New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
dependency-check report shows in column 'Highest severity' MEDIUM while CVSSv2 has value 8.5 (CVSSv3 has value 6.6) #5658
Comments
|
I am experiencing the same problem using the Maven Plugin. If a solution could be the following, but I haven't tested it since I couldn't run all tests on my mac Using Maven Plugin v8.3.1 and the report shows |
+1 Similar issue with CVE-2016-4055 as it fails our builds due to the CVSSv2 score of 7.8 HIGH even though the CVSSv3 score is 6.5 MEDIUM. We want the plugin to take into consideration only the CVSSv3 score due to company policy but I could not find a way to force it to exclusively use CVSSv3 scores. We can ignore the CVE but if the CVSSv3 score changes in the future we will not be notified. |
Describe the bug
The Gradle plugin fails with a found vulnerability with value greater than 7.0 during the analyze step:
Dependency-Analyze Failure:
One or more dependencies were identified with vulnerabilities that have a CVSS score greater than '7.0': CVE-2021-42550
See the dependency-check report for more details.
When I then look at the dependency-check report, I only see vulnerabilities with as 'Highest severity' the value MEDIUM. While I would expect a value of HIGH (because the analyze failed).
See screenshot:

When clicking on the logback-core-1.3.0.jar link, it shows (amongst others):
CVSSv2:
Base Score: HIGH (8.5)
Vector: /AV:N/AC:M/Au:S/C:C/I:C/A:C
CVSSv3:
Base Score: MEDIUM (6.6)
Vector: CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H
See screenshot:
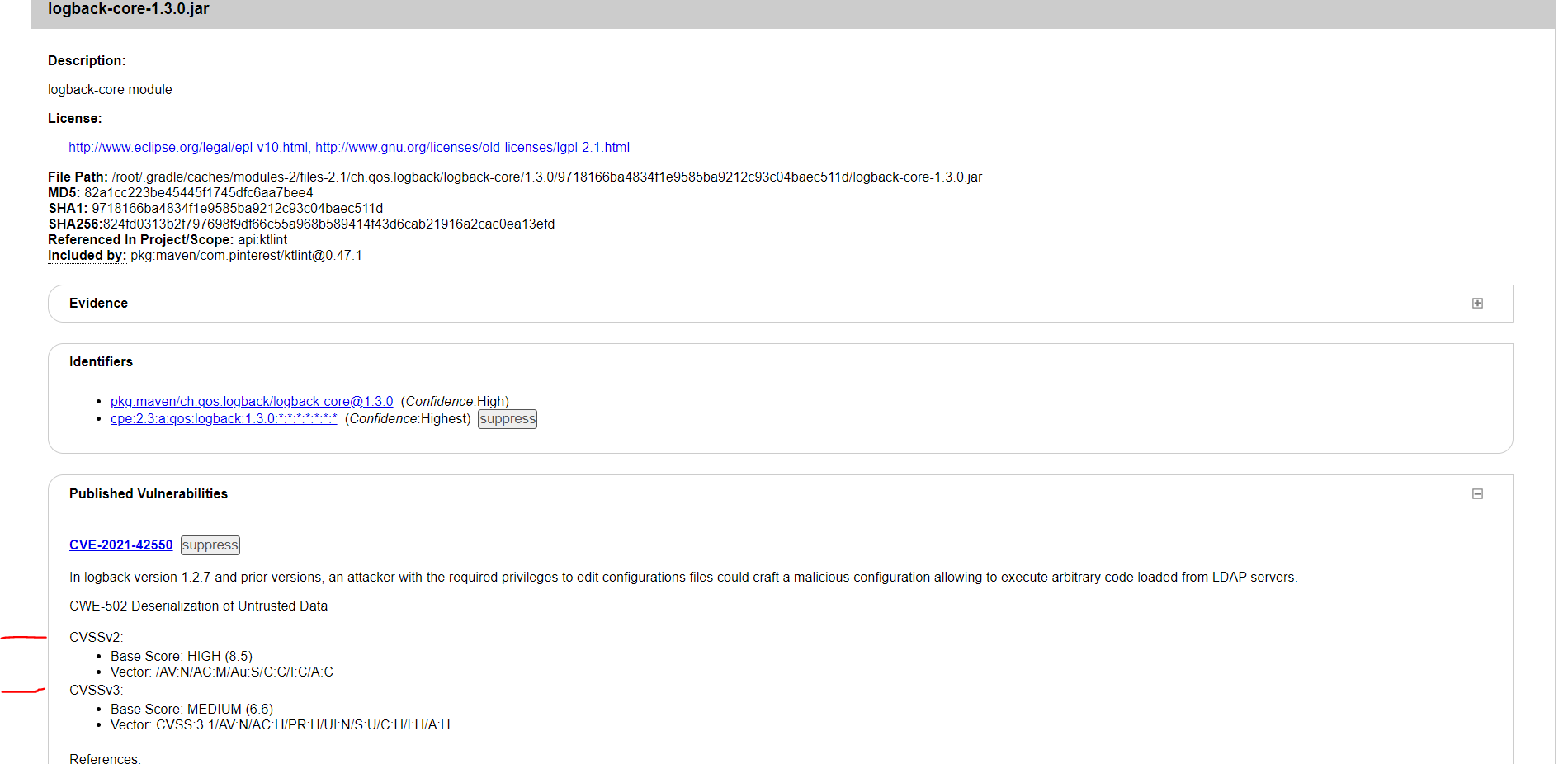
Note that the CVSSv2 score is 8.5 and the CVSSv3 is 6.6. It seems the plugin checks only for the status of the CVSSv3 value? That would be fine if it wouldn't fail the plugin analyze phase on reporting there is a vulnerability with score greater than 7.0 (which indicates a severity of value HIGH).
A solution could be: take the highest of the two CVSS scores and show that in the report column "Highest severity"? So in this case it would show HIGH (not MEDIUM)
Version of dependency-check used
The problem occurs using version 7.4.4 and 8.1.2 of the gradle plugin.
Log file
Only for now adding the reason why the job (plugin) is failing:
Dependency-Analyze Failure:
One or more dependencies were identified with vulnerabilities that have a CVSS score greater than '7.0': CVE-2021-42550
See the dependency-check report for more details.
To Reproduce
Steps to reproduce the behavior:
dependencyCheck {
failBuildOnCVSS = 7
failOnError = true
}
Expected behavior
Show in the report in the 'Highest severity' column the highest of the CVSSv2 and CVSSv3 score, in this example thus showing HIGH. This would be very useful because I use that column to sort on anything that is HIGH or more critical, to know where to focus on first. Now it won't show me the HIGHs always looking at that column.
Additional context
Looks similar/related to #2462 but isn't exactly the same.
The text was updated successfully, but these errors were encountered: