-
Notifications
You must be signed in to change notification settings - Fork 21.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
AKS authorized ip ranges does not mention devops environments #49578
Comments
|
@jemag Thank you for your feedback! We will review and provide an update as appropriate. |
|
@MicrosoftDocs/aks-pm Please add your comments. |
|
@jemag Once we enable the authorized ip ranges, Then it will allow only the ips added to that. So it restricts other environments to connect. For example , for the azure pipelines to connect, We need to add the ips of pipelines for that regions to the authorized ip ranges. problem is that those ips may change on weekly basis. Lets wait for the comments from the aks-pm team. |
|
@jemag Only way is to add the ips used by the azure pipelines of that region to the authorized ips list. Also we need to update the ips when it changes for that region. Please provide a feedback here for improvement. Community can vote on this feedback and product teams will look into this items to build their backlog |
|
@jakaruna-MSFT that seems quite unfortunate if this is the only option. With authorized IP ranges and now Private API Server in preview, it seems like there should be a better way to handle this. Having a Private API Server would be inconvenient with the current Environments requirements. Anyway, thanks for the clarification I will try to create a feedback post a suggested. |
|
@jakaruna-MSFT just to be sure, the link you provided is for AKS feedback, wouldn't it be more appropriate to leave the feedback for azure devops instead? Since environments is purely a devops concept. |
|
You can submit feedback in azure devops as well. It would be easier to add "allow Azure devops" as one of the rule in Authorized ip ranges. |
|
I have added this issue for review with Product team |
|
Adding the devops feedback url, for those who come by this issue: https://developercommunity.visualstudio.com/idea/947371/allow-devops-environments-communication-with-prote.html |
|
@jemag |
|
i faced similar issue today with AKS+Azure DevOps pipeline that AzureDevOps cannot connect to AKS with Authorized Ips even with correct IP regions ,, and we were able to solve by adding following Azure CLI task in the Azure Dev Ops : Task 1: add the MS hosted Ips Task 2: remove only the Agent Ip az aks update hope this helps |
Unless I am mistaken, restricting the ip ranges will prevent azure devops environments to connect to the cluster:
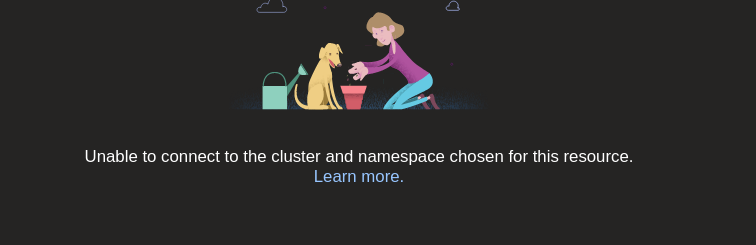
This scenario does not seem to be talked about in the documentation.
Are there any ways to make environments still work in such a setup? Perhaps by using some kind of agent pushing the data instead or re-using an hosted vsts agent?
Document Details
⚠ Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.
The text was updated successfully, but these errors were encountered: