Datree automatically validates Kubernetes objects for rule violations, ensuring no misconfigurations reach production. It’s an E2E policy enforcement solution that can be used on the command line, admission webhook, or even as a kubectl plugin.
It’s far more effective than manual processes, such as sending an email to a slew of developers, begging them to set various limits, which likely falls on deaf ears because developers are already overwhelmed.
Linux & MacOS: curl https://get.datree.io | /bin/bash
Windows: iwr -useb https://get.datree.io/windows_install.ps1 | iex
Other installation options (Homebrew, Docker, etc.) can be found here
datree test [k8s-manifest-file]
...and voilà, you just ran your first policy check! 🥳
Datree scans Kubernetes configurations and validates them against a centrally managed policy for rule violations and misconfigurations.
The CLI interface can be run locally, as a pre-commit hook, or in your CI, to shift left misconfiguration detection. With the admission webhook interface, you can enforce the same policy on the cluster.
- YAML validation
- Schema validation (Including CRD support)
- Policy check
Datree comes with dozens of battle-tested rules for you to select to create your policy. The policy rules cover a variety of Kubernetes resources such as workload security, networking availability, Argo best practices, NSA hardening guide, and many more.
In addition to our built-in rules, you can write any custom rule you wish and then run it against your Kubernetes configurations to check for rule violations. The custom rule engine is based on JSON Schema.
Datree's Helm plugin can be accessed through the helm CLI to provide a seamless experience to Helm users:
helm plugin install https://github.com/datreeio/helm-datree
Datree comes with out-of-the-box support for Kustomize:
datree kustomize test [kustomization.yaml dir path/]
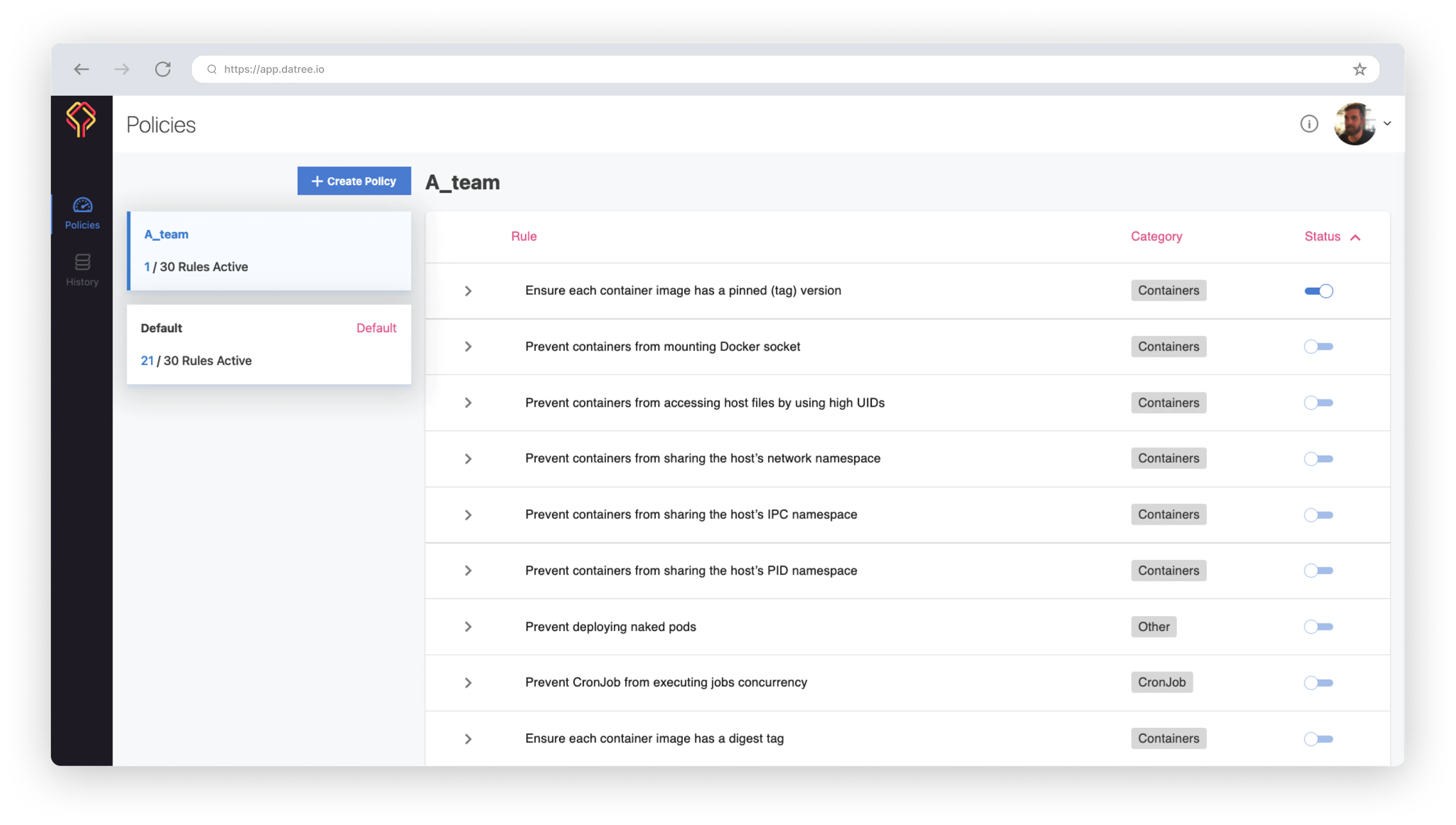
Datree can be customized via code (policy as code) or via a management dashboard. The dashboard offers the following capabilities in an intuitive visual interface:
- Customize policies
- Edit rules failure message
- Issue tokens
- View policy check history
- Configure Kubernetes schema version
From develop to runtime, you can use Datree in every step of your Kuberenetes pipeline to help you prevent misconfigurations:
- Develop (code) - run the CLI locally (or as a pre-commit hook) to get instant validation
- Distribute (CI) - integrate with your CI platform to shift-left policy checks
- Deploy (CD) - gate your cluster with the admission webhook
- Runtime (production) - query deployed resources with the kubectl plugin to your know your status
Contributions are welcome!
Thank you to all the people who already contributed to Datree ❤️