New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Can't trace sys_execve inside a c program #2523
Comments
|
Can you run with |
|
Hello, when run with '-kk', it give the following message, by the way, the test environment is in docker (on mac) |
|
Can you try to loop over and printf your argv from your code and see if it works after? |
could you show me the code, I am a beginner in kernel. |
|
It has nothing to do with the kernel, its your own C code Should be enough |
|
This is by design. Read this |
|
@ValdikSS what part of that doc are you referring to? Like I said earlier, the data you're using isn't in memory yet. These static strings are compiled in and are not actually faulted into memory until they're accessed. The access won't happen until its read, which is after your bpftrace probe ran. BPF won't pull the data in so you get an EFAULT/-14. By printing the values or just a random print of a constant string you pull the small amount of data into memory (as it goes by page, not by var) and then it works |
|
@fbs,
|
|
Looks like this is not a bpftrace bug. Can we close? |




I write a C program to make system call, I want to use bpftrace to trace it. But when I use it, it can't print out the thing I want.
Here is the C program.
Left window command:
Right window command:
bpftrace -e 'tracepoint:syscalls:sys_enter_execve { printf("%-6d %-8s", pid, comm); join(args->argv);}'but when I use strace
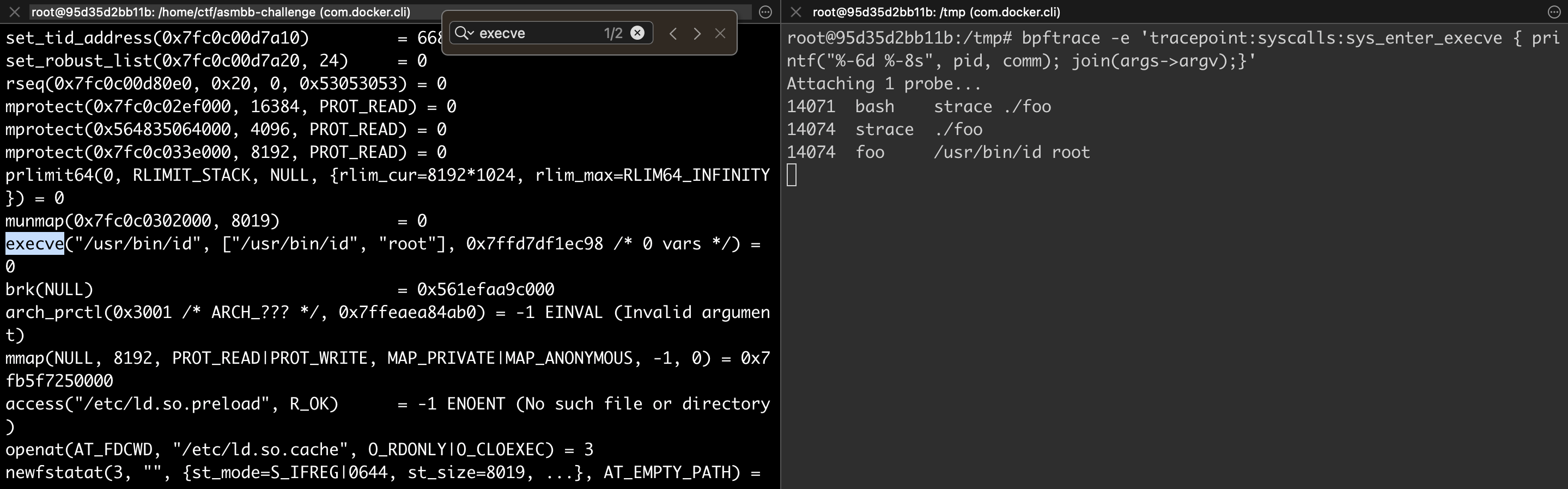
strace ./foo, everything works well. I got the line14074 foo /usr/bin/id rootwhere is the problem?
The text was updated successfully, but these errors were encountered: