Affected product: Vitogate 300
Vendor of the product: Viessmann
Product page: https://connectivity.viessmann.com/gb/mp-fp/vitogate/vitogate-300-bn-mb.html
Affected system version: 2.1.3.0 and lower
Firmware download address: https://connectivity.viessmann.com/gb/mp-fp/vitogate/vitogate-300-bn-mb/release-historie.html
Reported by: Wentao Yang (pushe4x@gmail.com)
Vitogate 300 is a gateway for connecting the Viessmann LON to the BACnet or Modbus. Two hardcoded administrative accounts that hardcoded in /cgi-bin/vitogate.cgi allows full access to the web management interface. One of them is a hidden account, absent from the backend account management and immune to removal or password modification.
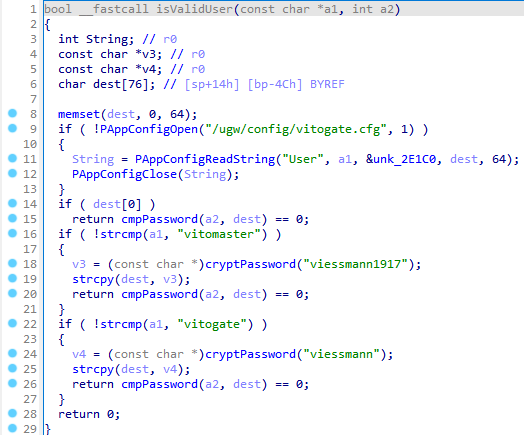
The isValidUser() function in the /ugw/httpd/html/cgi-bin/vitogate.cgi binary is utilised to authenticate credentials during user sign-in.
The function contains two hardcoded administrative accounts: "vitomaster" and "vitogate", with passwords "viessmann1917" and "viessmann".
Notably, "vitomaster" is a hidden account, absent from the backend account management and immune to removal or password modification.
Vulnerable Vitogate 300 device incorporates the following hardcoded administrative accounts:
- Username: vitomaster, Password: viessmann1917
- Username: vitogate, Password: viessmann