New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Bypass keycloak login with rest api #913
Comments
|
I don't think you'll be able to accomplish this without some modifications to Apiman. I'm happy to point you in the right direction on this sort of thing. It's going to depend on exactly how you are using Apiman, of course. I don't have enough information from "I am using Apiman inside one of my projects" - I'm not sure exactly what you mean by that. But basically authentication/authorization is handled in a few places. Essentially the Manager UI and Manager API are both protected, so you would need to update the configuration for both of those. If you're running e.g. in Wildfly that is controlled here: You could rip out Keycloak entirely and use some other authentication mechanism if you want. But whatever you do for authenticating the two components (UI and API) the UI must be configured in such a way that it can make authenticated API calls to the back-end. The UI's auth configuration is controlled here: And the UI itself handles authentication via an interceptor here: Going down this road is definitely possible, and there is already a bit of flexibility there (and a pattern to follow if you wish to implement something new). But the road is not trivial. The other thing you could try to do is use Keycloak to implement SSO across your app. You've indicated that your app has "conventional login" so I assume that option is not desirable. The bottom line is that it is possible to change Apiman to use some other form of authentication (Keycloak is not a hard requirement) but it may require some changes to Apiman depending on exactly what your requirements are. |
|
@EricWittmann Thanks for the response. User can either login with facebook/google credentials or user can login using email ID and password. When I create/register a user from user management( option from above screenshot) I am able to create user for apiman/keycloak using keycloak rest api. When I click on the second option API MANAGEMENT it should open apiman(hosted on http://IP2:8080/apimanui) but before that it opens up keycloak(hosted on http://IP3:8080) login page. After login in to this application is being redirected to apimanui As I said I want to bypass the keycloak login screen and when I login to my application and click on API MANAGEMENT it should directly open apiman for current logged in user. Is it at all possible to write custom authentication for apiman? if Yes then how can we achieve that. Please suggest a way out from this. Thanks!! |
|
Hello @iamakashk,
How do you authenticate with the keycloak rest api? We are using this npm module to login in our new developer portal (coming soon): Not sure about the fact that your applications are running on different ips but i think keycloak manages the user sessions over the user ip and so keycloak keeps the sessions over all application which have configured keycloak as authentication identity provider. |
@bekihm Thanks for the response :) About your second point: I also tried to use keycloak for angular 7 application in which I had a menu which will redirect to apiman dashboard. But again it was asking for login into keycloak. ( That means two keycloak login for a single client). Following are the settings which I used for this. ( keycloak for angular 7 application ) . Here is project outline which I am working on:
|
|
So the short answer here is that Keycloak can definitely be used to solve this problem. Keycloak is Red Hat's SSO platform - so one of its primary uses is to provide single-sign-on across multiple applications hosted on multiple IPs. If you configure both applications to use the same Keycloak realm, that should give you SSO across those apps. Each application is typically represented by a different client within the same realm. I'm not an expert in configuring Keycloak, but I'm confident in this answer. As a side note - Keycloak can also be configured to allow various social logins like Facebook and Google. So you wouldn't lose that functionality if you protected all your web apps using Keycloak. |
|
@EricWittmann Thanks Eric. |
|
@EricWittmann @bekihm Solved the issue. Thanks for the help.😊 |
|
@iamakashk Is the code for your dashboard somewhere available? Looks like a cool project :) |
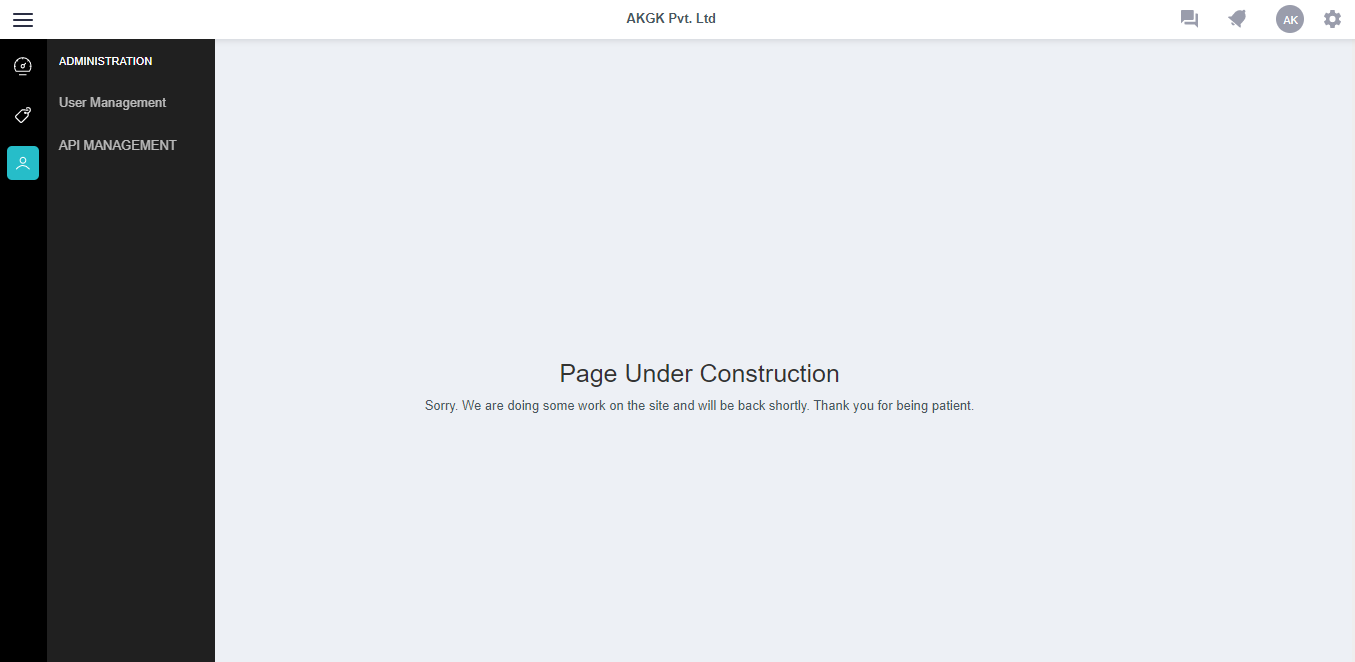


I am using APIMAN inside one of my project(app1) which has conventional login ( not keycloak). I am able to register users for apiman using keycloak rest api ( when I am registering user for my app1) . I want to bypass keycloak login screen of the apiman and jump directly into apiman dashboard. Is it possible to bypass keycloak or remove keycloak and jump directly into dashboard of the apiman.
The text was updated successfully, but these errors were encountered: