-
Notifications
You must be signed in to change notification settings - Fork 8.9k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
aws_iot_topic_rule Creates Rule in IoT but does not actually trigger Lambda #24196
Comments
|
Hey @emazzotta 👋 Thank you for taking the time to raise this! I started to look into it, which led me to this StackOverflow post that seems eerily similar to your situation. The answers within then led me to this AWS document which seems to indicate that this may be a permissions issue where you need to add an additional resource (or perhaps resources depending on your configuration) to allow IoT to invoke the Lambda function. Can you take a look over these documents and see if that resolves the issue you're seeing? |
|
Hey @justinretzolk! Thanks for the hint. I managed to fix it and it was indeed an issue with permissions. data "aws_iam_policy_document" "iam_invoke_lambda_policy_document" {
statement {
actions = ["lambda:InvokeFunction"]
resources = ["*"]
}
}However as it turns out, by checking the difference between a Lambda created by Terraform and one where I manually added the trigger I spotted the following difference: This was the missing permission, enabling everything to work as expected: resource "aws_lambda_permission" "decommission_access_topic_rule_permission" {
action = "lambda:InvokeFunction"
function_name = aws_lambda_function.decommissionRoasterAccess_lambda.function_name
principal = "iot.amazonaws.com"
source_arn = aws_iot_topic_rule.decommission_access_topic_rule.arn
}Thanks again for your input! 🙂 |
|
I'm going to lock this issue because it has been closed for 30 days ⏳. This helps our maintainers find and focus on the active issues. |


Community Note
Terraform CLI and Terraform AWS Provider Version
Terraform v1.1.8
on linux_amd64
Affected Resource(s)
Terraform Configuration Files
Please include all Terraform configurations required to reproduce the bug. Bug reports without a functional reproduction may be closed without investigation.
Debug Output
The logs don't hint at any issues during runtime.
Expected Behavior
When publishing to the topic
roaster/<something>/decommissionthe LambdadecommissionRoasterAccess_lambdashould be triggered.Also, I would expect the IoT Rule triggering the Lambda to be visible in the AWS web UI both from the IoT and the Lambda perspective.
Actual Behavior
The Lambda is not triggered.
According to the AWS web UI the trigger is correctly registered from an IoT perspective:

However it is missing from the Lambda perspective:
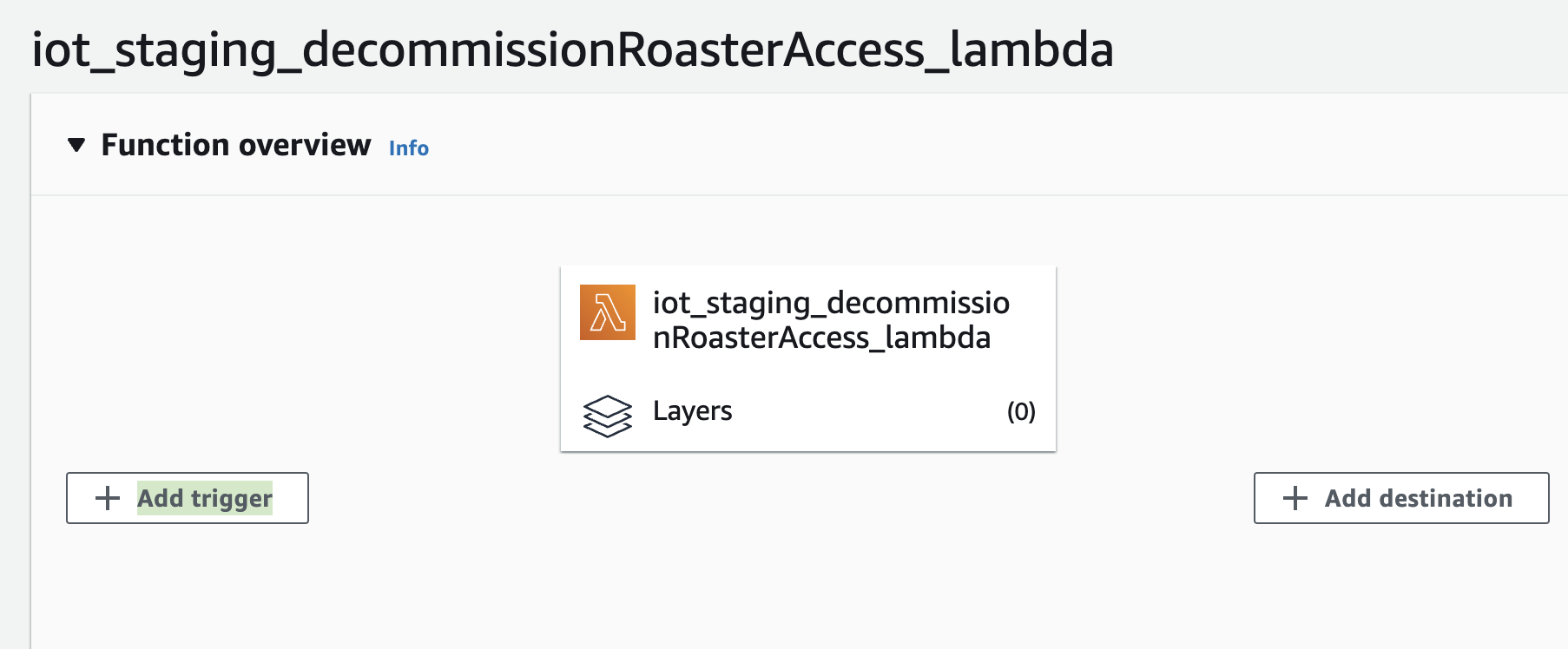
Once I manually add it as the Lambda trigger here:

The Lambda triggers successfully as expected.
Alternatively, if I manually remove the Lambda from the IoT Rule perspective (by clicking on "Clear" and reselecting the same Lambda), the Lambda is correctly registered as a trigger and again, works successfully.
The text was updated successfully, but these errors were encountered: