-
Notifications
You must be signed in to change notification settings - Fork 1
Can Drive Badger replace Pegasus?
Drive Badger is sometimes being compared to, recently popular in media, Pegasus spyware platform, developed by Israeli company NSO Group. In this article, we'll try, without going too far into technical details, to compare the functionalities of both platforms from purely functional side.
From technical point of view, Pegasus can be divided into several dozen separate functional modules (mostly related to remote infection and subsequent analysis of the victim's actions). But functionally, looking from the perspective of surveillance officer, it can be divided into 5 functional blocks:
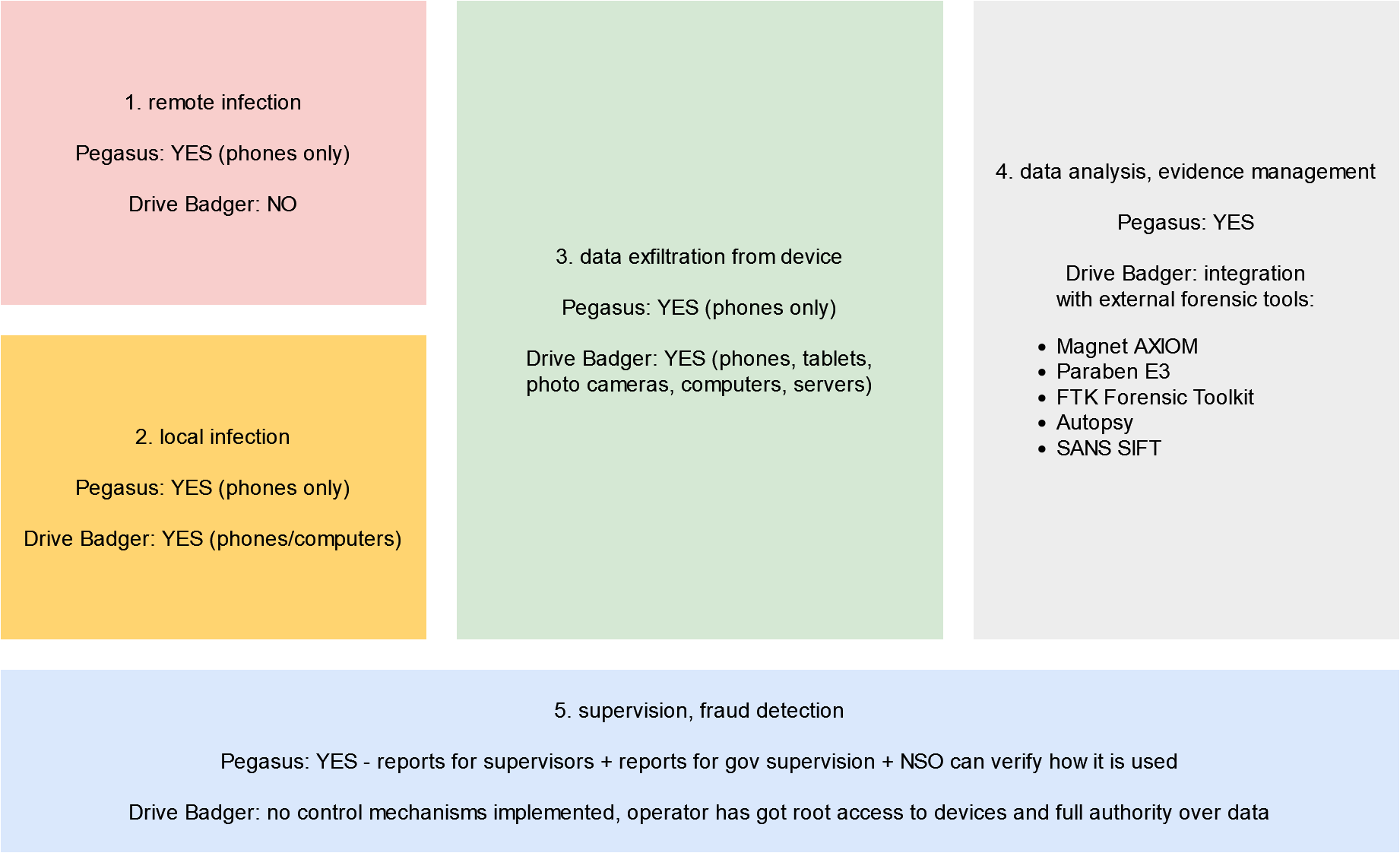
Fully remote phone infection ability is in fact the main competitive advantage of Pegasus and the reason, why it is chosen by uniformed services across the world above any other platform - including platforms with much better digital evidence analytics. Especially that Pegasus supports phones and tablets only, and it's not possible to combine evidence obtained from victim's phone and computer in any single tool.
Drive Badger can "infect" only locally - but full range of targets: computers, servers, mobile phones, tablets, pen drives, and even photo cameras. This functionality was developed for countries, where evidence or backdoor planting is legal, eg. Brasil, Vietnam, China and so on.
As Drive Badger is developed by a civillian company, without any cyberweapon trading licenses etc., as open source project, it is not directly weaponized (apart from this simple demo for Linux hosts). It fully allows injecting content into exfiltraded filesystems, but it is operator's responsibility to provide any exploits, evidence files or any other content to be injected.
While Pegasus' main competitive advantage is remote infection, Drive Badger excels in efficient data exfiltration, with support for all important disk encryption methods and automated key matching.
The whole data exfiltration process is fully automated, based on over 400 unique exclusion rules (for various operating systems, for both phones and computers), which reduce the amount of files to be copied by eliminating low-value files and directories from the list, thus save most of the time, that would be spent by "naive" script.
Pegasus comes with web panel for surveillance officers, allowing them to browse phone contents in a way similar to how most people uses Google services (especially Drive and Calendar): browse SMS contents, call lists, photos, calendar entries etc.
© Copyright 2020-2022 by Tomasz Klim Payload.pl