-
-
Notifications
You must be signed in to change notification settings - Fork 3.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Unsafe inline style violate Content Security Policy #7600
Comments
|
Hi @yinlam22, The styles used in that component are not unsafe, except I misunderstand what you're saying. Adding styles in the As far as I know, this will only be an issue when style elements are injected into the document. |
|
Hi @segunadebayo What I meant by unsafe inline style on that chakra UI component is it is blocked by the Content Security Policy when the "unsafe-inline" is not added to the Content-Security-Policy: style-src if the unsafe-inline source is not specified in the CSP style-src, then it will block the inline style attributes: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/style-src#unsafe_inline_styles I reproduced the scenario using codesandbox when inspecting the page, we noticed that all the |
|
Hey @segunadebayo is it possible to reopen this? I'm having the same issue |
|
Same here. I think this should be reopen. |
|
If using vite, this seems relevant (doesn't require
https://vitejs.dev/guide/features.html#content-security-policy-csp Would be great to see mention of this in Chakra docs 👍 (I'm not enough of an authority to contribute such, at this stage...) |
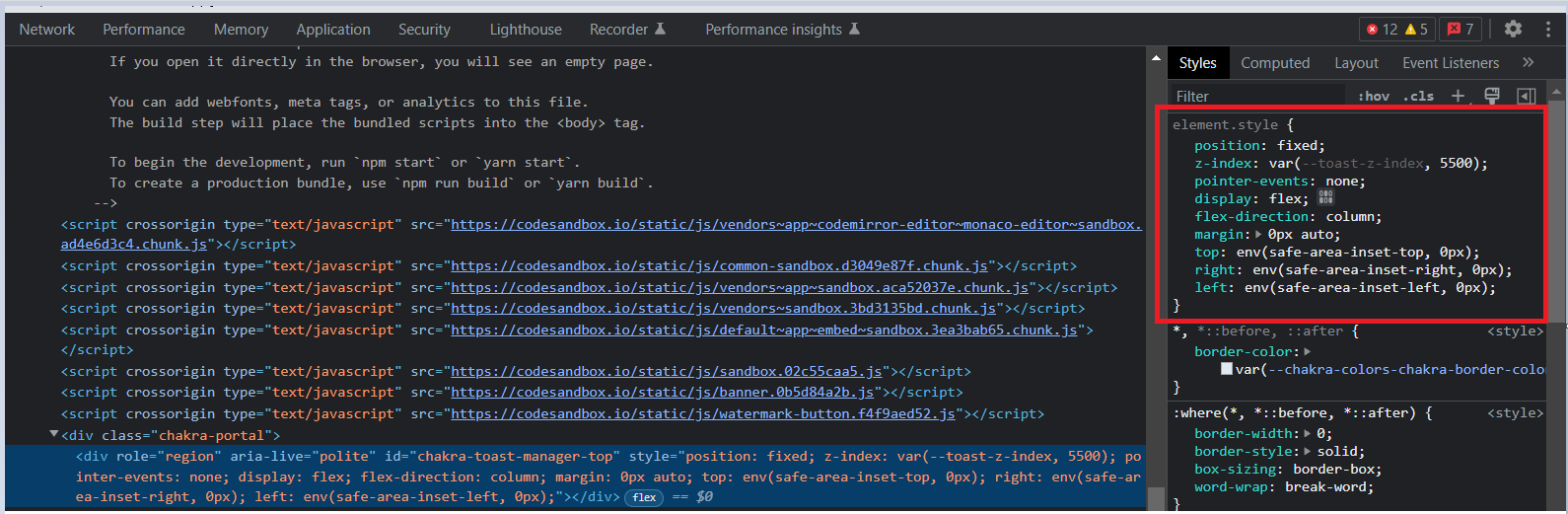
Description
Unsafe inline style is used in some of the chakra UI components that will violate the Content Security Policy
Example:
chakra-ui/packages/components/toast/src/toast.provider.tsx
Line 130 in d3fc1fd
Expected behavior
Link to Reproduction
Not really possible to show this in CodeSandbox
Steps to reproduce
Add the Content-Security-Policy header on a website with this value:
Chakra UI Version
2.4.1
Browser
No response
Operating System
Additional Information
No response
The text was updated successfully, but these errors were encountered: