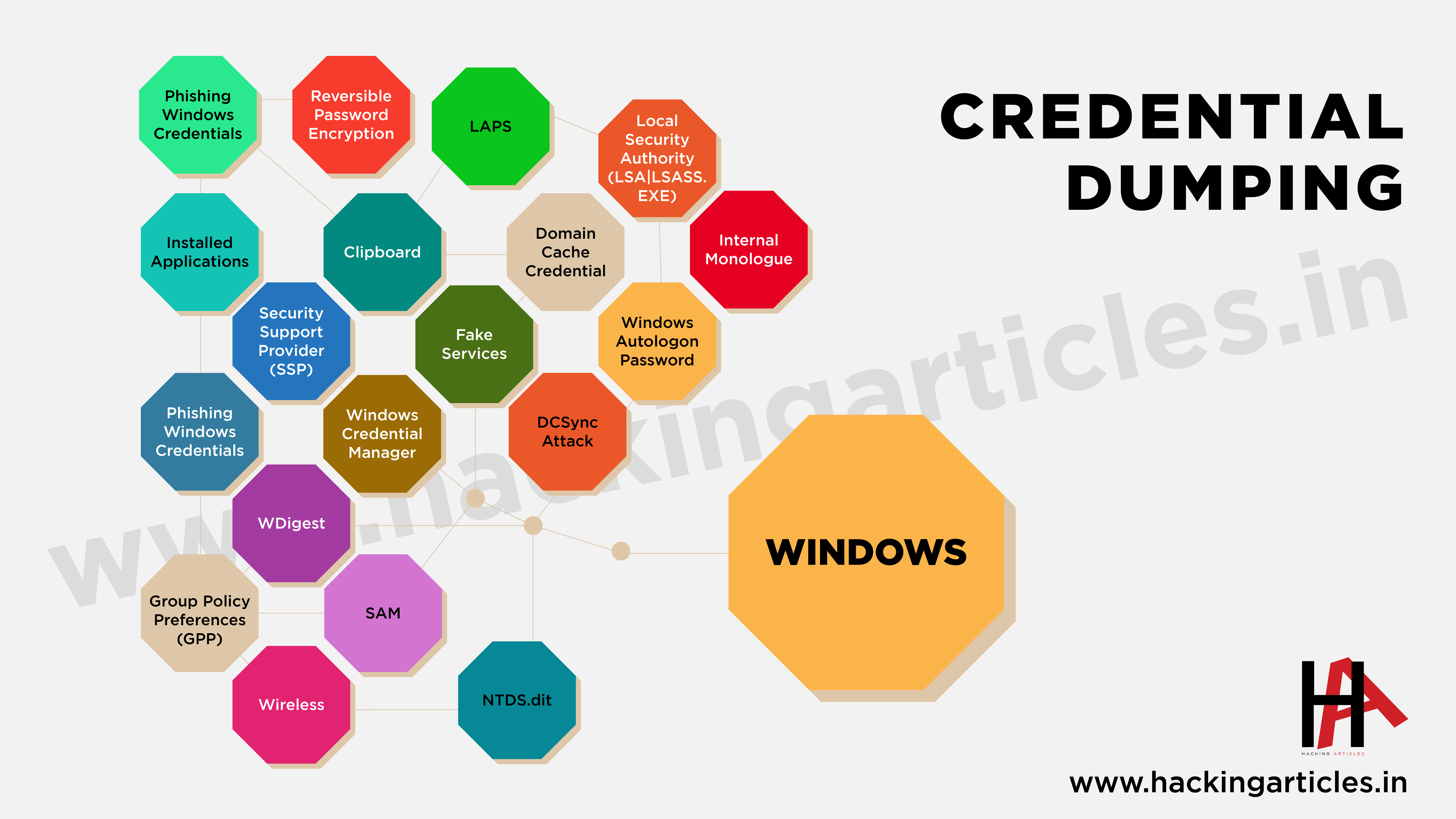
This cheatsheet is aimed at the Red Teamers to help them understand the fundamentals of Credential Dumping (a sub-technique of Credential Access) with examples. There are multiple ways to perform the same task. We have performed and compiled this list based on our experience. Please share this with your connections and direct queries and feedback to Hacking Articles.
- Wireless
- Group Policy Preferences (GPP)
- Windows Credential Manager
- WDigest
- Security Support Provider (SSP)
- SAM
- Installed Applications
- NTDS.dit
- Phishing Windows Credentials
- Local Security Authority (LSA|LSASS.EXE)
- Clipboard
- DCSync Attack
- LAPS
- Domain Cache Credential
- Fake Services
- Windows Autologon Password
- Internal Monologue
- Reversible Password Encryption