You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Discoverer: Zhao Jiapeng of Key Laboratory of Trustworthy Distributed Computing and Service (BUPT), Ministry of Education, Beijing University of Posts and Telecommunications
Description
A stack-buffer-overflow vulnerability exists in the econf_writeFile function. The vulnerability is triggered at libeconf/lib/libeconf.c line:546. The statement is: while ((line = strsep(&value_string, "\n")) != NULL) (line 546).
In this code, a buf buffer of 8192 bytes is defined and the contents of key_file->file_entry[i].comment_before_key are copied into the buf.
The strncpy function is used here, which ensures that the size of buf is not exceeded when copying, so the process does not result in a buffer overflow vulnerability.
Next, when using the strsep function, the value_string pointer is pointed to the beginning of the buf buffer.
The strsep function alone will not cause a buffer overflow vulnerability. However, in the strncpy function, if the length of key_file->file_entry[i].comment_before_key is greater than or equal to the size of buf, then it will not add the null character at the end of buf.
This may result in the strsep function not correctly identifying the end position of the string when splitting it, thus causing a buffer overflow.
Reproduction
Please reproduce this vulnerability using the following PoC.
This PoC is obtained by modifying the input data based on the test/tst-write-string-data.c testcase.
Use this PoC to replace the tst-write-string-data.c file in the libeconf/tests directory and configure the C compiler to use the -fsanitize=address flag, as follows:
The PoC file and the input file are here and here, respectively.
You must create a corpus subdirectory under the directory where you run the test target tst-write-string-data in order to run the test target correctly.
Using this command: cd /libeconfDir/build/tests && mkdir corpus and /libeconfDir/build/tests/tst-write-string-data econf_writeFile_546, you will get the following outputs:
This is the corresponding information of this overflow vulnerability from AddressSanitizer.
And attackers can use this bug to achieve a DoS attack even remote code execution attack.
Please reproduce and fix this vulnerability.
The text was updated successfully, but these errors were encountered:
Discoverer: Zhao Jiapeng of Key Laboratory of Trustworthy Distributed Computing and Service (BUPT), Ministry of Education, Beijing University of Posts and Telecommunications
Description
A stack-buffer-overflow vulnerability exists in the
econf_writeFilefunction. The vulnerability is triggered atlibeconf/lib/libeconf.cline:546. The statement is:while ((line = strsep(&value_string, "\n")) != NULL)(line 546).The corresponding statements as follows:
In this code, a
bufbuffer of 8192 bytes is defined and the contents ofkey_file->file_entry[i].comment_before_keyare copied into thebuf.The
strncpyfunction is used here, which ensures that the size ofbufis not exceeded when copying, so the process does not result in a buffer overflow vulnerability.Next, when using the
strsepfunction, thevalue_stringpointer is pointed to the beginning of the buf buffer.The
strsepfunction alone will not cause a buffer overflow vulnerability. However, in thestrncpyfunction, if the length ofkey_file->file_entry[i].comment_before_keyis greater than or equal to the size of buf, then it will not add the null character at the end ofbuf.This may result in the
strsepfunction not correctly identifying the end position of the string when splitting it, thus causing a buffer overflow.Reproduction
Please reproduce this vulnerability using the following PoC.
This PoC is obtained by modifying the input data based on the
test/tst-write-string-data.ctestcase.Use this PoC to replace the
tst-write-string-data.cfile in thelibeconf/testsdirectory and configure the C compiler to use the-fsanitize=addressflag, as follows:CC=clang CXX=$CC CFLAGS="-O2 -g -fsanitize=address -L/root/ -shared-libasan" make -C build/ check -j8The PoC file and the input file are here and here, respectively.
You must create a corpus subdirectory under the directory where you run the test target
tst-write-string-datain order to run the test target correctly.Using this command:
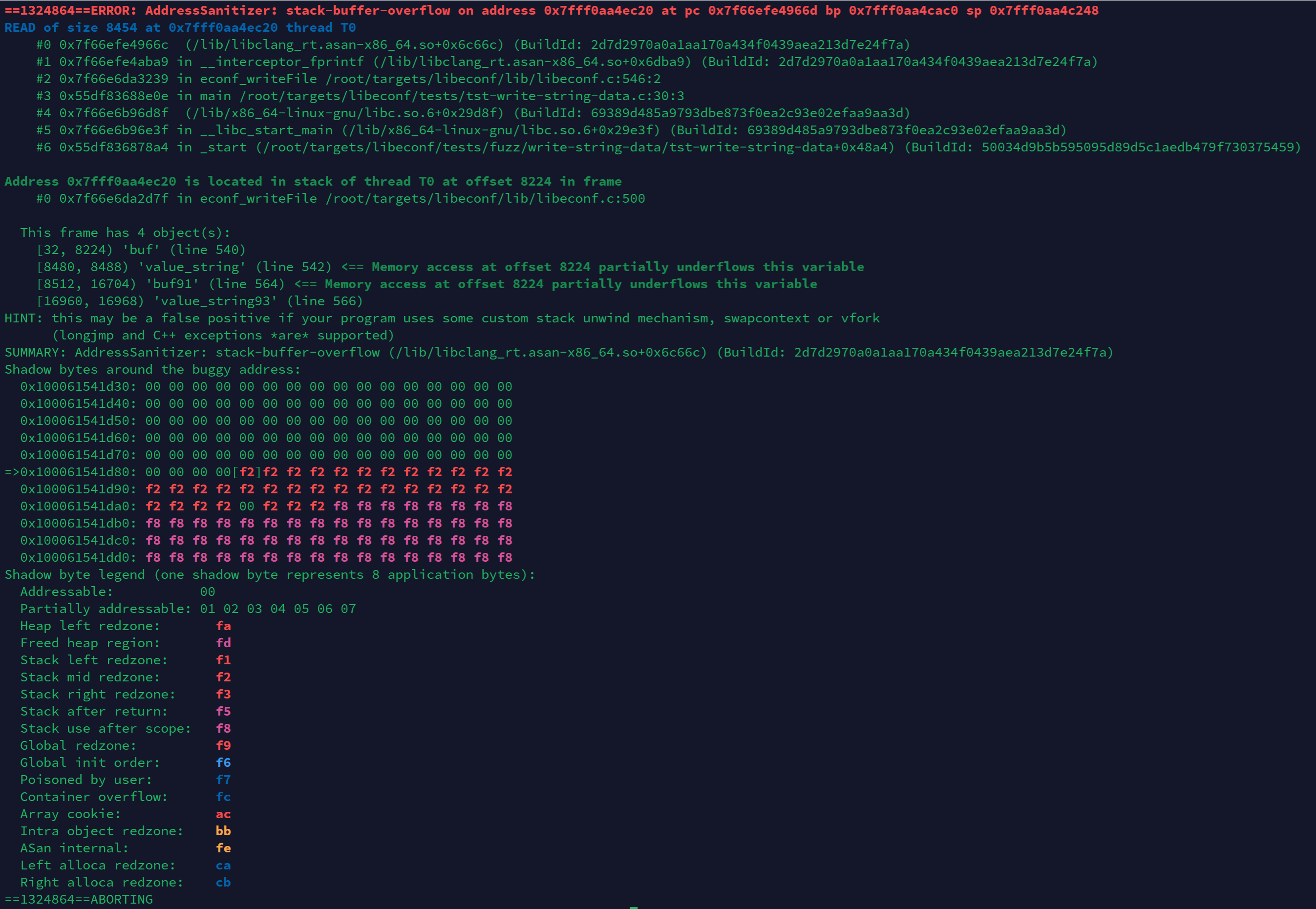
cd /libeconfDir/build/tests && mkdir corpusand/libeconfDir/build/tests/tst-write-string-data econf_writeFile_546, you will get the following outputs:This is the corresponding information of this overflow vulnerability from AddressSanitizer.
And attackers can use this bug to achieve a DoS attack even remote code execution attack.
Please reproduce and fix this vulnerability.
The text was updated successfully, but these errors were encountered: