New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Failing to integrate with GCP CAS #87
Comments
|
Thanks for the detailed issue @xunholy! I've drawn over your diagram a bit which hopefully should help things (apologies for my use of paint 😂). The flow for a istio workload is 1. mount in the CA certificates from the config-map that istio-csr manages, 2. the workload requests the certificate from istio-csr, 3. the workload can talk to istiod for config etc. What is happening in your case is that I think either:
Would you be able to share the relevant bits of the istio config you used for setting up your mesh? I would also always recommend setting the CA bundle to come from a static file on istio-csr ( |
|
Thanks @JoshVanL that makes a lot more sense, I did observe that the istio-proxy was trying to connect to the My error from the istio-proxy is as follows: This suggests to me the istio-proxy side car isn't loaded with the CA that is being used with the It sounds like your option 3 is the issue but how can I correct that - I've followed the instructions for configuration, is there something I've not seen that needs to be configured specifically for the httpbin/istio-proxy pod? |
|
@xunholy that does seem odd to me. Could you have a look at the root CA that is passed to the istio proxy to make sure it is the root CA for your Google CAS?
|
|
@JoshVanL I indeed think this is the error, the token isn't being mounted. I don't fully understand how the side car envoy gets this root cert in this model, I would have assumed |
|
@xunholy Indeed it is istio-csr which is populating this configmap in all namespaces. This should be on the istio proxy container rather than the main httpbin one: $ kubectl exec -n sandbox httpbin-74fb669cc6-6tm4x -c istio-proxy -- ls /var/run/secrets/istio
root-cert.pemIt should come from a mount which gets patched in on the pod by the istio mutating webhook: - configMap:
defaultMode: 420
name: istio-ca-root-cert
name: istiod-ca-cert....
volumeMounts:
- mountPath: /var/run/secrets/istio
name: istiod-ca-certYou can also check via the configmap itself too: $ kc get cm istio-ca-root-cert -o yaml
apiVersion: v1
data:
root-cert.pem: |
-----BEGIN CERTIFICATE-----
MIIDTDCCAjSgAwIBAgIQAPCeBptQRpatRpMVkHrhKzANBgkqhkiG9w0BAQsFADBA
... |
|
@xunholy if it helps, these are the manifests which I used when setting up with google-cas if you want to compare notes 🙂 apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
namespace: istio-system
spec:
profile: "demo"
hub: gcr.io/istio-release
meshConfig:
trustDomain: foo.bar
values:
global:
caAddress: cert-manager-istio-csr.cert-manager.svc:443
components:
pilot:
k8s:
env:
# Disable istiod CA Sever functionality
- name: ENABLE_CA_SERVER
value: "false"
overlays:
- apiVersion: apps/v1
kind: Deployment
name: istiod
patches:
# Mount istiod serving and webhook certificate from Secret mount
- path: spec.template.spec.containers.[name:discovery].args[-1]
value: "--tlsCertFile=/etc/cert-manager/tls/tls.crt"
- path: spec.template.spec.containers.[name:discovery].args[-1]
value: "--tlsKeyFile=/etc/cert-manager/tls/tls.key"
- path: spec.template.spec.containers.[name:discovery].args[-1]
value: "--caCertFile=/etc/cert-manager/ca/root-cert.pem"
- path: spec.template.spec.containers.[name:discovery].volumeMounts[-1]
value:
name: cert-manager
mountPath: "/etc/cert-manager/tls"
readOnly: true
- path: spec.template.spec.containers.[name:discovery].volumeMounts[-1]
value:
name: ca-root-cert
mountPath: "/etc/cert-manager/ca"
readOnly: true
- path: spec.template.spec.volumes[-1]
value:
name: cert-manager
secret:
secretName: istiod-tls
- path: spec.template.spec.volumes[-1]
value:
name: ca-root-cert
configMap:
defaultMode: 420
name: istio-ca-root-certapp:
certmanager:
preserveCertificateRequests: true
issuer:
name: istio-ca
kind: GoogleCASIssuer
group: cas-issuer.jetstack.io
tls:
trustDomain: foo.bar
rootCAFile: /etc/tls/root-cert.pem
volumes:
- name: root-ca
secret:
secretName: istio-ca-root-cert
volumeMounts:
- name: root-ca
mountPath: /etc/tls |
|
@JoshVanL Thanks for the tips. The configmap in the namespace is correct I suppose I'll take a look and compare notes against your configuration and check, I should probably mention we're using ASM vs OSS Istio, but essentially the same config is mirrored through the I can mention I didn't have I'll add these values though and check, but i don't know if this would impact the istio-proxy per se. |
|
@xunholy aha- this sounds like the culprit. I'm not very familiar with ASM myself so am not entirely sure how it is propagating the CA certificate, but would expect it to be possible to re-enable the sidecar injector to have those mounts there. |
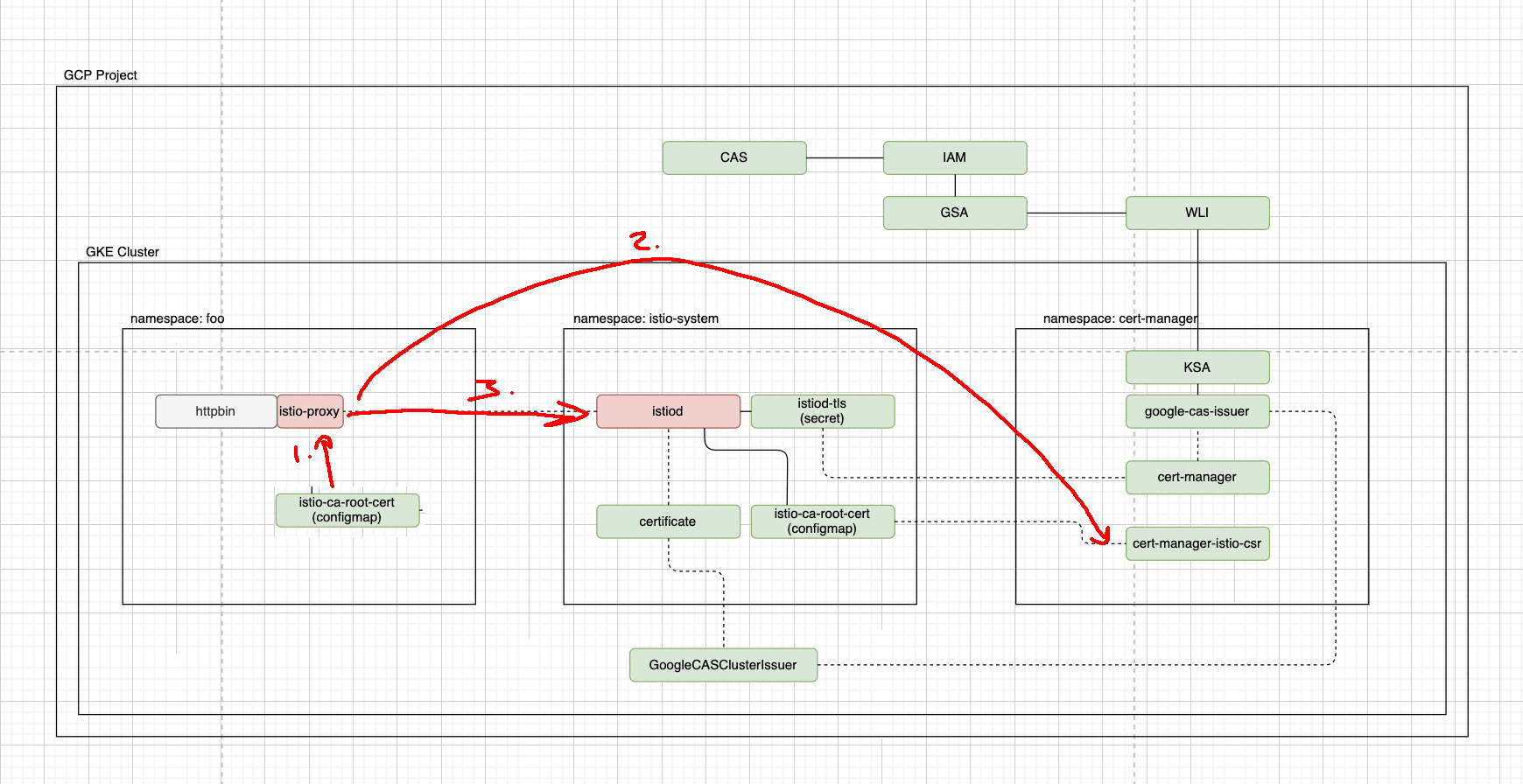
Description
We're using GCP CAS as our Cluster Issuer, which has been setup and works completely fine e2e using the traditional certificate resources to request certs for Ingress TLS certs. However, we'd like to use the same issuer with istio-csr to be able to issue these certs to our services running in the mesh so we can provide mTLS with our services in the cluster with the same CA which will also allow for traffic east <--> west to also be mTLS with our multi-cluster multi-mesh topology.
I'm deploying the default
httpbinservice through the istio examples and I can see the following logs:I can see my CA being loaded in
istiodcorrectly as I'd expect. (DUMMY CA)This lead me to believe that maybe something on the istio-csr side may be causing the issue but I've set verbosity to 5 and still don't have anything further to add context. Any further insights would be greatly appreciated.
I've also drafted up a diagram with the high level integration of the services and how it works together at present - maybe this will highlight something is either missing or incorrect.
The text was updated successfully, but these errors were encountered: