Repos:
- https://github.com/4sm-ops/aleo_python - Aleo Rust libraries for Python
- https://github.com/4sm-ops/zkDrop - zkDrop application
Tested environment:
- Python 3.7
- rustc 1.66
- maturin [latest version]
- Operating systems:
- Ubuntu 22.04.1 LTS
- MacOS Big Sur 11.2.3 (Apple M1)
- Install
aleo_pythonpackage
$ git clone https://github.com/4sm-ops/aleo_python.git
$ cd aleo_python
$ python3.7 -m venv .env
$ source .env/bin/activate
$ python3.7 -m pip install maturin
$ maturin develop
1.1 Strongly recommended to test aleo_python package
$ python3.7
>>> import aleo_python
>>> aleo_python.new_keys()
'{"AleoPrivateKey":"APrivateKey1zkp6jsksQrTZc5C5QLguxfinfjmb8WxLhEvjsEw7kd7zNoa","AleoViewKey":"AViewKey1fML5ZX9x2QbY8VBLfpwywGRob6T6ieKTVHEK1RnLHCxr","AleoAddress":"aleo15yn2z3cuafq0t5c805daqq5r5669uru8udwhp28nahs73vvw3sfqvqvct6"}'
>>> exit()
- Install and run zkDrop application
$ cd ../
$ git clone https://github.com/4sm-ops/zkDrop.git
$ cd zkDrop
$ python3.7 -m pip install -r requirements.txt
$ python3.7 zkdrop_qt.py
aleo_create_account.sh - Create Aleo keys and store it in aleo_keys folder in JSON format
pyumbral_decrypt.py - Decrypt file using pyUmbral
pyumbral_encrypt.py - Encrypt file using pyUmbral
pyumbral_network_encryption.py - Encryption
aleo_sign_verify - Aleo sign/verify tool written in Rust
aleo_keys - Aleo keys in JSON files aleo_pyumbral_keys - temp file for pyUmbral assets - assets folder lib - python libs secret_sharing - pyUmbral file
zkDrop.py - gui zkDrop application
Aleo based tool for file sharing and collaboration between addresses. Private, easy-to-use, and on-chain. Store, encrypt, and share multimedia files on-chain.
- Alex wants to share his files with Bob
- Alex takes Bob’s Aleo Account (Public key or QR code)
- Alex adds his file to application
- Application encrypts it and securely transfer to Bob
- Ms Liza wanted to open a bank account and she contacted one of the bank representatives Mr Vendy.
- Mr Vendy – after asking some basic details from Liza such as name, occupation etc advised her to obtain a digital ID for KYC purpose and asked her to use zkDrop.xyz
- Liza follows all the steps mentioned in zkDrop.xyz application.
- Finally she manages to get her Aleo Identity (public and private keys) .
- She shares the public key with Mr Vendy and proceeds with other formalities.
This is issued on a 1-to-1 basis unique to the customer only, and it cannot be a shared identity with other users. Any business that needs a customer’s information must request it in order to get approval.
KYC (Know Your Customer), AML (Anti-Money Laundering) and CFT (Counter-Financing Terrorism)
The customer’s data profile is stored locally in an encrypted format on their own device, and this can be shared in future for KYC requirements.
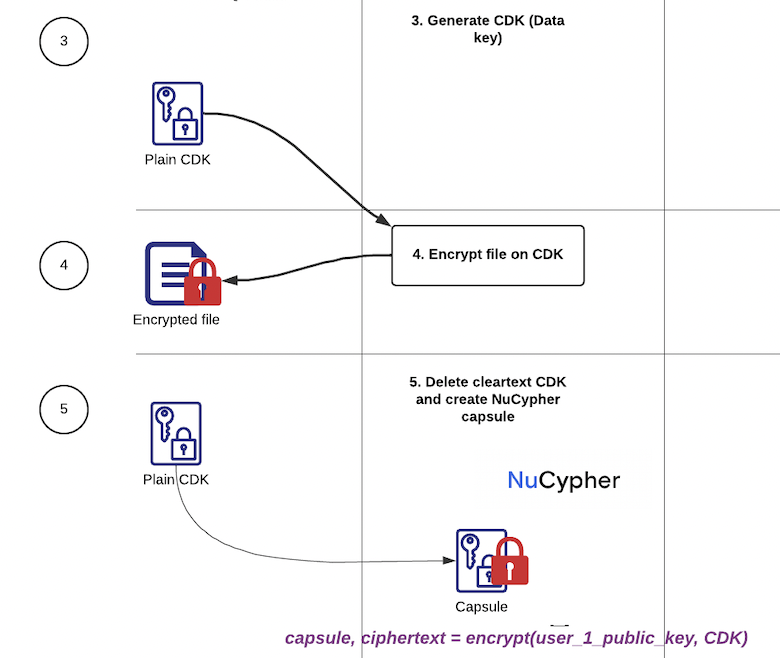
The Key principle of Secure Data Storage is encryption of Data Storage using data encryption keys. Encryption keys are stored on user’s device and protected by (Password and OTP/biometrics). In case of device loss recovery mechanism would be provided to regenerate the encryption key however this will be covered in the next phase of the project.
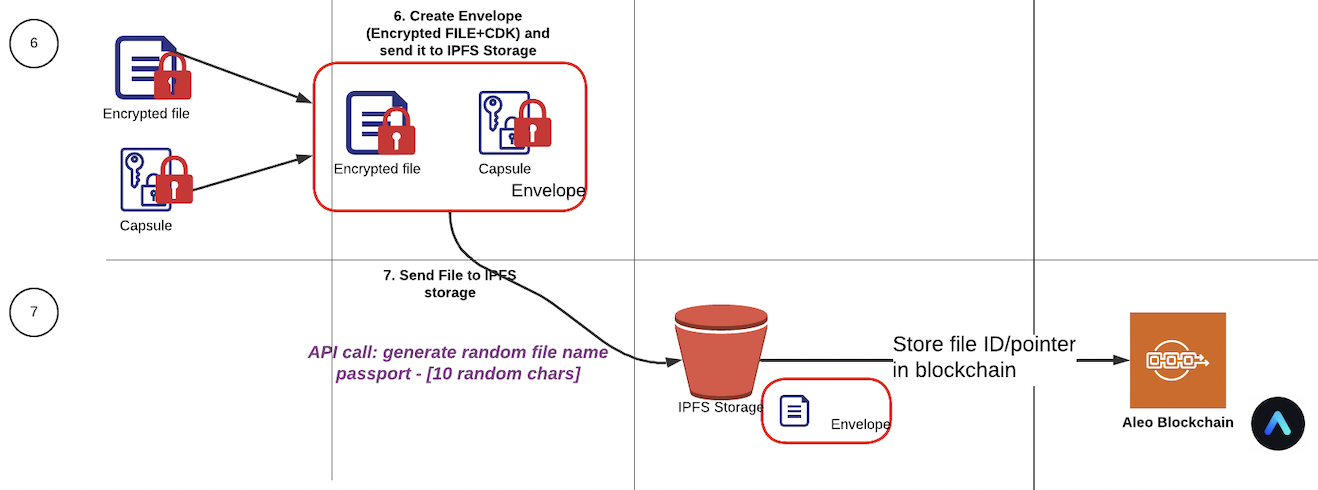
In all cases, the PRE Application must be integrated with a storage and transport layer in order to function properly. Along with the transport of ciphertexts, a nucypher application also needs to include channels for Alice and Bob to discover each other’s public keys, and provide policy encrypting information to Bob and Enrico.
Every data field is encrypted at rest with zero knowledge of its contents while the customer is the only one who can access it.
Other businesses who need to request personal data will also have to get the consent of the customer first.
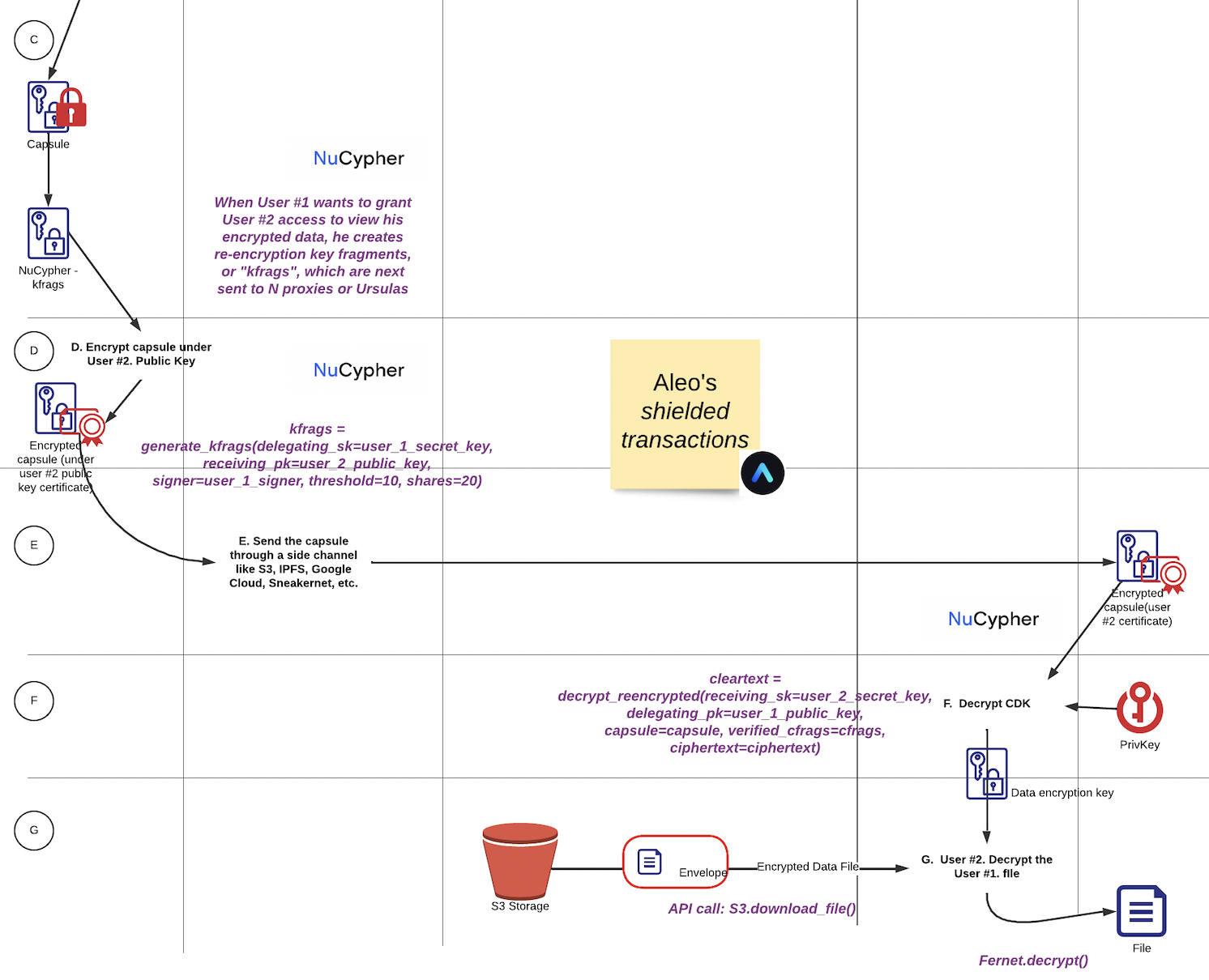
Using Umbral, Alice (the data owner) can delegate decryption rights to Bob for any ciphertext intended to her, through a re-encryption process performed by a set of semi-trusted proxies or Ursulas. When a threshold of these proxies participate by performing re-encryption, Bob is able to combine these independent re-encryptions and decrypt the original message using his private key.
Invocation of umbral.encrypt() returns both a capsule and a ciphertext. Note that anyone with Alice’s public key can perform this operation.
Since data was encrypted with Alice’s public key, Alice can open the capsule and decrypt the ciphertext with her private key.
When Alice wants to grant Bob access to view her encrypted data, she creates re-encryption key fragments, or “kfrags”, which are next sent to N proxies or Ursulas.
Alice must specify shares (the total number of kfrags), and a threshold (the minimum number of kfrags needed to activate a capsule). In the following example, Alice creates 20 kfrags, but Bob needs to get only 10 re-encryptions to activate the capsule.
If Bob attempts to open a capsule that was not encrypted for his public key, or re-encrypted for him by Ursula, he will not be able to open it.
If Bob received the capsule fragments in serialized form, he can verify that they are valid and really originate from Alice, using Alice’s public keys.
Finally, Bob decrypts the re-encrypted ciphertext using his key.
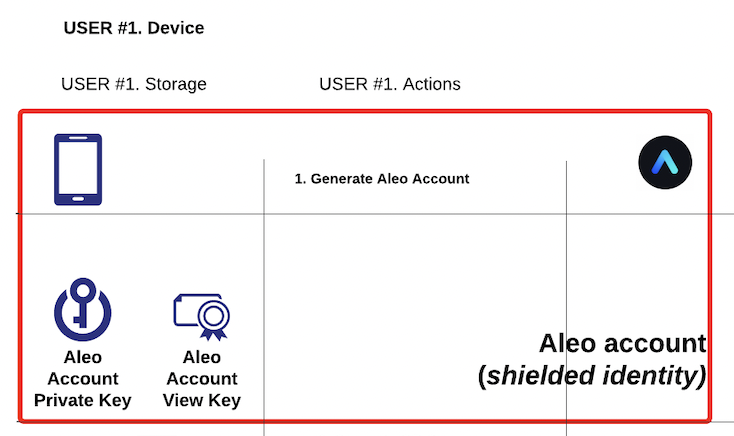
An Aleo account is composed of an account private key, account view key, and an ****account address.
The account private key is used to authorize a transaction, which updates the global state of account records. The account view key is used to decrypt account records, which are encrypted under the user's account address. Lastly, the account address enables users to interact with one another, sending and receiving records that encode values and application data.
{
"AccountName": "RustamOne",
"AleoPrivateKey": "APrivateKey1zkpEwiFtmMtKPfM8Mj8tteyVKvwZK3pVFwKZ91nGhHBgUTS",
"AleoViewKey": "AViewKey1iLBkmV1JhxBLYJVTusWsfiFn46VhSNyB1WCjeLtNFbaX",
"AleoAddress": "aleo1jn8pad7e58sa2r3w2743exv0s2fr7arsmdkrfgzq4d33ew2djvzshxgwqq"
}
Materials: