ooooo ooooo oooooooooooo oooooo oooo oooooooooo.
`888' `888' `888' `8 `888. .8' `888' `Y8b
888 888 888 `888. .8' 888 888
888ooooo888 888oooo8 `888. .8' 888 888
888 888 888 " `888.8' 888 888
888 888 888 o `888' 888 d88'
o888o o888o o888ooooood8 `8' o888bood8P'
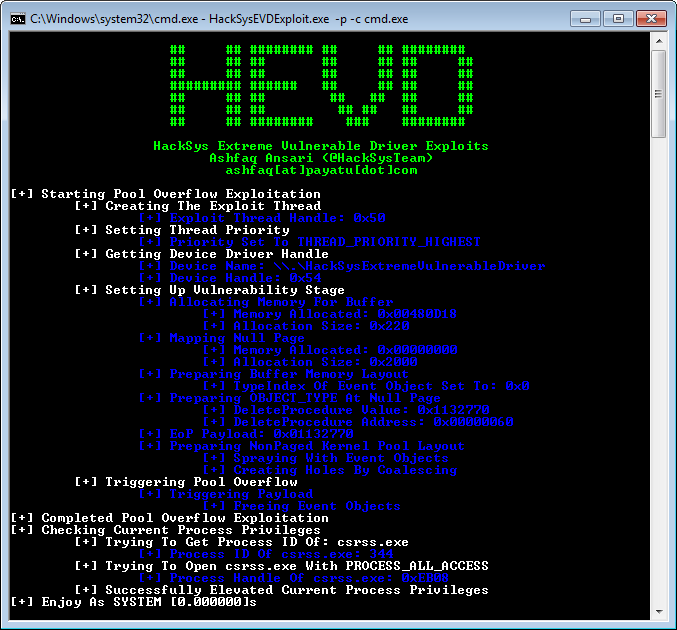
HackSys Extreme Vulnerable Driver is intentionally vulnerable Windows driver developed for security enthusiasts to learn and polish their exploitation skills at Kernel level.
HackSys Extreme Vulnerable Driver caters wide range of vulnerabilities ranging from simple Buffer Overflows to complex Use After Frees and Pool Overflows. This allows the researchers to explore the exploitation techniques for every implemented vulnerabilities.
http://www.payatu.com/hacksys-extreme-vulnerable-driver/
https://github.com/sam-b/HackSysDriverExploits
https://github.com/sizzop/HEVD-Exploits
https://github.com/badd1e/bug-free-adventure
https://github.com/FuzzySecurity/HackSysTeam-PSKernelPwn
https://github.com/theevilbit/exploits/tree/master/HEVD
https://github.com/GradiusX/HEVD-Python-Solutions
https://github.com/Cn33liz/HSEVD-StackOverflow
https://github.com/Cn33liz/HSEVD-StackOverflowX64
https://github.com/Cn33liz/HSEVD-StackCookieBypass
https://github.com/Cn33liz/HSEVD-ArbitraryOverwrite
https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteGDI
https://github.com/Cn33liz/HSEVD-StackOverflowGDI
https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteLowIL
https://github.com/mgeeky/HEVD_Kernel_Exploit
https://github.com/tekwizz123/HEVD-Exploit-Solutions
http://niiconsulting.com/checkmate/2016/01/windows-kernel-exploitation/
http://samdb.xyz/2016/01/16/intro_to_kernel_exploitation_part_0.html
http://samdb.xyz/2016/01/17/intro_to_kernel_exploitation_part_1.html
http://samdb.xyz/2016/01/18/intro_to_kernel_exploitation_part_2.html
http://samdb.xyz/2017/06/22/intro_to_kernel_exploitation_part_3.html
https://sizzop.github.io/2016/07/05/kernel-hacking-with-hevd-part-1.html
https://sizzop.github.io/2016/07/06/kernel-hacking-with-hevd-part-2.html
https://sizzop.github.io/2016/07/07/kernel-hacking-with-hevd-part-3.html
https://sizzop.github.io/2016/07/08/kernel-hacking-with-hevd-part-4.html
https://www.fuzzysecurity.com/tutorials/expDev/14.html
https://www.fuzzysecurity.com/tutorials/expDev/15.html
https://www.fuzzysecurity.com/tutorials/expDev/16.html
https://www.fuzzysecurity.com/tutorials/expDev/17.html
https://www.fuzzysecurity.com/tutorials/expDev/18.html
https://www.fuzzysecurity.com/tutorials/expDev/19.html
https://www.fuzzysecurity.com/tutorials/expDev/20.html
http://dokydoky.tistory.com/445
https://hshrzd.wordpress.com/2017/06/05/starting-with-windows-kernel-exploitation-part-2/
https://osandamalith.com/2017/04/05/windows-kernel-exploitation-stack-overflow/
https://osandamalith.com/2017/06/14/windows-kernel-exploitation-arbitrary-overwrite/
https://osandamalith.com/2017/06/22/windows-kernel-exploitation-null-pointer-dereference/
https://blahcat.github.io/2017/08/31/arbitrary-write-primitive-in-windows-kernel-hevd/
https://klue.github.io/blog/2017/09/hevd_stack_gs/
https://glennmcgui.re/introduction-to-windows-kernel-exploitation-pt-1/
https://glennmcgui.re/introduction-to-windows-kernel-driver-exploitation-pt-2/
Ashfaq Ansari
ashfaq[at]payatu[dot]com
@HackSysTeam | Blog | null
- Write NULL
- Double Fetch
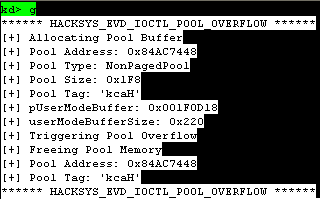
- Pool Overflow
- Use After Free
- Type Confusion
- Stack Overflow
- Integer Overflow
- Memory Disclosure
- Stack Overflow GS
- Arbitrary Overwrite
- Null Pointer Dereference
- Uninitialized Heap Variable
- Uninitialized Stack Variable
- Insecure Kernel Resource Access
- Install Windows Driver Kit
- Change
%localSymbolServerPath%inBuild_HEVD_Secure_x86.batandBuild_HEVD_Vulnerable_x86.batdriver builder - Run the appropriate driver builder
Build_HEVD_Secure_x86.batorBuild_HEVD_Vulnerable_x86.bat
If you do not want to build HackSys Extreme Vulnerable Driver from source, you could download pre-built executables for the latest release:
Use OSR Driver Loader to install HackSys Extreme Vulnerable Driver
The HackSys Extreme Vulnerable Driver and the respective exploits have been tested on Windows 7 SP1 x86
- Windows Kernel Exploitation 1
- Windows Kernel Exploitation 2
- Windows Kernel Exploitation 3
- Windows Kernel Exploitation 4
- Windows Kernel Exploitation 5
- Windows Kernel Exploitation 6
- Windows Kernel Exploitation 7
Please see the file LICENSE for copying permission
Please see the file CONTRIBUTING.md for contribution guidelines
Please file any enhancement request or bug report via GitHub Issue Tracker at the below given address: https://github.com/hacksysteam/HackSysExtremeVulnerableDriver/issues