-
Notifications
You must be signed in to change notification settings - Fork 156
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
win_dsc: fails to serialize properties into CimInstance #15
Comments
|
From @rukas on Aug 10, 2018 19:35 This seems to only happen with that specific DSC module so far. I'm using a few others without issue such as:
|
|
From @gstorme on Jun 21, 2019 11:58 I've encountered this error with the Disk resource on a Windows Server 2016, with ansible 2.7. - name: Create partition
win_dsc:
resource_name: Disk
DriveLetter: "{{ drive_letter }}"
DiskId: "{{ number }}"
Size:
FSLabel: "{{ label }}"
FSFormat: "{{ fs_type }}"
AllocationUnitSize: "{{ cluster_size }}"
when: drive_letter != 'C' |
|
From @ShachafGoldstein on Jun 22, 2019 17:45 A brief online search yields a possible answer, The resources giving the |
|
Is there any update on supporting composite resources? I'm running into this issue as well. |
|
There's been no progress because there hasn't been enough information to replicate the problem, I'm not even sure what a composite resource actually is. IIRC the last time I ran OPs original example it ran just fine. Without being able to replicate the problem we can't move forward with fixing it. |
|
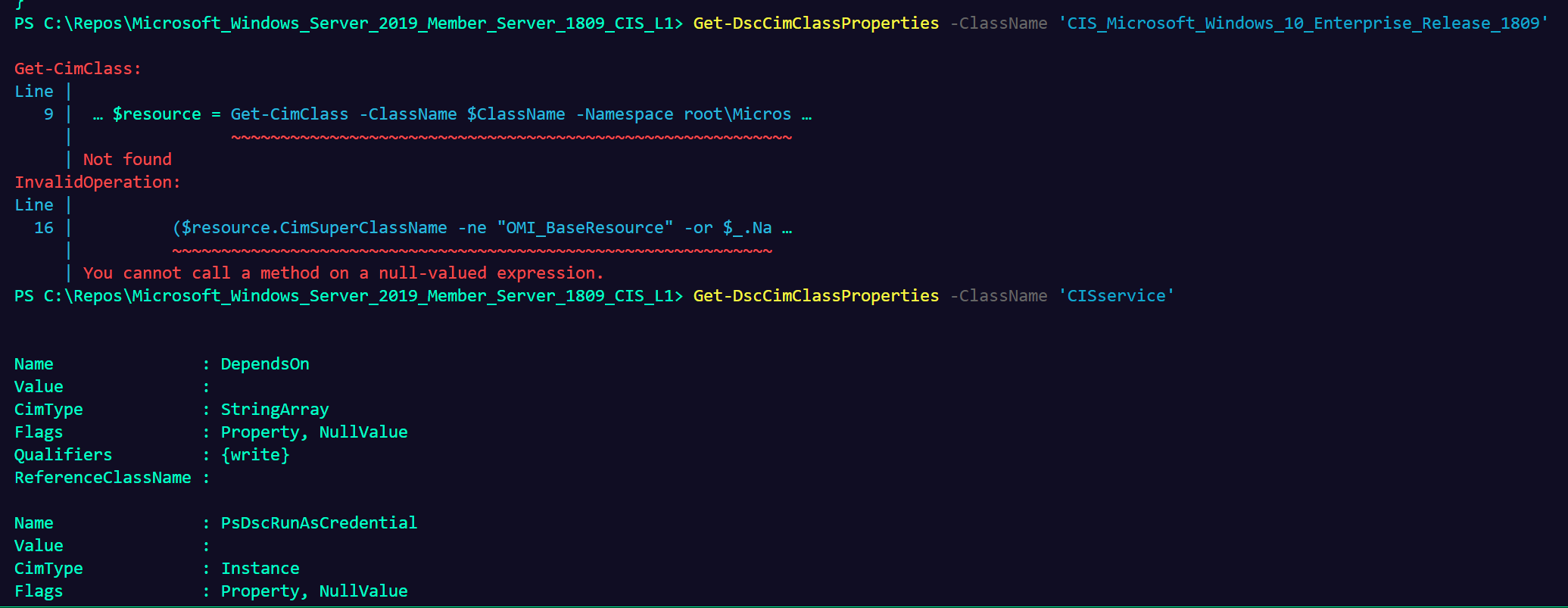
A composite resource is essentially a parameterized configuration that can be referenced as a resource else where. Resource Example and usage example The issue lies in the use of Invoke-DSCResource (note here) so I'm not sure if there's a reasonable solution on the win_dsc side honestly. Since traditionally when a mof is compiled it expands a composite resource and only makes reference to the guts. As seen in the below snippet of the MOF generated by my linked example. So trying to reference a composite resource natively like below fails to find the class. Below you can see how the CIM method of finding resources used by win_dsc locates the class based resource of 'CISService' but not the composites like Get-DSCResource does. |
|
I believe there is an achievable workaround and would be willing to help work on a PR. win_dsc would need to be composite resource aware and know to expand a composite resource and iterate invoke-dscresource on all of its contents. |
|
For sanity I checked the DSC resource from the OP and it is also a composite resource. |
|
Awesome wonderful information. I'm curious the example that you had
Wouldn't this result in a different error from this report or is it also If you are able to create a PR with the fix or at least a draft one we can definitely go from there. I'm afraid my knowledge of DSC isn't the best so this is definitely not something I've had to deal with before. Just as an FYI the reason we check CIM directly and not |
|
Since the logic for expanding a composite resource is currently closed source. The workaround I can think of is having a script block generate a mof, import the mof as hashtables, iterate through them with invoke-dscresource. So I think this is doable if we're not above having a mof exist for a second on the file system. |
|
I have a working POC below. It's certainly not pretty but it seems to work. The work around is basically generating a mof, parsing it, and looping through the expanded resources. It worked for me on a relatively complicated composite resource. |
|
@MKletz we've kicked this around at a couple meetings, but haven't seen you- stop by one of our IRC meetings if you can. |
|
@nitzmahone Will do, life has been crazy lately so I've not paid attention to my mentions I apologize. |
|
@jborean93 @MKletz Sorry to resurrect a four year old issue but was there ever any further conversations on implementing the workaround shown above? Running it on its own seems to work just fine. I'm just getting into Ansible but being able to run composite resources would be a huge benefit to what I'm trying to implement at work. The main module I would be using this with would be PowerSTIG as Microsoft has only implemented composite resources with their module. |
|
@camusicjunkie to my knowledge yes this is still an issue. This is a tricky one to fix due to the way composites are handled by the underlying DSC. They are not supported by Invoke-DSCResource so it would require a near total rewrite of the module to handle generating a mof file and executing it which could have other implications since that then involves the LCM on the node where we currently avoid that. If the node has configurations assigned via the LCM already I believe that causes issues trying to generate/execute against a new one ad-hoc. |


From @rukas on Aug 10, 2018 18:48
SUMMARY
Using win_dsc results in the following error:
Failed to serialize properties into CimInstance.The same configuration in pure DSC works without issue:
ISSUE TYPE
COMPONENT NAME
ANSIBLE VERSION
CONFIGURATION
OS / ENVIRONMENT
From Ubuntu 16.04.2
Managing Server 2016
STEPS TO REPRODUCE
hosts.yml
test_playbook.yml
EXPECTED RESULTS
The DSC configuration to be successful
ACTUAL RESULTS
The text was updated successfully, but these errors were encountered: