-
Notifications
You must be signed in to change notification settings - Fork 499
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Invalid scopes: openid openid profile email groups #4493
Comments
|
The passport-openidconnect module adds 'openid' to the beginning of the scope (as it is required), I removed it from the request as well as the unused 'groups' scope. |
|
Just accepted #4494, working on a release now. |
|
MeshCentral v1.0.81 is out with this fix. Thanks you @mstrhakr |
As always, I'm happy to help. |
|
Holy cow that was fast! You guys are awesome! 👍 |
Describe your issue
I'm having a strange issue with the generic OIDC authStrategy, where it seems to be duplicating the 'oidc' scope on callback to the '/oidc-callback' path. I'm using Keycloak as the OIDC provider, with AD/LDAP as the backend for it. All other aspects of MC2 seem to be working properly (including its integrated LDAP/AD auth), so it may just be something in my config. I guess I should ping @mstrhakr on this, since this is kind of his baby. :-)
Thanks in advance. Let me know if you need additional info, and I'll get it in here ASAP.
Screenshots
OIDC enabled:
Error page after clicking OIDC button:
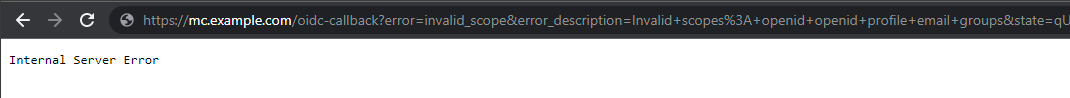
Text format of error page URL:
Server Software (please complete the following information):
Client Device (please complete the following information):
Your config.json file
Error message from MC2:
The text was updated successfully, but these errors were encountered: