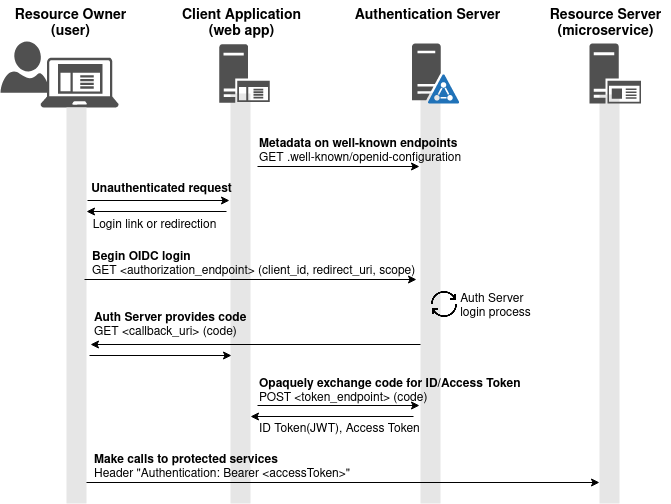
Python Flask web app that serves as the "Resource Server" entity in an OAuth2 Authorization Code flow.
It exposes a protected microservice at port 8081 that accepts an OAuth2 Access Token for authorization.
- GET /api - test of authenticated user
- GET /api/managers - authenticated user who is member of 'managers' group
Configured per my article on Keycloak setup
export AUTH_SERVER=keycloak.kubeadm.local
export AUTH_PROVIDER=keycloak
export REALM=<realmName>
# add custom CA from Keycloak, otherwise CERTIFICATE_VERIFY_FAILED errors
export CA_PEM=$(cat kubeadmCA.pem | sed 's/\n/ /')
Configured per my article on ADFS setup.
export AUTH_SERVER=win2k19-adfs1.fabian.lee
export AUTH_PROVIDER=adfs
# add custom CA from ADFS, otherwise CERTIFICATE_VERIFY_FAILED errors
export CA_PEM=$(cat adfsCA.pem | sed 's/\n/ /')
Configured per my article on Google OAuth2 setup.
export AUTH_SERVER=accounts.google.com
export AUTH_PROVIDER=google
# no custom cert needed, it has a public CA
Configured per my article on okta OAuth2 setup.
export AUTH_SERVER=dev-xxxx.okta.com
export AUTH_PROVIDER=okta
# no custom cert needed, it has a public CA
Configured per my article on Github OAuth2 setup. Github as a non-OIDC Auth provider is supported only on this resource server side.
export AUTH_SERVER=github.com
export AUTH_PROVIDER=github
# no custom cert needed, it has a public CA
Configured per my article on Spotify OAuth2 setup. Spotify as a non-OIDC Auth provider is supported only on this resource server side.
export AUTH_SERVER=accounts.spotify.com
export AUTH_PROVIDER=spotify
# no custom cert needed, it has a public CA
# need 3.x
python --version
# make sure Python3 and other essential OS packages are installed
sudo apt-get update
sudo apt-get install software-properties-common python3 python3-dev python3-pip python3-venv make curl git -y
# get my enhanced fork of flask-oidc
git clone https://github.com/fabianlee/flask-oidc.git
# setup virtual env for pip modules
python -m venv .
source bin/activate
pip install -r requirements.txt
# add custom CA certificate from 'CA_PEM' to trust store file
python src/add_ca.py3
# start Resource Server on port 8081, microservice at /api protected by OAuth2 Access Token
python src/app.py
docker --version
# clear out any older runs
docker rm docker-flask-oidc-resource-server
# run docker image locally, listening on localhost:8081
docker run \
--network host \
-p 8081:8081 \
--name docker-flask-oidc-resource-server \
-e AUTH_SERVER=$AUTH_SERVER \
-e AUTH_PROVIDER=$AUTH_PROVIDER \
-e CA_PEM="$CA_PEM" \
fabianlee/docker-flask-oidc-resource-server:1.0.0
Assumes you have already set environment variables, and run add_ca.py3 which adds custom CA to trust store.
export JWT=<the access token>
# runs tests against /api and /api/managers using bearer token
./test-jwt-auth.sh
Image is based on python:3.9-slim-buster and is ~152Mb
Had to lock pip module itsdangerous=2.0.1 puiterwijk/flask-oidc#147 ImportError: cannot import name 'JSONWebSignatureSerializer' from 'itsdangerous'
Manual addition to local CA trust store cat myCA.pem >> lib/python3.8/site-packages/certifi/cacert.pem