Background: I'm writing this up to document my own progress through the challenge, and write out how arrived at each answer. Hopefully this will help me and potentially others in future challenges. Although I'm a paying member of TryHackMe, the holiday challenge is open to all.
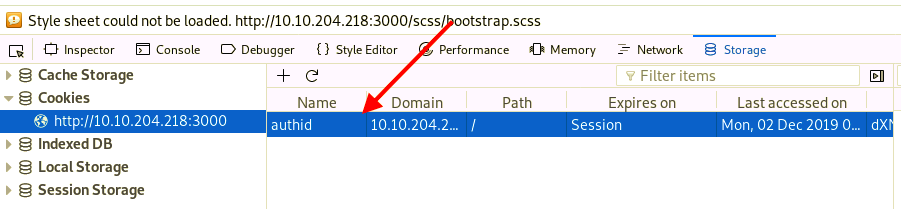
Luckily, this one can be answered easily enough by inspecting through the browser (web developer tools), as it is passed back from the web server. We can see that it's the cookie is named authid.
Allright, this one takes a little more work. Cookies are a key value pair in the form of name:value and used to establish/validate sessions. Session Management refers to how the server keeps track of the actions performed by a client.
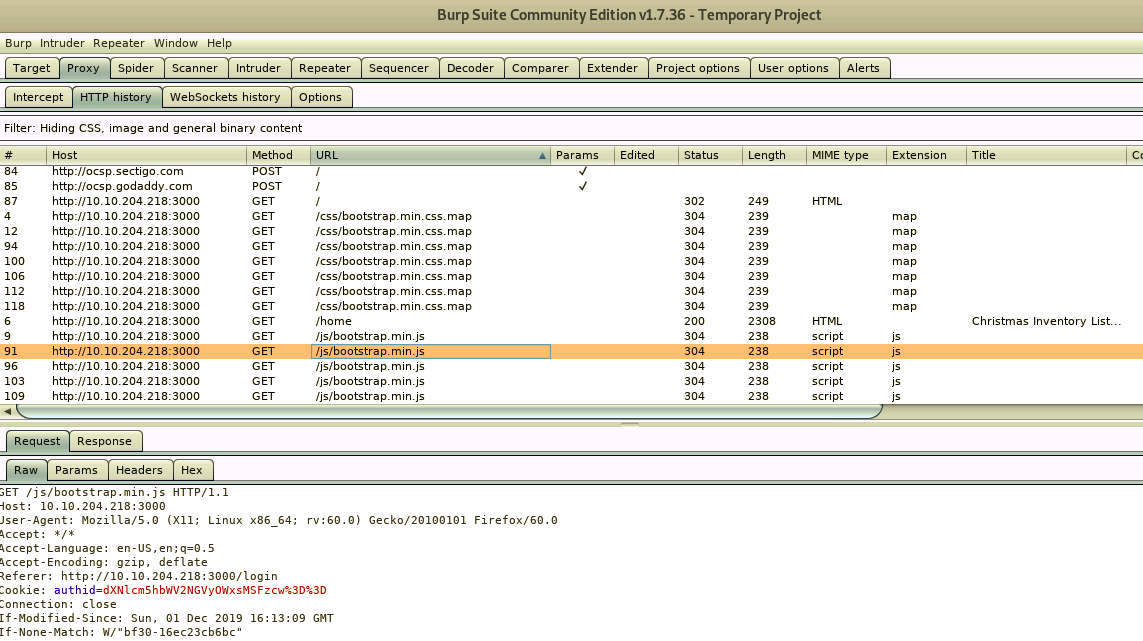
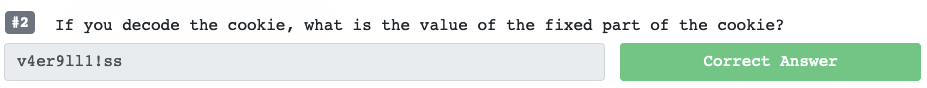
So we're able to identify the cookie name/value; but we need to separate the fixed part of the cookie, and de-code it. You can also use Burpsuite to proxy and inspect the traffic between the browser and egress to the web server.
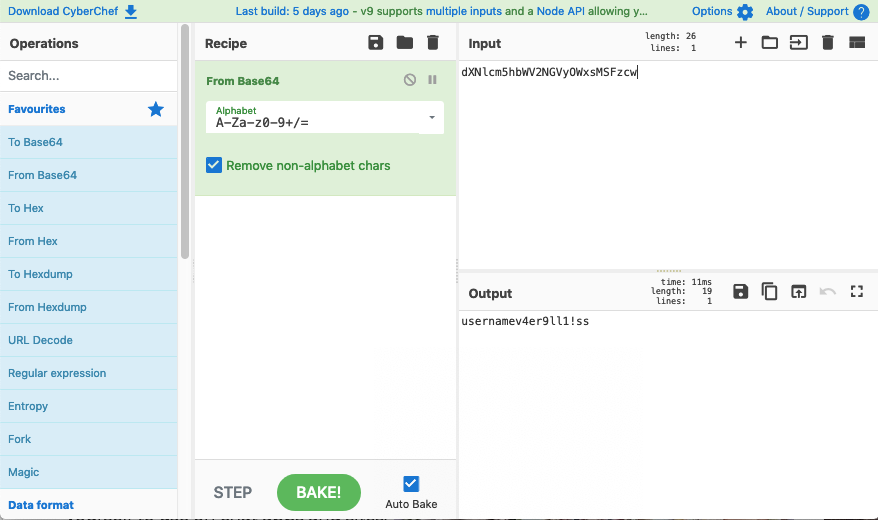
Allright, so - it's encoded at Base64, so let's we'll need to decode. Luckily there's a discord chat server for all this and someone recommended a neat coder/decoder tool on github. We then arrive with the results usernamev4er9ll1!ss.
I think I missed a step in separating the username/password in the encoding, and can probably be identified by creating a separate username or password (but not both), and identifying the differences as a seperator.
Yep, so I dug abit deeper and was able to confirm separation:
- Email: email@email.com
- Name: name
- Password: password
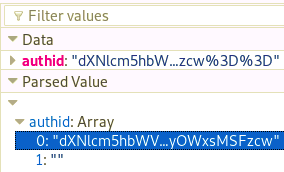
- Cookie: authid=dXNlcm5hbWV2NGVyOWxsMSFzcw%3D%3D
- First part: dXNlcm5hbWV2 - coded, username - uncoded
- Second part: NGVyOWxsMSFzcw, v4er9ll1!ss - uncoded
- Extra stuff: %3D%3D
Allright, so let's take a look at the next one:
In this exercise I suspect we'll need to re-code with admin credentials and attack the web authentication.