Summary
A reflected cross-site scripting (XSS) vulnerability has been discovered in the /admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=[here] page. This vulnerability can be exploited by an attacker to inject malicious HTML and JS code into the HTML page, which could then be executed by admin users when they visit the URL with the payload.
Details
The vulnerability is caused by the insecure injection of the plugin_id value from the URL into the HTML page. An attacker can exploit this vulnerability by crafting a malicious URL that contains a specially crafted plugin_id value. When a victim who is logged in as an administrator visits this URL, the malicious code will be injected into the HTML page and executed.
Vulnerable code
Using the &installstatus=ok parameter I was able to trigger the function that insecurely injects the plugin_id value of the url into the HTML to render, so we can execute JS
|
//--------------------------------------------------------------install result |
|
if (isset($_GET['installstatus'])) |
|
{ |
|
switch ($_GET['installstatus']) |
|
{ |
|
case 'ok': |
|
$activate_url = get_root_url().'admin.php?page=plugins' |
|
. '&plugin=' . $_GET['plugin_id'] |
|
. '&pwg_token=' . get_pwg_token() |
|
. '&action=activate' |
|
. '&filter=deactivated'; |
|
|
|
$page['infos'][] = l10n('Plugin has been successfully copied'); |
|
$page['infos'][] = '<a href="'. $activate_url . '">' . l10n('Activate it now') . '</a>'; |
|
|
PoC
Logged in as administrator, use the following code as the path to your hosted piwigo application
/admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=nfez2%22%3E%3Cscript%3Eprompt(/SEQODE/)%3C%2fscript%3Ehkugi
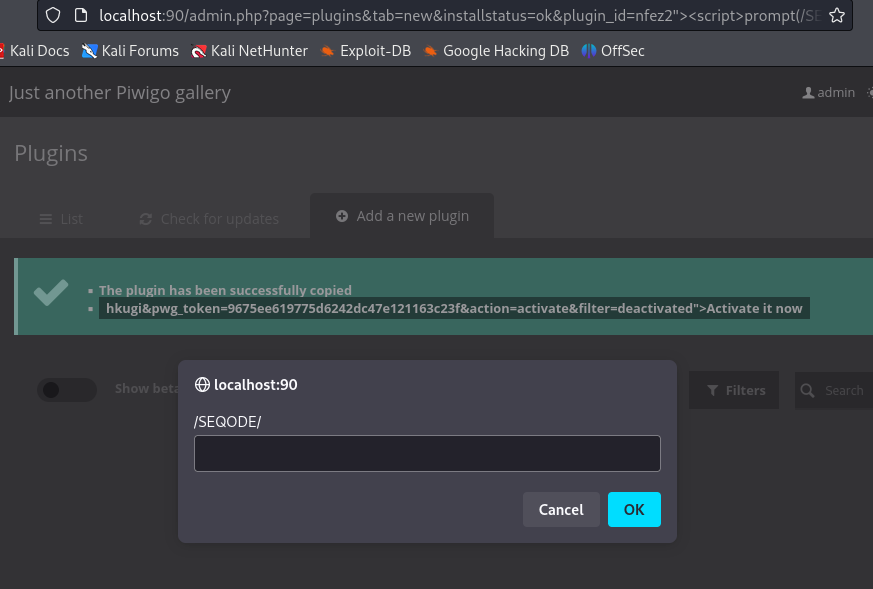
Impact
This is a reflected cross-site scripting (XSS) vulnerability. XSS is a type of web application vulnerability that allows an attacker to inject malicious code into the web page that is displayed to the victim. The malicious code can then be executed by the victim's browser, which can give the attacker control over the victim's account or even their entire computer.
This vulnerability can be exploited by any attacker who has access to a malicious URL. However, only users who are logged in as administrators are affected. This is because the vulnerability is only present on the /admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=[here] page, which is only accessible to administrators.
Summary
A reflected cross-site scripting (XSS) vulnerability has been discovered in the
/admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=[here]page. This vulnerability can be exploited by an attacker to inject malicious HTML and JS code into the HTML page, which could then be executed by admin users when they visit the URL with the payload.Details
The vulnerability is caused by the insecure injection of the
plugin_idvalue from the URL into the HTML page. An attacker can exploit this vulnerability by crafting a malicious URL that contains a specially craftedplugin_idvalue. When a victim who is logged in as an administrator visits this URL, the malicious code will be injected into the HTML page and executed.Vulnerable code
Using the
&installstatus=okparameter I was able to trigger the function that insecurely injects theplugin_idvalue of the url into the HTML to render, so we can execute JSPiwigo/admin/plugins_new.php
Lines 44 to 58 in c5b5dd0
PoC
Logged in as administrator, use the following code as the path to your hosted piwigo application

/admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=nfez2%22%3E%3Cscript%3Eprompt(/SEQODE/)%3C%2fscript%3Ehkugi
Impact
This is a reflected cross-site scripting (XSS) vulnerability. XSS is a type of web application vulnerability that allows an attacker to inject malicious code into the web page that is displayed to the victim. The malicious code can then be executed by the victim's browser, which can give the attacker control over the victim's account or even their entire computer.
This vulnerability can be exploited by any attacker who has access to a malicious URL. However, only users who are logged in as administrators are affected. This is because the vulnerability is only present on the
/admin.php?page=plugins&tab=new&installstatus=ok&plugin_id=[here]page, which is only accessible to administrators.