-
Notifications
You must be signed in to change notification settings - Fork 21.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Audit SAML (SSO) Certs expired dates through Powershell. #48662
Comments
|
@Ashok103606 Thanks for your feedback! We will investigate and update as appropriate. |
|
@Ashok103606 This is not possible and I suggest you to please post this as a feedback at UserVoice. This will allow the community to upvote and for the product team to include into their plans. "This Product" button in at the bottom section of the document now to take you directly to the appropriate feedback page. |
|
@saurabhsharma. So, you mean it's not Possible with the Powershell or totally azure does not have this feature. If I want to see the SAML certificate expired date of each application should I navigate to each application in Azure UI, this is the only option which available. |
|
@Ashok103606 sorry, my mistake. If you want to check for the certificate expiration associated with a particular SAML based application. Try using "Get-AzureADServicePrincipal" PowerShell cmdlet and then you can retrieve the certificate expiry dates using .KeyCredentials attribute. I hope you are looking for this information. |
|
@saurabhsharma Thanks for your information. But, Is there anyway that I can expose them as a report like Application name, Object Id , Certificate Expired date for SAML non-gallery application. With the following cmdlets with you provide that I need to pass each ObjectID for every application. $samlApplication = Get-AzureADServicePrincipal -ObjectId <> Like If I run the Get-AzureADApplication cmdlet how it gives objectId, AppId, Application name. |
|
@Ashok103606 No, I do not think any cmdlet exists which displays the information like a report. You may try writing PowerShell script to go through all applications and display matched application objects. |
|
@Ashok103606 We will now proceed to close this thread. If there are further questions regarding this matter, please reopen it and we will gladly continue the discussion. |
|
For anyone who is interested, I tossed together a quick script to show the expiring SAML certs in AzureAD Enterprise Applications. I hope this is of use to someone. |
|
I will have to try this out, I have been trying to find this information for a while, so it will be easier to manage our SAML SSO applications. Azure should of thought of something like this to prevent downtime. I will let you know my results and any modifications needed. |
|
I could not find a way to pull this info via graph api, but the saml signing cert can be retrieved from the metadata URL which is public, via this method: $saml_certificate.NotBefore and $saml_certificate.NotAfter will give you the signing cert start end expiry dates |
@samspade21 thanks a lot. But could you tell me what I need to provide at $doneID. Thanks again. |
|
@sktsjvs15 shouldn't need to touch that. I was just using that as a placeholder to not show the same application multiple times. Sort of a cheater (and not good) way to get a unique list. |
Hi @samspade21 I'm sorry I couldn't reply earlier. That script worked, absolute charm. Thanks a lot :) I am trying to schedule it to receive the report in an email. Thanks again. |
|
@sktsjvs15 Were you able to get the script to function as a scheduled task to email the Azure app cert expirations? Ig so, can you provide assistance on this? Thanks. |
|
Hi @phunboy, Here are the steps I did to scheduling the PowerShell script in Azure Automation:
4.Schedule the runbook: In the runbook page, click on the "Schedules" tab. Here, you can create a new schedule for your runbook. Click on "Add schedule" and define the schedule details, such as the start time, recurrence (weekly in my case), and any specific days or times when the script should run. Save the schedule. 5.Publish your runbook. Azure Automation will automatically trigger it based on the defined schedule after publishing. |
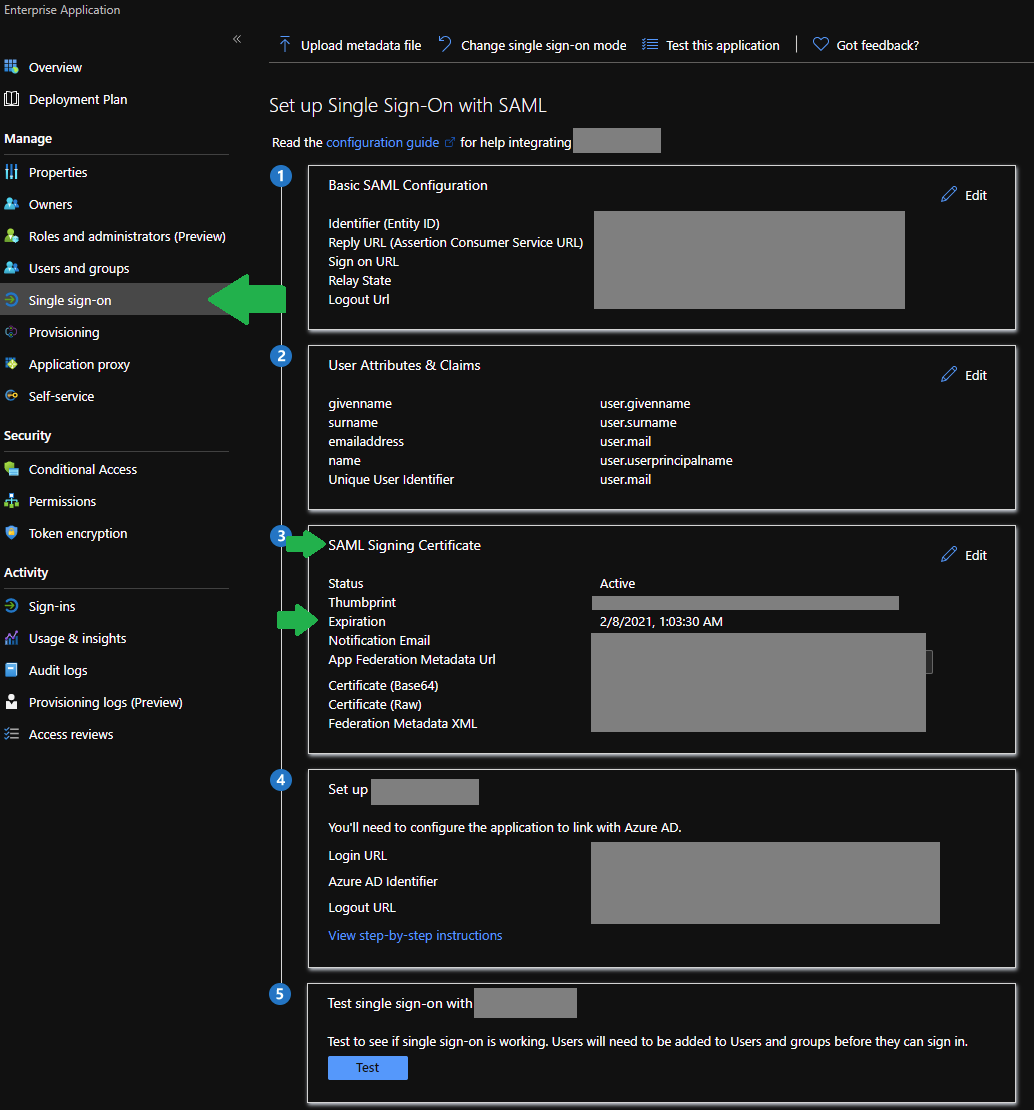
Is it possible to use PowerShell (AzureAD) to expose the expiration dates of SSO SAML certs? I would identify apps with expiring certs so they can be renewed in a timely fashion. Or is there a report or something else in Azure that can be run to expose this?
Document Details
⚠ Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.
The text was updated successfully, but these errors were encountered: