New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
acquireTokensilent return null accessToken randomly. #736
Comments
|
@mmuarc thank you for explaining your issue so well |
|
This looks like the issue I experienced in issue #722. |
|
MSAL.JS version 1.0.1 I am able to get around this issue by checking for a null token on a successful response, and calling calling my login function (without prompt since the user is already authenticated at this point). Login Function Get Token Method |
|
I'm experiencing this problem too. |
|
Still in progress, thanks for patience |
|
This seems to fix the issue on my end :) Good job! |
|
@raikoss Thanks for testing this. I will push a patch tonight to npm and CDN, |
|
Hi, @pkanher617 thanks for your work. This is embarrassing but although I pulled the branch I don't know exactly what to do to test it in my app since I'm using an npm package for msal.. Any place where I can find how to generate the package locally and maybe replace the current package manually in node_modules? |
|
@mmuarc What I did was:
Though this may be different than what others may do, this is what enabled me to test the new version. Don't forget to remove the reference to the local package by running Hope this was helpful to you. |
|
Thanks for your help @raikoss, @sameerag . I finally tested it. @pkanher617, this fixed the issue for me. Great job |
|
I have published 1.0.2. Thanks for all your feedback! |
|
Never mind my comment. I am including the clientid as the only scope. I learned that doing this causes the idToken to be renewed rather than the accessToken. |
|
@jfbloom22 What is your solution to the problem then? How did you solve this? |
|
@DarylThayil Sorry to ping you -- I am still seeing the same issue using 1.0.2 Meanwhile, the scope I have locally has been changed to Is it expected to modify the original scope when |
|
@ayuspark what solved it for me was passing in a single scope similar too: “https://B2CBlog.onmicrosoft.com/notes/read”
|
|
By passing Client ID as the only scope, you are renewing your ID token, not any access tokens you may have acquired beforehand. This is most likely why the access token is null, but as you can see you have a new ID token in the response. If you want to silently renew access tokens, you pass the same scopes as when you acquired them when you used Since you want the ID token, just check the |
|
How I learned that passing in the clientid as the only scope would result in the idToken being renewed was by stepping through the source code and finding this comment: microsoft-authentication-library-for-js/lib/msal-core/src/UserAgentApplication.ts Line 429 in ce4f045
|
|
Yeah I can't really find it either, I remember it was back in the old v0.2.4 documentstion at least. I would suggest creating a new issue for this, maybe someone will document it somewhere :) |
|
Thank you peeps for the response. This is how I tested the app: In this scenario, when passing a scope of just Hope this help clarify the question a bit more. Questions: ping @sameerag |
|
@ayuspark I will try to answer your questions.
Please let me know if I haven't answered any questions. I will update when I have more info about this issue. |
|
@pkanher617 |
|
@pkanher617 thoughts on just adding code to null check a successful response and throw an error if it is a false positive? |
|
@pkanher617 just making sure you saw this code comment I mentioned above. I believe the 'null' access token is intentional when the 'clientid' is used as the only scope.
If you ask me, changing the type of token returned based on which scope is passed in, is a confusing side effect. Might consider adding a config option for tokenType so that we can clearly request the type of token we want. |
|
@jfbloom22 In some apps, the services/apis can be behind the same clientId as the client app, hence calling with just the clientId as scopes when idToken exists, can return accessToken. I have addressed the issue with the msal team internally, and I'll follow up to see when to add new issues. |
|
@jfbloom22 As ayuspark says, in the cases where services and apis are behind the same clientId, the clientid scope will return an idToken and an accessToken (which are incidentally the same) which will grant access. I am pushing two separate PRs to address the fact that when you are returned ONLY an id_token, the tokenType will reflect that, and the scopes you give us will not be mutated. @ayuspark Thank you for the response, I am pushing these fixes now and will hopefully have a patch release out by Monday. |
|
Any news on this? |
|
@scale-tone So I chatted with @pkanher617 who works on MSAL.js, when using your own AAD app clientId as your scope, you are doing a self-authorizing, and id_token == access_token. And in this case, when you call acquireTokenSilent (ATS) when there's no id_token in cache, it'd first get you an id_token, and at this time, acess_token will be null. And if you call ATS the second time, it'd return you access_token, which is the same token as id_token. So when you see null access_token, maybe there's no id_token in cache at the time ATS is called? Right now it works as expected for our product team. |
I don't know whether there is or there isn't id_token in cache (how do I get to know that?).
The call succeeds, the returned authResponse.accessToken is null, while authResponse.idToken.rawIdToken contains a valid (and even not expired) token. Are you saying this behavior is expected? |
|
@scale-tone Hope it helps. |
|
@ayuspark , |
|
@scale-tone access tokens expire every hour. If the application needs to keep the token valid for longer times, please call The documentation for this can be found here. Let us know if you have any more questions. |
|
@mmuarc @scale-tone The new beta: Closing this. Please raise a new issue if needed. |
|
quoting @ayuspark from above:
It just hit me that it is the same situation in my application and it is not clear that the only reason I created a new scope was to avoid sending the clientId as the only scope. The scope I created does not serve any other purpose. Quoting myself from above:
Thanks for woking on this everyone who contributed! Looks like the issue with mutating the scope has been resolved. Unless I am missing something in this thread, the only way to avoid a null accessToken for those who are sending in the clientID as the only scope is to do what I have suggested. Can anyone confirm or deny this? |
Are you really suggesting to time the expiry in the client? I don't think people can put a timer in their client app to check if it's time to refresh the token.. |
Sadly this is what I ended doing. Putting a timer in my client to keep refreshing the token every X minutes or you lose your session and the calls will fail. I don't think it is a good approach at all but we are forced to do this as per the current implementation |
That's indeed sad :( What I did was intercepting my calls (with axios in React) and checking for a 401, then I would call the 'acuireTokenSilent' to get a new token and add it to the request. Have a look at this, maybe it can help :) |
I have something similar (using fetch). But still if your application, like mine, needs to stay logged for long periods without doing any request to the server you need to keep refreshing the token periodically ( I specifically refresh the idtoken) or when you try to do a request after let's say 1 hour and a half idle the access token renew won't work without user interaction, which means redirecting the user to the login page. I didn't want to do that so I had to put the timer to keep the session alive. I don't think there is a way around that since azure b2c doesn't support renew tokens in the flow they support for single page applications. |
I'm submitting a...
[ ] Regression (a behavior that used to work and stopped working in a new release)
[ ] Bug report
[ ] Performance issue
[ ] Feature request
[ ] Documentation issue or request
[ x] Other... Please describe:
Technical doubt and possibly a bug.
Browser:
Library version
<
Library version: 1.0.0
Current behavior
accessToken from acquireTokenSilent is null sometimes
Expected behavior
accessToken from acquireTokenSilent is never null. Any error should come in the error function.
Minimal reproduction of the problem with instructions
I have an apihelper that every time is going to do a call contacts my clientApplication wrapper like this:
The implementation of Ab2c.getTokenAsync is this:
So, basically I'm relying in clientApplication to handle the cached token for me since I understood that's what I'm supposed to do when using msal. But sometimes when I hit F5 in my page I get a valid loginResponse with a null accessToken.
When I refresh I do like 4 or 5 different requests which means 4 or 5 different calls to acquiretokensilent. What I see is that sometimes all of them work and sometimes the first actually works and returns a token but the following return a null value, most of the times all of them work...
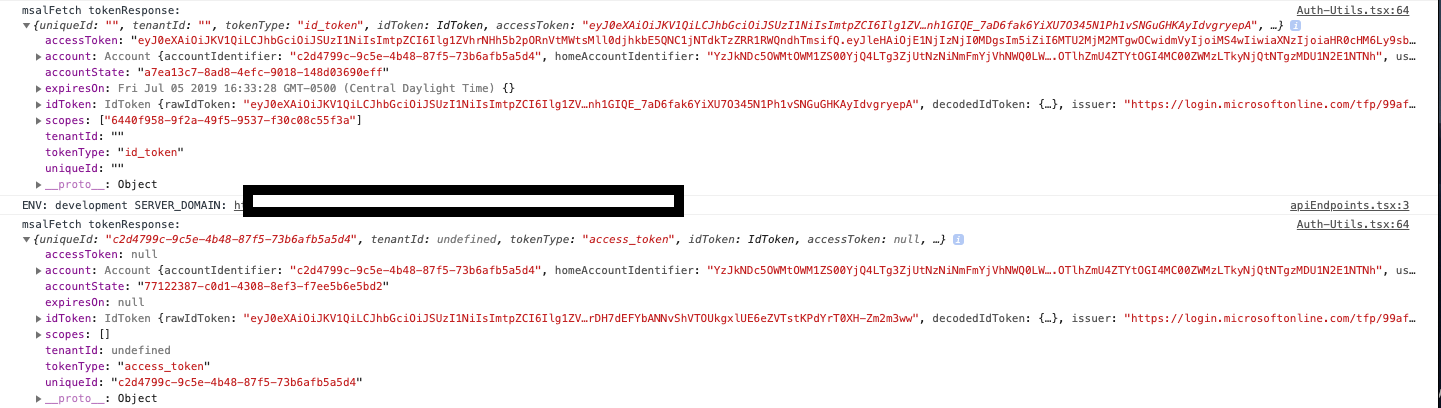
Log example.
valid token null token valid token valid token valid token valid tokenI think it might be related to refreshing while some request is still pending but I can't prove it.
Any ideas?
Miguel
The text was updated successfully, but these errors were encountered: