-
Notifications
You must be signed in to change notification settings - Fork 7k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
BluFi handle GATT packet has buffer overflow (IDFGH-3021) #5048
Comments
|
any progress? |
|
any progress? |
|
Hi @pokerfacett , |
|
Hi @WCCWCC , |
|
Hi @pokerfacett , I have submitted the MR and it will be modified as follows. |
|
@WCCWCC hi,First of all, thank you for submitting the repair. Secondly, considering that ESPIDF has thousands of users and is mounted on tens of millions of devices, the vulnerability will remotely cause code execution and denial of service attacks on the device.In order to maintain the security of the entire ecology for development, we recommend that ESPIDF notify developers through github's security announcement to fix the problem on their own version to achieve risk avoidance and reduction. |
出现这个错误,如何定位? |
|
@Leadrive please create new issues if you have a new problem |

INSTRUCTIONS
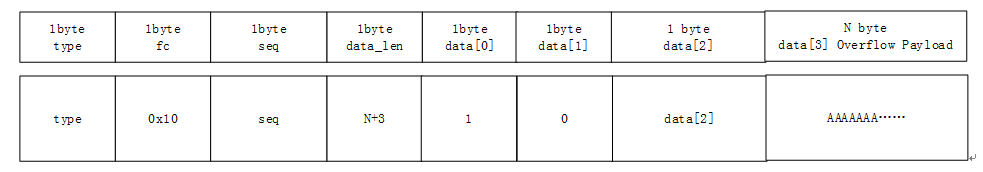
In the process of BluFi's network configurationg through ble, there is an overflow when processing the write ATT command at characteristic = 0xFF01. The specific problem is in the btc_blufi_recv_handler function of blufi_prf.c. First ,parse the incoming ATT data data [0] and data [1] as the length of memery which apply from heap. And then copy the memory data starting from data [2] to the applyed memory, causing a buffer overflow
DETAILS
Here, if the fc parameter is 0x10, the overflow part can be entered. Total_len is parsed from data. Here, control data [0] = 1, data [1] = 0, so hdr-> data [0] | (((uint16_t) hdr-> data [1]) << 8) == 1, that is, total_len = 1, that is, aggr_buf allocates 1 byte of heap memory, and then copies aggr_buf, which can eventually overflow N bytes
An attacker could construct GATT payload to cause crash or remote code execution
The GATT payload as follows:
FIX SUGGESTIONG
The text was updated successfully, but these errors were encountered: