Study guide that maps the Exam SC-900: Microsoft Security, Compliance, and Identity Fundamentals to the Microsoft Skills Measured PDF
| Methodologies | Description |
|---|---|
| Zero-Trust methodology | Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network. Regardless of where the request originates or what resource it accesses, the Zero Trust model teaches us to "never trust, always verify." The Zero Trust model has three principles which guide and underpin how security is implemented. These are: verify explicitly, least privilege access, and assume breach. 1 - Verify explicitly. Always authenticate and authorize based on the available data points, including user identity, location, device, service or workload, data classification, and anomalies. 2 - Least privileged access. Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive policies, and data protection to protect both data and productivity. 3 - Assume breach. Segment access by network, user, devices, and application. Use encryption to protect data, and use analytics to get visibility, detect threats, and improve your security. Six foundational pillars of Zero Trust In the Zero Trust model, all elements work together to provide end-to-end security. These six elements are the foundational pillars of the Zero Trust model: 1 - Identities may be users, services, or devices. When an identity attempts to access a resource, it must be verified with strong authentication, and follow least privilege access principles. 2 - Devices create a large attack surface as data flows from devices to on-premises workloads and the cloud. Monitoring devices for health and compliance is an important aspect of security. 3 - Applications are the way that data is consumed. This includes discovering all applications being used, sometimes called Shadow IT because not all applications are managed centrally. This pillar also includes managing permissions and access. 4 - Data should be classified, labeled, and encrypted based on its attributes. Security efforts are ultimately about protecting data, and ensuring it remains safe when it leaves devices, applications, infrastructure, and networks that the organization controls. 5 - Infrastructure, whether on-premises or cloud based, represents a threat vector. To improve security, you assess for version, configuration, and JIT access, and use telemetry to detect attacks and anomalies. This allows you to automatically block or flag risky behavior and take protective actions. 6 - Networks should be segmented, including deeper in-network micro segmentation. Also, real-time threat protection, end-to-end encryption, monitoring, and analytics should be employed. 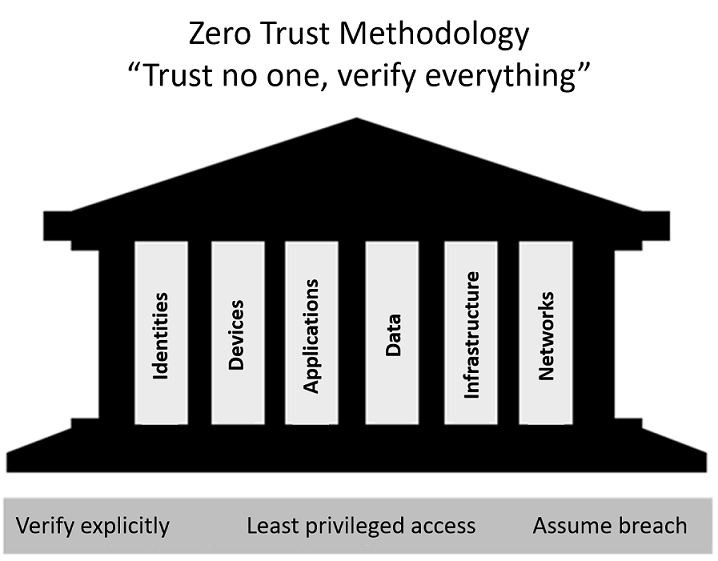 |
| Shared responsibility model | Reference AZ-900 |
| Defense in Depth | Defense in depth is a strategy that employs a series of mechanisms to slow the advance of an attack that's aimed at acquiring unauthorized access to information. Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure. |
| Common threats | Common threats include: • Data breach - A data breach is when data is stolen, and this includes personal data. • Dictionary attack - A dictionary attack is a type of identity attack where a hacker attempts to steal an identity by trying a large number of known passwords. Each password is automatically tested against a known username. Dictionary attacks are also known as brute force attacks. • Ransomware - Malware is the term used to describe malicious applications and code that can cause damage and disrupt normal use of devices. Malware can give attackers unauthorized access, which allows them to use system resources, lock you out of your computer, and ask for ransom. • Disruptive attacks - A Distributed Denial of Service (DDoS) attack attempts to exhaust an application's resources, making the application unavailable to legitimate users. DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet. Other common threats include coin miners, rootkits, trojans, worms, and exploits and exploit kits. |
| Encryption / hashing | There are two top-level types of encryption: symmetric and asymmetric. Symmetric encryption uses the same key to encrypt and decrypt the data. Asymmetric encryption uses a public key and private key pair. Either key can encrypt data, but a single key can’t be used to decrypt encrypted data. To decrypt, you need a paired key. Asymmetric encryption is used for things like Transport Layer Security (TLS), such as the HTTPS protocol, and data signing. Encryption may protect data at rest, or in transit. 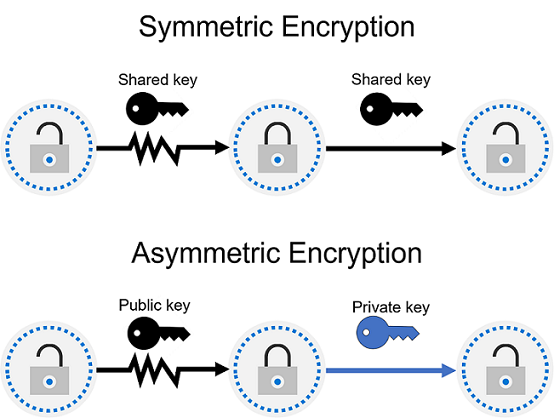 Encryption at rest also known as, data at rest, is the data that's stored on a physical device, such as a server. It may be stored in a database or a storage account but, regardless of where it's stored, encryption of data at rest ensures the data is unreadable without the keys and secrets needed to decrypt it. If an attacker obtained a hard drive with encrypted data and didn't have access to the encryption keys, they would be unable to read the data. Encryption in transit - Data in transit is the data moving from one location to another, such as across the internet or through a private network. Secure transfer can be handled by several different layers. It could be done by encrypting the data at the application layer before sending it over a network. HTTPS is an example of encryption in transit. Encrypting data in transit protects it from outside observers and provides a mechanism to transmit data while limiting the risk of exposure. Hashing - uses an algorithm to convert the original text to a unique fixed-length hash value. Each time the same text is hashed using the same algorithm, the same hash value is produced. That hash can then be used as a unique identifier of its associated data. Hashing is different to encryption in that it doesn't use keys, and the hashed value isn't subsequently decrypted back to the original. Hashing is used to store passwords. When a user enters their password, the same algorithm that created the stored hash creates a hash of the entered password. This is compared to the stored hashed version of the password. If they match, the user has entered their password correctly. This is more secure than storing plain text passwords, but hashing algorithms are also known to hackers.  |
| Confidentiality, Integrity, Availability (CIA) | Confidentiality refers to the need to keep confidential sensitive data such as customer information, passwords, or financial data. Integrity refers to keeping data or messages correct. Availability refers to making data available to those who need it. |
| Cloud Adoption Framework for Azure | The Microsoft Cloud Adoption Framework (CAF) for Azure is guidance that provides a proven and consistent methodology for implementing cloud technologies that are designed to help you create and implement business and technology strategies for the cloud based on best practices, documentation, and tools. CAF lifecycle includes the following: 1. Strategy - Define business justification and expected outcomes of adoption. 2. Plan - Align actionable adoption plans to business outcomes. 3. Ready - Prepare the cloud environment for the planned changes and move resources in. 4. Adopt: • Migrate: Migrate and modernize existing workloads. • Innovate: Develop new cloud-native or hybrid solutions. 5. Govern - Establish a well-managed cloud environment 6. Manage - Operations management for cloud and hybrid solutions. What is the Microsoft Cloud Adoption Framework for Azure? |
| Identity concepts | Description |
|---|---|
| Identity as the primary security perimeter | The traditional perimeter-based security model is no longer enough. Identity has become the new security perimeter that enables organizations to secure their assets. An identity is how someone or something can be verified and authenticated to be who they say they are. An identity may be associated with a user, an application, a device, or something else. Addressing each of these four pillars is key to a comprehensive and robust identity and access control solution. Four pillars of identity Identity is a concept that spans an entire environment, so organizations need to think about it broadly. There's a collection of processes, technologies, and policies for managing digital identities and controlling how they're used to access resources. There are four fundamental pillars of identity that organizations should consider when creating an identity infrastructure. 1 - Administration - Administration is about the creation and management/governance of identities for users, devices, and services. As an administrator, you manage how and under what circumstances the characteristics of identities can change (be created, updated, deleted). 2 - Authentication - The authentication pillar tells the story of how much assurance for a particular identity is enough. In other words, how much does an IT system need to know about an identity to have sufficient proof that they really are who they say they are? It involves the act of challenging a party for legitimate credentials. Authentication is sometimes shortened to AuthN. 3 - Authorization - The authorization pillar is about processing the incoming identity data to determine the level of access an authenticated person or service has within the application or service that it wants to access. Authorization is sometimes shortened to AuthZ. 4 - Auditing - The auditing pillar is about tracking who does what, when, where, and how. Auditing includes having in-depth reporting, alerts, and governance of identities. |
| Authentication (Who are you?) | The process of establishing the identity of a person or service looking to access a resource. It involves the act of challenging a party for legitimate credentials, and provides the basis for creating a security principal for identity and access control use. It establishes if they are who they say they are. |
| Authorization (What are you allowed to do?) | The process of establishing what level of access an authenticated person or service has. It specifies what data they're allowed to access and what they can do with it. |
| Identity providers | An identity provider creates, maintains, and manages identity information while providing authentication services to applications. When sharing your apps and resources with external users, Azure AD is the default identity provider for sharing. This means when you invite external users who already have an Azure AD or Microsoft account, they can automatically sign in without further configuration on your part. • Azure B2B collaboration collaboration lets you securely share your company's applications and services with guest users from any other organization, while maintaining control over your own corporate data. • B2C access management an idenity management solution for consumer facing apps. The Azure AD B2C service allows you to manage customer identities and their access to your applications. Identity Providers for External Identities |
| Active Directory | A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as names, passwords, phone numbers, and so on, and enables other authorized users on the same network to access this information. Overview of Active Directory Domain Services (AD DS) |
| Concept of Federated Services | Federation enables the access of services across organizational or domain boundaries by establishing trust relationships between the respective domain’s identity provider. With federation, there's no need for a user to maintain a different username and password when accessing resources in other domains. Federation is a collection of domains that have established trust. The level of trust may vary, but typically includes authentication and almost always includes authorization. You can federate your on-premises environment with Azure AD and use this federation for authentication and authorization. This sign-in method ensures that all user authentication occurs on-premises. This method allows administrators to implement more rigorous levels of access control. Federation with AD FS and PingFederate is available. |
| Identity Attacks | Password-based attacks - Many password-based attacks employ brute force techniques to gain unauthorized access. In a brute force attack, an attacker will attempt to gain access simply by trying different usernames and password combinations. Phishing - A phishing attack is when a hacker sends an email that appears to come from a reputable source. The email contains a credible story, such as a security breach, instructing the user to sign in and change their password. Instead of going to a legitimate website, the user is directed to the scammer’s website where they enter their username and password. The hacker has now captured the user’s identity, and their password. Spear phishing - A spear phishing scam is a variant on phishing. Hackers build databases of information about users, which can be used to create highly credible emails. The email may appear to come from someone in your organization who is requesting information. Although careful scrutiny might uncover the fraud, users may not read it carefully enough and send the requested information or login to the website before they realize the fraud. This practice is called spear phishing because it's highly targeted. |
| Capabilities Term | Description |
|---|---|
| Azure Active Directory | Reference AZ-900 |
| Azure AD identities | User - A user identity is a representation of something that's managed by Azure AD. Employees and guests are represented as users in Azure AD. If you have several users with the same access needs, you can create a group. You use groups to give access permissions to all members of the group, instead of having to assign access rights individually. Service principal - A service principal is a security identity used by applications or services to access specific Azure resources. You can think of it as an identity for an application that is commonly reffered to by its Service Principal Name (SPN). Managed identity -Managed identities are typically used to manage the credentials for authenticating a cloud application with an Azure service. Managed identities are automatically managed in Azure AD and may be user assigned or system assigned. There are several benefits to using managed identities, including: • Application developers can authenticate to services that support managed identities for Azure resources. For a complete list of services, refer to Azure Services that support managed identities. • Any Azure service that supports Azure AD authentication can use managed identities to authenticate to another Azure service; for example, accessing Azure Key Vault. Managed identities can be used without any extra cost. Device - A device is a piece of hardware, such as mobile devices, laptops, servers, or printer. Device identities can be set up in different ways in Azure AD, to determine properties such as who owns the device. |
| Hybrid identity | Hybrid identity referes to an identity solution that allows users both on-premises and in the cloud to authenticate using a single common user identity. Three hybrid authentication models exist within Azure: Password hash synchronization (PHS) - Password hash synchronization is one of the sign-in methods used to accomplish hybrid identity. Azure AD Connect synchronizes a hash, of the hash, of a user's password from an on-premises Active Directory instance to a cloud-based Azure AD instance. Pass-through authentication (PTA) - Azure Active Directory (Azure AD) pass-through authentication allows your users to sign in to both on-premises and cloud-based applications by using the same passwords. Pass-through authentication signs users in by validating their passwords directly against on-premises Active Directory. Federated authentication - Federation is a collection of domains that have established trust. The level of trust may vary, but typically includes authentication and almost always includes authorization. Azure AD Connect provides a simplified method to enable these hybrid solutions and allow users to log into Azure AD resources using their on-premises password. |
| Different external identity types (Guest Users) | With External Identities in Azure AD, you can allow people outside your organization to access your apps and resources, while letting them sign in using whatever identity they prefer. Within this framework, Azure AD supports a variety of scenarios from business-to-business (B2B) collaboration to access management for consumer/customer- or citizen-facing applications (business-to-customer, or B2C). Azure AD External Identities focuses less on a user's relationship to your organization and more on how the user wants to sign in to your apps and resources. John Saville YouTube |
| What is a device identity? | A device identity is an object in Azure Active Directory (Azure AD). This device object is similar to users, groups, or applications. A device identity gives administrators information they can use when making access or configuration decisions. There are three ways to get a device identity: • Azure AD registration • Azure AD join • Hybrid Azure AD join Device identities are a prerequisite for scenarios like device-based Conditional Access policies and Mobile Device Management with Microsoft Endpoint Manager. |
| Term | Description |
|---|---|
| Different authentication methods |  |
| What authentication and verification methods are available in Azure Active Directory? | Verification methods include: • Mobile app notification • Mobile app code • Mobile phone (SMS) • Office phone (voice) • Security questions • Physical token (e.g. FIDO2 key) |
| Self-service password reset (SSPR) | Azure Active Directory (Azure AD) self-service password reset (SSPR) gives users the ability to change or reset their password, with no administrator or help desk involvement. Self-service password reset works in the following scenarios: • Password change: when a user knows their password but wants to change it to something new. • Password reset: when a user can't sign in, such as when they forget the password, and want to reset it. • Account unlock: when a user can't sign in because their account is locked out. Self-service password reset (SSPR) |
| Password protection and management capabilities | • Global banned password list - A global banned password list with known weak passwords is automatically updated and enforced by Microsoft. This list is maintained by the Azure AD Identity Protection team, who analyze security telemetry data to find weak or compromised passwords. Examples of passwords that might be blocked are P@$$w0rd or Passw0rd1 and all variations. • Custom banned password lists - Admins can also create custom banned password lists to support specific business security needs. The custom banned password list prohibits passwords such as the organization name or location. • Protecting against password spray - Most password spray attacks submit a few of the known weakest passwords against each of the accounts in an enterprise. • Hybrid security - For hybrid security, admins can integrate Azure AD Password Protection within an on-premises Active Directory environment. |
| Azure Multi-Factor Authentication | Multi-factor authentication (MFA) provides additional security for your identities by requiring two or more elements for full authentication. These elements fall into three categories: • Something you know • Something you possess • Something you are |
| Windows Hello for Business | Windows Hello, an authentication feature built into Windows 10, replaces passwords with strong two-factor authentication on PCs and mobile devices. This authentication consists of a new type of user credential that's tied to a device and uses a biometric or PIN. Windows Hello lets users authenticate to: • A Microsoft account. • An Active Directory account. • An Azure Active Directory (Azure AD) account. • Identity Provider Services or Relying Party Services that support Fast ID Online (FIDO) v2.0 authentication (in preview) There are two configurations for Windows Hello: Windows Hello convenience PIN and Windows Hello for Business. • Windows Hello convenience PIN is configured by a user on their personal device. Windows Hello convenience PIN is not backed by asymmetric (public or private key) or certificate-based authentication. • Windows Hello for Business is configured by Group Policy or mobile device management (MDM) policy, such as Microsoft Intune. In addition, the PIN or biometric used with Windows Hello for Business is backed by key-based or certificate-based authentication, making it more secure than Windows Hello convenience PIN. |
| Term | Description |
|---|---|
| Conditional Access | Conditional Access is a feature of Azure AD that provides an extra layer of security before allowing authenticated users to access data or other assets. Conditional Access is implemented through policies that are created and managed in Azure AD. A Conditional Access policy analyses signals including user, location, device, application, and risk to automate decisions for authorizing access to resources (apps and data). What is Conditional Access? |
| Uses and benefits of conditional access | When the Conditional Access policy has been applied, an informed decision is reached on whether to grant access, block access, or require extra verification. The decision is referred to as the access controls portion of the Conditional Access policy and defines how a policy is enforced. Common decisions • Block access • Most restrictive decision • Grant access • Least restrictive decision, can still require one or more of the following options: • Require multi-factor authentication • Require device to be marked as compliant • Require Hybrid Azure AD joined device • Require approved client app • Require app protection policy (preview) Many organizations have common access concerns that Conditional Access policies can help with such as: • Requiring multi-factor authentication for users with administrative roles • Requiring multi-factor authentication for Azure management tasks • Blocking sign-ins for users attempting to use legacy authentication protocols • Requiring trusted locations for Azure AD Multi-Factor Authentication registration • Blocking or granting access from specific locations • Blocking risky sign-in behaviors • Requiring organization-managed devices for specific applications |
| Benefits of Azure AD roles | Azure AD roles control permissions to manage Azure AD resources. There are many built-in roles for different areas of responsibility. All built-in roles are preconfigured bundles of permissions designed for specific tasks. Azure AD built-in and custom roles are a form of RBAC in that Azure AD roles control access to Azure AD resources. It's best practice, and more secure, to grant users the least privilege to get their work done. |
| Term | Description |
|---|---|
| Identity governance | Azure Active Directory (Azure AD) Identity Governance allows you to balance your organization's need for security and employee productivity with the right processes and visibility. It provides you with capabilities to ensure that the right people have the right access to the right resources. Identity Governance give organizations the ability to do the following tasks across employees, business partners and vendors, and across services and applications both on-premises and in clouds: • Govern the identity lifecycle • Govern access lifecycle • Secure privileged access for administration Specifically, it is intended to help organizations address these four key questions: • Which users should have access to which resources? • What are those users doing with that access? • Are there effective organizational controls for managing access? • Can auditors verify that the controls are working? |
| Entitlement management | Azure Active Directory (Azure AD) entitlement management is an identity governance feature that enables organizations to manage identity and access lifecycle at scale, by automating access request workflows, access assignments, reviews, and expiration. Allows your organization to manage access to groups, applications, and SharePoint online sites for both useres internal and external or the org. This includes self service workflows, approval workflows and expiration policies. It does this in part by leveraging "access packages". An access package is a bundle of all the resources with the access a user needs to work on a project or perform their task. |
| Access reviews | Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. Primarily it provides: • Enables organizations to recertify, attest and audi users' access to resources - Office groups, Azure AD groups, Azure AD integration apps, Azure AD roles and Azure RBAC roles • Approve or deny employees and guest users continued access • Select reviewers to be group owners, members themselves and individuals in the directory • Recommends decisions to reviewer based on user sign-in activity • Option to set up recurring reviews and apply the decisions automatically When should you use access reviews? • Too many users in privileged roles • When automation is not possible • When a group is used for a new purpose • Business critical data access • To maintain a policy's exception list |
| Capabilities of Privileged Identity Management (PIM) | Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune. It does this through supporting the following: • Just-in-Time access (expires after per-defined activation period is over) • Time-bound assess (tied to start/end dates - Useful for guests/contractors) • Privileged Admin Workflow (e.g. manager OK's access) • Enforcement of MFA to activate role • Text box for user justification on their need to access a resources, which assists with internal / external audits. This may also include a ITSM ticket number. • Automated notifications sent to admins / SOC team. • Ability to perform access reviews through an audit history to determine a users need to continue access. This is sometimes referred to as an attestation campaign and can be delegated to groups or users to perform. • Downloadable audit history for internal / external audits. •Prevents removal of the last active Global Administrator role assignment PIM works with all built in and custom Azure AD Roles and Azure Resource Roles and is a CLOUD ONLY identity management solution. |
| Azure AD Identity Protection | Identity Protection is a tool that allows organizations to accomplish three key tasks: 1 - Automate the detection and remediation of identity-based risks. 2 - Investigate risks using data in the portal. 3 - Export risk detection data to your SIEM. It does this by categorizing (low/medium/high) identified risks of many types that include: • Anonymous IP address use • Atypical travel • Malware linked IP address • Unfamiliar sign-in properties • Leaked credentials • Password spray • Risky users • Risky sign-ins • Risk detentions |
| Term | Description |
|---|---|
| Network Security Groups (NSG) | NSGs operate at layers 3 & 4, and provide a list of allowed and denied (inbound / outbound) communication to and from network interfaces and subnets. NSGs are fully customizable, and give you the ability to fully lock down network communication to and from your virtual machines. By using NSGs, you can isolate applications between environments, tiers, and services. Note: NSGs uses static IP addresses and as your network scales this may become difficult to maintain. NSG security rules are evaluated by priority using five information points: source, source port, destination, destination port, and protocol to allow / deny |
| Azure DDoS Protection | DDoS Protection leverages the scale and elasticity of Microsoft’s global network to bring DDoS mitigation capacity to every Azure region. The Azure DDoS Protection service protects your Azure applications by scrubbing traffic at the Azure network edge before it can impact your service's availability. Within a few minutes of attack detection, you are notified using Azure Monitor metrics. Comes in two versions: Azure DDoS Protection Basic (Free) Azure DDoS Protection Standard (provides SLAs for Application and Cost Protection) Every property in Azure is protected by Azure's infrastructure DDoS (Basic) Protection at no additional cost and requires no user configuration or application changes.  DDoS Protection Standard can mitigate the following types of attacks: Volumetric attacks: These attacks flood the network layer with a substantial amount of seemingly legitimate traffic. They include UDP floods, amplification floods, and other spoofed-packet floods. DDoS Protection Standard mitigates these potential multi-gigabyte attacks by absorbing and scrubbing them, with Azure's global network scale, automatically. Protocol attacks: These attacks render a target inaccessible, by exploiting a weakness in the layer 3 and layer 4 protocol stack. They include SYN flood attacks, reflection attacks, and other protocol attacks. DDoS Protection Standard mitigates these attacks, differentiating between malicious and legitimate traffic, by interacting with the client, and blocking malicious traffic. Resource (application) layer attacks: These attacks target web application packets, to disrupt the transmission of data between hosts. They include HTTP protocol violations, SQL injection, cross-site scripting, and other layer 7 attacks. Use a Web Application Firewall, such as the Azure |
| Azure Firewall | Azure Firewall is a managed, cloud-based, network security service that protects your Azure Virtual Network resources. It is a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. Azure Firewall provides inbound protection for non-HTTP/S protocols. Examples of non-HTTP/S protocols include: Remote Desktop Protocol (RDP), Secure Shell (SSH), and File Transfer Protocol (FTP). It also provides outbound, network-level protection for all ports and protocols, and application-level protection for outbound HTTP/S. |
| Azure Bastion | Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal using Transport Layer Security (TLS). When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software. Key features of Azure Bastion include: • RDP and SSH directly in Azure portal • Remote session over TLS and firewall traversal for RDP/SSH: Use an HTML5-based web client that's automatically streamed to your local device. • No Public IP required on the Azure VM • No hassle of managing NSGs as you don't need to apply any NSGs on an Azure Bastion subnet • Protection against port scanning • Protect against zero-day exploits |
| Web Application Firewall | Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks. Web Application Firewall (WAF) provides centralized protection of your web applications from common exploits and vulnerabilities. A centralized WAF helps make security management simpler, improves the response time to a security threat, and allows patching a known vulnerability in one place, instead of securing each web application. A WAF also gives application administrators better assurance of protection against threats and intrusions. WAF can be deployed with Azure Application Gateway, Azure Front Door, and Azure Content Delivery Network (CDN) service from Microsoft. Introduction to Azure Web Application Firewalls |
Microsoft Azure provides many different ways to secure your data, each depending on the service or usage required.
- Azure Storage Service Encryption helps to protect data at rest by automatically encrypting before persisting it to Azure-managed disks, Azure Blob Storage, Azure Files, or Azure Queue Storage, and decrypts the data before retrieval.
- Azure Disk Encryption helps you encrypt Windows and Linux IaaS virtual machine disks. Azure Disk Encryption uses the industry-standard BitLocker feature of Windows and the dm-crypt feature of Linux to provide volume encryption for the OS and data disks.
- Transparent data encryption (TDE) helps protect Azure SQL Database and Azure Data Warehouse against the threat of malicious activity. It performs real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
Azure Key Vault is a centralized cloud service for storing your application secrets. Key Vault helps you control your applications' secrets by keeping them in a single, central location and by providing secure access, permissions control, and access logging capabilities. It's useful for different kinds of scenarios:
- Secrets management. You can use Key Vault to store securely and tightly control access to tokens, passwords, certificates, Application Programming Interface (API) keys, and other secrets.
- Key management. You can use Key Vault as a key management solution. Key Vault makes it easier to create and control the encryption keys used to encrypt your data.
- Certificate management. Key Vault lets you provision, manage, and deploy your public and private Secure Sockets Layer/ Transport Layer Security (SSL/ TLS) certificates for Azure, and internally connected, resources more easily.
- Store secrets backed by hardware security modules (HSMs). The secrets and keys can be protected either by software or by FIPS 140-2 Level 2 validated HSMs.
| Term | Description |
|---|---|
| Defender for Cloud | Defender for Cloud (formerly called Azure Security Center) is a monitoring service tool that provides threat protection across all of your services both in Azure, and on-premises and in other clouds due to integration with Azure Defender. Available in two tiers, Free (limited to assessments and recommendations only); Standard (full suite of security-related services including continious monitoring, threat detection and just-in-time access control) Usage scenarios: • Incident Response (Detect, Assess, Diagnose) • Implement Recommendations Key features include: • Compliance dashboard - Compares the configuration of your resources against requirements outlined within in industry standards, regulations, and benchmarks. • Security alerts - When Defender for Cloud detects a threat in any area of your environment, it generates a security alert. These alerts describe details of the affected resources, suggested remediation steps, and in some cases an option to trigger a logic app in response. • Secure score - A single score so that you can tell, at a glance, your current security situation (the higher the score, the lower the identified risk level). You can view your overall Secure score across your subscriptions or management groups, depending on the scope you select. The score is calculated based on the ratio between your healthy resources and your total resources and will vary based on subscription selected and the active recommendations on these subscriptions. • Resource security hygiene - Most prevalent recommendations and highest impact recommendations. |
| Azure secure score | Microsoft Defender for Cloud continually assesses your resources, subscriptions, and organization for security issues. It then aggregates all the findings into a single score so you can quickly see your current security situation: the higher the score, the lower the identified risk level. |
| Benefit and use cases of Azure Defender (now referred to as Microsoft Defender for Cloud) | Microsoft Defender for Cloud (formerly Azure Defender) is offered in two modes: • Without enhanced security features (free) - Microsoft Defender for Cloud is enabled for free on all your Azure subscriptions. Using this free mode provides the secure score and its related features: security policy, continuous security assessment, and actionable security recommendations to help you protect your Azure resources. • With enhanced security features (paid) - Enabling enhanced security extends the capabilities of the free mode to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads. Some of the major benefits of enhanced security features are listed below. Enhanced security features include the following: • Microsoft Defender for Endpoint - Microsoft Defender for servers includes Microsoft Defender for Endpoint for comprehensive endpoint detection and response (EDR). • Vulnerability scanning for virtual machines and container registries - Easily deploy a scanner to all of your virtual machines. View, investigate, and remediate the findings directly within Microsoft Defender for Cloud. • Multi-cloud security - Connect your accounts from Amazon Web Services (AWS) and Google Cloud Platform (GCP) to protect resources and workloads on those platforms with a range of Microsoft Defender for Cloud security features. • Hybrid security – Get a unified view of security across all of your on-premises and cloud workloads. Apply security policies and continuously assess the security of your hybrid cloud workloads to ensure compliance with security standards. Collect, search, and analyze security data from multiple sources, including firewalls and other partner solutions. • Threat protection alerts - Monitor networks, machines, and cloud services for incoming attacks and post-breach activity. Streamline investigation with interactive tools and contextual threat intelligence. • Track compliance with a range of standards - Microsoft Defender for Cloud continuously assesses your hybrid cloud environment to analyze the risk factors according to the controls and best practices in Azure Security Benchmark. When you enable the enhanced security features, you can apply a range of other industry standards, regulatory standards, and benchmarks according to your organization's needs. Add standards and track your compliance with them from the regulatory compliance dashboard. • Access and application controls - Block malware and other unwanted applications by applying machine learning powered recommendations adapted to your specific workloads to create allowlists and blocklists. Reduce the network attack surface with just-in-time, controlled access to management ports on Azure VMs. Access and application controls drastically reduce exposure to brute force and other network attacks. |
| Cloud security posture management (CSPM) | Cloud security posture management (CSPM) is a relatively new class of tools designed to improve your cloud security management. It assesses your systems and automatically alerts security staff in your IT department when a vulnerability is found. CSPM uses tools and services in your cloud environment to monitor and prioritize security enhancements and features. CSPM uses a combination of tools and services: • Zero Trust-based access control: Considers the active threat level during access control decisions. • Real-time risk scoring: To provide visibility into top risks. • Threat and vulnerability management (TVM): Establishes a holistic view of the organization's attack surface and risk and integrates it into operations and engineering decision-making. • Discover sharing risks: To understand the data exposure of enterprise intellectual property, on sanctioned and unsanctioned cloud services. • Technical policy: Apply guardrails to audit and enforce the organization's standards and policies to technical systems. • Threat modeling systems and architectures: Used alongside other specific applications. • Hardening guidance - to help you efficiently and effectively improve your security |
| Security baselines for Azure | Security baselines for Azure focus on cloud-centric control areas. These controls are consistent with well-known security benchmarks, such as those described by the Center for Internet Security (CIS). Our baselines provide guidance for the control areas listed in the Azure Security Benchmark. Each recommendation includes the following information: • Azure ID: The Azure Security Benchmark ID that corresponds to the recommendation. • Recommendation: Following directly after the Azure ID, the recommendation provides a high-level description of the control. • Guidance: The rationale for the recommendation and links to guidance on how to implement it. If the recommendation is supported by Microsoft Defender for Cloud, that information will also be listed. • Responsibility: Who is responsible for implementing the control. Possible scenarios are customer responsibility, Microsoft responsibility, or shared responsibility. • Microsoft Defender for Cloud monitoring: Whether the control is monitored by Microsoft Defender for Cloud, with link to reference. |
| Term | Description |
|---|---|
| Concepts of SIEM, SOAR, XDR | Security information and event management (SIEM): A SIEM system is a tool that an organization uses to collect data from across the whole estate, including infrastructure, software, and resources. It does analysis, looks for correlations or anomalies, and generates alerts and incidents. Security orchestration automated response (SOAR): A SOAR system takes alerts from many sources, such as a SIEM system. The SOAR system then triggers action-driven automated workflows and processes to run security tasks that mitigate the issue. Extended detection and response (XDR): An XDR system is designed to deliver intelligent, automated, and integrated security across an organization’s domain. It helps prevent, detect, and respond to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms. |
| Role and value of Azure Sentinel to provide integrated threat protection | Microsoft Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response. SOAR vs XDR: Security Orchestration & Automated Response (SOAR) platforms are used by mature security operations teams to construct and run multi-stage playbooks that automate actions across an API-connected ecosystem of security solutions. In contrast, XDR will enable ecosystem integrations via Marketplace and provide mechanisms to automate simple actions against 3rd-party security controls. SOAR is complex, costly, and requires a highly mature SOC to implement and maintain partner integrations and playbooks. XDR is meant to be ‘SOAR-lite’: a simple, intuitive, zero-code solution that provides actionability from the XDR platform to connected security tools. |
| Term | Description |
|---|---|
| Microsoft 365 Defender services | Microsoft 365 Defender is an enterprise defense suite that serves as integrated cross-domain threat detection and response solution that that protects against sophisticated cyberattacks. With Microsoft 365 Defender, you can natively coordinate the detection, prevention, investigation, and response to threats across identity, endpoints, apps and e-mail/collaboration suites. This suite is broken down into the following four offerings: 1 - Microsoft Defender for Identity 2 - Microsoft Defender for Office 365 3 - Microsoft Defender for Endpoint 4 - Microsoft Cloud App Security |
| Microsoft Defender for Identity | Microsoft Defender for Identity, formerly Azure Advanced Threat Protection (Azure ATP), is a cloud-based security solution. It uses your on-premises Active Directory data (called signals) to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Microsoft Defender for Identity covers these key areas: • Monitor and profile user behavior and activities. • Protect user identities and reduce the attack surface. • Identify suspicious activities and advanced attacks across the cyberattack kill-chain. |
| Microsoft Defender for Office 365 | Microsoft Defender for Office 365, formerly Office 365 Advanced Threat Protection, safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools, including Microsoft Teams, SharePoint Online, OneDrive for Business, and other Office clients. Microsoft Defender for Office 365 covers these key areas: Threat protection policies: Define threat protection policies to set the appropriate level of protection for your organization. • Reports: View real-time reports to monitor Microsoft Defender for Office 365 performance in your organization. • Threat investigation and response capabilities: Use leading-edge tools to investigate, understand, simulate, and prevent threats. • Automated investigation and response capabilities: Save time and effort investigating and mitigating threats. |
| Microsoft Defender for Endpoint | Microsoft Defender for Endpoint, formerly Microsoft Defender Advanced Threat Protection, is a platform designed to help enterprise networks protect endpoints. It does so by preventing, detecting, investigating, and responding to advanced threats. Microsoft Defender for Endpoint embeds technology built into Windows 10 and MSFT cloud services. |
| Microsoft Cloud App Security | Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB). It's a comprehensive cross-SaaS solution that operates as an intermediary between a cloud user and the cloud provider. Microsoft Defender for Cloud Apps provides rich visibility to your cloud services, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your Microsoft and third-party cloud services. Use this service to gain visibility into Shadow IT by discovering the cloud apps being used. You can control and protect data in the apps after you sanction them to the service. What is a Cloud Access Security Broker? A CASB acts as a gatekeeper to broker real-time access between your enterprise users and the cloud resources they use, wherever they're located, and whatever device they're using. CASBs address security gaps in an organization’s use of cloud services. Protection is provided by many capabilities across these areas: visibility to detect all cloud services, data security, threat protection, and compliance. These capability areas represent the basis of the Cloud App Security framework described below. |
| Term | Description |
|---|---|
| Microsoft 365 Defender portal | A centralized dashboard to access all Microsoft 365 services listed above. This provides users with the ability to monitor and respond to threat activity and strengthen security posture across your identities, email, data, endpoints, and apps with Microsoft 365 Defender |
| How to use Microsoft Secure Score | Microsoft Secure Score is a measurement of an organization's security posture, with a higher number indicating more improvement actions need to be taken. You're given points for the following actions: • Configuring recommended security features • Doing security-related tasks • Addressing the improvement action with a third-party application or software, or an alternate mitigation |
| Security reports and compliance dashboards | The Security & Compliance Center enables your organization to manage data protection and compliance. Assuming you have the necessary permissions (global administrator, a security administrator, or a security reader), the Security Dashboard enables you to review your Threat Protection Status, as well as view and act on security alerts. |
| Describe incidents and incident management capabilities | What is a security incident? Microsoft defines a security incident in its online services as a confirmed breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to customer data or personal data while being processed by Microsoft. Incidents are a collection of correlated alerts created when a suspicious event is found. Alerts are generated from a different device, user, and mailbox entities, and can come from many different domains. These alerts are automatically aggregated by Microsoft 365 Defender. It's the grouping of these related alerts that form an incident. The incident provides a comprehensive view and context of an attack. Security personnel can use an incident to determine where an attack started, what methods were used, and to what extent the attack has progressed within the network. They can also determine the scope of the attack, and how many users, devices, and mailboxes were affected. The severity of the attack can also be determined. Incident management: Managing incidents is critical in ensuring that threats are contained and addressed. In Microsoft 365 Defender, you can manage incidents on devices, users accounts, and mailboxes. You can manage incidents by selecting one from the Incidents queue. Incidents are automatically assigned a name based on an alert. You can edit the name of an incident, resolve it, then set its classification and determination. You can also assign the incident to yourself and add incident tags and comments. When you investigate cases where you want to move alerts from one incident to another, you can also do so from the Alerts tab. You'll create a larger or smaller incident that includes all relevant alerts. |
| Term | Description |
|---|---|
| What Intune is | Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). You control how your organization’s devices, including mobile phones, tablets, and laptops, are used. You can also configure specific policies to control applications. • Mobile device management (MDM): Allows for full mobile device management • Mobile application management (MAM): Allows for application and app data management on BYOD mobile devices Microsoft Intune is an MDM and MAM provider for your devices |
| Endpoint security with Intune | As a Security Admin, use the Endpoint security node in Intune to configure device security and to manage security tasks for devices when those devices are at risk. The Endpoint security policies are designed to help you focus on the security of your devices and mitigate risk. The available tasks can help you identify at-risk devices, to remediate those devices, and restore them to a compliant or more secure state. |
| Describe endpoint security with the Microsoft Endpoint Manager admin center | Endpoint Manager admin center: The admin center is a one-stop web site to create policies and manage your devices. It plugs-in other key device management services, including groups, security, conditional access, and reporting. This admin center also shows devices managed by Configuration Manager and Intune (in preview). |
| Term | Description |
|---|---|
| Offerings of the Service Trust portal | The Service Trust Portal contains details about Microsoft's implementation of controls and processes that protect our cloud services and the customer data therein. Offerings include: • Service Trust Portal – home page. • Compliance Manager – measures your progress in completing actions that help reduce risks around data protection and regulatory standards. To find out more, see the Microsoft Compliance Manager documentation in the Learn More section below. • Trust Documents – links to a security implementation and design information. • Industries & Regions – contains compliance information about Microsoft Cloud services organized by industry and region. The Industry Solutions link currently displays the home page for Financial Services. The Regional Solutions links currently have information for: Australia, Canada, Czech Republic, Denmark, Germany, Poland, Romania, Spain, and the United Kingdom. • Trust Center – links to the Microsoft Trust Center, which provides more information about security, compliance, and privacy in the Microsoft Cloud. • Resources – links to resources including information about the features and tools available for data governance and protection in Office 365, the Microsoft Global Datacenters, and Frequently Asked Questions. • My Library – allows you to add documents and resources that are relevant to your organization. Everything is in one place. You can also opt to have email notifications sent when a document is updated, and set the frequency you receive notifications.. |
| Microsoft’s privacy principles | Microsoft’s products and services run on trust. Microsoft focuses on six key privacy principles when making decisions about data. Privacy is about making meaningful choices for how and why data is collected and used. It's about ensuring that you have the information you need to make the choices that are right for you, across all Microsoft products and services. The six privacy principles are: • Control: Putting you, the customer, in control of your privacy with easy-to-use tools and clear choices. • Transparency: Being transparent about data collection and use so that everyone can make informed decisions. • Security: Protecting the data that's entrusted to Microsoft by using strong security and encryption. • Strong legal protections: Respecting local privacy laws and fighting for legal protection of privacy as a fundamental human right. • No content-based targeting: Not using email, chat, files, or other personal content to target advertising. • Benefits to you: When Microsoft does collect data, it's used to benefit you, the customer, and to make your experiences better. |
| Compliance center | The Microsoft 365 compliance center brings together all of the tools and data that are needed to help understand and manage an organization’s compliance needs. Only users with the following roles are able to access the Compliance center: Global administrator, Compliance administrator, Compliance data administrator. Microsoft 365 compliance center |
| Compliance manager | Microsoft Compliance Manager is a feature in the Microsoft 365 compliance center that helps admins to manage an organization’s global compliance requirements with greater ease and convenience. Compliance Manager can help organizations throughout their compliance journey, from taking inventory of data protection risks, to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors. Compliance Manager overview |
| Use and benefits of compliance score | Compliance score measures progress in completing recommended improvement actions within controls. The score can help an organization to understand its current compliance posture. It also helps organizations to prioritize actions based on their potential to reduce risk. How to understand the compliance score: The overall compliance score is calculated using scores that are assigned to actions. Actions come in two types: • Your improved actions: actions that the organization is expected to manage. • Microsoft actions: actions that Microsoft manages for the organization. These action types have points assigned to them that count towards the compliance score. Actions can also be considered technical or nontechnical, which also affects how they impact the overall compliance score. Actions are also assigned a score value based on whether they’re categorized as mandatory, discretionary, preventative, detective, or corrective: • Mandatory – these actions shouldn’t be bypassed. For example, creating a policy to set requirements for password length or expiration. • Discretionary – these actions depend on the users understanding and adhering to a policy. For example, a policy where users are required to ensure their devices are locked before they leave them. The following are subcategories of actions that can be classified as mandatory or discretionary: • Preventative actions are designed to handle specific risks, like using encryption to protect data at rest if there were breaches or attacks. • Detective actions actively monitor systems to identify irregularities that could represent risks, or that can be used to detect breaches or intrusions. Examples of these types of actions are system access audits, or regulatory compliance audits. • Corrective actions help admins to minimize the adverse effects of security incidents, by undertaking corrective measures to reduce their immediate effect or possibly even reverse damage. Compliance score calculation |
| Term | Description |
|---|---|
| Data classification capabilities | Sensitive information types have set patterns that can be used to identify them (e.g. server name + airport code). Microsoft 365 includes many built-in sensitive information types based on patterns that are defined by a regular expression (regex) or a function. (e.g. credit card numbers, SSN, bank account numbers, etc.) Trainable classifiers use artificial intelligence and machine learning to intelligently classify your data. They're most useful classifying data unique to an organization like specific kinds of contracts, invoices, or customer records. This method of classification is more about training a classifier to identify an item based on what the item is, not by elements that are in the item (pattern matching). Two types of classifier are available: • Pre-trained classifiers - Microsoft has created and pretrained many classifiers that you can start using without training them. These classifiers will appear with the status of Ready to use. Microsoft 365 comes with five pretrained classifiers that detect and classify things like resumes, source code, harassment, profanity, and threat (relates to committing violence or doing physical harm). • Custom trainable classifiers - Microsoft supports the ability to create and train custom classifiers. They're most useful when classifying data unique to an organization, like specific kinds of contracts, invoices, or customer records. Learn about data classification |
| Value of content and activity explorer | The content explorer is available as a tab in the data classification pane of compliance center. It enables administrators to gain visibility into the content that has been summarized in the overview pane. Access to content explorer is highly restricted because it makes it possible to read the contents of scanned files. There are two roles that grant access to content explorer: "Content explorer list viewer" and "Content explorer content viewer". Activity explorer provides visibility into what content has been discovered and labeled, and where that content is. It makes it possible to monitor what's being done with labeled content across the organization. Admins gain visibility into document-level activities like label changes and label downgrades (such as when someone changes a label from confidential to public). You should use activity explorer to see a historical view of what is being done with content labels. It provides detailed information about sensitivity label activities, retention label activities, Azure Information Protection (AIP) protection activity, and data loss prevention (DLP) policy matches events, including endpoint data loss prevention. Getting Started With Activity Explorer |
| Sensitivity labels | Sensitivity labels, available as part of information protection in the Microsoft 365 compliance center, enable the labeling and protection of content, without affecting productivity and collaboration. With sensitivity labels, organizations can decide on labels to apply to content such as emails and documents, much like different stamps are applied to physical documents and can be used to automate tasks such as encrypting e-mail based on the label. Labels are: • Customizable: Admins can create different categories specific to the organization, such as Personal, Public, Confidential, and Highly Confidential. • Clear text: Because each label is stored in clear text in the content's metadata, third-party apps and services can read it and then apply their own protective actions, if necessary. • Persistent. After you apply a sensitivity label to content, the label is stored in the metadata of that email or document. The label then moves with the content, including the protection settings, and this data becomes the basis for applying and enforcing policies. After sensitivity labels are created, they need to be published to make them available to people and services in the organization. Sensitivity labels are published to users or groups through label policies. Sensitivity labels will then appear in Office apps for those users and groups. |
| Retention Polices and Retention Labels | Retention labels and policies help organizations to manage and govern information by ensuring content is kept only for a required time, and then permanently deleted. Applying retention labels and assigning retention policies helps organizations: • Comply proactively with industry regulations and internal policies that require content to be kept for a minimum time. • Reduce risk when there's litigation or a security breach by permanently deleting old content that the organization is no longer required to keep. • Ensure users work only with content that's current and relevant to them. Retention policies Retention policies are used to assign the same retention settings to content at a site level or mailbox level. • A single policy can be applied to multiple locations, or to specific locations or users. • Items inherit the retention settings from their container specified in the retention policy. If a policy is configured to keep content, and an item is then moved outside that container, a copy of the item is kept in the workload's secured location. However, the retention settings don't travel with the content in its new location. Retention labels • Retention labels are used to assign retention settings at an item level, such as a folder, document, or email. • An email or document can have only a single retention label assigned to it at a time. • Retention settings from retention labels travel with the content if it’s moved to a different location within your Microsoft 365 tenant. • Admins can enable users in the organization to apply a retention label manually. • A retention label can be applied automatically if it matches defined conditions. • A default label can be applied for SharePoint documents. • Retention labels support disposition review to review the content before it's permanently deleted. Learn about retention policies and retention labels |
| Records Management | Organizations of all types require a management solution to manage regulatory, legal, and business-critical records across their corporate data. Records management in Microsoft 365 helps an organization look after their legal obligations. It also helps to demonstrate compliance with regulations, and increases efficiency with regular disposition of items that are no longer required to be kept, no longer of value, or no longer required for business purposes. It provides the following capabilities: Labeling content as a record. • Migrating and managing retention plans with file plan manager. • Establishing retention and deletion policies within the record label. • Triggering event-based retention. • Reviewing and validating disposition. • Proof of records deletion. • Exporting information about disposed items. • Setting specific permissions for record manager functions in the organization. When content is labeled as a record, the following happens: • Restrictions are put in place to block certain activities. • Activities are logged. • Proof of disposition is kept at the end of the retention period. Learn about records management in Microsoft 365 |
| Data Loss Prevention (DLP) | Data loss prevention (DLP) is a way to protect sensitive information and prevent its inadvertent disclosure. DLP policies protect content through the enforcement of rules that consist of: • Conditions that the content must match before the rule is enforced. • Actions that the admin wants the rule to take automatically when content that matches the conditions has been found. • Locations where the policy will be applied, such as Exchange, SharePoint, OneDrive, and more. Learn about data loss prevention |
| Term | Description |
|---|---|
| Describe insider risk management solution | Insider risk management in Microsoft 365 helps organizations address internal risks, such as IP theft, fraud, and sabotage. Learn about insider risk management and how Microsoft technologies can help you detect, investigate, and take action on risky activities in your organization. Learn about insider risk management in Microsoft 365 |
| Communication compliance | Communication compliance in Microsoft 365 is a solution that helps organizations address code-of-conduct policy violations in company communications, while also assisting organizations in regulated industries meet specific supervisory compliance requirements. Communication Compliance uses machine learning to intelligently detect violations across different communication channels such as Microsoft Teams, Exchange Online, or Yammer messages. Communication compliance in Microsoft 365 |
| Information barriers | Information barriers enable administrators to define policies to allow or prevent communications between groups of users in Microsoft Teams chats and channels. When information barrier policies are in place, people who should not communicate with other specific users won't be able to find, select, chat, or call those users. With information barriers, checks are in place to prevent unauthorized communication. Learn about information barriers in Microsoft 365 |
| Privileged access management (PAM) | Privileged access management allows granular access control over privileged admin tasks in Office 365. Privileged access management requires users to request just-in-time access to complete elevated and privileged tasks through a highly scoped and time-bound approval workflow. This configuration gives users just-enough-access to perform the task at hand without risking exposure of sensitive data or critical configuration settings. Learn about privileged access management Note: Privileged access management is defined and scoped at the task level, while Azure AD Privileged Identity Management applies protection at the role level with the ability to execute multiple tasks. Azure AD Privileged Identity Management primarily allows managing accesses for AD roles and role groups, while privileged access management in Microsoft 365 applies only at the task level. |
| Customer lockbox | Office 365 Customer Lockbox feature which will help a customer to control how a Microsoft support engineer is going to access customer data during a scenario where customers have raised a support request to investigate some service issues related to customers Office 365 tenant. Office 365 Customer Lockbox allows the customer to Approve or Reject access request made by the Microsoft Support engineers to access customer data. If customers give access by Approving the request, Microsoft Support Engineers will be able to access the data to help customers resolve issues if they deem necessary. Customer Lockbox in Office 365 |
| Term | Description |
|---|---|
| Purpose of eDiscovery | Electronic discovery, or eDiscovery, is the process of identifying and delivering electronic information that can be used as evidence in legal cases. eDiscovery solutions in Microsoft 365 |
| Capabilities of the content search tool | You can use eDiscovery tools in Microsoft 365 to search for content in Exchange Online, OneDrive for Business, SharePoint Online, Microsoft Teams, Microsoft 365 Groups, and Yammer teams. You can search mailboxes and sites in the same eDiscovery search, and then export the search results. You can use Core eDiscovery cases to identify, hold, and export content found in mailboxes and sites. If your organization has an Office 365 E5 or Microsoft 365 E5 subscription (or related E5 add-on subscriptions), you can further manage custodians and analyze content by using the feature-rich Advanced eDiscovery solution in Microsoft 365. Search for content using the Content search tool |
| Core eDiscovery workflow | Core eDiscovery in Microsoft 365 provides a basic tool that organizations can use to search and export content in Microsoft 365. Steps to perform this workflow are as follows: 1 - Create an eDiscovery hold (hold infinitly or for a date range) 2 - Search for content in the case 3 - Export content from a case (Results.csv will export) Get started with Core eDiscovery in Microsoft 365 |
| Advanced eDiscovery workflow | The Advanced eDiscovery solution in Microsoft 365 builds on the existing core eDiscovery. This new solution provides an end-to-end workflow to preserve, collect, review, analyze, and export content that's relevant to your organization's internal and external investigations. It also lets legal teams manage the entire legal hold notification workflow to communicate with custodians involved in a case. Steps to perform this workflow are as follows: 1 - Add custodians to a case. 2 - Search custodial data sources for data relevant to the case 3 - Add data to a review set 4 - Review and analyze data in a review set 5 - Export and download case data. Overview of Microsoft 365 Advanced eDiscovery |
| Core audit capabilities of M365 | The audit functionality in the Microsoft 365 compliance center allows organizations to view user and administrator activity through a unified audit log. The results of the audit log search, which can be filtered and exported to a CSV file and contain date, IP address, user, activity, item, and additional details on the activity. |
| Purpose and value of Advanced Auditing | Advanced Audit helps organizations to conduct forensic and compliance investigations by increasing audit log retention that's required to conduct an investigation. Audit log retention provides access to crucial events that help determine the scope of compromise, and faster access to Office 365 Management Activity API. These capabilities differentiate Advanced Audit from the core audit functionality described in the previous unit and require a Microsoft 365 E5 license, or a Microsoft 365 E3 or Office 365 E3 license with a Microsoft 365 E5 Compliance, or Microsoft 365 E5 eDiscovery and Audit add-on license. Advanced Audit in Microsoft 365 |
| Term | Description |
|---|---|
| Resource locks | As an administrator, you can lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. The lock overrides any permissions the user might have. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively. • CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource. • ReadOnly means authorized users can read a resource, but they can't delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role. |
| Azure Blueprints | Enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization's standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to rapidly build and stand up new environments with trust they're building within organizational compliance with a set of built-in components, such as networking, to speed up development and delivery. Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such as: • Role Assignments • Policy Assignments • Azure Resource Manager templates (ARM templates) • Resource Groups Azure Blueprints documentation Understand the lifecycle of an Azure Blueprint |
| Azure Policy and describe its use cases | Azure Policy is a service in Azure that enables you to create, assign, and manage policies that control or audit your resources. These policies enforce different rules across all of your resource configurations so that those configurations stay compliant with corporate standards. Common use cases for Azure Policy include implementing governance for resource consistency, regulatory compliance, security, cost, and management. Policy definitions for these common use cases are already available in your Azure environment as built-ins to help you get started. Azure Policy enables you to define both individual policies and groups of related policies, known as initiatives. Azure Policy evaluates your resources and highlights resources that aren't compliant with the policies you've created. Azure Policy can also prevent noncompliant resources from being created. |
Microsoft SC-900 page that includes free training, skills measured and exam details
Microsoft Enterprise Skills Initiative Study Guide for SC-900
Microsoft Learning - Microsoft Certified Trainer (MCT) lab for SC-900
Microsoft Learning - Microsoft Certified Trainer (MCT) labs for all exams