OSGiScanner is a simple Python 2.7 tool written to aid Penetration Testers in finding OSGi consoles.
OSGi consoles commonly have the default username and password combination of admin:admin.
Once a Tester has gained access to an OSGi console, they may be able to execute groovy script via the script console or deploy malicous bundle packages.
I've previously documented both attack types:
Shelling Apache Felix With Java Bundles
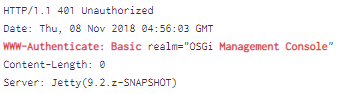
To find OSGi consoles, we simply search for the "/system/console" directory. The web request typically requires Basic auth and we can use the fingerprint 'WWW-Authenticate: Basic realm="OSGi Management Console"' to detect such a console.
On Shodan, you can may find these consoles inside your target range by using the basic auth fingerprint as a search term.
Next, execute OSGi scanner against that host or range of hosts to discover more potential targets.
python OSGiScanner.py --cidr 10.10.1.0/24 --port 80 --outfile myscan.log
python OSGiScanner.py --cidr 10.10.1.0/24 --port 443
python OSGiScanner.py --cidr 10.10.1.0/24 --port 9443 --ssl