Certificate rotation #6722
Labels
area/core
feature/tentacle
kind/enhancement
This issue represents an enhancement we are committed to adding to Octopus as some time
Prerequisites
The enhancement
What is the problem this solves or benefit it gives
There is multiple scenarios where this issue will become apparent however possibly the most common scenario will be the following:
If a customer has a bunch of polling tentacles connected using websockets, a Tentacles "Trusted Octopus Server thumbprint" value is not set to the Octopus Server thumbprint. It has to be set to the certificate fingerprint as described here: https://octopus.com/docs/infrastructure/deployment-targets/windows-targets/polling-tentacles-web-sockets#thumbprints
This will mean that the SSL certificate will likely expire every 2 years (possibly sooner) and the trusted fingerprint will need to be changed on all tentacles. This also means that the change to the new trusted certificate needs to happen at roughly the same time as the certifcate change on the server.
It is possible to automate the trusted certifcate task by using the Update-Trust Command. ( https://octopus.com/docs/octopus-rest-api/tentacle.exe-command-line/update-trust ). This causes multiple issues:
The other option is to add a second trusted Octopus Server so that at any point in time, the tentacle will have valid certifcate that it trusts.
Unfortunately the configuration can't be completed, using the Tentacle CLI.
The following command will work:
Tentacle.exe configure --trust=xxxxxxxxhowever this will result in the a configuration file similar to this one:
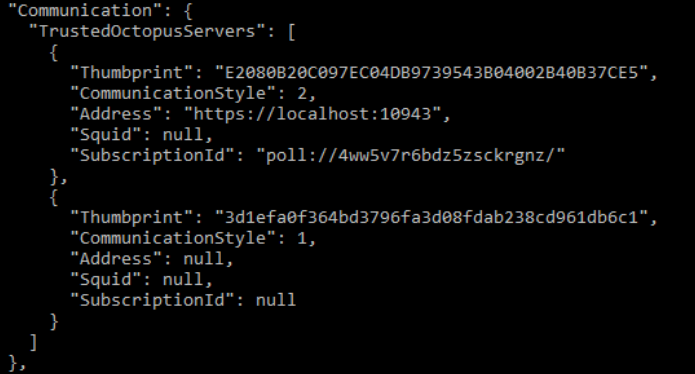
As you can see, without
The second trusted Octopus Server will not work.
Tentacle.exe configure --trust=xxxxxxxxdoes not accept any of the following parameters:--address
--comms-style
--server
Proposed solution
Make it mandatory for
Tentacle.exe configure --trust=xxxxxxxxto include the following additional parameters:--address (or --server)
--comms-style
Workarounds
Currently the only solution to this issue is to set up a scheduled task that will:
This scheduled task needs to be set with two triggers.
Links
https://octopus.zendesk.com/agent/tickets/62880
https://octopus.zendesk.com/agent/tickets/2403
https://octopus.zendesk.com/agent/tickets/19737
https://help.octopus.com/t/octopus-server-trust-certificate-rotation/22604/15
https://octopus.zendesk.com/agent/tickets/64930
The text was updated successfully, but these errors were encountered: