ⛔ | ✅ |
-| **Testing & Validation** | ⛔ | 🟡 | ✅ | ✅ |
-| **Logging & Tracing** | 🟡 | ✅ | ✅ | ✅ |
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/_category_.json b/docs/versioned_docs/version-0.3.x/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/enforcement.md b/docs/versioned_docs/version-0.3.x/getting-started/enforcement.md
deleted file mode 100644
index d7ee5f12..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/enforcement.md
+++ /dev/null
@@ -1,91 +0,0 @@
----
-sidebar_position: 4
----
-
-# Access Control Check
-
-In Permify, you can perform access control checks as both resource specific and subject specific (data filtering) with single API calls.
-
-A simple [resource based] access check takes form of ***Can the subject U perform action X on a resource Y ?***. A real world example would be: *can user:1 edit document:2* where the right side of the ":" represents identifier of the entity.
-
-On the other hand [subject based] access check takes form of ***Which resources does subject U perform an action X ?*** This option is best for filtering data or bulk permission checks.
-
-[resource based]: ../api-overview/permission/check-api.md
-[subject based]: ../api-overview/permission/lookup-entity.md
-
-## Performance & Availability
-
-Permify designed to answer these authorization questions efficiently and with minimal complexity while providing low latency with:
-- Using its parallel graph engine.
-- Storing the relationships between resources beforehand in Permify data store: [writeDB], rather than providing these relationships at “check” time.
-- Implementing permission caching to not recompute repeated permission checks, and in memory cache to store authorization schema.
-- Using [Snap Tokens](../../reference/snap-tokens) to achieve consistency and high performance in cache.
-
-Performance and availability of the API calls - especially access checks - are crucial for us and we're ongoingly improving and testing it with various methods.
-
-:::info
-We would love to create a test environment for you in order to test Permify API and see performance and availability of it. [Schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-[writeDB]: ../getting-started/sync-data.md
-
-## How Access Decisions Evaluated?
-
-Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
-
-In high level, access of an subject related with the relationships created between the subject and the resource. You can define this relationships in Permify Schema then create and store them as relational tuples, which is basically your authorization data.
-
-Permify Engine to compute access decision in 2 steps,
-1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
-2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
-
-Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
-
-[relational tuples]: ../../getting-started/sync-data
-[Permify Schema]: ../../getting-started/modeling
-
-When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity document {
-
- // represents documents parent organization
- relation parent @organization
-
- // represents owner of this document
- relation owner @user
-
- // permissions
- action edit = parent.admin or owner
- action delete = owner
-}
-```
-
-Which has a directed graph as follows:
-
-
-
-As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
-
-**Q1:** Get the owners of the `document:12`.
-
-**Q2:** Get admins of the organization where `document:12` belongs to.
-
-Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
-
-Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/examples/_category_.json b/docs/versioned_docs/version-0.3.x/getting-started/examples/_category_.json
deleted file mode 100644
index b3e4f801..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/examples/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Example Permission Structures",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/examples/facebook-groups.md b/docs/versioned_docs/version-0.3.x/getting-started/examples/facebook-groups.md
deleted file mode 100644
index 53a309a6..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/examples/facebook-groups.md
+++ /dev/null
@@ -1,537 +0,0 @@
-# Facebook Groups
-
-This example demonstrate the authorization structure for Facebook groups, which enables users to perform various actions based on their roles and permissions within the group.
-
-### Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
-
-```perm
-// Represents a user
-entity user {}
-
-// Represents a Facebook group
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
-}
-
-// Represents a post in a Facebook group
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
-}
-
-// Represents a comment like on a post in a Facebook group
-entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
-}
-
-// Definition of poll entity
-entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
-}
-
-// Definition of file entity
-entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
-}
-
-// Definition of event entity
-entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities and relations, as well as actions and permissions that can be taken by users within the group. Let's examine them shortly;
-
-### Entities & Relations
-
-* **`user`** entity represents a user in the Facebook.
-
-* **`group`** entity represents the Facebook group, and it has several relations including member, admin, and moderator to represent the members, admins, and moderators of the group. Additionally, there are relations to represent the posts and comments in the group.
-
-* **`post`** entity represents a post in the Facebook group, and it has relations to represent the owner of the post and the group that the post belongs to.
-
-* **`comment`** entity represents a comment on a post in the Facebook group, and it has relations to represent the owner of the comment, the post that the comment belongs to, and the comment itself.
-
-* **`like`** entity represents a like on a post in the Facebook group, and it has relations to represent the owner of the like and the post that the like belongs to.
-
-* **`poll`** entity represents a poll in the Facebook group, and it has relations to represent the owner of the poll and the group that the poll belongs to.
-
-* **`file`** entity represents a file in the Facebook group, and it has relations to represent the owner of the file and the group that the file belongs to.
-
-* **`event`** entity represents an event in the Facebook group, and it has relations to represent the owner of the event and the group that the event belongs to.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions.
-
-For example, the `create_group` action can only be performed by a `member`, as follows:
-
-#### Creating a group permission
-
-```perm
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
-
- ..
-
- // Create group permission
- action create_group = member
-
- ..
- ..
-}
-```
-
-Another example would be given from the `edit_post` action in the post entity, which specifies the permissions required to edit a post in a Facebook group.
-
-#### Editing a post permission
-
-```perm
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- ..
-
- action edit_post = owner or group.admin
-
- ..
- ..
-}
-```
-
-An **owner** of a post can always edit their own post. In addition, members who are defined as **admin** of the group - which the post belongs to - can also edit the post.
-
-Since most entities are deeply nested together, we also have multiple hierarchical permissions.
-
-#### Nested Hierarchies
-
-For example, we can define a permission "view_comment" if only user is owner of that comment or user is a member of the group which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-//group relationships
-group:1#member@user:1
-group:1#admin@user:2
-group:2#moderator@user:3
-group:2#member@user:4
-group:1#member@user:5
-
-//post relationships
-post:1#owner@user:1
-post:1#group@group:1
-post:2#owner@user:4
-post:2#group@group:1
-
-//comment relationships
-comment:1#owner@user:2
-comment:1#post@post:1
-comment:2#owner@user:5
-comment:2#post@post:2
-
-//like relationships
-like:1#owner@user:3
-like:1#post@post:1
-like:2#owner@user:4
-like:2#post@post:2
-
-//poll relationships
-poll:1#owner@user:2
-poll:1#group@group:1
-poll:2#owner@user:5
-poll:2#group@group:1
-
-//like relationships
-file:1#owner@user:1
-file:1#group@group:1
-
-//event relationships
-event:1#owner@user:3
-event:1#group@group:1
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:4 RSVP_to_event event:1 ?
-
-
-```perm
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
-
- ..
- ..
-
- action RSVP_to_event = owner or group.member
- }
-```
-
-According to what we have defined for the **'RSVP_to_event'** action, users who are either the owner of `event:1` or a member of the group that belongs to `event:1` can grant access to RSVP to the event.
-
-According to the relation tuples we created, `user:4` is not the **owner** of the event. Furthermore, when we check whether `user:4` is a **member** of the only group (`group:1`) that `event:1` is part of (`event:1#group@group:1`), we see that there is no **member** relation for `user:4` in that group.
-
-Therefore, the `user:4 RSVP_to_event event:1` check request should yield a **'false'** response.
-
-
-
-
-can user:5 view_comment comment:1 ?
-
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-According to the relation tuples we created, `user:5` is not the **owner** of the comment. But member of the `group:1` and thats grant `user:5` (`group:1#member@user:5`) access to perform view the comment:1. In particularly, `comment:1` is part of the `post:1` (`comment:1#post@post:1`) and `post:1` is part of the group:1 (`post:1#group@group:1`). And from the action definition on above model group:1 members can view the `comment:1`.
-
-Therefore, the `user:5 view_comment comment:1` check request should yield a **'true'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
- }
-
- entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
- }
-
- entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
- }
-
- entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
- }
-
- entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
- }
-
- entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
- }
-
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
- }
-
-relationships:
- - group:1#member@user:1
- - group:1#admin@user:2
- - group:2#moderator@user:3
- - group:2#member@user:4
- - group:1#member@user:5
- - post:1#owner@user:1
- - post:1#group@group:1
- - post:2#owner@user:4
- - post:2#group@group:1
- - comment:1#owner@user:2
- - comment:1#post@post:1
- - comment:2#owner@user:5
- - comment:2#post@post:2
- - like:1#owner@user:3
- - like:1#post@post:1
- - like:2#owner@user:4
- - like:2#post@post:2
- - poll:1#owner@user:2
- - poll:1#group@group:1
- - poll:2#owner@user:5
- - poll:2#group@group:1
- - file:1#owner@user:1
- - file:1#group@group:1
- - event:1#owner@user:3
- - event:1#group@group:1
-
-assertions:
- - "can user:4 RSVP_to_event event:1": false
- - "can user:5 view_comment comment:1": true
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make run`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/examples/google-docs.md b/docs/versioned_docs/version-0.3.x/getting-started/examples/google-docs.md
deleted file mode 100644
index 9e66f806..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/examples/google-docs.md
+++ /dev/null
@@ -1,304 +0,0 @@
-# Google Docs Simplified
-
-This example models a simplified version of Google Docs style permission system where users can be granted direct access to a resource, or access via organizations and nested groups.
-
-### Schema | [Open in playground](https://play.permify.co/?s=iuRic3nR1HeZJcFyRNKPo)
-
-```perm
-entity user {}
-
-entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
-}
-
-entity group {
- relation manager @user @group#member @group#manager
- relation member @user @group#member @group#manager
-}
-
-entity organization {
- relation group @group
- relation resource @resource
-
- relation administrator @user @group#member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-```
-
-## Breakdown of the Model
-
-### User
-
-```perm
-entity user {}
-```
-Represents a user who can be granted permission to access a resource directly, or through their membership in a group or organization.
-
-### Resource
-
-```perm
-entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
-}
-```
-
-Represents a resource that users can be granted permission to access. The resource entity has two relationships:
-
-#### Relations
-
-**manager:** A relationship between users who are authorized to manage the resource. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group member and manager relations.
-
-**viewer:** A relationship between users who are authorized to view the resource. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager relations.
-
-The resource entity has two actions defined:
-
-#### Actions
-
-**manage:**: An action that can be performed by users who are authorized to manage the resource, as determined by the manager relationship.
-
-**view:** An action that can be performed by users who are authorized to view the resource, as determined by the viewer and manager relationships.
-
-### group
-
-```perm
-entity group {
- relation manager @user @group#member @group#manager
- relation member @user @group#member @group#manager
-}
-```
-
-Represents a group of users who can be granted permission to access a resource. The group entity has two relationships:
-
-#### Relations
-
-**manager:** A relationship between users who are authorized to manage the group. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**member:** A relationship between users who are members of the group. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager.
-
-The group entity has one action defined:
-
-### Organization
-
-```perm
-entity organization {
- relation group @group
- relation resource @resource
-
- relation administrator @user @group#member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-```
-
-Represents an organization that can contain groups, users, and resources. The organization entity has several relationships:
-
-#### Relations
-
-**group:** A relationship between the organization and its groups. This relationship is defined by the `@group` annotation on the end corresponding to the group entity.
-
-**administrator:** A relationship between users who are authorized to manage the organization. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are directly members of the organization. This relationship is defined by the `@user` annotation on the end corresponding to the user entity.
-
-**resource:** A relationship between the organization and its resources. This relationship is defined by the `@resource` annotation on the end corresponding to the resource entity.
-
-The organization entity has two permissions defined:
-
-#### Permissions
-
-**admin:** An permission that can be performed by users who are authorized to manage the organization, as determined by the administrator relationship.
-
-**member:** An permission that can be performed by users who are directly members of the organization, or who have administrator relationship, or who are members of groups that are part of the organization,
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different groups
-group:tech#manager@user:ashley
-group:tech#member@user:david
-group:marketing#manager@user:john
-group:marketing#member@user:jenny
-group:hr#manager@user:josh
-group:hr#member@user:joe
-
-// Assign groups to other groups
-group:tech#member@group:marketing#member
-group:tech#member@group:hr#member
-
-// Connect groups to organization.
-organization:acme#group@group:tech
-organization:acme#group@group:marketing
-organization:acme#group@group:hr
-
-// Add some resources under the organization
-organization:acme#resource@resource:product_database
-organization:acme#resource@resource:marketing_materials
-organization:acme#resource@resource:hr_documents
-
-// Assign a user and members of a group as administrators for the organization
-organization:acme#administrator@group:tech#manager
-organization:acme#administrator@user:jenny
-
-// Set the permissions on some resources
-resource:product_database#manager@group:tech#manager
-resource:product_database#viewer@group:tech#member
-resource:marketing_materials#viewer@group:marketing#member
-resource:hr_documents#manager@group:hr#manager
-resource:hr_documents#viewer@group:hr#member
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:ashley edit resource:product_database ?
-
-
-```perm
- entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
- }
-```
-
-According what we have defined for the edit action only managers of can edit product database. In this context, Permify engine will check does subject `user:ashley` has any direct or indirect manager relation within `resource:product_database`.
-
-Ashley is manager in group tech (`group:tech#manager@user:ashley`) and we have defined that manager of group tech is manager of product_database with the tuple (`resource:product_database#manager@group:tech#manager`). Therefore, the **user:ashley edit resource:product_database** check request should yield **true** response.
-
-
-
-
-can user:joe view resource:hr_documents ?
-
-
-```perm
- entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
- }
-```
-
-According what we have defined for the view action viewers or managers of can view hr documents. In this context, Permify engine will check does subject `user:joe` has any direct or indirect manager or viewer relation within `resource:hr_documents`.
-
-Joe doesn't have manager relationship in that resource or within any entity but he is member in the hr group (`group:hr#member@user:joe`) and we defined hr members have viewer relationship in hr documents (`resource:hr_documents#viewer@group:hr#member`). So that, this enforcement should yield **true** response.
-
-
-
-```perm
- entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
- }
-```
-
-According what we have defined for the view action viewers or managers of can view hr documents. In this context, Permify engine will check does subject `user:david` has any direct or indirect manager or viewer relation within `resource:marketing_materials`.
-
-David doesn't have member or manager relationship related with marketing group or with the `resource:marketing_materials`. So that, this enforcement should yield **false** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity resource {
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager
- action view = viewer or manager
- }
-
- entity group {
- relation manager @user @group#member @group#manager
- relation member @user @group#member @group#manager
- }
-
- entity organization {
- relation group @group
- relation resource @resource
-
- relation administrator @user @group#member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
- }
-
-relationships:
- - group:tech#manager@user:ashley
- - group:tech#member@user:david
- - group:marketing#manager@user:john
- - group:marketing#member@user:jenny
- - group:hr#manager@user:josh
- - group:hr#member@user:joe
- - group:tech#member@group:marketing#member
- - group:tech#member@group:hr#member
- - organization:acme#group@group:tech
- - organization:acme#group@group:marketing
- - organization:acme#group@group:hr
- - organization:acme#resource@resource:product_database
- - organization:acme#resource@resource:marketing_materials
- - organization:acme#resource@resource:hr_documents
- - organization:acme#administrator@group:tech#manager
- - organization:acme#administrator@user:jenny
- - resource:product_database#manager@group:tech#manager
- - resource:product_database#viewer@group:tech#member
- - resource:marketing_materials#viewer@group:marketing#member
- - resource:hr_documents#manager@group:hr#manager
- - resource:hr_documents#viewer@group:hr#member
-
-assertions:
- - "can user:ashley edit resource:product_database": true
- - "can user:joe view resource:hr_documents": true
- - "can user:david view resource:marketing_materials": false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make run`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of modeling Google Docs style permission system. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/examples/notion.md b/docs/versioned_docs/version-0.3.x/getting-started/examples/notion.md
deleted file mode 100644
index f3ed3d8d..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/examples/notion.md
+++ /dev/null
@@ -1,540 +0,0 @@
-# Notion
-
-This is a schema definition of the authorization model for Notion, a popular productivity and organization tool.
-
-### Schema | [Open in playground](https://play.permify.co/?s=BsCvLmd4g81sB20XJZI5p)
-
-```perm
-entity user {}
-
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
-}
-
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
-}
-
-entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
-}
-
-entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
-}
-
-entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
-}
-
-entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
-}
-
-entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities, including users, workspaces, pages, databases, blocks, and integrations. It also includes several default roles, such as Admin, Bot, Guest, and Member. Here's a breakdown of the entities:
-
-### Entities & Relations
-
-* **`user`**: Represents a user in the system.
-
-* **`workspace`**: Represents a workspace in which users can collaborate. Each workspace has an owner, members, guests, and bots associated with it. The owner and admin users have permission to manage the workspace. Permissions are defined for creating pages, inviting members, viewing the workspace, and managing the workspace. The read and write permissions can be inherited by child entities.
-
-* **`page`**: Represents a page within a workspace. Each page is associated with a workspace and has a writer and readers. The read and write permissions are defined based on the writer and readers of the page and can be inherited from the workspace.
-
-* **`database`**: Represents a database within a workspace. Each database is associated with a workspace and has an editor and viewers. The read and write permissions are defined based on the editor and viewers of the database and can be inherited from the workspace. Permissions are also defined for creating and deleting databases.
-
-* **`block`**: Represents a block within a page or database. Each block is associated with a page or database and has an editor and commenters. The read and write permissions are defined based on the editor and commenters of the block and can be inherited from the database. Commenters are users who have permission to comment on the block.
-
-* **`comment`**: Represents a comment on a block. Each comment is associated with a block and has an author. The read and write permissions are defined based on the author of the comment and can be inherited from the block.
-
-* **`template`**: Represents a template within a workspace. Each template is associated with a workspace and has a creator and viewers. The read and write permissions are defined based on the creator and viewers of the template and can be inherited from the workspace. Permissions are also defined for creating and deleting templates.
-
-* **`integration`**: Represents an integration within a workspace. Each integration is associated with a workspace and has an owner. Permissions are defined for reading and writing to the integration.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions. Let's examine the **read** permission of the page entity.
-
-#### Page Read Permission
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- ..
-}
-
-entity page {
-
- // The workspace associated with the page
- relation workspace @workspace
-
- ..
- ..
-
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- ..
- ..
-
- // Define permissions for page actions
- permission read = reader or workspace.read
-
- ..
- ..
-}
-```
-
-This permission specifies who can read the contents of the page at Notion.
-
-The `reader` relation specifies the users who are members of the workspace associated with the page (`workspace#member`) or guests of the workspace (`workspace#guest`).
-
-Read permission of the workspace inherited as `workspace.read` in the page entity. THis permission specifies that any user who has been granted read access to the workspace object (i.e., the workspace that the page belongs to) can also read the page.
-
-In summary, any user who is a member or guest of the workspace and has been granted read access to the page through the reader relation, as well as any user who has been granted read access to the workspace itself, can read the contents of the page.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different workspaces:
-workspace:engineering_team#owner@user:alice
-workspace:engineering_team#member@user:bob
-workspace:engineering_team#guest@user:charlie
-workspace:engineering_team#admin@user:alice
-workspace:sales_team#owner@user:david
-workspace:sales_team#member@user:eve
-workspace:sales_team#guest@user:frank
-workspace:sales_team#admin@user:david
-
-// Connect pages, databases, and templates to workspaces:
-page:project_plan#workspace@workspace:engineering_team
-page:product_spec#workspace@workspace:engineering_team
-database:task_list#workspace@workspace:engineering_team
-template:weekly_report#workspace@workspace:sales_team
-database:customer_list#workspace@workspace:sales_team
-template:marketing_campaign#workspace@workspace:sales_team
-
-// Set permissions for pages, databases, and templates:
-page:project_plan#writer@user:frank
-page:project_plan#reader@user:bob
-
-database:task_list#editor@user:alice
-database:task_list#viewer@user:bob
-
-template:weekly_report#creator@user:alice
-template:weekly_report#viewer@user:bob
-
-page:product_spec#writer@user:david
-page:product_spec#reader@user:eve
-
-database:customer_list#editor@user:david
-database:customer_list#viewer@user:eve
-
-template:marketing_campaign#creator@user:david
-template:marketing_campaign#viewer@user:eve
-
-// Set relationships for blocks and comments:
-block:task_list_1#database@database:task_list
-block:task_list_1#editor@user:alice
-block:task_list_1#commenter@user:bob
-block:task_list_2#database@database:task_list
-block:task_list_2#editor@user:alice
-block:task_list_2#commenter@user:bob
-
-comment:task_list_1_comment_1#block@block:task_list_1
-comment:task_list_1_comment_1#author@user:bob
-comment:task_list_1_comment_2#block@block:task_list_1
-comment:task_list_1_comment_2#author@user:charlie
-comment:task_list_2_comment_1#block@block:task_list_2
-comment:task_list_2_comment_1#author@user:bob
-comment:task_list_2_comment_2#block@block:task_list_2
-comment:task_list_2_comment_2#author@user:charlie
-```
-
-## Test & Validation
-
-Since we have our schema and the sample relation tuples, let's check some permissions and test our authorization logic.
-
-can user:alice write database:task_list ?
-
-
-```perm
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
-
- ..
- ..
-
- // Define permissions for database actions
- ..
- ..
-
- permission write = editor or workspace.write
-
- ..
- ..
- }
-```
-
-According to what we have defined for the **'write'** permission, users who are either;
-
-* The editor in task list database (`database:task_list`)
-* Have a write permission in the engineering team workspace, which is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`)
-
-can edit the task list database (`database:task_list`)
-
-Based on the relation tuples we created, `user:alice` doesn't have the **editor** relationship with the `database:task_list`.
-
-Since `user:alice` is the owner and admin in the engineering team workspace (`workspace:engineering_team#admin@user:alice`) it has a write permission defined in the workspace entity, as you can see below:
-
-```
-entity workspace {
- // The owner of the workspace
- relation owner @user
- ..
- ..
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- ..
- permission write = owner or admin
-}
-```
-
-And as we mentioned the engineering team workspace is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`). Therefore, the `user:alice write database:task_list` check request should yield a **'true'** response.
-
-
-
-
-can user:charlie write page:product_spec ?
-
-
-```perm
- entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
-
- ..
- ..
-
- permission write = writer or workspace.write
- }
-```
-
-`user:charlie` is guest in the workspace (`workspace:engineering_team#guest@user:charlie`) and the engineering team workspace is the only workspace that `page:product_spec` belongs to.
-
-As we defined, guests doesn't have write permission in a workspace.
-
-```perm
- entity workspace {
- // The owner of the workspace
- relation owner @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- permission write = owner or admin
-}
-```
-
-So that, `user:charlie` doesn't have a write relationship in the workspace. And ultimately, the `user:charlie write page:product_spec` check request should yield a **'false'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
- }
-
- entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
- }
-
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
- }
-
- entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
- }
-
- entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
- }
-
- entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
- }
-
- entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
- }
-
-relationships:
- - workspace:engineering_team#owner@user:alice
- - workspace:engineering_team#member@user:bob
- - workspace:engineering_team#guest@user:charlie
- - workspace:engineering_team#admin@user:alice
- - workspace:sales_team#owner@user:david
- - workspace:sales_team#member@user:eve
- - workspace:sales_team#guest@user:frank
- - workspace:sales_team#admin@user:david
- - page:project_plan#workspace@workspace:engineering_team
- - page:product_spec#workspace@workspace:engineering_team
- - database:task_list#workspace@workspace:engineering_team
- - template:weekly_report#workspace@workspace:sales_team
- - database:customer_list#workspace@workspace:sales_team
- - template:marketing_campaign#workspace@workspace:sales_team
- - page:project_plan#writer@user:frank
- - page:project_plan#reader@user:bob
- - database:task_list#editor@user:alice
- - database:task_list#viewer@user:bob
- - template:weekly_report#creator@user:alice
- - template:weekly_report#viewer@user:bob
- - page:product_spec#writer@user:david
- - page:product_spec#reader@user:eve
- - database:customer_list#editor@user:david
- - database:customer_list#viewer@user:eve
- - template:marketing_campaign#creator@user:david
- - template:marketing_campaign#viewer@user:eve
- - block:task_list_1#database@database:task_list
- - block:task_list_1#editor@user:alice
- - block:task_list_1#commenter@user:bob
- - block:task_list_2#database@database:task_list
- - block:task_list_2#editor@user:alice
- - block:task_list_2#commenter@user:bob
- - comment:task_list_1_comment_1#block@block:task_list_1
- - comment:task_list_1_comment_1#author@user:bob
- - comment:task_list_1_comment_2#block@block:task_list_1
- - comment:task_list_1_comment_2#author@user:charlie
- - comment:task_list_2_comment_1#block@block:task_list_2
- - comment:task_list_2_comment_1#author@user:bob
- - comment:task_list_2_comment_2#block@block:task_list_2
- - comment:task_list_2_comment_2#author@user:charlie
-
-assertions:
- - "can user:alice write database:task_list": true
- - "user:charlie write page:product_spec": false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make run`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/modeling.md b/docs/versioned_docs/version-0.3.x/getting-started/modeling.md
deleted file mode 100644
index ba4b42c3..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/modeling.md
+++ /dev/null
@@ -1,287 +0,0 @@
----
-sidebar_position: 1
----
-
-# Modeling Authorization
-
-Permify has its own language that you can model your authorization logic with it. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like user types such as admin, manager, member, etc.
-
-
-
-## Permify Schema
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. It includes set-algebraic operators such as intersection and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-Here’s a simple breakdown of our schema.
-
-
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is **_".perm"_**.
-
-## Developing a Schema
-
-This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-
-We'll follow a simplified version of github access control system. To see completed model you can jump directly to [Github Example](#github-example).
-
-:::info
-You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
-
-[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-:::
-
-### Defining Entities
-
-The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
-
-Think of entities as tables in your relationship database. We are strongly advice to name entities same as your database table name that its corresponds. In that way you can easily model and reason your authorization as well as eliminating the error possibility.
-
-You can create entities using `entity` keyword. Since we're following example of simplified github access control, lets create some of our entities as follows.
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity team {}
-
-entity repository {}
-```
-
-Entities has 2 different attributes. These are;
-
-- **relations**
-- **actions (or permissions)**
-
-### Defining Relations
-
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions. Keyword **_relation_** need to used to create a entity relation with name and type attributes.
-
-**Relation Attributes:**
-
-- **name:** relation name.
-- **type:** relation type, basically the entity it’s related to (e.g. user, organization, document, etc.)
-
-An example relation takes form of,
-
-```perm
-relation [name] @[type]
-```
-
-Lets turn back to our example and define our relations inside our entities:
-
-#### User Entity
-
-→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
-
-```perm
-entity user {}
-```
-
-#### Organization Entity
-
-→ For the sake of simplicity let's define only 2 user types in an organization, these are administrators and direct members of the organization.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-```
-
-#### Team Entity
-
-→ Let's say teams can belong organizations and can have a member inside of it as follows,
-
-```perm
-entity team {
-
- relation parent @organization
- relation member @user
-
-}
-```
-
-The parent relation is indicating the organization the team belongs to. This way we can achieve **parent-child relationship** inside this entity.
-
-#### Repository Entity
-
-→ Organizations and users can have multiple repositories, so each repository is related with an organization and with users. We can define repository relations as as follows.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-}
-```
-
-The owner relation indicates the creator of the repository, that way we can achieve **ownership** in Permify.
-
-**Defining Multiple Relation Types**
-
-As you can see we have new syntax above,
-
-```perm
- relation maintainer @user @team#member
-```
-
-When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-
-:::info
-You can use **#** to reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
-
-Actual purpose of feature locking is to giving ability to specify the sets of users that can be assigned.
-
-For example:
-
-```perm
- relation viewer @user
-```
-
-When you define it like this, you can only add users directly as tuples (you can find out what relation tuples is in next section):
-
-* organization:1#viewer@user:U1
-* organization:1#viewer@user:U2
-
-However, if you define it as:
-
-```perm
- relation viewer @user @organization#member
-```
-
-You will then be able to specify not only individual users but also members of an organization:
-* organization:1#viewer@user:U1
-* organization:1#viewer@user:U2
-* organization:1#viewer@organization:O1#member
-
-You can think of these definitions as a precaution taken against creating undesired user set relationships.
-:::
-
-Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
-
-### Defining Actions and Permissions
-
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances. So, the basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
-
-The Permify Schema supports `and`, `or`, `and not` and `or not` operators for defining actions. The keywords **_action_** or **_permission_** can be used with those operators to form rules for your authorization logic.
-
-Lets get back to our github example and create some actions on repository entity,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- ..
- ..
-
- action push = owner
-
-}
-```
-
-→ `action push = owner or maintainer` indicates only the repository owner or maintainers can push to
-repository.
-
-:::info
-The same `push` can also be defined using the **permission** keyword, as follows:
-
-```perm
-permission push = owner
-```
-
-Using action or permission will yield the same result for defining permissions in your authorization logic.
-
-The reason we have two keywords (`action` and `permission`) for defining permissions is that while most permissions are based on actions (such as view, read, edit, etc.), there are still cases where we need to define permissions based on roles or user types, such as admin or member.
-
-Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
-
-See Real World Examples Section for examining the contextualize difference between using permission and action keyword. You can start with observing [Google Docs Simplified](./examples/google-docs.md) example.
-:::
-
-For this tutorial we'll continue with `action` keyword,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- ..
- ..
-
- action read = (owner or maintainer or org.member) and org.admin
-
-}
-```
-
-→ For more fine grained permission let's examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-
-:::info
-You can add actions to another action like relations, see below.
-
-```perm
- action edit = member or manager
- action delete = edit or org.admin
-```
-
-delete action can inherit the edit action rules like above. To sum up, only organization administrators and any relation that can perform edit action (member or manager) can perform delete action.
-:::
-
-### Full Schema
-
-Here is full implementation of simple Github access control example with using Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
- action edit = member or parent.admin
-
-}
-
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- action push = owner or maintainer
- action read = (owner or maintainer or parent.member) and parent.admin
- action delete = parent.admin or owner
-
-}
-```
-
-## Real World Examples
-
-This example shows almost all aspects of the Permify Schema.
-
-You can check out more schema examples from the [Real World Examples](../examples) section with their detailed examination.
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/sync-data.md b/docs/versioned_docs/version-0.3.x/getting-started/sync-data.md
deleted file mode 100644
index 4f0243a2..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/sync-data.md
+++ /dev/null
@@ -1,445 +0,0 @@
----
-sidebar_position: 2
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Managing Authorization Data
-
-Permify unifies your authorization data in a database you prefer. We named that database as Write Database, shortly **WriteDB**.
-
-Permify API provides various functionalities - checking access, reasoning permissions, etc - to maintain separate access control mechanisms for individual applications. And **WriteDB** stands as a source of truth for these authorization functionalities.
-
-## Access Control as Relations - Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. Each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-In Permify, the simplest form of relational tuple structured as: `entity # relation @ user`. Here are some relational tuples with semantics,
-
-
-
-## Where Relational Tuples Used ?
-
-In Permify, these relational tuples represents your authorization data.
-
-Permify stores your relational tuples (authorization data) in a database you prefer. You can configure the database when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-Stored relational tuples are queried and utilized in Permify APIs, including the check API, which is an access control check request used to determine whether a user's action is authorized.
-
-As an example; to decide whether a user could view a protected resource, Permify looks up the relations between that specific user and the protected resource. These relation types could be ownership, parent-child relation, or even a role such as an admin or manager.
-[WriteDB]: #write-database
-
-## Creating Relational Tuples
-
-Relational tuples can be created with an simple API call in runtime, since relations and authorization data's are live instances. Each relational tuple should be created according to its authorization model, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-
-
-Let's follow a simple document management system example with the following Permify Schema to see how to create relation tuples.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity document {
-
- relation owner @user
- relation parent @organization
- relation maintainer @user @organization#member
-
- action view = owner or parent.member or maintainer or parent.admin
- action edit = owner or maintainer or parent.admin
- action delete = owner or parent.admin
-}
-```
-
-According to the schema above; when a user creates a document in an organization, more specifically let's say, when user:1 create a document:2 we need to create the following relational tuple,
-
-- `document:2#owner@user:1`
-
-[WriteDB]: #write-database
-
-### Write Relationships API
-
-You can create relational tuples by using `Write Relationships API`.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "2",
- },
- Relation: "owner",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "2"
- },
- relation: "owner",
- subject: {
- type: "user",
- id: "1"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "2s"
- },
- "relation": "owner",
- "subject":{
- "type": "user",
- "id": "1",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Snap Tokens:
-
-In Write Relationships API response you'll get a snap token of the operation. This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../reference/snap-tokens.md)
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-## More Relationships
-
-Let's create more relationships according to the schema we defined above.
-
-### Organization Admin
-
-**relational tuple:** organization:1#admin@user:3
-
-**Semantics:** User 3 is administrator in organization 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "user",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Parent Organization
-
-**Relational Tuple:** document:1#parent@organization:1#…
-
-**Semantics:** Organization 1 is parent of document 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "parent",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "1",
- Relation: "..."
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "parent",
- subject: {
- type: "organization",
- id: "1",
- relation: "..."
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "parent",
- "subject":{
- "type": "organization",
- "id": "1",
- "relation": "..."
- }
- }
- ]
-}'
-```
-
-
-
-:::info
-Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
-
-Simply, the usage of ... is straightforward: if you're use user entity as an subject, you should not be using the `...` If you're using another subject rather than user entity then you need to use the `...`
-:::
-
-### Organization Members Are Maintainers in specific Doc
-
-**Created relational tuple:** document:1#maintainer@organization:2#member
-
-**Definition:** Members of organization 2 are maintainers in document 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "maintainer",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "2",
- Relation: "member"
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "maintainer",
- subject: {
- type: "organization",
- id: "2",
- relation: "member"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "maintainer",
- "subject":{
- "type": "organization",
- "id": "2",
- "relation": "member"
- }
- }
- ]
-}'
-```
-
-
-
-## Test this Example on Playground
-
-You can test and examine the above schema and relational tuples that we created in our playground using this [link](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_).
-
-## Next
-
-Let's now head over to the **Access Control Check** section and learn how to perform access control in Permify to ensure that only authorized users have the right level of access to our resources.
diff --git a/docs/versioned_docs/version-0.3.x/getting-started/testing.md b/docs/versioned_docs/version-0.3.x/getting-started/testing.md
deleted file mode 100644
index 124932d5..00000000
--- a/docs/versioned_docs/version-0.3.x/getting-started/testing.md
+++ /dev/null
@@ -1,106 +0,0 @@
----
-sidebar_position: 4
----
-
-# Testing & Validation
-
-Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
-
-Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
-
-We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Usage
-
-### Adding action to your workflow
-
-After adding [permify-validate-action] to your Github Action workflow, you need to define the schema validation yaml file as,
-
-- **With local file:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "test.yaml"
-```
-
-- **With external url:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
-```
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-### Creating Schema Validation File
-
-Below you can examine an example schema validation yaml file. It consists 3 parts; `schema` which is your new authorization model, sample `relationships` to test your model and lastly `assertions` which is the test access check questions and expected response - true or false.
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = (admin or member)
- action delete = admin
- }
-
- entity repository {
-
- relation owner @user @organization#member
- relation parent @organization
-
- action push = owner
- action read = (owner and (parent.admin and parent.member))
- action delete = (parent.member and (parent.admin or owner))
- action edit = parent.member and not owner
- }
-
-relationships:
- - "organization:1#admin@user:1"
- - "organization:1#member@user:1"
- - "repository:1#owner@user:1"
- - "repository:2#owner@user:2"
- - "repository:2#owner@user:3"
- - "repository:1#parent@organization:1#..."
- - "organization:1#member@user:43"
- - "repository:1#owner@user:43"
-
-assertions:
- - "can user:1 push repository:1": true
- - "can user:1 push repository:2": false
- - "can user:1 push repository:3": false
- - "can user:43 edit repository:1": false
-```
-
-## Testing in Local
-
-You can also test your new authorization model in your local (Permify clone) without using [permify-validate-action] at all.
-
-For that open up a new file and add a schema yaml file inside. Then build your project with, run `make run` command and run `./permify validate {path of your schema validation file}`.
-
-If we use the above example schema validation file, after running `./permify validate {path of your schema validation file}` it gives a result on the terminal as:
-
-
-
-[permify-validate-action]: https://github.com/Permify/permify-validate-action
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
-
diff --git a/docs/versioned_docs/version-0.3.x/installation.md b/docs/versioned_docs/version-0.3.x/installation.md
deleted file mode 100644
index c855058f..00000000
--- a/docs/versioned_docs/version-0.3.x/installation.md
+++ /dev/null
@@ -1,17 +0,0 @@
----
-id: installation
-title: Setup Permify
-slug: /installation
----
-
-# Setup Permify
-
-Here is some options that you can use to set up and deploy Permify in your servers.
-
-```mdx-code-block
-import {CardList} from '../../src/components/Card';
-
-
-```
-
-If options your deployment preference is not listed below please let us know Also if you have any questions join our [Discord community](https://discord.gg/n6KfzYxhPp) or send us an email at support@permify.co.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/installation/_category_.json b/docs/versioned_docs/version-0.3.x/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.3.x/installation/aws.md b/docs/versioned_docs/version-0.3.x/installation/aws.md
deleted file mode 100644
index c1c204d9..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/aws.md
+++ /dev/null
@@ -1,187 +0,0 @@
----
-title: AWS ECS, ECR & EC2
----
-
-# Deploy on AWS ECS, ECR & EC2
-
-AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
-
-There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
-
-ECS is a container management service. You can run your containers as task definitions, and It’s one of the easiest ways to deploy containers.
-
-If you’d like to watch this tutorial rather than reading. Here’s the video version.
-
-
-
-There is no prerequisite in this tutorial. You can simply deploy permify by following this step-by-step guide. However, if you want to integrate more advanced AWS security & networking features, we’ll follow up with a new tutorial guideline.
-
-At the end of this tutorial you’ll be able to;
-
-1. [Create a security group](#create-an-ec2-security-group)
-2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
-3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
-4. [Running our task definition](#4-running-our-task-definition)
-
-## 1. Create an EC2 Security Group
-
-So first thing first, let’s go over into security groups and create our security group. We’ll need this security group while creating our cluster.
-
-
-
-Search for “Security Groups” in the search bar. And go to the EC2 security groups feature.
-
-
-
-Then start creating a new security group.
-
-
-
-You have to name your security group, and give a description. Also, you need to choose the same VPC that you’ll going to use in EC2. So, I choose the default one. And I’m going to use same one while creating the ECS cluster.
-
-The next step is to configure our inbound rules. Here’s the configuration;
-
-```json
-//for mapping HTTP request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for mapping RPC request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3478",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for using SSH for connecting from your local computer.
-type = "Custom TCP", protocol = "TCP", port_range = "22",source = "Anywhere", 0.0.0.0/0
-```
-
-We have configured the HTTP and RPC ports for Permify. Also, we added port “22” for SSH connection. So, we can connect to EC2 through our local terminal.
-
-Now, we’re good to go. You can create the security group. And it’s ready to use in our ECS.
-
-## 2. Creating an ECS cluster
-
-
-
-The next step is to create an ECS cluster. From your AWS console search for Elastic Container Service or ECS for short.
-
-
-
-Then go over the clusters. As you can see there are 2 types of clusters. One is for ECS and another for EKS. We need to use ECS, EKS stands for Elastic Kubernetes Service. Today we’re not going to cover Kubernetes.
-
-Click **“Create Cluster”**
-
-
-
-Let’s create our first Cluster. Simply you have 3 options; Serverless(Network Only), Linux, and Windows. We’re going to cover EC2 Linux + Networking option.
-
-
-
-The next step is to configure our Cluster, starting with your Cluster name. Since we’re deploying Permify, I’ll call it “permify”.
-
-Then choose your instance type. You can take a look at different instances and pricing from [here](https://aws.amazon.com/ec2/pricing/on-demand/). I’m going with the t4 large. For cost purposes, you can choose t2.micro if you’re just trying out. It’s free tier eligible.
-
-Also, if you want to connect this EC2 instance from your local computer. You need to use SSH. Thus choose a key pair. If you have no such intention, leave it “none”.
-
-
-
-Now, we need to configure networking. First, choose your VPC, we use the default VPC as we did in the security groups. And choose any subnet on that VPC.
-
-You want to enable auto-assigned IP to make your app reachable from the internet.
-
-Choose the security group we have created previously.
-
-And voila, you can create your cluster. Now, we need to run our container in this cluster. To do that, let’s go over task definitions. And create our container definition.
-
-## 3. Creating and running task definitions
-
-Go over to ECS, and click the task definitions.
-
-
-
-And create a new task definition.
-
-
-
-Again, you’re going to ask to choose between; FARGATE, EC2, and EXTERNAL (On-premise). We’ll continue with EC2.
-
-Leave everything in default under the “Configure task and container definitions” section.
-
-
-
-Under the IAM role section you can choose “ecsTaskExecutionRole” if you want to use Cloud Watch later.
-
-You can leave task size in default since it’s optional for EC2.
-
-The critical part over here is to add our container. Click on the “Add Container” button.
-
-
-
-Then we need to add our container details. First, give a name. And then the most important part is our image URI. Permify is registered on the Github Registry so our image is;
-
-```yaml
-ghcr.io/permify/permify:latest
-```
-
-Then we need to define memory limit for the container, I went with 1024. You can define as much as your instance allows.
-
-Next step is to mapping our ports. As we mentioned in security groups, Permify by default listens;
-
-- `3476 for HTTP port`
-- `3478 for RPC port`
-
-
-
-Then we need to define command under the environment section. So, in order to start permify we first need to add “serve” command.
-
-For using properly we need a few other. Here’s the commands we need.
-
-```yaml
-serve, --database-engine=postgres, --database-uri=postgres://:@:/, --database-pool-max=20
-```
-
-- `serve` ⇒ for starting the Permify.
-- `--database-engine=postgres` ⇒ for defining the db we use.
-- `--database-uri=postgres://:password@:/` ⇒ for connecting your database with URI.
-- `--database-pool-max=20` ⇒ the depth for running in graph.
-
-We’re nice and clear, add the container and then just create your task definition. We’ll use this definition to run in our cluster.
-
-So, let’s go over and run our task definition.
-
-## 4. Running our task definition
-
-
-
-Let’s go to ECS and enter into our cluster. And go over into the tasks to run our task.
-
-
-
-Click to “Run new Task”
-
-
-
-Choose EC2 as a launch type. Then pick the task definition we just created. And leave everything else in the default. You can run your task now.
-
-We have just deployed our container into EC2 instance with ECS. Let’s test it.
-
-Now you can go over into EC2, and click on the running instances. Find the instance named `ECS Instance - EC2ContainerService-` in the running instances.
-
-
-
-Copy the Public IPv4 DNS from the right corner, and paste it into your browser. But you need to add `:3476` to access our http endpoint. So it should be like this;
-
-`:3476`
-
-and if you add healthz at the end like this;
-
-`:3476/healthz`
-
-you should get Serving status :)
-
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/installation/azure.md b/docs/versioned_docs/version-0.3.x/installation/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/installation/brew.md b/docs/versioned_docs/version-0.3.x/installation/brew.md
deleted file mode 100644
index e7388076..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/brew.md
+++ /dev/null
@@ -1,52 +0,0 @@
----
-title: "Install with Brew"
----
-
-# Brew With Configurations
-
-This section shows how to intall and run Permify Service with using brew.
-
-### Install Permify
-
-Open terminal and run following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-### Run Permify Service
-
-To run the Permify Service, `permify serve` command should be run with configurations.
-
-By default, the service is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather then an actual database. You can override these with running the command with configuration flags.
-
-### Configure With Using Flags
-
-See all configuration flags with running,
-
-```shell
-permify serve --help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flags' argument with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview/
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.3.x/installation/container.md b/docs/versioned_docs/version-0.3.x/installation/container.md
deleted file mode 100644
index 4802b078..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/container.md
+++ /dev/null
@@ -1,55 +0,0 @@
----
-title: "Docker Container"
----
-
-# Deploy using Docker
-
-This section shows how to run Permify Service from a docker container. You can run Permify service from a container with following steps.
-
-## Run following line on Terminal
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
-```
-
-This will start an API server with the configuration options that pointed out on the **{YOUR-CONFIG-PATH}**.
-
-### Configure With a YAML file
-
-This config path - `{YOUR-CONFIG-PATH}:/config` - addresses the [config yaml file](../reference/configuration.md), where you can configure running options of the Permify Server as well as define the ***database*** to store your authorization related data.
-
-:::info Talk to an Permify Engineer
-By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database.
-:::
-
-### Configure With Using Flags
-
-Alternatively, you can set configuration options with the respected flags when running the command. See all configuration flags with running,
-
-```shell
-docker run -p 8080:8080 ghcr.io/permify/permify serve -help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flags' argument with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.3.x/installation/google.md b/docs/versioned_docs/version-0.3.x/installation/google.md
deleted file mode 100644
index dcb3614a..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/google.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Google Compute Engine
----
-
-# Deploy on Google Compute Engine
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/installation/kubernetes.md b/docs/versioned_docs/version-0.3.x/installation/kubernetes.md
deleted file mode 100644
index f2a1e21b..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/kubernetes.md
+++ /dev/null
@@ -1,173 +0,0 @@
----
-title: Kubernetes Cluster
----
-
-# Deploy on Kubernetes Cluster
-
-In this section we’re going to deploy Permify in AWS EKS which is Amazon Elastic Kubernetes Service. EKS is a managed service that you can easily run Kubernetes in AWS.
-
-Here’s what we’re going to do step-by-step;
-
-1. [Configure our AWS IAM credentials](#configure-aws-cli-with-your-iam-account)
-3. [Create EKS cluster and configure nodes](#creating-an-aws-eks-cluster)
-4. [Deploy Permify to nodes](#deploying--running-permify-in-nodes)
-
-There are a couple of small prerequisites for this tutorial.
-
-### Pre-requisites
-
-- An AWS account.
-- The AWS Command Line Interface (CLI) is installed and configured on your local machine. — [Click here](https://us-east-1.console.aws.amazon.com/iamv2/home?region=us-east-1#/home) to go to IAM
-- The AWS IAM Authenticator for Kubernetes is installed and configured on your local machine.
-
-## Configure AWS CLI with your IAM account.
-
-The first step is to configure our AWS IAM account into our local terminal so that we can run commands. Most of you probably have a configured AWS account if you ever set up anything into AWS programmatically, so you can skip this. If you don’t follow these steps.
-
-### Create an AWS IAM Programmatic Access Account
-
-First, let’s create IAM credentials for ourselves. Search IAM from the AWS console. You need to write down the account ID if you want to log in AWS console with this account as well. Let’s go over users and start creating our credentials.
-
-
-
-At Users screen click to “Add users” — and you’ll end up in your first screen creating user credentials. Here you can define the name of the user. Also there 2 options that you can choose simultaneously.
-
-But you must choose “Access key - Programmatic access” option. It’ll allow us to configure our AWS CLI on our local machine.
-
-You can also choose “Password - AWS Management Console access” if you want to log in to this account through the console. But you’ll need the Account ID that I mentioned in the IAM console screen.
-
-In the next screen, you’ll be asked to create or copy the user-set permissions. For this tutorial, you’ll only need to access EKS resources and features. So lets create group by clicking the “Create group” — and then at pop-up screen search for EKS.
-
-
-
-I’ll choose all EKS permissions but if you have certain policies internally, just stick with them. You’ll only need following permission to;
-
-- `AmazonEKSClusterPolicy`
-- `AmazonEKSServicePolicy`
-- `AmazonEKSVPCResourceController`
-- `AmazonEKSWorkerNodePolicy`
-
-Then simply you can review and create the user.
-
-
-
-Once you created the credentials you’ll prompt the “Access key ID” and “Secret access key”, you should save this down somewhere. We’re going the use these to configure our local machine with AWS CLI.
-
-### **Configure AWS CLI with your IAM account**
-
-Let’s open our local terminal
-
-```jsx
-aws configure
-```
-
-Next you’ll ask for the following credentials;
-
-- `AWS Access Key ID`
-- `AWS Secret Access Key`
-- `Default region name`
-- `Default output format` (leave it empty)
-
-## Creating an AWS EKS Cluster
-
-For the first step, we need to install [eksctl](https://eksctl.io/) — which is like kubectl but for AWS EKS. It helps us to set up and deploy our cluster and nodes within a fraction of the time.
-
-Let’s download eksctl using brew.
-
-
-```jsx
-brew tap weaveworks/tap
-```
-
-While installing the eksctl, we’ll end up getting kubectl and other dependencies.
-
-```jsx
-brew install weaveworks/tap/eksctl
-```
-
-Now, we’re ready to create our EKS cluster. You can define certain things while deploying standard the cluster beside the name and version like; the region you want to deploy, the EC2 instance type of each node, and the number of nodes you want to run.
-
-```bash
-eksctl create cluster \
---name \
---version 1.24 \
---region \
---nodegroup-name permify \
---node-type t2.small \
---nodes 2
-```
-
-## Deploying & Running Permify in Nodes
-
-The next stop is applying our manifests which will help us to deploy and configure our container/Permify.
-
-Let’s create our deployment manifest first.
-
-```yaml
-apiVersion: apps/v1
-kind: Deployment
-metadata:
- labels:
- app: permify
- name: permify
-spec:
- replicas: 2
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://postgres:nOcodeSTIAnLAba@permify-test.ceuo5kqsxyea.us-east-1.rds.amazonaws.com:5432/demo"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
-status: {}
-```
-
-Now let’s apply our deployment manifest
-
-```jsx
-kubectl apply -f deployment.yaml
-```
-
-The next step is to create a service manifest, this will allow us to configure our container app.
-
-```jsx
-apiVersion: v1
-kind: Service
-metadata:
- name: permify
-spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
-status:
- loadBalancer: {}
-```
-
-Let’s apply service.yaml to our nodes.
-
-```jsx
-kubectl apply -f service.yaml
-```
-
-Last but not least, we can check our pods & nodes. And we can start using the container with load balancer
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/installation/overview.md b/docs/versioned_docs/version-0.3.x/installation/overview.md
deleted file mode 100644
index 330db2e2..00000000
--- a/docs/versioned_docs/version-0.3.x/installation/overview.md
+++ /dev/null
@@ -1,253 +0,0 @@
----
-sidebar_position: 1
----
-
-# Guide
-
-This guide shows how to set up Permify in your servers and use it across your applications. Set up and implementation consists of 4 steps,
-
-1. [Set Up & Run Permify Service](#set-up-permify-service)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Manage and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
-4. [Perform Access Check](#perform-access-check)
-
-:::info Talk to an Permify Engineer
-Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-## Set Up Permify Service
-
-You can run Permify Service with various options but in that tutorial we'll run it via docker container.
-
-### Run From Docker Container
-
-Production usage of Permify needs some configurations such as defining running options, selecting datastore to store authorization data and more.
-
-However, for the sake of this tutorial we'll not do any configurations and quickly start Permify on your local with running the docker command below:
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-:::info
-You can examine [Deploy using Docker] section to get more about the configuration options and learn the full integration to run Permify Service from docker container.
-
-[Deploy using Docker]: ../container
-:::
-
-### Test your connection
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core endpoints.
-
-[Using the API]: ../../api-overview
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-## Model your Authorization with Permify Schema
-
-After installation completed and Permify server is running, next step is modeling authorization with Permify authorization language - [Permify Schema] - and configure it to Permify API.
-
-You can define your entities, relations between them and access control decisions of each actions with using [Permify Schema].
-
-### Creating your authorization model
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-
-:::
-
-Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action view_files = admin or member
- action edit_files = admin
-
-}
-```
-
-We have 2 entities these are **"user"** and **"organization"**. Entities represents your main tables. We strongly advise naming entities the same as your original database entities.
-
-Lets roll back our example,
-
-- The `user` entity represents users. This entity is empty because it's only responsible for referencing users.
-
-- The `organization` entity has its own relations (`admin` and `member`) which related with user entity. This entity also has 2 actions, respectively:
- - Organization member and admin can view files.
- - Only admins can edit files.
-
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
-
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../use-cases/simple-rbac
-:::
-
-### Configuring Schema via API
-
-After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../api-overview/schema/write-schema.md) for configuration of your authorization model on Permify authorization service.
-
-:::caution Before Continue on Writing Schema
-You'll see **tenant_id** parameter almost all Permify APIs including Write Schema. With version 0.3.x Permify became a tenancy based authorization infrastructure, and supports multi-tenancy by default so its a mandatory parameter when doing any operations.
-
-We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
-:::
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-**POST /v1/tenants/{tenant_id}/schemas/write**
-
-
-
-## Store Authorization Data as Relational Tuples
-
-After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action.
-
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules at this writeDB by using [Write Relationships API](../api-overview/relationship/write-relationships.md)
-
-For our guide let's grant one of the team members (Ashley) an admin role.
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-**POST /v1/tenants/{tenant_id}relationships/write**
-
-```json
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1" //Organization identifier
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1", //Ashley's identifier
- "relation": ""
- }
- }
- ]
-}
-```
-
-
-
-**Created relational tuple:** organization:1#admin@user:1
-
-**Semantics:** User 1 (Ashley) has admin role on organization 1.
-
-:::tip
-In ideal production usage Permify stores your authorization data in a database you prefer. We called that database as WriteDB, and you can configure it with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) or CLI flag options.
-
-But in this tutorial Permify Service running default configurations on local, so authorization data will be stored in memory. You can find more detailed explanation how Permify stores authorization data in [Managing Authorization Data] section.
-
-[Managing Authorization Data]: ../../getting-started/sync-data
-:::
-
-## Perform Access Check
-
-Finally we're ready to control authorization. Access decision results computed according to relational tuples and the stored model, [Permify Schema] action conditions.
-
-Lets get back to our example and perform an example access check via [Check API]. We want to check whether an specific user has an access to view files in a organization.
-
-[Check API]: ../../api-overview/permission/check-api
-[Permify Schema]: ../../getting-started/modeling
-
-#### Example HTTP Request:
-
-***Can the user 45 view files on organization 1 ?***
-
-**POST /v1/tenants/{tenant_id}/permissions/check**
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | entity | object | - | name and id of the entity. Example: organization:1.
-| [x] | action | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action |
-| [ ] | schema_version | string | - | get results according to given schema version|
-| [ ] | depth | integer | 8 | |
-
-### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_files",
- "subject": {
- "type": "user",
- "id": "45",
- "relation": ""
- },
-}
-```
-
-### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "metadata": {
- "check_count": 0
- }
-}
-```
-
-See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-
-[Access Control Check]: ../getting-started/enforcement.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you struggle with installation or have any questions, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/migrating.md b/docs/versioned_docs/version-0.3.x/migrating.md
deleted file mode 100644
index c6906468..00000000
--- a/docs/versioned_docs/version-0.3.x/migrating.md
+++ /dev/null
@@ -1,153 +0,0 @@
----
-title: "Migrating to 0.3.x (Multi Tenancy)"
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-## Migration overview
-
-This doc guides you through migrating an existing Permify **0.2.x** authorization service to **0.3.x**. With version 0.3.x Permify moved to a tenancy-based infrastructure, which affects almost all of the API operations.
-
-## Multi Tenancy on Permify
-
-Multi-tenancy in Permify refers to an authorization architecture, where a single Permify authorization service serves multiple applications/organizations (tenants).
-
-This allows the ability to customize the authorization for each tenant's specific needs. With Multi-Tenancy support, you can create custom authorization schema and relation tuples accordingly for the different tenants and manage them in a single place - in [WriteDB](./getting-started/sync-data.md).
-
-For the users that don't have/need multi-tenancy in their authorization structure, we created a pre-inserted tenant (id: **t1**) that comes default when you serve a Permify service.
-
-## What have changed ?
-
-Several things changed when we moved to tenant based infrastructure, these are:
-
-* [API endpoints now have Tenant ID field](#api-endpoints-now-have-tenant-id-field)
-* [Added Tenancy Service](#added-tenancy-service)
-* [WriteDB tables and tenant id column](#writedb-tables-and-tenant-id-column)
-
-### API endpoints now have Tenant ID field
-
-All API endpoints that cover in 0.2.x now have a `tenant_id` mandatory field. Let's examine a check request below,
-
-#### Check API
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-Users that come from version 0.2.x and users that have a single tenant can enter **t1** as tenant id. See changes on the other endpoints from [API Overview Section](../api-overview/).
-
-### Added Tenancy Service
-
-To manage tenants we have added a Tenancy service; you can create, delete and list tenants accordingly. See the [Tenancy Service](../api-overview/tenancy/) on Using The API section.
-
-### WriteDB tenancy table and tenant id column
-
-#### Tenant Table
-
-Tenants table have added the Write DB to store tenant's details. The new WriteDB folder structure changed as follows:
-```
-tables
-├── migrations
-├── relation_tuples
-├── schema_definitions
-├── tenants
-├── transactions
-```
-
-#### Tenant ID Column
-
-Relation tuples and schema definition tables now have a tenant_id column, which stores the id of the tenant that data belongs.
-
-Let's take a look at a snapshot of the demo table on an example WriteDB.
-
-Example Relation Tuples data table:
-
-
-Example Schema Definitions data table
-
-
-## Need any help ?
-
-Our team is happy to help! If you struggle with migration or need help on using the multi-tenancy, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
diff --git a/docs/versioned_docs/version-0.3.x/permify-overview/_category_.json b/docs/versioned_docs/version-0.3.x/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/versioned_docs/version-0.3.x/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.3.x/permify-overview/authorization-service.md b/docs/versioned_docs/version-0.3.x/permify-overview/authorization-service.md
deleted file mode 100644
index 0810c6c2..00000000
--- a/docs/versioned_docs/version-0.3.x/permify-overview/authorization-service.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# What is Authorization Service?
-
-Authorization is an important part of software development. There are many different ways to implement authorization, but it's important for all apps to have some form of it in order to protect the user from malicious actors and unauthorized access attempts.
-
-An authorization service is a module that allows you to manage access to your application and ease the development and maintenance of your authorization system. It works in run time and respond to all authorization questions from any of your apps.
-
-
-
-[Permify] is a fully open source authorization service that offers a variety of binding and crafting options to secure your applications.
-
-[Permify]: https://github.com/Permify/permify
-
-## Why should I use Authorization Service instead of doing from scratch?
-
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch. You can started quickly with a simple API that you can easily integrate into your application to move and iterate faster.
-
-### Do Not Reinvent The Wheel
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps. Building a scalable and robust authorization system is hard and needs a quite engineering time. Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period. Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services.
-
-[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-
-### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group. Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time. Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
-
-### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road. Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product. Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production. After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
-
-### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security. Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
-
-## Cases that can benefit from An Authorization Service:
-
-- If you already have an identity/auth solution and want to plug in fine-grained authorization on top of that.
-- If you want to create a unified access control mechanism to use across your individual applications.
-- If you want to make future-proof authorization system and don't want to spend engineering effort for it.
-- If you’re managing authorization for growing micro-service infrastructure.
-- If your authorization logic is cluttering your code base.
-- If your data model is getting too complicated to handle your authorization within the service.
-- If your authorization is growing too complex to handle within code or API gateway.
-
diff --git a/docs/versioned_docs/version-0.3.x/permify-overview/infrastructure.md b/docs/versioned_docs/version-0.3.x/permify-overview/infrastructure.md
deleted file mode 100644
index 9cc9733c..00000000
--- a/docs/versioned_docs/version-0.3.x/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,50 +0,0 @@
-
-# Where does Permify fit into your environment?
-
-Permify is a simply GRPC service that responsible for managing and authorization in your environment. This section shows where and how does Permify fit into your environment with examining Permify's architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## Architecture
-
-Permify stores access control relations on a database you choose and performs authorization checks based on the stored relations. We called that database Write Database - **WriteDB** - and it behaves as a centralized data source for your authorization system.
-
-You can model your authorization with Permify's DSL - Permify Schema and your applications can talk to Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data, or make changes to data stored in WriteDb.
-
-
-
-### Permify with Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization. Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications. See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important. As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/versioned_docs/version-0.3.x/permify-overview/intro.md b/docs/versioned_docs/version-0.3.x/permify-overview/intro.md
deleted file mode 100644
index 8c58eaac..00000000
--- a/docs/versioned_docs/version-0.3.x/permify-overview/intro.md
+++ /dev/null
@@ -1,114 +0,0 @@
----
-sidebar_position: 1
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is an **open-source authorization service** for creating and maintaining fine-grained authorizations in your applications.
-
-With Permify you can easily structure your authorization model, store authorization data in a database you prefer, and interact with Permify API to handle all authorization queries from any of your applications.
-
-Permify is inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-## Key Features
-
-🛡️ **Production ready** authorization API that serve as **gRPC** and **REST**
-
-🔮 Domain Specific Authorization Language - Permify Schema - to **easily model** your authorization
-
-🔐 Database Configuration to store your permissions **in house** with **high availability**
-
-✅ Perform access control checks and get answers **down to 10ms** with **parallel graph engine**
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf)
-
-⚙️ Create custom permissions for your **tenants**, and manage them in single place with **Multi Tenancy**
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin]
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Getting Started
-
-In Permify, authorization divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify [Store Authorization Data] as relations.
-- Perform an [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../../getting-started/modeling
-[Store Authorization Data]: ../../getting-started/sync-data
-[Access Checks]: ../../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want trying out and examine it instantly,
-
-**Looking for Permify Managed Service?** See our [pricing plans](https://permify.co/pricing/).
-
-
-
-## Roadmap
-
-You can find Permify's Public Roadmap [here](https://github.com/orgs/Permify/projects/1)!
-
-## Community & Support
-
-We would love to hear from you :heart:
-
-You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
-
-For feature requests, bugs, or any improvements you can always open an issue.
-
-### Want to Contribute? Here are the ways to contribute to Permify
-
-* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
-* **Improve documentation:** Alongside our codebase, documentation one of the most significant part in our open-source journey. We're trying to give the best DX possible to explain ourselfs and Permify. And you can help on that with importing resources or adding new ones.
-* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
-
-You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
-
-## Communication Channels
-
-If you like Permify, please consider giving us a :star:
-
-
-
-## Need any help on Authorization ?
-
-Our team is happy to help you anything about authorization. Moreover, if you'd like to learn more about using Permify in your app or have any questions, [schedule a call with one of our founders](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/playground.md b/docs/versioned_docs/version-0.3.x/playground.md
deleted file mode 100644
index 00947b27..00000000
--- a/docs/versioned_docs/version-0.3.x/playground.md
+++ /dev/null
@@ -1,74 +0,0 @@
----
-sidebar_position: 6
----
-
-# Using Permify Playground
-
-You can use our [Playground] to create and test your authorization in a browser. Our playground consists 4 sections; Authorization Model, Visualizer, Authorization Data and Enforcement. Let's examine these sections by following a simple example.
-
-[Playground]: https://play.permify.co/
-
-## Authorization Model
-
-You can create your authorization model in this section with using Permify authorization language, Permify Schema. You can define your entities, relations between them and access control decisions with using Permify Schema. We already have a couple of use cases and example that you can choose to see how authorization can be structured with Permify Schema. Also, you can check our docs to learn more about how to model authorization in Permify.
-
-To demonstrate how playground works, let's choose the "empty" option from our dropdown to create a simple authorization model as follows:
-
-
-
-We have 2 permissions these are editing repository and deleting repository. Repository has parent child relation with organizations. Lastly organizations can have organizational wide roles such as admin and member. After completing your authorization model you can just save it with hitting the save button and start testing it.
-
-## Visualizer
-
-We get loads of feedback about the observability and reasonability of the authorization model across teams and colleagues. So we put a simple visualizer that shows how your authorization structure looks at a high level. In particular, you can examine relations between entities and their permissions. Here is a visualization for example model that we created above.
-
-
-
-## Authorization Data
-
-You can create sample authorization data to test your authorization logic. In Permify, authorization data stored as relation tuples and these tuples stored in a database that you preferred. The basic relation tuple takes the form of:
-
-`entity # relation @ user`
-
-So the entity can be any entity that you defined in your model. If we look up our example it can be an organization or repository (since the user is empty). The relation can be one of the defined relations in the selected entity. Lastly, the user is basically the user or user set in our system. Let's say we want make user 1 admin in organization 1 then we need to create an example relational tuple according to our model as follows:
-
-`organization:1#admin@user:1`
-
-To create a relation tuple in playground just hit the "new" button and a pop up will open.
-
-
-
-You can choose entity, relation and the subject (user or user set) with entering identifier to create sample data. Let's create the relation tuple `organization:1#admin@user:1` as follows.
-
-
-
-And this created tuple shown in the Authorization Data section as follows.
-
-
-
-Let's add one more relation tuple to perform a sample access check. I want to add repository:1 into organization:1 as follows:
-
-
-
-Created relational tuple after this will be: "repository:1#parent@organization:1#..." We used “...” when subject type is different from user entity. #… represents a relation that does not affect the semantics of the tuple.
-
-## Enforcement ( Access Checks)
-Finally as we have a sample data lets perform an access check from the right below. Let's check whether user:1 can edit the repository:1. Since organization:1 is parent of repository:1 ( `repository:1#parent@organization:1#...` ) and user:1 has an admin role in organization:1 ( `organization:1#admin@user:1` ) user:1 should allow to edit the repository:1 because the we define rule of the edit permission action as:
-
-`action edit = owner or parent.admin`
-
-which parent.admin indicates admin in the organization that repository belongs to. So let's type **"can user:1 edit repository:1"** and hit the check button to get result.
-
-
-
-
-Let's try to get unauthorized result. Type "can user:1 delete repository:1" on the question input. Since only owners can delete the repository this access check will result as unauthorized.
-
-
-
-As we seen above this is how you can model your authorization and test it with sample data in Permify Playground. Check out our docs for different modeling use cases, creating and storing relational tuples and more.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/reference/_category_.json b/docs/versioned_docs/version-0.3.x/reference/_category_.json
deleted file mode 100644
index b55d99d8..00000000
--- a/docs/versioned_docs/version-0.3.x/reference/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Reference",
- "position": 8,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.3.x/reference/configuration.md b/docs/versioned_docs/version-0.3.x/reference/configuration.md
deleted file mode 100644
index 205e59f1..00000000
--- a/docs/versioned_docs/version-0.3.x/reference/configuration.md
+++ /dev/null
@@ -1,312 +0,0 @@
-# Configuration File
-
-Permify offers various options for configuring your Permify API Server.
-
-Here is the example configuration YAML file with glossary below. You can also find this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-
-***Example config.yaml file***
-
-```yaml
-server:
- http:
- enabled: true
- port: 3476
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
- grpc:
- port: 3478
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
-
-logger:
- level: 'info'
-
-profiler:
- enabled: true
- port: 6060
-
-authn:
- method: preshared
- enabled: false
- keys: []
-
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://localhost:9411/api/v2/spans'
- enabled: true
-
-meter:
- exporter: 'otlp'
- endpoint: 'localhost:4318'
- enabled: true
-
-service:
- circuit_breaker: false
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
- permission:
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
- relationship:
-
-database:
- engine: 'postgres'
- uri: 'postgres://user:password@host:5432/db_name'
- auto_migrate: false
- max_open_connections: 20
- max_idle_connections: 1
- max_connection_lifetime: 300s
- max_connection_idle_time: 60s
- garbage_collection:
- enable: true
- interval: 3m
- timeout: 3m
- window: 720h
- number_of_threads: 1
-```
-
-## Options
-
-server | Server Configurations
-
-
-#### Definition
-Server options to run Permify. (`grpc` and `http` available for now.)
-
-#### Structure
-```
-├── server
- ├── (`grpc` or `http`)
- │ ├── enabled
- │ ├── port
- │ └── tls
- │ ├── enabled
- │ ├── cert
- │ └── key
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|---------|
-| [x] | [ server_type ] | - | server option type can either be `grpc` or `http`.
-| [ ] | enabled (for server type) | true | switch option for server. |
-| [x] | port | - | port that server run on.
-| [x] | tls | - | transport layer security options. |
-| [ ] | enabled (for tls) | false | switch option for tls |
-| [ ] | cert | - | tls certificate path. |
-| [ ] | key | - | tls key pat |
-
-
-
-#### Definition
-
-You can choose to authenticate users to interact with Permify API.
-
-There are 2 authentication method you can choose:
-
-* [Pre Shared Keys](#pre-shared-keys)
-* [OpenID Connect](#openid-connect)
-
-#### Pre Shared Keys
-
-On this method, you must provide a pre shared keys in order to identify yourself.
-
-#### Structure
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── keys
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|---------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`.
-| [ ] | enabled | true | switch option authentication config |
-| [x] | keys | - | Private key/keys for server authentication. Permify does not provide this key, so it must be generated by the users.
-
-#### OpenID Connect
-
-Permify supports OpenID Connect (OIDC). OIDC provides an identity layer on top of OAuth 2.0 to address the shortcomings of using OAuth 2.0 for establishing identity.
-
-With this authentication method, you be able to integrate your existing Identity Provider (IDP) to validate JSON Web Tokens (JWTs) using JSON Web Keys (JWKs). By doing so, only trusted tokens from the IDP will be accepted for authentication.
-
-#### Structure
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── client-id
-| ├── issuer
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|---------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`.
-| [ ] | enabled | false | switch option authentication config |
-| [x] | client_id | - | This is the client ID of the application you're developing. It is a unique identifier that is assigned to your application by the OpenID Connect provider, and it should be included in the JWTs that are issued by the provider.
-| [x] | issuer | - | This is the URL of the provider that is responsible for authenticating users. You will use this URL to discover information about the provider in step 1 of the authentication process. |
-
-
-
-
-
-
-tracer | Tracing Configurations
-
-
-#### Definition
-Permify integrated with [jaeger] , [signoz] and [zipkin] tacing tools to analyze performance and behavior of your authorization when using Permify.
-#### Structure
-```
-├── tracer
-| ├── exporter
-| ├── endpoint
-| ├── enabled
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|---------|
-| [x] | exporter | - | Tracer exporter, the options are `jaeger`, `signoz` and `zipkin`
-| [x] | endpoint | - | export uri for tracing data. |
-| [ ] | enabled | false | switch option for tracing.
-
-
-
-#### Definition
-Configurations for the database that points out where your want to store your authorization data (relation tuples, audits, decision logs, authorization model)
-
-#### Structure
-```
-├── database
-| ├── engine
-| ├── uri
-| ├── auto_migrate
-| ├── max_open_connections
-| ├── max_idle_connections
-| ├── max_connection_lifetime
-| ├── max_connection_idle_time
-| ├──garbage_collection
-| ├──enable: true
-| ├──interval: 3m
-| ├──timeout: 3m
-| ├──window: 720h
-| ├──number_of_threads: 1
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|---------------------------------|---------|---------|
-| [x] | engine | memory | Data source. Permify supports **PostgreSQL**(`'postgres'`) for now. Contact with us for your preferred database.
-| [x] | uri | - | Uri of your data source. |
-| [ ] | auto_migrate | true | When its configured as false migrating flow won't work
-| [ ] | max_open_connections | 20 | Configuration parameter determines the maximum number of concurrent connections to the database that are allowed.
-| [ ] | max_idle_connections | 1 | Determines the maximum number of idle connections that can be held in the connection pool.
-| [ ] | max_connection_lifetime | 300s | Determines the maximum lifetime of a connection in seconds.
-| [ ] | max_connection_idle_time | 60s | Determines the maximum time in seconds that a connection can remain idle before it is closed.
-| [ ] | enable (for garbage collection) | false | Switch option for garbage collection.
-| [ ] | interval | 3m | Determines the run period of a Garbage Collection operation.
-| [ ] | timeout | 3m | Sets the duration of the Garbage Collection timeout.
-| [ ] | window | 720h | Determines how much backward cleaning the Garbage Collection process will perform.
-| [ ] | number_of_threads | 1 | Limits how many threads Garbage Collection processes concurrently with.
-
-
-
-#### Definition
-pprof is a performance profiler for Go programs. It allows developers to analyze and understand the performance characteristics of their code by generating detailed profiles of program execution
-#### Structure
-```
-├── meter
-| ├── enabled
-| ├── port
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|---------|
-| [ ] | enabled | true | switch option for profiler.
-| [x] | port | - | port that profiler runs on *(default: 6060)* |
-
-
-
-
-[jaeger]: https://www.jaegertracing.io/
-[zipkin]: https://zipkin.io/
-[signoz]: https://signoz.io/
diff --git a/docs/versioned_docs/version-0.3.x/reference/glossary.md b/docs/versioned_docs/version-0.3.x/reference/glossary.md
deleted file mode 100644
index ccefde53..00000000
--- a/docs/versioned_docs/version-0.3.x/reference/glossary.md
+++ /dev/null
@@ -1,45 +0,0 @@
----
-sidebar_position: 1
----
-
-# Glossary
-
-This section explains the basic concepts that commonly mentioned in Permify, as well as in this document. You can find the whole context on right menu.
-
-## Google Zanzibar (or just Zanzibar)
-
-[Google Zanzibar] is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
-
-Google published Zanzibar back in 2019, and in a short time it gained attention quickly. In fact some big tech companies started to shift their legacy authorization structure to Zanzibar style systems. Additionaly, Zanzibar based solutions increased over the time. All disclosure; [Permify] is an authorization system based on Zanzibar.
-
-For more about Zanzibar check our blog post, [Google Zanzibar In A Nutshell]
-
-[Google Zanzibar In A Nutshell]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-[Google Zanzibar]: https://research.google/pubs/pub48190/
-[Permify]: https://permify.co/
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it, we called it Permify Schema. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager etc. You can define your entities, relations between them and access control decisions with using Permify Schema.
-
-It includes set-algebraic operators such as inter- section and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-## Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. The simplest form of relational tuple structured as `entity # relation @ user` and each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-## Write Database - WriteDB
-
-Permify stores your relational tuples (authorization data) in **WriteDB**. You can configure it **WriteDB** when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-## Relationship Based Access Control (ReBAC)
-
-ReBAC is an access control model that defines permissions based on the relationships between entities and subjects of your system. Although ReBAC is best known for social networks because its core concept is about the network of relations, it can be applied beyond that.
-
-Check out [Relationship Based Access Control](https://permify.co/post/relationship-based-access-control-rebac/) post learn more about ReBAC and its common usage.
-
-## Domain Specific Language (DSL)
-
-Domain Specific Language is a language that specialized to a particular application domain. Permify has its DSL basically an authorization language which you can model and structure your authorization with it. We called it Permify Schema.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/reference/snap-tokens.md b/docs/versioned_docs/version-0.3.x/reference/snap-tokens.md
deleted file mode 100644
index 47303667..00000000
--- a/docs/versioned_docs/version-0.3.x/reference/snap-tokens.md
+++ /dev/null
@@ -1,50 +0,0 @@
-
-# Snap Tokens & Zookies
-
-A Snap Token is a token that consists of an encoded timestamp, which is used to ensure fresh results in access control checks.
-
-## Why you should use Snap Tokens ?
-
-Basically, you should use snap tokens both for consistency and performance. The main goal of Permify is to provide an authorization system that ensures excellent performance that can handle millions of requests from different environments while ensuring data consistency.
-
-Performance standards can be achievable with caching. In Permify, the cache mechanism eliminates re-computing of access control checks that once occurred, unless any relationships of resources don't change.
-
-Still, all caches suffer from the risk of becoming stale. If some schema update happens, or relations change then all of the caches should be updated according to it to prevent false positive or false negative results.
-
-Permify avoids this problem with an approach of snapshot reads. Simply, it ensures that access control is evaluated at a consistent point in time to prevent inconsistency.
-
-To achieve this, we developed tokens called Snap Tokens that consist of a timestamp that is compared in access checks to ensure that the snapshot of the access control is at least as fresh as the resource timestamp - basically its stored snap token.
-
-## How to use Snap Tokens
-
-Snap Tokens used in endpoints to represent the snapshot and get fresh results of the API's. It mainly used in [Write API] and [Check API].
-
-The general workflow for using snap token is getting the snap token from the reponse of Write API request - basically when writing a relational tuple - then mapped it with the resource. One way of doing that is storing snap token in the additional column in your relational database.
-
-Then this snap token can be used in endpoints. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-```json
-{
- "schema_version": "ce8siqtmmud16etrelag",
- "snap_token": "gp/twGSvLBc=",
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- },
-}
-```
-
-[Write API]: ../../api-overview/relationship/write-relationships
-[Check API]: ../../api-overview/permission/check-api
-
-#### All endpoints that used snap token
-
-- [Write API](../../api-overview/relationship/write-relationships)
-- [Check API](../../api-overview/permission/check-api)
-- [Expand API](../../api-overview/permission/expand-api)
-- [Schema Lookup](../../api-overview/permission/schema-lookup)
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/reference/tracing.md b/docs/versioned_docs/version-0.3.x/reference/tracing.md
deleted file mode 100644
index 9f6a3193..00000000
--- a/docs/versioned_docs/version-0.3.x/reference/tracing.md
+++ /dev/null
@@ -1,52 +0,0 @@
-
-# Tracing Tools
-
-Permify has integrations with some of popular tracing tools to analyze performance and behavior of your authorization. These are:
-
-- [Jaeger](https://www.jaegertracing.io/)
-- [Signoz](https://signoz.io/)
-- [Zipkin](https://zipkin.io/)
-
-## Usage
-
-### Set Up
-
-Adding one of these tracing tools to your authorization system is quite simple, you just need to define it in the Permify configuration file as **tracer**.
-
-```yaml
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-```
-- ***exporter***: enter the tool name that you want to use. `jaeger` , `signoz` and `zipkin`.
-- ***endpoint***: export url for tracing data.
-- ***disabled***: switch option for tracing.
-
-**Example YAML configuration file**
-
-```yaml
-app:
- name: ‘permify’
-http:
- port: 3476
-logger:
- log_level: ‘debug’
- rollbar_env: ‘permify’
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-database:
- write:
- connection: 'postgres'
- database: 'morf-health-demo'
- uri: 'postgres://postgres:SphU4Uf3QXNntT@permify.us-east-1.rds.amazonaws.com:5432'
- pool_max: 2
-```
-
-After running Permify in your server, you should run Zipkin as well. If you're using docker here is the docker pull request for Zipkin:
-
-```
-docker run -d -p 9411:9411 openzipkin/zipkin
-```
diff --git a/docs/versioned_docs/version-0.3.x/use-cases.md b/docs/versioned_docs/version-0.3.x/use-cases.md
deleted file mode 100644
index 6fae082c..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases.md
+++ /dev/null
@@ -1,20 +0,0 @@
----
-id: use-cases
-title: Common Use Cases
-slug: /use-cases
----
-
-# Common Use Cases
-
-Common modeling patterns and uses cases we have seen so far from the users from small startups with simple RBAC to multi-regional enterprises that run tens of Permify instances with deeply nested relationships.
-
-:::success Missing a specific use case?
-No problem, let's discuss it together! just open an [issue](https://github.com/Permify/permify/issues) about it or join our conversation at [discord](https://discord.gg/n6KfzYxhPp)!
-:::
-
-```mdx-code-block
-import {CaseList} from '@site/src/components/Case';
-import list from './use-cases/_list.json';
-
-
-```
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/_category_.json b/docs/versioned_docs/version-0.3.x/use-cases/_category_.json
deleted file mode 100644
index 9f9db2d4..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Common Use Cases",
- "position": 8,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/_list.json b/docs/versioned_docs/version-0.3.x/use-cases/_list.json
deleted file mode 100644
index 81aacd1a..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/_list.json
+++ /dev/null
@@ -1,38 +0,0 @@
-[
- {
- "id": 1,
- "title": "Role Based Access Control (RBAC)",
- "description": "Want to implement role to your application ? Define an entity and manage your roles throught your applications.",
- "link": "./simple-rbac"
- },
- {
- "id": 2,
- "title": "Nested Hierarchies",
- "description": "Define a hierarchy of roles and permissions to inherit permissions from higher level roles.",
- "link": "./nested-hierarchies"
- },
- {
- "id": 3,
- "title": "Organizational",
- "description": "Group your users by organization with giving them access organizational-wide resources.",
- "link": "./organizational"
- },
- {
- "id": 4,
- "title": "User Groups & Teams permissions",
- "description": "Organize permissions based on groupings of users or resources.",
- "link": "./user-groups"
- },
- {
- "id": 5,
- "title": "Sharing & Collaboration",
- "description": "For sharing resources with other users, you can use the invite action.",
- "link": "./sharing"
- },
- {
- "id": 6,
- "title": "Ownership",
- "description": "Ownership is a special case of sharing where the owner of a resource has full access to it.",
- "link": "./ownership"
- }
-]
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/nested-hierarchies.md b/docs/versioned_docs/version-0.3.x/use-cases/nested-hierarchies.md
deleted file mode 100644
index 787a5acc..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/nested-hierarchies.md
+++ /dev/null
@@ -1,73 +0,0 @@
-
-# Nested Hierarchies
-
-This use case shows solving deeply nested hierarchies with [Permify Schema]. We have a unique **action** usage for nested hierarchies, where parent and child entities can share permissions between them. Let's follow the below team project authorization model to examine this case.
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organization user types
- relation admin @user
-}
-
-entity team {
-
- //refers to organization that team belongs to
- relation org @organization
-
- // Only the organization administrator can edit
- action edit = org.admin
-}
-
-entity project {
-
- //refers to team that project belongs to
- relation team @team
-
- // This action responsible for nested permission inheritance
- // team.edit refers edit action on the team entity which we defined above
- // Semantics of this is: Only the organization administrator, who has the
- // team, to which this project belongs can edit.
- action edit = team.edit
-}
-```
-
-## Sample Relational Tuples
-
-organization:1#admin@user:1
-
-team:1#org@organization:1#...
-
-project:1#team@team:1#...
-
-Lets assume we created above [relational tuples]. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** result since the `user:1` is organizational admin and `project:1` belongs to `team:1`, which belongs to `organization:1`.
-
-[relational tuples]: ../getting-started/sync-data.md
-
-Let's break down this case,
-
-```perm
-entity project {
-
- relation team @team
-
- action edit = team.edit
-}
-```
-
-Above `team.edit` points out the **edit** action in the **team** (that project belongs to).
-
-And edit action on the team entity: `action edit = org.admin` states that only **organization (which that team belongs to) admins** can edit. So our project inherits that action and conducts a result accordingly.
-
-If we roll back to our enforcement: `Can user:1 edit project:1?` gives **Allow** result, because user:1 is admin in an organization that the projects' parent team belongs to.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/organizational.md b/docs/versioned_docs/version-0.3.x/use-cases/organizational.md
deleted file mode 100644
index 836945f6..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/organizational.md
+++ /dev/null
@@ -1,149 +0,0 @@
-
-
-# Organization Specific Resources
-
-Group your users by organization with giving them access organizational-wide resources. In this use case we'll follow a simplified version of Github's access control that shows how to model basic repository push, read and delete permissions with our authorization language DSL, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents user of this repository
- relation owner @user
-
- // permissions
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 3 entities,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that user and repositories belongs.
-
-- `repository`, represents a repository in a github.
-
-### Relations
-
-To define relation, **relations** needed to be created as entity attributes.
-
-#### organization entity
-
-In our schema we defined 2 relation in organization entity, respectively; ``admin`` and ``member``
-
-```perm
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-``admin`` indicates that the user got an administrative role in that organization and with the same logic ``member`` represents the default user that belongs to that organization.
-
-#### repository entity
-
-Repository entities have 2 relations, these are ``parent`` and ``owner``. Both of these relations represents actual database relations with other entities rather than a role-based approach likewise to the **organization** entity above.
-
-```perm
-entity repository {
-
- relation parent @organization
- relation owner @user
-
-}
-```
-
-``parent`` relation represents the parent organization with a repository. And ``owner`` represents the specific user, the repository's owner.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### repository actions
-
-In our schema, we examined one of the main functionalities can the user make on any GitHub repository. These are pushing to the repo, reading & viewing the repo, and deleting that repo.
-
-We can say only,
-
-- Repository owners can ``push`` to that repo.
-- Repository owners, who also need to have an administrative role or be an owner of the parent organization, can ``read``.
-- Repository owners or administrative roles in an organization can ``delete`` the repository.
-
-```
-entity repository {
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-Since ``parent` represents the parent organization of repository. It can reach repositories parent organization relations with comma. So,
-
-- ``parent.admin``
-indicates admin role on organization
-
-- ``parent.member``
-indicates member of that organization.
-
-## Example Relational Tuples
-
-organization:2#admin@user:daniel
-
-organization:54#member@user:ege
-
-organization:12#member@user:jack
-
-repository:34#parent@organization:54
-
-repository:68#owner@user:12
-
-repository:12#owner@user:46
-
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/ownership.md b/docs/versioned_docs/version-0.3.x/use-cases/ownership.md
deleted file mode 100644
index f7dc5b94..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/ownership.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# Ownership
-
-Granting privileges to the owner of the resource is a common pattern that many applications follow. Generally we want creators of the resource - document, post, comment etc - have superior power on that resource. Check out the below model see how ownership can be modeled with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity comment {
-
- // represents comment's owner
- relation owner @user
-
- // permissions
- action edit = owner
- action delete = owner
-}
-
-```
-
-## Sample Relational Tuples
-
-comment:2#owner@user:1
-
-comment:3#owner@user:51
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/sharing.md b/docs/versioned_docs/version-0.3.x/use-cases/sharing.md
deleted file mode 100644
index 4a97b41b..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/sharing.md
+++ /dev/null
@@ -1,40 +0,0 @@
-
-# Sharing & Collaboration
-
-Inviting a team member to a document, project or repository should be hassle free to model. In Permify you can achieve this with simply defining a invite action. Check out the below model block see how sharing can be modeled with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
- relation manager @user
-
-}
-
-entity project {
-
- // represents project's parent organization
- relation org @organization
-
- // represents owner of this project
- relation owner @user
-
- // invite permission
- action invite = org.admin or owner
-
-}
-
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/simple-rbac.md b/docs/versioned_docs/version-0.3.x/use-cases/simple-rbac.md
deleted file mode 100644
index 82767daa..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/simple-rbac.md
+++ /dev/null
@@ -1,128 +0,0 @@
----
-sidebar_position: 1
----
-
-# Role Based Access Control
-
-Want to implement role and permissions to your application ? Permify fully covers you at that point. Below example shows how to model simple role based access control for organizational roles and permissions with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
- //organization files access permissions
- action view_files = admin or manager or (member and not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 2 entities,
-
-- `user`, represents users (maybe corresponds as employees). This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, representing the organization the user (employees) belongs. It has several roles and permissions related to the specific resources such as organization files and vendor files.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles. In this example, we have 4 organizational wide roles, respectively; admin, manager, member, and agent.
-
-```perm
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
-}
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### organization actions
-
-In our schema, we define several actions for controlling access permissions on organization files and organization vendor's files.
-
-```perm
-entity organization {
-
- //organization files access permissions
- action view_files = admin or manager or (member and not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-let's take a look at some of the actions:
-
-- ``action edit_files = admin or manager``
-indicates that only the admin or manager has permission to edit files in the organization.
-
-- ``action view_files = admin or manager or (member and not agent)``
-indicates that the admin, manager, or members (without having the agent role) can view organization files.
-
-
-
-## Example Relational Tuples for this case
-
-organization:2#admin@user:daniel
-
-organization:5#member@user:ashley
-
-organization:17#manager@user:mert
-
-organization:21#agent@user:ege
-
-.
-.
-.
-
-For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.3.x/use-cases/user-groups.md b/docs/versioned_docs/version-0.3.x/use-cases/user-groups.md
deleted file mode 100644
index 597ab55b..00000000
--- a/docs/versioned_docs/version-0.3.x/use-cases/user-groups.md
+++ /dev/null
@@ -1,201 +0,0 @@
-
-# User Groups & Team Permissions
-
-This use case shows how to organize permissions based on groupings of users or resources. In this use case we'll follow a simple project management app with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- // represents owner or creator of the team
- relation owner @user
-
- // represents direct member of the team
- relation member @user
-
- // reference for organization that team belong
- relation org @organization
-
- // organization admins or owners can edit, delete the team details
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- // to invite someone you need to be admin and either owner or member of this team
- action invite = org.admin and (owner or member)
-
- // only owners can remove users
- action remove_user = owner
-
-}
-
-entity project {
-
- // references for team and organization that project belongs
- relation team @team
- relation org @organization
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 4 entity,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that contain teams.
-
-- `team`, represents teams, which belongs to a organization.
-
-- `project`, represents projects that belongs teams.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles.
-
-The organization entity has 2 relations ``admin`` and ``member`` users. Think of these as organizational-wide roles.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-#### team entity
-
-The eeam entity has its own relations respectively, ``owner``, ``member`` and ``org``
-
-```perm
-entity team {
-
- relation owner @user
- relation member @user
- relation org @organization
-
-}
-```
-
-#### project entity
-
-Project entity has ``team`` and ``org`` relations. Both these relations represents parent relationship with other entites, parent team and parent organization.
-
-```perm
-entity project {
-
- relation team @team
- relation org @organization
-
-}
-```
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### team actions
-
-- Only organization ***admin (admin role)*** and ***team owner*** can perform editing and deleting team spesific resources.
-
-- Moreover, for inviting a colleague to a team you must have ***admin role*** and either be a ***owner*** or ***member*** on that team.
-
-- To remove users in team you must be a ***owner*** of that team.
-
-And these rules reflects Permify Schema as:
-
-```perm
-entity team {
-
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- action invite = org.admin and (owner or member)
- action remove_user = owner
-
-}
-```
-
-#### project actions
-
-And there are the project actions below. It consists of checking access for basic operations such as viewing, editing, or deleting project resources.
-
-```perm
-entity project {
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Example Relational Tuples
-
-team:2#member@user:daniel
-
-team:54#owner@user:daniel
-
-organization:12#admin@user:jack
-
-organization:51#member@user:jack
-
-organiation:41#member@team:42#member
-
-project:35#team@team:34#....
-
-
-.
-.
-.
-.
-.
-
-
-organization:41#member@team:42#member
-
-**--> represents members of team 42 also members in organization 41**
-
-project:35#team@team:34#....
-
-**--> represents project 54 is in team 34**
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/api-overview.md b/docs/versioned_docs/version-0.4.x/api-overview.md
deleted file mode 100644
index 64e4a6d1..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview.md
+++ /dev/null
@@ -1,83 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Overview
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [RelationshipService]: Authorization data operations such as creating, deleting and reading relational tuples.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ./permission
-[RelationshipService]: ./relationship
-[SchemaService]: ./schema
-[TenancyService]: ./tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](./api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Relationships](./api-overview/relationship/write-relationships.md)
-- Read relation tuples and filter them with [Read API](./api-overview/relationship/read-api.md)
-- Check access with [Check API](./api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](./api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](./api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/relationship/delete-relationships.md)
-- Expand schema actions with [Expand API](./api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](./api-overview/watch/watch-changes.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our [documentation](https://docs.permify.co/docs/reference/configuration). We used [Token bucket](https://en.wikipedia.org/wiki/Token_bucket) algorithm for rate limiting.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/permission/_category_.json
deleted file mode 100644
index f91d5b46..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Permission Service",
- "position": 3,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/check-api.md b/docs/versioned_docs/version-0.4.x/api-overview/permission/check-api.md
deleted file mode 100644
index ab24405c..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/check-api.md
+++ /dev/null
@@ -1,192 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
-
-In Permify, you can perform two different types access checks,
-
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **subject based** authorization checks, in form of `Which resources can user U edit ?`
-
-In this section we'll look at the resource based check request of Permify. You can find subject based access checks in [Entity (Data) Filtering] section.
-
-[Entity (Data) Filtering]: ../lookup-entity
-
-## Request
-
-**Path:** POST /v1/permissions/check
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. , see more details on [Contextual Tuples](../../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionCheckRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "can": "RESULT_ALLOWED",
- "remaining_depth": 0
-}
-```
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism.
-
-## How Access Decisions Evaluated?
-
-Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
-
-In high level, access of an subject related with the relationships created between the subject and the resource. You can define this relationships in Permify Schema then create and store them as relational tuples, which is basically your authorization data.
-
-Permify Engine to compute access decision in 2 steps,
-1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
-2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
-
-Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
-
-[relational tuples]: ../../getting-started/sync-data.md
-[Permify Schema]: ../../getting-started/modeling.md
-
-When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity document {
-
- // represents documents parent organization
- relation parent @organization
-
- // represents owner of this document
- relation owner @user
-
- // permissions
- action edit = parent.admin or owner
- action delete = owner
-}
-```
-
-Which has a directed graph as follows:
-
-
-
-As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
-
-**Q1:** Get the owners of the `document:12`.
-
-**Q2:** Get admins of the organization where `document:12` belongs to.
-
-Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
-
-Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
-
-## Latency & Performance
-
-With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
-
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../reference/cache.md)
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/expand-api.md b/docs/versioned_docs/version-0.4.x/api-overview/permission/expand-api.md
deleted file mode 100644
index d742de2e..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/expand-api.md
+++ /dev/null
@@ -1,314 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-
-Retrieve all subjects (users and user sets) that have a relationship with given entity and permission
-
-Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
-
-:::caution When To Use ?
-Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
-
-It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
-:::
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), &v1.PermissionExpandRequest{
- TenantId: "t1",
- Metadata: &v1.PermissionExpandRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "",
- "snap_token": ""
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "push"
-}'
-```
-
-
-
-## Example Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:** POST /v1/tenants/{tenant_id}/permissions/expand
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”. |
-| [x] | permission | string | - | The permission the user wants to perform on the resource |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-### Expand Push Action
-
-Request
-
-
-
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-entity.md b/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-entity.md
deleted file mode 100644
index 77c9f1c6..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-entity.md
+++ /dev/null
@@ -1,216 +0,0 @@
----
-title: Entity (Data) Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Entity Filtering
-
-Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So, we provide 2 separate endpoints for data filtering check request,
-
-- [/v1/permissions/lookup-entity](#lookup-entity)
-- [/v1/permissions/lookup-entity-stream](#lookup-entity-streaming)
-
-## Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
-
-**POST** /v1/permissions/lookup-entity
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- EntityType: "document",
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupEntity({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity_type: "document",
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response.entity_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type":"user",
- "id":"1"
- }
-}'
-```
-
-
-
-## How Lookup Operations Evaluated
-
-We explicitly designed reverse lookup to be more performant with changing its evaluation pattern. We do not query all the documents in bulk to get response, instead of this Permify first finds the necessary relations with given subject and the permission/action in the API call. Then query these relations with the subject id this way we reduce lots of additional queries.
-
-To give an example,
-
-```jsx
-entity user {}
-
-entity organization {
- relation admin @user
-}
-
-entity container {
- relation parent @organization
- relation container_admin @user
- action admin = parent.admin or container_admin
-}
-
-entity document {
- relation container @container
- relation viewer @user
- relation owner @user
- action view = viewer or owner or container.admin
-}
-```
-
-Lets say we called (reverse) lookup API to find the documents that user:1 can view. Permify first finds the relations that linked with view action, these are
-
-- `document#viewer`
-- `document#owner`
-- `organization#admin`
-- `container#``container_admin`
-
-Then queries each of them with `user:1.`
-
-### Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-**POST** /v1/permissions/lookup-entity-stream
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-
-
-
-```go
-str, err: = client.Permission.LookupEntityStream(context.Background(), &v1.PermissionLookupEntityRequest {
- Metadata: &v1.PermissionLookupEntityRequestMetadata {
- SnapToken: "",
- SchemaVersion: ""
- Depth: 50,
- },
- EntityType: "document",
- Permission: "view",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-
-// handle stream response
-for {
- res, err: = str.Recv()
-
- if err == io.EOF {
- break
- }
-
- // res.EntityId
-}
-```
-
-
-
-
-```javascript
-const permify = require("@permify/permify-node");
-const {PermissionLookupEntityStreamResponse} = require("@permify/permify-node/dist/src/grpc/generated/base/v1/service");
-
-function main() {
- const client = new permify.grpc.newClient({
- endpoint: "localhost:3478",
- })
-
- let res = client.permission.lookupEntityStream({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entityType: "document",
- permission: "view",
- subject: {
- type: "user",
- id: "1"
- }
- })
-
- handle(res)
-}
-
-async function handle(res: AsyncIterable) {
- for await (const response of res) {
- // response.entityId
- }
-}
-```
-
-
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-subject.md b/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-subject.md
deleted file mode 100644
index 27ab6128..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/lookup-subject.md
+++ /dev/null
@@ -1,107 +0,0 @@
----
-title: Subject Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Filtering
-
-Lookup Subject endpoint lets you ask questions in form of **“Which subjects can do action Y on entity:X?”**. As a response of this you’ll get a subject results in a format of string array.
-
-So, we provide 1 endpoint for subject filtering request,
-
-- [/v1/permissions/lookup-subject](#lookup-subject)
-
-## Lookup Subject
-
-In this endpoint you'll get directly the IDs' of the subjects that are authorized in an array.
-
-**POST** /v1/permissions/lookup-subject
-
-| Required | Argument | Type | Default | Description |
-|----------|---------------------|----------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1 |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject_reference | object | - | the subject or subject reference who wants to take the action. It contains type and relation of the subject. |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSubject(context.Background(), &v1.PermissionLookupSubjectRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionLookupSubjectRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Permission: "edit",
- SubjectReference: &v1.RelationReference{
- Type: "user",
- Relation: "",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupSubject({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- Entity: {
- Type: "document",
- Id: "1",
- },
- permission: "edit",
- subject_reference: {
- type: "user",
- relation: ""
- }
-}).then((response) => {
- console.log(response.subject_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": ""
- },
- "entity": {
- type: "document",
- id: "1'
- },
- "permission": "edit",
- "subject_reference": {
- "type": "user",
- "relation": ""
- }
-}'
-```
-
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/permission/subject-permission.md b/docs/versioned_docs/version-0.4.x/api-overview/permission/subject-permission.md
deleted file mode 100644
index c2ff2eaf..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/permission/subject-permission.md
+++ /dev/null
@@ -1,128 +0,0 @@
----
-title: Subject Permission List
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Permission List
-
-The Subject Permission List endpoint allows you to inquire in the form of **“Which permissions user:x can perform on entity:y?”**. In response, you'll receive a list of permissions specific to the user for the given entity, returned in the format of a map.
-
-So, we provide 1 endpoint for subject permission list,
-
-- [/v1/permissions/subject-permission](#subject-permission)
-
-In this endpoint, you'll receive a map of permissions and their statuses directly. The structure is map[string]CheckResult, such as "sample-permission" -> "ALLOWED". This represents the permissions and their associated states in a key-value pair format.
-
-## Request
-
-**Path:** POST /v1/permissions/subject-permission
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | only_permission | bool | false | By default, the endpoint returns both permissions and relations associated with the user and entity. However, when the "only_permission" parameter is set to true, it returns only the permissions. | |
-| [ ] | contextual_tuples | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. , see more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.SubjectPermission(context.Background(), &v1.PermissionSubjectPermissionRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionSubjectPermissionRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- OnlyPermission: false,
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-```
-
-
-
-
-```javascript
-client.permission.subjectPermission({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- onlyPermission: true,
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response);
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "only_permission": true,
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "results": [
- {
- "key": "delete",
- "value": "RESULT_ALLOWED"
- },
- {
- "key": "edit",
- "value": "RESULT_ALLOWED"
- }
- ]
-}
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/relationship/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/relationship/_category_.json
deleted file mode 100644
index bca5fd5e..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/relationship/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Relationship Service",
- "position": 2,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/relationship/delete-relationships.md b/docs/versioned_docs/version-0.4.x/api-overview/relationship/delete-relationships.md
deleted file mode 100644
index d63b7e68..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/relationship/delete-relationships.md
+++ /dev/null
@@ -1,103 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Relational Tuples
-
-You can delete any stored relation tuples with following API
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/relationships/delete
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Relationship.Delete(context.Background(), & v1.RelationshipDeleteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipDeleteRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.delete({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "filter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/relationship/read-api.md b/docs/versioned_docs/version-0.4.x/api-overview/relationship/read-api.md
deleted file mode 100644
index eb70b30c..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/relationship/read-api.md
+++ /dev/null
@@ -1,103 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id/relationships/read
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Relationship.Read(context.Background(), & v1.RelationshipReadRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.read({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/relationship/write-relationships.md b/docs/versioned_docs/version-0.4.x/api-overview/relationship/write-relationships.md
deleted file mode 100644
index 0646ff4e..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/relationship/write-relationships.md
+++ /dev/null
@@ -1,196 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Relationships
-
-In Permify, relations between your entities, objects and users stored as [relational tuples] in [writeDB]. Since relations and authorization data's are live instances these relational tuples can be created with an simple API call in runtime.
-
-When using Permify, the application client should update writeDB about the changes happening in entities or resources that are related to the authorization structure. If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [writeDB] up-to-date. Besides, each relational tuple should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as relation tuples and store in [writeDB].
-
-
-
-[relational tuples]: ../../../getting-started/sync-data
-[writeDB]: ../../../getting-started/sync-data#where-relational-tuples-used
-
-## Request
-
-So if user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` must be created by using **/v1/relationships/write** endpoint.
-
-**Path:** POST /v1/tenants/{tenant_id}/relationships/write
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "admin",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../../reference/snap-tokens) and how its avoiding stale cache.
-
-## Suggested Workflow
-
-The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-
-### Two Phase Commit Approach
-In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
-
-To give more concurrent example of this action, let's take a look at below createDocument function
-
-```go
-func CreateDocuments(db *gorm.DB) error {
-
- tx := db.Begin()
- defer func() {
- if r := recover(); r != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- }
- }()
-
- if err := tx.Error; err != nil {
- return err
- }
-
- if err := tx.Create(docs).Error; err != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteRelationships(...)
- return err
- }
-
- // if transaction successful, write relation tuple to Permify
- permify.WriteRelationships(...)
-
- return tx.Commit().Error
-}
-```
-The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-
-### Relationships that not stored in application database
-
-Although ownership generally stored in application databases, there are some relations that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
-
-For example, you can model a simple project management authorization in Permify as follows,
-
-```perm
-entity user {}
-
-entity team {
-
- relation owner @user
- relation member @user
-}
-
-entity project {
-
- relation team @team
- relation owner @user
-
- action view = team.member or team.owner or project.owner
- action edit = project.owner or team.owner
- action delete = project.owner or team.owner
-
-}
-```
-
-This **team member** relation won't need to be stored in the application database. Storing it only in Permify - WriteDB - is enough. In that situation, `WriteRelationships` can be performed in any logical place in your stack.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/schema/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/schema/_category_.json
deleted file mode 100644
index 8fd1e959..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/schema/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Schema Service",
- "position": 1,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/schema/write-schema.md b/docs/versioned_docs/version-0.4.x/api-overview/schema/write-schema.md
deleted file mode 100644
index 47a0e1ff..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/schema/write-schema.md
+++ /dev/null
@@ -1,93 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
-
-Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
-
-We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-:::
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-## Request
-
-**POST** /v1/tenants/{tenant_id}/schemas/write
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- TenantId: "t1",
- Schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- tenantId: "t1",
- schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "schema": "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/write"**
-
-**Example Request on Postman:**
-
-
-
-
-## Suggested Workflow For Schema Changes
-
-It's expected that your initial schema will eventually change as your product or system evolves
-
-As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
-
-A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database (your writeDB) unless you delete them with the [delete API](../relationship/delete-relationships.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
-
-We recommend applying the following pattern to safely handle schema changes:
-
-- Set up a central git repository that includes the schema.
-- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
-- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
-
-## Need any help ?
-
-Depending on the frequency and the type of the changes that you made on the schemas, this method may not be optimal for you - In such cases, we are open to exploring alternative solutions. Please feel free to [schedule a call with one of our engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/tenancy/_category_.json
deleted file mode 100644
index 9771416d..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Tenancy Service",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/create-tenant.md b/docs/versioned_docs/version-0.4.x/api-overview/tenancy/create-tenant.md
deleted file mode 100644
index 412ddaec..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/create-tenant.md
+++ /dev/null
@@ -1,55 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Create Tenant
-
-Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
-
-:::caution
-We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
-:::
-
-## Request
-
-**POST /v1/tenants/create**
-
-
-
-
-```go
-rr, err: = client.Tenancy.Create(context.Background(), & v1.TenantCreateRequest {
- Id: ""
- Name: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.create({
- id: "",
- name: ""
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'http://localhost:3476/v1/tenants/create' \
---header 'Content-Type: application/json' \
---data-raw '{
- "id": "",
- "name": ""
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/delete-tenant.md b/docs/versioned_docs/version-0.4.x/api-overview/tenancy/delete-tenant.md
deleted file mode 100644
index d8bd4a43..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/tenancy/delete-tenant.md
+++ /dev/null
@@ -1,44 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Tenant
-
-You can delete a tenant with following API.
-
-## Request
-
-**DELETE /v1/tenants/{id}**
-
-
-
-
-```go
-rr, err: = client.Tenancy.Delete(context.Background(), & v1.TenantDeleteRequest {
- Id: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.delete({
- id: "",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/watch/_category_.json b/docs/versioned_docs/version-0.4.x/api-overview/watch/_category_.json
deleted file mode 100644
index f65c41fd..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/watch/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Watch Service",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/api-overview/watch/watch-changes.md b/docs/versioned_docs/version-0.4.x/api-overview/watch/watch-changes.md
deleted file mode 100644
index 921fac97..00000000
--- a/docs/versioned_docs/version-0.4.x/api-overview/watch/watch-changes.md
+++ /dev/null
@@ -1,140 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Watch
-
-The Permify Watch API acts as a real-time broadcaster that shows changes in the relation tuples.
-
-The Watch API exclusively supports gRPC and works with PostgreSQL, given the track_commit_timestamp option is enabled. Please note, it doesn't support in-memory databases or HTTP communication.
-
-# Requirements
-
-- PostgreSQL database set up with track_commit_timestamp option enabled
-
-## Enabling track_commit_timestamp on PostgreSQL
-
-To ensure data consistency and synchronization between your application and Permify, enable track_commit_timestamp on
-your PostgreSQL server. This can be done by executing the following options in your PostgreSQL:
-
-### Option 1: SQL Command
-
-1. Open your PostgreSQL command line interface.
-2. Execute the following command:
-
- ```sql
- ALTER SYSTEM SET track_commit_timestamp = ON;
- ```
-
-3. Reload the configuration with the following command:
-
- ```sql
- SELECT pg_reload_conf();
- ```
-
-### Option 2: Editing postgresql.conf
-
-1. Find and open the postgresql.conf file in a text editor. Its location depends on your PostgreSQL installation. Common
- locations are:
- - Debian-based systems: /etc/postgresql/[version]/main/postgresql.conf
- - Red Hat-based systems: /var/lib/pgsql/data/postgresql.conf
-
-2. Add or modify the following line in the postgresql.conf file:
- ```
- track_commit_timestamp = on
- ```
-
-3. Save and close the postgresql.conf file.
-4. Reload the PostgreSQL configuration for the changes to take effect. This can be done via the PostgreSQL console:
- ```sql
- SELECT pg_reload_conf();
- ```
-
- Or if you have command line access, use:
-
- ```bash
- sudo service postgresql reload
- ```
-
-Please ensure you have the necessary permissions to execute these commands or modify the postgresql.conf file. Also, remember that changes in the postgresql.conf file will persist across restarts, while the SQL method may need to be reapplied depending on your PostgreSQL version and setup.
-
-:::info
-Important Configuration Requirement: To use the Watch API, it must be enabled in your configuration file. Add or modify the following lines:
-
-```yaml
-service:
- watch:
- enabled: true
-```
-
-:::
-
-## Request
-
-**Path:** POST /v1/watch/watch
-
-| Required | Argument | Type | Default | Description |
-|----------|------------|--------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | snap_token | string | - | specifies the starting point for broadcasting changes. If a snap_token is provided, all changes following that specific snapshot will be broadcasted. If a snap_token is not provided, the Watch API will broadcast all changes that occur after the Watch API is initiated., see more details on [Snap Tokens](../../reference/snap-tokens). |
-
-
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```go)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```javascript)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-## Response
-
-```json
-{
- "changes": {
- "tuple_changes": [
- {
- "operation": "OPERATION_CREATE",
- "tuple": {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "56",
- "relation": ""
- }
- }
- }
- ],
- "snap_token": "MgMAAAAAAAA="
- }
-}
-```
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or
-have any questions about this
-example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/comparision.md b/docs/versioned_docs/version-0.4.x/comparision.md
deleted file mode 100644
index a73e70f9..00000000
--- a/docs/versioned_docs/version-0.4.x/comparision.md
+++ /dev/null
@@ -1,38 +0,0 @@
----
-id: comparison
-title: Comparison Between Other Zanzibar implementations
----
-
-:::caution Note
-This comparison table shows the differentiation between authorization solutions based or inspired by Google Zanzibar paper. If you use any of these solutions and feel the information could be improved, feel free to reach out.
-:::
-
-## General Aspects
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|---------------------------------|------------|------------|-----------|-----------|
-| **Zanzibar Paper Faithfulness** | Medium | High | High | High |
-| **Scalability** | Medium | Medium | High | High |
-| **Consistency & Cache** | No Zookies | No Zookies | Supported | Supported |
-| **Dev UX** | Average | Average | High | High |
-
-## Feature Set
-
-- ✅ Supported, and ready to use with no added configuration or code
-- 🟡 Limited support and requires extra user-code to implement.
-- ⛔ Not officially supported or documented.
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|--------------------------|----------|---------|---------|---------|
-| **Check API** | ✅ | ✅ | ✅ | ✅ |
-| **Write API** | ✅ | ✅ | ✅ | ✅ |
-| **Read API** | ✅ | ✅ | ✅ | ✅ |
-| **Expand API** | ✅ | ✅ | ✅ | ✅ |
-| **Watch API** | ✅ | ✅ | ✅ | ✅ |
-| **RBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ReBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ABAC** | ⛔ | 🟡 | ✅ | ⛔ |
-| **Data Filtering** | ⛔ | ✅ | ✅ | ✅ |
-| **Multi Tenancy** | ⛔ | ✅ | ⛔ | ✅ |
-| **Testing & Validation** | ⛔ | 🟡 | ✅ | ✅ |
-| **Logging & Tracing** | 🟡 | ✅ | ✅ | ✅ |
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/_category_.json b/docs/versioned_docs/version-0.4.x/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/enforcement.md b/docs/versioned_docs/version-0.4.x/getting-started/enforcement.md
deleted file mode 100644
index 9a810df3..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/enforcement.md
+++ /dev/null
@@ -1,93 +0,0 @@
----
-sidebar_position: 4
----
-
-# Interacting With The API
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests, permission checks and their configurations.
-- [RelationshipService]: Authorization data operations such as creating, deleting and reading relational tuples.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ../../api-overview/permission
-[RelationshipService]: ../../api-overview/relationship
-[SchemaService]: ../../api-overview/schema
-[TenancyService]: ../../api-overview/tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](../api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Relationships](../api-overview/relationship/write-relationships.md)
-- Read relation tuples and filter them with [Read API](../api-overview/relationship/read-api.md)
-- Check access with [Check API](../api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](../api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](../api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](../api-overview/relationship/delete-relationships.md)
-- Expand schema actions with [Expand API](../api-overview/permission/expand-api.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration.md)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Performance & Latency
-
-Permify designed to answer these authorization questions efficiently and with minimal complexity while providing low latency with:
-- Using its parallel graph engine.
-- Storing the relationships between resources beforehand in Permify data store: [writeDB], rather than providing these relationships at “check” time.
-- Implementing permission caching to not recompute repeated permission checks, and in memory cache to store authorization schema.
-- Using [Snap Tokens](../../reference/snap-tokens) to achieve consistency and high performance in cache.
-
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisms](../reference/cache.md)
-
-[writeDB]: ../getting-started/sync-data.md
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our documentation.
-
-- doc: https://docs.permify.co/docs/reference/configuration
-- algorithm: https://en.wikipedia.org/wiki/Token_bucket
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/examples/_category_.json b/docs/versioned_docs/version-0.4.x/getting-started/examples/_category_.json
deleted file mode 100644
index b3e4f801..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/examples/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Example Permission Structures",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/examples/notion.md b/docs/versioned_docs/version-0.4.x/getting-started/examples/notion.md
deleted file mode 100644
index 9095d464..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/examples/notion.md
+++ /dev/null
@@ -1,548 +0,0 @@
-# Notion
-
-This is a schema definition of the authorization model for Notion, a popular productivity and organization tool.
-
-### Schema | [Open in playground](https://play.permify.co/?s=BsCvLmd4g81sB20XJZI5p)
-
-```perm
-entity user {}
-
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
-}
-
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
-}
-
-entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
-}
-
-entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
-}
-
-entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
-}
-
-entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
-}
-
-entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities, including users, workspaces, pages, databases, blocks, and integrations. It also includes several default roles, such as Admin, Bot, Guest, and Member. Here's a breakdown of the entities:
-
-### Entities & Relations
-
-- **`user`**: Represents a user in the system.
-
-- **`workspace`**: Represents a workspace in which users can collaborate. Each workspace has an owner, members, guests, and bots associated with it. The owner and admin users have permission to manage the workspace. Permissions are defined for creating pages, inviting members, viewing the workspace, and managing the workspace. The read and write permissions can be inherited by child entities.
-
-- **`page`**: Represents a page within a workspace. Each page is associated with a workspace and has a writer and readers. The read and write permissions are defined based on the writer and readers of the page and can be inherited from the workspace.
-
-- **`database`**: Represents a database within a workspace. Each database is associated with a workspace and has an editor and viewers. The read and write permissions are defined based on the editor and viewers of the database and can be inherited from the workspace. Permissions are also defined for creating and deleting databases.
-
-- **`block`**: Represents a block within a page or database. Each block is associated with a page or database and has an editor and commenters. The read and write permissions are defined based on the editor and commenters of the block and can be inherited from the database. Commenters are users who have permission to comment on the block.
-
-- **`comment`**: Represents a comment on a block. Each comment is associated with a block and has an author. The read and write permissions are defined based on the author of the comment and can be inherited from the block.
-
-- **`template`**: Represents a template within a workspace. Each template is associated with a workspace and has a creator and viewers. The read and write permissions are defined based on the creator and viewers of the template and can be inherited from the workspace. Permissions are also defined for creating and deleting templates.
-
-- **`integration`**: Represents an integration within a workspace. Each integration is associated with a workspace and has an owner. Permissions are defined for reading and writing to the integration.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions. Let's examine the **read** permission of the page entity.
-
-#### Page Read Permission
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- ..
-}
-
-entity page {
-
- // The workspace associated with the page
- relation workspace @workspace
-
- ..
- ..
-
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- ..
- ..
-
- // Define permissions for page actions
- permission read = reader or workspace.read
-
- ..
- ..
-}
-```
-
-This permission specifies who can read the contents of the page at Notion.
-
-The `reader` relation specifies the users who are members of the workspace associated with the page (`workspace#member`) or guests of the workspace (`workspace#guest`).
-
-Read permission of the workspace inherited as `workspace.read` in the page entity. THis permission specifies that any user who has been granted read access to the workspace object (i.e., the workspace that the page belongs to) can also read the page.
-
-In summary, any user who is a member or guest of the workspace and has been granted read access to the page through the reader relation, as well as any user who has been granted read access to the workspace itself, can read the contents of the page.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different workspaces:
-workspace:engineering_team#owner@user:alice
-workspace:engineering_team#member@user:bob
-workspace:engineering_team#guest@user:charlie
-workspace:engineering_team#admin@user:alice
-workspace:sales_team#owner@user:david
-workspace:sales_team#member@user:eve
-workspace:sales_team#guest@user:frank
-workspace:sales_team#admin@user:david
-
-// Connect pages, databases, and templates to workspaces:
-page:project_plan#workspace@workspace:engineering_team
-page:product_spec#workspace@workspace:engineering_team
-database:task_list#workspace@workspace:engineering_team
-template:weekly_report#workspace@workspace:sales_team
-database:customer_list#workspace@workspace:sales_team
-template:marketing_campaign#workspace@workspace:sales_team
-
-// Set permissions for pages, databases, and templates:
-page:project_plan#writer@user:frank
-page:project_plan#reader@user:bob
-
-database:task_list#editor@user:alice
-database:task_list#viewer@user:bob
-
-template:weekly_report#creator@user:alice
-template:weekly_report#viewer@user:bob
-
-page:product_spec#writer@user:david
-page:product_spec#reader@user:eve
-
-database:customer_list#editor@user:david
-database:customer_list#viewer@user:eve
-
-template:marketing_campaign#creator@user:david
-template:marketing_campaign#viewer@user:eve
-
-// Set relationships for blocks and comments:
-block:task_list_1#database@database:task_list
-block:task_list_1#editor@user:alice
-block:task_list_1#commenter@user:bob
-block:task_list_2#database@database:task_list
-block:task_list_2#editor@user:alice
-block:task_list_2#commenter@user:bob
-
-comment:task_list_1_comment_1#block@block:task_list_1
-comment:task_list_1_comment_1#author@user:bob
-comment:task_list_1_comment_2#block@block:task_list_1
-comment:task_list_1_comment_2#author@user:charlie
-comment:task_list_2_comment_1#block@block:task_list_2
-comment:task_list_2_comment_1#author@user:bob
-comment:task_list_2_comment_2#block@block:task_list_2
-comment:task_list_2_comment_2#author@user:charlie
-```
-
-## Test & Validation
-
-Since we have our schema and the sample relation tuples, let's check some permissions and test our authorization logic.
-
-can user:alice write database:task_list ?
-
-
-```perm
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
-
- ..
- ..
-
- // Define permissions for database actions
- ..
- ..
-
- permission write = editor or workspace.write
-
- ..
- ..
- }
-```
-
-According to what we have defined for the **'write'** permission, users who are either;
-
-- The editor in task list database (`database:task_list`)
-- Have a write permission in the engineering team workspace, which is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`)
-
-can edit the task list database (`database:task_list`)
-
-Based on the relation tuples we created, `user:alice` doesn't have the **editor** relationship with the `database:task_list`.
-
-Since `user:alice` is the owner and admin in the engineering team workspace (`workspace:engineering_team#admin@user:alice`) it has a write permission defined in the workspace entity, as you can see below:
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- ..
- ..
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- ..
- permission write = owner or admin
-}
-```
-
-And as we mentioned the engineering team workspace is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`). Therefore, the `user:alice write database:task_list` check request should yield a **'true'** response.
-
-
-
-
-can user:charlie write page:product_spec ?
-
-
-```perm
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
-
- ..
- ..
-
- permission write = writer or workspace.write
-}
-```
-
-`user:charlie` is guest in the workspace (`workspace:engineering_team#guest@user:charlie`) and the engineering team workspace is the only workspace that `page:product_spec` belongs to.
-
-As we defined, guests doesn't have write permission in a workspace.
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- permission write = owner or admin
-}
-```
-
-So that, `user:charlie` doesn't have a write relationship in the workspace. And ultimately, the `user:charlie write page:product_spec` check request should yield a **'false'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
- }
-
- entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
- }
-
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
- }
-
- entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
- }
-
- entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
- }
-
- entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
- }
-
- entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
- }
-
-relationships:
- - workspace:engineering_team#owner@user:alice
- - workspace:engineering_team#member@user:bob
- - workspace:engineering_team#guest@user:charlie
- - workspace:engineering_team#admin@user:alice
- - workspace:sales_team#owner@user:david
- - workspace:sales_team#member@user:eve
- - workspace:sales_team#guest@user:frank
- - workspace:sales_team#admin@user:david
- - page:project_plan#workspace@workspace:engineering_team
- - page:product_spec#workspace@workspace:engineering_team
- - database:task_list#workspace@workspace:engineering_team
- - template:weekly_report#workspace@workspace:sales_team
- - database:customer_list#workspace@workspace:sales_team
- - template:marketing_campaign#workspace@workspace:sales_team
- - page:project_plan#writer@user:frank
- - page:project_plan#reader@user:bob
- - database:task_list#editor@user:alice
- - database:task_list#viewer@user:bob
- - template:weekly_report#creator@user:alice
- - template:weekly_report#viewer@user:bob
- - page:product_spec#writer@user:david
- - page:product_spec#reader@user:eve
- - database:customer_list#editor@user:david
- - database:customer_list#viewer@user:eve
- - template:marketing_campaign#creator@user:david
- - template:marketing_campaign#viewer@user:eve
- - block:task_list_1#database@database:task_list
- - block:task_list_1#editor@user:alice
- - block:task_list_1#commenter@user:bob
- - block:task_list_2#database@database:task_list
- - block:task_list_2#editor@user:alice
- - block:task_list_2#commenter@user:bob
- - comment:task_list_1_comment_1#block@block:task_list_1
- - comment:task_list_1_comment_1#author@user:bob
- - comment:task_list_1_comment_2#block@block:task_list_1
- - comment:task_list_1_comment_2#author@user:charlie
- - comment:task_list_2_comment_1#block@block:task_list_2
- - comment:task_list_2_comment_1#author@user:bob
- - comment:task_list_2_comment_2#block@block:task_list_2
- - comment:task_list_2_comment_2#author@user:charlie
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "database:task_list"
- subject: "user:alice"
- assertions:
- write: true
- - entity: "page:product_spec"
- subject: "user:charlie"
- assertions:
- write: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/modeling.md b/docs/versioned_docs/version-0.4.x/getting-started/modeling.md
deleted file mode 100644
index ba07ed5f..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/modeling.md
+++ /dev/null
@@ -1,442 +0,0 @@
----
-sidebar_position: 1
----
-
-# Modeling Authorization
-
-Permify has its own language that you can model your authorization logic with it. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager, member and also dynamic attributes such as boolean variables, IP range, time period, etc.
-
-
-
-## Permify Schema
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. It includes set-algebraic operators such as intersection and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-Here’s a simple breakdown of our schema.
-
-
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is **_".perm"_**.
-
-## Developing a Schema
-
-This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-
-We'll follow a simplified version of github access control system. To see completed model you can jump directly to [Github Example](#github-example).
-
-:::info
-You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
-
-[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-
-:::
-
-### Defining Entities
-
-The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
-
-Think of entities as tables in your relationship database. We are strongly advice to name entities same as your database table name that its corresponds. In that way you can easily model and reason your authorization as well as eliminating the error possibility.
-
-You can create entities using `entity` keyword. Since we're following example of simplified github access control, lets create some of our entities as follows.
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity team {}
-
-entity repository {}
-```
-
-Entities has 2 different attributes. These are;
-
-- **relations**
-- **actions (or permissions)**
-
-### Defining Relations
-
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions. Keyword **_relation_** need to used to create a entity relation with name and type attributes.
-
-**Relation Attributes:**
-
-- **name:** relation name.
-- **type:** relation type, basically the entity it’s related to (e.g. user, organization, document, etc.)
-
-An example relation takes form of,
-
-```perm
-relation [name] @[type]
-```
-
-Lets turn back to our example and define our relations inside our entities:
-
-#### User Entity
-
-→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
-
-```perm
-entity user {}
-```
-
-#### Organization Entity
-
-→ For the sake of simplicity let's define only 2 user types in an organization, these are administrators and direct members of the organization.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-```
-
-#### Team Entity
-
-→ Let's say teams can belong organizations and can have a member inside of it as follows,
-
-```perm
-entity team {
-
- relation parent @organization
- relation member @user
-
-}
-```
-
-The parent relation is indicating the organization the team belongs to. This way we can achieve **parent-child relationship** inside this entity.
-
-#### Repository Entity
-
-→ Organizations and users can have multiple repositories, so each repository is related with an organization and with users. We can define repository relations as as follows.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-}
-```
-
-The owner relation indicates the creator of the repository, that way we can achieve **ownership** in Permify.
-
-**Defining Multiple Relation Types**
-
-As you can see we have new syntax above,
-
-```perm
- relation maintainer @user @team#member
-```
-
-When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-
-:::info
-You can use **#** to reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
-
-Actual purpose of feature locking is to giving ability to specify the sets of users that can be assigned.
-
-For example:
-
-```perm
- relation viewer @user
-```
-
-When you define it like this, you can only add users directly as tuples (you can find out what relation tuples is in next section):
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-
-However, if you define it as:
-
-```perm
- relation viewer @user @organization#member
-```
-
-You will then be able to specify not only individual users but also members of an organization:
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-- organization:1#viewer@organization:O1#member
-
-You can think of these definitions as a precaution taken against creating undesired user set relationships.
-:::
-
-Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
-
-### Defining Actions and Permissions
-
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances. So, the basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
-
-#### Intersection and Exclusion
-
-The Permify Schema supports **`and`**, **`or`** and **`not`** operators to achieve permission **intersection** and **exclusion**. The keywords **_action_** or **_permission_** can be used with those operators to form rules for your authorization logic.
-
-Lets get back to our github example and create some permissions on repository entity,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- ..
- ..
-
- action push = owner
-
-}
-```
-
-→ `action push = owner or maintainer` indicates only the repository owner or maintainers can push to
-repository.
-
-:::info
-The same `push` can also be defined using the **permission** keyword, as follows:
-
-```perm
-permission push = owner
-```
-
-Using `action` and `permission` will yield the same result for defining permissions in your authorization logic.
-
-The reason we have two keywords for defining permissions is that while most permissions are based on actions (such as view, read, edit, etc.), there are still cases where we need to define permissions based on roles or user types, such as admin or member.
-
-Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
-
-See **Real World Examples Section** for examining the contextualize difference between using permission and action keyword. You can start with observing [Google Docs Simplified](./examples/google-docs.md) example.
-:::
-
-For this tutorial we'll continue with `action` keyword,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- ..
- ..
-
- action read = org.admin and (owner or maintainer or org.member)
-
-}
-```
-
-→ Let's examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-
-:::info Permission Union
-
-Permify allows you to set permissions that are effectively the union of multiple permission sets.
-
-You can define permissions as relations to union all rules that permissions have. Here is an simple demonstration how to achieve permission union in our DSL, you can use actions (or permissions) when defining another action (or permission) like relations,
-
-```perm
- action edit = member or manager
- action delete = edit or org.admin
-```
-
-The `delete` action inherits the rules from the `edit` action. By doing that, we'll be able to state that only organization administrators and any relation capable of performing the edit action (member or manager) can also perform the delete action.
-
-Permission union is super beneficial in scenarios where a user needs to have varied access across different departments or roles.
-:::
-
-### Completed Schema
-
-Here is full implementation of simple Github access control example with using Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
- action edit = member or parent.admin
-
-}
-
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- action push = owner or maintainer
- action read = (owner or maintainer or parent.member) and parent.admin
- action delete = parent.admin or owner
-
-}
-```
-
-
-### Defining Attribute Based Permissions
-
-:::success Beta
-Please keep in mind that this feature is still in the **beta stage**, and we're actively seeking user feedback to improve it. As a Beta feature, Permify ABAC support may have some limitations, and its functionality and interface could change in future updates.
-:::
-
-
-To support Attribute Based Access Control (ABAC) in Permify, we've added two main components into our DSL: **attributes** and **rules**.
-
-Attributes are used to define properties for entities in specific data types. For instance, an attribute could be an IP range associated with an organization, defined as a string array:
-
-```perm
-attribute ip_range string[]
-```
-
-There are different types of attributes you can use;
-
-#### 1. Boolean
-
-For attributes that represent a binary choice or state, such as a yes/no question, the `Boolean` data type is an excellent choice.
-
-```perm
-entity post {
- attribute is_public boolean
-
- permission view = is_public
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
-:::
-
-#### 2. **String**
-
-String can be used as attribute data type in a variety of scenarios where text-based information is needed to make access control decisions. Here are a few examples:
-
-- **Location:** If you need to control access based on geographical location, you might have a location attribute (e.g., "USA", "EU", "Asia") stored as a string.
-- **Device Type**: If access control decisions need to consider the type of device being used, a device type attribute (e.g., "mobile", "desktop", "tablet") could be stored as a string.
-- **Time Zone**: If access needs to be controlled based on time zones, a time zone attribute (e.g., "EST", "PST", "GMT") could be stored as a string.
-- **Day of the Week:** In a scenario where access to certain resources is determined by the day of the week, the string data type can be used to represent these days (e.g., "Monday", "Tuesday", etc.) as attributes!
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute location string[]
-
- permission view = check_location(request.current_location, location) or admin
-}
-
-rule check_location(current_location string, location string[]) {
- current_location in location
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts string as `""`
-:::
-
-:::info Defining Rules
-
-In above we defined a function called with **rule** keyword.
-
-Rules are structures that allow you to write specific conditions for the model. They accept parameters and are based on conditions.
-
-Another example, a rule could be used to check if a given IP address falls within a specified IP range:
-
-```perm
-rule check_ip_range(ip string, ip_range string[]) {
- ip in ip_range
-}
-```
-:::
-
-#### 3. Integer
-
-Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
-- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
-- **Resource Size or Length:** If access to resources is controlled based on their size or length (like a document's length or a file's size), these can be stored as integer attributes.
-- **Version Number:** If access control decisions need to consider the version number of a resource (like a software version or a document revision), these can be stored as integer attributes.
-
-```perm
-entity content {
- permission view = check_age(request.age)
-}
-
-rule check_age(age integer) {
- age >= 18
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts integer as `0`
-:::
-
-#### 4. **Double**
-
-Double can be used as attribute data type in several scenarios where precise numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Usage Limit:** If a user has a usage limit (like the amount of storage they can use or the amount of data they can download), and this limit needs to be represented with decimal precision, it can be stored as a double attribute.
-- **Transaction Amount:** In a financial system, if access control decisions need to consider the amount of a transaction, and this amount needs to be represented with decimal precision (like $100.50), these amounts can be stored as double attributes.
-- **User Rating:** If access control decisions need to consider a user's rating (like a rating out of 5 with decimal points, such as 4.7), these ratings can be stored as double attributes.
-- **Geolocation:** If access control decisions need to consider precise geographical coordinates (like latitude and longitude, which are often represented with decimal points), these coordinates can be stored as double attributes.
-
-```perm
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts double as `0.0`
-:::
-
-See more details on [Attribute Based Access Control](../../use-cases/abac) section to learn our approach on ABAC as well as how it operates in Permify.
-
-## Permission Capabilities
-
-1. **Permission Union:**
-
-Permify allows you to set permissions that are effectively the union of multiple permission sets. For example, if a user belongs to multiple roles, each with their own permissions, the user’s effective permissions will be the union of all permissions of the roles they belong to. This is beneficial in scenarios where a user needs to have varied access across different departments or roles.
-
-2. **Permission Indirection: (ReBAC)**
-
-Permify supports indirect permission granting through relationships. For instance, you can define that a user has certain permissions because of their relation to other entities.
-
-An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group. This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-We utilize ReBAC and Google Zanzibar to create natural linkage between business units, functions, and entities of an organization.
-
-## Real World Examples
-
-This example shows almost all aspects of the Permify Schema.
-
-You can check out more schema examples from the [Real World Examples](../examples) section with their detailed examination.
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/sync-data.md b/docs/versioned_docs/version-0.4.x/getting-started/sync-data.md
deleted file mode 100644
index 98a1bca6..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/sync-data.md
+++ /dev/null
@@ -1,461 +0,0 @@
----
-sidebar_position: 2
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Managing Authorization Data
-
-Permify unifies your authorization data in a database you prefer. We named that database as Write Database, shortly **WriteDB**.
-
-Permify API provides various functionalities - checking access, reasoning permissions, etc - to maintain separate access control mechanisms for individual applications. And **WriteDB** stands as a source of truth for these authorization functionalities.
-
-## Access Control as Relations - Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. Each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-In Permify, the simplest form of relational tuple structured as: `entity # relation @ user`. Here are some relational tuples with semantics,
-
-
-
-## Where Relational Tuples Used ?
-
-In Permify, these relational tuples represents your authorization data.
-
-Permify stores your relational tuples (authorization data) in a database you prefer. You can configure the database when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-Stored relational tuples are queried and utilized in Permify APIs, including the check API, which is an access control check request used to determine whether a user's action is authorized.
-
-As an example; to decide whether a user could view a protected resource, Permify looks up the relations between that specific user and the protected resource. These relation types could be ownership, parent-child relation, or even a role such as an admin or manager.
-[WriteDB]: #write-database
-
-## Creating Relational Tuples
-
-Relational tuples can be created with an simple API call in runtime, since relations and authorization data's are live instances. Each relational tuple should be created according to its authorization model, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-
-
-Let's follow a simple document management system example with the following Permify Schema to see how to create relation tuples.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity document {
-
- relation owner @user
- relation parent @organization
- relation maintainer @user @organization#member
-
- action view = owner or parent.member or maintainer or parent.admin
- action edit = owner or maintainer or parent.admin
- action delete = owner or parent.admin
-}
-```
-
-According to the schema above; when a user creates a document in an organization, more specifically let's say, when user:1 create a document:2 we need to create the following relational tuple,
-
-- `document:2#owner@user:1`
-
-[WriteDB]: #write-database
-
-### Write Relationships API
-
-You can create relational tuples by using `Write Relationships API`.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "2",
- },
- Relation: "owner",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "2"
- },
- relation: "owner",
- subject: {
- type: "user",
- id: "1"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "2s"
- },
- "relation": "owner",
- "subject":{
- "type": "user",
- "id": "1",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Snap Tokens
-
-In Write Relationships API response you'll get a snap token of the operation.
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../reference/snap-tokens.md)
-
-## More Relationships
-
-Let's create more relationships according to the schema we defined above.
-
-### Organization Admin
-
-**relational tuple:** organization:1#admin@user:3
-
-**Semantics:** User 3 is administrator in organization 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "user",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Parent Organization
-
-**Relational Tuple:** document:1#parent@organization:1#…
-
-**Semantics:** Organization 1 is parent of document 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "parent",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "1",
- Relation: "..."
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "parent",
- subject: {
- type: "organization",
- id: "1",
- relation: "..."
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "parent",
- "subject":{
- "type": "organization",
- "id": "1",
- "relation": "..."
- }
- }
- ]
-}'
-```
-
-
-
-:::info
-Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
-
-Simply, the usage of ... is straightforward: if you're use user entity as an subject, you should not be using the `...` If you're using another subject rather than user entity then you need to use the `...`
-:::
-
-### Organization Members Are Maintainers in specific Doc
-
-**Created relational tuple:** document:1#maintainer@organization:2#member
-
-**Definition:** Members of organization 2 are maintainers in document 1.
-
-
-
-
-```go
-rr, err: = client.Relationship.Write(context.Background(), & v1.RelationshipWriteRequest {
- TenantId: "t1",
- Metadata: &v1.RelationshipWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "maintainer",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "2",
- Relation: "member"
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.relationship.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "maintainer",
- subject: {
- type: "organization",
- id: "2",
- relation: "member"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/relationships/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "maintainer",
- "subject":{
- "type": "organization",
- "id": "2",
- "relation": "member"
- }
- }
- ]
-}'
-```
-
-
-
-#### Test this Example on [Playground](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_)
-
-## Audit Logs For Permission Changes
-
-Permify does support audit logs for permission changes. Leveraging the [MVCC (Multi-Version Concurrency Control)](http://mbukowicz.github.io/databases/2020/05/01/snapshot-isolation-in-postgresql.html) pattern, we maintain a history of all permission data changes. This essentially provides an audit trail, allowing users to track alterations and when they occurred.
-
-In cloud version, our system supports change history auditing. It automatically generates and securely stores logs for all significant actions. These logs detail who made the change, what was changed, and when the change occurred. Furthermore, your system allows for easy searching and analysis of these logs, supporting automated alerting for suspicious activities. This comprehensive approach ensures thorough and effective auditing of all changes
-
-## Permission Baselining (Reviewing)
-
-We have a strong foundation for permission baselining and review, thanks to MVCC.
-
-**Historical Review:** You can review the history of permissions changes as each version is stored. This enables retrospective audits and analysis.
-
-**Current State Review:** You can review the current state of permissions by examining the latest versions of each permission setting.
-
-**Cleanup:** Your system incorporates a garbage collector for managing old relationships, which helps keep your permissions structure clean and optimized.
-
-## Next
-
-Let's now head over to the **Access Control Check** section and learn how to perform access control in Permify to ensure that only authorized users have the right level of access to our resources.
diff --git a/docs/versioned_docs/version-0.4.x/getting-started/testing.md b/docs/versioned_docs/version-0.4.x/getting-started/testing.md
deleted file mode 100644
index 950b1b44..00000000
--- a/docs/versioned_docs/version-0.4.x/getting-started/testing.md
+++ /dev/null
@@ -1,243 +0,0 @@
----
-sidebar_position: 4
----
-
-# Testing & Validation
-
-Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
-
-Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
-
-We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Adding Validate Action To Your Workflow
-
-After adding [permify-validate-action] to your Github Action workflow, you need to define the schema validation yaml file as,
-
-- **With local file:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "test.yaml"
-```
-
-- **With external url:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
-```
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Schema Validation File
-
-Below you can examine an example schema validation yaml file. It consists 3 parts;
-- `schema` which is the authorization model you want to test,
-- `relationships` sample data to test your model,
-- `scenarios` to test access check queries within created scenarios.
-
-Here is an example Schema Validation file,
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = (admin or member)
- action delete = admin
- }
-
- entity repository {
-
- relation owner @user @organization#member
- relation parent @organization
-
- action push = owner
- action read = (owner and (parent.admin and parent.member))
- action delete = (parent.member and (parent.admin or owner))
- action edit = parent.member not owner
- }
-
-relationships:
- - "organization:1#admin@user:1"
- - "organization:1#member@user:1"
- - "repository:1#owner@user:1"
- - "repository:2#owner@user:2"
- - "repository:2#owner@user:3"
- - "repository:1#parent@organization:1#..."
- - "organization:1#member@user:43"
- - "repository:1#owner@user:43"
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "repository:1"
- subject: "user:1"
- assertions:
- push : true
- owner : true
- - entity: "repository:2"
- subject: "user:1"
- assertions:
- push : false
- - entity: "repository:3"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- assertions:
- push : true
- - entity: "repository:1"
- subject: "user:43"
- assertions:
- edit : false
- entity_filters:
- - entity_type: "repository"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- - "repository:4#owner@user:1"
- - "repository:5#owner@user:1"
- assertions:
- push : ["1", "3", "4", "5"]
- edit : []
- subject_filters:
- - subject_reference: "user"
- entity: "repository:1"
- context:
- - "organization:1#member@user:58"
- assertions:
- push : ["1", "43"]
- edit : ["58"]
-```
-
-Assuming that you're well-familiar with the `schema` and `relationships` sections of the above YAML file. If not, please see the previous sections to learn how to create an authorization model (schema) and generate data (relationships) according to it.
-
-We'll continue by examining how to create scenarios.
-
-## Creating Test Scenarios
-
-You can create multiple access checks at once to test whether your authorization logic behaves as expected or not.
-
-Besides simple access checks you can also test subject filtering queries and data (entity) filtering with it.
-
-Let's deconstruct the `scenarios`,
-
-### Scenarios
-
-```js
-scenarios:
- - name: // name of the scenario
- description: // description of the scenario
- checks: // simple access check case/cases
- entity_filters: // entity (data) filtering query/queries
- subject_filters: // subject filtering query/queries
-```
-
-### Access Check
-
-You can create `check` inside `scenarios` to test multiple access check cases,
-
-```js
-checks:
- - entity: "repository:3" // resource/entity that you want to check access for
- subject: "user:1" // subject that performs the access check
- context: // additional data provided during an access check to be evaluated
- - "repository:3#owner@user:1"
- assertions: // expected result/results for specific action/s or an permission/s.
- push : true
-```
-
-Semantics for above check is: whether `user:1` can push to `repository:3`, additional to stored tuples take account that user:1 is owner of repository:3 (`repository:3#owner@user:1`). Expected result for that check it **true** - `push : true`
-
-:::info Contextual Tuples
-We use `context` (Contextual Tuples) with simple relational tuples for simplicity in this example. However, it is primarily used for dynamic access checks, such as those involving time, date, or IP address, etc.
-
-To learn more about how `context` works, see the [Contextual Tuples](../reference/contextual-tuples.md) section.
-:::
-
-### Entity Filtering
-
-You can create `entity_filters` within `scenarios` to test your data filtering queries.
-
-```js
-entity_filters:
- - entity_type: "repository" // entity that you want to filter
- subject: "user:1" // subject that you want to perform data filtering
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "3", "4", "5"] // IDs of the resources that we expected to return
- edit : []
-```
-
-The major difference between `check` lies in the assertions part. Since we're performing data filtering with bulk data, instead of a true-false result, we enter the IDs of the resources that we expect to be returned
-
-### Subject Filtering
-
-You can create `subject_filters` within `scenarios` to test your subject filtering queries, a.k.a which users can perform action Y or have permission X on entity:Z?
-
-```js
-- subject_reference: "user"
- entity: "repository:1"
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "43"] // IDs of the users that we expected to return
- edit : ["58"]
-```
-
-:::info API Endpoints
-You can find the related API endpoints for `check`, `entity_filters`, and `subject_filters` in the Permission service in the [Using The API](../api-overview.md) section.
-:::
-
-## Coverage Analysis
-
-By using the command `permify coverage {path of your schema validation file}`, you can measure the coverage for your schema.
-
-The coverage is calculated by analyzing the relationships and assertions in your created model, identifying any missing elements.
-
-The output of the example provided above is as follows.
-
-
-
-## Testing in Local
-
-You can also test your new authorization model in your local (Permify clone) without using [permify-validate-action] at all.
-
-For that open up a new file and add a schema yaml file inside. Then build your project with, run `make serve` command and run `./permify validate {path of your schema validation file}`.
-
-If we use the above example schema validation file, after running `./permify validate {path of your schema validation file}` it gives a result on the terminal as:
-
-
-
-[permify-validate-action]: https://github.com/Permify/permify-validate-action
-
-## Unit Tests For Schema Changes
-
-We recommend leveraging Permify's in-memory databases for a simplified and isolated testing environment. These in-memory databases can be easily created and disposed of for each individual unit test, ensuring that your tests do not interfere with each other and each one starts with a clean slate.
-
-For managing permission/relation changes, we suggest storing schema in an abstracted place such as a git repo and centrally checking and approving every change before deploying it via the CI pipeline that utilizes the **Write Schema API**.
-
-We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-
-You can find more details about our suggested workflow to handle schema changes in [Write Schema](hhttps://docs.permify.co/docs/api-overview/schema/write-schema#suggested-workflow-for-schema-changes) section.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
-
diff --git a/docs/versioned_docs/version-0.4.x/installation.md b/docs/versioned_docs/version-0.4.x/installation.md
deleted file mode 100644
index c855058f..00000000
--- a/docs/versioned_docs/version-0.4.x/installation.md
+++ /dev/null
@@ -1,17 +0,0 @@
----
-id: installation
-title: Setup Permify
-slug: /installation
----
-
-# Setup Permify
-
-Here is some options that you can use to set up and deploy Permify in your servers.
-
-```mdx-code-block
-import {CardList} from '../../src/components/Card';
-
-
-```
-
-If options your deployment preference is not listed below please let us know Also if you have any questions join our [Discord community](https://discord.gg/n6KfzYxhPp) or send us an email at support@permify.co.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/installation/_category_.json b/docs/versioned_docs/version-0.4.x/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.4.x/installation/azure.md b/docs/versioned_docs/version-0.4.x/installation/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/installation/brew.md b/docs/versioned_docs/version-0.4.x/installation/brew.md
deleted file mode 100644
index c56a06d8..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/brew.md
+++ /dev/null
@@ -1,66 +0,0 @@
----
-title: "Install with Brew"
----
-
-# Brew With Configurations
-
-This section shows how to intall and run Permify Service with using brew.
-
-### Install Permify
-
-Open terminal and run following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-### Run Permify Service
-
-To run the Permify Service, `permify serve` command should be run with configurations.
-
-By default, the service is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather then an actual database. You can override these with running the command with configuration flags.
-
-### Configure With Using Flags
-
-See all configuration flags with running,
-
-```shell
-permify serve --help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flags' argument with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Configure With Using Config File
-
-You can also configure Permify Service with using a configuration file.
-
-```shell
- permify serve -c=config.yaml
-```
-
-or
-
-```shell
- permify serve --config=config.yaml
-```
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview/
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/installation/container.md b/docs/versioned_docs/version-0.4.x/installation/container.md
deleted file mode 100644
index c91a1ac4..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/container.md
+++ /dev/null
@@ -1,58 +0,0 @@
----
-title: "Docker Container"
----
-
-# Deploy using Docker
-
-This section shows how to run Permify Service from a docker container. You can run Permify service from a container with following steps.
-
-## Run following line on Terminal
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
-```
-
-This will start an API server with the configuration options that pointed out on the **{YOUR-CONFIG-PATH}**.
-
-### Configure With a YAML file
-
-This config path - `{YOUR-CONFIG-PATH}` - addresses the [config yaml file](../reference/configuration.md), where you can configure running options of the Permify Server as well as define the ***database*** to store your authorization related data.
-
-As an example if you had a "config.yaml" file at your Desktop, the path `{YOUR-CONFIG-PATH}:/config` would look like:
-`Users/your_user_name/Desktop:/config`.
-
-:::info Talk to an Permify Engineer
-By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database.
-:::
-
-### Configure With Using Flags
-
-Alternatively, you can set configuration options with the respected flags when running the command. See all configuration flags with running,
-
-```shell
-docker run -p 8080:8080 ghcr.io/permify/permify serve -help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flags' argument with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Test your connection.
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/installation/google.md b/docs/versioned_docs/version-0.4.x/installation/google.md
deleted file mode 100644
index deb30dc9..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/google.md
+++ /dev/null
@@ -1,271 +0,0 @@
----
-title: Deploy on Google Compute Engine
----
-
-This guide outlines the process of deploying Permify, on Google Compute Engine. The steps include setting up Google Cloud SDK and kubectl, managing containers using Google Kubernetes Engine (GKE), deploying Permify, and implementing Permify in a distributed configuration with Serf. By following these steps, you can efficiently deploy Permify on Google's scalable and secure infrastructure.
-
-## Google Cloud SDK Install
-
-1. At the command line, run the following command:
-
- ```bash
- curl https://sdk.cloud.google.com | bash
- ```
-
-2. When prompted, choose a location on your file system (usually your Home directory) to create the `google-cloud-sdk` subdirectory under.
-3. If you want to send anonymous usage statistics to help improve gcloud CLI, answer `Y` when prompted.
-4. To add gcloud CLI command-line tools to your `PATH` and enable command completion, answer `Y` when prompted
-5. Restart your shell:
-
- ```bash
- exec -l $SHELL
- ```
-
-6. To initialize the Google Cloud CLI environment, run `gcloud init`
-
-## Install kubectl
-
-1. Install the `kubectl` component:
-
- ```bash
- gcloud components install kubectl
- ```
-
-2. Verify that `kubectl` is installed:
-
- ```bash
- kubectl version
- ```
-
-3. Install Authn Plug-in
-
- ```bash
- gcloud components install gke-gcloud-auth-plugin
- ```
-
- Check the `gke-gcloud-auth-plugin` binary version:
-
- ```bash
- gke-gcloud-auth-plugin --version
- ```
-
-
-## Create Containers with GKE
-
-1. Login & Initialize Google Cloud CLI
-
- ```bash
- gcloud init
- ```
-
-2. Follow configuration instructions
-3. Create Container Cluster
-
- ```bash
- gcloud container clusters create [CLUSTER_NAME]
- ```
-
-4. Authenticate the cluster
-
- ```bash
- gcloud container clusters get-credentials [CLUSTER_NAME]
- ```
-
-
-## Deploy Permify
-
-1. Apply deployment config
-
- ```bash
- kubectl apply -f deployment.yaml
- ```
-
- - **Deployment.yaml**
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- labels:
- app: permify
- name: permify
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
- status: {}
- ```
-
-2. Apply service manfiest
-
- ```bash
- kubectl apply -f service.yaml
- ```
-
- - **Service Manifest**
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
- status:
- loadBalancer: {}
- ```
-
-
-## Deploying Permify in a Distributed Configuration
-
-If you aim to deploy Permify in a distributed configuration, you will need to create a Serf deployment. The Serf deployment can be dockerized to our Container Registry under the name permify/serf:v1.0, which is provided by Hashicorp.
-
-Please note: It is crucial to ensure that both Serf and Permify deployments reside within the same namespace for proper operation.
-
-1. Serf Service Create:
- - Serf Deployment&Service yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: serf-deployment
- spec:
- replicas: 1
- selector:
- matchLabels:
- app: serf
- template:
- metadata:
- labels:
- app: serf
- spec:
- containers:
- - name: serf
- image: permify/serf:v1.0
- args:
- - "-node=main-serf"
- ports:
- - containerPort: 7946
- resources:
- requests:
- cpu: 100m
- memory: 128Mi
- limits:
- cpu: 200m
- memory: 256Mi
- ---
- apiVersion: v1
- kind: Service
- metadata:
- name: serf
- spec:
- selector:
- app: serf
- ports:
- - protocol: TCP
- port: 7946
- targetPort: 7946
- name: serf
- type: ClusterIP
- ```
-
-2. Apply Deployment Manifest
- - Deployment.yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: permify-deployment
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: permify/permify:tagname
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- - "--distributed-enabled=true"
- - "--distributed-node=serf:7946"
- - "--distributed-node-name=main-serf"
- - "--distributed-protocol=serf"
- resources:
- requests:
- memory: "128Mi"
- cpu: "200m"
- limits:
- memory: "128Mi"
- cpu: "400m"
- ports:
- - containerPort: 3476
- name: permify-port
- - containerPort: 7946
- name: permify-dist
- - containerPort: 6060
- name: permify-pprof
- ```
-
-3. Apply Service Manifest
- - Service.yaml
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: permify-port
- port: 3476
- targetPort: 3476
- - name: permify-dist
- port: 7946
- targetPort: 7946
- selector:
- app: permify
- type: LoadBalancer
- ```
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/installation/kubernetes.md b/docs/versioned_docs/version-0.4.x/installation/kubernetes.md
deleted file mode 100644
index f2a1e21b..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/kubernetes.md
+++ /dev/null
@@ -1,173 +0,0 @@
----
-title: Kubernetes Cluster
----
-
-# Deploy on Kubernetes Cluster
-
-In this section we’re going to deploy Permify in AWS EKS which is Amazon Elastic Kubernetes Service. EKS is a managed service that you can easily run Kubernetes in AWS.
-
-Here’s what we’re going to do step-by-step;
-
-1. [Configure our AWS IAM credentials](#configure-aws-cli-with-your-iam-account)
-3. [Create EKS cluster and configure nodes](#creating-an-aws-eks-cluster)
-4. [Deploy Permify to nodes](#deploying--running-permify-in-nodes)
-
-There are a couple of small prerequisites for this tutorial.
-
-### Pre-requisites
-
-- An AWS account.
-- The AWS Command Line Interface (CLI) is installed and configured on your local machine. — [Click here](https://us-east-1.console.aws.amazon.com/iamv2/home?region=us-east-1#/home) to go to IAM
-- The AWS IAM Authenticator for Kubernetes is installed and configured on your local machine.
-
-## Configure AWS CLI with your IAM account.
-
-The first step is to configure our AWS IAM account into our local terminal so that we can run commands. Most of you probably have a configured AWS account if you ever set up anything into AWS programmatically, so you can skip this. If you don’t follow these steps.
-
-### Create an AWS IAM Programmatic Access Account
-
-First, let’s create IAM credentials for ourselves. Search IAM from the AWS console. You need to write down the account ID if you want to log in AWS console with this account as well. Let’s go over users and start creating our credentials.
-
-
-
-At Users screen click to “Add users” — and you’ll end up in your first screen creating user credentials. Here you can define the name of the user. Also there 2 options that you can choose simultaneously.
-
-But you must choose “Access key - Programmatic access” option. It’ll allow us to configure our AWS CLI on our local machine.
-
-You can also choose “Password - AWS Management Console access” if you want to log in to this account through the console. But you’ll need the Account ID that I mentioned in the IAM console screen.
-
-In the next screen, you’ll be asked to create or copy the user-set permissions. For this tutorial, you’ll only need to access EKS resources and features. So lets create group by clicking the “Create group” — and then at pop-up screen search for EKS.
-
-
-
-I’ll choose all EKS permissions but if you have certain policies internally, just stick with them. You’ll only need following permission to;
-
-- `AmazonEKSClusterPolicy`
-- `AmazonEKSServicePolicy`
-- `AmazonEKSVPCResourceController`
-- `AmazonEKSWorkerNodePolicy`
-
-Then simply you can review and create the user.
-
-
-
-Once you created the credentials you’ll prompt the “Access key ID” and “Secret access key”, you should save this down somewhere. We’re going the use these to configure our local machine with AWS CLI.
-
-### **Configure AWS CLI with your IAM account**
-
-Let’s open our local terminal
-
-```jsx
-aws configure
-```
-
-Next you’ll ask for the following credentials;
-
-- `AWS Access Key ID`
-- `AWS Secret Access Key`
-- `Default region name`
-- `Default output format` (leave it empty)
-
-## Creating an AWS EKS Cluster
-
-For the first step, we need to install [eksctl](https://eksctl.io/) — which is like kubectl but for AWS EKS. It helps us to set up and deploy our cluster and nodes within a fraction of the time.
-
-Let’s download eksctl using brew.
-
-
-```jsx
-brew tap weaveworks/tap
-```
-
-While installing the eksctl, we’ll end up getting kubectl and other dependencies.
-
-```jsx
-brew install weaveworks/tap/eksctl
-```
-
-Now, we’re ready to create our EKS cluster. You can define certain things while deploying standard the cluster beside the name and version like; the region you want to deploy, the EC2 instance type of each node, and the number of nodes you want to run.
-
-```bash
-eksctl create cluster \
---name \
---version 1.24 \
---region \
---nodegroup-name permify \
---node-type t2.small \
---nodes 2
-```
-
-## Deploying & Running Permify in Nodes
-
-The next stop is applying our manifests which will help us to deploy and configure our container/Permify.
-
-Let’s create our deployment manifest first.
-
-```yaml
-apiVersion: apps/v1
-kind: Deployment
-metadata:
- labels:
- app: permify
- name: permify
-spec:
- replicas: 2
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://postgres:nOcodeSTIAnLAba@permify-test.ceuo5kqsxyea.us-east-1.rds.amazonaws.com:5432/demo"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
-status: {}
-```
-
-Now let’s apply our deployment manifest
-
-```jsx
-kubectl apply -f deployment.yaml
-```
-
-The next step is to create a service manifest, this will allow us to configure our container app.
-
-```jsx
-apiVersion: v1
-kind: Service
-metadata:
- name: permify
-spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
-status:
- loadBalancer: {}
-```
-
-Let’s apply service.yaml to our nodes.
-
-```jsx
-kubectl apply -f service.yaml
-```
-
-Last but not least, we can check our pods & nodes. And we can start using the container with load balancer
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/installation/overview.md b/docs/versioned_docs/version-0.4.x/installation/overview.md
deleted file mode 100644
index 4dc5560d..00000000
--- a/docs/versioned_docs/version-0.4.x/installation/overview.md
+++ /dev/null
@@ -1,259 +0,0 @@
----
-sidebar_position: 1
----
-
-# Guide
-
-This guide shows you how to set up Permify in your servers and use it across your applications.
-
-:::info Minimum Requirements
-PostgreSQL: Version 13.8 or higher
-:::
-
-Please ensure your system meets these requirements before proceeding with the following steps:
-
-1. [Set Up & Run Permify Service](#set-up-permify-service)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Manage and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
-4. [Perform Access Check](#perform-access-check)
-
-:::info Talk to an Permify Engineer
-Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-## Set Up Permify Service
-
-You can run Permify Service with various options but in that tutorial we'll run it via docker container.
-
-### Run From Docker Container
-
-Production usage of Permify needs some configurations such as defining running options, selecting datastore to store authorization data and more.
-
-However, for the sake of this tutorial we'll not do any configurations and quickly start Permify on your local with running the docker command below:
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-:::info
-You can examine [Deploy using Docker] section to get more about the configuration options and learn the full integration to run Permify Service from docker container.
-
-[Deploy using Docker]: ../container
-:::
-
-### Test your connection
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core endpoints.
-
-[Using the API]: ../../api-overview
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-## Model your Authorization with Permify Schema
-
-After installation completed and Permify server is running, next step is modeling authorization with Permify authorization language - [Permify Schema]- and configure it to Permify API.
-
-You can define your entities, relations between them and access control decisions of each actions with using [Permify Schema].
-
-### Creating your authorization model
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-
-:::
-
-Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action view_files = admin or member
- action edit_files = admin
-
-}
-```
-
-We have 2 entities these are **"user"** and **"organization"**. Entities represents your main tables. We strongly advise naming entities the same as your original database entities.
-
-Lets roll back our example,
-
-- The `user` entity represents users. This entity is empty because it's only responsible for referencing users.
-
-- The `organization` entity has its own relations (`admin` and `member`) which related with user entity. This entity also has 2 actions, respectively:
- - Organization member and admin can view files.
- - Only admins can edit files.
-
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
-
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../use-cases/simple-rbac
-:::
-
-### Configuring Schema via API
-
-After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../api-overview/schema/write-schema.md) for configuration of your authorization model on Permify authorization service.
-
-:::caution Before Continue on Writing Schema
-You'll see **tenant_id** parameter almost all Permify APIs including Write Schema. With version 0.3.x Permify became a tenancy based authorization infrastructure, and supports multi-tenancy by default so its a mandatory parameter when doing any operations.
-
-We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
-:::
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-**POST /v1/tenants/{tenant_id}/schemas/write**
-
-
-
-## Store Authorization Data as Relational Tuples
-
-After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action.
-
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules at this writeDB by using [Write Relationships API](../api-overview/relationship/write-relationships.md)
-
-For our guide let's grant one of the team members (Ashley) an admin role.
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-**POST /v1/tenants/{tenant_id}relationships/write**
-
-```json
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1" //Organization identifier
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1", //Ashley's identifier
- "relation": ""
- }
- }
- ]
-}
-```
-
-
-
-**Created relational tuple:** organization:1#admin@user:1
-
-**Semantics:** User 1 (Ashley) has admin role on organization 1.
-
-:::tip
-In ideal production usage Permify stores your authorization data in a database you prefer. We called that database as WriteDB, and you can configure it with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) or CLI flag options.
-
-But in this tutorial Permify Service running default configurations on local, so authorization data will be stored in memory. You can find more detailed explanation how Permify stores authorization data in [Managing Authorization Data] section.
-
-[Managing Authorization Data]: ../../getting-started/sync-data
-:::
-
-## Perform Access Check
-
-Finally we're ready to control authorization. Access decision results computed according to relational tuples and the stored model, [Permify Schema] action conditions.
-
-Lets get back to our example and perform an example access check via [Check API]. We want to check whether an specific user has an access to view files in a organization.
-
-[Check API]: ../../api-overview/permission/check-api
-[Permify Schema]: ../../getting-started/modeling
-
-#### Example HTTP Request:
-
-***Can the user 45 view files on organization 1 ?***
-
-**POST /v1/tenants/{tenant_id}/permissions/check**
-
-| Required | Argument | Type | Default | Description |
-|----------|----------------|----------|---------|---------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field. |
-| [x] | entity | object | - | name and id of the entity. Example: organization:1. |
-| [x] | action | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action |
-| [ ] | schema_version | string | - | get results according to given schema version |
-| [ ] | depth | integer | 8 | - |
-
-### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_files",
- "subject": {
- "type": "user",
- "id": "45",
- "relation": ""
- },
-}
-```
-
-### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "metadata": {
- "check_count": 0
- }
-}
-```
-
-See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-
-[Access Control Check]: ../api-overview/permission/check-api.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you struggle with installation or have any questions, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/permify-overview/_category_.json b/docs/versioned_docs/version-0.4.x/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/versioned_docs/version-0.4.x/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.4.x/permify-overview/authorization-service.md b/docs/versioned_docs/version-0.4.x/permify-overview/authorization-service.md
deleted file mode 100644
index e8df72d3..00000000
--- a/docs/versioned_docs/version-0.4.x/permify-overview/authorization-service.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# What is Authorization Service?
-
-Authorization is an important part of software development. There are many different ways to implement authorization, but it's important for all apps to have some form of it in order to protect the user from malicious actors and unauthorized access attempts.
-
-An authorization service is a module that allows you to manage access to your application and ease the development and maintenance of your authorization system. It works in run time and respond to all authorization questions from any of your apps.
-
-
-
-[Permify] is a fully open source authorization service that offers a variety of binding and crafting options to secure your applications.
-
-[Permify]: https://github.com/Permify/permify
-
-## Why should I use Authorization Service instead of doing from scratch?
-
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch. You can get started quickly with a simple API that you can easily integrate into your application to move and iterate faster.
-
-### Do Not Reinvent The Wheel
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps. Building a scalable and robust authorization system is hard and needs a quite engineering time. Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period. Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services.
-
-[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-
-### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group. Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time. Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
-
-### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road. Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product. Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production. After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
-
-### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security. Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
-
-## Cases that can benefit from An Authorization Service:
-
-- If you already have an identity/auth solution and want to plug in fine-grained authorization on top of that.
-- If you want to create a unified access control mechanism to use across your individual applications.
-- If you want to make future-proof authorization system and don't want to spend engineering effort for it.
-- If you’re managing authorization for growing micro-service infrastructure.
-- If your authorization logic is cluttering your code base.
-- If your data model is getting too complicated to handle your authorization within the service.
-- If your authorization is growing too complex to handle within code or API gateway.
-
diff --git a/docs/versioned_docs/version-0.4.x/permify-overview/infrastructure.md b/docs/versioned_docs/version-0.4.x/permify-overview/infrastructure.md
deleted file mode 100644
index 9cc9733c..00000000
--- a/docs/versioned_docs/version-0.4.x/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,50 +0,0 @@
-
-# Where does Permify fit into your environment?
-
-Permify is a simply GRPC service that responsible for managing and authorization in your environment. This section shows where and how does Permify fit into your environment with examining Permify's architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## Architecture
-
-Permify stores access control relations on a database you choose and performs authorization checks based on the stored relations. We called that database Write Database - **WriteDB** - and it behaves as a centralized data source for your authorization system.
-
-You can model your authorization with Permify's DSL - Permify Schema and your applications can talk to Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data, or make changes to data stored in WriteDb.
-
-
-
-### Permify with Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization. Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications. See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important. As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/versioned_docs/version-0.4.x/permify-overview/intro.md b/docs/versioned_docs/version-0.4.x/permify-overview/intro.md
deleted file mode 100644
index 90312362..00000000
--- a/docs/versioned_docs/version-0.4.x/permify-overview/intro.md
+++ /dev/null
@@ -1,130 +0,0 @@
----
-sidebar_position: 1
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is a **relationship based authorization service** for creating and maintaining fine-grained authorizations while ensuring least privilege across your organization.
-
-With Permify, you can easily structure your authorization model, store authorization data in your preferred database, and interact with the Permify API to handle all authorization queries from your applications or services.
-
-Permify inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-## A true ReBAC solution to ensure least privilege
-
-Permify has designed and structured as a true ReBAC solution, so besides roles and traditional permissions Permify also supports indirect permission granting through relationships.
-
-For instance, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group. This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-Our goal is to create a robust, flexible, and easily auditable authorization system that establishes a natural linkage between permissions across the business units, functions, and entities of an organization.
-
-## Key Features
-
-🛡️ **Production ready** authorization API that serve as **gRPC** and **REST**
-
-🔮 Domain Specific Authorization Language - Permify Schema - to **easily model** your authorization
-
-🔐 Database Configuration to store your permissions **in house** with **high availability**
-
-✅ Perform access control checks and get answers **down to 10ms** with **parallel graph engine**
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf)
-
-⚙️ Create custom permissions for your **tenants**, and manage them in single place with **Multi Tenancy**
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin]
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Features Beyond Zanzibar
-
-We’re trying to make [Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf) available to everyone to use and benefit in their applications and services. So that we utilize Zanzibar features and add new features on top of it to achieve robust permission systems. Here are some additional features that we have,
-
-- **Multi-Tenancy Support** - It enables users to create a custom authorization model for different applications, all managed within a single Permify instance.
-
-- **Testing Framework - Permify Validate** - This enhances the testability of authorization logic. It includes features like scenario-based validation actions, policy coverage analysis, and IDL parser Integration to achieve end-to-end validation for the desired authorization schema.
-
-- **Data Filtering** - In Zanzibar typical access check has the form of **"Does user U has relation R to object O?”** and yields true or false response. Additional to that, we have data filtering endpoints that let you ask questions in the form of **“Which resources can user:X do action Y?”** or **“Which user(s) can edit doc:Y”**. As a response to this, you’ll get a entity results in the format of a string array or as a streaming response depending on the endpoint you're using.
-
-## Getting Started
-
-In Permify, authorization divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify [Store Authorization Data] as relations.
-- Perform an [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../../getting-started/modeling
-[Store Authorization Data]: ../../getting-started/sync-data
-[Access Checks]: ../../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want trying out and examine it instantly,
-
-
-
-## Community & Support
-
-We would love to hear from you :heart:
-
-You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
-
-For feature requests, bugs, or any improvements you can always open an issue.
-
-### Want to Contribute? Here are the ways to contribute to Permify
-
-* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
-* **Improve documentation:** Alongside our codebase, documentation one of the most significant part in our open-source journey. We're trying to give the best DX possible to explain ourselfs and Permify. And you can help on that with importing resources or adding new ones.
-* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
-
-You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
-
-## Communication Channels
-
-If you like Permify, please consider giving us a :star:
-
-
-
-## Roadmap
-
-You can find Permify's Public Roadmap [here](https://github.com/orgs/Permify/projects/1)!
-
-## Need any help on Authorization ?
-
-Our team is happy to help you anything about authorization. Moreover, if you'd like to learn more about using Permify in your app or have any questions, [schedule a call with one of our founders](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/playground.md b/docs/versioned_docs/version-0.4.x/playground.md
deleted file mode 100644
index 73f6ca4d..00000000
--- a/docs/versioned_docs/version-0.4.x/playground.md
+++ /dev/null
@@ -1,136 +0,0 @@
----
-sidebar_position: 6
----
-
-# Using Permify Playground
-
-You can use our [Playground] to create and test your authorization in a browser. Our playground consists 4 sections,
-
-- Schema (Authorization Model)
-- Authorization Data
-- Visualizer
-- Enforcement
-
-Let's examine these sections by following a simple example.
-
-[Playground]: https://play.permify.co/
-
-## Schema (Authorization Model)
-
-You can create your authorization model in this section with using Permify authorization language, Permify Schema.
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. We already have a couple of use cases and example that you can choose to see how authorization can be structured. Also, you can check our docs to learn more about how to model authorization in Permify.
-
-To demonstrate how the playground works, let's create a simple authorization model as follows. This model should be selected as the default when you open the playground.
-
-
-
-We have 2 permissions, `edit` for editing repository and `delete` for deleting repository.
-
-Repository has parent child relation with organizations. The `parent` relation in the repository entity represents that parent child association, while ownership of the repository is represented with the `owner` relation.
-
-Organizations can have organizational wide roles such as admin and member, which defined as `admin` and `member` relation in organization entity.
-
-:::info Automatic Saving for Schema Changes
-Schema changes are captured automatically, and other sections update accordingly. Some delays may occur at times; please feel free to reach out if these delays hinder your testing process.
-:::
-
-## Visualizer
-
-We get loads of feedback about the observability and reasonability of the authorization model across teams and colleagues.
-
-So we put a simple visualizer that shows how your authorization structure looks at a high level. In particular, you can examine relations between entities and their permissions. Here is a visualization for example model that we created above.
-
-
-
-## Authorization Data
-
-You can create sample authorization data to test your authorization logic. In Permify, authorization data stored as relation tuples and these tuples stored in a database that you preferred.
-
-The basic relation tuple takes the form of:
-
-`entity # relation @ user`
-
-So the entity can be any entity that you defined in your model. If we look up our example it can be an organization or repository (since the user is empty). The relation can be one of the defined relations in the selected entity.
-
-The user is basically the user or user set in our system. Let's say we want make the **user 1** `admin` in **organization 1** then we need to create an example relational tuple according to our model as follows:
-
-`organization:1#admin@user:1`
-
-To create a relation tuple in playground just hit the **Add Relationship** button.
-
-
-
-You can choose entity, relation and the subject (user or user set) with entering identifier to create sample data. Let's create the relation tuple `organization:1#admin@user:1` as follows.
-
-
-
-Let's add one more relation tuple to perform a sample access check. I want to add repository:1 into organization:1 - `repository:1#parent@organization:1#...` as follows:
-
-
-
-Created tuples shown in the **Data** section as follows.
-
-
-
-## Enforcement (Access Checks)
-
-Finally as we have a sample data let's perform an access check!
-
-In Playground you should create an scenario in order to perform access checks. This scenario based testing process gives ability to perform complex access scenarios in a single place.
-
-Hit the **New Scenario** button in the right side and a pop up will open. You can enter name and description of the scenario in here.
-
-
-
-
-
-Let's check **whether user:1 can edit the repository:1** as follows:
-
-
-
-In the above YAML structure,
-
-#### entity
-Represents the resource for which we want to check access - `repository:1`
-
-#### subject
-Represents the subject that performs the action or grants access - `user:1`.
-
-#### context
-Refers to additional data provided during an access check to be evaluated for the access decision. It's primarily used for dynamic access checks, such as those involving time, date, or IP address, etc.
-
-In our case, we leave it empty as null.For our case we leave it empty as null. You can check the details from the [Contextual Tuples](./reference/contextual-tuples.md) section.
-
-#### assertions
-
-Assertions stands for defining the expected result for specific action or an permission. In our case we're evaluating access for edit action.
-
-Since organization:1 is parent of repository:1 ( `repository:1#parent@organization:1#...` ) and user:1 has an admin role in organization:1 ( `organization:1#admin@user:1` ) user:1 should allow to edit the repository:1 because the we define rule of the edit permission as:
-
-`permission edit = parent.admin or owner`
-
-which `parent.admin` indicates admin in the organization that repository belongs to. So user:1 should be able to edit resource:1, therefore expected outcome for that access request is true - `edit: true`
-
-:::info Create More Advanced Scenarios
-For simplicity, we've created a basic scenario. However, you can create more advanced scenarios using our validation YAML structure.
-
-To learn how to use this syntax for complex scenarios, refer to the [Creating Test Scenarios](../getting-started/testing#creating-test-scenarios) section in [Testing & Validation](../getting-started/testing) page.
-:::
-
-Let's click the Run button to execute our scenario. The scenario name should turn green once the scenario result is confirmed as correct.
-
-
-
-Let's change the expected outcome as false (`edit: false`) and hit the **Run** button again we'll see an error message.
-
-
-
-As we seen above this is how you can model your authorization and test it with sample data in Permify Playground.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/reference/_category_.json b/docs/versioned_docs/version-0.4.x/reference/_category_.json
deleted file mode 100644
index b55d99d8..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Reference",
- "position": 8,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.4.x/reference/cache.md b/docs/versioned_docs/version-0.4.x/reference/cache.md
deleted file mode 100644
index f281a1a1..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/cache.md
+++ /dev/null
@@ -1,87 +0,0 @@
-# Cache Mechanisms
-
-This section showcases the cache mechanisms that Permify uses.
-
-## Schema Cache
-
-Schemas are stored in an in-memory cache based on their versions. If a version is specified in the request metadata, it will be searched for in the in-memory cache. If not found, it will query the database for the version and store it in the cache. If no version information is given in the metadata, versions will be assumed to be alphanumeric and sorted in that order, and Permify will request the head version and check if it exists in the memory cache.
-
-The size of this can be determined through the Permify configuration. Here is an example configuration:
-service:
-
-```yaml
-…
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
-…
-```
-
-The cache library used is: https://github.com/dgraph-io/ristretto
-
-## Relationships Cache
-
-Permify applies the MVCC (Multi Version Concurrency Control) pattern for Postgres, creating a separate database snapshot for each write and delete operation. This both enhances performance and provides a consistent cache.
-
-An example of a cache key is:
-check_{tenant_id}_{schema_version}:{snapshot_token}:{check_request}
-
-Permify hashes each request and searches for the same key. If it cannot find it, it runs the check engine and writes to the cache, thus creating a consistently working hash.
-
-The size of this can also be determined via the Permify configuration. Here’s an example:
-service:
-
-```yaml
- …
- permission:
- bulk_limit: 100
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
- …
-```
-
-The cache library used is: https://github.com/dgraph-io/ristretto
-
-Note: Another advantage of the MVCC pattern is the ability to historically store data. However, it has a downside of accumulation of too many relationships. For this, we have developed a garbage collector that will delete old relationships at a time period you specify.
-
-## Distributed Cache
-
-Permify does provide a distributed cache across availability zones (within an AWS region) via **Consistent Hashing**. Permify uses Consistent Hashing across its distributed instances for more efficient use of their individual caches.
-
-This would allow for high availability and resilience in the face of individual nodes or even entire availability zone failure, as well as improved performance due to data locality benefits.
-
-Consistent Hashing is a distributed hashing scheme that operates independently of the number of objects in a distributed hash table. This method hashes according to the nodes’ peers, estimating which node a key would be on and thereby ensuring the most suitable request goes to the most suitable node, effectively creating a natural load balancer.
-
-### How Consistent Hashing Operates in Permify
-
-With a single instance, when an API request is made, request and corresponding response stored in its corresponding local cache.
-
-If we have more than one Permify instance consistent hashing activates on API calls, hashes the request, and outputs a unique key representing the node/instance that will store the request's data. Suppose it stored in the instance 2, subsequent API calls with the same hash will retrieve the response from the instance 2, regardless of which instance that API called from.
-
-Using this consistent hashing approach, we can effectively utilize individual cache capacities. Adding more instances automatically increases the total cache capacity in Permify.
-
-You can learn more about consistent hashing from the following blog post: [Introducing Consistent Hashing](https://itnext.io/introducing-consistent-hashing-9a289769052e)
-
-:::info
-Note, however, that while the consistent hashing approach will distribute keys evenly across the cache nodes, it's up to the application logic to ensure the cache is used effectively (i.e., that it reads from and writes to the cache appropriately).
-:::
-
-Here is an example configuration:
-
-```yaml
-distributed:
- enabled: false
- nodes: ["permify-1:3480", "permify-2:3480", "permify-3:3480"]
-```
-
-Additional to that we’re using a [circuit breaker](https://blog.bitsrc.io/circuit-breaker-pattern-in-microservices-26bf6e5b21ff) pattern to detect and handle failures when the underlying database is unavailable. It prevents unnecessary calls when the database is down and handles the process on the rebooting phase.
-
-## Need any help ?
-
-Our team is happy help you to structure right architecture for your permission system. Feel free to [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
diff --git a/docs/versioned_docs/version-0.4.x/reference/configuration.md b/docs/versioned_docs/version-0.4.x/reference/configuration.md
deleted file mode 100644
index bda87c61..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/configuration.md
+++ /dev/null
@@ -1,465 +0,0 @@
-# Configuration File
-
-Permify offers various options for configuring your Permify API Server.
-
-Here is the example configuration YAML file with glossary below. You can also find
-this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-
-***Example config.yaml file***
-
-```yaml
-server:
- rate_limit: 100
- http:
- enabled: true
- port: 3476
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
- grpc:
- port: 3478
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
-
-logger:
- level: 'info'
-
-profiler:
- enabled: true
- port: 6060
-
-authn:
- method: preshared
- enabled: false
- keys: [ ]
-
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://localhost:9411/api/v2/spans'
- enabled: true
-
-meter:
- exporter: 'otlp'
- endpoint: 'localhost:4318'
- enabled: true
-
-service:
- circuit_breaker: false
- watch:
- enabled: false
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
- permission:
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
- relationship:
-
-database:
- engine: 'postgres'
- uri: 'postgres://user:password@host:5432/db_name'
- auto_migrate: false
- max_open_connections: 20
- max_idle_connections: 1
- max_connection_lifetime: 300s
- max_connection_idle_time: 60s
- garbage_collection:
- enable: true
- interval: 3m
- timeout: 3m
- window: 720h
- number_of_threads: 1
-```
-
-## Options
-
-server | Server Configurations
-
-
-#### Definition
-
-Server options to run Permify. (`grpc` and `http` available for now.)
-
-#### Structure
-
-```
-├── server
- ├── rate_limit
- ├── (`grpc` or `http`)
- │ ├── enabled
- │ ├── port
- │ └── tls
- │ ├── enabled
- │ ├── cert
- │ └── key
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|---------------------------|---------|---------------------------------------------------------------------|
-| [ ] | rate_limit | 100 | the maximum number of requests the server should handle per second. |
-| [x] | [ server_type ] | - | server option type can either be `grpc` or `http`. |
-| [ ] | enabled (for server type) | true | switch option for server. |
-| [x] | port | - | port that server run on. |
-| [x] | tls | - | transport layer security options. |
-| [ ] | enabled (for tls) | false | switch option for tls |
-| [ ] | cert | - | tls certificate path. |
-| [ ] | key | - | tls key pat |
-
-#### ENV
-
-| Argument | ENV | Type |
-|---------------------------|-----------------------------------|--------------|
-| rate_limit | PERMIFY_RATE_LIMIT | int |
-| grpc-port | PERMIFY_GRPC_PORT | string |
-| grpc-tls-enabled | PERMIFY_GRPC_TLS_ENABLED | boolean |
-| grpc-tls-key-path | PERMIFY_GRPC_TLS_KEY_PATH | string |
-| grpc-tls-cert-path | PERMIFY_GRPC_TLS_CERT_PATH | string |
-| http-enabled | PERMIFY_HTTP_ENABLED | boolean |
-| http-port | PERMIFY_HTTP_PORT | string |
-| http-tls-key-path | PERMIFY_HTTP_TLS_KEY_PATH | string |
-| http-tls-cert-path | PERMIFY_HTTP_TLS_CERT_PATH | string |
-| http-cors-allowed-origins | PERMIFY_HTTP_CORS_ALLOWED_ORIGINS | string array |
-| http-cors-allowed-headers | PERMIFY_HTTP_CORS_ALLOWED_HEADERS | string array |
-
-
-
-#### Definition
-
-You can choose to authenticate users to interact with Permify API.
-
-There are 2 authentication method you can choose:
-
-* [Pre Shared Keys](#pre-shared-keys)
-* [OpenID Connect](#openid-connect)
-
-#### Pre Shared Keys
-
-On this method, you must provide a pre shared keys in order to identify yourself.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── keys
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | true | switch option authentication config |
-| [x] | keys | - | Private key/keys for server authentication. Permify does not provide this key, so it must be generated by the users. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-preshared-keys | PERMIFY_AUTHN_PRESHARED_KEYS | string array |
-
-
-#### OpenID Connect
-
-Permify supports OpenID Connect (OIDC). OIDC provides an identity layer on top of OAuth 2.0 to address the shortcomings
-of using OAuth 2.0 for establishing identity.
-
-With this authentication method, you be able to integrate your existing Identity Provider (IDP) to validate JSON Web
-Tokens (JWTs) using JSON Web Keys (JWKs). By doing so, only trusted tokens from the IDP will be accepted for
-authentication.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── client-id
-| ├── issuer
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|-----------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | false | switch option authentication config |
-| [x] | client_id | - | This is the client ID of the application you're developing. It is a unique identifier that is assigned to your application by the OpenID Connect provider, and it should be included in the JWTs that are issued by the provider. |
-| [x] | issuer | - | This is the URL of the provider that is responsible for authenticating users. You will use this URL to discover information about the provider in step 1 of the authentication process. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-oidc-issuer | PERMIFY_AUTHN_OIDC_ISSUER | string |
-| authn-oidc-client-id | PERMIFY_AUTHN_OIDC_CLIENT_ID | string |
-
-
-
-
-
-tracer | Tracing Configurations
-
-
-#### Definition
-
-Permify integrated with [jaeger], [otlp], [signoz], and [zipkin] tacing tools to analyze performance and behavior of your
-authorization when using Permify.
-
-#### Structure
-
-```
-├── tracer
-| ├── exporter
-| ├── endpoint
-| ├── enabled
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------|
-| [x] | exporter | - | Tracer exporter, the options are `jaeger`, `otlp`, `signoz`, and `zipkin`. |
-| [x] | endpoint | - | export uri for tracing data. |
-| [ ] | enabled | false | switch option for tracing. |
-| [ ] | insecure | false | Whether to use HTTP instead of HTTPs for exporting the traces. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|----------------------|-------------------------------|--------------|
-| tracer-enabled | PERMIFY_TRACER_ENABLED | boolean |
-| tracer-exporter | PERMIFY_TRACER_EXPORTER | string |
-| tracer-endpoint | PERMIFY_TRACER_ENDPOINT | string |
-| tracer-insecure | PERMIFY_TRACER_INSECURE | boolean |
-
-
-
-#### Definition
-
-A consistent hashing ring ensures data distribution that minimizes reorganization when nodes are added or removed, improving scalability and performance in distributed systems."
-
-#### Structure
-
-```
-├── distributed
-| ├── enabled
-| ├── node
-| ├── node-name
-| ├── protocol
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|-----------|---------|--------------------------------------------------------------------------|
-| [x] | enabled | false | switch option for distributed. |
-| [x] | node | - | endpoint definition for distributed |
-| [x] | node-name | - | node name definition for protocol agent (for example serf node name) |
-| [x] | protocol | - | a field where you specify which gossip protocol to use, for example serf |
-
-
-#### ENV
-
-| Argument | ENV | Type |
-|------------------------|-------------------------------|---------|
-| distributed-enabled | PERMIFY_DISTRIBUTED_ENABLED | boolean |
-| distributed-node | PERMIFY_DISTRIBUTED_NODE | string |
-| distributed-node-name | PERMIFY_DISTRIBUTED_NODE_NAME | string |
-| distributed-protocol | PERMIFY_DISTRIBUTED_PROTOCOL | string |
-
-
-
-
-[jaeger]: https://www.jaegertracing.io/
-
-[otlp]: https://opentelemetry.io/
-
-[zipkin]: https://zipkin.io/
-
-[signoz]: https://signoz.io/
diff --git a/docs/versioned_docs/version-0.4.x/reference/contextual-tuples.md b/docs/versioned_docs/version-0.4.x/reference/contextual-tuples.md
deleted file mode 100644
index d92c536d..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/contextual-tuples.md
+++ /dev/null
@@ -1,246 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Contextual Tuples (Dynamic Permissions)
-
-## What is it ?
-
-Contextual tuples are relations that can be dynamically added to permission request operations. When you send these relations along with your requests, they get processed alongside existing relations in the database and will return a result.
-
-You can utilize Contextual Tuples in authorization checks that depend on certain dynamic or contextual data (such as location, time, IP address, etc) that have not been written as traditional Permify relation tuples.
-
-## Use Case
-
-Let's give an example to better understand the usage of Contextual Tuples aka dynamic permissions in access checks.
-
-Consider you're modeling an permission system for an internal application that belongs to an multi regional organization.
-
-### Authorization Model
-
-In that application an employee that belongs to HR department can view details of another employee if:
-
-1. If he/she is an Manager in HR department
-2. Connected via the branch's internal network or through the branch's VPN
-
-As you notice we can model the rule **1.** easily with our existing schema language, which gives ability to define arbitrary relations between users and objects such as manager of HR entity, as follows,
-
-```perm
-entity user {}
-
-entity organization {
-
- relation employee @user
- relation hr_manager @user @organization#employee
-
-}
-```
-
-But to create the `view_employee` permission in the organization entity, we need to consider not only whether the employee is a manager but also check the IP address.
-
-At this point, traditional relation tuples of Permify are insufficient since network address is an dynamic variable that cannot be added as static relations.
-
-So, to incorporate the IP address into our authorization model we will use Contextual Tuples and send dynamic relations values when sending the access check request.
-
-Let's extend our authorization model with adding contextual entities and relations to create the `view_employee` action.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation employee @user
- relation hr_manager @user @organization#employee
-
- relation ip_address_range @ip_address_range
-
- action view_employee = hr_manager and ip_address_range.user
-
-}
-
-entity ip_address_range {
- relation user @user
-}
-```
-
-A quick breakdown we define **type** for contextual variable `ip_address_range` and related them with user. Afterwards call that dynamic entities inside our organization entity and form the `view_employee` permission as follows:
-
-```perm
-action view_employee = hr_manager and ip_address_range.user
-```
-
-### Dynamic Access Check
-
-Since we cannot create relation statically for `ip_address_range` we need to send ip value on runtime, specifically when performing access control check.
-
-So let's say user Ashley trying to view employee X. And lets assume that,
-
-* She has a **manager** relation in HR department with the tuple `organization:1#hr_manager@user:1`
-* She connected to VPN which connected to network 192.158.1.38 - which is Branch's internal network.
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Permission: "view_employee",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
- ContextualTuples: []*v1.Tuple{
- {
- Entity: &v1.Entity {
- Type: "organization",
- Id: "1",
- },
- relation: "ip_address_range",
- Subject: &v1.Subject {
- Type: "ip_address_range",
- Id: "192.158.1.38",
- },
- },
- {
- Entity: &v1.Entity {
- Type: "ip_address_range",
- Id: "192.158.1.38",
- },
- relation: "user",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
- },
- }
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "organization",
- id: "1"
- },
- permission: "view_employee",
- subject: {
- type: "user",
- id: "1"
- },
- contextualTuples: [
- {
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "ip_address_range",
- subject: {
- type: "ip_address_range",
- id: "192.158.1.38",
- }
- },
- {
- entity: {
- type: "ip_address_range",
- id: "192.158.1.38"
- },
- relation: "user",
- subject: {
- type: "user",
- id: "1",
- }
- }
- ]
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_employee",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
- "contextual_tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "ip_address_range",
- "subject": {
- "type": "ip_address_range",
- "id": "192.158.1.38"
- }
- },
- {
- "entity": {
- "type": "ip_address_range",
- "id": "192.158.1.38"
- },
- "relation": "user",
- "subject": {
- "type": "user",
- "id": "1"
- }
- }
- ]
-}'
-```
-
-
-
-
-A quick note,
-
-When you use contextual tuples, the cache system will not be operational. This is because the cache system is written along with snapshots and if contextual tuples are written, using the cache would lead to incorrect results.
-
-Hence, to prevent this, the use of the cache is blocked at the time of the request. See more on the section [Permify Cache Mechanisims](./cache.md)
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/reference/glossary.md b/docs/versioned_docs/version-0.4.x/reference/glossary.md
deleted file mode 100644
index ccefde53..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/glossary.md
+++ /dev/null
@@ -1,45 +0,0 @@
----
-sidebar_position: 1
----
-
-# Glossary
-
-This section explains the basic concepts that commonly mentioned in Permify, as well as in this document. You can find the whole context on right menu.
-
-## Google Zanzibar (or just Zanzibar)
-
-[Google Zanzibar] is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
-
-Google published Zanzibar back in 2019, and in a short time it gained attention quickly. In fact some big tech companies started to shift their legacy authorization structure to Zanzibar style systems. Additionaly, Zanzibar based solutions increased over the time. All disclosure; [Permify] is an authorization system based on Zanzibar.
-
-For more about Zanzibar check our blog post, [Google Zanzibar In A Nutshell]
-
-[Google Zanzibar In A Nutshell]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-[Google Zanzibar]: https://research.google/pubs/pub48190/
-[Permify]: https://permify.co/
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it, we called it Permify Schema. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager etc. You can define your entities, relations between them and access control decisions with using Permify Schema.
-
-It includes set-algebraic operators such as inter- section and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-## Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. The simplest form of relational tuple structured as `entity # relation @ user` and each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-## Write Database - WriteDB
-
-Permify stores your relational tuples (authorization data) in **WriteDB**. You can configure it **WriteDB** when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-## Relationship Based Access Control (ReBAC)
-
-ReBAC is an access control model that defines permissions based on the relationships between entities and subjects of your system. Although ReBAC is best known for social networks because its core concept is about the network of relations, it can be applied beyond that.
-
-Check out [Relationship Based Access Control](https://permify.co/post/relationship-based-access-control-rebac/) post learn more about ReBAC and its common usage.
-
-## Domain Specific Language (DSL)
-
-Domain Specific Language is a language that specialized to a particular application domain. Permify has its DSL basically an authorization language which you can model and structure your authorization with it. We called it Permify Schema.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/reference/snap-tokens.md b/docs/versioned_docs/version-0.4.x/reference/snap-tokens.md
deleted file mode 100644
index 919974f5..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/snap-tokens.md
+++ /dev/null
@@ -1,54 +0,0 @@
-
-# Snap Tokens & Zookies
-
-A Snap Token is a token that consists of an encoded timestamp, which is used to ensure fresh results in access control checks.
-
-## Why you should use Snap Tokens ?
-
-Basically, you should use snap tokens both for consistency and performance. The main goal of Permify is to provide an authorization system that ensures excellent performance that can handle millions of requests from different environments while ensuring data consistency.
-
-Performance standards can be achievable with caching. In Permify, the cache mechanism eliminates re-computing of access control checks that once occurred, unless any relationships of resources don't change.
-
-Still, all caches suffer from the risk of becoming stale. If some schema update happens, or relations change then all of the caches should be updated according to it to prevent false positive or false negative results.
-
-Permify avoids this problem with an approach of snapshot reads. Simply, it ensures that access control is evaluated at a consistent point in time to prevent inconsistency.
-
-To achieve this, we developed tokens called Snap Tokens that consist of a timestamp that is compared in access checks to ensure that the snapshot of the access control is at least as fresh as the resource timestamp - basically its stored snap token.
-
-## How to use Snap Tokens
-
-Snap Tokens used in endpoints to represent the snapshot and get fresh results of the API's. It mainly used in [Write API] and [Check API].
-
-The general workflow for using snap token is getting the snap token from the response of Write API request - basically when writing a relational tuple - then mapped it with the resource. One way of doing that is storing snap token in the additional column in your relational database.
-
-Then this snap token can be used in endpoints. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-```json
-{
- "schema_version": "ce8siqtmmud16etrelag",
- "snap_token": "gp/twGSvLBc=",
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- },
-}
-```
-
-[Write API]: ../../api-overview/relationship/write-relationships
-[Check API]: ../../api-overview/permission/check-api
-
-#### All endpoints that used snap token
-
-- [Write API](../../api-overview/relationship/write-relationships)
-- [Check API](../../api-overview/permission/check-api)
-- [Expand API](../../api-overview/permission/expand-api)
-
-
-## More on Cache Mechanism
-
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisms](./cache.md)
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/reference/tracing.md b/docs/versioned_docs/version-0.4.x/reference/tracing.md
deleted file mode 100644
index 12810526..00000000
--- a/docs/versioned_docs/version-0.4.x/reference/tracing.md
+++ /dev/null
@@ -1,55 +0,0 @@
-
-# Tracing Tools
-
-Permify has integrations with some of popular tracing tools to analyze performance and behavior of your authorization. These are:
-
-- [Jaeger](https://www.jaegertracing.io/)
-- [OpenTelemetry](https://opentelemetry.io/)
-- [Signoz](https://signoz.io/)
-- [Zipkin](https://zipkin.io/)
-
-## Usage
-
-### Set Up
-
-Adding one of these tracing tools to your authorization system is quite simple, you just need to define it in the Permify configuration file as **tracer**.
-
-```yaml
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-```
-
-- ***exporter***: enter the tool name that you want to use. `jaeger` , `otlp`, `signoz`, and `zipkin`.
-- ***endpoint***: export url for tracing data.
-- ***disabled***: switch option for tracing.
-- ***insecure***: configures the exporter to connect to the collcetor using HTTP instead of HTTPS. This configuration is relevant only for `signoz` and `otlp`.
-
-**Example YAML configuration file**
-
-```yaml
-app:
- name: ‘permify’
-http:
- port: 3476
-logger:
- log_level: ‘debug’
- rollbar_env: ‘permify’
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-database:
- write:
- connection: 'postgres'
- database: 'morf-health-demo'
- uri: 'postgres://postgres:SphU4Uf3QXNntT@permify.us-east-1.rds.amazonaws.com:5432'
- pool_max: 2
-```
-
-After running Permify in your server, you should run Zipkin as well. If you're using docker here is the docker pull request for Zipkin:
-
-```
-docker run -d -p 9411:9411 openzipkin/zipkin
-```
diff --git a/docs/versioned_docs/version-0.4.x/use-cases.md b/docs/versioned_docs/version-0.4.x/use-cases.md
deleted file mode 100644
index 6fae082c..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases.md
+++ /dev/null
@@ -1,20 +0,0 @@
----
-id: use-cases
-title: Common Use Cases
-slug: /use-cases
----
-
-# Common Use Cases
-
-Common modeling patterns and uses cases we have seen so far from the users from small startups with simple RBAC to multi-regional enterprises that run tens of Permify instances with deeply nested relationships.
-
-:::success Missing a specific use case?
-No problem, let's discuss it together! just open an [issue](https://github.com/Permify/permify/issues) about it or join our conversation at [discord](https://discord.gg/n6KfzYxhPp)!
-:::
-
-```mdx-code-block
-import {CaseList} from '@site/src/components/Case';
-import list from './use-cases/_list.json';
-
-
-```
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/_category_.json b/docs/versioned_docs/version-0.4.x/use-cases/_category_.json
deleted file mode 100644
index 9f9db2d4..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Common Use Cases",
- "position": 8,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/_list.json b/docs/versioned_docs/version-0.4.x/use-cases/_list.json
deleted file mode 100644
index 7b6e7fb1..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/_list.json
+++ /dev/null
@@ -1,32 +0,0 @@
-[
- {
- "id": 1,
- "title": "Role Based Access Control (RBAC)",
- "description": "Want to implement role to your application ? Define an entity and manage your roles throught your applications.",
- "link": "./simple-rbac"
- },
- {
- "id": 2,
- "title": "Attribute Based Access Control (ABAC)",
- "description": "Grant access what based on specific characteristics or attributes.",
- "link": "./abac"
- },
- {
- "id": 3,
- "title": "Relationship Based Access Control (ReBAC)",
- "description": "Define permissions based on the relationships between resources and subjects in your system",
- "link": "./rebac"
- },
- {
- "id": 4,
- "title": "Custom Roles",
- "description": "Assign specific permissions to users based on the custom roles that they are assigned within the system.",
- "link": "./custom-roles"
- },
- {
- "id": 5,
- "title": "Multi Tenancy",
- "description": "Create custom authorization schema and relation tuples for the different tenants and manage them in a single place.",
- "link": "./multi-tenancy"
- }
-]
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/abac.md b/docs/versioned_docs/version-0.4.x/use-cases/abac.md
deleted file mode 100644
index e3945ec0..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/abac.md
+++ /dev/null
@@ -1,590 +0,0 @@
-# Attribute Based Access Control (Beta)
-
-This page explains design approach of Permify ABAC support as well as demonstrates how to create and use attribute based permissions in Permify.
-
-:::info
-You can find Permify's support for ABAC in our [beta release](https://github.com/Permify/permify/pkgs/container/permify-beta) and explore the active [API documentation](https://permify.github.io/permify-swagger/) for the ***beta*** version.
-
-We are eager to hear your thoughts and looking forward to your feedback!
-:::
-
-# What is Attribute Based Access Control (ABAC)?
-
-Attribute-Based Access Control (ABAC) is like a security guard that decides who gets to access what based on specific characteristics or "attributes".
-
-These attributes can be associated with users, resources, or the environment, and their values can influence the outcome of an access request.
-
-Let’s make an analogy, it’s the best of way to understanding complex ideas.
-
-Think about an amusement park, and there are 3 different rides. In order to access each ride, you need to obtain different qualities. For the;
-
-1. first ride you need to be over 6ft tall.
-2. second ride you need to be under 200lbs.
-3. third ride you need to be between 12 - 18 years old.
-
-Similar to this ABAC check certain qualities that you defined on users, resources, or the environment.
-
-# Why Would Need ABAC?
-
-It’s obvious but simple answer is “use cases”… Sometimes, using ReBAC and RBAC isn't the best fit for the job. It's like using winter tires on a hot desert road, or summer tires in a snowstorm - they're just not the right tools for the conditions.
-
-1. **Geographically Restricted:** Think of ABAC like a bouncer at a club who only lets in people from certain towns. For example, a movie streaming service might only show certain movies in certain countries because of rules about who can watch what and where.
-2. **Time-Based:** ABAC can also act like a parent setting rules about when you can use the computer. For example, a system might only let you do certain things during office hours.
-3. **Compliance with Privacy Regulations:** ABAC can help follow rules about privacy. For example, a hospital system might need to limit who can see a patient's data based on the patient's permission, why they want to see it, and who the person is.
-4. **Limit Range:** ABAC can help you create a rules defining a number limit or range. For instance, a banking system might have limits for wiring or withdrawing money.
-5. **Device Information:** ABAC can control access based on attributes of the device, such as the device type, operating system version, or whether the device has the latest security patches.
-
-As you can see ABAC has more contextual approach. You can define access rights regarding context around subject and object in an application.
-
-# Introducing New Key Elements
-
-To support ABAC in Permify, we've added two main components into our DSL: attributes and rules.
-
-## Attribute
-
-Attributes are used to define properties for entities in specific data types. For instance, an attribute could be an IP range associated with an organization, defined as a string array:
-
-```sql
-attribute ip_range string[]
-```
-
-There are different types of attributes you can use;
-
-### Boolean
-
-For attributes that represent a binary choice or state, such as a yes/no question, the `Boolean` data type is an excellent choice.
-
-```go
-entity post {
- attribute is_public boolean
-
- permission view = is_public
-}
-```
-
-
-
-### String
-
-String can be used as attribute data type in a variety of scenarios where text-based information is needed to make access control decisions. Here are a few examples:
-
-- **Location:** If you need to control access based on geographical location, you might have a location attribute (e.g., "USA", "EU", "Asia") stored as a string.
-- **Device Type**: If access control decisions need to consider the type of device being used, a device type attribute (e.g., "mobile", "desktop", "tablet") could be stored as a string.
-- **Time Zone**: If access needs to be controlled based on time zones, a time zone attribute (e.g., "EST", "PST", "GMT") could be stored as a string.
-- **Day of the Week:** In a scenario where access to certain resources is determined by the day of the week, the string data type can be used to represent these days (e.g., "Monday", "Tuesday", etc.) as attributes!
-
-```sql
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute location string[]
-
- permission view = check_location(request.current_location, location) or admin
-}
-
-rule check_location(current_location string, location string[]) {
- current_location in location
-}
-```
-
-
-
-### Integer
-
-Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
-- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
-- **Resource Size or Length:** If access to resources is controlled based on their size or length (like a document's length or a file's size), these can be stored as integer attributes.
-- **Version Number:** If access control decisions need to consider the version number of a resource (like a software version or a document revision), these can be stored as integer attributes.
-
-```jsx
-entity content {
- permission view = check_age(request.age)
-}
-
-rule check_age(age integer) {
- age >= 18
-}
-```
-
-
-
-### Double
-
-Double can be used as attribute data type in several scenarios where precise numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Usage Limit:** If a user has a usage limit (like the amount of storage they can use or the amount of data they can download), and this limit needs to be represented with decimal precision, it can be stored as a double attribute.
-- **Transaction Amount:** In a financial system, if access control decisions need to consider the amount of a transaction, and this amount needs to be represented with decimal precision (like $100.50), these amounts can be stored as double attributes.
-- **User Rating:** If access control decisions need to consider a user's rating (like a rating out of 5 with decimal points, such as 4.7), these ratings can be stored as double attributes.
-- **Geolocation:** If access control decisions need to consider precise geographical coordinates (like latitude and longitude, which are often represented with decimal points), these coordinates can be stored as double attributes.
-
-```sql
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-
-
-## Rule
-
-Rules are structures that allow you to write specific conditions for the model. They accept parameters and are based on conditions. For example, a rule could be used to check if a given IP address falls within a specified IP range:
-
-```sql
-rule check_ip_range(ip string, ip_range string[]) {
- ip in ip_range
-}
-```
-
-## Evaluation
-
-**Model**
-
-```sql
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute ip_range string[]
-
- permission view = check_ip_range(request.ip_address, ip_range) or admin
-}
-
-rule check_ip_range(ip_address string, ip_range string[]) {
- ip in ip_range
-}
-```
-
-In this case, the part written as 'context' refers to the context within the request. Any type of data can be added from within the request and can be called within model.
-
-For instance,
-
-```sql
-...
-"context": {
- "ip_address": "187.182.51.206",
- "day_of_week": "monday"
-}
-...
-```
-
-**Relationships**
-
-- organization:1#admin@user:1
-
-**Attributes**
-
-- organization:1$ip_range|string[]:[‘187.182.51.206’, ‘250.89.38.115’]
-
-**Check request**
-
-```sql
-{
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view",
- "subject" : {
- "type": "user",
- "id": "1"
- },
- "context": {
- "ip_address": "187.182.51.206"
- }
-}
-```
-
-**Check Evolution Sub Queries Organization View**
-→ organization:1$check_ip_range(context.ip_address,ip_range) → true
-→ organization:1#admin@user:1 → true
-
-**Cache Mechanism**
-The cache mechanism works by hashing the snapshot of the database, schema version, and sub-queries as keys and adding their results, so it will operate in the same way in calls as in relationships. For example,
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_organization:1#admin@user:1 → true
-- check_{snapshot}_{schema_version}_{context}_organization:1$check_ip_range(ip_range) → true
-
-## Some Use Cases
-
-### Example of Public/Private Repository
-
-In this example, **`is_public`** is defined as a boolean attribute. If an attribute is boolean, it can be directly written without the need for a rule. This is only applicable for boolean types.
-
-```sql
-entity user {}
-
-entity post {
-
- relation owner @user
-
- attribute is_public boolean
-
- permission view = is_public or owner
- permission edit = owner
-}
-```
-
-In this context, if the **`is_public`** attribute of the repository is set to true, everyone can view it. If it's not public (i.e., **`is_public`** is false), only the owner, in this case **`user:1`**, can view it.
-
-The permissions in this model are defined as such:
-
-**`permission view = is_public or owner`**
-
-This means that the 'view' permission is granted if either the repository is public (**`is_public`** is true) or if the current user is the owner of the repository.
-
-**relationships:**
-
-- post:1#owner@user:1
-
-**attributes:**
-
-- post:1$is_public|boolean:true
-
-**Check Evolution Sub Queries Post View**
-→ post:1#is_public → true
-→ post:1#admin@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_post:1$is_public → true
-- check_{snapshot}_{schema_version}_{context}_post:1#admin@user:1 → true
-
-### Example of Weekday
-
-In this example, to be able to view the repository, it must not be a weekend, and the user must be a member of the organization.
-
-```sql
-entity user {}
-
-entity organization {
-
- relation member @user
-
- permission view = is_weekday(request.day_of_week) and member
-}
-
-entity repository {
-
- relation organization @organization
-
- permission view = organization.view
-}
-
-rule is_weekday(day_of_week string) {
- day_of_week != 'saturday' && day_of_week != 'sunday'
-}
-```
-
-The permissions in this model state that to 'view' the repository, the user must fulfill two conditions: the current day (according to the context data **`day_of_week`**) must not be a weekend (determined by the **`is_weekday`** rule), and the user must be a member of the organization that owns the repository.
-
-**Relationships:**
-
-- organization:1#member@user:1
-
-**Check Evolution Sub Queries Organization View**
-→ organization:1$is_weekday(context.day_of_week) → true
-→ organization:1#member@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_organization:1$is_weekday(context.day_of_week) → true
-- check_{snapshot}_{schema_version}_{context}_post:1#member@user:1 → true
-
-### Example of Banking System
-
-This model represents a banking system with two entities: **`user`** and **`account`**.
-
-1. **`user`**: Represents a customer of the bank.
-2. **`account`**: Represents a bank account that has an **`owner`** (which is a **`user`**), and a **`balance`** (amount of money in the account).
-
-```sql
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-**The check_balance rule:** This rule verifies if the withdrawal amount is less than or equal to the account's balance and doesn't exceed 5000 (the maximum amount allowed for a withdrawal). It accepts two parameters, the withdrawal amount (amount) and the account's current balance (balance).
-**The owner check:** This condition checks if the person requesting the withdrawal is the owner of the account.
-
-Both of these conditions need to be true for the **`withdraw`** permission to be granted. In other words, a user can withdraw money from an account only if they are the owner of that account, and the amount they want to withdraw is within the account balance and doesn't exceed 5000.
-
-**Relationships**
-
-- account:1#owner@user:1
-
-**Attributes**
-
-- account:1$balance|double:4000
-
-**Check Evolution Sub Queries For Account Withdraw**
-→ account:1$check_balance(context.amount,balance) → true
-→ account:1#owner@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_account:1$check_balance(context.amount,balance) → true
-- check_{snapshot}_{schema_version}_{context}_account:1#owner@user:1 → true
-
-### Hierarchical Usage
-
-In this model:
-
-1. **`employee`**: Represents an individual worker. It has no specific attributes or relations in this case.
-2. **`organization`**: Represents an entire organization, which has a **`founding_year`** attribute. The **`view`** permission is granted if the **`check_founding_year`** rule (which checks if the organization was founded after 2000) returns true.
-3. **`department`**: Represents a department within the organization. It has a **`budget`** attribute and a relation to its parent **`organization`**. The **`view`** permission is granted if the department's budget is more than 10,000 (checked by the **`check_budget`** rule) and if the **`organization.view`** permission is true.
-
-Note: In this model, permissions can refer to higher-level permissions (like **`organization.view`**). However, you cannot use the attribute of a relation in this way. For example, you cannot directly reference **`organization.founding_year`** in a permission expression. Permissions can depend on permissions in a related entity, but not directly on the related entity's attributes.
-
-```sql
-entity employee {}
-
-entity organization {
- attribute founding_year integer
-
- permission view = check_founding_year(founding_year)
-}
-
-entity department {
- relation organization @organization
- attribute budget double
-
- permission view = check_budget(budget) and organization.view
-}
-
-rule check_founding_year(founding_year integer) {
- founding_year > 2000
-}
-
-rule check_budget(budget double) {
- budget > 10000
-}
-```
-
-**Relationships**
-
-- department:1#organization@organization:1
-- department:1#organization@organization:2
-
-**Attributes**
-
-- department:1$budget|double:20000
-- organization:1$organization|integer:2021
-
-**Check Evolution Sub Queries For Department View**
-→ department:1$check_budget(budget) → true
-→ department:1#organization@user:1 → true
- → organization:2$check_founding_year(founding_year) → false
- → organization:1$check_founding_year(founding_year) → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_department:1$check_budget(budget) → true
-- check_{snapshot}_{schema_version}_{context}_organization:2$check_founding_year(founding_year) → false
-- check_{snapshot}_{schema_version}_{context}_organization:1$check_founding_year(founding_year) → true
-
-## How To Use Demo
-
-**Install Permify nightly release**
-
-```yaml
-docker pull **ghcr.io/permify/permify-beta:latest**
-```
-
-**New Validation Yaml Structure**
-
-```yaml
-schema: >-
- {string schem}
-
-relationships:
- - entity_name:entity_id#relation@subject_type:subject_id
-
-attributes:
- - entity_name:entity_id#attribute@attribute_type:attribute_value
-
-scenarios:
- - name: "name"
- description: "description"
- checks:
- - entity: "entity_name:entity_id"
- subject: "subject_name:subject_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result
- entity_filters:
- - entity_type: "entity_name"
- subject: "subject_name:subject_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result_array
- subject_filters:
- - subject_reference: "subject_name"
- entity: "entity_name:entity_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result_array
-```
-
-**Note:** The 'data' field within the 'context' can be assigned a desired value as a key-value pair. Later, this value can be retrieved within the model using 'request.key'.
-
-**Example in validation file:**
-
-```yaml
-context:
- tuples: []
- attributes: []
- data:
- day_of_week: "saturday"
-```
-
-This YAML snippet specifies a validation context with no tuples or attributes, and a data field indicating the day of the week is Saturday.
-
-**Example in model**
-
-```yaml
-permission delete = is_weekday(request.day_of_week)
-```
-
-In the model, a **`delete`** permission rule is set. It calls the function **`is_weekday`** with the value of **`day_of_week`** from the context. If **`is_weekday("saturday")`** is true, the delete permission is granted.
-
-**Create Validation File**
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation member @user
-
- attribute credit integer
-
- permission view = check_credit(credit) and member
- }
-
- entity repository {
-
- relation organization @organization
-
- attribute is_public boolean
-
- permission view = is_public
- permission edit = organization.view
- permission delete = is_weekday(request.day_of_week)
- }
-
- rule check_credit(credit integer) {
- credit > 5000
- }
-
- rule is_weekday(day_of_week string) {
- day_of_week != 'saturday' && day_of_week != 'sunday'
- }
-
-relationships:
- - organization:1#member@user:1
- - repository:1#organization@organization:1
-
-attributes:
- - organization:1$credit|integer:6000
- - repository:1$is_public|boolean:true
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "repository:1"
- subject: "user:1"
- context:
- assertions:
- view: true
- - entity: "repository:1"
- subject: "user:1"
- context:
- tuples: []
- attributes: []
- data:
- day_of_week: "saturday"
- assertions:
- view: true
- delete: false
- - entity: "organization:1"
- subject: "user:1"
- context:
- assertions:
- view: true
- entity_filters:
- - entity_type: "repository"
- subject: "user:1"
- context:
- assertions:
- view : ["1"]
- subject_filters:
- - subject_reference: "user"
- entity: "repository:1"
- context:
- assertions:
- view : ["1"]
- edit : ["1"]
-```
-
-**Run validation command**
-
-```yaml
-docker run -v {your_config_folder}:/config **ghcr.io/permify/permify-beta:latest validate /config/validation.yaml**
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/custom-roles.md b/docs/versioned_docs/version-0.4.x/use-cases/custom-roles.md
deleted file mode 100644
index 1df64794..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/custom-roles.md
+++ /dev/null
@@ -1,74 +0,0 @@
-
-# Custom Roles
-
-This document highlights a solution for custom roles with [Permify Schema]. In this tutorial, we will create custom **admin** and **member** roles in a project. Then set the permissions of these roles according to their capabilities on the dashboard and tasks.
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity role {
- relation assignee @user
-}
-
-entity dashboard {
- relation view @role#assignee
- relation edit @role#assignee
-}
-
-entity task {
- relation view @role#assignee
- relation edit @role#assignee
-}
-```
-
-This schema encompasses several crucial elements to structure a custom role-based access control system. The role entity serves as a particularly important component, as it enables the creation of multiple custom roles. These roles may vary according to the needs of the application and could include roles like **admin**, **editor**, or **member**, among others.
-
-Once these custom roles have been established, they can be assigned to other entities in the system. Specifically, in this schema, these roles are attached to the dashboard and task entities. Each of these entities, dashboard and task, has pre-defined permissions associated with them. These permissions, defined within the schema or model, could represent various operations such as **view**, **edit**, and so forth.
-
-With this setup, it's possible to map these pre-defined permissions of the dashboard and task entities to the custom roles that have been created. This implies that specific permissions, for instance, **view** and **edit** for a dashboard or a task, could be assigned to a particular custom role.
-
-Based on this model, the example relationships are as follows. With these relationships, custom roles such as **admin** and **member** have been created.
-
-## Relationships
-
-dashboard:project-progress#view@role:admin#assignee
-
-dashboard:project-progress#view@role:member#assignee
-
-dashboard:project-progress#edit@role:admin#assignee
-
-task:website-design-review#view@role:admin#assignee
-
-task:website-design-review#view@role:member#assignee
-
-task:website-design-review#edit@role:admin#assignee
-
-Together with these relationships and the model, a view has been created for the **project-progress** dashboard and the **website-design-review** task as shown in the table below.
-
-| permission | admin | member |
-|--------------------|-------|---------|
-| **dashboard:view** | ✅ | ✅ |
-| **dashboard:edit** | ✅ | ⛔ |
-| **task:view** | ✅ | ✅ |
-| **task:edit** | ✅ | ⛔ |
-
-
-Subsequently, you can make authorization decisions by assigning these custom roles to the users that you have created.
-
-role:member#assignee@user:1
-
-When we write these relationship, the final situation will be as follows.
-
-`Can user:1 view dashboard:project-progress?` gives **Allow** result since the `user:1` is assignee of `role:member` and `role:member` has `dashboard:project-progress#view` permission.
-
-`Can user:1 view task:website-design-review?` gives **Denied** result since the `user:1` is not assignee of `role:admin`.
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/multi-tenancy.md b/docs/versioned_docs/version-0.4.x/use-cases/multi-tenancy.md
deleted file mode 100644
index 00a455b4..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/multi-tenancy.md
+++ /dev/null
@@ -1,149 +0,0 @@
----
-title: "Multi Tenancy"
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-With version 0.3.x Permify moved to a tenancy-based infrastructure, which affects almost all of the API operations.
-
-## Multi Tenancy on Permify
-
-Multi-tenancy in Permify refers to an authorization architecture, where a single Permify authorization service serves multiple applications/organizations (tenants).
-
-This allows the ability to customize the authorization for each tenant's specific needs. With Multi-Tenancy support, you can create custom authorization schema and relation tuples accordingly for the different tenants and manage them in a single place.
-
-For the users that don't have/need multi-tenancy in their authorization structure, we created a pre-inserted tenant (id: **t1**) that comes default when you serve a Permify service.
-
-Several things changed when we moved to tenant based infrastructure, these are:
-
-* [API endpoints now have Tenant ID field](#api-endpoints-now-have-tenant-id-field)
-* [Added Tenancy Service](#added-tenancy-service)
-* [WriteDB tables and tenant id column](#writedb-tables-and-tenant-id-column)
-
-### API endpoints now have Tenant ID field
-
-All API endpoints now have a `tenant_id` mandatory field. Let's examine a check request below,
-
-#### Check API
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), & v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: & v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-Users that come from version 0.2.x and users that have a single tenant can enter **t1** as tenant id. See changes on the other endpoints from [API Overview Section](../api-overview.md).
-
-### Added Tenancy Service
-
-To manage tenants we have added a Tenancy service; you can create, delete and list tenants accordingly. See the [Tenancy Service](../../api-overview/tenancy) on Using The API section.
-
-### WriteDB tenancy table and tenant id column
-
-#### Tenant Table
-
-Tenants table have added the Write DB to store tenant's details. The new WriteDB folder structure changed as follows:
-```
-tables
-├── migrations
-├── relation_tuples
-├── schema_definitions
-├── tenants
-├── transactions
-```
-
-#### Tenant ID Column
-
-Relation tuples and schema definition tables now have a tenant_id column, which stores the id of the tenant that data belongs.
-
-Let's take a look at a snapshot of the demo table on an example WriteDB.
-
-Example Relation Tuples data table:
-
-
-Example Schema Definitions data table
-
-
-## Need any help ?
-
-Our team is happy to help! If you struggle with migration or need help on using the multi-tenancy, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/nested-hierarchies.md b/docs/versioned_docs/version-0.4.x/use-cases/nested-hierarchies.md
deleted file mode 100644
index 787a5acc..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/nested-hierarchies.md
+++ /dev/null
@@ -1,73 +0,0 @@
-
-# Nested Hierarchies
-
-This use case shows solving deeply nested hierarchies with [Permify Schema]. We have a unique **action** usage for nested hierarchies, where parent and child entities can share permissions between them. Let's follow the below team project authorization model to examine this case.
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organization user types
- relation admin @user
-}
-
-entity team {
-
- //refers to organization that team belongs to
- relation org @organization
-
- // Only the organization administrator can edit
- action edit = org.admin
-}
-
-entity project {
-
- //refers to team that project belongs to
- relation team @team
-
- // This action responsible for nested permission inheritance
- // team.edit refers edit action on the team entity which we defined above
- // Semantics of this is: Only the organization administrator, who has the
- // team, to which this project belongs can edit.
- action edit = team.edit
-}
-```
-
-## Sample Relational Tuples
-
-organization:1#admin@user:1
-
-team:1#org@organization:1#...
-
-project:1#team@team:1#...
-
-Lets assume we created above [relational tuples]. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** result since the `user:1` is organizational admin and `project:1` belongs to `team:1`, which belongs to `organization:1`.
-
-[relational tuples]: ../getting-started/sync-data.md
-
-Let's break down this case,
-
-```perm
-entity project {
-
- relation team @team
-
- action edit = team.edit
-}
-```
-
-Above `team.edit` points out the **edit** action in the **team** (that project belongs to).
-
-And edit action on the team entity: `action edit = org.admin` states that only **organization (which that team belongs to) admins** can edit. So our project inherits that action and conducts a result accordingly.
-
-If we roll back to our enforcement: `Can user:1 edit project:1?` gives **Allow** result, because user:1 is admin in an organization that the projects' parent team belongs to.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/organizational.md b/docs/versioned_docs/version-0.4.x/use-cases/organizational.md
deleted file mode 100644
index f5438bf0..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/organizational.md
+++ /dev/null
@@ -1,149 +0,0 @@
-
-
-# Organization Specific Resources
-
-Group your users by organization with giving them access organizational-wide resources. In this use case we'll follow a simplified version of Github's access control that shows how to model basic repository push, read and delete permissions with our authorization language DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents user of this repository
- relation owner @user
-
- // permissions
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 3 entities,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that user and repositories belongs.
-
-- `repository`, represents a repository in a github.
-
-### Relations
-
-To define relation, **relations** needed to be created as entity attributes.
-
-#### organization entity
-
-In our schema we defined 2 relation in organization entity, respectively; ``admin`` and ``member``
-
-```perm
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-``admin`` indicates that the user got an administrative role in that organization and with the same logic ``member`` represents the default user that belongs to that organization.
-
-#### repository entity
-
-Repository entities have 2 relations, these are ``parent`` and ``owner``. Both of these relations represents actual database relations with other entities rather than a role-based approach likewise to the **organization** entity above.
-
-```perm
-entity repository {
-
- relation parent @organization
- relation owner @user
-
-}
-```
-
-``parent`` relation represents the parent organization with a repository. And ``owner`` represents the specific user, the repository's owner.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### repository actions
-
-In our schema, we examined one of the main functionalities can the user make on any GitHub repository. These are pushing to the repo, reading & viewing the repo, and deleting that repo.
-
-We can say only,
-
-- Repository owners can ``push`` to that repo.
-- Repository owners, who also need to have an administrative role or be an owner of the parent organization, can ``read``.
-- Repository owners or administrative roles in an organization can ``delete`` the repository.
-
-```
-entity repository {
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-Since ``parent` represents the parent organization of repository. It can reach repositories parent organization relations with comma. So,
-
-- ``parent.admin``
-indicates admin role on organization
-
-- ``parent.member``
-indicates member of that organization.
-
-## Example Relational Tuples
-
-organization:2#admin@user:daniel
-
-organization:54#member@user:ege
-
-organization:12#member@user:jack
-
-repository:34#parent@organization:54
-
-repository:68#owner@user:12
-
-repository:12#owner@user:46
-
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/ownership.md b/docs/versioned_docs/version-0.4.x/use-cases/ownership.md
deleted file mode 100644
index f7dc5b94..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/ownership.md
+++ /dev/null
@@ -1,42 +0,0 @@
-
-# Ownership
-
-Granting privileges to the owner of the resource is a common pattern that many applications follow. Generally we want creators of the resource - document, post, comment etc - have superior power on that resource. Check out the below model see how ownership can be modeled with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity comment {
-
- // represents comment's owner
- relation owner @user
-
- // permissions
- action edit = owner
- action delete = owner
-}
-
-```
-
-## Sample Relational Tuples
-
-comment:2#owner@user:1
-
-comment:3#owner@user:51
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/rebac.md b/docs/versioned_docs/version-0.4.x/use-cases/rebac.md
deleted file mode 100644
index 36ad8d54..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/rebac.md
+++ /dev/null
@@ -1,426 +0,0 @@
-
-# Relationship Based Access Control
-
-Permify has designed and structured as a true [Relationship Based Access Control(ReBAC)](https://permify.co/post/relationship-based-access-control-rebac/) solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-
-Here are some common use cases where you can benefit from using ReBAC models in your Permify Schema.
-
-- [Protecting Organizational-Wide Resources](#protecting-organizational-wide-resources)
-- [Deeply Nested Hierarchies](#deeply-nested-hierarchies)
-- [User Groups & Team Permissions](#user-groups--team-permissions)
-
-## Protecting Organizational-Wide Resources
-
-This example demonstrate grouping the users by organization with giving them access organizational-wide resources.
-
-In this use case we'll follow a simplified version of Github's access control that shows how to model basic repository push, read and delete permissions with our authorization language DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents user of this repository
- relation owner @user
-
- // permissions
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-### Schema Deconstruction
-
-#### Entities
-
-This schema consists 3 entities,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that user and repositories belongs.
-
-- `repository`, represents a repository in a github.
-
-#### Relations
-
-To define relation, **relations** needed to be created as entity attributes.
-
-##### organization entity
-
-In our schema we defined 2 relation in organization entity, respectively; ``admin`` and ``member``
-
-```perm
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-``admin`` indicates that the user got an administrative role in that organization and with the same logic ``member`` represents the default user that belongs to that organization.
-
-##### repository entity
-
-Repository entities have 2 relations, these are ``parent`` and ``owner``. Both of these relations represents actual database relations with other entities rather than a role-based approach likewise to the **organization** entity above.
-
-```perm
-entity repository {
-
- relation parent @organization
- relation owner @user
-
-}
-```
-
-``parent`` relation represents the parent organization with a repository. And ``owner`` represents the specific user, the repository's owner.
-
-#### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-##### repository actions
-
-In our schema, we examined one of the main functionalities can the user make on any GitHub repository. These are pushing to the repo, reading & viewing the repo, and deleting that repo.
-
-We can say only,
-
-- Repository owners can ``push`` to that repo.
-- Repository owners, who also need to have an administrative role or be an owner of the parent organization, can ``read``.
-- Repository owners or administrative roles in an organization can ``delete`` the repository.
-
-```
-entity repository {
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-Since ``parent` represents the parent organization of repository. It can reach repositories parent organization relations with comma. So,
-
-- ``parent.admin``
-indicates admin role on organization
-
-- ``parent.member``
-indicates member of that organization.
-
-### Sample Relational Tuples
-
-organization:2#admin@user:daniel
-
-organization:54#member@user:ege
-
-organization:12#member@user:jack
-
-repository:34#parent@organization:54
-
-repository:68#owner@user:12
-
-repository:12#owner@user:46
-
-
-.
-.
-.
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-For instance, you can define that a user has certain permissions because of their relation to other entities.
-
-An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group. This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-## Deeply Nested Hierarchies
-
-This use case shows solving deeply nested hierarchies with [Permify Schema].
-
-We have a unique **action** usage for nested hierarchies, where parent and child entities can share permissions between them. Let's follow the below team project authorization model to examine this case.
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organization user types
- relation admin @user
-}
-
-entity team {
-
- //refers to organization that team belongs to
- relation org @organization
-
- // Only the organization administrator can edit
- action edit = org.admin
-}
-
-entity project {
-
- //refers to team that project belongs to
- relation team @team
-
- // This action responsible for nested permission inheritance
- // team.edit refers edit action on the team entity which we defined above
- // Semantics of this is: Only the organization administrator, who has the
- // team, to which this project belongs can edit.
- action edit = team.edit
-}
-```
-
-### Sample Relational Tuples
-
-organization:1#admin@user:1
-
-team:1#org@organization:1#...
-
-project:1#team@team:1#...
-
-Lets assume we created above [relational tuples]. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** result since the `user:1` is organizational admin and `project:1` belongs to `team:1`, which belongs to `organization:1`.
-
-[relational tuples]: ../getting-started/sync-data.md
-
-Let's break down this case,
-
-```perm
-entity project {
-
- relation team @team
-
- action edit = team.edit
-}
-```
-
-Above `team.edit` points out the **edit** action in the **team** (that project belongs to).
-
-And edit action on the team entity: `action edit = org.admin` states that only **organization (which that team belongs to) admins** can edit. So our project inherits that action and conducts a result accordingly.
-
-If we roll back to our enforcement: `Can user:1 edit project:1?` gives **Allow** result, because user:1 is admin in an organization that the projects' parent team belongs to.
-
-## User Groups & Team Permissions
-
-This use case shows how to organize permissions based on groupings of users or resources. In this use case we'll follow a simple project management app with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- // represents owner or creator of the team
- relation owner @user
-
- // represents direct member of the team
- relation member @user
-
- // reference for organization that team belong
- relation org @organization
-
- // organization admins or owners can edit, delete the team details
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- // to invite someone you need to be admin and either owner or member of this team
- action invite = org.admin and (owner or member)
-
- // only owners can remove users
- action remove_user = owner
-
-}
-
-entity project {
-
- // references for team and organization that project belongs
- relation team @team
- relation org @organization
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-### Schema Deconstruction
-
-#### Entities
-
-This schema consists 4 entity,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that contain teams.
-
-- `team`, represents teams, which belongs to a organization.
-
-- `project`, represents projects that belongs teams.
-
-#### Relations
-
-##### organization entity
-
-We can use **relations** to define roles.
-
-The organization entity has 2 relations ``admin`` and ``member`` users. Think of these as organizational-wide roles.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-##### team entity
-
-The eeam entity has its own relations respectively, ``owner``, ``member`` and ``org``
-
-```perm
-entity team {
-
- relation owner @user
- relation member @user
- relation org @organization
-
-}
-```
-
-##### project entity
-
-Project entity has ``team`` and ``org`` relations. Both these relations represents parent relationship with other entites, parent team and parent organization.
-
-```perm
-entity project {
-
- relation team @team
- relation org @organization
-
-}
-```
-
-#### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or*** and ***not*** operators to define actions.
-
-##### team actions
-
-- Only organization ***admin (admin role)*** and ***team owner*** can perform editing and deleting team spesific resources.
-
-- Moreover, for inviting a colleague to a team you must have ***admin role*** and either be a ***owner*** or ***member*** on that team.
-
-- To remove users in team you must be a ***owner*** of that team.
-
-And these rules reflects Permify Schema as:
-
-```perm
-entity team {
-
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- action invite = org.admin and (owner or member)
- action remove_user = owner
-
-}
-```
-
-##### project actions
-
-And there are the project actions below. It consists of checking access for basic operations such as viewing, editing, or deleting project resources.
-
-```perm
-entity project {
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-### Sample Relational Tuples
-
-team:2#member@user:daniel
-
-team:54#owner@user:daniel
-
-organization:12#admin@user:jack
-
-organization:51#member@user:jack
-
-organiation:41#member@team:42#member
-
-project:35#team@team:34#....
-
-
-.
-.
-.
-.
-.
-
-
-organization:41#member@team:42#member
-
-**--> represents members of team 42 also members in organization 41**
-
-project:35#team@team:34#....
-
-**--> represents project 54 is in team 34**
-
-## Need any help on Authorization ?
-
-Our team is happy to help you anything about authorization. If you'd like to learn more about using Permify in your app or have any questions, [schedule a call with one of our founders](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/sharing.md b/docs/versioned_docs/version-0.4.x/use-cases/sharing.md
deleted file mode 100644
index 4a97b41b..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/sharing.md
+++ /dev/null
@@ -1,40 +0,0 @@
-
-# Sharing & Collaboration
-
-Inviting a team member to a document, project or repository should be hassle free to model. In Permify you can achieve this with simply defining a invite action. Check out the below model block see how sharing can be modeled with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
- relation manager @user
-
-}
-
-entity project {
-
- // represents project's parent organization
- relation org @organization
-
- // represents owner of this project
- relation owner @user
-
- // invite permission
- action invite = org.admin or owner
-
-}
-
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/simple-rbac.md b/docs/versioned_docs/version-0.4.x/use-cases/simple-rbac.md
deleted file mode 100644
index f5cf485b..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/simple-rbac.md
+++ /dev/null
@@ -1,128 +0,0 @@
----
-sidebar_position: 1
----
-
-# Role Based Access Control
-
-Want to implement role and permissions to your application ? Permify fully covers you at that point. Below example shows how to model simple role based access control for organizational roles and permissions with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
- //organization files access permissions
- action view_files = admin or manager or (member not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 2 entities,
-
-- `user`, represents users (maybe corresponds as employees). This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, representing the organization the user (employees) belongs. It has several roles and permissions related to the specific resources such as organization files and vendor files.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles. In this example, we have 4 organizational wide roles, respectively; admin, manager, member, and agent.
-
-```perm
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
-}
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or*** and ***not*** operators to define actions.
-
-#### organization actions
-
-In our schema, we define several actions for controlling access permissions on organization files and organization vendor's files.
-
-```perm
-entity organization {
-
- //organization files access permissions
- action view_files = admin or manager or (member not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-let's take a look at some of the actions:
-
-- ``action edit_files = admin or manager``
-indicates that only the admin or manager has permission to edit files in the organization.
-
-- ``action view_files = admin or manager or (member not agent)``
-indicates that the admin, manager, or members (without having the agent role) can view organization files.
-
-
-
-## Example Relational Tuples for this case
-
-organization:2#admin@user:daniel
-
-organization:5#member@user:ashley
-
-organization:17#manager@user:mert
-
-organization:21#agent@user:ege
-
-.
-.
-.
-
-For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.4.x/use-cases/user-groups.md b/docs/versioned_docs/version-0.4.x/use-cases/user-groups.md
deleted file mode 100644
index aa48ce15..00000000
--- a/docs/versioned_docs/version-0.4.x/use-cases/user-groups.md
+++ /dev/null
@@ -1,201 +0,0 @@
-
-# User Groups & Team Permissions
-
-This use case shows how to organize permissions based on groupings of users or resources. In this use case we'll follow a simple project management app with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- // represents owner or creator of the team
- relation owner @user
-
- // represents direct member of the team
- relation member @user
-
- // reference for organization that team belong
- relation org @organization
-
- // organization admins or owners can edit, delete the team details
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- // to invite someone you need to be admin and either owner or member of this team
- action invite = org.admin and (owner or member)
-
- // only owners can remove users
- action remove_user = owner
-
-}
-
-entity project {
-
- // references for team and organization that project belongs
- relation team @team
- relation org @organization
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists 4 entity,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that contain teams.
-
-- `team`, represents teams, which belongs to a organization.
-
-- `project`, represents projects that belongs teams.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles.
-
-The organization entity has 2 relations ``admin`` and ``member`` users. Think of these as organizational-wide roles.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-#### team entity
-
-The eeam entity has its own relations respectively, ``owner``, ``member`` and ``org``
-
-```perm
-entity team {
-
- relation owner @user
- relation member @user
- relation org @organization
-
-}
-```
-
-#### project entity
-
-Project entity has ``team`` and ``org`` relations. Both these relations represents parent relationship with other entites, parent team and parent organization.
-
-```perm
-entity project {
-
- relation team @team
- relation org @organization
-
-}
-```
-
-### Actions
-
-Actions describe what relations, or relation’s relation can do, think of actions as entities' permissions. Actions defines who can perform a specific action in which circumstances.
-
-Permify Schema supports ***and***, ***or*** and ***not*** operators to define actions.
-
-#### team actions
-
-- Only organization ***admin (admin role)*** and ***team owner*** can perform editing and deleting team spesific resources.
-
-- Moreover, for inviting a colleague to a team you must have ***admin role*** and either be a ***owner*** or ***member*** on that team.
-
-- To remove users in team you must be a ***owner*** of that team.
-
-And these rules reflects Permify Schema as:
-
-```perm
-entity team {
-
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- action invite = org.admin and (owner or member)
- action remove_user = owner
-
-}
-```
-
-#### project actions
-
-And there are the project actions below. It consists of checking access for basic operations such as viewing, editing, or deleting project resources.
-
-```perm
-entity project {
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-## Example Relational Tuples
-
-team:2#member@user:daniel
-
-team:54#owner@user:daniel
-
-organization:12#admin@user:jack
-
-organization:51#member@user:jack
-
-organiation:41#member@team:42#member
-
-project:35#team@team:34#....
-
-
-.
-.
-.
-.
-.
-
-
-organization:41#member@team:42#member
-
-**--> represents members of team 42 also members in organization 41**
-
-project:35#team@team:34#....
-
-**--> represents project 54 is in team 34**
-
-For more details about how relational tuples created and stored your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.5.x/api-overview.md b/docs/versioned_docs/version-0.5.x/api-overview.md
deleted file mode 100644
index 08346b46..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview.md
+++ /dev/null
@@ -1,83 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Overview
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [DataService]: Authorization data operations such as creating, deleting and reading relational tuples.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ./permission
-[DataService]: ./data
-[SchemaService]: ./schema
-[TenancyService]: ./tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](./api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](./api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](./api-overview/data/read-relationships.md)
-- Check access with [Check API](./api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](./api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](./api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](./api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](./api-overview/watch/watch-changes.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our [documentation](https://docs.permify.co/docs/reference/configuration). We used [Token bucket](https://en.wikipedia.org/wiki/Token_bucket) algorithm for rate limiting.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/data/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/data/_category_.json
deleted file mode 100644
index d245a3c3..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/data/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Data Service",
- "position": 2,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/data/delete-data.md b/docs/versioned_docs/version-0.5.x/api-overview/data/delete-data.md
deleted file mode 100644
index fe8ba7d4..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/data/delete-data.md
+++ /dev/null
@@ -1,108 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Data
-
-You can delete any stored relation tuples or attributes with following API
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/data/delete
-
-[](https://permify.github.io/permify-swagger/#/Data/data.delete)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | tuples_filter | object |filter to delete relational tuples. Contains **entity**, **relation** and **subject**.
-| [x] | attribute_filter | object | filter to delete attributes. Contains **entity** and **attributes**.
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | relation of the given entity |
-| [x] | attribute | string array | attributes to be deleted |
-| [ ] | subject | object | the user or user set. It contains type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.Delete(context.Background(), & v1.DataDeleteRequest {
- TenantId: "t1",
- Metadata: &v1.DataDeleteRequestMetadata {
- SnapToken: ""
- },
- TupleFilter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.delete({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- tupleFilter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "tupleFilter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- },
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/data/read-attributes.md b/docs/versioned_docs/version-0.5.x/api-overview/data/read-attributes.md
deleted file mode 100644
index 248d34d9..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/data/read-attributes.md
+++ /dev/null
@@ -1,94 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Attributes
-
-Read API allows for directly querying the stored graph data to display and filter stored attributes.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/data/attributes/read
-
-[](https://permify.github.io/permify-swagger/#/Data/data.attributes.read)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | attributes | string array | attributes of the given entity |
-
-
-
-
-
-```go
-rr, err: = client.Data.ReadAttributes(context.Background(), & v1.Data.AttributeReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.AttributeReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.AttributeFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Attributes: []string {"private"},
-})
-```
-
-
-
-
-
-```javascript
-client.data.readAttributes.read({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/attributes/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/data/read-relationships.md b/docs/versioned_docs/version-0.5.x/api-overview/data/read-relationships.md
deleted file mode 100644
index 384f766f..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/data/read-relationships.md
+++ /dev/null
@@ -1,105 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id/data/relationships/read
-
-[](https://permify.github.io/permify-swagger/#/Data/data.relationships.read)
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.ReadRelationships(context.Background(), & v1.Data.RelationshipReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.readRelationships({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/relationships/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/data/write-data.md b/docs/versioned_docs/version-0.5.x/api-overview/data/write-data.md
deleted file mode 100644
index 73199ac7..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/data/write-data.md
+++ /dev/null
@@ -1,366 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Authorization Data
-
-In Permify, relations between your entities, objects and users stored as [relational tuples] in a [preferred database]. Since relations and authorization data's are live instances these relational tuples can be created with an simple API call in runtime.
-
-When using Permify, the application client should update preferred database about the changes happening in entities or resources that are related to the authorization structure. If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [preferred database] up-to-date. Besides, each relational tuple should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as relation tuples and store in [preferred database].
-
-
-
-[relational tuples]: ../../../getting-started/sync-data
-[preferred database]: ../../../getting-started/sync-data#where-relational-tuples-used
-
-## Write Request
-
-:::info
-You can use the **/v1/tenants/{tenant_id}/data/write** endpoint for both creating **relation tuples** and for creating **attribute data**.
-:::
-
-**Path:** POST /v1/tenants/{tenant_id}/data/write
-
-[](https://permify.github.io/permify-swagger/#/Data/data.write)
-
-#### Glossary for parameters & payload objects:
-
-| Required | Argument | Type | Default | Description |
-| -------- | -------------- | ------ | ------- | ----------------------------------------------------------------------------------------------------------------------------------------------------- |
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this parameter. |
-| [ ] | schema_version | string | 8 | Version of the schema. |
-| [x] | tuples | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **relation**, and **subject** arguments.|
-| [x] | attributes | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **attribute**, and **value** arguments. |
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1” |
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc. |
-| [x] | attribute | string | - | Custom attribute name. |
-| [x] | value | object | - | Represents value and type of the attribute data. |
-
-
-### Creating Relational Tuple
-
-Let's create an example relation tuple. If user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` should be created as follows:
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "admin",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data
- .write({
- tenantId: "t1",
- metadata: {
- schemaVersion: "",
- },
- tuples: [
- {
- entity: {
- type: "organization",
- id: "1",
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3",
- },
- },
- ],
- })
- .then((response) => {
- // handle response
- });
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-
-### Creating Attribute Data
-
-You can use `attributes` argument to create attribute/attributes, similarly the `tuples`.
-
-Let's conitnue with an example: Assume user:1 has been granted an admin role in organization:1 and organization:1 is a private (boolean) organization:
-
-:::warning **value** field
-**value** field is mandatory on attribute data creation.
-
-Here are the available attribute value types:
-
-- **type.googleapis.com/base.v1.StringValue**
-- **type.googleapis.com/base.v1.BooleanValue**
-- **type.googleapis.com/base.v1.IntegerValue**
-- **type.googleapis.com/base.v1.DoubleValue**
-- **type.googleapis.com/base.v1.StringArrayValue**
-- **type.googleapis.com/base.v1.BooleanArrayValue**
-- **type.googleapis.com/base.v1.IntegerArrayValue**
-- **type.googleapis.com/base.v1.DoubleArrayValue**
-:::
-
-
-
-
-```go
-// Convert the wrapped attribute value into Any proto message
-value, err := anypb.New(&v1.BooleanValue{
- Data: true,
-})
-if err != nil {
- // Handle error
-}
-
-cr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{
- TenantId: "t1",,
- Metadata: &v1.DataWriteRequestMetadata{
- SchemaVersion: "",
- },
- Tuples: []*v1.Attribute{
- {
- Entity: &v1.Entity{
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: &v1.Subject{
- Type: "user",
- Id: "1",
- Relation: "",
- },
- },
- },
- Attributes: []*v1.Attribute{
- {
- Entity: &v1.Entity{
- Type: "account",
- Id: "1",
- },
- Attribute: "public",
- Value: value,
- },
- },
-})
-```
-
-
-
-
-
-```javascript
-const booleanValue = BooleanValue.fromJSON({ data: true });
-
-const value = Any.fromJSON({
- typeUrl: 'type.googleapis.com/base.v1.BooleanValue',
- value: BooleanValue.encode(booleanValue).finish()
-});
-
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "1"
- }
- }],
- attributes: [{
- entity: {
- type: "document",
- id: "1"
- },
- attribute: "public",
- value: value,
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1"
- }
- }
- ],
- "attributes": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "attribute": "private",
- "value": {
- "@type": "type.googleapis.com/base.v1.BooleanValue",
- "data": true
- }
- }
- ]
-}
-}'
-```
-
-
-
-
-## Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../../reference/snap-tokens) and how its avoiding stale cache.
-
-## Suggested Workflow
-
-The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-
-### Two Phase Commit Approach
-
-In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
-
-To give more concurrent example of this action, let's take a look at below createDocument function
-
-```go
-func CreateDocuments(db *gorm.DB) error {
-
- tx := db.Begin()
- defer func() {
- if r := recover(); r != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteData(...)
- }
- }()
-
- if err := tx.Error; err != nil {
- return err
- }
-
- if err := tx.Create(docs).Error; err != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteData(...)
- return err
- }
-
- // if transaction successful, write relation tuple to Permify
- permify.WriteData(...)
-
- return tx.Commit().Error
-}
-```
-
-The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-
-### Data that not stored in application database
-
-Although ownership generally stored in application databases, there are some data that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
-
-For example, you can model a simple project management authorization in Permify as follows,
-
-```perm
-entity user {}
-
-entity team {
-
- relation owner @user
- relation member @user
-}
-
-entity project {
-
- relation team @team
- relation owner @user
-
- action view = team.member or team.owner or project.owner
- action edit = project.owner or team.owner
- action delete = project.owner or team.owner
-
-}
-```
-
-This **team member** relation won't need to be stored in the application database. Storing it only in Permify - preferred database - is enough. In that situation, `WriteData` can be performed in any logical place in your stack.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/permission/_category_.json
deleted file mode 100644
index f91d5b46..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Permission Service",
- "position": 3,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/check-api.md b/docs/versioned_docs/version-0.5.x/api-overview/permission/check-api.md
deleted file mode 100644
index e85b48af..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/check-api.md
+++ /dev/null
@@ -1,194 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Check Access Control
-
-In Permify, you can perform two different types access checks,
-
-- **resource based** authorization checks, in form of `Can user U perform action Y in resource Z ?`
-- **subject based** authorization checks, in form of `Which resources can user U edit ?`
-
-In this section we'll look at the resource based check request of Permify. You can find subject based access checks in [Entity (Data) Filtering] section.
-
-[Entity (Data) Filtering]: ../lookup-entity
-
-## Request
-
-**Path:** POST /v1/permissions/check
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.check)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. , see more details on [Contextual Tuples](../../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionCheckRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Permission: "edit",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "can": "RESULT_ALLOWED",
- "remaining_depth": 0
-}
-```
-
-Answering access checks is accomplished within Permify using a basic graph walking mechanism.
-
-## How Access Decisions Evaluated?
-
-Access decisions are evaluated by stored [relational tuples] and your authorization model, [Permify Schema].
-
-In high level, access of an subject related with the relationships or attributes created between the subject and the resource. You can define this data in Permify Schema then create and store them as relational tuples and attributes, which is basically forms your authorization data.
-
-Permify Engine to compute access decision in 2 steps,
-1. Looking up authorization model for finding the given action's ( **edit**, **push**, **delete** etc.) relations.
-2. Walk over a graph of each relation to find whether given subject ( user or user set ) is related with the action.
-
-Let's turn back to above authorization question ( ***"Can the user 3 edit document 12 ?"*** ) to better understand how decision evaluation works.
-
-[relational tuples]: ../../getting-started/sync-data.md
-[Permify Schema]: ../../getting-started/modeling.md
-
-When Permify Engine receives this question it directly looks up to authorization model to find document `edit` action. Let's say we have a model as follows
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity document {
-
- // represents documents parent organization
- relation parent @organization
-
- // represents owner of this document
- relation owner @user
-
- // permissions
- action edit = parent.admin or owner
- action delete = owner
-}
-```
-
-Which has a directed graph as follows:
-
-
-
-As we can see above: only users with an admin role in an organization, which `document:12` belongs, and owners of the `document:12` can edit. Permify runs two concurrent queries for **parent.admin** and **owner**:
-
-**Q1:** Get the owners of the `document:12`.
-
-**Q2:** Get admins of the organization where `document:12` belongs to.
-
-Since edit action consist **or** between owner and parent.admin, if Permify Engine found user:3 in results of one of these queries then it terminates the other ongoing queries and returns authorized true to the client.
-
-Rather than **or**, if we had an **and** relation then Permify Engine waits the results of these queries to returning a decision.
-
-## Latency & Performance
-
-With the right architecture we expect **7-12 ms** latency. Depending on your load, cache usage and architecture you can get up to **30ms**.
-
-Permify implements several cache mechanisms in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](../../reference/cache.md)
-
-## Need any help ?
-
-:::info
-Bulk permission check or with other name data filtering is a common use case we have seen so far. If you have a similar use case we would love to hear from you. Join our [discord](https://discord.gg/n6KfzYxhPp) to discuss or [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/expand-api.md b/docs/versioned_docs/version-0.5.x/api-overview/permission/expand-api.md
deleted file mode 100644
index ea91bb1f..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/expand-api.md
+++ /dev/null
@@ -1,316 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-
-Retrieve all subjects (users and user sets) that have a relationship or attribute with given entity and permission
-
-Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
-
-:::caution When To Use ?
-Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
-
-It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
-:::
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.expand)
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), &v1.PermissionExpandRequest{
- TenantId: "t1",
- Metadata: &v1.PermissionExpandRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "",
- "snap_token": ""
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "push"
-}'
-```
-
-
-
-## Example Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:** POST /v1/tenants/{tenant_id}/permissions/expand
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”. |
-| [x] | permission | string | - | The permission the user wants to perform on the resource |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-### Expand Push Action
-
-Request
-
-
-
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-entity.md b/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-entity.md
deleted file mode 100644
index a14679db..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-entity.md
+++ /dev/null
@@ -1,222 +0,0 @@
----
-title: Entity (Data) Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Entity Filtering
-
-Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So, we provide 2 separate endpoints for data filtering check request,
-
-- [Entity Filtering](#entity-filtering)
- - [Lookup Entity](#lookup-entity)
- - [How Lookup Operations Evaluated](#how-lookup-operations-evaluated)
- - [Lookup Entity (Streaming)](#lookup-entity-streaming)
-
-## Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
-
-**POST** /v1/permissions/lookup-entity
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntity)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- EntityType: "document",
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupEntity({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity_type: "document",
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response.entity_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type":"user",
- "id":"1"
- }
-}'
-```
-
-
-
-## How Lookup Operations Evaluated
-
-We explicitly designed reverse lookup to be more performant with changing its evaluation pattern. We do not query all the documents in bulk to get response, instead of this Permify first finds the necessary relations with given subject and the permission/action in the API call. Then query these relations with the subject id this way we reduce lots of additional queries.
-
-To give an example,
-
-```jsx
-entity user {}
-
-entity organization {
- relation admin @user
-}
-
-entity container {
- relation parent @organization
- relation container_admin @user
- action admin = parent.admin or container_admin
-}
-
-entity document {
- relation container @container
- relation viewer @user
- relation owner @user
- action view = viewer or owner or container.admin
-}
-```
-
-Lets say we called (reverse) lookup API to find the documents that user:1 can view. Permify first finds the relations that linked with view action, these are
-
-- `document#viewer`
-- `document#owner`
-- `organization#admin`
-- `container#``container_admin`
-
-Then queries each of them with `user:1.`
-
-### Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-**POST** /v1/permissions/lookup-entity-stream
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntityStream)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../../reference/contextual-tuples) |
-
-
-
-
-```go
-str, err: = client.Permission.LookupEntityStream(context.Background(), &v1.PermissionLookupEntityRequest {
- Metadata: &v1.PermissionLookupEntityRequestMetadata {
- SnapToken: "",
- SchemaVersion: ""
- Depth: 50,
- },
- EntityType: "document",
- Permission: "view",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-
-// handle stream response
-for {
- res, err: = str.Recv()
-
- if err == io.EOF {
- break
- }
-
- // res.EntityId
-}
-```
-
-
-
-
-```javascript
-const permify = require("@permify/permify-node");
-const {PermissionLookupEntityStreamResponse} = require("@permify/permify-node/dist/src/grpc/generated/base/v1/service");
-
-function main() {
- const client = new permify.grpc.newClient({
- endpoint: "localhost:3478",
- })
-
- let res = client.permission.lookupEntityStream({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entityType: "document",
- permission: "view",
- subject: {
- type: "user",
- id: "1"
- }
- })
-
- handle(res)
-}
-
-async function handle(res: AsyncIterable) {
- for await (const response of res) {
- // response.entityId
- }
-}
-```
-
-
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-subject.md b/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-subject.md
deleted file mode 100644
index baaacd6b..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/lookup-subject.md
+++ /dev/null
@@ -1,109 +0,0 @@
----
-title: Subject Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Filtering
-
-Lookup Subject endpoint lets you ask questions in form of **“Which subjects can do action Y on entity:X?”**. As a response of this you’ll get a subject results in a format of string array.
-
-So, we provide 1 endpoint for subject filtering request,
-
-- [/v1/permissions/lookup-subject](#lookup-subject)
-
-## Lookup Subject
-
-In this endpoint you'll get directly the IDs' of the subjects that are authorized in an array.
-
-**POST** /v1/permissions/lookup-subject
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupSubject)
-
-| Required | Argument | Type | Default | Description |
-|----------|---------------------|----------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1 |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject_reference | object | - | the subject or subject reference who wants to take the action. It contains type and relation of the subject. |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. See more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSubject(context.Background(), &v1.PermissionLookupSubjectRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionLookupSubjectRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Permission: "edit",
- SubjectReference: &v1.RelationReference{
- Type: "user",
- Relation: "",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupSubject({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- Entity: {
- Type: "document",
- Id: "1",
- },
- permission: "edit",
- subject_reference: {
- type: "user",
- relation: ""
- }
-}).then((response) => {
- console.log(response.subject_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": ""
- },
- "entity": {
- type: "document",
- id: "1'
- },
- "permission": "edit",
- "subject_reference": {
- "type": "user",
- "relation": ""
- }
-}'
-```
-
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/permission/subject-permission.md b/docs/versioned_docs/version-0.5.x/api-overview/permission/subject-permission.md
deleted file mode 100644
index 9048b33c..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/permission/subject-permission.md
+++ /dev/null
@@ -1,130 +0,0 @@
----
-title: Subject Permission List
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Permission List
-
-The Subject Permission List endpoint allows you to inquire in the form of **“Which permissions user:x can perform on entity:y?”**. In response, you'll receive a list of permissions specific to the user for the given entity, returned in the format of a map.
-
-So, we provide 1 endpoint for subject permission list,
-
-- [/v1/permissions/subject-permission](#subject-permission)
-
-In this endpoint, you'll receive a map of permissions and their statuses directly. The structure is map[string]CheckResult, such as "sample-permission" -> "ALLOWED". This represents the permissions and their associated states in a key-value pair format.
-
-## Request
-
-**Path:** POST /v1/permissions/subject-permission
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.subjectPermission)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | only_permission | bool | false | By default, the endpoint returns both permissions and relations associated with the user and entity. However, when the "only_permission" parameter is set to true, it returns only the permissions. | |
-| [ ] | context | object | - | Contextual tuples are relations that can be dynamically added to permission request operations. , see more details on [Contextual Tuples](../../reference/contextual-tuples) |
-
-
-
-
-```go
-cr, err: = client.Permission.SubjectPermission(context.Background(), &v1.PermissionSubjectPermissionRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionSubjectPermissionRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- OnlyPermission: false,
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-```
-
-
-
-
-```javascript
-client.permission.subjectPermission({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- onlyPermission: true,
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response);
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "only_permission": true,
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "results": [
- {
- "key": "delete",
- "value": "RESULT_ALLOWED"
- },
- {
- "key": "edit",
- "value": "RESULT_ALLOWED"
- }
- ]
-}
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/schema/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/schema/_category_.json
deleted file mode 100644
index 8fd1e959..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/schema/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Schema Service",
- "position": 1,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/schema/write-schema.md b/docs/versioned_docs/version-0.5.x/api-overview/schema/write-schema.md
deleted file mode 100644
index bb4f9459..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/schema/write-schema.md
+++ /dev/null
@@ -1,95 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
-
-Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
-
-We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-:::
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-## Request
-
-**POST** /v1/tenants/{tenant_id}/schemas/write
-
-[](https://permify.github.io/permify-swagger/#/Schema/schemas.write)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- TenantId: "t1",
- Schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- tenantId: "t1",
- schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "schema": "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/write"**
-
-**Example Request on Postman:**
-
-
-
-
-## Suggested Workflow For Schema Changes
-
-It's expected that your initial schema will eventually change as your product or system evolves
-
-As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
-
-A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database unless you delete them with the [delete API](../data/delete-data.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
-
-We recommend applying the following pattern to safely handle schema changes:
-
-- Set up a central git repository that includes the schema.
-- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
-- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
-
-## Need any help ?
-
-Depending on the frequency and the type of the changes that you made on the schemas, this method may not be optimal for you - In such cases, we are open to exploring alternative solutions. Please feel free to [schedule a call with one of our engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/tenancy/_category_.json
deleted file mode 100644
index 9771416d..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Tenancy Service",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/create-tenant.md b/docs/versioned_docs/version-0.5.x/api-overview/tenancy/create-tenant.md
deleted file mode 100644
index 69a7a6ff..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/create-tenant.md
+++ /dev/null
@@ -1,57 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Create Tenant
-
-Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
-
-:::caution
-We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
-:::
-
-## Request
-
-**POST /v1/tenants/create**
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.create)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Create(context.Background(), & v1.TenantCreateRequest {
- Id: ""
- Name: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.create({
- id: "",
- name: ""
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'http://localhost:3476/v1/tenants/create' \
---header 'Content-Type: application/json' \
---data-raw '{
- "id": "",
- "name": ""
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/delete-tenant.md b/docs/versioned_docs/version-0.5.x/api-overview/tenancy/delete-tenant.md
deleted file mode 100644
index a74a11e8..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/tenancy/delete-tenant.md
+++ /dev/null
@@ -1,46 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Tenant
-
-You can delete a tenant with following API.
-
-## Request
-
-**DELETE /v1/tenants/{id}**
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.delete)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Delete(context.Background(), & v1.TenantDeleteRequest {
- Id: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.delete({
- id: "",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/watch/_category_.json b/docs/versioned_docs/version-0.5.x/api-overview/watch/_category_.json
deleted file mode 100644
index f65c41fd..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/watch/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Watch Service",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/api-overview/watch/watch-changes.md b/docs/versioned_docs/version-0.5.x/api-overview/watch/watch-changes.md
deleted file mode 100644
index ff48c097..00000000
--- a/docs/versioned_docs/version-0.5.x/api-overview/watch/watch-changes.md
+++ /dev/null
@@ -1,142 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Watch
-
-The Permify Watch API acts as a real-time broadcaster that shows changes in the relation tuples.
-
-The Watch API exclusively supports gRPC and works with PostgreSQL, given the track_commit_timestamp option is enabled. Please note, it doesn't support in-memory databases or HTTP communication.
-
-# Requirements
-
-- PostgreSQL database set up with track_commit_timestamp option enabled
-
-## Enabling track_commit_timestamp on PostgreSQL
-
-To ensure data consistency and synchronization between your application and Permify, enable track_commit_timestamp on
-your PostgreSQL server. This can be done by executing the following options in your PostgreSQL:
-
-### Option 1: SQL Command
-
-1. Open your PostgreSQL command line interface.
-2. Execute the following command:
-
- ```sql
- ALTER SYSTEM SET track_commit_timestamp = ON;
- ```
-
-3. Reload the configuration with the following command:
-
- ```sql
- SELECT pg_reload_conf();
- ```
-
-### Option 2: Editing postgresql.conf
-
-1. Find and open the postgresql.conf file in a text editor. Its location depends on your PostgreSQL installation. Common
- locations are:
- - Debian-based systems: /etc/postgresql/[version]/main/postgresql.conf
- - Red Hat-based systems: /var/lib/pgsql/data/postgresql.conf
-
-2. Add or modify the following line in the postgresql.conf file:
- ```
- track_commit_timestamp = on
- ```
-
-3. Save and close the postgresql.conf file.
-4. Reload the PostgreSQL configuration for the changes to take effect. This can be done via the PostgreSQL console:
- ```sql
- SELECT pg_reload_conf();
- ```
-
- Or if you have command line access, use:
-
- ```bash
- sudo service postgresql reload
- ```
-
-Please ensure you have the necessary permissions to execute these commands or modify the postgresql.conf file. Also, remember that changes in the postgresql.conf file will persist across restarts, while the SQL method may need to be reapplied depending on your PostgreSQL version and setup.
-
-:::info
-Important Configuration Requirement: To use the Watch API, it must be enabled in your configuration file. Add or modify the following lines:
-
-```yaml
-service:
- watch:
- enabled: true
-```
-
-:::
-
-## Request
-
-**Path:** POST /v1/watch/watch
-
-[](https://permify.github.io/permify-swagger/#/Watch/watch.watch)
-
-| Required | Argument | Type | Default | Description |
-|----------|------------|--------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | snap_token | string | - | specifies the starting point for broadcasting changes. If a snap_token is provided, all changes following that specific snapshot will be broadcasted. If a snap_token is not provided, the Watch API will broadcast all changes that occur after the Watch API is initiated., see more details on [Snap Tokens](../../reference/snap-tokens). |
-
-
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```go)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```javascript)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-## Response
-
-```json
-{
- "changes": {
- "tuple_changes": [
- {
- "operation": "OPERATION_CREATE",
- "tuple": {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "56",
- "relation": ""
- }
- }
- }
- ],
- "snap_token": "MgMAAAAAAAA="
- }
-}
-```
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or
-have any questions about this
-example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.5.x/comparision.md b/docs/versioned_docs/version-0.5.x/comparision.md
deleted file mode 100644
index 75fb39c4..00000000
--- a/docs/versioned_docs/version-0.5.x/comparision.md
+++ /dev/null
@@ -1,38 +0,0 @@
----
-id: comparison
-title: Comparison Between Other Zanzibar implementations
----
-
-:::caution Note
-This comparison table shows the differentiation between authorization solutions based or inspired by Google Zanzibar paper. If you use any of these solutions and feel the information could be improved, feel free to reach out.
-:::
-
-## General Aspects
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|---------------------------------|------------|------------|-----------|-----------|
-| **Zanzibar Paper Faithfulness** | Medium | High | High | High |
-| **Scalability** | Medium | Medium | High | High |
-| **Consistency & Cache** | No Zookies | No Zookies | Supported | Supported |
-| **Dev UX** | Average | Average | High | High |
-
-## Feature Set
-
-- ✅ Supported, and ready to use with no added configuration or code
-- 🟡 Limited support and requires extra user-code to implement.
-- ⛔ Not officially supported or documented.
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|--------------------------|----------|---------|---------|---------|
-| **Check API** | ✅ | ✅ | ✅ | ✅ |
-| **Write API** | ✅ | ✅ | ✅ | ✅ |
-| **Read API** | ✅ | ✅ | ✅ | ✅ |
-| **Expand API** | ✅ | ✅ | ✅ | ✅ |
-| **Watch API** | ✅ | ✅ | ✅ | ✅ |
-| **RBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ReBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ABAC** | ⛔ | 🟡 | ✅ | ✅ |
-| **Data Filtering** | ⛔ | ✅ | ✅ | ✅ |
-| **Multi Tenancy** | ⛔ | ✅ | ⛔ | ✅ |
-| **Testing & Validation** | ⛔ | 🟡 | ✅ | ✅ |
-| **Logging & Tracing** | 🟡 | ✅ | ✅ | ✅ |
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/_category_.json b/docs/versioned_docs/version-0.5.x/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/enforcement.md b/docs/versioned_docs/version-0.5.x/getting-started/enforcement.md
deleted file mode 100644
index df4c80f5..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/enforcement.md
+++ /dev/null
@@ -1,80 +0,0 @@
----
-sidebar_position: 4
----
-
-# Interacting With The API
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [DataService]: Authorization data operations such as creating, deleting and reading relational tuples.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permify/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ../../api-overview/permission
-[DataService]: ../../api-overview/data
-[SchemaService]: ../../api-overview/schema
-[TenancyService]: ../../api-overview/tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](../api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](../api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](../api-overview/data/read-relationships.md)
-- Check access with [Check API](../api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](../api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](../api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](../api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](../api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](../api-overview/watch/watch-changes.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our [documentation](https://docs.permify.co/docs/reference/configuration). We used [Token bucket](https://en.wikipedia.org/wiki/Token_bucket) algorithm for rate limiting.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/_category_.json b/docs/versioned_docs/version-0.5.x/getting-started/examples/_category_.json
deleted file mode 100644
index b3e4f801..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Example Permission Structures",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/facebook-groups.md b/docs/versioned_docs/version-0.5.x/getting-started/examples/facebook-groups.md
deleted file mode 100644
index 1b918630..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/facebook-groups.md
+++ /dev/null
@@ -1,546 +0,0 @@
-# Facebook Groups
-
-This example demonstrate the authorization structure for Facebook groups, which enables users to perform various actions based on their roles and permissions within the group.
-
-### Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
-
-```perm
-// Represents a user
-entity user {}
-
-// Represents a Facebook group
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
-}
-
-// Represents a post in a Facebook group
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
-}
-
-// Represents a comment like on a post in a Facebook group
-entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
-}
-
-// Definition of poll entity
-entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
-}
-
-// Definition of file entity
-entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
-}
-
-// Definition of event entity
-entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities and relations, as well as actions and permissions that can be taken by users within the group. Let's examine them shortly;
-
-### Entities & Relations
-
-* **`user`** entity represents a user in the Facebook.
-
-* **`group`** entity represents the Facebook group, and it has several relations including member, admin, and moderator to represent the members, admins, and moderators of the group. Additionally, there are relations to represent the posts and comments in the group.
-
-* **`post`** entity represents a post in the Facebook group, and it has relations to represent the owner of the post and the group that the post belongs to.
-
-* **`comment`** entity represents a comment on a post in the Facebook group, and it has relations to represent the owner of the comment, the post that the comment belongs to, and the comment itself.
-
-* **`like`** entity represents a like on a post in the Facebook group, and it has relations to represent the owner of the like and the post that the like belongs to.
-
-* **`poll`** entity represents a poll in the Facebook group, and it has relations to represent the owner of the poll and the group that the poll belongs to.
-
-* **`file`** entity represents a file in the Facebook group, and it has relations to represent the owner of the file and the group that the file belongs to.
-
-* **`event`** entity represents an event in the Facebook group, and it has relations to represent the owner of the event and the group that the event belongs to.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions.
-
-For example, the `create_group` action can only be performed by a `member`, as follows:
-
-#### Creating a group permission
-
-```perm
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
-
- ..
-
- // Create group permission
- action create_group = member
-
- ..
- ..
-}
-```
-
-Another example would be given from the `edit_post` action in the post entity, which specifies the permissions required to edit a post in a Facebook group.
-
-#### Editing a post permission
-
-```perm
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- ..
-
- action edit_post = owner or group.admin
-
- ..
- ..
-}
-```
-
-An **owner** of a post can always edit their own post. In addition, members who are defined as **admin** of the group - which the post belongs to - can also edit the post.
-
-Since most entities are deeply nested together, we also have multiple hierarchical permissions.
-
-#### Nested Hierarchies
-
-For example, we can define a permission "view_comment" if only user is owner of that comment or user is a member of the group which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-//group relationships
-group:1#member@user:1
-group:1#admin@user:2
-group:2#moderator@user:3
-group:2#member@user:4
-group:1#member@user:5
-
-//post relationships
-post:1#owner@user:1
-post:1#group@group:1
-post:2#owner@user:4
-post:2#group@group:1
-
-//comment relationships
-comment:1#owner@user:2
-comment:1#post@post:1
-comment:2#owner@user:5
-comment:2#post@post:2
-
-//like relationships
-like:1#owner@user:3
-like:1#post@post:1
-like:2#owner@user:4
-like:2#post@post:2
-
-//poll relationships
-poll:1#owner@user:2
-poll:1#group@group:1
-poll:2#owner@user:5
-poll:2#group@group:1
-
-//like relationships
-file:1#owner@user:1
-file:1#group@group:1
-
-//event relationships
-event:1#owner@user:3
-event:1#group@group:1
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:4 RSVP_to_event event:1 ?
-
-
-```perm
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
-
- ..
- ..
-
- action RSVP_to_event = owner or group.member
- }
-```
-
-According to what we have defined for the **'RSVP_to_event'** action, users who are either the owner of `event:1` or a member of the group that belongs to `event:1` can grant access to RSVP to the event.
-
-According to the relation tuples we created, `user:4` is not the **owner** of the event. Furthermore, when we check whether `user:4` is a **member** of the only group (`group:1`) that `event:1` is part of (`event:1#group@group:1`), we see that there is no **member** relation for `user:4` in that group.
-
-Therefore, the `user:4 RSVP_to_event event:1` check request should yield a **'false'** response.
-
-
-
-
-can user:5 view_comment comment:1 ?
-
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-According to the relation tuples we created, `user:5` is not the **owner** of the comment. But member of the `group:1` and thats grant `user:5` (`group:1#member@user:5`) access to perform view the comment:1. In particularly, `comment:1` is part of the `post:1` (`comment:1#post@post:1`) and `post:1` is part of the group:1 (`post:1#group@group:1`). And from the action definition on above model group:1 members can view the `comment:1`.
-
-Therefore, the `user:5 view_comment comment:1` check request should yield a **'true'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
- }
-
- entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
- }
-
- entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
- }
-
- entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
- }
-
- entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
- }
-
- entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
- }
-
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
- }
-
-relationships:
- - group:1#member@user:1
- - group:1#admin@user:2
- - group:2#moderator@user:3
- - group:2#member@user:4
- - group:1#member@user:5
- - post:1#owner@user:1
- - post:1#group@group:1
- - post:2#owner@user:4
- - post:2#group@group:1
- - comment:1#owner@user:2
- - comment:1#post@post:1
- - comment:2#owner@user:5
- - comment:2#post@post:2
- - like:1#owner@user:3
- - like:1#post@post:1
- - like:2#owner@user:4
- - like:2#post@post:2
- - poll:1#owner@user:2
- - poll:1#group@group:1
- - poll:2#owner@user:5
- - poll:2#group@group:1
- - file:1#owner@user:1
- - file:1#group@group:1
- - event:1#owner@user:3
- - event:1#group@group:1
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "event:1"
- subject: "user:4"
- assertions:
- RSVP_to_event : false
- - entity: "comment:1"
- subject: "user:5"
- assertions:
- view_comment : true
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/google-docs.md b/docs/versioned_docs/version-0.5.x/getting-started/examples/google-docs.md
deleted file mode 100644
index 3f14e1f7..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/google-docs.md
+++ /dev/null
@@ -1,344 +0,0 @@
-# Google Docs Simplified
-
-This example models a simplified version of Google Docs style permission system where users can be granted direct access to a document, or access via organizations and nested groups.
-
-### Schema | [Open in playground](https://play.permify.co/?s=iuRic3nR1HeZJcFyRNKPo)
-
-```perm
-entity user {}
-
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-## Breakdown of the Model
-
-### User
-
-```perm
-entity user {}
-```
-
-Represents a user who can be granted permission to access a documents directly, or through their membership in a group or organization.
-
-### Document
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-Represents a document that users can be granted permission to access. The document entity has two relationships:
-
-#### Relations
-
-**org:** Represents organization that document belongs to.
-
-**manager:** A relationship between users who are authorized to manage the document. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group member and manager relations.
-
-**viewer:** A relationship between users who are authorized to view the document. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager relations.
-
-The document entity has two actions defined:
-
-#### Actions
-
-**manage:**: An action that can be performed by users who are authorized to manage the document, as determined by the manager relationship.
-
-**view:** An action that can be performed by users who are authorized to view the document, as determined by the viewer and manager relationships.
-
-### Group
-
-```perm
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-```
-
-Represents a group of users who can be granted permission to access a document. The group entity has two relationships:
-
-#### Relations
-
-**manager:** A relationship between users who are authorized to manage the group. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are members of the group. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager.
-
-The group entity has one action defined:
-
-### Organization
-
-```perm
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-```
-
-Represents an organization that can contain groups, users, and documents. The organization entity has several relationships:
-
-#### Relations
-
-**group:** A relationship between the organization and its groups. This relationship is defined by the `@group` annotation on the end corresponding to the group entity.
-
-**document:** A relationship between the organization and its document. This relationship is defined by the `@document` annotation on the end corresponding to the group entity.
-
-**administrator:** A relationship between users who are authorized to manage the organization. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are directly members of the organization. This relationship is defined by the `@user` annotation on the end corresponding to the user entity.
-
-The organization entity has two permissions defined:
-
-#### Permissions
-
-**admin:** An permission that can be performed by users who are authorized to manage the organization, as determined by the administrator relationship.
-
-**member:** An permission that can be performed by users who are directly members of the organization, or who have administrator relationship, or who are members of groups that are part of the organization,
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different groups
-group:tech#manager@user:ashley
-group:tech#direct_member@user:david
-group:marketing#manager@user:john
-group:marketing#direct_member@user:jenny
-group:hr#manager@user:josh
-group:hr#direct_member@user:joe
-
-// Assign groups to other groups
-group:tech#direct_member@group:marketing#direct_member
-group:tech#direct_member@group:hr#direct_member
-
-// Connect groups to organization
-organization:acme#group@group:tech
-organization:acme#group@group:marketing
-organization:acme#group@group:hr
-
-// Add some documents under the organization
-organization:acme#document@document:product_database
-organization:acme#document@document:marketing_materials
-organization:acme#document@document:hr_documents
-
-// Assign a user and members of a group as administrators for the organization
-organization:acme#administrator@group:tech#manager
-organization:acme#administrator@user:jenny
-
-// Set the permissions on some documents
-document:product_database#manager@group:tech#manager
-document:product_database#viewer@group:tech#direct_member
-document:marketing_materials#viewer@group:marketing#direct_member
-document:hr_documents#manager@group:hr#manager
-document:hr_documents#viewer@group:hr#direct_member
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:ashley edit document:product_database ?
-
-
-```perm
- entity document {
- relation org @organization
-
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-```
-
-According what we have defined for the edit action managers and admins, of the organization that document belongs, can edit product database. In this context, Permify engine will check does subject `user:ashley` has any direct or indirect manager relation within `document:product_database`. Consecutively it will check does `user:ashley` has admin relation in the Acme Org - `organization:acme#document@document:product_database`.
-
-Ashley doesn't have any administrative relation in Acme Org but she is the manager in group tech (`group:tech#manager@user:ashley`) and we have defined that manager of group tech is manager of product_database with the tuple (`document:product_database#manager@group:tech#manager`). Therefore, the **user:ashley edit document:product_database** check request should yield **true** response.
-
-
-
-
-can user:joe view document:hr_documents ?
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check whether subject `user:joe` has any direct or indirect manager or viewer relation within `document:hr_documents`. Also consecutively it will check does `user:joe` has admin relation in the Acme Org - `organization:acme#document@document:hr_documents`.
-
-Joe doesn't have administrative role/relation in Acme Org.
-
-Also he doesn't have have manager relationship in that document or within any entity.
-
-But he is member in the hr group (`group:hr#member@user:joe`) and we defined hr members have viewer relationship in hr documents (`document:hr_documents#viewer@group:hr#member`). So that, this enforcement should yield **true** response.
-
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check does subject `user:david` has any direct or indirect manager or viewer relation within `document:marketing_materials`. Also consecutively it will check does `user:david` has admin relation in the Acme Org - `organization:acme#document@document:marketing_materials`.
-
-Similar Joe and Ashley, David also doesn't have administrative role/relation in Acme Org.
-
-Also David doesn't have member or manager relationship related with marketing group - `document:marketing_materials`. So that, this enforcement should yield **false** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
- }
-
- entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
- }
-
- entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-
-relationships:
- - group:tech#manager@user:ashley
- - group:tech#direct_member@user:david
- - group:marketing#manager@user:john
- - group:marketing#direct_member@user:jenny
- - group:hr#manager@user:josh
- - group:hr#direct_member@user:joe
-
- - group:tech#direct_member@group:marketing#direct_member
- - group:tech#direct_member@group:hr#direct_member
-
- - organization:acme#group@group:tech
- - organization:acme#group@group:marketing
- - organization:acme#group@group:hr
- - organization:acme#document@document:product_database
- - organization:acme#document@document:marketing_materials
- - organization:acme#document@document:hr_documents
- - organization:acme#administrator@group:tech#manager
- - organization:acme#administrator@user:jenny
-
- - document:product_database#manager@group:tech#manager
- - document:product_database#viewer@group:tech#direct_member
- - document:marketing_materials#viewer@group:marketing#direct_member
- - document:hr_documents#manager@group:hr#manager
- - document:hr_documents#viewer@group:hr#direct_member
-
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "document:product_database"
- subject: "user:ashley"
- assertions:
- edit: true
- - entity: "document:hr_documents"
- subject: "user:joe"
- assertions:
- view: true
- - entity: "document:marketing_materials"
- subject: "user:david"
- assertions:
- view: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of modeling Google Docs style permission system. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/mercury.md b/docs/versioned_docs/version-0.5.x/getting-started/examples/mercury.md
deleted file mode 100644
index c755aafc..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/mercury.md
+++ /dev/null
@@ -1,74 +0,0 @@
-# Mercury
-
-Explore **Mercury's Authorization Schema** in this example, delving into the intricate interplay among **users**, **organizations**, and **accounts**. Uncover the defined user roles, approval workflows, and limits, providing a snapshot of the dynamic relationships within the Mercury ecosystem.
-
-## Schema | [Open in playground](https://play.permify.co/?s=mercury&tab=schema)
-
-```perm
-entity user {}
-
-entity organization {
- relation admin @user
- relation member @user
-
- attribute admin_approval_limit integer
- attribute member_approval_limit integer
- attribute approval_num integer
-
- action approve = admin
- action create_account = admin
-
- permission approval = (member and check_member_approval(approval_num, member_approval_limit)) or (admin and check_admin_approval(approval_num, admin_approval_limit))
-}
-
-entity account {
- relation checkings @account
- relation savings @account
-
- relation owner @organization
-
- attribute withdraw_limit double
- attribute balance double
-
- action withdraw = check_balance(balance, request.amount) and (check_limit(withdraw_limit, request.amount) or owner.approval)
-}
-
-rule check_balance(balance double, amount double) {
- balance >= amount
-}
-
-rule check_limit(withdraw_limit double, amount double) {
- withdraw_limit >= amount
-}
-
-rule check_admin_approval(approval_num integer, admin_approval_limit integer) {
- approval_num >= admin_approval_limit
-}
-
-rule check_member_approval(approval_num integer, member_approval_limit integer) {
- approval_num >= member_approval_limit
-}
-```
-
-## Brief Examination of the Model
-
-Mercury's authorization model consists of three primary entities: **user**, **organization**, and **account**.
-These entities are interconnected through defined relations and governed by specific rules and actions.
-
-### Entities & Relations
-
-**user**: Represents individual users within the system.
-
-**organization**: Represents organizational entities and establishes relations with users (`admin` and `member`). Additionally, this entity holds attributes like `admin_approval_limit`, `member_approval_limit`, and `approval_num`.
-
-**account**: Represents user accounts with relations to different account types (`checkings` and `savings`). It also has a relation to the owning `organization` and attributes such as `withdraw_limit` and `balance`.
-
-### Permissions
-
-The authorization schema defines two crucial permissions:
-
-**approval**: Determines the conditions under which a user (either `member` or `admin`) can approve actions based on approval limits.
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/examples/notion.md b/docs/versioned_docs/version-0.5.x/getting-started/examples/notion.md
deleted file mode 100644
index 9095d464..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/examples/notion.md
+++ /dev/null
@@ -1,548 +0,0 @@
-# Notion
-
-This is a schema definition of the authorization model for Notion, a popular productivity and organization tool.
-
-### Schema | [Open in playground](https://play.permify.co/?s=BsCvLmd4g81sB20XJZI5p)
-
-```perm
-entity user {}
-
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
-}
-
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
-}
-
-entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
-}
-
-entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
-}
-
-entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
-}
-
-entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
-}
-
-entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities, including users, workspaces, pages, databases, blocks, and integrations. It also includes several default roles, such as Admin, Bot, Guest, and Member. Here's a breakdown of the entities:
-
-### Entities & Relations
-
-- **`user`**: Represents a user in the system.
-
-- **`workspace`**: Represents a workspace in which users can collaborate. Each workspace has an owner, members, guests, and bots associated with it. The owner and admin users have permission to manage the workspace. Permissions are defined for creating pages, inviting members, viewing the workspace, and managing the workspace. The read and write permissions can be inherited by child entities.
-
-- **`page`**: Represents a page within a workspace. Each page is associated with a workspace and has a writer and readers. The read and write permissions are defined based on the writer and readers of the page and can be inherited from the workspace.
-
-- **`database`**: Represents a database within a workspace. Each database is associated with a workspace and has an editor and viewers. The read and write permissions are defined based on the editor and viewers of the database and can be inherited from the workspace. Permissions are also defined for creating and deleting databases.
-
-- **`block`**: Represents a block within a page or database. Each block is associated with a page or database and has an editor and commenters. The read and write permissions are defined based on the editor and commenters of the block and can be inherited from the database. Commenters are users who have permission to comment on the block.
-
-- **`comment`**: Represents a comment on a block. Each comment is associated with a block and has an author. The read and write permissions are defined based on the author of the comment and can be inherited from the block.
-
-- **`template`**: Represents a template within a workspace. Each template is associated with a workspace and has a creator and viewers. The read and write permissions are defined based on the creator and viewers of the template and can be inherited from the workspace. Permissions are also defined for creating and deleting templates.
-
-- **`integration`**: Represents an integration within a workspace. Each integration is associated with a workspace and has an owner. Permissions are defined for reading and writing to the integration.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions. Let's examine the **read** permission of the page entity.
-
-#### Page Read Permission
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- ..
-}
-
-entity page {
-
- // The workspace associated with the page
- relation workspace @workspace
-
- ..
- ..
-
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- ..
- ..
-
- // Define permissions for page actions
- permission read = reader or workspace.read
-
- ..
- ..
-}
-```
-
-This permission specifies who can read the contents of the page at Notion.
-
-The `reader` relation specifies the users who are members of the workspace associated with the page (`workspace#member`) or guests of the workspace (`workspace#guest`).
-
-Read permission of the workspace inherited as `workspace.read` in the page entity. THis permission specifies that any user who has been granted read access to the workspace object (i.e., the workspace that the page belongs to) can also read the page.
-
-In summary, any user who is a member or guest of the workspace and has been granted read access to the page through the reader relation, as well as any user who has been granted read access to the workspace itself, can read the contents of the page.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different workspaces:
-workspace:engineering_team#owner@user:alice
-workspace:engineering_team#member@user:bob
-workspace:engineering_team#guest@user:charlie
-workspace:engineering_team#admin@user:alice
-workspace:sales_team#owner@user:david
-workspace:sales_team#member@user:eve
-workspace:sales_team#guest@user:frank
-workspace:sales_team#admin@user:david
-
-// Connect pages, databases, and templates to workspaces:
-page:project_plan#workspace@workspace:engineering_team
-page:product_spec#workspace@workspace:engineering_team
-database:task_list#workspace@workspace:engineering_team
-template:weekly_report#workspace@workspace:sales_team
-database:customer_list#workspace@workspace:sales_team
-template:marketing_campaign#workspace@workspace:sales_team
-
-// Set permissions for pages, databases, and templates:
-page:project_plan#writer@user:frank
-page:project_plan#reader@user:bob
-
-database:task_list#editor@user:alice
-database:task_list#viewer@user:bob
-
-template:weekly_report#creator@user:alice
-template:weekly_report#viewer@user:bob
-
-page:product_spec#writer@user:david
-page:product_spec#reader@user:eve
-
-database:customer_list#editor@user:david
-database:customer_list#viewer@user:eve
-
-template:marketing_campaign#creator@user:david
-template:marketing_campaign#viewer@user:eve
-
-// Set relationships for blocks and comments:
-block:task_list_1#database@database:task_list
-block:task_list_1#editor@user:alice
-block:task_list_1#commenter@user:bob
-block:task_list_2#database@database:task_list
-block:task_list_2#editor@user:alice
-block:task_list_2#commenter@user:bob
-
-comment:task_list_1_comment_1#block@block:task_list_1
-comment:task_list_1_comment_1#author@user:bob
-comment:task_list_1_comment_2#block@block:task_list_1
-comment:task_list_1_comment_2#author@user:charlie
-comment:task_list_2_comment_1#block@block:task_list_2
-comment:task_list_2_comment_1#author@user:bob
-comment:task_list_2_comment_2#block@block:task_list_2
-comment:task_list_2_comment_2#author@user:charlie
-```
-
-## Test & Validation
-
-Since we have our schema and the sample relation tuples, let's check some permissions and test our authorization logic.
-
-can user:alice write database:task_list ?
-
-
-```perm
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
-
- ..
- ..
-
- // Define permissions for database actions
- ..
- ..
-
- permission write = editor or workspace.write
-
- ..
- ..
- }
-```
-
-According to what we have defined for the **'write'** permission, users who are either;
-
-- The editor in task list database (`database:task_list`)
-- Have a write permission in the engineering team workspace, which is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`)
-
-can edit the task list database (`database:task_list`)
-
-Based on the relation tuples we created, `user:alice` doesn't have the **editor** relationship with the `database:task_list`.
-
-Since `user:alice` is the owner and admin in the engineering team workspace (`workspace:engineering_team#admin@user:alice`) it has a write permission defined in the workspace entity, as you can see below:
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- ..
- ..
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- ..
- permission write = owner or admin
-}
-```
-
-And as we mentioned the engineering team workspace is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`). Therefore, the `user:alice write database:task_list` check request should yield a **'true'** response.
-
-
-
-
-can user:charlie write page:product_spec ?
-
-
-```perm
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
-
- ..
- ..
-
- permission write = writer or workspace.write
-}
-```
-
-`user:charlie` is guest in the workspace (`workspace:engineering_team#guest@user:charlie`) and the engineering team workspace is the only workspace that `page:product_spec` belongs to.
-
-As we defined, guests doesn't have write permission in a workspace.
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- permission write = owner or admin
-}
-```
-
-So that, `user:charlie` doesn't have a write relationship in the workspace. And ultimately, the `user:charlie write page:product_spec` check request should yield a **'false'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
- }
-
- entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
- }
-
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
- }
-
- entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
- }
-
- entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
- }
-
- entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
- }
-
- entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
- }
-
-relationships:
- - workspace:engineering_team#owner@user:alice
- - workspace:engineering_team#member@user:bob
- - workspace:engineering_team#guest@user:charlie
- - workspace:engineering_team#admin@user:alice
- - workspace:sales_team#owner@user:david
- - workspace:sales_team#member@user:eve
- - workspace:sales_team#guest@user:frank
- - workspace:sales_team#admin@user:david
- - page:project_plan#workspace@workspace:engineering_team
- - page:product_spec#workspace@workspace:engineering_team
- - database:task_list#workspace@workspace:engineering_team
- - template:weekly_report#workspace@workspace:sales_team
- - database:customer_list#workspace@workspace:sales_team
- - template:marketing_campaign#workspace@workspace:sales_team
- - page:project_plan#writer@user:frank
- - page:project_plan#reader@user:bob
- - database:task_list#editor@user:alice
- - database:task_list#viewer@user:bob
- - template:weekly_report#creator@user:alice
- - template:weekly_report#viewer@user:bob
- - page:product_spec#writer@user:david
- - page:product_spec#reader@user:eve
- - database:customer_list#editor@user:david
- - database:customer_list#viewer@user:eve
- - template:marketing_campaign#creator@user:david
- - template:marketing_campaign#viewer@user:eve
- - block:task_list_1#database@database:task_list
- - block:task_list_1#editor@user:alice
- - block:task_list_1#commenter@user:bob
- - block:task_list_2#database@database:task_list
- - block:task_list_2#editor@user:alice
- - block:task_list_2#commenter@user:bob
- - comment:task_list_1_comment_1#block@block:task_list_1
- - comment:task_list_1_comment_1#author@user:bob
- - comment:task_list_1_comment_2#block@block:task_list_1
- - comment:task_list_1_comment_2#author@user:charlie
- - comment:task_list_2_comment_1#block@block:task_list_2
- - comment:task_list_2_comment_1#author@user:bob
- - comment:task_list_2_comment_2#block@block:task_list_2
- - comment:task_list_2_comment_2#author@user:charlie
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "database:task_list"
- subject: "user:alice"
- assertions:
- write: true
- - entity: "page:product_spec"
- subject: "user:charlie"
- assertions:
- write: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/modeling.md b/docs/versioned_docs/version-0.5.x/getting-started/modeling.md
deleted file mode 100644
index 4a0a8316..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/modeling.md
+++ /dev/null
@@ -1,555 +0,0 @@
----
-sidebar_position: 1
----
-
-# Modeling Authorization
-
-Permify was designed and structured as a true ReBAC solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-
-With Permify, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group.
-
-This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager, member and also dynamic attributes such as boolean variables, IP range, time period, etc.
-
-
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. It includes set-algebraic operators such as intersection and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-Here’s a simple breakdown of our schema.
-
-
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is **_".perm"_**.
-
-## Developing a Schema
-
-This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-
-We'll follow a simplified version of the GitHub access control system, where teams and organizations have control over the viewing, editing, or deleting access rights of repositories.
-
-Before start I want to share the full implementation of simple Github access control example with using Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
- action edit = member or parent.admin
-
-}
-
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- action push = owner or maintainer
- action read = org.admin and (owner or maintainer or org.member)
- action delete = parent.admin or owner
-
-}
-```
-
-:::info
-You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
-
-[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-
-:::
-
-## Defining Entities
-
-The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
-
-Think of entities as tables in your database. We are strongly advice to name entities same as your database table name that its corresponds. In that way you can easily model and reason your authorization as well as eliminating the error possibility.
-
-You can create entities using `entity` keyword. Let's create some entities according to our example GitHub authorization logic."
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity team {}
-
-entity repository {}
-```
-
-Entities has 2 different attributes. These are;
-
-- **relations**
-- **actions or permissions**
-
-## Defining Relations
-
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions.
-
-Keyword **_relation_** need to used to create a entity relation with name and type attributes.
-
-**Relation Attributes:**
-
-- **name:** relation name.
-- **type:** relation type, basically the entity it’s related to (e.g. user, organization, document, etc.)
-
-An example relation takes form of,
-
-```perm
-relation [name] @[type]
-```
-
-Lets turn back to our example and define our relations inside our entities:
-
-#### User Entity
-
-→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
-
-```perm
-entity user {}
-```
-
-### Roles and User Types
-
-You can define user types and roles within the entity. If you specifically want to define a global role, such as `admin`, we advise defining it at the entity with the most global hierarchy, such as an organization. Then, spread it to the rest of the entities to include it within permissions.
-
-For the sake of simplicity, let's define only 2 user types in an organization, these are administrators and direct members of the organization.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-```
-
-### Parent-Child Relationship
-
-→ Let's say teams can belong organizations and can have a member inside of it as follows,
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
-}
-```
-
-The parent relation is indicating the organization the team belongs to. This way we can achieve **parent-child relationship** within these entities.
-
-### Ownership
-
-In Github workflow, organizations and users can have multiple repositories, so each repository is related with an organization and with users. We can define repository relations as as follows.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-}
-```
-
-The owner relation indicates the creator of the repository, that way we can achieve **ownership** in Permify.
-
-### Multiple Relation Types
-
-As you can see we have new syntax above,
-
-```perm
- relation maintainer @user @team#member
-```
-
-When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-
-:::info
-You can use **#** to reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
-
-Actual purpose of feature locking is to giving ability to specify the sets of users that can be assigned.
-
-For example:
-
-```perm
- relation viewer @user
-```
-
-When you define it like this, you can only add users directly as tuples (you can find out what relation tuples is in next section):
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-
-However, if you define it as:
-
-```perm
- relation viewer @user @organization#member
-```
-
-You will then be able to specify not only individual users but also members of an organization:
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-- organization:1#viewer@organization:O1#member
-
-You can think of these definitions as a precaution taken against creating undesired user set relationships.
-:::
-
-Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
-
-## Defining Actions and Permissions
-
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances.
-
-The basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
-
-### Intersection and Exclusion
-
-The Permify Schema supports **`and`**, **`or`** and **`not`** operators to achieve permission **intersection** and **exclusion**. The keywords **_action_** or **_permission_** can be used with those operators to form rules for your authorization logic.
-
-#### Intersection
-
-Lets get back to our github example and create a read action on repository entity to represent usage of **`and`** &, **`or`** operators,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- ..
- ..
-
- action read = org.admin and (owner or maintainer or org.member)
-
-}
-```
-
-→ If we examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-
-:::info Permission Keyword
-The same `read` can also be defined using the **permission** keyword, as follows:
-
-```perm
- permission read = org.admin and (owner or maintainer or org.member)
-```
-
-Using `action` and `permission` will yield the same result for defining permissions in your authorization logic. See why we have 2 keywords for defining an permission from the [Nested Hierarchies](#nested-hierarchies) section.
-:::
-
-#### Exclusion
-
-After this point, we'll move beyond the GitHub example and explore more advanced abilities of Permify DSL.
-
-Before delving into details, let's examine the **`not`** operator and conclude [Intersection and Exclusion](#intersection-and-exclusion) section.
-
-Here is the **post** entity from our sample [Instagram Authorization Structure](./examples/google-docs.md)example,
-
-```perm
-entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- ..
- ..
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
-}
-```
-
-As you can see from the comment and like actions, a user tagged with the `restricted` attribute — details of defining attributes can be found in the [Attribute Based Permissions (ABAC)](#attribute-based-permissions-abac) section — won't be able to like or comment on the specific post.
-
-This is a simple example to demonstrate how you can exclude users, resources, or any subject from permissions using the **`not`** operator.
-
-### Permission Union
-
-Permify allows you to set permissions that are effectively the union of multiple permission sets.
-
-You can define permissions as relations to union all rules that permissions have. Here is an simple demonstration how to achieve permission union in our DSL, you can use actions (or permissions) when defining another action (or permission) like relations,
-
-```perm
- action edit = member or manager
- action delete = edit or org.admin
-```
-
-The `delete` action inherits the rules from the `edit` action. By doing that, we'll be able to state that only organization administrators and any relation capable of performing the edit action (member or manager) can also perform the delete action.
-
-Permission union is super beneficial in scenarios where a user needs to have varied access across different departments or roles.
-
-### Nested Hierarchies
-
-The reason we have two keywords for defining permissions (`action` and `permission`) is that while most permissions are based on actions (such as view, read, edit, etc.), there are still cases where we need to define permissions based on roles or user types, such as admin or member.
-
-Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
-
-Here is a simple example to demonstrate inherited permissions.
-
-Let's examine a small snippet from our [Facebook Groups](./examples/google-docs.md) real world example. Let's create a permission called 'view' in the comment entity (which represents the comments of the post in Facebook Groups)
-
-Users can only view a comment if:
-
-- The user is the owner of that comment
-**or**
-- The user is a member of the group to which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-### Recursive ReBAC
-
-With Permify DSL, you can define recursive relationship-based permissions within the same entity.
-
-As an example, consider a system where there are multiple organizations within a company, some of which may have a parent-child relationship between them.
-
-As expected, organization members are also granted permission to view their organization details. You can model that as follows:
-
-```perm
-entity user {}
-
-entity organization {
- relation parent @organization
- relation member @user @organization#member
-
- action view = member or parent.member
-}
-```
-
-Let's extend the scenario by adding a rule allowing parent organization members to view details of child organizations. Specifically, a member of **Organization Alpha** could view the details of **Organization Beta** if **Organization Beta** belongs to **Organization Alpha**.
-
-
-
-First authorization schema that we provide won't solve this issue because `parent.member` accommodate single upward traversal in a hierarchy.
-
-Instead of `parent.member` we can call the parent view permission on the same entity - `parent.view` to achieve multiple levels of upward traversal, as follows:
-
-```perm
-entity user {}
-
-entity organization {
- relation parent @organization
- relation member @user @organization#member
-
- action view = member or parent.view
-}
-```
-
-This way, we achieve a recursive relationship between parent-child organizations.
-
-:::note
-*Credits to [Léo](https://github.com/LeoFVO) for the illustration and for [highlighting](https://github.com/Permify/permify/issues/790) this use case.*
-:::
-
-## Attribute Based Permissions (ABAC)
-
-:::success Beta
-Please keep in mind that this feature is still in the **beta stage**, and we're actively seeking user feedback to improve it. As a Beta feature, Permify ABAC support may have some limitations, and its functionality and interface could change in future updates.
-:::
-
-
-To support Attribute Based Access Control (ABAC) in Permify, we've added two main components into our DSL: **attributes** and **rules**.
-
-Attributes are used to define properties for entities in specific data types. For instance, an attribute could be an IP range associated with an organization, defined as a string array:
-
-```perm
-attribute ip_range string[]
-```
-
-There are different types of attributes you can use;
-
-### Boolean - True/False Conditions
-
-For attributes that represent a binary choice or state, such as a yes/no question, the `Boolean` data type is an excellent choice.
-
-```perm
-entity post {
- attribute is_public boolean
-
- permission view = is_public
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
-:::
-
-### Text & Object Based Conditions
-
-String can be used as attribute data type in a variety of scenarios where text-based information is needed to make access control decisions. Here are a few examples:
-
-- **Location:** If you need to control access based on geographical location, you might have a location attribute (e.g., "USA", "EU", "Asia") stored as a string.
-- **Device Type**: If access control decisions need to consider the type of device being used, a device type attribute (e.g., "mobile", "desktop", "tablet") could be stored as a string.
-- **Time Zone**: If access needs to be controlled based on time zones, a time zone attribute (e.g., "EST", "PST", "GMT") could be stored as a string.
-- **Day of the Week:** In a scenario where access to certain resources is determined by the day of the week, the string data type can be used to represent these days (e.g., "Monday", "Tuesday", etc.) as attributes!
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute location string[]
-
- permission view = check_location(request.current_location, location) or admin
-}
-
-rule check_location(current_location string, location string[]) {
- current_location in location
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts string as `""`
-:::
-
-:::info Defining Rules
-
-In above we defined a function called with **rule** keyword.
-
-Rules are structures that allow you to write specific conditions for the model. They accept parameters and are based on conditions.
-
-Another example, a rule could be used to check if a given IP address falls within a specified IP range:
-
-```perm
-rule check_ip_range(ip string, ip_range string[]) {
- ip in ip_range
-}
-```
-:::
-
-### Numerical Conditions
-
-#### Integers
-
-Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
-- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
-- **Resource Size or Length:** If access to resources is controlled based on their size or length (like a document's length or a file's size), these can be stored as integer attributes.
-- **Version Number:** If access control decisions need to consider the version number of a resource (like a software version or a document revision), these can be stored as integer attributes.
-
-```perm
-entity content {
- permission view = check_age(request.age)
-}
-
-rule check_age(age integer) {
- age >= 18
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts integer as `0`
-:::
-
-#### Double - Precise numerical information
-
-Double can be used as attribute data type in several scenarios where precise numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Usage Limit:** If a user has a usage limit (like the amount of storage they can use or the amount of data they can download), and this limit needs to be represented with decimal precision, it can be stored as a double attribute.
-- **Transaction Amount:** In a financial system, if access control decisions need to consider the amount of a transaction, and this amount needs to be represented with decimal precision (like $100.50), these amounts can be stored as double attributes.
-- **User Rating:** If access control decisions need to consider a user's rating (like a rating out of 5 with decimal points, such as 4.7), these ratings can be stored as double attributes.
-- **Geolocation:** If access control decisions need to consider precise geographical coordinates (like latitude and longitude, which are often represented with decimal points), these coordinates can be stored as double attributes.
-
-```perm
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts double as `0.0`
-:::
-
-See more details on [Attribute Based Access Control](#attribute-based-permissions-abac) section to learn our approach on ABAC as well as how it operates in Permify.
-
-## More Advanced Examples
-
-You can check out more advanced and completed schema examples from the [Real World Examples](https://docs.permify.co/docs/getting-started/examples/) section with their detailed examination.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/getting-started/sync-data.md b/docs/versioned_docs/version-0.5.x/getting-started/sync-data.md
deleted file mode 100644
index b8726a02..00000000
--- a/docs/versioned_docs/version-0.5.x/getting-started/sync-data.md
+++ /dev/null
@@ -1,456 +0,0 @@
----
-sidebar_position: 2
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Managing Authorization Data
-
-Permify unifies your authorization data in a database of your preference, which serves as the single source of truth for all authorization queries and requests via the Permify API.
-
-## Access Control as Relations - Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. Each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-In Permify, the simplest form of relational tuple structured as: `entity # relation @ user`. Here are some relational tuples with semantics,
-
-
-
-## Where Relational Tuples Used ?
-
-In Permify, these relational tuples represents your authorization data.
-
-Permify stores your relational tuples (authorization data) in a database you prefer. You can configure the database when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-Stored relational tuples are queried and utilized in Permify APIs, including the check API, which is an access control check request used to determine whether a user's action is authorized.
-
-As an example; to decide whether a user could view a protected resource, Permify looks up the relations between that specific user and the protected resource. These relation types could be ownership, parent-child relation, or even a role such as an admin or manager.
-
-## Creating Relational Tuples
-
-Relational tuples can be created with an simple API call in runtime, since relations and authorization data's are live instances. Each relational tuple should be created according to its authorization model, [Permify Schema].
-
-[Permify Schema]: ../modeling
-
-
-
-Let's follow a simple document management system example with the following Permify Schema to see how to create relation tuples.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity document {
-
- relation owner @user
- relation parent @organization
- relation maintainer @user @organization#member
-
- action view = owner or parent.member or maintainer or parent.admin
- action edit = owner or maintainer or parent.admin
- action delete = owner or parent.admin
-}
-```
-
-According to the schema above; when a user creates a document in an organization, more specifically let's say, when user:1 create a document:2 we need to create the following relational tuple,
-
-- `document:2#owner@user:1`
-
-### Write Data API
-
-You can create relational tuples by using `Write Data API`.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "2",
- },
- Relation: "owner",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "2"
- },
- relation: "owner",
- subject: {
- type: "user",
- id: "1"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "2s"
- },
- "relation": "owner",
- "subject":{
- "type": "user",
- "id": "1",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Snap Tokens
-
-In Write Data API response you'll get a snap token of the operation.
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../reference/snap-tokens.md)
-
-## More Examples
-
-Let's create more example data according to the schema we defined above.
-
-### Organization Admin
-
-**relational tuple:** organization:1#admin@user:3
-
-**Semantics:** User 3 is administrator in organization 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "user",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Parent Organization
-
-**Relational Tuple:** document:1#parent@organization:1#…
-
-**Semantics:** Organization 1 is parent of document 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "parent",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "1",
- Relation: "..."
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "parent",
- subject: {
- type: "organization",
- id: "1",
- relation: "..."
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "parent",
- "subject":{
- "type": "organization",
- "id": "1",
- "relation": "..."
- }
- }
- ]
-}'
-```
-
-
-
-:::info
-Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
-
-Simply, the usage of ... is straightforward: if you're use user entity as an subject, you should not be using the `...` If you're using another subject rather than user entity then you need to use the `...`
-:::
-
-### Organization Members Are Maintainers in specific Doc
-
-**Created relational tuple:** document:1#maintainer@organization:2#member
-
-**Definition:** Members of organization 2 are maintainers in document 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "maintainer",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "2",
- Relation: "member"
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "maintainer",
- subject: {
- type: "organization",
- id: "2",
- relation: "member"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "maintainer",
- "subject":{
- "type": "organization",
- "id": "2",
- "relation": "member"
- }
- }
- ]
-}'
-```
-
-
-
-#### Test this Example on [Playground](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_)
-
-## Audit Logs For Permission Changes
-
-Permify does support audit logs for permission changes. Leveraging the [MVCC (Multi-Version Concurrency Control)](http://mbukowicz.github.io/databases/2020/05/01/snapshot-isolation-in-postgresql.html) pattern, we maintain a history of all permission data changes. This essentially provides an audit trail, allowing users to track alterations and when they occurred.
-
-In cloud version, our system supports change history auditing. It automatically generates and securely stores logs for all significant actions. These logs detail who made the change, what was changed, and when the change occurred. Furthermore, your system allows for easy searching and analysis of these logs, supporting automated alerting for suspicious activities. This comprehensive approach ensures thorough and effective auditing of all changes
-
-## Permission Baselining (Reviewing)
-
-We have a strong foundation for permission baselining and review, thanks to MVCC.
-
-**Historical Review:** You can review the history of permissions changes as each version is stored. This enables retrospective audits and analysis.
-
-**Current State Review:** You can review the current state of permissions by examining the latest versions of each permission setting.
-
-**Cleanup:** Your system incorporates a garbage collector for managing old data, which helps keep your permissions structure clean and optimized.
-
-## Next
-
-Let's now head over to the **Access Control Check** section and learn how to perform access control in Permify to ensure that only authorized users have the right level of access to our resources.
diff --git a/docs/versioned_docs/version-0.5.x/installation.md b/docs/versioned_docs/version-0.5.x/installation.md
deleted file mode 100644
index c855058f..00000000
--- a/docs/versioned_docs/version-0.5.x/installation.md
+++ /dev/null
@@ -1,17 +0,0 @@
----
-id: installation
-title: Setup Permify
-slug: /installation
----
-
-# Setup Permify
-
-Here is some options that you can use to set up and deploy Permify in your servers.
-
-```mdx-code-block
-import {CardList} from '../../src/components/Card';
-
-
-```
-
-If options your deployment preference is not listed below please let us know Also if you have any questions join our [Discord community](https://discord.gg/n6KfzYxhPp) or send us an email at support@permify.co.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/installation/_category_.json b/docs/versioned_docs/version-0.5.x/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.5.x/installation/aws.md b/docs/versioned_docs/version-0.5.x/installation/aws.md
deleted file mode 100644
index c1c204d9..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/aws.md
+++ /dev/null
@@ -1,187 +0,0 @@
----
-title: AWS ECS, ECR & EC2
----
-
-# Deploy on AWS ECS, ECR & EC2
-
-AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
-
-There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
-
-ECS is a container management service. You can run your containers as task definitions, and It’s one of the easiest ways to deploy containers.
-
-If you’d like to watch this tutorial rather than reading. Here’s the video version.
-
-
-
-There is no prerequisite in this tutorial. You can simply deploy permify by following this step-by-step guide. However, if you want to integrate more advanced AWS security & networking features, we’ll follow up with a new tutorial guideline.
-
-At the end of this tutorial you’ll be able to;
-
-1. [Create a security group](#create-an-ec2-security-group)
-2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
-3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
-4. [Running our task definition](#4-running-our-task-definition)
-
-## 1. Create an EC2 Security Group
-
-So first thing first, let’s go over into security groups and create our security group. We’ll need this security group while creating our cluster.
-
-
-
-Search for “Security Groups” in the search bar. And go to the EC2 security groups feature.
-
-
-
-Then start creating a new security group.
-
-
-
-You have to name your security group, and give a description. Also, you need to choose the same VPC that you’ll going to use in EC2. So, I choose the default one. And I’m going to use same one while creating the ECS cluster.
-
-The next step is to configure our inbound rules. Here’s the configuration;
-
-```json
-//for mapping HTTP request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for mapping RPC request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3478",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for using SSH for connecting from your local computer.
-type = "Custom TCP", protocol = "TCP", port_range = "22",source = "Anywhere", 0.0.0.0/0
-```
-
-We have configured the HTTP and RPC ports for Permify. Also, we added port “22” for SSH connection. So, we can connect to EC2 through our local terminal.
-
-Now, we’re good to go. You can create the security group. And it’s ready to use in our ECS.
-
-## 2. Creating an ECS cluster
-
-
-
-The next step is to create an ECS cluster. From your AWS console search for Elastic Container Service or ECS for short.
-
-
-
-Then go over the clusters. As you can see there are 2 types of clusters. One is for ECS and another for EKS. We need to use ECS, EKS stands for Elastic Kubernetes Service. Today we’re not going to cover Kubernetes.
-
-Click **“Create Cluster”**
-
-
-
-Let’s create our first Cluster. Simply you have 3 options; Serverless(Network Only), Linux, and Windows. We’re going to cover EC2 Linux + Networking option.
-
-
-
-The next step is to configure our Cluster, starting with your Cluster name. Since we’re deploying Permify, I’ll call it “permify”.
-
-Then choose your instance type. You can take a look at different instances and pricing from [here](https://aws.amazon.com/ec2/pricing/on-demand/). I’m going with the t4 large. For cost purposes, you can choose t2.micro if you’re just trying out. It’s free tier eligible.
-
-Also, if you want to connect this EC2 instance from your local computer. You need to use SSH. Thus choose a key pair. If you have no such intention, leave it “none”.
-
-
-
-Now, we need to configure networking. First, choose your VPC, we use the default VPC as we did in the security groups. And choose any subnet on that VPC.
-
-You want to enable auto-assigned IP to make your app reachable from the internet.
-
-Choose the security group we have created previously.
-
-And voila, you can create your cluster. Now, we need to run our container in this cluster. To do that, let’s go over task definitions. And create our container definition.
-
-## 3. Creating and running task definitions
-
-Go over to ECS, and click the task definitions.
-
-
-
-And create a new task definition.
-
-
-
-Again, you’re going to ask to choose between; FARGATE, EC2, and EXTERNAL (On-premise). We’ll continue with EC2.
-
-Leave everything in default under the “Configure task and container definitions” section.
-
-
-
-Under the IAM role section you can choose “ecsTaskExecutionRole” if you want to use Cloud Watch later.
-
-You can leave task size in default since it’s optional for EC2.
-
-The critical part over here is to add our container. Click on the “Add Container” button.
-
-
-
-Then we need to add our container details. First, give a name. And then the most important part is our image URI. Permify is registered on the Github Registry so our image is;
-
-```yaml
-ghcr.io/permify/permify:latest
-```
-
-Then we need to define memory limit for the container, I went with 1024. You can define as much as your instance allows.
-
-Next step is to mapping our ports. As we mentioned in security groups, Permify by default listens;
-
-- `3476 for HTTP port`
-- `3478 for RPC port`
-
-
-
-Then we need to define command under the environment section. So, in order to start permify we first need to add “serve” command.
-
-For using properly we need a few other. Here’s the commands we need.
-
-```yaml
-serve, --database-engine=postgres, --database-uri=postgres://:@:/, --database-pool-max=20
-```
-
-- `serve` ⇒ for starting the Permify.
-- `--database-engine=postgres` ⇒ for defining the db we use.
-- `--database-uri=postgres://:password@:/` ⇒ for connecting your database with URI.
-- `--database-pool-max=20` ⇒ the depth for running in graph.
-
-We’re nice and clear, add the container and then just create your task definition. We’ll use this definition to run in our cluster.
-
-So, let’s go over and run our task definition.
-
-## 4. Running our task definition
-
-
-
-Let’s go to ECS and enter into our cluster. And go over into the tasks to run our task.
-
-
-
-Click to “Run new Task”
-
-
-
-Choose EC2 as a launch type. Then pick the task definition we just created. And leave everything else in the default. You can run your task now.
-
-We have just deployed our container into EC2 instance with ECS. Let’s test it.
-
-Now you can go over into EC2, and click on the running instances. Find the instance named `ECS Instance - EC2ContainerService-` in the running instances.
-
-
-
-Copy the Public IPv4 DNS from the right corner, and paste it into your browser. But you need to add `:3476` to access our http endpoint. So it should be like this;
-
-`:3476`
-
-and if you add healthz at the end like this;
-
-`:3476/healthz`
-
-you should get Serving status :)
-
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/installation/azure.md b/docs/versioned_docs/version-0.5.x/installation/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/installation/brew.md b/docs/versioned_docs/version-0.5.x/installation/brew.md
deleted file mode 100644
index 0212df8b..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/brew.md
+++ /dev/null
@@ -1,66 +0,0 @@
----
-title: "Install with Brew"
----
-
-# Brew With Configurations
-
-This section shows how to install and run Permify Service using brew.
-
-### Install Permify
-
-Open terminal and run the following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-### Run Permify Service
-
-To run the Permify Service, `permify serve` command should be run.
-
-By default, the service is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather then an actual database. You can override these by running the command with configuration flags.
-
-### Configure By Using Flags
-
-See all the configuration flags by running,
-
-```shell
-permify serve --help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Configure With Using Config File
-
-You can also configure Permify Service by using a configuration file.
-
-```shell
- permify serve -c=config.yaml
-```
-
-or
-
-```shell
- permify serve --config=config.yaml
-```
-
-### Test your connection.
-
-You can test your connection by making an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview/
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with a Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/installation/container.md b/docs/versioned_docs/version-0.5.x/installation/container.md
deleted file mode 100644
index aa0b7686..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/container.md
+++ /dev/null
@@ -1,55 +0,0 @@
----
-title: "Docker Container"
----
-
-# Run using Docker
-
-This section shows how to run Permify using our docker container. You can run Permify using Docker with following command.
-
-## Run in a terminal
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
-```
-
-This will start a Permify server with the configuration that is in **{YOUR-CONFIG-PATH}**.
-
-### Configure with a YAML file
-
-This config path - `{YOUR-CONFIG-PATH}` - should contain the [config yaml file](../reference/configuration.md), where you can configure the Permify Server as well as define the ***database*** to store your authorization related data in.
-
-:::info Talk to an Permify Engineer
-By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database.
-:::
-
-### Configure Using Flags
-
-Alternatively, you can set configuration options using flags when running the command. See all the configuration flags by running,
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve -help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Test your connection.
-
-You can test your connection by making an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with a Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/installation/google.md b/docs/versioned_docs/version-0.5.x/installation/google.md
deleted file mode 100644
index deb30dc9..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/google.md
+++ /dev/null
@@ -1,271 +0,0 @@
----
-title: Deploy on Google Compute Engine
----
-
-This guide outlines the process of deploying Permify, on Google Compute Engine. The steps include setting up Google Cloud SDK and kubectl, managing containers using Google Kubernetes Engine (GKE), deploying Permify, and implementing Permify in a distributed configuration with Serf. By following these steps, you can efficiently deploy Permify on Google's scalable and secure infrastructure.
-
-## Google Cloud SDK Install
-
-1. At the command line, run the following command:
-
- ```bash
- curl https://sdk.cloud.google.com | bash
- ```
-
-2. When prompted, choose a location on your file system (usually your Home directory) to create the `google-cloud-sdk` subdirectory under.
-3. If you want to send anonymous usage statistics to help improve gcloud CLI, answer `Y` when prompted.
-4. To add gcloud CLI command-line tools to your `PATH` and enable command completion, answer `Y` when prompted
-5. Restart your shell:
-
- ```bash
- exec -l $SHELL
- ```
-
-6. To initialize the Google Cloud CLI environment, run `gcloud init`
-
-## Install kubectl
-
-1. Install the `kubectl` component:
-
- ```bash
- gcloud components install kubectl
- ```
-
-2. Verify that `kubectl` is installed:
-
- ```bash
- kubectl version
- ```
-
-3. Install Authn Plug-in
-
- ```bash
- gcloud components install gke-gcloud-auth-plugin
- ```
-
- Check the `gke-gcloud-auth-plugin` binary version:
-
- ```bash
- gke-gcloud-auth-plugin --version
- ```
-
-
-## Create Containers with GKE
-
-1. Login & Initialize Google Cloud CLI
-
- ```bash
- gcloud init
- ```
-
-2. Follow configuration instructions
-3. Create Container Cluster
-
- ```bash
- gcloud container clusters create [CLUSTER_NAME]
- ```
-
-4. Authenticate the cluster
-
- ```bash
- gcloud container clusters get-credentials [CLUSTER_NAME]
- ```
-
-
-## Deploy Permify
-
-1. Apply deployment config
-
- ```bash
- kubectl apply -f deployment.yaml
- ```
-
- - **Deployment.yaml**
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- labels:
- app: permify
- name: permify
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
- status: {}
- ```
-
-2. Apply service manfiest
-
- ```bash
- kubectl apply -f service.yaml
- ```
-
- - **Service Manifest**
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
- status:
- loadBalancer: {}
- ```
-
-
-## Deploying Permify in a Distributed Configuration
-
-If you aim to deploy Permify in a distributed configuration, you will need to create a Serf deployment. The Serf deployment can be dockerized to our Container Registry under the name permify/serf:v1.0, which is provided by Hashicorp.
-
-Please note: It is crucial to ensure that both Serf and Permify deployments reside within the same namespace for proper operation.
-
-1. Serf Service Create:
- - Serf Deployment&Service yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: serf-deployment
- spec:
- replicas: 1
- selector:
- matchLabels:
- app: serf
- template:
- metadata:
- labels:
- app: serf
- spec:
- containers:
- - name: serf
- image: permify/serf:v1.0
- args:
- - "-node=main-serf"
- ports:
- - containerPort: 7946
- resources:
- requests:
- cpu: 100m
- memory: 128Mi
- limits:
- cpu: 200m
- memory: 256Mi
- ---
- apiVersion: v1
- kind: Service
- metadata:
- name: serf
- spec:
- selector:
- app: serf
- ports:
- - protocol: TCP
- port: 7946
- targetPort: 7946
- name: serf
- type: ClusterIP
- ```
-
-2. Apply Deployment Manifest
- - Deployment.yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: permify-deployment
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: permify/permify:tagname
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- - "--distributed-enabled=true"
- - "--distributed-node=serf:7946"
- - "--distributed-node-name=main-serf"
- - "--distributed-protocol=serf"
- resources:
- requests:
- memory: "128Mi"
- cpu: "200m"
- limits:
- memory: "128Mi"
- cpu: "400m"
- ports:
- - containerPort: 3476
- name: permify-port
- - containerPort: 7946
- name: permify-dist
- - containerPort: 6060
- name: permify-pprof
- ```
-
-3. Apply Service Manifest
- - Service.yaml
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: permify-port
- port: 3476
- targetPort: 3476
- - name: permify-dist
- port: 7946
- targetPort: 7946
- selector:
- app: permify
- type: LoadBalancer
- ```
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/installation/overview.md b/docs/versioned_docs/version-0.5.x/installation/overview.md
deleted file mode 100644
index 76fb8a56..00000000
--- a/docs/versioned_docs/version-0.5.x/installation/overview.md
+++ /dev/null
@@ -1,259 +0,0 @@
----
-sidebar_position: 1
----
-
-# Guide
-
-This guide shows you how to set up Permify in your servers and use it across your applications.
-
-:::info Minimum Requirements
-PostgreSQL: Version 13.8 or higher
-:::
-
-Please ensure your system meets these requirements before proceeding with the following steps:
-
-1. [Set Up & Run Permify Service](#set-up-permify-service)
-2. [Model your Authorization with Permify's DSL, Permify Schema](#model-your-authorization-with-permify-schema)
-3. [Manage and Store Authorization Data as Relational Tuples](#store-authorization-data-as-relational-tuples)
-4. [Perform Access Check](#perform-access-check)
-
-:::info Talk to an Permify Engineer
-Want to walk through this guide 1x1 rather than docs ? [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-:::
-
-## Set Up Permify Service
-
-You can run Permify Service with various options but in that tutorial we'll run it via docker container.
-
-### Run From Docker Container
-
-Production usage of Permify needs some configurations such as defining running options, selecting datastore to store authorization data and more.
-
-However, for the sake of this tutorial we'll not do any configurations and quickly start Permify on your local with running the docker command below:
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve
-```
-
-This will start Permify with the default configuration options:
-* Port 3476 is used to serve the REST API.
-* Port 3478 is used to serve the GRPC Service.
-* Authorization data stored in memory.
-
-:::info
-You can examine [Deploy using Docker] section to get more about the configuration options and learn the full integration to run Permify Service from docker container.
-
-[Deploy using Docker]: ../container
-:::
-
-### Test your connection
-
-You can test your connection with creating an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core endpoints.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-## Model your Authorization with Permify Schema
-
-After installation completed and Permify server is running, next step is modeling authorization with Permify authorization language - [Permify Schema]- and configure it to Permify API.
-
-You can define your entities, relations between them and access control decisions of each actions with using [Permify Schema].
-
-### Creating your authorization model
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-
-:::
-
-Let's create our authorization model. We'll be using following a simple user-organization authorization case for this guide.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action view_files = admin or member
- action edit_files = admin
-
-}
-```
-
-We have 2 entities these are **"user"** and **"organization"**. Entities represents your main tables. We strongly advise naming entities the same as your original database entities.
-
-Lets roll back our example,
-
-- The `user` entity represents users. This entity is empty because it's only responsible for referencing users.
-
-- The `organization` entity has its own relations (`admin` and `member`) which related with user entity. This entity also has 2 actions, respectively:
- - Organization member and admin can view files.
- - Only admins can edit files.
-
-:::info
-For implementation sake we'll not dive more deep about modeling but you can find more information about modeling on [Modeling Authorization with Permify] section. Also can check out [example use cases] to better understand some basic use cases modeled with Permify Schema.
-
-[Modeling Authorization with Permify]: ../../getting-started/modeling
-[example use cases]: ../../use-cases/simple-rbac
-:::
-
-### Configuring Schema via API
-
-After modeling completed, you need to send Permify Schema - authorization model - to [Write Schema API](../api-overview/schema/write-schema.md) for configuration of your authorization model on Permify authorization service.
-
-:::caution Before Continue on Writing Schema
-You'll see **tenant_id** parameter almost all Permify APIs including Write Schema. With version 0.3.x Permify became a tenancy based authorization infrastructure, and supports multi-tenancy by default so its a mandatory parameter when doing any operations.
-
-We provide a pre-inserted tenant - **t1** - for ones that don't need/want to use multi-tenancy. So, we will be passing **t1** to all tenant id parameters throughout this guidance.
-:::
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-**POST /v1/tenants/{tenant_id}/schemas/write**
-
-
-
-## Store Authorization Data as Relational Tuples
-
-After you completed configuration of your authorization model via Permify Schema. Its time to add authorizations data to see Permify in action.
-
-### Create Relational Tuples
-
-You can create relational tuples as authorization rules by using [Write Data API](../api-overview/data/write-data.md)
-
-For our guide let's grant one of the team members (Ashley) an admin role.
-
-#### Example HTTP Request on Postman:
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field.
-| [x] | tuples | array | - | Can contain multiple relation tuple object|
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1”|
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc.|
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-
-**POST /v1/tenants/{tenant_id}/data/write**
-
-```json
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1" //Organization identifier
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "1", //Ashley's identifier
- "relation": ""
- }
- }
- ]
-}
-```
-
-
-
-**Created relational tuple:** organization:1#admin@user:1
-
-**Semantics:** User 1 (Ashley) has admin role on organization 1.
-
-:::tip
-In ideal production usage Permify stores your authorization data in a database you prefer. You can configure the database with using [configuration yaml file](https://github.com/Permify/permify/blob/master/example.config.yaml) or CLI flag options.
-
-But in this tutorial Permify Service running default configurations on local, so authorization data will be stored in memory. You can find more detailed explanation how Permify stores authorization data in [Managing Authorization Data] section.
-
-[Managing Authorization Data]: ../../getting-started/sync-data
-:::
-
-## Perform Access Check
-
-Finally we're ready to control authorization. Access decision results computed according to relational tuples and the stored model, [Permify Schema] action conditions.
-
-Lets get back to our example and perform an example access check via [Check API]. We want to check whether an specific user has an access to view files in a organization.
-
-[Check API]: ../../api-overview/permission/check-api
-[Permify Schema]: ../../getting-started/modeling
-
-#### Example HTTP Request:
-
-***Can the user 45 view files on organization 1 ?***
-
-**POST /v1/tenants/{tenant_id}/permissions/check**
-
-| Required | Argument | Type | Default | Description |
-|----------|----------------|----------|---------|---------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this field. |
-| [x] | entity | object | - | name and id of the entity. Example: organization:1. |
-| [x] | action | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action |
-| [ ] | schema_version | string | - | get results according to given schema version |
-| [ ] | depth | integer | 8 | - |
-
-### Request
-
-```json
-{
- "metadata": {
- "schema_version": "",
- "snap_token": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_files",
- "subject": {
- "type": "user",
- "id": "45",
- "relation": ""
- },
-}
-```
-
-### Response
-
-```json
-{
- "can": "RESULT_ALLOW",
- "metadata": {
- "check_count": 0
- }
-}
-```
-
-See [Access Control Check] section for learn how access checks works and access decisions evaluated in Permify
-
-[Access Control Check]: ../api-overview/permission/check-api.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you struggle with installation or have any questions, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/permify-overview/_category_.json b/docs/versioned_docs/version-0.5.x/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/versioned_docs/version-0.5.x/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.5.x/permify-overview/authorization-service.md b/docs/versioned_docs/version-0.5.x/permify-overview/authorization-service.md
deleted file mode 100644
index 55a6906d..00000000
--- a/docs/versioned_docs/version-0.5.x/permify-overview/authorization-service.md
+++ /dev/null
@@ -1,40 +0,0 @@
-
-# Authorization As A Service
-
-An authorization service is a module that allows you to manage access to your application and ease the development and maintenance of your authorization system. It works in run time and respond to all authorization questions from any of your apps.
-
-
-
-[Permify] is a fully open source **authorization service** that offers a variety of binding and crafting options to secure your applications. It's designed to be deployed as a authorization service rather than a library compiled into an application.
-
-[Permify]: https://github.com/Permify/permify
-
-## Benefits of using an Authorization Service
-
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch. You can get started quickly with a simple API that you can easily integrate into your application to move and iterate faster.
-
-### Scale As You Wish
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps. Building a scalable and robust authorization system is hard and needs a quite engineering time. Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period. Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services.
-
-[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-
-### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group. Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time. Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
-
-### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road. Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product. Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production. After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
-
-### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security. Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
-
-## Cases that can benefit from An Authorization Service:
-
-- If you already have an identity/auth solution and want to plug in fine-grained authorization on top of that.
-- If you want to create a unified access control mechanism to use across your individual applications.
-- If you want to make future-proof authorization system and don't want to spend engineering effort for it.
-- If you’re managing authorization for growing micro-service infrastructure.
-- If your authorization logic is cluttering your code base.
-- If your data model is getting too complicated to handle your authorization within the service.
-- If your authorization is growing too complex to handle within code or API gateway.
-
diff --git a/docs/versioned_docs/version-0.5.x/permify-overview/infrastructure.md b/docs/versioned_docs/version-0.5.x/permify-overview/infrastructure.md
deleted file mode 100644
index 0f29223d..00000000
--- a/docs/versioned_docs/version-0.5.x/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,79 +0,0 @@
-
-# Architecture & Deployment
-
-Permify is a infrastructure for ease the process of creating and managing scalable authorization systems in your environment.
-
-This section shows where and how does Permify fit into your environment with examining Permify's high level design, internal architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## High Level Design
-
-You can model your authorization logic with **Permify's domain specific language** and your applications can interpolate with Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data and more!
-
-Permify stores access control relations in a **database of your choice**, and each API request evaluates and takes into account access decisions based on the stored relations.
-
-So this preferred database behaves as a **centralized data source** for your authorization system.
-
-
-
-### Permify vs Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Architecture
-
-Permify supports both HTTP and GRPC. HTTP requests are converted to GRPC and then transferred to Permify servers.
-
-There are 4 servers in a Permify Instance: Permission, Relationship, Schema, and Watch.
-
-- **Permission Server:** The permission server forwards the request to the invoker. The invoker checks for any missing parts of the query, let’s say if no snapshot is provided, it finds the head snapshot. It then hashes the request (with snapshot and schema version) and forwards it to the most convenient Permify instance. If the hash matches its own, it directs it to the local cache. If the cache does not contain the request, it proceeds to the engine. The engine breaks down the query into sub-queries and returns it to the invoker. This process continues until a final decision is made.
-- **Relationship Server:** After validating the request, it passes it to the database access layer.
-- **Schema Server:** After validating the request, it passes it to the database access layer.
-- **Watch Server:** It broadcasts changes in relationships based on their snapshots.
-
-
-
-Database abstractions for the reader and writer can use a database like Aurora Postgres.
-
-When deploying, separate hosts can be used in the Permify config for the reader and writer. This way, different Permify instances can read from different read replicas.
-
-**Note:** we are using serf (https://github.com/hashicorp/serf) agent for node discovery on hashring.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization.
-
-Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications.
-
-See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important.
-
-As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/versioned_docs/version-0.5.x/permify-overview/intro.md b/docs/versioned_docs/version-0.5.x/permify-overview/intro.md
deleted file mode 100644
index 69c135f2..00000000
--- a/docs/versioned_docs/version-0.5.x/permify-overview/intro.md
+++ /dev/null
@@ -1,117 +0,0 @@
----
-sidebar_position: 1
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is an **open source authorization service** for creating fine-grained and scalable authorization systems.
-
-With Permify, you can easily structure your authorization model, store authorization data in your preferred database, and interact with the Permify API to handle all authorization queries from your applications or services.
-
-Permify is inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://permify.co/post/google-zanzibar-in-a-nutshell/).
-
-### Motivation
-
-Our goal is to make **Google's Zanzibar** available to everyone and help them to build robust, flexible, and easily auditable authorization system that establishes a [natural linkage between permissions](https://permify.co/post/relationship-based-access-control-rebac/) across the business units, functions, and entities of an organization.
-
-## Key Features
-
-🛡️ **Production ready** authorization API that serve as **gRPC** and **REST**.
-
-🔮 Domain Specific Authorization Language to **easily model** your authorization. Supporting RBAC, ReBAC, ABAC and more.
-
-🔐 Database Configuration to store your permissions with **high availability** and **low latency**.
-
-✅ Perform access control checks and get answers **down to 10ms** with our various cache mechanisms that we operate.
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-⚙️ Create custom permissions for your **tenants**, and manage them in a single place with **Multi Tenancy**.
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin].
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Getting Started
-
-In Permify, authorization is divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify will [Store Authorization Data] as relations.
-- Perform [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../../getting-started/modeling
-[Store Authorization Data]: ../../getting-started/sync-data
-[Access Checks]: ../../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want to try it out and examine it instantly,
-
-
-
-## Community & Support
-
-We would love to hear from you :heart:
-
-You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
-
-For feature requests, bugs, or any improvements you can always open an [issue](https://github.com/permify/permify/issues).
-
-### Want to Contribute? Here are the ways to contribute to Permify
-
-* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
-* **Improve documentation:** Alongside our codebase, documentation is an important part of our open-source journey. We're trying to give the best DX possible to explain ourselves and Permify. And you can help with that by importing resources or adding new ones.
-* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
-
-You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
-
-## Communication Channels
-
-If you like Permify, please consider giving us a :star: on [github](https://github.com/permify/permify)
-
-
-
-## Roadmap
-
-You can find Permify's Public Roadmap [here](https://github.com/orgs/Permify/projects/1)!
-
-## Need any help on Authorization ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify or how it might fit into your authorization workflow, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.5.x/playground.md b/docs/versioned_docs/version-0.5.x/playground.md
deleted file mode 100644
index 384c3485..00000000
--- a/docs/versioned_docs/version-0.5.x/playground.md
+++ /dev/null
@@ -1,160 +0,0 @@
----
-sidebar_position: 6
----
-
-# Using Permify Playground
-
-You can use our [Playground] to create and test your authorization schema in a browser.
-
-Our playground consists 3 main sections,
-
-- [Schema (Authorization Model)](#schema-authorization-model)
-- [Authorization Data](#authorization-data)
-- [Enforcement](#enforcement-access-check-scenarios)
-
-Let's examine these sections by following a simple example.
-
-[Playground]: https://play.permify.co/
-
-## Schema (Authorization Model)
-
-You can create your authorization model in this section with using our domain specific language.
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. We already have a couple of use cases and example that you can choose to see how authorization can be structured. Also, you can check our docs to [learn more about how to model authorization](./getting-started/modeling.md) in Permify.
-
-To demonstrate how the playground works, let's create a simple authorization model as follows. This model should be selected as the default when you open the playground.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents owner of this repository
- relation owner @user
-
- // permissions
- permission edit = parent.admin or owner
- permission delete = owner
-}
-```
-
-We have 2 permissions, `edit` for access of editing repository and `delete` for access of deleting repository.
-
-Repositories has parent child relation with organizations. The `parent` relation in the repository entity represents that parent child association, while ownership of the repository is represented with the `owner` relation.
-
-Organizations can have organizational wide roles such as admin and member, which defined as `admin` and `member` relation in organization entity.
-
-:::info Automatic Saving for Schema Changes
-Schema changes are captured automatically, and other sections update accordingly. Some delays may occur at times; please feel free to reach out if these delays hinder your testing process.
-:::
-
-### Visualizer
-
-We get loads of feedback about the observability and reasonability of the authorization model across teams and colleagues.
-
-So we put a simple visualizer that shows how your authorization structure looks at a high level. In particular, you can examine relations between entities and their permissions.
-
-
-
-## Authorization Data
-
-You can create sample authorization data to test your authorization logic. In Permify, authorization data stored as tuples and these tuples stored in a database that you preferred.
-
-The basic tuple takes the form of:
-
-`entity # relation @ user`
-
-So the entity can be any entity that you defined in your model. If we look up our example it can be an organization or repository (since the user is empty). The relation can be one of the defined relations in the selected entity.
-
-The user is basically the user or user set in our system. Let's say we want make the **user 1** `admin` in **organization 1** then we need to create an example relational tuple according to our model as follows:
-
-`organization:1#admin@user:1`
-
-To create a relation tuple in playground just hit the **Add Relationship** button.
-
-
-
-You can choose entity, relation and the subject (user or user set) with entering identifier to create sample data. Let's create the relation tuple `organization:1#admin@user:1` as follows.
-
-
-
-Let's add one more relation tuple to perform a sample access check. I want to add repository:1 into organization:1 - `repository:1#parent@organization:1#...` as follows:
-
-
-
-Created tuples shown in the **Data** section as follows.
-
-
-
-## Enforcement (Access Check Scenarios)
-
-Finally as we have a sample data let's perform an access check!
-
-The YAML in the Enforcement section represents a test scenario for conducting access checks. This scenario-based testing process provides the ability to execute complex access scenarios in a single place.
-
-Let's name our scenario **"admin_access_test"** and create tests to check:
-
-- Whether user:1 (admin) can edit repository:1?
-- Whether user:1 (admin) can delete repository:1?
-
-Below is the YAML scenario covering these two tests:
-
-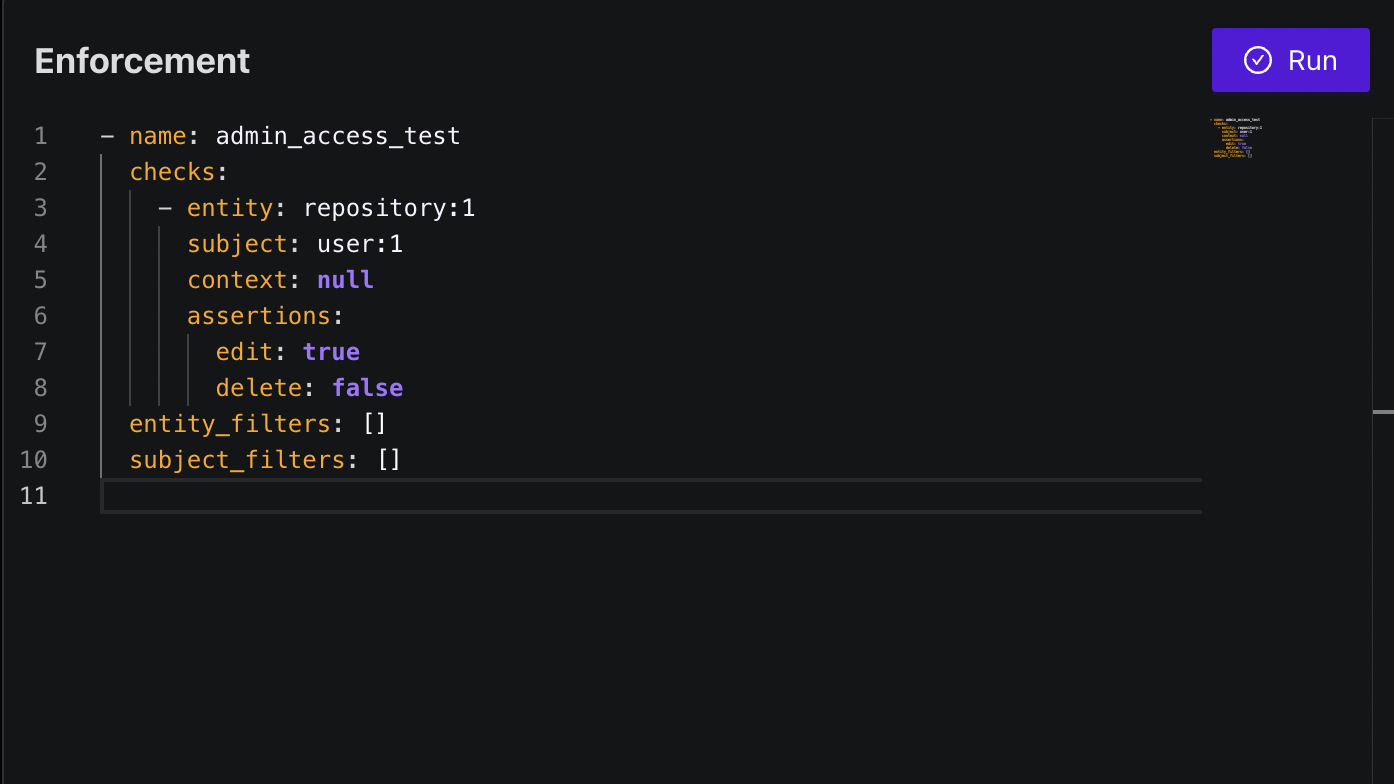
-
-In the above YAML structure,
-
-#### entity
-
-Represents the resource for which we want to check access - `repository:1`
-
-#### subject
-
-Represents the subject that performs the action or grants access - `user:1`.
-
-#### assertions
-
-Assertions stands for defining the expected result for specific action or an permission. In our case we're evaluating access for edit action.
-
-Since organization:1 is parent of repository:1 ( `repository:1#parent@organization:1#...` ) and user:1 has an admin role in organization:1 ( `organization:1#admin@user:1` ) user:1 should allow to edit the repository:1 because the we define rule of the edit permission as:
-
-`permission edit = parent.admin or owner`
-
-:::note
-which `parent.admin` indicates admin in the organization that repository belongs to.
-:::
-
-So user:1 should be able to edit resource:1, therefore expected outcome for that access request is true.
-- `edit: true`
-
-On the other hand, user:1 should't be able to delete resource:1, because only owners can. Therefore expected outcome for that is false.
-- `delete: false`
-
-:::info Create More Advanced Scenarios
-For simplicity, we've created a basic scenario. However, you can create more advanced scenarios using our validation YAML structure.
-
-To learn how to use this syntax for complex scenarios, refer to the [Creating Test Scenarios](../getting-started/testing#creating-test-scenarios) section in [Testing & Validation](./getting-started/testing.md) page.
-:::
-
-Let's click the Run button to execute our scenario.
-
-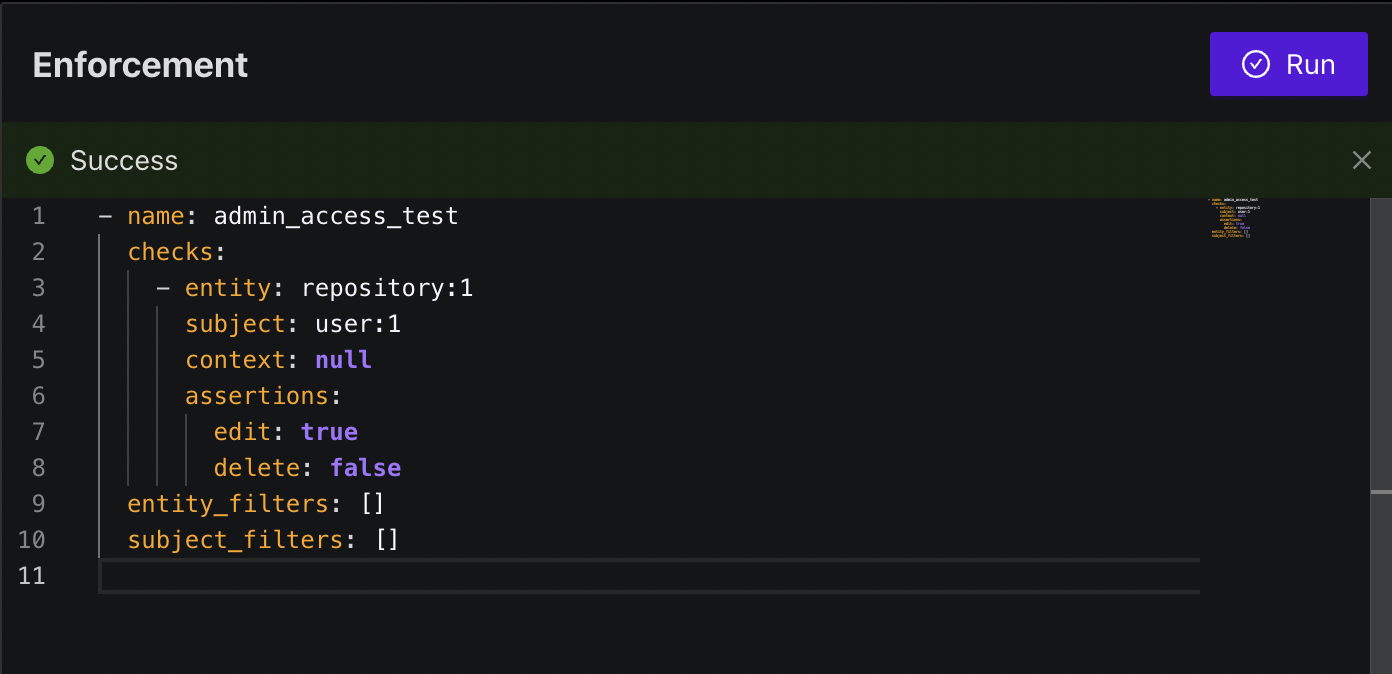
-
-Let's change the expected outcome as false (`edit: false`) and hit the **Run** button again we'll see an error message.
-
-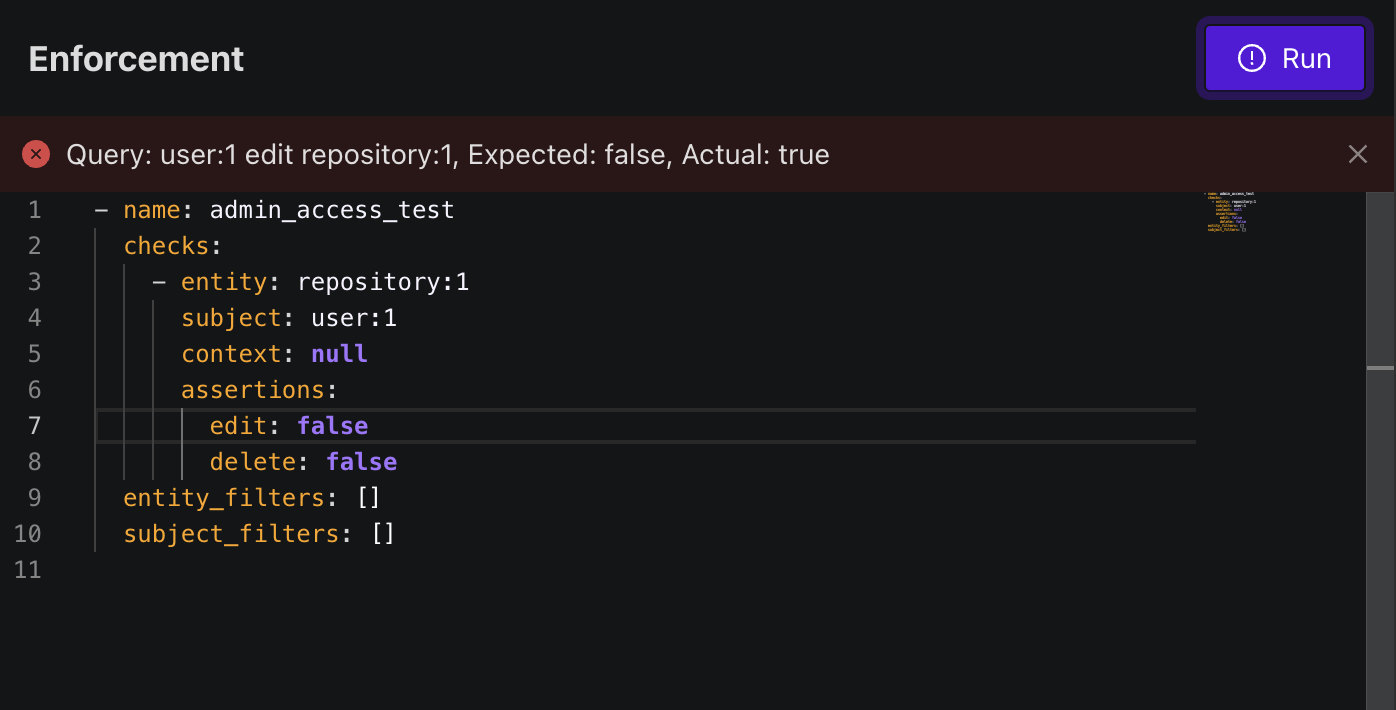
-
-As we seen above this is how you can model your authorization and test it with sample data in Permify Playground.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/reference/_category_.json b/docs/versioned_docs/version-0.5.x/reference/_category_.json
deleted file mode 100644
index b55d99d8..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Reference",
- "position": 8,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.5.x/reference/configuration.md b/docs/versioned_docs/version-0.5.x/reference/configuration.md
deleted file mode 100644
index df94202b..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/configuration.md
+++ /dev/null
@@ -1,491 +0,0 @@
-# Configuration File
-
-Permify offers various options for configuring your Permify API Server.
-
-Here is the example configuration YAML file with glossary below. You can also find
-this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-
-***Example config.yaml file***
-
-```yaml
-# The server section specifies the HTTP and gRPC server settings,
-# including whether or not TLS is enabled and the certificate and
-# key file locations.
-server:
- rate_limit: 100
- http:
- enabled: true
- port: 3476
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
- grpc:
- port: 3478
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
-
-# The logger section sets the logging level for the service.
-logger:
- level: info
-
-# The profiler section enables or disables the pprof profiler and
-# sets the port number for the profiler endpoint.
-profiler:
- enabled: true
- port: 6060
-
-# The authn section specifies the authentication method for the service.
-authn:
- enabled: true
- method: preshared
- preshared:
- keys: []
-
-# The tracer section enables or disables distributed tracing and sets the
-# exporter and endpoint for the tracing data.
-tracer:
- exporter: zipkin
- endpoint: http://localhost:9411/api/v2/spans
- enabled: true
-
-# The meter section enables or disables metrics collection and sets the
-# exporter and endpoint for the collected metrics.
-meter:
- exporter: otlp
- endpoint: localhost:4318
- enabled: true
-
-# The service section sets various service-level settings, including whether
-# or not to use a circuit breaker, and cache sizes for schema, permission,
-# and relationship data.
-service:
- circuit_breaker: false
- watch:
- enabled: false
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
- permission:
- bulk_limit: 100
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
- relationship:
-
-# The database section specifies the database engine and connection settings,
-# including the URI for the database, whether or not to auto-migrate the database,
-# and connection pool settings.
-database:
- engine: postgres
- uri: postgres://user:password@host:5432/db_name
- auto_migrate: false
- max_open_connections: 20
- max_idle_connections: 1
- max_connection_lifetime: 300s
- max_connection_idle_time: 60s
- garbage_collection:
- enabled: true
- interval: 200h
- window: 200h
- timeout: 5m
-
-# distributed configuration settings
-distributed:
- # Indicates whether the distributed mode is enabled or not
- enabled: true
-
- # The address of the distributed service.
- # Using a Kubernetes DNS name suggests this service runs in a Kubernetes cluster
- # under the 'default' namespace and is named 'permify'
- address: "kubernetes:///permify.default"
-
- # The port on which the service is exposed
- port: "5000"
-
-```
-
-## Options
-
-server | Server Configurations
-
-
-#### Definition
-
-Server options to run Permify. (`grpc` and `http` available for now.)
-
-#### Structure
-
-```
-├── server
- ├── rate_limit
- ├── (`grpc` or `http`)
- │ ├── enabled
- │ ├── port
- │ └── tls
- │ ├── enabled
- │ ├── cert
- │ └── key
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|---------------------------|---------|---------------------------------------------------------------------|
-| [ ] | rate_limit | 100 | the maximum number of requests the server should handle per second. |
-| [x] | [ server_type ] | - | server option type can either be `grpc` or `http`. |
-| [ ] | enabled (for server type) | true | switch option for server. |
-| [x] | port | - | port that server run on. |
-| [x] | tls | - | transport layer security options. |
-| [ ] | enabled (for tls) | false | switch option for tls |
-| [ ] | cert | - | tls certificate path. |
-| [ ] | key | - | tls key pat |
-
-#### ENV
-
-| Argument | ENV | Type |
-|---------------------------|-----------------------------------|--------------|
-| rate_limit | PERMIFY_RATE_LIMIT | int |
-| grpc-port | PERMIFY_GRPC_PORT | string |
-| grpc-tls-enabled | PERMIFY_GRPC_TLS_ENABLED | boolean |
-| grpc-tls-key-path | PERMIFY_GRPC_TLS_KEY_PATH | string |
-| grpc-tls-cert-path | PERMIFY_GRPC_TLS_CERT_PATH | string |
-| http-enabled | PERMIFY_HTTP_ENABLED | boolean |
-| http-port | PERMIFY_HTTP_PORT | string |
-| http-tls-key-path | PERMIFY_HTTP_TLS_KEY_PATH | string |
-| http-tls-cert-path | PERMIFY_HTTP_TLS_CERT_PATH | string |
-| http-cors-allowed-origins | PERMIFY_HTTP_CORS_ALLOWED_ORIGINS | string array |
-| http-cors-allowed-headers | PERMIFY_HTTP_CORS_ALLOWED_HEADERS | string array |
-
-
-
-#### Definition
-
-You can choose to authenticate users to interact with Permify API.
-
-There are 2 authentication method you can choose:
-
-* [Pre Shared Keys](#pre-shared-keys)
-* [OpenID Connect](#openid-connect)
-
-#### Pre Shared Keys
-
-On this method, you must provide a pre shared keys in order to identify yourself.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── keys
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | true | switch option authentication config |
-| [x] | keys | - | Private key/keys for server authentication. Permify does not provide this key, so it must be generated by the users. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-preshared-keys | PERMIFY_AUTHN_PRESHARED_KEYS | string array |
-
-
-#### OpenID Connect
-
-Permify supports OpenID Connect (OIDC). OIDC provides an identity layer on top of OAuth 2.0 to address the shortcomings
-of using OAuth 2.0 for establishing identity.
-
-With this authentication method, you be able to integrate your existing Identity Provider (IDP) to validate JSON Web
-Tokens (JWTs) using JSON Web Keys (JWKs). By doing so, only trusted tokens from the IDP will be accepted for
-authentication.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── client-id
-| ├── issuer
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|-----------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | false | switch option authentication config |
-| [x] | client_id | - | This is the client ID of the application you're developing. It is a unique identifier that is assigned to your application by the OpenID Connect provider, and it should be included in the JWTs that are issued by the provider. |
-| [x] | issuer | - | This is the URL of the provider that is responsible for authenticating users. You will use this URL to discover information about the provider in step 1 of the authentication process. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-oidc-issuer | PERMIFY_AUTHN_OIDC_ISSUER | string |
-| authn-oidc-client-id | PERMIFY_AUTHN_OIDC_CLIENT_ID | string |
-
-
-
-
-
-tracer | Tracing Configurations
-
-
-#### Definition
-
-Permify integrated with [jaeger], [otlp], [signoz], and [zipkin] tacing tools to analyze performance and behavior of your
-authorization when using Permify.
-
-#### Structure
-
-```
-├── tracer
-| ├── exporter
-| ├── endpoint
-| ├── enabled
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------|
-| [x] | exporter | - | Tracer exporter, the options are `jaeger`, `otlp`, `signoz`, and `zipkin`. |
-| [x] | endpoint | - | export uri for tracing data. |
-| [ ] | enabled | false | switch option for tracing. |
-| [ ] | insecure | false | Whether to use HTTP instead of HTTPs for exporting the traces. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|----------------------|-------------------------------|--------------|
-| tracer-enabled | PERMIFY_TRACER_ENABLED | boolean |
-| tracer-exporter | PERMIFY_TRACER_EXPORTER | string |
-| tracer-endpoint | PERMIFY_TRACER_ENDPOINT | string |
-| tracer-insecure | PERMIFY_TRACER_INSECURE | boolean |
-
-
-
-#### Definition
-
-A consistent hashing ring ensures data distribution that minimizes reorganization when nodes are added or removed, improving scalability and performance in distributed systems."
-
-#### Structure
-
-```
-├── distributed
-| ├── enabled
-| ├── address
-| ├── port
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|-------------|---------|--------------------------------------|
-| [x] | enabled | false | switch option for distributed. |
-| [] | address | - | address of the distributed service |
-| [] | port | 5000 | port on which the service is exposed |
-
-
-#### ENV
-
-| Argument | ENV | Type |
-|----------------------|-----------------------------|---------|
-| distributed-enabled | PERMIFY_DISTRIBUTED_ENABLED | boolean |
-| distributed-address | PERMIFY_DISTRIBUTED_ADDRESS | string |
-| distributed-port | PERMIFY_DISTRIBUTED_PORT | string |
-
-
-
-
-[jaeger]: https://www.jaegertracing.io/
-
-[otlp]: https://opentelemetry.io/
-
-[zipkin]: https://zipkin.io/
-
-[signoz]: https://signoz.io/
diff --git a/docs/versioned_docs/version-0.5.x/reference/contextual-tuples.md b/docs/versioned_docs/version-0.5.x/reference/contextual-tuples.md
deleted file mode 100644
index ff3a806b..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/contextual-tuples.md
+++ /dev/null
@@ -1,252 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Context (Dynamic Permissions)
-
-## What is it ?
-
-Contextual tuples are relations that can be dynamically added to permission request operations. When you send these relations along with your requests, they get processed alongside existing relations in the database and will return a result.
-
-You can utilize Contextual Tuples in authorization checks that depend on certain dynamic or contextual data (such as location, time, IP address, etc) that have not been written as traditional Permify relation tuples.
-
-## Use Case
-
-Let's give an example to better understand the usage of Contextual Tuples aka dynamic permissions in access checks.
-
-Consider you're modeling an permission system for an internal application that belongs to an multi regional organization.
-
-### Authorization Model
-
-In that application an employee that belongs to HR department can view details of another employee if:
-
-1. If he/she is an Manager in HR department
-2. Connected via the branch's internal network or through the branch's VPN
-
-As you notice we can model the rule **1.** easily with our existing schema language, which gives ability to define arbitrary relations between users and objects such as manager of HR entity, as follows,
-
-```perm
-entity user {}
-
-entity organization {
-
- relation employee @user
- relation hr_manager @user @organization#employee
-
-}
-```
-
-But to create the `view_employee` permission in the organization entity, we need to consider not only whether the employee is a manager but also check the IP address.
-
-At this point, traditional relation tuples of Permify are insufficient since network address is an dynamic variable that cannot be added as static relations.
-
-So, to incorporate the IP address into our authorization model we will use Contextual Tuples and send dynamic relations values when sending the access check request.
-
-Let's extend our authorization model with adding contextual entities and relations to create the `view_employee` action.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation employee @user
- relation hr_manager @user @organization#employee
-
- relation ip_address_range @ip_address_range
-
- action view_employee = hr_manager and ip_address_range.user
-
-}
-
-entity ip_address_range {
- relation user @user
-}
-```
-
-A quick breakdown we define **type** for contextual variable `ip_address_range` and related them with user. Afterwards call that dynamic entities inside our organization entity and form the `view_employee` permission as follows:
-
-```perm
-action view_employee = hr_manager and ip_address_range.user
-```
-
-### Dynamic Access Check
-
-Since we cannot create relation statically for `ip_address_range` we need to send ip value on runtime, specifically when performing access control check.
-
-So let's say user Ashley trying to view employee X. And lets assume that,
-
-* She has a **manager** relation in HR department with the tuple `organization:1#hr_manager@user:1`
-* She connected to VPN which connected to network 192.158.1.38 - which is Branch's internal network.
-
-
-
-
-```go
-cr, err: = client.Permission.Check(context.Background(), &v1.PermissionCheckRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionCheckRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Permission: "view_employee",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
- Context: *v1.Context {
- Tuples: []*v1.Tuple{
- {
- Entity: &v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "ip_address_range",
- Subject: &v1.Subject {
- Type: "ip_address_range",
- Id: "192.158.1.38",
- },
- },
- {
- Entity: &v1.Entity {
- Type: "ip_address_range",
- Id: "192.158.1.38",
- },
- Relation: "user",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
- },
- },
- }
-
- if (cr.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- // RESULT_ALLOWED
- } else {
- // RESULT_DENIED
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.check({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity: {
- type: "organization",
- id: "1"
- },
- permission: "view_employee",
- subject: {
- type: "user",
- id: "1"
- },
- context: {
- tuples: [
- {
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "ip_address_range",
- subject: {
- type: "ip_address_range",
- id: "192.158.1.38",
- }
- },
- {
- entity: {
- type: "ip_address_range",
- id: "192.158.1.38"
- },
- relation: "user",
- subject: {
- type: "user",
- id: "1",
- }
- }
- ]
- }
-}).then((response) => {
- if (response.can === PermissionCheckResponse_Result.RESULT_ALLOWED) {
- console.log("RESULT_ALLOWED")
- } else {
- console.log("RESULT_DENIED")
- }
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/check' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view_employee",
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
- "context": {
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "ip_address_range",
- "subject": {
- "type": "ip_address_range",
- "id": "192.158.1.38"
- }
- },
- {
- "entity": {
- "type": "ip_address_range",
- "id": "192.158.1.38"
- },
- "relation": "user",
- "subject": {
- "type": "user",
- "id": "1"
- }
- }
- ]
- }
-}'
-```
-
-
-
-
-A quick note,
-
-When you use contextual tuples, the cache system will not be operational. This is because the cache system is written along with snapshots and if contextual tuples are written, using the cache would lead to incorrect results.
-
-Hence, to prevent this, the use of the cache is blocked at the time of the request. See more on the section [Permify Cache Mechanisims](./cache.md)
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.5.x/reference/glossary.md b/docs/versioned_docs/version-0.5.x/reference/glossary.md
deleted file mode 100644
index ab02007e..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/glossary.md
+++ /dev/null
@@ -1,45 +0,0 @@
----
-sidebar_position: 1
----
-
-# Glossary
-
-This section explains the basic concepts that commonly mentioned in Permify, as well as in this document. You can find the whole context on right menu.
-
-## Google Zanzibar (or just Zanzibar)
-
-[Google Zanzibar] is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps.
-
-Google published Zanzibar back in 2019, and in a short time it gained attention quickly. In fact some big tech companies started to shift their legacy authorization structure to Zanzibar style systems. Additionaly, Zanzibar based solutions increased over the time. All disclosure; [Permify] is an authorization system based on Zanzibar.
-
-For more about Zanzibar check our blog post, [Google Zanzibar In A Nutshell]
-
-[Google Zanzibar In A Nutshell]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-[Google Zanzibar]: https://research.google/pubs/pub48190/
-[Permify]: https://permify.co/
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it, we called it Permify Schema. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager etc. You can define your entities, relations between them and access control decisions with using Permify Schema.
-
-It includes set-algebraic operators such as inter- section and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-## Relational Tuples
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. The simplest form of relational tuple structured as `entity # relation @ user` and each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-## Permission Database
-
-Permify stores your relational tuples (authorization data) in a database you prefer. You can configure it when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-## Relationship Based Access Control (ReBAC)
-
-ReBAC is an access control model that defines permissions based on the relationships between entities and subjects of your system. Although ReBAC is best known for social networks because its core concept is about the network of relations, it can be applied beyond that.
-
-Check out [Relationship Based Access Control](https://permify.co/post/relationship-based-access-control-rebac/) post learn more about ReBAC and its common usage.
-
-## Domain Specific Language (DSL)
-
-Domain Specific Language is a language that specialized to a particular application domain. Permify has its DSL basically an authorization language which you can model and structure your authorization with it. We called it Permify Schema.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/reference/snap-tokens.md b/docs/versioned_docs/version-0.5.x/reference/snap-tokens.md
deleted file mode 100644
index 8f1a2178..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/snap-tokens.md
+++ /dev/null
@@ -1,53 +0,0 @@
-
-# Snap Tokens & Zookies
-
-A Snap Token is a token that consists of an encoded timestamp, which is used to ensure fresh results in access control checks.
-
-## Why you should use Snap Tokens ?
-
-Basically, you should use snap tokens both for consistency and performance. The main goal of Permify is to provide an authorization system that ensures excellent performance that can handle millions of requests from different environments while ensuring data consistency.
-
-Performance standards can be achievable with caching. In Permify, the cache mechanism eliminates re-computing of access control checks that once occurred, unless any relationships of resources don't change.
-
-Still, all caches suffer from the risk of becoming stale. If some schema update happens, or relations change then all of the caches should be updated according to it to prevent false positive or false negative results.
-
-Permify avoids this problem with an approach of snapshot reads. Simply, it ensures that access control is evaluated at a consistent point in time to prevent inconsistency.
-
-To achieve this, we developed tokens called Snap Tokens that consist of a timestamp that is compared in access checks to ensure that the snapshot of the access control is at least as fresh as the resource timestamp - basically its stored snap token.
-
-## How to use Snap Tokens
-
-Snap Tokens used in endpoints to represent the snapshot and get fresh results of the API's. It mainly used in [Write API] and [Check API].
-
-The general workflow for using snap token is getting the snap token from the reponse of Write API request - basically when writing a relational tuple - then mapped it with the resource. One way of doing that is storing snap token in the additional column in your relational database.
-
-Then this snap token can be used in endpoints. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-```json
-{
- "schema_version": "ce8siqtmmud16etrelag",
- "snap_token": "gp/twGSvLBc=",
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "edit",
- "subject": {
- "type": "user",
- "id": "1",
- },
-}
-```
-
-[Write API]: ../../api-overview/data/write-data/
-[Check API]: ../../api-overview/permission/check-api
-
-#### All endpoints that used snap token
-
-- [Write API](../../api-overview/data/write-data/)
-- [Expand API](../../api-overview/permission/expand-api)
-
-
-## More on Cache Mechanism
-
-Permify implements several cache mecnanisims in order to achieve low latency in scaled distributed systems. See more on the section [Cache Mechanisims](./cache.md)
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/reference/tracing.md b/docs/versioned_docs/version-0.5.x/reference/tracing.md
deleted file mode 100644
index 12810526..00000000
--- a/docs/versioned_docs/version-0.5.x/reference/tracing.md
+++ /dev/null
@@ -1,55 +0,0 @@
-
-# Tracing Tools
-
-Permify has integrations with some of popular tracing tools to analyze performance and behavior of your authorization. These are:
-
-- [Jaeger](https://www.jaegertracing.io/)
-- [OpenTelemetry](https://opentelemetry.io/)
-- [Signoz](https://signoz.io/)
-- [Zipkin](https://zipkin.io/)
-
-## Usage
-
-### Set Up
-
-Adding one of these tracing tools to your authorization system is quite simple, you just need to define it in the Permify configuration file as **tracer**.
-
-```yaml
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-```
-
-- ***exporter***: enter the tool name that you want to use. `jaeger` , `otlp`, `signoz`, and `zipkin`.
-- ***endpoint***: export url for tracing data.
-- ***disabled***: switch option for tracing.
-- ***insecure***: configures the exporter to connect to the collcetor using HTTP instead of HTTPS. This configuration is relevant only for `signoz` and `otlp`.
-
-**Example YAML configuration file**
-
-```yaml
-app:
- name: ‘permify’
-http:
- port: 3476
-logger:
- log_level: ‘debug’
- rollbar_env: ‘permify’
-tracer:
- exporter: 'zipkin'
- endpoint: 'http://172.17.0.4:9411/api/v2/spans'
- disabled: false
-database:
- write:
- connection: 'postgres'
- database: 'morf-health-demo'
- uri: 'postgres://postgres:SphU4Uf3QXNntT@permify.us-east-1.rds.amazonaws.com:5432'
- pool_max: 2
-```
-
-After running Permify in your server, you should run Zipkin as well. If you're using docker here is the docker pull request for Zipkin:
-
-```
-docker run -d -p 9411:9411 openzipkin/zipkin
-```
diff --git a/docs/versioned_docs/version-0.5.x/use-cases.md b/docs/versioned_docs/version-0.5.x/use-cases.md
deleted file mode 100644
index 6fae082c..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases.md
+++ /dev/null
@@ -1,20 +0,0 @@
----
-id: use-cases
-title: Common Use Cases
-slug: /use-cases
----
-
-# Common Use Cases
-
-Common modeling patterns and uses cases we have seen so far from the users from small startups with simple RBAC to multi-regional enterprises that run tens of Permify instances with deeply nested relationships.
-
-:::success Missing a specific use case?
-No problem, let's discuss it together! just open an [issue](https://github.com/Permify/permify/issues) about it or join our conversation at [discord](https://discord.gg/n6KfzYxhPp)!
-:::
-
-```mdx-code-block
-import {CaseList} from '@site/src/components/Case';
-import list from './use-cases/_list.json';
-
-
-```
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/_category_.json b/docs/versioned_docs/version-0.5.x/use-cases/_category_.json
deleted file mode 100644
index 9f9db2d4..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Common Use Cases",
- "position": 8,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/_list.json b/docs/versioned_docs/version-0.5.x/use-cases/_list.json
deleted file mode 100644
index 7b6e7fb1..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/_list.json
+++ /dev/null
@@ -1,32 +0,0 @@
-[
- {
- "id": 1,
- "title": "Role Based Access Control (RBAC)",
- "description": "Want to implement role to your application ? Define an entity and manage your roles throught your applications.",
- "link": "./simple-rbac"
- },
- {
- "id": 2,
- "title": "Attribute Based Access Control (ABAC)",
- "description": "Grant access what based on specific characteristics or attributes.",
- "link": "./abac"
- },
- {
- "id": 3,
- "title": "Relationship Based Access Control (ReBAC)",
- "description": "Define permissions based on the relationships between resources and subjects in your system",
- "link": "./rebac"
- },
- {
- "id": 4,
- "title": "Custom Roles",
- "description": "Assign specific permissions to users based on the custom roles that they are assigned within the system.",
- "link": "./custom-roles"
- },
- {
- "id": 5,
- "title": "Multi Tenancy",
- "description": "Create custom authorization schema and relation tuples for the different tenants and manage them in a single place.",
- "link": "./multi-tenancy"
- }
-]
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/abac.md b/docs/versioned_docs/version-0.5.x/use-cases/abac.md
deleted file mode 100644
index a4acee33..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/abac.md
+++ /dev/null
@@ -1,590 +0,0 @@
-# Attribute Based Access Control (Beta)
-
-This page explains the design approach of Permify's ABAC support as well as demonstrates how to create and use attribute based permissions in Permify.
-
-:::info
-You can find Permify's support for ABAC in our [beta release](https://github.com/Permify/permify/pkgs/container/permify-beta) and explore the active [API documentation](https://permify.github.io/permify-swagger/) for the ***beta*** version.
-
-We are eager to hear your thoughts and looking forward to your feedback!
-:::
-
-# What is Attribute Based Access Control (ABAC)?
-
-Attribute-Based Access Control (ABAC) is like a security guard that decides who gets to access what based on specific characteristics or "attributes".
-
-These attributes can be associated with users, resources, or the environment, and their values can influence the outcome of an access request.
-
-Let’s make an analogy, it’s the best way to understand complex ideas.
-
-Think about an amusement park, and there are 3 different rides. In order to access each ride, you need to have different qualities. For example:
-
-1. ride one you need to be over 6ft tall.
-2. ride two you need to be under 200lbs.
-3. ride three you need to be between 12 - 18 years old.
-
-Similar to this ABAC checks certain qualities that you have defined on users, resources, or the environment.
-
-# Why Would Need ABAC?
-
-It’s obvious but the simple answer is “use cases”… Sometimes, using ReBAC and RBAC isn't the best fit for the job. It's like using winter tires on a hot desert road, or summer tires in a snowstorm - they're just not the right tools for the conditions.
-
-1. **Geographically Restricted:** Think of ABAC like a bouncer at a club who only lets in people from certain towns. For example, a movie streaming service might only show certain movies in certain countries because of rules about who can watch what and where.
-2. **Time-Based:** ABAC can also act like a parent setting rules about when you can use the computer. For example, a system might only let you do certain things during office hours.
-3. **Compliance with Privacy Regulations:** ABAC can help follow rules about privacy. For example, a hospital system might need to limit who can see a patient's data based on the patient's permission, why they want to see it, and who the person is.
-4. **Limit Range:** ABAC can help you create a rules defining a number limit or range. For instance, a banking system might have limits for wiring or withdrawing money.
-5. **Device Information:** ABAC can control access based on attributes of the device, such as the device type, operating system version, or whether the device has the latest security patches.
-
-As you can see ABAC has a more contextual approach. You can define access rights regarding context around subjects and objects in an application.
-
-# Introducing New Key Elements
-
-To support ABAC in Permify, we've added two main components into our DSL: attributes and rules.
-
-## Attribute
-
-Attributes are used to define properties for entities in specific data types. For instance, an attribute could be an IP range associated with an organization, defined as a string array:
-
-```sql
-attribute ip_range string[]
-```
-
-There are different types of attributes you can use;
-
-### Boolean
-
-For attributes that represent a binary choice or state, such as a yes/no question, the `Boolean` data type is an excellent choice.
-
-```go
-entity post {
- attribute is_public boolean
-
- permission view = is_public
-}
-```
-
-
-
-### String
-
-String can be used as an attribute data type in a variety of scenarios where text-based information is needed to make access control decisions. Here are a few examples:
-
-- **Location:** If you need to control access based on geographical location, you might have a location attribute (e.g., "USA", "EU", "Asia") stored as a string.
-- **Device Type**: If access control decisions need to consider the type of device being used, a device type attribute (e.g., "mobile", "desktop", "tablet") could be stored as a string.
-- **Time Zone**: If access needs to be controlled based on time zones, a time zone attribute (e.g., "EST", "PST", "GMT") could be stored as a string.
-- **Day of the Week:** In a scenario where access to certain resources is determined by the day of the week, the string data type can be used to represent these days (e.g., "Monday", "Tuesday", etc.) as attributes!
-
-```sql
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute location string[]
-
- permission view = check_location(request.current_location, location) or admin
-}
-
-rule check_location(current_location string, location string[]) {
- current_location in location
-}
-```
-
-
-
-### Integer
-
-Integer can be used as an attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
-- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
-- **Resource Size or Length:** If access to resources is controlled based on their size or length (like a document's length or a file's size), these can be stored as integer attributes.
-- **Version Number:** If access control decisions need to consider the version number of a resource (like a software version or a document revision), these can be stored as integer attributes.
-
-```jsx
-entity content {
- permission view = check_age(request.age)
-}
-
-rule check_age(age integer) {
- age >= 18
-}
-```
-
-
-
-### Double
-
-Double can be used as an attribute data type in several scenarios where precise numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Usage Limit:** If a user has a usage limit (like the amount of storage they can use or the amount of data they can download), and this limit needs to be represented with decimal precision, it can be stored as a double attribute.
-- **Transaction Amount:** In a financial system, if access control decisions need to consider the amount of a transaction, and this amount needs to be represented with decimal precision (like $100.50), these amounts can be stored as double attributes.
-- **User Rating:** If access control decisions need to consider a user's rating (like a rating out of 5 with decimal points, such as 4.7), these ratings can be stored as double attributes.
-- **Geolocation:** If access control decisions need to consider precise geographical coordinates (like latitude and longitude, which are often represented with decimal points), these coordinates can be stored as double attributes.
-
-```sql
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-
-
-## Rule
-
-Rules are structures that allow you to write specific conditions for the model. They accept parameters and are based on conditions. For example, a rule could be used to check if a given IP address falls within a specified IP range:
-
-```sql
-rule check_ip_range(ip string, ip_range string[]) {
- ip in ip_range
-}
-```
-
-## Evaluation
-
-**Model**
-
-```sql
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute ip_range string[]
-
- permission view = check_ip_range(request.ip_address, ip_range) or admin
-}
-
-rule check_ip_range(ip_address string, ip_range string[]) {
- ip in ip_range
-}
-```
-
-In this case, the part written as 'context' refers to the context within the request. Any type of data can be added from within the request and can be called within the model.
-
-For instance,
-
-```sql
-...
-"context": {
- "ip_address": "187.182.51.206",
- "day_of_week": "monday"
-}
-...
-```
-
-**Relationships**
-
-- organization:1#admin@user:1
-
-**Attributes**
-
-- organization:1$ip_range|string[]:[‘187.182.51.206’, ‘250.89.38.115’]
-
-**Check request**
-
-```sql
-{
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "permission": "view",
- "subject" : {
- "type": "user",
- "id": "1"
- },
- "context": {
- "ip_address": "187.182.51.206"
- }
-}
-```
-
-**Check Evolution Sub Queries Organization View**
-→ organization:1$check_ip_range(context.ip_address,ip_range) → true
-→ organization:1#admin@user:1 → true
-
-**Cache Mechanism**
-The cache mechanism works by hashing the snapshot of the database, schema version, and sub-queries as keys and adding their results, so it will operate in the same way in calls as in relationships. For example,
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_organization:1#admin@user:1 → true
-- check_{snapshot}_{schema_version}_{context}_organization:1$check_ip_range(ip_range) → true
-
-## Some Use Cases
-
-### Example of Public/Private Repository
-
-In this example, **`is_public`** is defined as a boolean attribute. If an attribute is a boolean, it can be directly used without the need for a rule. This is only applicable for boolean types.
-
-```sql
-entity user {}
-
-entity post {
-
- relation owner @user
-
- attribute is_public boolean
-
- permission view = is_public or owner
- permission edit = owner
-}
-```
-
-In this context, if the **`is_public`** attribute of the repository is set to true, everyone can view it. If it's not public (i.e., **`is_public`** is false), only the owner, in this case **`user:1`**, can view it.
-
-The permissions in this model are defined as such:
-
-**`permission view = is_public or owner`**
-
-This means that the 'view' permission is granted if either the repository is public (**`is_public`** is true) or if the current user is the owner of the repository.
-
-**relationships:**
-
-- post:1#owner@user:1
-
-**attributes:**
-
-- post:1$is_public|boolean:true
-
-**Check Evolution Sub Queries Post View**
-→ post:1#is_public → true
-→ post:1#admin@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_post:1$is_public → true
-- check_{snapshot}_{schema_version}_{context}_post:1#admin@user:1 → true
-
-### Example of Weekday
-
-In this example, to be able to view the repository it must not be a weekend, and the user must be a member of the organization.
-
-```sql
-entity user {}
-
-entity organization {
-
- relation member @user
-
- permission view = is_weekday(request.day_of_week) and member
-}
-
-entity repository {
-
- relation organization @organization
-
- permission view = organization.view
-}
-
-rule is_weekday(day_of_week string) {
- day_of_week != 'saturday' && day_of_week != 'sunday'
-}
-```
-
-The permissions in this model state that to 'view' the repository, the user must fulfill two conditions: the current day (according to the context data **`day_of_week`**) must not be a weekend (determined by the **`is_weekday`** rule), and the user must be a member of the organization that owns the repository.
-
-**Relationships:**
-
-- organization:1#member@user:1
-
-**Check Evolution Sub Queries Organization View**
-→ organization:1$is_weekday(context.day_of_week) → true
-→ organization:1#member@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_organization:1$is_weekday(context.day_of_week) → true
-- check_{snapshot}_{schema_version}_{context}_post:1#member@user:1 → true
-
-### Example of Banking System
-
-This model represents a banking system with two entities: **`user`** and **`account`**.
-
-1. **`user`**: Represents a customer of the bank.
-2. **`account`**: Represents a bank account that has an **`owner`** (which is a **`user`**), and a **`balance`** (amount of money in the account).
-
-```sql
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-**The check_balance rule:** This rule verifies if the withdrawal amount is less than or equal to the account's balance and doesn't exceed 5000 (the maximum amount allowed for a withdrawal). It accepts two parameters, the withdrawal amount (amount) and the account's current balance (balance).
-**The owner check:** This condition checks if the person requesting the withdrawal is the owner of the account.
-
-Both of these conditions need to be true for the **`withdraw`** permission to be granted. In other words, a user can withdraw money from an account only if they are the owner of that account, and the amount they want to withdraw is within the account balance and doesn't exceed 5000.
-
-**Relationships**
-
-- account:1#owner@user:1
-
-**Attributes**
-
-- account:1$balance|double:4000
-
-**Check Evolution Sub Queries For Account Withdraw**
-→ account:1$check_balance(context.amount,balance) → true
-→ account:1#owner@user:1 → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_account:1$check_balance(context.amount,balance) → true
-- check_{snapshot}_{schema_version}_{context}_account:1#owner@user:1 → true
-
-### Hierarchical Usage
-
-In this model:
-
-1. **`employee`**: Represents an individual worker. It has no specific attributes or relations in this case.
-2. **`organization`**: Represents an entire organization, which has a **`founding_year`** attribute. The **`view`** permission is granted if the **`check_founding_year`** rule (which checks if the organization was founded after 2000) returns true.
-3. **`department`**: Represents a department within the organization. It has a **`budget`** attribute and a relation to its parent **`organization`**. The **`view`** permission is granted if the department's budget is more than 10,000 (checked by the **`check_budget`** rule) and if the **`organization.view`** permission is true.
-
-Note: In this model, permissions can refer to higher-level permissions (like **`organization.view`**). However, you cannot use the attribute of a relation in this way. For example, you cannot directly reference **`organization.founding_year`** in a permission expression. Permissions can depend on permissions in a related entity, but not directly on the related entity's attributes.
-
-```sql
-entity employee {}
-
-entity organization {
- attribute founding_year integer
-
- permission view = check_founding_year(founding_year)
-}
-
-entity department {
- relation organization @organization
- attribute budget double
-
- permission view = check_budget(budget) and organization.view
-}
-
-rule check_founding_year(founding_year integer) {
- founding_year > 2000
-}
-
-rule check_budget(budget double) {
- budget > 10000
-}
-```
-
-**Relationships**
-
-- department:1#organization@organization:1
-- department:1#organization@organization:2
-
-**Attributes**
-
-- department:1$budget|double:20000
-- organization:1$organization|integer:2021
-
-**Check Evolution Sub Queries For Department View**
-→ department:1$check_budget(budget) → true
-→ department:1#organization@user:1 → true
- → organization:2$check_founding_year(founding_year) → false
- → organization:1$check_founding_year(founding_year) → true
-
-**Request keys before hash**
-
-- check_{snapshot}_{schema_version}_{context}_department:1$check_budget(budget) → true
-- check_{snapshot}_{schema_version}_{context}_organization:2$check_founding_year(founding_year) → false
-- check_{snapshot}_{schema_version}_{context}_organization:1$check_founding_year(founding_year) → true
-
-## How To Use Demo
-
-**Install Permify nightly release**
-
-```yaml
-docker pull **ghcr.io/permify/permify-beta:latest**
-```
-
-**New Validation Yaml Structure**
-
-```yaml
-schema: >-
- {string schema}
-
-relationships:
- - entity_name:entity_id#relation@subject_type:subject_id
-
-attributes:
- - entity_name:entity_id#attribute@attribute_type:attribute_value
-
-scenarios:
- - name: "name"
- description: "description"
- checks:
- - entity: "entity_name:entity_id"
- subject: "subject_name:subject_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result
- entity_filters:
- - entity_type: "entity_name"
- subject: "subject_name:subject_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result_array
- subject_filters:
- - subject_reference: "subject_name"
- entity: "entity_name:entity_id"
- context:
- tuples: []
- attributes: []
- data:
- key: {value}
- assertions:
- permission: result_array
-```
-
-**Note:** The 'data' field within the 'context' can be assigned a desired value as a key-value pair. Later, this value can be retrieved within the model using 'request.key'.
-
-**Example in validation file:**
-
-```yaml
-context:
- tuples: []
- attributes: []
- data:
- day_of_week: "saturday"
-```
-
-This YAML snippet specifies a validation context with no tuples or attributes, and a data field indicating the day of the week is Saturday.
-
-**Example in model**
-
-```yaml
-permission delete = is_weekday(request.day_of_week)
-```
-
-In the model, a **`delete`** permission rule is set. It calls the function **`is_weekday`** with the value of **`day_of_week`** from the context. If **`is_weekday("saturday")`** is true, the delete permission is granted.
-
-**Create Validation File**
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation member @user
-
- attribute credit integer
-
- permission view = check_credit(credit) and member
- }
-
- entity repository {
-
- relation organization @organization
-
- attribute is_public boolean
-
- permission view = is_public
- permission edit = organization.view
- permission delete = is_weekday(request.day_of_week)
- }
-
- rule check_credit(credit integer) {
- credit > 5000
- }
-
- rule is_weekday(day_of_week string) {
- day_of_week != 'saturday' && day_of_week != 'sunday'
- }
-
-relationships:
- - organization:1#member@user:1
- - repository:1#organization@organization:1
-
-attributes:
- - organization:1$credit|integer:6000
- - repository:1$is_public|boolean:true
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "repository:1"
- subject: "user:1"
- context:
- assertions:
- view: true
- - entity: "repository:1"
- subject: "user:1"
- context:
- tuples: []
- attributes: []
- data:
- day_of_week: "saturday"
- assertions:
- view: true
- delete: false
- - entity: "organization:1"
- subject: "user:1"
- context:
- assertions:
- view: true
- entity_filters:
- - entity_type: "repository"
- subject: "user:1"
- context:
- assertions:
- view : ["1"]
- subject_filters:
- - subject_reference: "user"
- entity: "repository:1"
- context:
- assertions:
- view : ["1"]
- edit : ["1"]
-```
-
-**Run validation command**
-
-```yaml
-docker run -v {your_config_folder}:/config **ghcr.io/permify/permify-beta:latest validate /config/validation.yaml**
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/custom-roles.md b/docs/versioned_docs/version-0.5.x/use-cases/custom-roles.md
deleted file mode 100644
index 4ddf1658..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/custom-roles.md
+++ /dev/null
@@ -1,74 +0,0 @@
-
-# Custom Roles
-
-This document highlights a solution for custom roles with the [Permify Schema]. In this tutorial, we will create custom **admin** and **member** roles in a project. Then set the permissions of these roles according to their capabilities on the dashboard and tasks.
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity role {
- relation assignee @user
-}
-
-entity dashboard {
- relation view @role#assignee
- relation edit @role#assignee
-}
-
-entity task {
- relation view @role#assignee
- relation edit @role#assignee
-}
-```
-
-This schema encompasses several crucial elements to structure a custom role-based access control system. The role entity serves as a particularly important component, as it enables the creation of multiple custom roles. These roles may vary according to the needs of the application and could include roles like **admin**, **editor**, or **member**, among others.
-
-Once these custom roles have been established, they can be assigned to other entities in the system. Specifically, in this schema, these roles are attached to the dashboard and task entities. Each of these entities, dashboard and task, has pre-defined permissions associated with them. These permissions, defined within the schema or model, could represent various operations such as **view**, **edit**, and so forth.
-
-With this setup, it's possible to map these pre-defined permissions of the dashboard and task entities to the custom roles that have been created. This implies that specific permissions, for instance, **view** and **edit** for a dashboard or a task, could be assigned to a particular custom role.
-
-Based on this model, the example relationships are as follows. With these relationships, custom roles such as **admin** and **member** have been created.
-
-## Relationships
-
-dashboard:project-progress#view@role:admin#assignee
-
-dashboard:project-progress#view@role:member#assignee
-
-dashboard:project-progress#edit@role:admin#assignee
-
-task:website-design-review#view@role:admin#assignee
-
-task:website-design-review#view@role:member#assignee
-
-task:website-design-review#edit@role:admin#assignee
-
-Together with these relationships and the model, a view has been created for the **project-progress** dashboard and the **website-design-review** task as shown in the table below.
-
-| permission | admin | member |
-|--------------------|-------|---------|
-| **dashboard:view** | ✅ | ✅ |
-| **dashboard:edit** | ✅ | ⛔ |
-| **task:view** | ✅ | ✅ |
-| **task:edit** | ✅ | ⛔ |
-
-
-Subsequently, you can make authorization decisions by assigning these custom roles to the users that you have created.
-
-role:member#assignee@user:1
-
-When we write these relationship, the final situation will be as follows.
-
-`Can user:1 view dashboard:project-progress?` gives **Allow** result since the `user:1` is assignee of `role:member` and `role:member` has `dashboard:project-progress#view` permission.
-
-`Can user:1 view task:website-design-review?` gives **Denied** result since the `user:1` is not assignee of `role:admin`.
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
-
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/rebac.md b/docs/versioned_docs/version-0.5.x/use-cases/rebac.md
deleted file mode 100644
index 561b500e..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/rebac.md
+++ /dev/null
@@ -1,424 +0,0 @@
-
-# Relationship Based Access Control
-
-Permify was designed and structured as a true [Relationship Based Access Control(ReBAC)](https://permify.co/post/relationship-based-access-control-rebac/) solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-
-Here are some common use cases where you can benefit from using ReBAC models in your Permify Schema.
-
-- [Protecting Organizational-Wide Resources](#protecting-organizational-wide-resources)
-- [Deeply Nested Hierarchies](#deeply-nested-hierarchies)
-- [User Groups & Team Permissions](#user-groups--team-permissions)
-
-## Protecting Organizational-Wide Resources
-
-This example demonstrates grouping the users by organization and giving them access to organizational-wide resources.
-
-In this use case we'll follow a simplified version of Github's access control that shows how to model basic repository push, read and delete permissions with our authorization language DSL, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents user of this repository
- relation owner @user
-
- // permissions
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-### Schema Deconstruction
-
-#### Entities
-
-This schema consists of 3 entities,
-
-- `user`, represents users. This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents organization that user and repositories belongs.
-
-- `repository`, represents a repository in a github.
-
-#### Relations
-
-To define a relation, **relations** need to be created as entity attributes.
-
-##### organization entity
-
-In our schema we defined 2 relations in the organization entity: ``admin`` and ``member``.
-
-```perm
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-``admin`` indicates that the user got an administrative role in that organization and with the same logic ``member`` represents a default user that belongs to that organization.
-
-##### repository entity
-
-Repository entities have 2 relations: ``parent`` and ``owner``. Both of these relations represent actual database relations with other entities rather than a role-based approach similar to the **organization** entity above.
-
-```perm
-entity repository {
-
- relation parent @organization
- relation owner @user
-
-}
-```
-
-The ``parent`` relation represents the parent organization of a repository. And ``owner`` represents the specific user, the repository's owner.
-
-#### Actions
-
-Actions describe what relations, or relation's relation, can do. You can think of actions as entities' permissions. Actions define who can perform a specific action and in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-##### repository actions
-
-In our schema, we examined one of the main functionalities user can make on any GitHub repository. These are pushing to the repo, reading & viewing the repo, and deleting that repo.
-
-We can say only,
-
-- Repository owners can ``push`` to that repo.
-- Repository owners, who have an admin or member role of the parent organization, can ``read``.
-- Repository owners or admins of the parent organization can ``delete`` the repository.
-
-```
-entity repository {
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
- action delete = parent.admin or owner
-
-}
-```
-
-Since `parent` represents the parent organization of a repository. It can reach repositories parent organization relations with comma. So,
-
-- ``parent.admin``
-indicates admin role on organization
-
-- ``parent.member``
-indicates member of that organization.
-
-### Sample Relational Tuples
-
-organization:2#admin@user:daniel
-
-organization:54#member@user:ege
-
-organization:12#member@user:jack
-
-repository:34#parent@organization:54
-
-repository:68#owner@user:12
-
-repository:12#owner@user:46
-
-
-.
-.
-.
-
-For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-For instance, you can define that a user has certain permissions because of their relation to other entities.
-
-An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group. This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-## Deeply Nested Hierarchies
-
-This use case shows solving deeply nested hierarchies with the [Permify Schema].
-
-We have a unique **action** usage for nested hierarchies, where parent and child entities can share permissions between them. Let's follow the below team project authorization model to examine this case.
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organization user types
- relation admin @user
-}
-
-entity team {
-
- //refers to the organization that a team belongs to
- relation org @organization
-
- // Only the organization administrator can edit
- action edit = org.admin
-}
-
-entity project {
-
- //refers to the team that a project belongs to
- relation team @team
-
- // This action is responsible for nested permission inheritance
- // team.edit refers to the edit action on the team entity which we defined above
- // This means that the organization admin, who can edit the team
- // can also edit the project related to the team.
- action edit = team.edit
-}
-```
-
-### Sample Relational Tuples
-
-organization:1#admin@user:1
-
-team:1#org@organization:1#...
-
-project:1#team@team:1#...
-
-Lets assume we created the above [relational tuples]. If we try to enforce `Can user:1 edit project:1?` we will get **Allow** since the `user:1` is an admin of the `organization:1` and `project:1` belongs to `team:1`, which belongs to `organization:1`.
-
-[relational tuples]: ../getting-started/sync-data.md
-
-Let's break down this case,
-
-```perm
-entity project {
-
- relation team @team
-
- action edit = team.edit
-}
-```
-
-In the above `team.edit` points to the **edit** action in the **team** (that the project belongs to). That edit action on the team entity (`action edit = org.admin`) states that only admins of the **organization (which that team belongs to)** can edit. So our project inherits that action and conducts a result accordingly.
-
-If we go back to our question: `Can user:1 edit project:1?` this will give an **Allow** result, because user:1 is an admin in an organization that the projects' parent team belongs to.
-
-## User Groups & Team Permissions
-
-This use case shows how to organize permissions based on groupings of users or resources. In this use case we'll follow a simple project management app with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //organizational roles
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- // represents owner or creator of the team
- relation owner @user
-
- // represents direct member of the team
- relation member @user
-
- // represents the organization that the team belongs to
- relation org @organization
-
- // organization admins or team owners can edit, delete the team details
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- // to invite someone you need to be an organization admin and either an owner or member of this team
- action invite = org.admin and (owner or member)
-
- // only team owners can remove users
- action remove_user = owner
-
-}
-
-entity project {
-
- // represents team and organization that a project belongs to
- relation team @team
- relation org @organization
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-### Schema Deconstruction
-
-#### Entities
-
-This schema consists of 4 entities,
-
-- `user`, represents users. This entity is empty because its only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents an organization that contain teams.
-
-- `team`, represents teams, which belong to an organization.
-
-- `project`, represents projects that belong to teams.
-
-#### Relations
-
-##### organization entity
-
-We can use **relations** to define roles.
-
-The organization entity has 2 relations ``admin`` and ``member`` users. Think of these as organizational-wide roles.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-```
-
-Roles (relations) can be scoped with different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates that each organization has its own roles.
-
-##### team entity
-
-The team entity has its own relations respectively, ``owner``, ``member`` and ``org``
-
-```perm
-entity team {
-
- relation owner @user
- relation member @user
- relation org @organization
-
-}
-```
-
-##### project entity
-
-The project entity has ``team`` and ``org`` relations. Both these relations represent parent relationships with other entities, parent team and parent organization.
-
-```perm
-entity project {
-
- relation team @team
- relation org @organization
-
-}
-```
-
-#### Actions
-
-Actions describe what relations, or relation's relation, can do. You can think of actions as entities' permissions. Actions define who can perform a specific action and in which circumstances.
-
-Permify Schema supports ***and***, ***or*** and ***not*** operators to define actions.
-
-##### team actions
-
-- Only organization ***admin (admin role)*** and ***team owner*** can edit and delete team specific resources.
-
-- Moreover, to invite a colleague to a team you must have an organizational ***admin role*** and either be a ***owner*** or ***member*** of that team.
-
-- To remove users in team you must be an ***owner*** of that team.
-
-And these rules are defined in Permify Schema as:
-
-```perm
-entity team {
-
- action edit = org.admin or owner
- action delete = org.admin or owner
-
- action invite = org.admin and (owner or member)
- action remove_user = owner
-
-}
-```
-
-##### project actions
-
-And here are the project actions. The actions consist of checking access for basic operations such as viewing, editing, or deleting project resources.
-
-```perm
-entity project {
-
- action view = org.admin or team.member
- action edit = org.admin or team.member
- action delete = team.member
-
-}
-```
-
-### Sample Relational Tuples
-
-team:2#member@user:daniel
-
-team:54#owner@user:daniel
-
-organization:12#admin@user:jack
-
-organization:51#member@user:jack
-
-organization:41#member@team:42#member
-
-project:35#team@team:34#....
-
-
-.
-.
-.
-.
-.
-
-
-organization:41#member@team:42#member
-
-**--> represents members of team 42 are also members of organization 41**
-
-project:35#team@team:34#....
-
-**--> represents project 54 is in team 34**
-
-## Need any help on Authorization ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.5.x/use-cases/simple-rbac.md b/docs/versioned_docs/version-0.5.x/use-cases/simple-rbac.md
deleted file mode 100644
index 85d70b6b..00000000
--- a/docs/versioned_docs/version-0.5.x/use-cases/simple-rbac.md
+++ /dev/null
@@ -1,128 +0,0 @@
----
-sidebar_position: 1
----
-
-# Role Based Access Control
-
-Want to implement roles and permissions in your application? Permify fully covers you at that point. The example below shows how to model simple role based access controls for organizational roles and permissions with our authorization language, [Permify Schema].
-
-[Permify Schema]: ../../getting-started/modeling
-
-Before we get started, here's the final schema that we will create in this tutorial.
-
-```perm
-entity user {}
-
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
- //organization files access permissions
- action view_files = admin or manager or (member not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-## Schema Deconstruction
-
-### Entities
-
-This schema consists of 2 entities,
-
-- `user`, represents users (maybe corresponds to employees). This entity is empty because it's only responsible for referencing users.
-
-```perm
- entity user {}
-```
-
-- `organization`, represents the organization the user (employees) belongs. It has several roles and permissions related to the specific resources such as organization files and vendor files.
-
-### Relations
-
-#### organization entity
-
-We can use **relations** to define roles. In this example, we have 4 organization wide roles: admin, manager, member, and agent.
-
-```perm
-entity organization {
-
- //roles
- relation admin @user
- relation member @user
- relation manager @user
- relation agent @user
-
-}
-```
-
-Roles (relations) can be scoped to different kinds of entities. But for simplicity, we follow a multi-tenancy approach, which demonstrates each organization has its own roles.
-
-### Actions
-
-Actions describe what relations, or relation's relation, can do. You can think of actions as entities' permissions. Actions define who can perform a specific action and in which circumstances.
-
-Permify Schema supports ***and***, ***or***, ***and not*** and ***or not*** operators to define actions.
-
-#### organization actions
-
-In our schema, we define several actions for controlling access permissions on organization files and organization vendor's files.
-
-```perm
-entity organization {
-
- //organization files access permissions
- action view_files = admin or manager or (member not agent)
- action edit_files = admin or manager
- action delete_file = admin
-
- //vendor files access permissions
- action view_vendor_files = admin or manager or agent
- action edit_vendor_files = admin or agent
- action delete_vendor_file = agent
-
-}
-```
-
-let's take a look at some of the actions:
-
-- ``action edit_files = admin or manager``
-indicates that only the admin or manager has permission to edit files in the organization.
-
-- ``action view_files = admin or manager or (member not agent)``
-indicates that the admin, manager, or members (without having the agent role) can view organization files.
-
-
-
-## Example Relational Tuples for this case
-
-organization:2#admin@user:daniel
-
-organization:5#member@user:ashley
-
-organization:17#manager@user:mert
-
-organization:21#agent@user:ege
-
-.
-.
-.
-
-For more details about how relational tuples are created and stored in your preferred database, see [Relational Tuples].
-
-[Relational Tuples]: ../getting-started/sync-data.md
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert). Alternatively you can join our [discord community](https://discord.com/invite/MJbUjwskdH) to discuss.
-
diff --git a/docs/versioned_docs/version-0.6.x/api-overview.md b/docs/versioned_docs/version-0.6.x/api-overview.md
deleted file mode 100644
index 931d562b..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview.md
+++ /dev/null
@@ -1,93 +0,0 @@
----
-id: api-overview
-title: API Overview
-sidebar_label: Using the API
-slug: /api-overview
----
-
-# Overview
-
-Permify API provides various functionalities around authorization such as performing access checks, reading and writing relation tuples, expanding your permissions (schema actions), and more.
-
-We structured Permify API in 4 core parts:
-
-- [PermissionService]: Consists access control requests and options.
-- [DataService]: Authorization data operations such as creating, deleting and reading relational tuples and attributes.
-- [BundleService]: Facilitates the creation and execution of bundles that perform predefined operations, establishing relationships and attributes based on provided arguments.
-- [SchemaService]: Modeling and Permify Schema related functionalities including configuration and auditing.
-- [TenancyService]: Consists tenant operations such as creating, deleting and listing.
-
-Permify exposes its APIs via both [gRPC](https://buf.build/permifyco/permify/docs/main:base.v1) - with [go] and [nodeJS] client options - and [REST](https://restfulapi.net/).
-
-[PermissionService]: ./permission
-[DataService]: ./data
-[BundleService]: ./bundle
-[SchemaService]: ./schema
-[TenancyService]: ./tenancy
-[go]: https://github.com/Permify/permify-go
-[nodeJS]: https://github.com/Permify/permify-node
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-:::info Integration with a Service Mesh
-Our software does not include built-in support for service meshes (eg. Istio).
-
-However, since it communicates using standard protocols like gRPC and HTTP, it is compatible with Istio and similar service meshes. Users will need to configure their service mesh setup manually to manage traffic for our software within their deployment environment.
-:::
-
-## Core Paths
-
-- Configure your authorization model with [Schema Write](./api-overview/schema/write-schema.md)
-- Write relational tuples with [Write Data](./api-overview/data/write-data.md)
-- Read relation tuples and filter them with [Read Relationships](./api-overview/data/read-relationships.md)
-- Check access with [Check API](./api-overview/permission/check-api.md)
-- Check entities permissions with [Lookup Entity](./api-overview/permission/lookup-entity.md)
-- Check subject permissions with [Lookup Subject](./api-overview/permission/lookup-subject.md)
-- Delete relation tuples with [Delete Tuple](./api-overview/data/delete-data.md)
-- Expand schema actions with [Expand API](./api-overview/permission/expand-api.md)
-- Watch changes in the relation tuples in real-time with [Watch API](./api-overview/watch/watch-changes.md)
-
-## Authentication
-
-You can secure APIs with our authentication methods; **Open ID Connect** or **Pre Shared Keys**. They can be configurable with flags or using configuration yaml file. See more details how to enable authentication from [Configuration Options](../reference/configuration)
-
-To access the endpoints after enabling authentication, it's necessary to provide a Bearer Token for identification. If your using golang or nodeJs client library, an authentication token can be provided via interceptors. You can find details in the clients' documentation.
-
-## Availability of the Service
-
-For our dedicated instance service we do have **99.9%** level of availability and to assure this level of availability, we employ several strategies:
-
-1. **Redundancy:** We deploy our system across multiple Availability Zones in a region, ensuring that it remains operational even if one zone experiences issues.
-2. **Load Balancing:** Load balancers are used to distribute traffic across multiple instances of the service, ensuring that no single instance becomes a bottleneck.
-3. **Auto-Scaling:** Our system is capable of scaling automatically based on the incoming load, ensuring that we have sufficient capacity to handle any increase in traffic.
-4. **Data Replication:** Our PostgreSQL database replicates data to ensure its availability even in the event of a single-node failure.
-5. **Backup and Recovery:** Regular backups are maintained, and our system supports a robust recovery strategy in case of significant failures.
-6. **Monitoring & Alerts:** Using tools like Amazon CloudWatch, we monitor the health and performance of our system and can quickly respond to any detected issues.
-
-## Service Credits for Availability Failures
-
-In case of availability failures, Permify's Service Level Agreement (SLA) provides for Service Credits which are applied as a discount on your future bills:
-
-- If uptime is less than 99.95% but above or equal to 99.0%, you get a 10% Service Credit.
-- If uptime is less than 99.0%, you get a 25% Service Credit.
-- If uptime is less than 95.0%, you get a 100% Service Credit.
-
-These credits are your sole remedy for any availability failures under our SLA.
-
-## Request Rate Limits
-
-Default rate limit is set to 100 requests per second. However, users can adjust this based on their specific needs following our [documentation](https://docs.permify.co/docs/reference/configuration). We used [Token bucket](https://en.wikipedia.org/wiki/Token_bucket) algorithm for rate limiting.
-
-## Error Handling
-
-Permify API uses a set of defined error codes to indicate various types of failures or issues.
-Understanding these error codes and their implications is vital for effective error handling and troubleshooting within the Permify API.
-Each error code is designed to provide clear insights into what went wrong and how to resolve it, ensuring a smoother integration and operation of the API in your applications
-Refer to the [Error Codes](https://github.com/Permify/permify/blob/master/proto/base/v1/errors.proto) documentation for detailed descriptions and resolution steps for each error code.
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/_category_.json
deleted file mode 100644
index 5e515400..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Using the API",
- "position": 5,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/bundle/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/bundle/_category_.json
deleted file mode 100644
index d8d37140..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/bundle/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Bundle Service",
- "position": 4,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/bundle/delete-bundle.md b/docs/versioned_docs/version-0.6.x/api-overview/bundle/delete-bundle.md
deleted file mode 100644
index d175eda8..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/bundle/delete-bundle.md
+++ /dev/null
@@ -1,58 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Bundle [Beta]
-
-The "Delete Bundle" API is designed for removing specific data bundles within a multi-tenant application environment. This API facilitates the deletion of a bundle, identified by its unique name, from a designated tenant's environment.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/delete
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.delete)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-
-
-
-
-```go
-rr, err: = client.Bundle.Delete(context.Background(), &v1.BundleDeleteRequest{
- TenantId: "t1",
- Name: "organization_created",
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.delete({
- tenantId: "t1",
- name: "organization_created",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/bundle/read-bundle.md b/docs/versioned_docs/version-0.6.x/api-overview/bundle/read-bundle.md
deleted file mode 100644
index f96a54ce..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/bundle/read-bundle.md
+++ /dev/null
@@ -1,58 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Bundle [Beta]
-
-The "Read Bundle" API is a crucial tool for retrieving details of specific data bundles in a multi-tenant application setup. It is designed to access information about a bundle, uniquely identified by its name, within the specified tenant's environment.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/read
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.read)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-
-
-
-
-```go
-rr, err: = client.Bundle.Read(context.Background(), &v1.BundleReadRequest{
- TenantId: "t1",
- Name: "organization_created",
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.read({
- tenantId: "t1",
- name: "organization_created",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/bundle/write-bundle.md b/docs/versioned_docs/version-0.6.x/api-overview/bundle/write-bundle.md
deleted file mode 100644
index 9ee9d653..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/bundle/write-bundle.md
+++ /dev/null
@@ -1,117 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Bundle [Beta]
-
-The "Write Bundle" API is designed for handling data in a multi-tenant application environment. Its primary function is to write and delete data according to predefined structures. This API allows users to define or update data bundles, each distinguished by a unique name.
-
-## Request
-
-**Path:** POST /v1/tenants/{tenant_id}/bundle/write
-
-[](https://permify.github.io/permify-swagger/#/Bundle/bundle.write)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-| [x] | operations | object | Represent actions that can be performed on data, such as adding or deleting relationships or attributes when certain events occur. |
-| [x] | arguments | string[] | Parameters that will be used in the operations |
-
-
-
-
-```go
-rr, err := client.Bundle.Write(context.Background(), &v1.BundleWriteRequest{
- TenantId: "t1",
- Bundles: []*v1.DataBundle{
- {
- Name: "organization_created",
- Arguments: []string{
- "creatorID",
- "organizationID",
- },
- Operations: []*v1.Operation{
- {
- RelationshipsWrite: []string{
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- },
- AttributesWrite: []string{
- "organization:{{.organizationID}}$public|boolean:false",
- },
- },
- },
- },
- },
-})
-```
-
-
-
-
-
-```javascript
-client.bundle.write({
- tenantId: "t1",
- bundles: [
- {
- name: "organization_created",
- arguments: [
- "creatorID",
- "organizationID",
- ],
- operations: [
- {
- relationships_write: [
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- ],
- attributes_write: [
- "organization:{{.organizationID}}$public|boolean:false",
- ]
- }
- ]
- }
- ]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/bundle/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "bundles": [
- {
- "name": "organization_created"
- "arguments": [
- "creatorID",
- "organizationID"
- ],
- "operations": [
- {
- "relationships_write": [
- "organization:{{.organizationID}}#admin@user:{{.creatorID}}",
- "organization:{{.organizationID}}#manager@user:{{.creatorID}}",
- ],
- "attributes_write": [
- "organization:{{.organizationID}}$public|boolean:false",
- ],
- },
- ],
- },
- ],
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/data/_category_.json
deleted file mode 100644
index 1a2612e1..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Data Service",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/delete-data.md b/docs/versioned_docs/version-0.6.x/api-overview/data/delete-data.md
deleted file mode 100644
index b8d09e33..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/delete-data.md
+++ /dev/null
@@ -1,111 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Data
-
-You can delete any stored relation tuples or attributes with following API
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/tenants/{tenant_id}/data/delete
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.delete)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | tuples_filter | object |filter to delete relational tuples. Contains **entity**, **relation** and **subject**.
-| [x] | attribute_filter | object | filter to delete attributes. Contains **entity** and **attributes**.
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | relation of the given entity |
-| [x] | attribute | string array | attributes to be deleted |
-| [ ] | subject | object | the user or user set. It contains type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.Delete(context.Background(), & v1.DataDeleteRequest {
- TenantId: "t1",
- Metadata: &v1.DataDeleteRequestMetadata {
- SnapToken: ""
- },
- TupleFilter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "admin",
- Subject: &v1.SubjectFilter {
- Type: "user",
- Id: []string {"1"},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.delete({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- tupleFilter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "admin",
- subject: {
- type: "user",
- ids: [
- "1"
- ],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/delete' \
---header 'Content-Type: application/json' \
---data-raw '{
- "tupleFilter": {
- "entity": {
- "type": "organization",
- "ids": [
- "1"
- ]
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "ids": [
- "1"
- ],
- "relation": ""
- }
- },
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/read-attributes.md b/docs/versioned_docs/version-0.6.x/api-overview/data/read-attributes.md
deleted file mode 100644
index 86b4af1b..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/read-attributes.md
+++ /dev/null
@@ -1,95 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Attributes
-
-Read API allows for directly querying the stored graph data to display and filter stored attributes.
-
-## Request
-```javascript
-POST /v1/tenants/{tenant_id}/data/attributes/read
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.attributes.read)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | contains entity type and id of the entity. Example: repository:1”.
-| [x] | attributes | string array | attributes of the given entity |
-
-
-
-
-
-```go
-rr, err: = client.Data.ReadAttributes(context.Background(), & v1.Data.AttributeReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.AttributeReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.AttributeFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Attributes: []string {"private"},
-})
-```
-
-
-
-
-
-```javascript
-client.data.readAttributes({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/attributes/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- attributes: [
- "private"
- ],
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/read-relationships.md b/docs/versioned_docs/version-0.6.x/api-overview/data/read-relationships.md
deleted file mode 100644
index f59a3d57..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/read-relationships.md
+++ /dev/null
@@ -1,106 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Read Relational Tuples
-
-Read API allows for directly querying the stored graph data to display and filter stored relational tuples.
-
-## Request
-```javascript
-POST /v1/tenants/{tenant_id}/data/relationships/read
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.relationships.read)
-
-| Required | Argument | Type | Default | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens) |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1”.
-| [x] | relation | string | - | relation of the given entity |
-| [ ] | subject | object | - | the user or user set. It containes type and id of the subject. ||
-
-
-
-
-```go
-rr, err: = client.Data.ReadRelationships(context.Background(), & v1.Data.RelationshipReadRequest {
- TenantId: "t1",
- Metadata: &v1.Data.RelationshipReadRequestMetadata {
- SnapToken: ""
- },
- Filter: &v1.TupleFilter {
- Entity: &v1.EntityFilter {
- Type: "organization",
- Ids: []string {"1"} ,
- },
- Relation: "member",
- Subject: &v1.SubjectFilter {
- Type: "",
- Id: []string {""},
- Relation: ""
- }}
-})
-```
-
-
-
-
-
-```javascript
-client.data.readRelationships({
- tenantId: "t1",
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/relationships/read' \
---header 'Content-Type: application/json' \
---data-raw '{
- metadata: {
- snap_token: "",
- },
- filter: {
- entity: {
- type: "organization",
- ids: [
- "1"
- ]
- },
- relation: "member",
- subject: {
- type: "",
- ids: [],
- relation: ""
- }
- }
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/run-bundle.md b/docs/versioned_docs/version-0.6.x/api-overview/data/run-bundle.md
deleted file mode 100644
index a86d53ea..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/run-bundle.md
+++ /dev/null
@@ -1,75 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Run Bundle [Beta]
-
-The "Run Bundle" API provides a straightforward way to execute predefined bundles within your application's tenant
-environment. By sending a POST request to this endpoint, you can activate specific functionalities or processes
-encapsulated in a bundle.
-
-## Request
-
-```javascript
- POST /v1/tenants/{tenant_id}/data/run-bundle
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/bundle.run)
-
-| Required | Argument | Type | Description |
-|----------|----------|---------|---------|-------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [x] | name | string | unique name identifying the bundle. |
-| [ ] | arguments | map | parameters for the bundle in key-value format. |
-
-
-
-
-```go
-rr, err: = client.Data.RunBundle(context.Background(), &v1.BundleRunRequest{
- TenantId: "t1",
- Name: "organization_created",
- Arguments: map[string]string{
- "creatorID": "564",
- "organizationID": "789",
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.runBundle({
- tenantId: "t1",
- name: "organization_created",
- arguments: {
- creatorID: "564",
- organizationID: "789",
- }
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/run-bundle' \
---header 'Content-Type: application/json' \
---data-raw '{
- "name": "organization_created",
- "arguments": {
- "creatorID": "564",
- "organizationID": "789",
- }
-}'
-```
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/data/write-data.md b/docs/versioned_docs/version-0.6.x/api-overview/data/write-data.md
deleted file mode 100644
index 67e87027..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/data/write-data.md
+++ /dev/null
@@ -1,477 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Authorization Data
-
-In Permify, attributes and relations between your entities, objects and users represents your authorization data. These data stored as tuples in a [preferred database].
-
-Since these attributes and relations are live instances, meaning they can be affected by specific user actions within the application, they can be created/deleted with a simple Permify API call at runtime.
-
-More specifically, the application client should update preferred database about the changes happening in entities or resources that are related to the authorization structure.
-
-If we consider a document system; when some user joins a group that has edit access on some documents, the application side needs to write relational tuples to keep [preferred database] up-to-date. Besides, each attribute or relationship should be created according to its authorization model, Permify Schema.
-
-Another example: when one a company executive grant admin role to user (lets say with id = 3) on their organization, application side needs to tell that update to Permify in order to reform that as tuples and store in [preferred database].
-
-
-
-[relational tuples]: ../../../getting-started/sync-data
-[preferred database]: ../../../getting-started/sync-data#where-relational-tuples-used
-
-## Write Request
-
-:::info
-You can use the **/v1/tenants/{tenant_id}/data/write** endpoint for both creating **relation tuples** and for creating **attribute data**.
-:::
-
-**Path:**
-```javascript
- POST /v1/tenants/{tenant_id}/data/write
-```
-
-[](https://permify.github.io/permify-swagger/#/Data/data.write)
-
-#### Glossary for parameters & payload objects:
-
-| Required | Argument | Type | Default | Description |
-| -------- | -------------- | ------ | ------- | ----------------------------------------------------------------------------------------------------------------------------------------------------- |
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant in your system) use pre-inserted tenant **t1** for this parameter. |
-| [ ] | schema_version | string | 8 | Version of the schema. |
-| [x] | tuples | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **relation**, and **subject** arguments.|
-| [x] | attributes | array | - | Array of objects that are used to define relationships. Each object contains **entity**, **attribute**, and **value** arguments. |
-| [x] | entity | object | - | Type and id of the entity. Example: "organization:1” |
-| [x] | subject | string | - | User or user set who wants to take the action. |
-| [x] | relation | string | - | Custom relation name. Eg. admin, manager, viewer etc. |
-| [x] | attribute | string | - | Custom attribute name. |
-| [x] | value | object | - | Represents value and type of the attribute data. |
-
-
-### Creating Relational Tuple
-
-Let's create an example relation tuple. If user:3 has been granted an admin role in organization:1, relational tuple `organization:1#admin@user:3` should be created as follows:
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "user",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data
- .write({
- tenantId: "t1",
- metadata: {
- schemaVersion: "",
- },
- tuples: [
- {
- entity: {
- type: "organization",
- id: "1",
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3",
- },
- },
- ],
- })
- .then((response) => {
- // handle response
- });
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-
-### Creating Attribute Data
-
-You can use `attributes` argument to create attribute/attributes with a single API call, similarly creating a `relational tuple`.
-
-Let's say **document:1** is a **private (boolean)** document, that only specific users have view access - `document:1$is_private|boolean:true`.
-
-:::info Attribute Data Syntax
-As you noticed, the attribute tuple syntax differs from the relationship syntax, structured similarly as:
-`entity $ attribute | value`
-:::
-
-
-
-
-```go
-// Convert the wrapped attribute value into Any proto message
-value, err := anypb.New(&v1.BooleanValue{
- Data: true,
-})
-if err != nil {
- // Handle error
-}
-
-cr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{
- TenantId: "t1",,
- Metadata: &v1.DataWriteRequestMetadata{
- SchemaVersion: "",
- },
- Attributes: []*v1.Attribute{
- {
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Attribute: "is_private",
- Value: value,
- },
- },
-})
-```
-
-
-
-
-
-```javascript
-const booleanValue = BooleanValue.fromJSON({ data: true });
-
-const value = Any.fromJSON({
- typeUrl: 'type.googleapis.com/base.v1.BooleanValue',
- value: BooleanValue.encode(booleanValue).finish()
-});
-
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- attributes: [{
- entity: {
- type: "document",
- id: "1"
- },
- attribute: "is_private",
- value: value,
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
-{
- "metadata": {
- "schema_version": ""
- },
- "attributes": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "attribute": "is_private",
- "value": {
- "@type": "type.googleapis.com/base.v1.BooleanValue",
- "data": true
- }
- }
- ]
-}
-}'
-```
-
-
-
-
-:::warning Attribute **value** field
-**value** field is mandatory on attribute data creation.
-
-Here are the available attribute value types:
-
-- **type.googleapis.com/base.v1.StringValue**
-- **type.googleapis.com/base.v1.BooleanValue**
-- **type.googleapis.com/base.v1.IntegerValue**
-- **type.googleapis.com/base.v1.DoubleValue**
-- **type.googleapis.com/base.v1.StringArrayValue**
-- **type.googleapis.com/base.v1.BooleanArrayValue**
-- **type.googleapis.com/base.v1.IntegerArrayValue**
-- **type.googleapis.com/base.v1.DoubleArrayValue**
-:::
-
-#### Creating Attributes and Relations In Single Request
-
-Assume we want to both create relational tuple and attribute within in single request. Specifically we want to create following tuples,
-
-- `document:1#editor@user:1`
-- `document:1$is_private|boolean:true`
-
-
-
-
-
-```go
-// Convert the wrapped attribute value into Any proto message
-value, err := anypb.New(&v1.BooleanValue{
- Data: true,
-})
-if err != nil {
- // Handle error
-}
-
-cr, err := client.Data.Write(context.Background(), &v1.DataWriteRequest{
- TenantId: "t1",,
- Metadata: &v1.DataWriteRequestMetadata{
- SchemaVersion: "",
- },
- Tuples: []*v1.Attribute{
- {
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Relation: "editor",
- Subject: &v1.Subject{
- Type: "user",
- Id: "1",
- Relation: "",
- },
- },
- },
- Attributes: []*v1.Attribute{
- {
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Attribute: "is_private",
- Value: value,
- },
- },
-})
-```
-
-
-
-
-
-```javascript
-const booleanValue = BooleanValue.fromJSON({ data: true });
-
-const value = Any.fromJSON({
- typeUrl: 'type.googleapis.com/base.v1.BooleanValue',
- value: BooleanValue.encode(booleanValue).finish()
-});
-
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "editor",
- subject: {
- type: "user",
- id: "1"
- }
- }],
- attributes: [{
- entity: {
- type: "document",
- id: "1"
- },
- attribute: "is_private",
- value: value,
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
-{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "editor",
- "subject": {
- "type": "user",
- "id": "1"
- }
- }
- ],
- "attributes": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "attribute": "is_private",
- "value": {
- "@type": "type.googleapis.com/base.v1.BooleanValue",
- "data": true
- }
- }
- ]
-}
-}'
-```
-
-
-
-
-## Response
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-You can store that snap token alongside with the resource in your relational database, then use it used in endpoints to get fresh results from the API's. For example it can be used in access control check with sending via `snap_token` field to ensure getting check result as fresh as previous request.
-
-See more details on what is [Snap Tokens](../../reference/snap-tokens) and how its avoiding stale cache.
-
-## Suggested Workflow
-
-The most of the data that should written in Permify also needs to be write or engage with applications database as well. So where and how to write relationships into both applications database and Permify ?
-
-### Two Phase Commit Approach
-
-In a standard relational based databases, the suggested place to write relationships to Permify is sending the write request in database transaction of the client action: such as storing the owner of the document when an user creates a document.
-
-To give more concurrent example of this action, let's take a look at below createDocument function
-
-```go
-func CreateDocuments(db *gorm.DB) error {
-
- tx := db.Begin()
- defer func() {
- if r := recover(); r != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteData(...)
- }
- }()
-
- if err := tx.Error; err != nil {
- return err
- }
-
- if err := tx.Create(docs).Error; err != nil {
- tx.Rollback()
- // if transaction fails, then delete malformed relation tuple
- permify.DeleteData(...)
- return err
- }
-
- // if transaction successful, write relation tuple to Permify
- permify.WriteData(...)
-
- return tx.Commit().Error
-}
-```
-
-The key point to take way from above approach is if the transaction fails for any reason, the relation will also be deleted from Permify to provide maximum consistency.
-
-### Data That Not Stored In Application Database
-
-Although ownership generally stored in application databases, there are some data that not needed to be stored in your actual database. Such as defining organizational roles, group members, project editors etc.
-
-For example, you can model a simple project management authorization in Permify as follows,
-
-```perm
-entity user {}
-
-entity team {
-
- relation owner @user
- relation member @user
-}
-
-entity project {
-
- relation team @team
- relation owner @user
-
- action view = team.member or team.owner or project.owner
- action edit = project.owner or team.owner
- action delete = project.owner or team.owner
-
-}
-```
-
-This **team member** relation won't need to be stored in the application database. Storing it only in Permify - preferred database - is enough. In that situation, `WriteData` can be performed in any logical place in your stack.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/permission/_category_.json
deleted file mode 100644
index e810c587..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Permission Service",
- "position": 2,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/expand-api.md b/docs/versioned_docs/version-0.6.x/api-overview/permission/expand-api.md
deleted file mode 100644
index 998955c1..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/expand-api.md
+++ /dev/null
@@ -1,319 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Expand API
-
-Retrieve all subjects (users and user sets) that have a relationship or attribute with given entity and permission
-
-Expand API response is represented by a user set tree, whose leaf nodes are user IDs or user sets pointing to other ⟨object#relation⟩ pairs.
-
-:::caution When To Use ?
-Expand is designed for reasoning the complete set of users that have access to their objects, which allows our users to build efficient search indices for access-controlled content.
-
-It is not designed to use as a check access. Expand request has a high latency which can cause a performance issues when its used as access check.
-:::
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.expand)
-
-
-
-
-```go
-cr, err: = client.Permission.Expand(context.Background(), &v1.PermissionExpandRequest{
- TenantId: "t1",
- Metadata: &v1.PermissionExpandRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- },
- Entity: &v1.Entity{
- Type: "repository",
- Id: "1",
- },
- Permission: "push",
-})
-```
-
-
-
-
-
-```javascript
-client.permission.expand({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- },
- entity: {
- type: "repository",
- id: "1"
- },
- permission: "push",
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/expand' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": "",
- "snap_token": ""
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "permission": "push"
-}'
-```
-
-
-
-## Example Usage
-
-To give an example usage for Expand API, let's examine following authorization model.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity repository {
-
- relation parent @organization
- relation owner @user
-
- action push = owner
- action read = owner and (parent.admin or parent.member)
-
-}
-```
-
-Above schema - modeled with Permify DSL - represents a simplified version of GitHub access control. When we look at the repository entity, we can see two actions and corresponding accesses:
-
- - Only owners can push to a private repository.
- - To read a private repository, the user should be one of the owners of that repository and need to belong to the parent organization of that repository ( user can either be admin or member on that organization).
-
-According to above authorization model, let's create 3 example relation tuples for testing expand API,
-
-`organization:1#admin@user:1` --> User 1 is admin in organization 1
-
-`repository:1#owner@user:1` --> User 1 is owner of repository 1
-
-`repository:1#parent@organization:1#...` --> repository 1 belongs to organization 1
-
-We can use expand API to reason the access actions. If we want to reason access structure for actions of repository entity, we can use expand API with ***POST "/v1/permissions/expand"***.
-
-**Path:**
-```javascript
-POST /v1/tenants/{tenant_id}/permissions/expand
-```
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md) |
-| [x] | entity | string | - | Name and id of the entity. Example: repository:1”. |
-| [x] | permission | string | - | The permission the user wants to perform on the resource |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-### Expand Push Action
-
-Request
-
-
-
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-entity.md b/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-entity.md
deleted file mode 100644
index b87d77a4..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-entity.md
+++ /dev/null
@@ -1,228 +0,0 @@
----
-title: Entity (Data) Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Entity Filtering
-
-Lookup Entity endpoint lets you ask questions in form of **“Which resources can user:X do action Y?”**. As a response of this you’ll get a entity results in a format of string array or as a streaming response depending on the endpoint you're using.
-
-So, we provide 2 separate endpoints for data filtering check request,
-
-- [Lookup Entity](#lookup-entity)
-- [Lookup Entity (Streaming)](#lookup-entity-streaming)
-
-## Lookup Entity
-
-In this endpoint you'll get directly the IDs' of the entities that are authorized in an array.
-
-**Path**
-```javascript
- POST /v1/permissions/lookup-entity
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntity)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../../reference/snap-tokens) |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupEntity(context.Background(), & v1.PermissionLookupEntityRequest {
- TenantId: "t1",
- Metadata: & v1.PermissionLookupEntityRequestMetadata {
- SnapToken: ""
- SchemaVersion: ""
- Depth: 20,
- },
- EntityType: "document",
- Permission: "edit",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupEntity({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entity_type: "document",
- permission: "edit",
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response.entity_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-entity' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "depth": 20
- },
- "entity_type": "document",
- "permission": "edit",
- "subject": {
- "type":"user",
- "id":"1"
- }
-}'
-```
-
-
-
-## How Lookup Operations Evaluated
-
-We explicitly designed reverse lookup to be more performant with changing its evaluation pattern. We do not query all the documents in bulk to get response, instead of this Permify first finds the necessary relations with given subject and the permission/action in the API call. Then query these relations with the subject id this way we reduce lots of additional queries.
-
-To give an example,
-
-```jsx
-entity user {}
-
-entity organization {
- relation admin @user
-}
-
-entity container {
- relation parent @organization
- relation container_admin @user
- action admin = parent.admin or container_admin
-}
-
-entity document {
- relation container @container
- relation viewer @user
- relation owner @user
- action view = viewer or owner or container.admin
-}
-```
-
-Lets say we called (reverse) lookup API to find the documents that user:1 can view. Permify first finds the relations that linked with view action, these are
-
-- `document#viewer`
-- `document#owner`
-- `organization#admin`
-- `container#``container_admin`
-
-Then queries each of them with `user:1.`
-
-## Lookup Entity (Streaming)
-
-The difference between this endpoint from direct Lookup Entity is response of this entity gives the IDs' as stream. This could be useful if you have large data set that getting all of the authorized data can take long with direct lookup entity endpoint.
-
-**Path**
-```javascript
- POST /v1/permissions/lookup-entity-stream
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupEntityStream)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md) |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [x] | entity_type | object | - | type of the entity. Example: repository”. |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-str, err: = client.Permission.LookupEntityStream(context.Background(), &v1.PermissionLookupEntityRequest {
- Metadata: &v1.PermissionLookupEntityRequestMetadata {
- SnapToken: "",
- SchemaVersion: ""
- Depth: 50,
- },
- EntityType: "document",
- Permission: "view",
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-
-// handle stream response
-for {
- res, err: = str.Recv()
-
- if err == io.EOF {
- break
- }
-
- // res.EntityId
-}
-```
-
-
-
-
-```javascript
-const permify = require("@permify/permify-node");
-const {PermissionLookupEntityStreamResponse} = require("@permify/permify-node/dist/src/grpc/generated/base/v1/service");
-
-function main() {
- const client = new permify.grpc.newClient({
- endpoint: "localhost:3478",
- })
-
- let res = client.permission.lookupEntityStream({
- metadata: {
- snapToken: "",
- schemaVersion: "",
- depth: 20
- },
- entityType: "document",
- permission: "view",
- subject: {
- type: "user",
- id: "1"
- }
- })
-
- handle(res)
-}
-
-async function handle(res: AsyncIterable) {
- for await (const response of res) {
- // response.entityId
- }
-}
-```
-
-
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-subject.md b/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-subject.md
deleted file mode 100644
index 0d0e17ff..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/lookup-subject.md
+++ /dev/null
@@ -1,116 +0,0 @@
----
-title: Subject Filtering
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Filtering
-
-Lookup Subject endpoint lets you ask questions in form of **“Which subjects can do action Y on entity:X?”**. As a response of this you’ll get a subject results in a format of string array.
-
-So, we provide 1 endpoint for subject filtering request,
-
-- [/v1/permissions/lookup-subject](#lookup-subject)
-
-## Lookup Subject
-
-In this endpoint you'll get directly the IDs' of the subjects that are authorized in an array.
-
-**POST**
-```javascript
-/v1/permissions/lookup-subject
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.lookupSubject)
-
-| Required | Argument | Type | Default | Description |
-|----------|---------------------|----------|---------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | - | Version of the schema |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1 |
-| [x] | permission | string | - | the action the user wants to perform on the resource |
-| [x] | subject_reference | object | - | the subject or subject reference who wants to take the action. It contains type and relation of the subject. |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.LookupSubject(context.Background(), &v1.PermissionLookupSubjectRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionLookupSubjectRequestMetadata{
- SnapToken: "",
- SchemaVersion: "",
- Depth: 20,
- },
- Entity: &v1.Entity{
- Type: "document",
- Id: "1",
- },
- Permission: "edit",
- SubjectReference: &v1.RelationReference{
- Type: "user",
- Relation: "",
- }
-})
-```
-
-
-
-
-```javascript
-client.permission.lookupSubject({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: ""
- depth: 20,
- },
- Entity: {
- Type: "document",
- Id: "1",
- },
- permission: "edit",
- subject_reference: {
- type: "user",
- relation: ""
- }
-}).then((response) => {
- console.log(response.subject_ids)
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/lookup-subject' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": ""
- "depth": 20,
- },
- "entity": {
- type: "document",
- id: "1'
- },
- "permission": "edit",
- "subject_reference": {
- "type": "user",
- "relation": ""
- }
-}'
-```
-
-
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/permission/subject-permission.md b/docs/versioned_docs/version-0.6.x/api-overview/permission/subject-permission.md
deleted file mode 100644
index 8157f3dc..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/permission/subject-permission.md
+++ /dev/null
@@ -1,133 +0,0 @@
----
-title: Subject Permission List
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Subject Permission List
-
-The Subject Permission List endpoint allows you to inquire in the form of **“Which permissions user:x can perform on entity:y?”**. In response, you'll receive a list of permissions specific to the user for the given entity, returned in the format of a map.
-
-So, we provide 1 endpoint for subject permission list,
-
-- [/v1/permissions/subject-permission](#subject-permission)
-
-In this endpoint, you'll receive a map of permissions and their statuses directly. The structure is map[string]CheckResult, such as "sample-permission" -> "ALLOWED". This represents the permissions and their associated states in a key-value pair format.
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/permissions/subject-permission
-```
-
-[](https://permify.github.io/permify-swagger/#/Permission/permissions.subjectPermission)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|---------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | schema_version | string | 8 | Version of the schema |
-| [ ] | snap_token | string | - | the snap token to avoid stale cache, see more details on [Snap Tokens](../../reference/snap-tokens.md). |
-| [x] | entity | object | - | contains entity type and id of the entity. Example: repository:1. |
-| [x] | subject | object | - | the user or user set who wants to take the action. It contains type and id of the subject. |
-| [x] | depth | integer | 8 | Timeout limit when if recursive database queries got in loop |
-| [ ] | only_permission | bool | false | By default, the endpoint returns both permissions and relations associated with the user and entity. However, when the "only_permission" parameter is set to true, it returns only the permissions. | |
-| [ ] | context | object | - | Contextual data that can be dynamically added to permission check requests. See details on [Contextual Data](../../reference/contextual-tuples.md) |
-
-
-
-
-```go
-cr, err: = client.Permission.SubjectPermission(context.Background(), &v1.PermissionSubjectPermissionRequest {
- TenantId: "t1",
- Metadata: &v1.PermissionSubjectPermissionRequestMetadata {
- SnapToken: "",
- SchemaVersion: "",
- OnlyPermission: false,
- Depth: 20,
- },
- Entity: &v1.Entity {
- Type: "repository",
- Id: "1",
- },
- Subject: &v1.Subject {
- Type: "user",
- Id: "1",
- },
-})
-```
-
-
-
-
-```javascript
-client.permission.subjectPermission({
- tenantId: "t1",
- metadata: {
- snapToken: "",
- schemaVersion: "",
- onlyPermission: true,
- depth: 20
- },
- entity: {
- type: "repository",
- id: "1"
- },
- subject: {
- type: "user",
- id: "1"
- }
-}).then((response) => {
- console.log(response);
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/permissions/subject-permission' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata":{
- "snap_token": "",
- "schema_version": "",
- "only_permission": true,
- "depth": 20
- },
- "entity": {
- "type": "repository",
- "id": "1"
- },
- "subject": {
- "type": "user",
- "id": "1",
- "relation": ""
- },
-}'
-```
-
-
-
-## Response
-
-```json
-{
- "results": [
- {
- "key": "delete",
- "value": "RESULT_ALLOWED"
- },
- {
- "key": "edit",
- "value": "RESULT_ALLOWED"
- }
- ]
-}
-```
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/schema/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/schema/_category_.json
deleted file mode 100644
index 8fd1e959..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/schema/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Schema Service",
- "position": 1,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/schema/write-schema.md b/docs/versioned_docs/version-0.6.x/api-overview/schema/write-schema.md
deleted file mode 100644
index 4ae10d83..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/schema/write-schema.md
+++ /dev/null
@@ -1,97 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Write Schema
-
-Permify provide it's own authorization language to model common patterns of easily. We called the authorization model Permify Schema and it can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor.
-
-We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is ***".perm"***.
-
-:::caution Use Playground For Testing
-If you're planning to test Permify manually, maybe with an API Design platform such as [Postman](https://www.postman.com/), [Insomnia](https://insomnia.rest/), etc; we're suggesting using our playground to create model. Because Permify Schema needs to be configured (send to API) in Permify API in a **string** format. Therefore, created model should be converted to **string**.
-
-Although, it could easily be done programmatically, it could be little challenging to do it manually. To help on that, we have a button on the playground to copy created model to the clipboard as a string, so you get your model in string format easily.
-
-
-:::
-
-Permify Schema needed to be send to API endpoint **/v1/schemas/write"** for configuration of your authorization model on Permify API.
-
-## Request
-
-```javascript
-POST /v1/tenants/{tenant_id}/schemas/write
-```
-
-[](https://permify.github.io/permify-swagger/#/Schema/schemas.write)
-
-| Required | Argument | Type | Default | Description |
-|----------|-------------------|--------|---------|-------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field.
-| [x] | schema | string | - | Permify Schema as string|
-
-
-
-
-```go
-sr, err: = client.Schema.Write(context.Background(), &v1.SchemaWriteRequest {
- TenantId: "t1",
- Schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `,
-})
-```
-
-
-
-
-```javascript
-client.schema.write({
- tenantId: "t1",
- schema: `
- "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
- `
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/schemas/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "schema": "entity user {}\n\n entity organization {\n\n relation admin @user\n relation member @user\n\n action create_repository = (admin or member)\n action delete = admin\n }\n\n entity repository {\n\n relation owner @user\n relation parent @organization\n\n action push = owner\n action read = (owner and (parent.admin and parent.member))\n action delete = (parent.member and (parent.admin or owner))\n }"
-}'
-```
-
-
-
-## Example Request on Postman
-**POST** "/v1/tenants/{tenant_id}/schemas/write"**
-
-**Example Request on Postman:**
-
-
-
-
-## Suggested Workflow For Schema Changes
-
-It's expected that your initial schema will eventually change as your product or system evolves
-
-As an example when a new feature arise and related permissions created you need to change the schema (rewrite it with adding new permission) then configure it using this Write Schema API. Afterwards, you can use the preferred version of the schema in your API requests with **schema_version**. If you do not prefer to use **schema_version** params in API calls Permify automatically gets the latest schema on API calls.
-
-A potential caveat of changing or creating schemas too often is the creation of many idle relation tuples. In Permify, created relation tuples are not removed from the stored database unless you delete them with the [delete API](../data/delete-data.md). For this case, we have a [garbage collector](https://github.com/Permify/permify/pull/381) which you can use to clear expired or idle relation tuples.
-
-We recommend applying the following pattern to safely handle schema changes:
-
-- Set up a central git repository that includes the schema.
-- Teams or individuals who need to update the schema should add new permissions or relations to this repository.
-- Centrally check and approve every change before deploying it via CI pipeline that utilizes the **Write Schema API**. We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-- After successful deployment, you can use the newly created schema on further API calls by either specifying its schema ID or by not providing any schema ID, which will automatically retrieve the latest schema on API calls.
-
-## Need any help ?
-
-Depending on the frequency and the type of the changes that you made on the schemas, this method may not be optimal for you - In such cases, we are open to exploring alternative solutions. Please feel free to [schedule a call with one of our engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/tenancy/_category_.json
deleted file mode 100644
index e1ebce3c..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Tenancy Service",
- "position": 5,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/create-tenant.md b/docs/versioned_docs/version-0.6.x/api-overview/tenancy/create-tenant.md
deleted file mode 100644
index 20a35d7e..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/create-tenant.md
+++ /dev/null
@@ -1,59 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Create Tenant
-
-Permify Multi Tenancy support you can create custom schemas for tenants and manage them in a single place. You can create a tenant with following API.
-
-:::caution
-We have a pre-inserted tenant - **t1** - by default for the ones that don't use multi-tenancy.
-:::
-
-## Request
-
-```javascript
-POST /v1/tenants/create
-```
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.create)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Create(context.Background(), & v1.TenantCreateRequest {
- Id: ""
- Name: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.create({
- id: "",
- name: ""
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'http://localhost:3476/v1/tenants/create' \
---header 'Content-Type: application/json' \
---data-raw '{
- "id": "",
- "name": ""
-}'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/delete-tenant.md b/docs/versioned_docs/version-0.6.x/api-overview/tenancy/delete-tenant.md
deleted file mode 100644
index aca60ef7..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/tenancy/delete-tenant.md
+++ /dev/null
@@ -1,47 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Delete Tenant
-
-You can delete a tenant with following API.
-
-## Request
-```javascript
-DELETE /v1/tenants/{id}
-```
-
-[](https://permify.github.io/permify-swagger/#/Tenancy/tenants.delete)
-
-
-
-
-```go
-rr, err: = client.Tenancy.Delete(context.Background(), & v1.TenantDeleteRequest {
- Id: ""
-})
-```
-
-
-
-
-
-```javascript
-client.tenancy.delete({
- id: "",
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request DELETE 'http://localhost:3476/v1/tenants/t1'
-```
-
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/watch/_category_.json b/docs/versioned_docs/version-0.6.x/api-overview/watch/_category_.json
deleted file mode 100644
index bb0c647b..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/watch/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Watch Service",
- "position": 6,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/api-overview/watch/watch-changes.md b/docs/versioned_docs/version-0.6.x/api-overview/watch/watch-changes.md
deleted file mode 100644
index aabc7416..00000000
--- a/docs/versioned_docs/version-0.6.x/api-overview/watch/watch-changes.md
+++ /dev/null
@@ -1,145 +0,0 @@
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Watch
-
-The Permify Watch API acts as a real-time broadcaster that shows changes in the relation tuples.
-
-The Watch API exclusively supports gRPC and works with PostgreSQL, given the track_commit_timestamp option is enabled. Please note, it doesn't support in-memory databases or HTTP communication.
-
-# Requirements
-
-- PostgreSQL database set up with track_commit_timestamp option enabled
-
-## Enabling track_commit_timestamp on PostgreSQL
-
-To ensure data consistency and synchronization between your application and Permify, enable track_commit_timestamp on
-your PostgreSQL server. This can be done by executing the following options in your PostgreSQL:
-
-### Option 1: SQL Command
-
-1. Open your PostgreSQL command line interface.
-2. Execute the following command:
-
- ```sql
- ALTER SYSTEM SET track_commit_timestamp = ON;
- ```
-
-3. Reload the configuration with the following command:
-
- ```sql
- SELECT pg_reload_conf();
- ```
-
-### Option 2: Editing postgresql.conf
-
-1. Find and open the postgresql.conf file in a text editor. Its location depends on your PostgreSQL installation. Common
- locations are:
- - Debian-based systems: /etc/postgresql/[version]/main/postgresql.conf
- - Red Hat-based systems: /var/lib/pgsql/data/postgresql.conf
-
-2. Add or modify the following line in the postgresql.conf file:
- ```
- track_commit_timestamp = on
- ```
-
-3. Save and close the postgresql.conf file.
-4. Reload the PostgreSQL configuration for the changes to take effect. This can be done via the PostgreSQL console:
- ```sql
- SELECT pg_reload_conf();
- ```
-
- Or if you have command line access, use:
-
- ```bash
- sudo service postgresql reload
- ```
-
-Please ensure you have the necessary permissions to execute these commands or modify the postgresql.conf file. Also, remember that changes in the postgresql.conf file will persist across restarts, while the SQL method may need to be reapplied depending on your PostgreSQL version and setup.
-
-:::info
-Important Configuration Requirement: To use the Watch API, it must be enabled in your configuration file. Add or modify the following lines:
-
-```yaml
-service:
- watch:
- enabled: true
-```
-
-:::
-
-## Request
-
-**Path:**
-```javascript
-POST /v1/watch/watch
-```
-
-[](https://permify.github.io/permify-swagger/#/Watch/watch.watch)
-
-| Required | Argument | Type | Default | Description |
-|----------|------------|--------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | tenant_id | string | - | identifier of the tenant, if you are not using multi-tenancy (have only one tenant) use pre-inserted tenant `t1` for this field. |
-| [ ] | snap_token | string | - | specifies the starting point for broadcasting changes. If a snap_token is provided, all changes following that specific snapshot will be broadcasted. If a snap_token is not provided, the Watch API will broadcast all changes that occur after the Watch API is initiated., see more details on [Snap Tokens](../../../reference/snap-tokens). |
-
-
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```go)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-[//]: # ()
-[//]: # (```javascript)
-
-[//]: # ()
-[//]: # (```)
-
-[//]: # ()
-[//]: # ()
-
-[//]: # ()
-
-## Response
-
-```json
-{
- "changes": {
- "tuple_changes": [
- {
- "operation": "OPERATION_CREATE",
- "tuple": {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject": {
- "type": "user",
- "id": "56",
- "relation": ""
- }
- }
- }
- ],
- "snap_token": "MgMAAAAAAAA="
- }
-}
-```
-
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or
-have any questions about this
-example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.6.x/comparision.md b/docs/versioned_docs/version-0.6.x/comparision.md
deleted file mode 100644
index 75fb39c4..00000000
--- a/docs/versioned_docs/version-0.6.x/comparision.md
+++ /dev/null
@@ -1,38 +0,0 @@
----
-id: comparison
-title: Comparison Between Other Zanzibar implementations
----
-
-:::caution Note
-This comparison table shows the differentiation between authorization solutions based or inspired by Google Zanzibar paper. If you use any of these solutions and feel the information could be improved, feel free to reach out.
-:::
-
-## General Aspects
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|---------------------------------|------------|------------|-----------|-----------|
-| **Zanzibar Paper Faithfulness** | Medium | High | High | High |
-| **Scalability** | Medium | Medium | High | High |
-| **Consistency & Cache** | No Zookies | No Zookies | Supported | Supported |
-| **Dev UX** | Average | Average | High | High |
-
-## Feature Set
-
-- ✅ Supported, and ready to use with no added configuration or code
-- 🟡 Limited support and requires extra user-code to implement.
-- ⛔ Not officially supported or documented.
-
-| | Ory/Keto | OpenFGA | SpiceDB | Permify |
-|--------------------------|----------|---------|---------|---------|
-| **Check API** | ✅ | ✅ | ✅ | ✅ |
-| **Write API** | ✅ | ✅ | ✅ | ✅ |
-| **Read API** | ✅ | ✅ | ✅ | ✅ |
-| **Expand API** | ✅ | ✅ | ✅ | ✅ |
-| **Watch API** | ✅ | ✅ | ✅ | ✅ |
-| **RBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ReBAC** | ✅ | ✅ | ✅ | ✅ |
-| **ABAC** | ⛔ | 🟡 | ✅ | ✅ |
-| **Data Filtering** | ⛔ | ✅ | ✅ | ✅ |
-| **Multi Tenancy** | ⛔ | ✅ | ⛔ | ✅ |
-| **Testing & Validation** | ⛔ | 🟡 | ✅ | ✅ |
-| **Logging & Tracing** | 🟡 | ✅ | ✅ | ✅ |
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/_category_.json b/docs/versioned_docs/version-0.6.x/getting-started/_category_.json
deleted file mode 100644
index 52b54bbb..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Getting Started",
- "position": 2,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/_category_.json b/docs/versioned_docs/version-0.6.x/getting-started/examples/_category_.json
deleted file mode 100644
index b3e4f801..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/_category_.json
+++ /dev/null
@@ -1,6 +0,0 @@
-{
- "label": "Example Permission Structures",
- "position": 4,
- "collapsed": true
-}
-
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/facebook-groups.md b/docs/versioned_docs/version-0.6.x/getting-started/examples/facebook-groups.md
deleted file mode 100644
index 1b918630..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/facebook-groups.md
+++ /dev/null
@@ -1,546 +0,0 @@
-# Facebook Groups
-
-This example demonstrate the authorization structure for Facebook groups, which enables users to perform various actions based on their roles and permissions within the group.
-
-### Schema | [Open in playground](https://play.permify.co/?s=XNEAs8dr0AINwCuSMcxHI)
-
-```perm
-// Represents a user
-entity user {}
-
-// Represents a Facebook group
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
-}
-
-// Represents a post in a Facebook group
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
-}
-
-// Represents a comment like on a post in a Facebook group
-entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
-}
-
-// Definition of poll entity
-entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
-}
-
-// Definition of file entity
-entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
-}
-
-// Definition of event entity
-entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities and relations, as well as actions and permissions that can be taken by users within the group. Let's examine them shortly;
-
-### Entities & Relations
-
-* **`user`** entity represents a user in the Facebook.
-
-* **`group`** entity represents the Facebook group, and it has several relations including member, admin, and moderator to represent the members, admins, and moderators of the group. Additionally, there are relations to represent the posts and comments in the group.
-
-* **`post`** entity represents a post in the Facebook group, and it has relations to represent the owner of the post and the group that the post belongs to.
-
-* **`comment`** entity represents a comment on a post in the Facebook group, and it has relations to represent the owner of the comment, the post that the comment belongs to, and the comment itself.
-
-* **`like`** entity represents a like on a post in the Facebook group, and it has relations to represent the owner of the like and the post that the like belongs to.
-
-* **`poll`** entity represents a poll in the Facebook group, and it has relations to represent the owner of the poll and the group that the poll belongs to.
-
-* **`file`** entity represents a file in the Facebook group, and it has relations to represent the owner of the file and the group that the file belongs to.
-
-* **`event`** entity represents an event in the Facebook group, and it has relations to represent the owner of the event and the group that the event belongs to.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions.
-
-For example, the `create_group` action can only be performed by a `member`, as follows:
-
-#### Creating a group permission
-
-```perm
-entity group {
-
- // Relation to represent the members of the group
- relation member @user
-
- ..
-
- // Create group permission
- action create_group = member
-
- ..
- ..
-}
-```
-
-Another example would be given from the `edit_post` action in the post entity, which specifies the permissions required to edit a post in a Facebook group.
-
-#### Editing a post permission
-
-```perm
-entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- ..
-
- action edit_post = owner or group.admin
-
- ..
- ..
-}
-```
-
-An **owner** of a post can always edit their own post. In addition, members who are defined as **admin** of the group - which the post belongs to - can also edit the post.
-
-Since most entities are deeply nested together, we also have multiple hierarchical permissions.
-
-#### Nested Hierarchies
-
-For example, we can define a permission "view_comment" if only user is owner of that comment or user is a member of the group which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-//group relationships
-group:1#member@user:1
-group:1#admin@user:2
-group:2#moderator@user:3
-group:2#member@user:4
-group:1#member@user:5
-
-//post relationships
-post:1#owner@user:1
-post:1#group@group:1
-post:2#owner@user:4
-post:2#group@group:1
-
-//comment relationships
-comment:1#owner@user:2
-comment:1#post@post:1
-comment:2#owner@user:5
-comment:2#post@post:2
-
-//like relationships
-like:1#owner@user:3
-like:1#post@post:1
-like:2#owner@user:4
-like:2#post@post:2
-
-//poll relationships
-poll:1#owner@user:2
-poll:1#group@group:1
-poll:2#owner@user:5
-poll:2#group@group:1
-
-//like relationships
-file:1#owner@user:1
-file:1#group@group:1
-
-//event relationships
-event:1#owner@user:3
-event:1#group@group:1
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:4 RSVP_to_event event:1 ?
-
-
-```perm
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
-
- ..
- ..
-
- action RSVP_to_event = owner or group.member
- }
-```
-
-According to what we have defined for the **'RSVP_to_event'** action, users who are either the owner of `event:1` or a member of the group that belongs to `event:1` can grant access to RSVP to the event.
-
-According to the relation tuples we created, `user:4` is not the **owner** of the event. Furthermore, when we check whether `user:4` is a **member** of the only group (`group:1`) that `event:1` is part of (`event:1#group@group:1`), we see that there is no **member** relation for `user:4` in that group.
-
-Therefore, the `user:4 RSVP_to_event event:1` check request should yield a **'false'** response.
-
-
-
-
-can user:5 view_comment comment:1 ?
-
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view_comment = owner or post.group_member
-
- ..
- ..
-}
-```
-
-According to the relation tuples we created, `user:5` is not the **owner** of the comment. But member of the `group:1` and thats grant `user:5` (`group:1#member@user:5`) access to perform view the comment:1. In particularly, `comment:1` is part of the `post:1` (`comment:1#post@post:1`) and `post:1` is part of the group:1 (`post:1#group@group:1`). And from the action definition on above model group:1 members can view the `comment:1`.
-
-Therefore, the `user:5 view_comment comment:1` check request should yield a **'true'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity group {
-
- // Relation to represent the members of the group
- relation member @user
- // Relation to represent the admins of the group
- relation admin @user
- // Relation to represent the moderators of the group
- relation moderator @user
-
- // Permissions for the group entity
- action create = member
- action join = member
- action leave = member
- action invite_to_group = admin
- action remove_from_group = admin or moderator
- action edit_settings = admin or moderator
- action post_to_group = member
- action comment_on_post = member
- action view_group_insights = admin or moderator
- }
-
- entity post {
-
- // Relation to represent the owner of the post
- relation owner @user
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
- action view_post = owner or group.member
- action edit_post = owner or group.admin
- action delete_post = owner or group.admin
-
- permission group_member = group.member
- }
-
- entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
-
- // Permissions for the comment entity
- action view_comment = owner or post.group_member
- action edit_comment = owner
- action delete_comment = owner
- }
-
- entity like {
-
- // Relation to represent the owner of the like
- relation owner @user
-
- // Relation to represent the post that the like belongs to
- relation post @post
-
- // Permissions for the like entity
- action like_post = owner or post.group_member
- action unlike_post = owner or post.group_member
- }
-
- entity poll {
-
- // Relation to represent the owner of the poll
- relation owner @user
-
- // Relation to represent the group that the poll belongs to
- relation group @group
-
- // Permissions for the poll entity
- action create_poll = owner or group.admin
- action view_poll = owner or group.member
- action edit_poll = owner or group.admin
- action delete_poll = owner or group.admin
- }
-
- entity file {
-
- // Relation to represent the owner of the file
- relation owner @user
-
- // Relation to represent the group that the file belongs to
- relation group @group
-
- // Permissions for the file entity
- action upload_file = owner or group.member
- action view_file = owner or group.member
- action delete_file = owner or group.admin
- }
-
- entity event {
-
- // Relation to represent the owner of the event
- relation owner @user
- // Relation to represent the group that the event belongs to
- relation group @group
-
- // Permissions for the event entity
- action create_event = owner or group.admin
- action view_event = owner or group.member
- action edit_event = owner or group.admin
- action delete_event = owner or group.admin
- action RSVP_to_event = owner or group.member
- }
-
-relationships:
- - group:1#member@user:1
- - group:1#admin@user:2
- - group:2#moderator@user:3
- - group:2#member@user:4
- - group:1#member@user:5
- - post:1#owner@user:1
- - post:1#group@group:1
- - post:2#owner@user:4
- - post:2#group@group:1
- - comment:1#owner@user:2
- - comment:1#post@post:1
- - comment:2#owner@user:5
- - comment:2#post@post:2
- - like:1#owner@user:3
- - like:1#post@post:1
- - like:2#owner@user:4
- - like:2#post@post:2
- - poll:1#owner@user:2
- - poll:1#group@group:1
- - poll:2#owner@user:5
- - poll:2#group@group:1
- - file:1#owner@user:1
- - file:1#group@group:1
- - event:1#owner@user:3
- - event:1#group@group:1
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "event:1"
- subject: "user:4"
- assertions:
- RSVP_to_event : false
- - entity: "comment:1"
- subject: "user:5"
- assertions:
- view_comment : true
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/google-docs.md b/docs/versioned_docs/version-0.6.x/getting-started/examples/google-docs.md
deleted file mode 100644
index 3f14e1f7..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/google-docs.md
+++ /dev/null
@@ -1,344 +0,0 @@
-# Google Docs Simplified
-
-This example models a simplified version of Google Docs style permission system where users can be granted direct access to a document, or access via organizations and nested groups.
-
-### Schema | [Open in playground](https://play.permify.co/?s=iuRic3nR1HeZJcFyRNKPo)
-
-```perm
-entity user {}
-
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-## Breakdown of the Model
-
-### User
-
-```perm
-entity user {}
-```
-
-Represents a user who can be granted permission to access a documents directly, or through their membership in a group or organization.
-
-### Document
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-Represents a document that users can be granted permission to access. The document entity has two relationships:
-
-#### Relations
-
-**org:** Represents organization that document belongs to.
-
-**manager:** A relationship between users who are authorized to manage the document. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group member and manager relations.
-
-**viewer:** A relationship between users who are authorized to view the document. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager relations.
-
-The document entity has two actions defined:
-
-#### Actions
-
-**manage:**: An action that can be performed by users who are authorized to manage the document, as determined by the manager relationship.
-
-**view:** An action that can be performed by users who are authorized to view the document, as determined by the viewer and manager relationships.
-
-### Group
-
-```perm
-entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
-}
-```
-
-Represents a group of users who can be granted permission to access a document. The group entity has two relationships:
-
-#### Relations
-
-**manager:** A relationship between users who are authorized to manage the group. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are members of the group. This relationship is defined by the `@user` annotation on one end and the `@group#member` and `@group#manager` annotations on the other end corresponding to the group entity member and manager.
-
-The group entity has one action defined:
-
-### Organization
-
-```perm
-entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
-}
-```
-
-Represents an organization that can contain groups, users, and documents. The organization entity has several relationships:
-
-#### Relations
-
-**group:** A relationship between the organization and its groups. This relationship is defined by the `@group` annotation on the end corresponding to the group entity.
-
-**document:** A relationship between the organization and its document. This relationship is defined by the `@document` annotation on the end corresponding to the group entity.
-
-**administrator:** A relationship between users who are authorized to manage the organization. This relationship is defined by the `@user` annotation on both ends, and by the `@group#member` and `@group#manager` annotations on the ends corresponding to the group entity member and manager.
-
-**direct_member:** A relationship between users who are directly members of the organization. This relationship is defined by the `@user` annotation on the end corresponding to the user entity.
-
-The organization entity has two permissions defined:
-
-#### Permissions
-
-**admin:** An permission that can be performed by users who are authorized to manage the organization, as determined by the administrator relationship.
-
-**member:** An permission that can be performed by users who are directly members of the organization, or who have administrator relationship, or who are members of groups that are part of the organization,
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different groups
-group:tech#manager@user:ashley
-group:tech#direct_member@user:david
-group:marketing#manager@user:john
-group:marketing#direct_member@user:jenny
-group:hr#manager@user:josh
-group:hr#direct_member@user:joe
-
-// Assign groups to other groups
-group:tech#direct_member@group:marketing#direct_member
-group:tech#direct_member@group:hr#direct_member
-
-// Connect groups to organization
-organization:acme#group@group:tech
-organization:acme#group@group:marketing
-organization:acme#group@group:hr
-
-// Add some documents under the organization
-organization:acme#document@document:product_database
-organization:acme#document@document:marketing_materials
-organization:acme#document@document:hr_documents
-
-// Assign a user and members of a group as administrators for the organization
-organization:acme#administrator@group:tech#manager
-organization:acme#administrator@user:jenny
-
-// Set the permissions on some documents
-document:product_database#manager@group:tech#manager
-document:product_database#viewer@group:tech#direct_member
-document:marketing_materials#viewer@group:marketing#direct_member
-document:hr_documents#manager@group:hr#manager
-document:hr_documents#viewer@group:hr#direct_member
-```
-
-## Test & Validation
-
-Finally, let's check some permissions and test our authorization logic.
-
-can user:ashley edit document:product_database ?
-
-
-```perm
- entity document {
- relation org @organization
-
- relation viewer @user @group#member @group#manager
- relation manager @user @group#member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-```
-
-According what we have defined for the edit action managers and admins, of the organization that document belongs, can edit product database. In this context, Permify engine will check does subject `user:ashley` has any direct or indirect manager relation within `document:product_database`. Consecutively it will check does `user:ashley` has admin relation in the Acme Org - `organization:acme#document@document:product_database`.
-
-Ashley doesn't have any administrative relation in Acme Org but she is the manager in group tech (`group:tech#manager@user:ashley`) and we have defined that manager of group tech is manager of product_database with the tuple (`document:product_database#manager@group:tech#manager`). Therefore, the **user:ashley edit document:product_database** check request should yield **true** response.
-
-
-
-
-can user:joe view document:hr_documents ?
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check whether subject `user:joe` has any direct or indirect manager or viewer relation within `document:hr_documents`. Also consecutively it will check does `user:joe` has admin relation in the Acme Org - `organization:acme#document@document:hr_documents`.
-
-Joe doesn't have administrative role/relation in Acme Org.
-
-Also he doesn't have have manager relationship in that document or within any entity.
-
-But he is member in the hr group (`group:hr#member@user:joe`) and we defined hr members have viewer relationship in hr documents (`document:hr_documents#viewer@group:hr#member`). So that, this enforcement should yield **true** response.
-
-
-
-```perm
-entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
-}
-```
-
-According what we have defined for the view action viewers or managers or org.admin's can view hr documents. In this context, Permify engine will check does subject `user:david` has any direct or indirect manager or viewer relation within `document:marketing_materials`. Also consecutively it will check does `user:david` has admin relation in the Acme Org - `organization:acme#document@document:marketing_materials`.
-
-Similar Joe and Ashley, David also doesn't have administrative role/relation in Acme Org.
-
-Also David doesn't have member or manager relationship related with marketing group - `document:marketing_materials`. So that, this enforcement should yield **false** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
- relation group @group
- relation document @document
- relation administrator @user @group#direct_member @group#manager
- relation direct_member @user
-
- permission admin = administrator
- permission member = direct_member or administrator or group.member
- }
-
- entity group {
- relation manager @user @group#direct_member @group#manager
- relation direct_member @user @group#direct_member @group#manager
-
- permission member = direct_member or manager
- }
-
- entity document {
- relation org @organization
-
- relation viewer @user @group#direct_member @group#manager
- relation manager @user @group#direct_member @group#manager
-
- action edit = manager or org.admin
- action view = viewer or manager or org.admin
- }
-
-relationships:
- - group:tech#manager@user:ashley
- - group:tech#direct_member@user:david
- - group:marketing#manager@user:john
- - group:marketing#direct_member@user:jenny
- - group:hr#manager@user:josh
- - group:hr#direct_member@user:joe
-
- - group:tech#direct_member@group:marketing#direct_member
- - group:tech#direct_member@group:hr#direct_member
-
- - organization:acme#group@group:tech
- - organization:acme#group@group:marketing
- - organization:acme#group@group:hr
- - organization:acme#document@document:product_database
- - organization:acme#document@document:marketing_materials
- - organization:acme#document@document:hr_documents
- - organization:acme#administrator@group:tech#manager
- - organization:acme#administrator@user:jenny
-
- - document:product_database#manager@group:tech#manager
- - document:product_database#viewer@group:tech#direct_member
- - document:marketing_materials#viewer@group:marketing#direct_member
- - document:hr_documents#manager@group:hr#manager
- - document:hr_documents#viewer@group:hr#direct_member
-
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "document:product_database"
- subject: "user:ashley"
- assertions:
- edit: true
- - entity: "document:hr_documents"
- subject: "user:joe"
- assertions:
- view: true
- - entity: "document:marketing_materials"
- subject: "user:david"
- assertions:
- view: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of modeling Google Docs style permission system. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/instagram.md b/docs/versioned_docs/version-0.6.x/getting-started/examples/instagram.md
deleted file mode 100644
index 9cd83163..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/instagram.md
+++ /dev/null
@@ -1,376 +0,0 @@
-# Instagram
-
-This example presents an Instagram Authorization Schema, outlining the intricate relationships between users, accounts, and posts on the platform. It defines user access levels, privacy settings, and interactions, offering insights into how followers, account owners, and post restrictions are managed within the Instagram ecosystem.
-
-## Schema | [Open in playground](https://play.permify.co/?s=instagram&tab=schema)
-
-```perm
-entity user {}
-
-entity account {
- // users have accounts
- relation owner @user
-
- // accounts can follow other users/accounts.
- relation following @user
-
- // other users/accounts can follow account.
- relation follower @user
-
- // accounts can be private or public.
- attribute public boolean
-
- // users can view an account if they're followers, owners, or if the account is not private.
- action view = (owner or follower) or public
-
-}
-
-entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- // users can view the posts, if they have access to view the linked accounts.
- action view = account.view
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
-}
-```
-
-## Brief Examination of the Model
-
-The Instagram Authorization Schema models the relationships between users, accounts, and posts in the Instagram platform.
-
-Users can own accounts, follow other accounts, and be followed by other users. Accounts can have public or private settings, and access to view an account is determined by ownership, followers, and privacy settings. Posts are associated with accounts and can have restricted comments and likes based on account privacy.
-
-### Entities & Relations
-
-- **`User`**: Represents a user on the Instagram platform.
-
-- **`Account`**: Represents a user account on Instagram. Accounts have owners, followers, and can follow other accounts.
-
-- **`Post`**: Represents a post on Instagram. Posts are linked to accounts and can have restricted comments and likes.
-
-### Permissions
-
-Users can view an account if they are the owner, a follower, or if the account is public.
-Users can comment and like posts if they have access to view the linked account and the post is unrestricted.
-
-### Relationships and Attributes
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Relationships
-// Users, Accounts and Posts:
- account:1#owner@user:kevin
- account:2#owner@user:george
- account:1#following@user:george
- account:2#follower@user:kevin
- post:1#account@account:1
- post:2#account@account:2
-
-// Attributes
-// Accounts and Posts:
- account:1$public|boolean:true
- account:2$public|boolean:false
- post:1$restricted|boolean:false
- post:2$restricted|boolean:true
-```
-
-## Test & Validation
-
-To validate our authorization logic, let's run some tests on different scenarios using the Instagram Authorization Schema.
-
-### Test 1: Checking Account Viewing Permissions
-
-
-
- Can user:kevin view account:1?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:kevin` is the owner of `account:1`. Hence, `user:kevin` should be able to view `account:1`. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:kevin view account:2?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:kevin` follows `account:2`. Hence, `user:kevin` should be able to view `account:2` because he is a follower. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:george view account:1?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:george` can view `account:1`, because the account is public. Hence, `user:george` should be able to view `account:1`. The expected result is `'true'`.
-
-
-
-
-
-
- Can user:george view account:2?
-
-
-
-
-```perm
- entity account {
- relation owner @user
- relation following @user
- relation follower @user
- attribute public boolean
- action view = (owner or follower) or public
- }
-```
-
-According to the schema, `user:george` is the owner of `account:2`. Hence, `user:george` should be able to view `account:2`. The expected result is `'true'`.
-
-
-
-
-### Test 2: Checking Post Viewing Permissions
-
-Can user:george view post:1?
-
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:1` is linked with `account:1`, and it does not have restricted access. Also, `user:george` is following `account:1`. Hence, `user:george` should be able to view `post:1`. The expected result is `'true'`.
-
-
-
-
-Can user:kevin view post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it has restricted access. Also, `user:george` is not following `account:1`. Hence, `user:kevin` should not be able to view `post:2`. The expected result is `'false'`.
-
-
-
-
-Can user:george view post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action view = account.view
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it is restricted access. Also, `user:george` can view his own `post:2`. The expected result is `'true'`.
-
-
-
-
-### Test 3: Checking Post Commenting Permissions
-
-Can user:george comment post:1?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action comment = account.following not restricted
-}
-```
-
-According to the schema, `post:1` is linked with `account:1`, and it is not restricted. Also, `user:george` can comment on `post:1`. The expected result is `'true'`.
-
-
-
-
-Can user:kevin comment post:2?
-
-
-```perm
-entity post {
- relation account @account
- attribute restricted boolean
- action comment = account.following not restricted
-}
-```
-
-According to the schema, `post:2` is linked with `account:2`, and it is restricted. `user:kevin` cannot comment on `post:2`. The expected result is `'false'`.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: |-
- entity user {}
-
- entity account {
- // users have accounts
- relation owner @user
-
- // accounts can follow other users/accounts.
- relation following @user
-
- // other users/accounts can follow account.
- relation follower @user
-
- // accounts can be private or public.
- attribute public boolean
-
- // users can view an account if they're followers, owners, or if the account is not private.
- action view = (owner or follower) or public
-
- }
-
- entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- // users can view the posts, if they have access to view the linked accounts.
- action view = account.view
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
- }
-relationships:
- - account:1#owner@user:kevin
- - account:2#owner@user:george
- - account:1#following@user:george
- - account:2#follower@user:kevin
- - post:1#account@account:1
- - post:2#account@account:2
-attributes:
- - account:1$public|boolean:true
- - account:2$public|boolean:false
- - post:1$restricted|boolean:false
- - post:2$restricted|boolean:true
-scenarios:
- - name: Account Viewing Permissions
- description: Evaluate account viewing permissions for 'kevin' and 'george'.
- checks:
- - entity: account:1
- subject: user:kevin
- assertions:
- view: true
- - entity: account:2
- subject: user:kevin
- assertions:
- view: true
- - entity: account:1
- subject: user:george
- assertions:
- view: true
- - entity: account:2
- subject: user:george
- assertions:
- view: true
- - name: Post Viewing Permissions
- description: Determine post viewing permissions for 'kevin' and 'george'.
- checks:
- - entity: post:1
- subject: user:george
- assertions:
- view: true
- - entity: post:2
- subject: user:kevin
- assertions:
- view: true
- - entity: post:2
- subject: user:george
- assertions:
- view: true
- - name: Post Commenting Permissions
- description: Evaluate post commenting permissions for 'kevin' and 'george'.
- checks:
- - entity: post:1
- subject: user:george
- assertions:
- comment: true
- - entity: post:2
- subject: user:kevin
- assertions:
- comment: false
-```
-
-## Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/mercury.md b/docs/versioned_docs/version-0.6.x/getting-started/examples/mercury.md
deleted file mode 100644
index 796c6211..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/mercury.md
+++ /dev/null
@@ -1,157 +0,0 @@
-# Mercury
-
-Explore **Mercury's Authorization Schema** in this example, delving into the intricate interplay among **users**, **organizations**, and **accounts**. Uncover the defined user roles, approval workflows, and limits, providing a snapshot of the dynamic relationships within the Mercury ecosystem.
-
-For those who don’t know, Mercury is a bank offering both checking and savings accounts, complete with debit and credit card features. Given the delicate nature of financial transactions, Mercury has built-in access control features to ensure security.
-
-But today we’re going to focus on approvals. Mercury allows it’s users to set a number amount for multiple user approval for any action.
-
-For instance, an admin can decide that withdrawals above $1000 by members require approval from two designated approvers. This means, if a member wants to withdraw more than $1000, they need a green light from two admin. And if an admin tries to withdraw they need an approval form another admin.
-
-- Admin → Withdraw $1000 → needs an approver
-- Member → Withdraw $1000 → needs 2 approvers.
-
-## Full Schema | [Open in playground](https://play.permify.co/?s=mercury&tab=schema)
-
-So let’s start with building basics. We need Users, Organization, Accounts both Savings and Deposits as entities in the mercury
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity teams {}
-
-entity accounts {}
-```
-
-Then inserting relations into these entities.
-
-```perm
-entity user {}
-
-entity organization {
- relation admin @user
- relation member @user
-}
-
-entity accounts {
- relation checkings @accounts
- relation savings @accounts
-
- relation org @organization
-}
-```
-
-Next step is to define actions in our use case.
-
-```perm
-entity user {}
-
-entity organization {
- relation admin @user
- relation member @user
-}
-
-entity account {
-
- relation checkings @account
- relation savings @account
-
- relation org @organization
-
- action withdraw =
-
-}
-```
-
-Now we need to define our attributes which will help us create access rights via Withdraw Limit and Admin Approval of the account.
-
-Every organization has a set withdrawal limit. Additionally, for members and admins of the organization, there are specific approval limits in place when they attempt to withdraw amounts exceeding this limit.
-
-```perm
-entity user {}
-
-entity organization {
- relation admin @user
- relation member @user
-}
-
-entity account {
-
- relation checkings @account
- relation savings @account
-
- relation org @organization
-
- attribute approval integer
- attribute balance double
-
- action withdraw =
-
-}
-```
-
-Let’s create our rules that defines our attribute-based access rights.
-
-- Balance of the account must be more than withdraw amount
-- If withdraw amount is less than the withdraw limit we don’t need approval
-- Else; we need approve of two admins if we’re member, and we need approve of single admin if we’re another admin.
-
-```perm
-entity user {}
-
-entity organization {
- relation admin @user
- relation member @user
-
- attribute admin_approval_limit integer
- attribute member_approval_limit integer
- attribute approval_num integer
-
- action approve = admin
- action create_account = admin
-
- permission approval = (member and check_member_approval(approval_num, member_approval_limit)) or (admin and check_admin_approval(approval_num, admin_approval_limit))
-}
-
-entity account {
- relation checkings @account
- relation savings @account
-
- relation owner @organization
-
- attribute withdraw_limit double
- attribute balance double
-
- action withdraw = check_balance(balance, request.amount) and (check_limit(withdraw_limit, request.amount) or owner.approval)
-}
-
-rule check_balance(balance double, amount double) {
- balance >= amount
-}
-
-rule check_limit(withdraw_limit double, amount double) {
- withdraw_limit >= amount
-}
-
-rule check_admin_approval(approval_num integer, admin_approval_limit integer) {
- approval_num >= admin_approval_limit
-}
-
-rule check_member_approval(approval_num integer, member_approval_limit integer) {
- approval_num >= member_approval_limit
-}
-```
-
-At last, as you can see we use the Rules to define access rights to withdraw which basically translates into;
-
-- Check balance if it’s over the withdraw amount. If not don’t allow the action.
-- Check withdraw limit; if it’s less than the limit allow the action…
-- Else;
- - Check if user is admin, and have approval more than the approval limit for admins.
- - Check if user is member, and have approval more than the approval limit for members.
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/examples/notion.md b/docs/versioned_docs/version-0.6.x/getting-started/examples/notion.md
deleted file mode 100644
index 9095d464..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/examples/notion.md
+++ /dev/null
@@ -1,548 +0,0 @@
-# Notion
-
-This is a schema definition of the authorization model for Notion, a popular productivity and organization tool.
-
-### Schema | [Open in playground](https://play.permify.co/?s=BsCvLmd4g81sB20XJZI5p)
-
-```perm
-entity user {}
-
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
-}
-
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
-}
-
-entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
-}
-
-entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
-}
-
-entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
-}
-
-entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
-}
-
-entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
-}
-```
-
-## Brief Examination of the Model
-
-The model defines several entities, including users, workspaces, pages, databases, blocks, and integrations. It also includes several default roles, such as Admin, Bot, Guest, and Member. Here's a breakdown of the entities:
-
-### Entities & Relations
-
-- **`user`**: Represents a user in the system.
-
-- **`workspace`**: Represents a workspace in which users can collaborate. Each workspace has an owner, members, guests, and bots associated with it. The owner and admin users have permission to manage the workspace. Permissions are defined for creating pages, inviting members, viewing the workspace, and managing the workspace. The read and write permissions can be inherited by child entities.
-
-- **`page`**: Represents a page within a workspace. Each page is associated with a workspace and has a writer and readers. The read and write permissions are defined based on the writer and readers of the page and can be inherited from the workspace.
-
-- **`database`**: Represents a database within a workspace. Each database is associated with a workspace and has an editor and viewers. The read and write permissions are defined based on the editor and viewers of the database and can be inherited from the workspace. Permissions are also defined for creating and deleting databases.
-
-- **`block`**: Represents a block within a page or database. Each block is associated with a page or database and has an editor and commenters. The read and write permissions are defined based on the editor and commenters of the block and can be inherited from the database. Commenters are users who have permission to comment on the block.
-
-- **`comment`**: Represents a comment on a block. Each comment is associated with a block and has an author. The read and write permissions are defined based on the author of the comment and can be inherited from the block.
-
-- **`template`**: Represents a template within a workspace. Each template is associated with a workspace and has a creator and viewers. The read and write permissions are defined based on the creator and viewers of the template and can be inherited from the workspace. Permissions are also defined for creating and deleting templates.
-
-- **`integration`**: Represents an integration within a workspace. Each integration is associated with a workspace and has an owner. Permissions are defined for reading and writing to the integration.
-
-### Permissions
-
-We have several actions attached with the entities, which are limited by certain permissions. Let's examine the **read** permission of the page entity.
-
-#### Page Read Permission
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- ..
-}
-
-entity page {
-
- // The workspace associated with the page
- relation workspace @workspace
-
- ..
- ..
-
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- ..
- ..
-
- // Define permissions for page actions
- permission read = reader or workspace.read
-
- ..
- ..
-}
-```
-
-This permission specifies who can read the contents of the page at Notion.
-
-The `reader` relation specifies the users who are members of the workspace associated with the page (`workspace#member`) or guests of the workspace (`workspace#guest`).
-
-Read permission of the workspace inherited as `workspace.read` in the page entity. THis permission specifies that any user who has been granted read access to the workspace object (i.e., the workspace that the page belongs to) can also read the page.
-
-In summary, any user who is a member or guest of the workspace and has been granted read access to the page through the reader relation, as well as any user who has been granted read access to the workspace itself, can read the contents of the page.
-
-## Relationships
-
-Based on our schema, let's create some sample relationships to test both our schema and our authorization logic.
-
-```perm
-// Assign users to different workspaces:
-workspace:engineering_team#owner@user:alice
-workspace:engineering_team#member@user:bob
-workspace:engineering_team#guest@user:charlie
-workspace:engineering_team#admin@user:alice
-workspace:sales_team#owner@user:david
-workspace:sales_team#member@user:eve
-workspace:sales_team#guest@user:frank
-workspace:sales_team#admin@user:david
-
-// Connect pages, databases, and templates to workspaces:
-page:project_plan#workspace@workspace:engineering_team
-page:product_spec#workspace@workspace:engineering_team
-database:task_list#workspace@workspace:engineering_team
-template:weekly_report#workspace@workspace:sales_team
-database:customer_list#workspace@workspace:sales_team
-template:marketing_campaign#workspace@workspace:sales_team
-
-// Set permissions for pages, databases, and templates:
-page:project_plan#writer@user:frank
-page:project_plan#reader@user:bob
-
-database:task_list#editor@user:alice
-database:task_list#viewer@user:bob
-
-template:weekly_report#creator@user:alice
-template:weekly_report#viewer@user:bob
-
-page:product_spec#writer@user:david
-page:product_spec#reader@user:eve
-
-database:customer_list#editor@user:david
-database:customer_list#viewer@user:eve
-
-template:marketing_campaign#creator@user:david
-template:marketing_campaign#viewer@user:eve
-
-// Set relationships for blocks and comments:
-block:task_list_1#database@database:task_list
-block:task_list_1#editor@user:alice
-block:task_list_1#commenter@user:bob
-block:task_list_2#database@database:task_list
-block:task_list_2#editor@user:alice
-block:task_list_2#commenter@user:bob
-
-comment:task_list_1_comment_1#block@block:task_list_1
-comment:task_list_1_comment_1#author@user:bob
-comment:task_list_1_comment_2#block@block:task_list_1
-comment:task_list_1_comment_2#author@user:charlie
-comment:task_list_2_comment_1#block@block:task_list_2
-comment:task_list_2_comment_1#author@user:bob
-comment:task_list_2_comment_2#block@block:task_list_2
-comment:task_list_2_comment_2#author@user:charlie
-```
-
-## Test & Validation
-
-Since we have our schema and the sample relation tuples, let's check some permissions and test our authorization logic.
-
-can user:alice write database:task_list ?
-
-
-```perm
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
-
- ..
- ..
-
- // Define permissions for database actions
- ..
- ..
-
- permission write = editor or workspace.write
-
- ..
- ..
- }
-```
-
-According to what we have defined for the **'write'** permission, users who are either;
-
-- The editor in task list database (`database:task_list`)
-- Have a write permission in the engineering team workspace, which is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`)
-
-can edit the task list database (`database:task_list`)
-
-Based on the relation tuples we created, `user:alice` doesn't have the **editor** relationship with the `database:task_list`.
-
-Since `user:alice` is the owner and admin in the engineering team workspace (`workspace:engineering_team#admin@user:alice`) it has a write permission defined in the workspace entity, as you can see below:
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- ..
- ..
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- // Define permissions that can be inherited by child entities
- ..
- permission write = owner or admin
-}
-```
-
-And as we mentioned the engineering team workspace is the only workspace that task list is associated (`database:task_list#workspace@workspace:engineering_team`). Therefore, the `user:alice write database:task_list` check request should yield a **'true'** response.
-
-
-
-
-can user:charlie write page:product_spec ?
-
-
-```perm
-entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
-
- ..
- ..
-
- permission write = writer or workspace.write
-}
-```
-
-`user:charlie` is guest in the workspace (`workspace:engineering_team#guest@user:charlie`) and the engineering team workspace is the only workspace that `page:product_spec` belongs to.
-
-As we defined, guests doesn't have write permission in a workspace.
-
-```perm
-entity workspace {
- // The owner of the workspace
- relation owner @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- ..
- ..
-
- permission write = owner or admin
-}
-```
-
-So that, `user:charlie` doesn't have a write relationship in the workspace. And ultimately, the `user:charlie write page:product_spec` check request should yield a **'false'** response.
-
-
-
-
-Let's test these access checks in our local with using **permify validator**. We'll use the below schema for the schema validation file.
-
-```yaml
-schema: >-
- entity user {}
-
- entity workspace {
- // The owner of the workspace
- relation owner @user
- // Members of the workspace
- relation member @user
- // Guests (users with read-only access) of the workspace
- relation guest @user
- // Bots associated with the workspace
- relation bot @user
- // Admin users who have permission to manage the workspace
- relation admin @user
-
- // Define permissions for workspace actions
- permission create_page = owner or member or admin
- permission invite_member = owner or admin
- permission view_workspace = owner or member or guest or bot
- permission manage_workspace = owner or admin
-
- // Define permissions that can be inherited by child entities
- permission read = member or guest or bot or admin
- permission write = owner or admin
- }
-
- entity page {
- // The workspace associated with the page
- relation workspace @workspace
- // The user who can write to the page
- relation writer @user
- // The user(s) who can read the page (members of the workspace or guests)
- relation reader @user @workspace#member @workspace#guest
-
- // Define permissions for page actions
- permission read = reader or workspace.read
- permission write = writer or workspace.write
- }
-
- entity database {
- // The workspace associated with the database
- relation workspace @workspace
- // The user who can edit the database
- relation editor @user
- // The user(s) who can view the database (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for database actions
- permission read = viewer or workspace.read
- permission write = editor or workspace.write
- permission create = editor or workspace.write
- permission delete = editor or workspace.write
- }
-
- entity block {
- // The page associated with the block
- relation page @page
- // The database associated with the block
-
- relation database @database
- // The user who can edit the block
- relation editor @user
- // The user(s) who can comment on the block (readers of the parent object)
- relation commenter @user @page#reader
-
- // Define permissions for block actions
- permission read = database.read or commenter
- permission write = editor or database.write
- permission comment = commenter
- }
-
- entity comment {
- // The block associated with the comment
- relation block @block
-
- // The author of the comment
- relation author @user
-
- // Define permissions for comment actions
- permission read = block.read
- permission write = author
- }
-
- entity template {
- // The workspace associated with the template
- relation workspace @workspace
- // The user who creates the template
- relation creator @user
-
- // The user(s) who can view the page (members of the workspace or guests)
- relation viewer @user @workspace#member @workspace#guest
-
- // Define permissions for template actions
- permission read = viewer or workspace.read
- permission write = creator or workspace.write
- permission create = creator or workspace.write
- permission delete = creator or workspace.write
- }
-
- entity integration {
- // The workspace associated with the integration
- relation workspace @workspace
-
- // The owner of the integration
- relation owner @user
-
- // Define permissions for integration actions
- permission read = workspace.read
- permission write = owner or workspace.write
- }
-
-relationships:
- - workspace:engineering_team#owner@user:alice
- - workspace:engineering_team#member@user:bob
- - workspace:engineering_team#guest@user:charlie
- - workspace:engineering_team#admin@user:alice
- - workspace:sales_team#owner@user:david
- - workspace:sales_team#member@user:eve
- - workspace:sales_team#guest@user:frank
- - workspace:sales_team#admin@user:david
- - page:project_plan#workspace@workspace:engineering_team
- - page:product_spec#workspace@workspace:engineering_team
- - database:task_list#workspace@workspace:engineering_team
- - template:weekly_report#workspace@workspace:sales_team
- - database:customer_list#workspace@workspace:sales_team
- - template:marketing_campaign#workspace@workspace:sales_team
- - page:project_plan#writer@user:frank
- - page:project_plan#reader@user:bob
- - database:task_list#editor@user:alice
- - database:task_list#viewer@user:bob
- - template:weekly_report#creator@user:alice
- - template:weekly_report#viewer@user:bob
- - page:product_spec#writer@user:david
- - page:product_spec#reader@user:eve
- - database:customer_list#editor@user:david
- - database:customer_list#viewer@user:eve
- - template:marketing_campaign#creator@user:david
- - template:marketing_campaign#viewer@user:eve
- - block:task_list_1#database@database:task_list
- - block:task_list_1#editor@user:alice
- - block:task_list_1#commenter@user:bob
- - block:task_list_2#database@database:task_list
- - block:task_list_2#editor@user:alice
- - block:task_list_2#commenter@user:bob
- - comment:task_list_1_comment_1#block@block:task_list_1
- - comment:task_list_1_comment_1#author@user:bob
- - comment:task_list_1_comment_2#block@block:task_list_1
- - comment:task_list_1_comment_2#author@user:charlie
- - comment:task_list_2_comment_1#block@block:task_list_2
- - comment:task_list_2_comment_1#author@user:bob
- - comment:task_list_2_comment_2#block@block:task_list_2
- - comment:task_list_2_comment_2#author@user:charlie
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "database:task_list"
- subject: "user:alice"
- assertions:
- write: true
- - entity: "page:product_spec"
- subject: "user:charlie"
- assertions:
- write: false
-```
-
-### Using Schema Validator in Local
-
-After cloning [Permify](https://github.com/Permify/permify), open up a new file and copy the **schema yaml file** content inside. Then, build and run Permify instance using the command `make serve`.
-
-
-
-Then run `permify validate {path of your schema validation file}` to start the test process.
-
-The validation result according to our example schema validation file:
-
-
-
-## Need any help ?
-
-This is the end of demonstration of the authorization structure for Facebook groups. To install and implement this see the [Set Up Permify](../../installation.md) section.
-
-If you need any kind of help, our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/modeling.md b/docs/versioned_docs/version-0.6.x/getting-started/modeling.md
deleted file mode 100644
index 0e3231f5..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/modeling.md
+++ /dev/null
@@ -1,608 +0,0 @@
----
-sidebar_position: 1
----
-
-# Modeling Authorization
-
-Permify was designed and structured as a true ReBAC solution, so besides roles and attributes Permify also supports indirect permission granting through relationships.
-
-With Permify, you can define that a user has certain permissions because of their relation to other entities. An example of this would be granting a manager the same permissions as their subordinates, or giving a user access to a resource because they belong to a certain group.
-
-This is facilitated by our relationship-based access control, which allows the definition of complex permission structures based on the relationships between users, roles, and resources.
-
-## Permify Schema
-
-Permify has its own language that you can model your authorization logic with it. The language allows to define arbitrary relations between users and objects, such as owner, editor, commenter or roles like admin, manager, member and also dynamic attributes such as boolean variables, IP range, time period, etc.
-
-
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. It includes set-algebraic operators such as intersection and union for specifying potentially complex access control policies in terms of those user-object relations.
-
-Here’s a simple breakdown of our schema.
-
-
-
-Permify Schema can be created on our [playground](https://play.permify.co/) as well as in any IDE or text editor. We also have a [VS Code extension](https://marketplace.visualstudio.com/items?itemName=Permify.perm) to ease modeling Permify Schema with code snippets and syntax highlights. Note that on VS code the file with extension is **_".perm"_**.
-
-## Developing a Schema
-
-This guide will show how to develop a Permify Schema from scratch with a simple example, yet it will show almost every aspect of our modeling language.
-
-We'll follow a simplified version of the GitHub access control system, where teams and organizations have control over the viewing, editing, or deleting access rights of repositories.
-
-Before start I want to share the full implementation of simple Github access control example with using Permify Schema.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = admin or member
- action delete = admin
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
- action edit = member or parent.admin
-
-}
-
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
- action push = owner or maintainer
- action read = org.admin and (owner or maintainer or org.member)
- action delete = parent.admin or owner
-
-}
-```
-
-:::info
-You can start developing Permify Schema on [VSCode]. You can install the extension by searching for **Perm** in the extensions marketplace.
-
-[vscode]: https://marketplace.visualstudio.com/items?itemName=Permify.perm
-
-:::
-
-## Defining Entities
-
-The very first step to build Permify Schema is creating your Entities. Entity is an object that defines your resources that held role in your permission system.
-
-Think of entities as tables in your database. We are strongly advice to name entities same as your database table name that its corresponds. In that way you can easily model and reason your authorization as well as eliminating the error possibility.
-
-You can create entities using `entity` keyword. Let's create some entities according to our example GitHub authorization logic."
-
-```perm
-entity user {}
-
-entity organization {}
-
-entity team {}
-
-entity repository {}
-```
-
-Entities has 2 different attributes. These are;
-
-- **relations**
-- **actions or permissions**
-
-## Defining Relations
-
-Relations represent relationships between entities. It's probably the most critical part of the schema because Permify mostly based on relations between resources and their permissions.
-
-Keyword **_relation_** need to used to create a entity relation with name and type attributes.
-
-**Relation Attributes:**
-
-- **name:** relation name.
-- **type:** relation type, basically the entity it’s related to (e.g. user, organization, document, etc.)
-
-An example relation takes form of,
-
-```perm
-relation [name] @[type]
-```
-
-Lets turn back to our example and define our relations inside our entities:
-
-#### User Entity
-
-→ The user entity is a mandatory entity in Permify. It generally will be empty but it will used a lot in other entities as a relation type to referencing users.
-
-```perm
-entity user {}
-```
-
-### Roles and User Types
-
-You can define user types and roles within the entity. If you specifically want to define a global role, such as `admin`, we advise defining it at the entity with the most global hierarchy, such as an organization. Then, spread it to the rest of the entities to include it within permissions.
-
-For the sake of simplicity, let's define only 2 user types in an organization, these are administrators and direct members of the organization.
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-```
-
-### Parent-Child Relationship
-
-→ Let's say teams can belong organizations and can have a member inside of it as follows,
-
-```perm
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity team {
-
- relation parent @organization
- relation member @user
-
-}
-```
-
-The parent relation is indicating the organization the team belongs to. This way we can achieve **parent-child relationship** within these entities.
-
-### Ownership
-
-In Github workflow, organizations and users can have multiple repositories, so each repository is related with an organization and with users. We can define repository relations as as follows.
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-}
-```
-
-The owner relation indicates the creator of the repository, that way we can achieve **ownership** in Permify.
-
-### Multiple Relation Types
-
-As you can see we have new syntax above,
-
-```perm
- relation maintainer @user @team#member
-```
-
-When we look at the maintainer relation, it indicates that the maintainer can be an `user` as well as this user can be a `team member`.
-
-:::info
-You can use **#** to reach entities relation. When we look at the `@team#member` it specifies that if the user has a relation with the team, this relation can only be the `member`. We called that feature locking, because it basically locks the relation type according to the prefixed entity.
-
-Actual purpose of feature locking is to giving ability to specify the sets of users that can be assigned.
-
-For example:
-
-```perm
- relation viewer @user
-```
-
-When you define it like this, you can only add users directly as tuples (you can find out what relation tuples is in next section):
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-
-However, if you define it as:
-
-```perm
- relation viewer @user @organization#member
-```
-
-You will then be able to specify not only individual users but also members of an organization:
-
-- organization:1#viewer@user:U1
-- organization:1#viewer@user:U2
-- organization:1#viewer@organization:O1#member
-
-You can think of these definitions as a precaution taken against creating undesired user set relationships.
-:::
-
-Defining multiple relation types totally optional. The goal behind it to improve validation and reasonability. And for complex models, it allows you to model your entities in a more structured way.
-
-## Defining Actions and Permissions
-
-Actions describe what relations, or relation’s relation can do. Think of actions as permissions of the entity it belongs. So actions defines who can perform a specific action on a resource in which circumstances.
-
-The basic form of authorization check in Permify is **_Can the user U perform action X on a resource Y ?_**.
-
-### Intersection and Exclusion
-
-The Permify Schema supports **`and`**, **`or`** and **`not`** operators to achieve permission **intersection** and **exclusion**. The keywords **_action_** or **_permission_** can be used with those operators to form rules for your authorization logic.
-
-#### Intersection
-
-Lets get back to our github example and create a read action on repository entity to represent usage of **`and`** &, **`or`** operators,
-
-```perm
-entity repository {
-
- relation parent @organization
-
- relation owner @user
- relation maintainer @user @team#member
-
-
- ..
- ..
-
- action read = org.admin and (owner or maintainer or org.member)
-
-}
-```
-
-→ If we examine the `read` action rules; user that is `organization admin` and following users can read the repository: `owner` of the repository, or `maintainer`, or `member` of the organization which repository belongs to.
-
-:::info Permission Keyword
-The same `read` can also be defined using the **permission** keyword, as follows:
-
-```perm
- permission read = org.admin and (owner or maintainer or org.member)
-```
-
-Using `action` and `permission` will yield the same result for defining permissions in your authorization logic. See why we have 2 keywords for defining an permission from the [Nested Hierarchies](#nested-hierarchies) section.
-:::
-
-#### Exclusion
-
-After this point, we'll move beyond the GitHub example and explore more advanced abilities of Permify DSL.
-
-Before delving into details, let's examine the **`not`** operator and conclude [Intersection and Exclusion](#intersection-and-exclusion) section.
-
-Here is the **post** entity from our sample [Instagram Authorization Structure](./examples/google-docs.md)example,
-
-```perm
-entity post {
- // posts are linked with accounts.
- relation account @account
-
- // comments are limited to people followed by the parent account.
- attribute restricted boolean
-
- ..
- ..
-
- // users can comment and like on unrestricted posts or posts by owners who follow them.
- action comment = account.following not restricted
- action like = account.following not restricted
-}
-```
-
-As you can see from the comment and like actions, a user tagged with the `restricted` attribute — details of defining attributes can be found in the [Attribute Based Permissions (ABAC)](#attribute-based-permissions-abac) section — won't be able to like or comment on the specific post.
-
-This is a simple example to demonstrate how you can exclude users, resources, or any subject from permissions using the **`not`** operator.
-
-### Permission Union
-
-Permify allows you to set permissions that are effectively the union of multiple permission sets.
-
-You can define permissions as relations to union all rules that permissions have. Here is an simple demonstration how to achieve permission union in our DSL, you can use actions (or permissions) when defining another action (or permission) like relations,
-
-```perm
- action edit = member or manager
- action delete = edit or org.admin
-```
-
-The `delete` action inherits the rules from the `edit` action. By doing that, we'll be able to state that only organization administrators and any relation capable of performing the edit action (member or manager) can also perform the delete action.
-
-Permission union is super beneficial in scenarios where a user needs to have varied access across different departments or roles.
-
-### Nested Hierarchies
-
-The reason we have two keywords for defining permissions (`action` and `permission`) is that while most permissions are based on actions (such as view, read, edit, etc.), there are still cases where we need to define permissions based on roles or user types, such as admin or member.
-
-Additionally, there may be permissions that need to be inherited by child entities. Using the `permission` keyword in these cases is more convenient and provides better reasoning of the schema.
-
-Here is a simple example to demonstrate inherited permissions.
-
-Let's examine a small snippet from our [Facebook Groups](./examples/google-docs.md) real world example. Let's create a permission called 'view' in the comment entity (which represents the comments of the post in Facebook Groups)
-
-Users can only view a comment if:
-
-- The user is the owner of that comment
-**or**
-- The user is a member of the group to which the comment's post belongs.
-
-```perm
-// Represents a post in a Facebook group
-entity post {
-
- ..
- ..
-
- // Relation to represent the group that the post belongs to
- relation group @group
-
- // Permissions for the post entity
-
- ..
- ..
- permission group_member = group.member
-}
-
-// Represents a comment on a post in a Facebook group
-entity comment {
-
- // Relation to represent the owner of the comment
- relation owner @user
-
- // Relation to represent the post that the comment belongs to
- relation post @post
- relation comment @comment
-
- ..
- ..
-
- // Permissions
- action view = owner or post.group_member
-
- ..
- ..
-}
-```
-
-The `post.group_member` refers to the members of the group to which the post belongs. We defined it as action in **post** entity as,
-
-```perm
-permission group_member = group.member
-```
-
-Permissions can be inherited as relations in other entities. This allows to form nested hierarchical relationships between entities.
-
-In this example, a comment belongs to a post which is part of a group. Since there is a **'member'** relation defined for the group entity, we can use the **'group_member'** permission to inherit the **member** relation from the group in the post and then use it in the comment.
-
-### Recursive ReBAC
-
-With Permify DSL, you can define recursive relationship-based permissions within the same entity.
-
-As an example, consider a system where there are multiple organizations within a company, some of which may have a parent-child relationship between them.
-
-As expected, organization members are also granted permission to view their organization details. You can model that as follows:
-
-```perm
-entity user {}
-
-entity organization {
- relation parent @organization
- relation member @user @organization#member
-
- action view = member or parent.member
-}
-```
-
-Let's extend the scenario by adding a rule allowing parent organization members to view details of child organizations. Specifically, a member of **Organization Alpha** could view the details of **Organization Beta** if **Organization Beta** belongs to **Organization Alpha**.
-
-
-
-First authorization schema that we provide won't solve this issue because `parent.member` accommodate single upward traversal in a hierarchy.
-
-Instead of `parent.member` we can call the parent view permission on the same entity - `parent.view` to achieve multiple levels of upward traversal, as follows:
-
-```perm
-entity user {}
-
-entity organization {
- relation parent @organization
- relation member @user @organization#member
-
- action view = member or parent.view
-}
-```
-
-This way, we achieve a recursive relationship between parent-child organizations.
-
-:::note
-*Credits to [Léo](https://github.com/LeoFVO) for the illustration and for [highlighting](https://github.com/Permify/permify/issues/790) this use case.*
-:::
-
-## Attribute Based Permissions (ABAC)
-
-To support Attribute Based Access Control (ABAC) in Permify, we've added two main components into our schema language: `attribute` and `rule`.
-
-### Defining Attributes
-
-Attributes are used to define properties for entities in specific data types. For instance, an attribute could be an IP range associated with an organization, defined as a string array:
-
-```perm
-attribute ip_range string[]
-```
-
-Here are the all attribute types that you use when defining an `attribute`.
-
-```perm
-// A boolean attribute type
-boolean
-
-// A boolean array attribute type.
-boolean[]
-
-// A string attribute type.
-string
-
-// A string array attribute type.
-string[]
-
-// An integer attribute type.
-integer
-
-// An integer array attribute type.
-integer[]
-
-// A double attribute type.
-double
-
-// A double array attribute type.
-double[]
-```
-
-### Defining Rules
-
-Rules are structures that allow you to write specific conditions for the model. You can think rules as simple functions of every software language have. They accept parameters and are based on condition to return a true/false result.
-
-In the following example schema, a rule could be used to check if a given IP address falls within a specified IP range:
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute ip_range string[]
-
- permission view = check_ip_range(request.ip, ip_range) or admin
-}
-
-rule check_ip_range(ip string, ip_range string[]) {
- ip in ip_range
-}
-```
-
-:::info Syntax
-We design our schema language based on [Common Expression Language (CEL)](https://github.com/google/cel-go). So the syntax looks nearly identical to equivalent expressions in C++, Go, Java, and TypeScript.
-
-Please let us know via our [Discord channel](https://discord.gg/n6KfzYxhPp) if you have questions regarding syntax, definitions or any operator you identify not working as expected.
-:::
-
-Let's examine some of common usage of ABAC with small schema examples.
-
-### Boolean - True/False Conditions
-
-For attributes that represent a binary choice or state, such as a yes/no question, the `Boolean` data type is an excellent choice.
-
-```perm
-entity post {
- attribute is_public boolean
-
- permission view = is_public
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts boolean as `FALSE`
-:::
-
-### Text & Object Based Conditions
-
-String can be used as attribute data type in a variety of scenarios where text-based information is needed to make access control decisions. Here are a few examples:
-
-- **Location:** If you need to control access based on geographical location, you might have a location attribute (e.g., "USA", "EU", "Asia") stored as a string.
-- **Device Type**: If access control decisions need to consider the type of device being used, a device type attribute (e.g., "mobile", "desktop", "tablet") could be stored as a string.
-- **Time Zone**: If access needs to be controlled based on time zones, a time zone attribute (e.g., "EST", "PST", "GMT") could be stored as a string.
-- **Day of the Week:** In a scenario where access to certain resources is determined by the day of the week, the string data type can be used to represent these days (e.g., "Monday", "Tuesday", etc.) as attributes!
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
-
- attribute location string[]
-
- permission view = check_location(request.current_location, location) or admin
-}
-
-rule check_location(current_location string, location string[]) {
- current_location in location
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts string as `""`
-:::
-
-### Numerical Conditions
-
-#### Integers
-
-Integer can be used as attribute data type in several scenarios where numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Age:** If access to certain resources is age-restricted, an age attribute stored as an integer can be used to control access.
-- **Security Clearance Level:** In a system where users have different security clearance levels, these levels can be stored as integer attributes (e.g., 1, 2, 3 with 3 being the highest clearance).
-- **Resource Size or Length:** If access to resources is controlled based on their size or length (like a document's length or a file's size), these can be stored as integer attributes.
-- **Version Number:** If access control decisions need to consider the version number of a resource (like a software version or a document revision), these can be stored as integer attributes.
-
-```perm
-entity content {
- permission view = check_age(request.age)
-}
-
-rule check_age(age integer) {
- age >= 18
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts integer as `0`
-:::
-
-#### Double - Precise numerical information
-
-Double can be used as attribute data type in several scenarios where precise numerical information is needed to make access control decisions. Here are a few examples:
-
-- **Usage Limit:** If a user has a usage limit (like the amount of storage they can use or the amount of data they can download), and this limit needs to be represented with decimal precision, it can be stored as a double attribute.
-- **Transaction Amount:** In a financial system, if access control decisions need to consider the amount of a transaction, and this amount needs to be represented with decimal precision (like $100.50), these amounts can be stored as double attributes.
-- **User Rating:** If access control decisions need to consider a user's rating (like a rating out of 5 with decimal points, such as 4.7), these ratings can be stored as double attributes.
-- **Geolocation:** If access control decisions need to consider precise geographical coordinates (like latitude and longitude, which are often represented with decimal points), these coordinates can be stored as double attributes.
-
-```perm
-entity user {}
-
-entity account {
- relation owner @user
- attribute balance double
-
- permission withdraw = check_balance(request.amount, balance) and owner
-}
-
-rule check_balance(amount double, balance double) {
- (balance >= amount) && (amount <= 5000)
-}
-```
-
-:::caution
-⛔ If you don’t create the related attribute data, Permify accounts double as `0.0`
-:::
-
-See more details on [Attribute Based Access Control](#attribute-based-permissions-abac) section to learn our approach on ABAC as well as how it operates in Permify. you can see more comprehensive ABAC examples in the [Example ABAC Use Cases](../use-cases/abac/#example-use-cases) section in related page.
-
-## More Comprehensive Examples
-
-You can check out more comprehensive schema examples from the [Real World Examples](../examples.md) section.
-
-Here is what each example focuses on,
-
-* [Google Docs]: how users can gain direct access to a document through **organizational roles** or through **inherited/nested permissions**.
-* [Facebook Groups]: how users can perform various actions based on the **roles and permissions within the groups** they belong.
-* [Notion]: how **one global entity (workspace) can manage access rights** in the child entities that belong to it.
-* [Instagram]: how **public/private attributes** play role in granting access to specific users.
-* [Mercury]: how **attributes and rules interact within the hierarchical relationships**.
-
-[Google Docs]:./examples/google-docs.md
-[Facebook Groups]:./examples/facebook-groups.md
-[Notion]:./examples/notion.md
-[Instagram]:./examples/instagram.md
-[Mercury]:./examples/mercury.md
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/sync-data.md b/docs/versioned_docs/version-0.6.x/getting-started/sync-data.md
deleted file mode 100644
index 07f0759f..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/sync-data.md
+++ /dev/null
@@ -1,480 +0,0 @@
----
-sidebar_position: 2
----
-
-import Tabs from '@theme/Tabs';
-import TabItem from '@theme/TabItem';
-
-# Managing Authorization Data
-
-Permify unifies your authorization data in a database of your preference, which serves as the single source of truth for all authorization queries and requests via the Permify API.
-
-In Permify, you can store authorization data in two different forms: as **relationships** and as **attributes**.
-
-Let's examine relationships first.
-
-## Access Control as Relationships
-
-In Permify, relationship between your entities, objects, and users builds up a collection of access control lists (ACLs).
-
-These ACLs called relational tuples: the underlying data form that represents object-to-object and object-to-subject relations. Each relational tuple represents an action that a specific user or user set can do on a resource and takes form of `user U has relation R to object O`, where user U could be a simple user or a user set such as team X members.
-
-In Permify, the simplest form of relational tuple structured as: `entity # relation @ user`. Here are some relational tuples with semantics,
-
-
-
-## Attributes
-
-Besides creating and storing your authorization-related data as relationships, you can also create attributes along with your resources and users.
-
-For certain use cases, using relationships (ReBAC) or roles (RBAC) might not be the best fit. For example, geo-based permissions where access is granted only if associated with a geographical or regional attribute. Or consider time-based permissions, restricting certain actions to office hours. A simpler scenario involves defining certain individuals as banned, filtering them out from access despite meeting other requirements.
-
-Attribute-Based Access Control takes a more contextual approach, allowing you to define access rights based on the context around subjects and objects in an application.
-
-In Permify, the form of attributes are similar to relational tuples but with a small syntax differentiation:
-
-`subject $ attribute | value`
-
-Here are some attributes with semantics,
-
-* `account:1$balance|double:4000` - account:1's balance is defined as 4000.
-* `post:546$is_restricted|boolean:true` - post:546 is labeled as restricted post within the system.
-* `user:122$regions|string[]:US,MEX` - user:122 is associated with regions United States and Mexico.
-
-## Where is the stored Authorization Data used?
-
-These relational tuples and attributes represents your authorization data.
-
-Permify stores your these data in a database you prefer. You can configure the database when running Permify Service with using both [configuration flags](../../installation/brew#configuration-flags) or [configuration YAML file](https://github.com/Permify/permify/blob/master/example.config.yaml).
-
-Stored data are queried and utilized in Permify APIs, including the check API, which is an access control check request used to determine whether a user's action is authorized.
-
-As an example; to decide whether a user could view a protected resource, Permify looks up the relations between that specific user and the protected resource. These relation types could be ownership, parent-child relation, a role such as an admin or manager or even an attribute.
-
-## Creating Authorization Data
-
-Relationships and attributes can be created with an simple API call, Since these attributes and relations are live instances, meaning they can be affected by specific user actions within the application, they should be created/deleted with a simple Permify API call at runtime.
-
-Each relational tuple or attribute should be created according to its authorization model, [Permify Schema].
-
-[Permify Schema]: ../modeling
-
-
-
-Let's follow a simple document management system example with the following Permify Schema to see how to create relation tuples.
-
-```perm
-entity user {}
-
-entity organization {
-
- relation admin @user
- relation member @user
-
-}
-
-entity document {
-
- relation owner @user
- relation parent @organization
- relation maintainer @user @organization#member
-
- action view = owner or parent.member or maintainer or parent.admin
- action edit = owner or maintainer or parent.admin
- action delete = owner or parent.admin
-}
-```
-
-According to the schema above; when a user creates a document in an organization, more specifically let's say, when user:1 create a document:2 we need to create the following relational tuple,
-
-- `document:2#owner@user:1`
-
-### Write Data API
-
-You can create relational tuples by using `Write Data API`.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "2",
- },
- Relation: "owner",
- Subject: & v1.Subject {
- Type: "user",
- Id: "1",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "2"
- },
- relation: "owner",
- subject: {
- type: "user",
- id: "1"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "2s"
- },
- "relation": "owner",
- "subject":{
- "type": "user",
- "id": "1",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Snap Tokens
-
-In Write Data API response you'll get a snap token of the operation.
-
-```json
-{
- "snap_token": "FxHhb4CrLBc="
-}
-```
-
-This token consists of an encoded timestamp, which is used to ensure fresh results in access control checks. We're suggesting to use snap tokens in production to prevent data inconsistency and optimize the performance. See more on [Snap Tokens](../reference/snap-tokens.md)
-
-## More Examples
-
-Let's create more example data according to the schema we defined above.
-
-### Organization Admin
-
-**relational tuple:** organization:1#admin@user:3
-
-**Semantics:** User 3 is administrator in organization 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "organization",
- Id: "1",
- },
- Relation: "admin",
- Subject: & v1.Subject {
- Type: "user",
- Id: "3",
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "organization",
- id: "1"
- },
- relation: "admin",
- subject: {
- type: "user",
- id: "3"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "organization",
- "id": "1"
- },
- "relation": "admin",
- "subject":{
- "type": "user",
- "id": "3",
- "relation": ""
- }
- }
- ]
-}'
-```
-
-
-
-### Parent Organization
-
-**Relational Tuple:** document:1#parent@organization:1#…
-
-**Semantics:** Organization 1 is parent of document 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "parent",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "1",
- Relation: "..."
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "parent",
- subject: {
- type: "organization",
- id: "1",
- relation: "..."
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "parent",
- "subject":{
- "type": "organization",
- "id": "1",
- "relation": "..."
- }
- }
- ]
-}'
-```
-
-
-
-:::info
-Note: `relation: “...”` used when subject type is different from **user** entity. **#…** represents a relation that does not affect the semantics of the tuple.
-
-Simply, the usage of ... is straightforward: if you're use user entity as an subject, you should not be using the `...` If you're using another subject rather than user entity then you need to use the `...`
-:::
-
-### Organization Members Are Maintainers in specific Doc
-
-**Created relational tuple:** document:1#maintainer@organization:2#member
-
-**Definition:** Members of organization 2 are maintainers in document 1.
-
-
-
-
-```go
-rr, err: = client.Data.Write(context.Background(), & v1.DataWriteRequest {
- TenantId: "t1",
- Metadata: &v1.DataWriteRequestMetadata {
- SchemaVersion: ""
- },
- Tuples: [] * v1.Tuple {
- {
- Entity: & v1.Entity {
- Type: "document",
- Id: "1",
- },
- Relation: "maintainer",
- Subject: & v1.Subject {
- Type: "organization",
- Id: "2",
- Relation: "member"
- },
- }
- },
-})
-```
-
-
-
-
-
-```javascript
-client.data.write({
- tenantId: "t1",
- metadata: {
- schemaVersion: ""
- },
- tuples: [{
- entity: {
- type: "document",
- id: "1"
- },
- relation: "maintainer",
- subject: {
- type: "organization",
- id: "2",
- relation: "member"
- }
- }]
-}).then((response) => {
- // handle response
-})
-```
-
-
-
-
-```curl
-curl --location --request POST 'localhost:3476/v1/tenants/{tenant_id}/data/write' \
---header 'Content-Type: application/json' \
---data-raw '{
- "metadata": {
- "schema_version": ""
- },
- "tuples": [
- {
- "entity": {
- "type": "document",
- "id": "1"
- },
- "relation": "maintainer",
- "subject":{
- "type": "organization",
- "id": "2",
- "relation": "member"
- }
- }
- ]
-}'
-```
-
-
-
-#### Test this Example on [Playground](https://play.permify.co/?s=bCDvst-22ISFR6DV90y8_)
-
-## Audit Logs For Permission Changes
-
-Permify does support audit logs for permission changes. Leveraging the [MVCC (Multi-Version Concurrency Control)](http://mbukowicz.github.io/databases/2020/05/01/snapshot-isolation-in-postgresql.html) pattern, we maintain a history of all permission data changes. This essentially provides an audit trail, allowing users to track alterations and when they occurred.
-
-In cloud version, our system supports change history auditing. It automatically generates and securely stores logs for all significant actions. These logs detail who made the change, what was changed, and when the change occurred. Furthermore, your system allows for easy searching and analysis of these logs, supporting automated alerting for suspicious activities. This comprehensive approach ensures thorough and effective auditing of all changes
-
-## Permission Baselining (Reviewing)
-
-We have a strong foundation for permission baselining and review, thanks to MVCC.
-
-**Historical Review:** You can review the history of permissions changes as each version is stored. This enables retrospective audits and analysis.
-
-**Current State Review:** You can review the current state of permissions by examining the latest versions of each permission setting.
-
-**Cleanup:** Your system incorporates a garbage collector for managing old data, which helps keep your permissions structure clean and optimized.
-
-## Next
-
-Let's now head over to the **Access Control Check** section and learn how to perform access control in Permify to ensure that only authorized users have the right level of access to our resources.
diff --git a/docs/versioned_docs/version-0.6.x/getting-started/testing.md b/docs/versioned_docs/version-0.6.x/getting-started/testing.md
deleted file mode 100644
index 977fcf2d..00000000
--- a/docs/versioned_docs/version-0.6.x/getting-started/testing.md
+++ /dev/null
@@ -1,279 +0,0 @@
----
-sidebar_position: 4
----
-
-# Testing & Validation
-
-Testing is critical process when building and maintaining an authorization system. This page explains how to ensure the new authorization model and related authorization data works as expected in Permify.
-
-Assuming that you're familiar with creating an authorization model and forming relation tuples in Permify. If not, we're strongly advising you to examine them before testing.
-
-We provide a GitHub action repository called [permify-validate-action] for testing and validation. This repository runs the Permify validate command on the created schema validation yaml file that consists of schema (authorization model) and relationships (sample authorization data) and assertions (sample check queries and results).
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [related page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Adding Validate Action To Your Workflow
-
-After adding [permify-validate-action] to your Github Action workflow, you need to define the schema validation yaml file as,
-
-- **With local file:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "test.yaml"
-```
-
-- **With external url:**
-```yaml
-steps:
-- uses: "permify/permify-validate-action@v1.0.0"
- with:
- validationFile: "https://gist.github.com/permify-bot/bb8f95acb64525d2a41688ae0a6f4274"
-```
-
-:::info
-If you don't know how to create Github action workflow and add a action to it, you can examine [quickstart page](https://docs.github.com/en/actions/quickstart) on Github docs.
-:::
-
-## Schema Validation File
-
-Below you can examine an example schema validation yaml file. It consists 3 parts;
-- `schema` which is the authorization model you want to test,
-- `relationships` sample data to test your model,
-- `scenarios` to test access check queries within created scenarios.
-
-### Defining the Schema:
-
-You can define the `schema` in the YAML file in one of two ways:
-
-1. **Directly in the File:** Define the schema directly within the YAML file.
-
- ```yaml
- schema: >-
- entity user {}
- entity organization {
- ...
- }
-
-2. **Via URL or File Path:** Specify a URL or a file path to an external schema file.
- **Example with URL:**
-
- ```yaml
- schema: https://example.com/path/to/schema.txt
- ```
-
- **Example with File Path:**
- ```yaml
- schema: /path/to/your/schema/file.txt
- ```
-
-Here is an example Schema Validation file,
-
-```yaml
-schema: >-
- entity user {}
-
- entity organization {
-
- relation admin @user
- relation member @user
-
- action create_repository = (admin or member)
- action delete = admin
- }
-
- entity repository {
-
- relation owner @user @organization#member
- relation parent @organization
-
- action push = owner
- action read = (owner and (parent.admin and parent.member))
- action delete = (parent.member and (parent.admin or owner))
- action edit = parent.member not owner
- }
-
-relationships:
- - "organization:1#admin@user:1"
- - "organization:1#member@user:1"
- - "repository:1#owner@user:1"
- - "repository:2#owner@user:2"
- - "repository:2#owner@user:3"
- - "repository:1#parent@organization:1#..."
- - "organization:1#member@user:43"
- - "repository:1#owner@user:43"
-
-scenarios:
- - name: "scenario 1"
- description: "test description"
- checks:
- - entity: "repository:1"
- subject: "user:1"
- assertions:
- push : true
- owner : true
- - entity: "repository:2"
- subject: "user:1"
- assertions:
- push : false
- - entity: "repository:3"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- assertions:
- push : true
- - entity: "repository:1"
- subject: "user:43"
- assertions:
- edit : false
- entity_filters:
- - entity_type: "repository"
- subject: "user:1"
- context:
- - "repository:3#owner@user:1"
- - "repository:4#owner@user:1"
- - "repository:5#owner@user:1"
- assertions:
- push : ["1", "3", "4", "5"]
- edit : []
- subject_filters:
- - subject_reference: "user"
- entity: "repository:1"
- context:
- - "organization:1#member@user:58"
- assertions:
- push : ["1", "43"]
- edit : ["58"]
-```
-
-Assuming that you're well-familiar with the `schema` and `relationships` sections of the above YAML file. If not, please see the previous sections to learn how to create an authorization model (schema) and generate data (relationships) according to it.
-
-We'll continue by examining how to create scenarios.
-
-## Creating Test Scenarios
-
-You can create multiple access checks at once to test whether your authorization logic behaves as expected or not.
-
-Besides simple access checks you can also test subject filtering queries and data (entity) filtering with it.
-
-Let's deconstruct the `scenarios`,
-
-### Scenarios
-
-```js
-scenarios:
- - name: // name of the scenario
- description: // description of the scenario
- checks: // simple access check case/cases
- entity_filters: // entity (data) filtering query/queries
- subject_filters: // subject filtering query/queries
-```
-
-### Access Check
-
-You can create `check` inside `scenarios` to test multiple access check cases,
-
-```js
-checks:
- - entity: "repository:3" // resource/entity that you want to check access for
- subject: "user:1" // subject that performs the access check
- context: // additional data provided during an access check to be evaluated
- - "repository:3#owner@user:1"
- assertions: // expected result/results for specific action/s or an permission/s.
- push : true
-```
-
-Semantics for above check is: whether `user:1` can push to `repository:3`, additional to stored tuples take account that user:1 is owner of repository:3 (`repository:3#owner@user:1`). Expected result for that check it **true** - `push : true`
-
-:::info Contextual Tuples
-We use `context` (Contextual Tuples) with simple relational tuples for simplicity in this example. However, it is primarily used for dynamic access checks, such as those involving time, date, or IP address, etc.
-
-To learn more about how `context` works, see the [Contextual Tuples](../../reference/contextual-tuples) section.
-:::
-
-### Entity Filtering
-
-You can create `entity_filters` within `scenarios` to test your data filtering queries.
-
-```js
-entity_filters:
- - entity_type: "repository" // entity that you want to filter
- subject: "user:1" // subject that you want to perform data filtering
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "3", "4", "5"] // IDs of the resources that we expected to return
- edit : []
-```
-
-The major difference between `check` lies in the assertions part. Since we're performing data filtering with bulk data, instead of a true-false result, we enter the IDs of the resources that we expect to be returned
-
-### Subject Filtering
-
-You can create `subject_filters` within `scenarios` to test your subject filtering queries, a.k.a which users can perform action Y or have permission X on entity:Z?
-
-```js
-- subject_reference: "user"
- entity: "repository:1"
- context: null // additional data provided during an access check to be evaluated
- assertions:
- push : ["1", "43"] // IDs of the users that we expected to return
- edit : ["58"]
-```
-
-:::info API Endpoints
-You can find the related API endpoints for `check`, `entity_filters`, and `subject_filters` in the Permission service in the [Using The API](../../api-overview) section.
-:::
-
-## Coverage Analysis
-
-By using the command `permify coverage {path of your schema validation file}`, you can measure the coverage for your schema.
-
-The coverage is calculated by analyzing the relationships and assertions in your created model, identifying any missing elements.
-
-The output of the example provided above is as follows.
-
-
-
-## Testing in Local
-
-You can also test your new authorization model in your local (Permify clone) without using [permify-validate-action] at all.
-
-For that open up a new file and add a schema yaml file inside. Then build your project with, run `make build` command and run `./permify validate {path of your schema validation file}`.
-
-If we use the above example schema validation file, after running `./permify validate {path of your schema validation file}` it gives a result on the terminal as:
-
-
-
-[permify-validate-action]: https://github.com/Permify/permify-validate-action
-
-## AST Conversion
-
-By utilizing the command `permify ast {path of your schema validation file}`, you can effortlessly convert your model into an Abstract Syntax Tree (AST) representation.
-
-The conversion to AST provides a structured representation of your model, making it easier to navigate, modify, and analyze. This process ensures that your model is syntactically correct and can be processed by other tools without issues.
-
-The output after running the above example command is illustrated below.
-
-
-
-
-## Unit Tests For Schema Changes
-
-We recommend leveraging Permify's in-memory databases for a simplified and isolated testing environment. These in-memory databases can be easily created and disposed of for each individual unit test, ensuring that your tests do not interfere with each other and each one starts with a clean slate.
-
-For managing permission/relation changes, we suggest storing schema in an abstracted place such as a git repo and centrally checking and approving every change before deploying it via the CI pipeline that utilizes the **Write Schema API**.
-
-We recommend adding our [schema validator](https://github.com/Permify/permify-validate-action) to the pipeline to ensure that any changes are automatically validated.
-
-You can find more details about our suggested workflow to handle schema changes in [Write Schema](../../api-overview/schema/write-schema#suggested-workflow-for-schema-changes) section.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about it, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
-
diff --git a/docs/versioned_docs/version-0.6.x/installation.md b/docs/versioned_docs/version-0.6.x/installation.md
deleted file mode 100644
index c428e1f5..00000000
--- a/docs/versioned_docs/version-0.6.x/installation.md
+++ /dev/null
@@ -1,17 +0,0 @@
----
-id: installation
-title: Setup Permify
-slug: /installation
----
-
-# Setup Permify
-
-Here is some options that you can use to set up and deploy Permify in your servers.
-
-```mdx-code-block
-import {CardList} from '../../src/components/Card';
-
-
-```
-
-If your deployment preference is not listed above, please let us know by joining our [Discord Community](https://discord.gg/n6KfzYxhPp)!
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/installation/_category_.json b/docs/versioned_docs/version-0.6.x/installation/_category_.json
deleted file mode 100644
index 24b32a32..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Set Up Permify",
- "position": 3,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/installation/aws.md b/docs/versioned_docs/version-0.6.x/installation/aws.md
deleted file mode 100644
index c1c204d9..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/aws.md
+++ /dev/null
@@ -1,187 +0,0 @@
----
-title: AWS ECS, ECR & EC2
----
-
-# Deploy on AWS ECS, ECR & EC2
-
-AWS is a piece of cake no one ever said! That’s why today we’re bringing this tutorial to help you deploy Permify in AWS.
-
-There are many ways to deploy and use Permify in AWS. Today we’ll start with Elastic Container Service (ECS).
-
-ECS is a container management service. You can run your containers as task definitions, and It’s one of the easiest ways to deploy containers.
-
-If you’d like to watch this tutorial rather than reading. Here’s the video version.
-
-
-
-There is no prerequisite in this tutorial. You can simply deploy permify by following this step-by-step guide. However, if you want to integrate more advanced AWS security & networking features, we’ll follow up with a new tutorial guideline.
-
-At the end of this tutorial you’ll be able to;
-
-1. [Create a security group](#create-an-ec2-security-group)
-2. [Creating and configuring ECS Clusters](#2-creating-an-ecs-cluster)
-3. [Creating and defining task definitions](#3-creating-and-running-task-definitions)
-4. [Running our task definition](#4-running-our-task-definition)
-
-## 1. Create an EC2 Security Group
-
-So first thing first, let’s go over into security groups and create our security group. We’ll need this security group while creating our cluster.
-
-
-
-Search for “Security Groups” in the search bar. And go to the EC2 security groups feature.
-
-
-
-Then start creating a new security group.
-
-
-
-You have to name your security group, and give a description. Also, you need to choose the same VPC that you’ll going to use in EC2. So, I choose the default one. And I’m going to use same one while creating the ECS cluster.
-
-The next step is to configure our inbound rules. Here’s the configuration;
-
-```json
-//for mapping HTTP request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for mapping RPC request port.
-type = "Custom TCP", protocol = "TCP", port_range = "3478",source = "Anywhere", ::/0
-
-type = "Custom TCP", protocol = "TCP", port_range = "3476",source = "Anywhere", 0.0.0.0/0
-
-//for using SSH for connecting from your local computer.
-type = "Custom TCP", protocol = "TCP", port_range = "22",source = "Anywhere", 0.0.0.0/0
-```
-
-We have configured the HTTP and RPC ports for Permify. Also, we added port “22” for SSH connection. So, we can connect to EC2 through our local terminal.
-
-Now, we’re good to go. You can create the security group. And it’s ready to use in our ECS.
-
-## 2. Creating an ECS cluster
-
-
-
-The next step is to create an ECS cluster. From your AWS console search for Elastic Container Service or ECS for short.
-
-
-
-Then go over the clusters. As you can see there are 2 types of clusters. One is for ECS and another for EKS. We need to use ECS, EKS stands for Elastic Kubernetes Service. Today we’re not going to cover Kubernetes.
-
-Click **“Create Cluster”**
-
-
-
-Let’s create our first Cluster. Simply you have 3 options; Serverless(Network Only), Linux, and Windows. We’re going to cover EC2 Linux + Networking option.
-
-
-
-The next step is to configure our Cluster, starting with your Cluster name. Since we’re deploying Permify, I’ll call it “permify”.
-
-Then choose your instance type. You can take a look at different instances and pricing from [here](https://aws.amazon.com/ec2/pricing/on-demand/). I’m going with the t4 large. For cost purposes, you can choose t2.micro if you’re just trying out. It’s free tier eligible.
-
-Also, if you want to connect this EC2 instance from your local computer. You need to use SSH. Thus choose a key pair. If you have no such intention, leave it “none”.
-
-
-
-Now, we need to configure networking. First, choose your VPC, we use the default VPC as we did in the security groups. And choose any subnet on that VPC.
-
-You want to enable auto-assigned IP to make your app reachable from the internet.
-
-Choose the security group we have created previously.
-
-And voila, you can create your cluster. Now, we need to run our container in this cluster. To do that, let’s go over task definitions. And create our container definition.
-
-## 3. Creating and running task definitions
-
-Go over to ECS, and click the task definitions.
-
-
-
-And create a new task definition.
-
-
-
-Again, you’re going to ask to choose between; FARGATE, EC2, and EXTERNAL (On-premise). We’ll continue with EC2.
-
-Leave everything in default under the “Configure task and container definitions” section.
-
-
-
-Under the IAM role section you can choose “ecsTaskExecutionRole” if you want to use Cloud Watch later.
-
-You can leave task size in default since it’s optional for EC2.
-
-The critical part over here is to add our container. Click on the “Add Container” button.
-
-
-
-Then we need to add our container details. First, give a name. And then the most important part is our image URI. Permify is registered on the Github Registry so our image is;
-
-```yaml
-ghcr.io/permify/permify:latest
-```
-
-Then we need to define memory limit for the container, I went with 1024. You can define as much as your instance allows.
-
-Next step is to mapping our ports. As we mentioned in security groups, Permify by default listens;
-
-- `3476 for HTTP port`
-- `3478 for RPC port`
-
-
-
-Then we need to define command under the environment section. So, in order to start permify we first need to add “serve” command.
-
-For using properly we need a few other. Here’s the commands we need.
-
-```yaml
-serve, --database-engine=postgres, --database-uri=postgres://:@:/, --database-pool-max=20
-```
-
-- `serve` ⇒ for starting the Permify.
-- `--database-engine=postgres` ⇒ for defining the db we use.
-- `--database-uri=postgres://:password@:/` ⇒ for connecting your database with URI.
-- `--database-pool-max=20` ⇒ the depth for running in graph.
-
-We’re nice and clear, add the container and then just create your task definition. We’ll use this definition to run in our cluster.
-
-So, let’s go over and run our task definition.
-
-## 4. Running our task definition
-
-
-
-Let’s go to ECS and enter into our cluster. And go over into the tasks to run our task.
-
-
-
-Click to “Run new Task”
-
-
-
-Choose EC2 as a launch type. Then pick the task definition we just created. And leave everything else in the default. You can run your task now.
-
-We have just deployed our container into EC2 instance with ECS. Let’s test it.
-
-Now you can go over into EC2, and click on the running instances. Find the instance named `ECS Instance - EC2ContainerService-` in the running instances.
-
-
-
-Copy the Public IPv4 DNS from the right corner, and paste it into your browser. But you need to add `:3476` to access our http endpoint. So it should be like this;
-
-`:3476`
-
-and if you add healthz at the end like this;
-
-`:3476/healthz`
-
-you should get Serving status :)
-
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/installation/azure.md b/docs/versioned_docs/version-0.6.x/installation/azure.md
deleted file mode 100644
index 7f32ade5..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/azure.md
+++ /dev/null
@@ -1,7 +0,0 @@
----
-title: Azure CR & Application Service
----
-
-# Deploy on Azure CR, & Application Service
-
-## TO:DO
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/installation/brew.md b/docs/versioned_docs/version-0.6.x/installation/brew.md
deleted file mode 100644
index 0212df8b..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/brew.md
+++ /dev/null
@@ -1,66 +0,0 @@
----
-title: "Install with Brew"
----
-
-# Brew With Configurations
-
-This section shows how to install and run Permify Service using brew.
-
-### Install Permify
-
-Open terminal and run the following line,
-
-```shell
-brew install permify/tap/permify
-```
-
-### Run Permify Service
-
-To run the Permify Service, `permify serve` command should be run.
-
-By default, the service is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather then an actual database. You can override these by running the command with configuration flags.
-
-### Configure By Using Flags
-
-See all the configuration flags by running,
-
-```shell
-permify serve --help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Configure With Using Config File
-
-You can also configure Permify Service by using a configuration file.
-
-```shell
- permify serve -c=config.yaml
-```
-
-or
-
-```shell
- permify serve --config=config.yaml
-```
-
-### Test your connection.
-
-You can test your connection by making an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../../api-overview/
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with a Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/installation/container.md b/docs/versioned_docs/version-0.6.x/installation/container.md
deleted file mode 100644
index aa0b7686..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/container.md
+++ /dev/null
@@ -1,55 +0,0 @@
----
-title: "Docker Container"
----
-
-# Run using Docker
-
-This section shows how to run Permify using our docker container. You can run Permify using Docker with following command.
-
-## Run in a terminal
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 -v {YOUR-CONFIG-PATH}:/config ghcr.io/permify/permify serve
-```
-
-This will start a Permify server with the configuration that is in **{YOUR-CONFIG-PATH}**.
-
-### Configure with a YAML file
-
-This config path - `{YOUR-CONFIG-PATH}` - should contain the [config yaml file](../reference/configuration.md), where you can configure the Permify Server as well as define the ***database*** to store your authorization related data in.
-
-:::info Talk to an Permify Engineer
-By default, the container is configured to listen on ports 3476 (HTTP) and 3478 (gRPC) and store the authorization data in memory rather than an actual database.
-:::
-
-### Configure Using Flags
-
-Alternatively, you can set configuration options using flags when running the command. See all the configuration flags by running,
-
-```shell
-docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serve -help
-```
-
-:::info Environment Variables
-In addition to CLI flags, Permify also supports configuration via environment variables. You can replace any flag with an environment variable by converting dashes into underscores and prefixing with PERMIFY_ (e.g. **--log-level** becomes **PERMIFY_LOG_LEVEL**).
-:::
-
-### Test your connection.
-
-You can test your connection by making an HTTP GET request,
-
-```shell
-localhost:3476/healthz
-```
-
-You can use our Postman Collection to work with the API. Also see the [Using the API] section for details of core functions.
-
-[Using the API]: ../api-overview.md
-
-[](https://www.postman.com/permify-dev/workspace/permify/collection)
-[](https://permify.github.io/permify-swagger/)
-
-
-### Need any help ?
-
-Our team is happy to help you get started with Permify, [schedule a call with a Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/installation/google.md b/docs/versioned_docs/version-0.6.x/installation/google.md
deleted file mode 100644
index deb30dc9..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/google.md
+++ /dev/null
@@ -1,271 +0,0 @@
----
-title: Deploy on Google Compute Engine
----
-
-This guide outlines the process of deploying Permify, on Google Compute Engine. The steps include setting up Google Cloud SDK and kubectl, managing containers using Google Kubernetes Engine (GKE), deploying Permify, and implementing Permify in a distributed configuration with Serf. By following these steps, you can efficiently deploy Permify on Google's scalable and secure infrastructure.
-
-## Google Cloud SDK Install
-
-1. At the command line, run the following command:
-
- ```bash
- curl https://sdk.cloud.google.com | bash
- ```
-
-2. When prompted, choose a location on your file system (usually your Home directory) to create the `google-cloud-sdk` subdirectory under.
-3. If you want to send anonymous usage statistics to help improve gcloud CLI, answer `Y` when prompted.
-4. To add gcloud CLI command-line tools to your `PATH` and enable command completion, answer `Y` when prompted
-5. Restart your shell:
-
- ```bash
- exec -l $SHELL
- ```
-
-6. To initialize the Google Cloud CLI environment, run `gcloud init`
-
-## Install kubectl
-
-1. Install the `kubectl` component:
-
- ```bash
- gcloud components install kubectl
- ```
-
-2. Verify that `kubectl` is installed:
-
- ```bash
- kubectl version
- ```
-
-3. Install Authn Plug-in
-
- ```bash
- gcloud components install gke-gcloud-auth-plugin
- ```
-
- Check the `gke-gcloud-auth-plugin` binary version:
-
- ```bash
- gke-gcloud-auth-plugin --version
- ```
-
-
-## Create Containers with GKE
-
-1. Login & Initialize Google Cloud CLI
-
- ```bash
- gcloud init
- ```
-
-2. Follow configuration instructions
-3. Create Container Cluster
-
- ```bash
- gcloud container clusters create [CLUSTER_NAME]
- ```
-
-4. Authenticate the cluster
-
- ```bash
- gcloud container clusters get-credentials [CLUSTER_NAME]
- ```
-
-
-## Deploy Permify
-
-1. Apply deployment config
-
- ```bash
- kubectl apply -f deployment.yaml
- ```
-
- - **Deployment.yaml**
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- labels:
- app: permify
- name: permify
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
- status: {}
- ```
-
-2. Apply service manfiest
-
- ```bash
- kubectl apply -f service.yaml
- ```
-
- - **Service Manifest**
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
- status:
- loadBalancer: {}
- ```
-
-
-## Deploying Permify in a Distributed Configuration
-
-If you aim to deploy Permify in a distributed configuration, you will need to create a Serf deployment. The Serf deployment can be dockerized to our Container Registry under the name permify/serf:v1.0, which is provided by Hashicorp.
-
-Please note: It is crucial to ensure that both Serf and Permify deployments reside within the same namespace for proper operation.
-
-1. Serf Service Create:
- - Serf Deployment&Service yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: serf-deployment
- spec:
- replicas: 1
- selector:
- matchLabels:
- app: serf
- template:
- metadata:
- labels:
- app: serf
- spec:
- containers:
- - name: serf
- image: permify/serf:v1.0
- args:
- - "-node=main-serf"
- ports:
- - containerPort: 7946
- resources:
- requests:
- cpu: 100m
- memory: 128Mi
- limits:
- cpu: 200m
- memory: 256Mi
- ---
- apiVersion: v1
- kind: Service
- metadata:
- name: serf
- spec:
- selector:
- app: serf
- ports:
- - protocol: TCP
- port: 7946
- targetPort: 7946
- name: serf
- type: ClusterIP
- ```
-
-2. Apply Deployment Manifest
- - Deployment.yaml
-
- ```yaml
- apiVersion: apps/v1
- kind: Deployment
- metadata:
- name: permify-deployment
- spec:
- replicas: 3
- selector:
- matchLabels:
- app: permify
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: permify/permify:tagname
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://user:password@host:5432/db_name"
- - "--database-max-open-connections=20"
- - "--distributed-enabled=true"
- - "--distributed-node=serf:7946"
- - "--distributed-node-name=main-serf"
- - "--distributed-protocol=serf"
- resources:
- requests:
- memory: "128Mi"
- cpu: "200m"
- limits:
- memory: "128Mi"
- cpu: "400m"
- ports:
- - containerPort: 3476
- name: permify-port
- - containerPort: 7946
- name: permify-dist
- - containerPort: 6060
- name: permify-pprof
- ```
-
-3. Apply Service Manifest
- - Service.yaml
-
- ```yaml
- apiVersion: v1
- kind: Service
- metadata:
- name: permify
- spec:
- ports:
- - name: permify-port
- port: 3476
- targetPort: 3476
- - name: permify-dist
- port: 7946
- targetPort: 7946
- selector:
- app: permify
- type: LoadBalancer
- ```
-
-
-## Need any help ?
-
-Our team is happy to help you to deploy Permify, [schedule a call with an Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/installation/kubernetes.md b/docs/versioned_docs/version-0.6.x/installation/kubernetes.md
deleted file mode 100644
index f2a1e21b..00000000
--- a/docs/versioned_docs/version-0.6.x/installation/kubernetes.md
+++ /dev/null
@@ -1,173 +0,0 @@
----
-title: Kubernetes Cluster
----
-
-# Deploy on Kubernetes Cluster
-
-In this section we’re going to deploy Permify in AWS EKS which is Amazon Elastic Kubernetes Service. EKS is a managed service that you can easily run Kubernetes in AWS.
-
-Here’s what we’re going to do step-by-step;
-
-1. [Configure our AWS IAM credentials](#configure-aws-cli-with-your-iam-account)
-3. [Create EKS cluster and configure nodes](#creating-an-aws-eks-cluster)
-4. [Deploy Permify to nodes](#deploying--running-permify-in-nodes)
-
-There are a couple of small prerequisites for this tutorial.
-
-### Pre-requisites
-
-- An AWS account.
-- The AWS Command Line Interface (CLI) is installed and configured on your local machine. — [Click here](https://us-east-1.console.aws.amazon.com/iamv2/home?region=us-east-1#/home) to go to IAM
-- The AWS IAM Authenticator for Kubernetes is installed and configured on your local machine.
-
-## Configure AWS CLI with your IAM account.
-
-The first step is to configure our AWS IAM account into our local terminal so that we can run commands. Most of you probably have a configured AWS account if you ever set up anything into AWS programmatically, so you can skip this. If you don’t follow these steps.
-
-### Create an AWS IAM Programmatic Access Account
-
-First, let’s create IAM credentials for ourselves. Search IAM from the AWS console. You need to write down the account ID if you want to log in AWS console with this account as well. Let’s go over users and start creating our credentials.
-
-
-
-At Users screen click to “Add users” — and you’ll end up in your first screen creating user credentials. Here you can define the name of the user. Also there 2 options that you can choose simultaneously.
-
-But you must choose “Access key - Programmatic access” option. It’ll allow us to configure our AWS CLI on our local machine.
-
-You can also choose “Password - AWS Management Console access” if you want to log in to this account through the console. But you’ll need the Account ID that I mentioned in the IAM console screen.
-
-In the next screen, you’ll be asked to create or copy the user-set permissions. For this tutorial, you’ll only need to access EKS resources and features. So lets create group by clicking the “Create group” — and then at pop-up screen search for EKS.
-
-
-
-I’ll choose all EKS permissions but if you have certain policies internally, just stick with them. You’ll only need following permission to;
-
-- `AmazonEKSClusterPolicy`
-- `AmazonEKSServicePolicy`
-- `AmazonEKSVPCResourceController`
-- `AmazonEKSWorkerNodePolicy`
-
-Then simply you can review and create the user.
-
-
-
-Once you created the credentials you’ll prompt the “Access key ID” and “Secret access key”, you should save this down somewhere. We’re going the use these to configure our local machine with AWS CLI.
-
-### **Configure AWS CLI with your IAM account**
-
-Let’s open our local terminal
-
-```jsx
-aws configure
-```
-
-Next you’ll ask for the following credentials;
-
-- `AWS Access Key ID`
-- `AWS Secret Access Key`
-- `Default region name`
-- `Default output format` (leave it empty)
-
-## Creating an AWS EKS Cluster
-
-For the first step, we need to install [eksctl](https://eksctl.io/) — which is like kubectl but for AWS EKS. It helps us to set up and deploy our cluster and nodes within a fraction of the time.
-
-Let’s download eksctl using brew.
-
-
-```jsx
-brew tap weaveworks/tap
-```
-
-While installing the eksctl, we’ll end up getting kubectl and other dependencies.
-
-```jsx
-brew install weaveworks/tap/eksctl
-```
-
-Now, we’re ready to create our EKS cluster. You can define certain things while deploying standard the cluster beside the name and version like; the region you want to deploy, the EC2 instance type of each node, and the number of nodes you want to run.
-
-```bash
-eksctl create cluster \
---name \
---version 1.24 \
---region \
---nodegroup-name permify \
---node-type t2.small \
---nodes 2
-```
-
-## Deploying & Running Permify in Nodes
-
-The next stop is applying our manifests which will help us to deploy and configure our container/Permify.
-
-Let’s create our deployment manifest first.
-
-```yaml
-apiVersion: apps/v1
-kind: Deployment
-metadata:
- labels:
- app: permify
- name: permify
-spec:
- replicas: 2
- selector:
- matchLabels:
- app: permify
- strategy:
- type: Recreate
- template:
- metadata:
- labels:
- app: permify
- spec:
- containers:
- - image: ghcr.io/permify/permify
- name: permify
- args:
- - "serve"
- - "--database-engine=postgres"
- - "--database-uri=postgres://postgres:nOcodeSTIAnLAba@permify-test.ceuo5kqsxyea.us-east-1.rds.amazonaws.com:5432/demo"
- - "--database-max-open-connections=20"
- ports:
- - containerPort: 3476
- protocol: TCP
- resources: {}
- restartPolicy: Always
-status: {}
-```
-
-Now let’s apply our deployment manifest
-
-```jsx
-kubectl apply -f deployment.yaml
-```
-
-The next step is to create a service manifest, this will allow us to configure our container app.
-
-```jsx
-apiVersion: v1
-kind: Service
-metadata:
- name: permify
-spec:
- ports:
- - name: 3476-tcp
- port: 3476
- protocol: TCP
- targetPort: 3476
- selector:
- app: permify
- type: LoadBalancer
-status:
- loadBalancer: {}
-```
-
-Let’s apply service.yaml to our nodes.
-
-```jsx
-kubectl apply -f service.yaml
-```
-
-Last but not least, we can check our pods & nodes. And we can start using the container with load balancer
\ No newline at end of file
diff --git a/docs/versioned_docs/version-0.6.x/permify-overview/_category_.json b/docs/versioned_docs/version-0.6.x/permify-overview/_category_.json
deleted file mode 100644
index 0f0135be..00000000
--- a/docs/versioned_docs/version-0.6.x/permify-overview/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "First Glance",
- "position": 1,
- "collapsed": false
-}
diff --git a/docs/versioned_docs/version-0.6.x/permify-overview/authorization-service.md b/docs/versioned_docs/version-0.6.x/permify-overview/authorization-service.md
deleted file mode 100644
index 55a6906d..00000000
--- a/docs/versioned_docs/version-0.6.x/permify-overview/authorization-service.md
+++ /dev/null
@@ -1,40 +0,0 @@
-
-# Authorization As A Service
-
-An authorization service is a module that allows you to manage access to your application and ease the development and maintenance of your authorization system. It works in run time and respond to all authorization questions from any of your apps.
-
-
-
-[Permify] is a fully open source **authorization service** that offers a variety of binding and crafting options to secure your applications. It's designed to be deployed as a authorization service rather than a library compiled into an application.
-
-[Permify]: https://github.com/Permify/permify
-
-## Benefits of using an Authorization Service
-
-### Move & Iterate Faster
-Avoid the hassle of building your a new authorization system, save time and money by leveraging existing, battle-tested code that has been developed by a team rather than starting from scratch. You can get started quickly with a simple API that you can easily integrate into your application to move and iterate faster.
-
-### Scale As You Wish
-Permify based on [Google Zanzibar], which is the global authorization system used at Google for handling authorization for hundreds of its services and products including; YouTube, Drive, Calendar, Cloud and Maps. Building a scalable and robust authorization system is hard and needs a quite engineering time. Zanzibar system achieved more than 95% of the access checks responded in 10 milliseconds and has maintained more than 99.999% availability for the 3 year period. Permify applies proven techniques that Google used. We’re trying to make Zanzibar available to everyone to use and benefit in their applications and services.
-
-[Google Zanzibar]: https://permify.co/post/google-zanzibar-in-a-nutshell/
-
-### Gain Visibility Across Teams
-Enterprise-grade authorizations require robust and fine-grained permissions as well as being able to observe and work on these permissions as a group. Yet, code-level authorization logic and distributed authorization data among multiple services make it harder to change permissions and keep them up to date all the time. Permify is designed to abstract authorization logic from your code and make authorization available to everyone including non-technical people in your organization.
-
-### Be Extendable, At Any Time
-Products quickly changes due to never-ending user requirements as the company scales. It's so common that oldest authorization systems will fall short and needs to be changed in the road. Refactoring existing authorization systems is hard because generally these systems sit at the heart of your product. Permify has an extendable authorization language that allows you to update the current authorization model easily, securely, and without affecting production. After it's tested and ready to go, you can switch new version of your model without breaking a sweat.
-
-### Audit Your Authorization and Ensure Security
-Protect your data, prevent unauthorized access and ensure your customers security. Permify can help you with things like fraud detection, real-time transaction monitoring, and even risk assessment with various functions that can be used easily with single API calls.
-
-## Cases that can benefit from An Authorization Service:
-
-- If you already have an identity/auth solution and want to plug in fine-grained authorization on top of that.
-- If you want to create a unified access control mechanism to use across your individual applications.
-- If you want to make future-proof authorization system and don't want to spend engineering effort for it.
-- If you’re managing authorization for growing micro-service infrastructure.
-- If your authorization logic is cluttering your code base.
-- If your data model is getting too complicated to handle your authorization within the service.
-- If your authorization is growing too complex to handle within code or API gateway.
-
diff --git a/docs/versioned_docs/version-0.6.x/permify-overview/infrastructure.md b/docs/versioned_docs/version-0.6.x/permify-overview/infrastructure.md
deleted file mode 100644
index 0f29223d..00000000
--- a/docs/versioned_docs/version-0.6.x/permify-overview/infrastructure.md
+++ /dev/null
@@ -1,79 +0,0 @@
-
-# Architecture & Deployment
-
-Permify is a infrastructure for ease the process of creating and managing scalable authorization systems in your environment.
-
-This section shows where and how does Permify fit into your environment with examining Permify's high level design, internal architecture, deployment patterns and the usage with the authentication and identity providers.
-
-## High Level Design
-
-You can model your authorization logic with **Permify's domain specific language** and your applications can interpolate with Permify API over REST API or GRPC Service to perform access control checks, read or query authorization-related data and more!
-
-Permify stores access control relations in a **database of your choice**, and each API request evaluates and takes into account access decisions based on the stored relations.
-
-So this preferred database behaves as a **centralized data source** for your authorization system.
-
-
-
-### Permify vs Authentication
-
-Authentication involves verifying that the person actually is who they purport to be, while authorization refers to what a person or service is allowed to do once inside the system.
-
-To clear out, Permify doesn't handle authentication or user management. Permify behave as you have a different place to handle authentication and store relevant data. Authentication or user management solutions (AWS Cognito, Auth0, etc) only can feed Permify with user information (attributes, identities, etc) to provide more consistent authorization across your stack.
-
-### Permify with Identity Providers
-
-Identity providers help you store and control your users’ and employees’ identities in a single place.
-
-Let’s say you build a project management application. And a client wants to connect this application via SSO. You need to connect your app to Okta. And your client can control who can access the application, and which group of authorization types they can have. But as a maker of this project management app. You need to build the permissions and then map to Okta.
-
-What we do is, help you build these permissions and eventually map anywhere you want.
-
-## Architecture
-
-Permify supports both HTTP and GRPC. HTTP requests are converted to GRPC and then transferred to Permify servers.
-
-There are 4 servers in a Permify Instance: Permission, Relationship, Schema, and Watch.
-
-- **Permission Server:** The permission server forwards the request to the invoker. The invoker checks for any missing parts of the query, let’s say if no snapshot is provided, it finds the head snapshot. It then hashes the request (with snapshot and schema version) and forwards it to the most convenient Permify instance. If the hash matches its own, it directs it to the local cache. If the cache does not contain the request, it proceeds to the engine. The engine breaks down the query into sub-queries and returns it to the invoker. This process continues until a final decision is made.
-- **Relationship Server:** After validating the request, it passes it to the database access layer.
-- **Schema Server:** After validating the request, it passes it to the database access layer.
-- **Watch Server:** It broadcasts changes in relationships based on their snapshots.
-
-
-
-Database abstractions for the reader and writer can use a database like Aurora Postgres.
-
-When deploying, separate hosts can be used in the Permify config for the reader and writer. This way, different Permify instances can read from different read replicas.
-
-**Note:** we are using serf (https://github.com/hashicorp/serf) agent for node discovery on hashring.
-
-## Deployment Patterns
-
-There are two main deployment patterns that you can follow, integrate Permify into your applications as a sidecar or using Permify as a service across your applications. Despite for both of these deployment patterns implementation is same - running Permify API in a environment you choose - the architectural aspects and usages differs. So let's examine them both.
-
-### Permify As A Service
-
-Permify can be deployed as a sole service that abstracts authorization logic from core applications and behaves as a single source of truth for authorization.
-
-Gathering authorization logic in a central place offers important advantages over maintaining separate access control mechanisms for individual applications.
-
-See the [What is Authorization Service] Section for a detailed explanation of those advantages.
-
-[What is Authorization Service]: ../authorization-service
-
-
-
-Since multiple applications could interact with the Permify Service on that pattern, preventing bottleneck for Permify endpoints and providing high availability is important.
-
-As shown from above schema, you can horizontally scale Permify Service with positioning Permify instances behind of a load balancer.
-
-### Using Permify as a Sidecar
-
-Permify can be used as a sidecar as well. In this deployment model, each application uses its own Permify instance and manages its own specific authorization.
-
-
-
-Although unified authorization offers many advantages, using the sidecar model ensures high performance and availability plus avoids the risk of a single point of failure of the centered authorization mechanism.
-
-
diff --git a/docs/versioned_docs/version-0.6.x/permify-overview/intro.md b/docs/versioned_docs/version-0.6.x/permify-overview/intro.md
deleted file mode 100644
index 69c135f2..00000000
--- a/docs/versioned_docs/version-0.6.x/permify-overview/intro.md
+++ /dev/null
@@ -1,117 +0,0 @@
----
-sidebar_position: 1
----
-
-# What is Permify?
-
-[Permify](https://github.com/Permify/permify) is an **open source authorization service** for creating fine-grained and scalable authorization systems.
-
-With Permify, you can easily structure your authorization model, store authorization data in your preferred database, and interact with the Permify API to handle all authorization queries from your applications or services.
-
-Permify is inspired by Google’s consistent, global authorization system, [Google Zanzibar](https://permify.co/post/google-zanzibar-in-a-nutshell/).
-
-### Motivation
-
-Our goal is to make **Google's Zanzibar** available to everyone and help them to build robust, flexible, and easily auditable authorization system that establishes a [natural linkage between permissions](https://permify.co/post/relationship-based-access-control-rebac/) across the business units, functions, and entities of an organization.
-
-## Key Features
-
-🛡️ **Production ready** authorization API that serve as **gRPC** and **REST**.
-
-🔮 Domain Specific Authorization Language to **easily model** your authorization. Supporting RBAC, ReBAC, ABAC and more.
-
-🔐 Database Configuration to store your permissions with **high availability** and **low latency**.
-
-✅ Perform access control checks and get answers **down to 10ms** with our various cache mechanisms that we operate.
-
-💪 Battle tested, robust **authorization architecture and data model** based on [Google Zanzibar](https://storage.googleapis.com/pub-tools-public-publication-data/pdf/41f08f03da59f5518802898f68730e247e23c331.pdf).
-
-⚙️ Create custom permissions for your **tenants**, and manage them in a single place with **Multi Tenancy**.
-
-⚡ Analyze **performance and behavior** of your authorization with tracing tools [jaeger], [signoz] or [zipkin].
-
-[jaeger]: https://www.jaegertracing.io/
-[signoz]: https://signoz.io/
-[zipkin]: https://zipkin.io/
-
-## Getting Started
-
-In Permify, authorization is divided into 3 core aspects; **modeling**, **storing authorization data** and **access checks**.
-
-- See how to [Model your Authorization] using Permify Schema.
-- Learn how Permify will [Store Authorization Data] as relations.
-- Perform [Access Checks] anywhere in your stack.
-
-[Model your Authorization]: ../../getting-started/modeling
-[Store Authorization Data]: ../../getting-started/sync-data
-[Access Checks]: ../../getting-started/enforcement
-
-This document explains how Permify handles these aspects to provide a robust and scalable authorization system for your applications. For the ones that want to try it out and examine it instantly,
-
-
-
-## Community & Support
-
-We would love to hear from you :heart:
-
-You can get immediate help on our Discord channel. This can be any kind of question-related to Permify, authorization, or authentication and identity management. We'd love to discuss anything related to access control space.
-
-For feature requests, bugs, or any improvements you can always open an [issue](https://github.com/permify/permify/issues).
-
-### Want to Contribute? Here are the ways to contribute to Permify
-
-* **Contribute to codebase:** We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
-* **Improve documentation:** Alongside our codebase, documentation is an important part of our open-source journey. We're trying to give the best DX possible to explain ourselves and Permify. And you can help with that by importing resources or adding new ones.
-* **Contribute to playground:** Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
-
-You can find more details about contributions on [CONTRIBUTING.md](https://github.com/Permify/permify/blob/master/CONTRIBUTING.md).
-
-## Communication Channels
-
-If you like Permify, please consider giving us a :star: on [github](https://github.com/permify/permify)
-
-
-
-## Roadmap
-
-You can find Permify's Public Roadmap [here](https://github.com/orgs/Permify/projects/1)!
-
-## Need any help on Authorization ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify or how it might fit into your authorization workflow, [schedule a call with one of our Permify engineers](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
diff --git a/docs/versioned_docs/version-0.6.x/playground.md b/docs/versioned_docs/version-0.6.x/playground.md
deleted file mode 100644
index 384c3485..00000000
--- a/docs/versioned_docs/version-0.6.x/playground.md
+++ /dev/null
@@ -1,160 +0,0 @@
----
-sidebar_position: 6
----
-
-# Using Permify Playground
-
-You can use our [Playground] to create and test your authorization schema in a browser.
-
-Our playground consists 3 main sections,
-
-- [Schema (Authorization Model)](#schema-authorization-model)
-- [Authorization Data](#authorization-data)
-- [Enforcement](#enforcement-access-check-scenarios)
-
-Let's examine these sections by following a simple example.
-
-[Playground]: https://play.permify.co/
-
-## Schema (Authorization Model)
-
-You can create your authorization model in this section with using our domain specific language.
-
-You can define your entities, relations between them and access control decisions with using Permify Schema. We already have a couple of use cases and example that you can choose to see how authorization can be structured. Also, you can check our docs to [learn more about how to model authorization](./getting-started/modeling.md) in Permify.
-
-To demonstrate how the playground works, let's create a simple authorization model as follows. This model should be selected as the default when you open the playground.
-
-```perm
-entity user {}
-
-entity organization {
-
- // organizational roles
- relation admin @user
- relation member @user
-}
-
-entity repository {
-
- // represents repositories parent organization
- relation parent @organization
-
- // represents owner of this repository
- relation owner @user
-
- // permissions
- permission edit = parent.admin or owner
- permission delete = owner
-}
-```
-
-We have 2 permissions, `edit` for access of editing repository and `delete` for access of deleting repository.
-
-Repositories has parent child relation with organizations. The `parent` relation in the repository entity represents that parent child association, while ownership of the repository is represented with the `owner` relation.
-
-Organizations can have organizational wide roles such as admin and member, which defined as `admin` and `member` relation in organization entity.
-
-:::info Automatic Saving for Schema Changes
-Schema changes are captured automatically, and other sections update accordingly. Some delays may occur at times; please feel free to reach out if these delays hinder your testing process.
-:::
-
-### Visualizer
-
-We get loads of feedback about the observability and reasonability of the authorization model across teams and colleagues.
-
-So we put a simple visualizer that shows how your authorization structure looks at a high level. In particular, you can examine relations between entities and their permissions.
-
-
-
-## Authorization Data
-
-You can create sample authorization data to test your authorization logic. In Permify, authorization data stored as tuples and these tuples stored in a database that you preferred.
-
-The basic tuple takes the form of:
-
-`entity # relation @ user`
-
-So the entity can be any entity that you defined in your model. If we look up our example it can be an organization or repository (since the user is empty). The relation can be one of the defined relations in the selected entity.
-
-The user is basically the user or user set in our system. Let's say we want make the **user 1** `admin` in **organization 1** then we need to create an example relational tuple according to our model as follows:
-
-`organization:1#admin@user:1`
-
-To create a relation tuple in playground just hit the **Add Relationship** button.
-
-
-
-You can choose entity, relation and the subject (user or user set) with entering identifier to create sample data. Let's create the relation tuple `organization:1#admin@user:1` as follows.
-
-
-
-Let's add one more relation tuple to perform a sample access check. I want to add repository:1 into organization:1 - `repository:1#parent@organization:1#...` as follows:
-
-
-
-Created tuples shown in the **Data** section as follows.
-
-
-
-## Enforcement (Access Check Scenarios)
-
-Finally as we have a sample data let's perform an access check!
-
-The YAML in the Enforcement section represents a test scenario for conducting access checks. This scenario-based testing process provides the ability to execute complex access scenarios in a single place.
-
-Let's name our scenario **"admin_access_test"** and create tests to check:
-
-- Whether user:1 (admin) can edit repository:1?
-- Whether user:1 (admin) can delete repository:1?
-
-Below is the YAML scenario covering these two tests:
-
-
-
-In the above YAML structure,
-
-#### entity
-
-Represents the resource for which we want to check access - `repository:1`
-
-#### subject
-
-Represents the subject that performs the action or grants access - `user:1`.
-
-#### assertions
-
-Assertions stands for defining the expected result for specific action or an permission. In our case we're evaluating access for edit action.
-
-Since organization:1 is parent of repository:1 ( `repository:1#parent@organization:1#...` ) and user:1 has an admin role in organization:1 ( `organization:1#admin@user:1` ) user:1 should allow to edit the repository:1 because the we define rule of the edit permission as:
-
-`permission edit = parent.admin or owner`
-
-:::note
-which `parent.admin` indicates admin in the organization that repository belongs to.
-:::
-
-So user:1 should be able to edit resource:1, therefore expected outcome for that access request is true.
-- `edit: true`
-
-On the other hand, user:1 should't be able to delete resource:1, because only owners can. Therefore expected outcome for that is false.
-- `delete: false`
-
-:::info Create More Advanced Scenarios
-For simplicity, we've created a basic scenario. However, you can create more advanced scenarios using our validation YAML structure.
-
-To learn how to use this syntax for complex scenarios, refer to the [Creating Test Scenarios](../getting-started/testing#creating-test-scenarios) section in [Testing & Validation](./getting-started/testing.md) page.
-:::
-
-Let's click the Run button to execute our scenario.
-
-
-
-Let's change the expected outcome as false (`edit: false`) and hit the **Run** button again we'll see an error message.
-
-
-
-As we seen above this is how you can model your authorization and test it with sample data in Permify Playground.
-
-## Need any help ?
-
-Our team is happy to help you get started with Permify. If you'd like to learn more about using Permify in your app or have any questions about this example, [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
diff --git a/docs/versioned_docs/version-0.6.x/reference/_category_.json b/docs/versioned_docs/version-0.6.x/reference/_category_.json
deleted file mode 100644
index b55d99d8..00000000
--- a/docs/versioned_docs/version-0.6.x/reference/_category_.json
+++ /dev/null
@@ -1,5 +0,0 @@
-{
- "label": "Reference",
- "position": 8,
- "collapsed": true
-}
diff --git a/docs/versioned_docs/version-0.6.x/reference/cache.md b/docs/versioned_docs/version-0.6.x/reference/cache.md
deleted file mode 100644
index 1910705a..00000000
--- a/docs/versioned_docs/version-0.6.x/reference/cache.md
+++ /dev/null
@@ -1,95 +0,0 @@
-# Cache Mechanisms
-
-This section showcases the cache mechanisms that Permify uses.
-
-## Schema Cache
-
-Schemas are stored in an in-memory cache based on their versions. If a version is specified in the request metadata, it will be searched for in the in-memory cache. If not found, it will query the database for the version and store it in the cache. If no version information is given in the metadata, versions will be assumed to be alphanumeric and sorted in that order, and Permify will request the head version and check if it exists in the memory cache.
-
-The size of this can be determined through the Permify configuration. Here is an example configuration:
-service:
-
-```yaml
-…
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
-…
-```
-
-The cache library used is: https://github.com/dgraph-io/ristretto
-
-## Data Cache
-
-Permify applies the MVCC (Multi Version Concurrency Control) pattern for Postgres, creating a separate database snapshot for each write and delete operation. This both enhances performance and provides a consistent cache.
-
-An example of a cache key is:
-check_{tenant_id}_{schema_version}:{snapshot_token}:{check_request}
-
-Permify hashes each request and searches for the same key. If it cannot find it, it runs the check engine and writes to the cache, thus creating a consistently working hash.
-
-The size of this can also be determined via the Permify configuration. Here’s an example:
-service:
-
-```yaml
- …
- permission:
- bulk_limit: 100
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
- …
-```
-
-The cache library used is: https://github.com/dgraph-io/ristretto
-
-Note: Another advantage of the MVCC pattern is the ability to historically store data. However, it has a downside of accumulation of too many relationships. For this, we have developed a garbage collector that will delete old data at a time period you specify.
-
-## Distributed Cache
-
-Permify does provide a distributed cache across availability zones (within an AWS region) via **Consistent Hashing**. Permify uses Consistent Hashing across its distributed instances for more efficient use of their individual caches.
-
-This would allow for high availability and resilience in the face of individual nodes or even entire availability zone failure, as well as improved performance due to data locality benefits.
-
-Consistent Hashing is a distributed hashing scheme that operates independently of the number of objects in a distributed hash table. This method hashes according to the nodes’ peers, estimating which node a key would be on and thereby ensuring the most suitable request goes to the most suitable node, effectively creating a natural load balancer.
-
-### How Consistent Hashing Operates in Permify
-
-With a single instance, when an API request is made, request and corresponding response stored in its corresponding local cache.
-
-If we have more than one Permify instance consistent hashing activates on API calls, hashes the request, and outputs a unique key representing the node/instance that will store the request's data. Suppose it stored in the instance 2, subsequent API calls with the same hash will retrieve the response from the instance 2, regardless of which instance that API called from.
-
-Using this consistent hashing approach, we can effectively utilize individual cache capacities. Adding more instances automatically increases the total cache capacity in Permify.
-
-You can learn more about consistent hashing from the following blog post: [Introducing Consistent Hashing](https://itnext.io/introducing-consistent-hashing-9a289769052e)
-
-:::info
-Note, however, that while the consistent hashing approach will distribute keys evenly across the cache nodes, it's up to the application logic to ensure the cache is used effectively (i.e., that it reads from and writes to the cache appropriately).
-:::
-
-Here is an example configuration:
-
-```yaml
-distributed:
- # Indicates whether the distributed mode is enabled or not
- enabled: true
-
- # The address of the distributed service.
- # Using a Kubernetes DNS name suggests this service runs in a Kubernetes cluster
- # under the 'default' namespace and is named 'permify'
- address: "kubernetes:///permify.default:5000"
-
- # The port on which the service is exposed
- port: "5000"
-```
-
-Additional to that we’re using a [circuit breaker](https://blog.bitsrc.io/circuit-breaker-pattern-in-microservices-26bf6e5b21ff) pattern to detect and handle failures when the underlying database is unavailable. It prevents unnecessary calls when the database is down and handles the process on the rebooting phase.
-
-## Need any help ?
-
-Our team is happy help you to structure right architecture for your permission system. Feel free to [schedule a call with one of our Permify engineer](https://meetings-eu1.hubspot.com/ege-aytin/call-with-an-expert).
-
-
-
diff --git a/docs/versioned_docs/version-0.6.x/reference/configuration.md b/docs/versioned_docs/version-0.6.x/reference/configuration.md
deleted file mode 100644
index 184366ab..00000000
--- a/docs/versioned_docs/version-0.6.x/reference/configuration.md
+++ /dev/null
@@ -1,553 +0,0 @@
-# Configuration File
-
-Permify offers various options for configuring your Permify API Server.
-
-Here is the example configuration YAML file with glossary below. You can also find
-this [example config file](https://github.com/Permify/permify/blob/master/example.config.yaml) in Permify repo.
-
-***Example config.yaml file***
-
-```yaml
-# The server section specifies the HTTP and gRPC server settings,
-# including whether or not TLS is enabled and the certificate and
-# key file locations.
-server:
- rate_limit: 100
- http:
- enabled: true
- port: 3476
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
- grpc:
- port: 3478
- tls:
- enabled: true
- cert: /etc/letsencrypt/live/yourdomain.com/fullchain.pem
- key: /etc/letsencrypt/live/yourdomain.com/privkey.pem
-
-# The logger section sets the logging level for the service.
-logger:
- level: info
-
-# The profiler section enables or disables the pprof profiler and
-# sets the port number for the profiler endpoint.
-profiler:
- enabled: true
- port: 6060
-
-# The authn section specifies the authentication method for the service.
-authn:
- enabled: true
- method: preshared
- preshared:
- keys: []
-
-# The tracer section enables or disables distributed tracing and sets the
-# exporter and endpoint for the tracing data.
-tracer:
- exporter: zipkin
- endpoint: http://localhost:9411/api/v2/spans
- enabled: true
-
-# The meter section enables or disables metrics collection and sets the
-# exporter and endpoint for the collected metrics.
-meter:
- exporter: otlp
- endpoint: localhost:4318
- enabled: true
-
-# The service section sets various service-level settings, including whether
-# or not to use a circuit breaker, and cache sizes for schema, permission,
-# and relationship data.
-service:
- circuit_breaker: false
- watch:
- enabled: false
- schema:
- cache:
- number_of_counters: 1_000
- max_cost: 10MiB
- permission:
- bulk_limit: 100
- concurrency_limit: 100
- cache:
- number_of_counters: 10_000
- max_cost: 10MiB
-
-# The database section specifies the database engine and connection settings,
-# including the URI for the database, whether or not to auto-migrate the database,
-# and connection pool settings.
-database:
- engine: postgres
- uri: postgres://user:password@host:5432/db_name
- auto_migrate: false
- max_open_connections: 20
- max_idle_connections: 1
- max_connection_lifetime: 300s
- max_connection_idle_time: 60s
- garbage_collection:
- enabled: true
- interval: 200h
- window: 200h
- timeout: 5m
-
-# distributed configuration settings
-distributed:
- # Indicates whether the distributed mode is enabled or not
- enabled: true
-
- # The address of the distributed service.
- # Using a Kubernetes DNS name suggests this service runs in a Kubernetes cluster
- # under the 'default' namespace and is named 'permify'
- address: "kubernetes:///permify.default"
-
- # The port on which the service is exposed
- port: "5000"
-
-```
-
-## Options
-
-server | Server Configurations
-
-
-#### Definition
-
-Server options to run Permify. (`grpc` and `http` available for now.)
-
-#### Structure
-
-```
-├── server
- ├── rate_limit
- ├── (`grpc` or `http`)
- │ ├── enabled
- │ ├── port
- │ └── tls
- │ ├── enabled
- │ ├── cert
- │ └── key
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|---------------------------|---------|---------------------------------------------------------------------|
-| [ ] | rate_limit | 100 | the maximum number of requests the server should handle per second. |
-| [x] | [ server_type ] | - | server option type can either be `grpc` or `http`. |
-| [ ] | enabled (for server type) | true | switch option for server. |
-| [x] | port | - | port that server run on. |
-| [x] | tls | - | transport layer security options. |
-| [ ] | enabled (for tls) | false | switch option for tls |
-| [ ] | cert | - | tls certificate path. |
-| [ ] | key | - | tls key pat |
-
-#### ENV
-
-| Argument | ENV | Type |
-|---------------------------|-----------------------------------|--------------|
-| rate_limit | PERMIFY_RATE_LIMIT | int |
-| grpc-port | PERMIFY_GRPC_PORT | string |
-| grpc-tls-enabled | PERMIFY_GRPC_TLS_ENABLED | boolean |
-| grpc-tls-key-path | PERMIFY_GRPC_TLS_KEY_PATH | string |
-| grpc-tls-cert-path | PERMIFY_GRPC_TLS_CERT_PATH | string |
-| http-enabled | PERMIFY_HTTP_ENABLED | boolean |
-| http-port | PERMIFY_HTTP_PORT | string |
-| http-tls-key-path | PERMIFY_HTTP_TLS_KEY_PATH | string |
-| http-tls-cert-path | PERMIFY_HTTP_TLS_CERT_PATH | string |
-| http-cors-allowed-origins | PERMIFY_HTTP_CORS_ALLOWED_ORIGINS | string array |
-| http-cors-allowed-headers | PERMIFY_HTTP_CORS_ALLOWED_HEADERS | string array |
-
-
-
-#### Definition
-
-You can choose to authenticate users to interact with Permify API.
-
-There are 2 authentication method you can choose:
-
-* [Pre Shared Keys](#pre-shared-keys)
-* [OpenID Connect](#openid-connect)
-
-#### Pre Shared Keys
-
-On this method, you must provide a pre shared keys in order to identify yourself.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── keys
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | true | switch option authentication config |
-| [x] | keys | - | Private key/keys for server authentication. Permify does not provide this key, so it must be generated by the users. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-preshared-keys | PERMIFY_AUTHN_PRESHARED_KEYS | string array |
-
-
-#### OpenID Connect
-
-Permify supports OpenID Connect (OIDC). OIDC provides an identity layer on top of OAuth 2.0 to address the shortcomings
-of using OAuth 2.0 for establishing identity.
-
-With this authentication method, you be able to integrate your existing Identity Provider (IDP) to validate JSON Web
-Tokens (JWTs) using JSON Web Keys (JWKs). By doing so, only trusted tokens from the IDP will be accepted for
-authentication.
-
-#### Structure
-
-```
-├── authn
-| ├── method
-| ├── enabled
-| ├── client-id
-| ├── issuer
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|-----------|---------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| [x] | method | - | Authentication method can be either `oidc` or `preshared`. |
-| [ ] | enabled | false | switch option authentication config |
-| [x] | client_id | - | This is the client ID of the application you're developing. It is a unique identifier that is assigned to your application by the OpenID Connect provider, and it should be included in the JWTs that are issued by the provider. |
-| [x] | issuer | - | This is the URL of the provider that is responsible for authenticating users. You will use this URL to discover information about the provider in step 1 of the authentication process. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|-----------------------|-------------------------------|--------------|
-| authn-enabled | PERMIFY_AUTHN_ENABLED | boolean |
-| authn-method | PERMIFY_AUTHN_METHOD | string |
-| authn-oidc-issuer | PERMIFY_AUTHN_OIDC_ISSUER | string |
-| authn-oidc-client-id | PERMIFY_AUTHN_OIDC_CLIENT_ID | string |
-
-
-
-
-
-tracer | Tracing Configurations
-
-
-#### Definition
-
-Permify integrated with [jaeger], [otlp], [signoz], and [zipkin] tacing tools to analyze performance and behavior of your
-authorization when using Permify.
-
-#### Structure
-
-```
-├── tracer
-| ├── exporter
-| ├── endpoint
-| ├── enabled
-| ├── insecure
-| ├── urlpath
-```
-
-#### Glossary
-
-| Required | Argument | Default | Description |
-|----------|----------|---------|----------------------------------------------------------------------------|
-| [x] | exporter | - | Tracer exporter, the options are `jaeger`, `otlp`, `signoz`, and `zipkin`. |
-| [x] | endpoint | - | export uri for tracing data. |
-| [ ] | enabled | false | switch option for tracing. |
-| [ ] | urlpath | | allows one to override the default URL path for otlp, used for sending traces. If unset, default ("/v1/traces") will be used. |
-| [ ] | insecure | false | Whether to use HTTP instead of HTTPs for exporting the traces. |
-
-#### ENV
-
-| Argument | ENV | Type |
-|----------------------|-------------------------------|--------------|
-| tracer-enabled | PERMIFY_TRACER_ENABLED | boolean |
-| tracer-exporter | PERMIFY_TRACER_EXPORTER | string |
-| tracer-endpoint | PERMIFY_TRACER_ENDPOINT | string |
-| tracer-urlpath | PERMIFY_TRACER_URL_PATH | string |
-| tracer-insecure | PERMIFY_TRACER_INSECURE | boolean |
-
-