This demo showcases an AMQ messaging layer which simulates the messaging federation of two different OpenShift clusters using AMQ Interconnect. As it has became more of an usual use case to have one data centers located away from one another hence there is a need to connect messaging brokers into one logical cluster.

For demo sake, OpenShift namespaces will be used to simulate two different clusters.
- 1x OpenShift cluster (Tested on v4.3)
- Java environment with maven setup
- The AMQ clients used are Spring Boot based and will be implemented using Red Hat Fuse
- Deploy AMQ Interconnect in the first cluster
- Deploy AMQ Interconnect in the second cluster
- Deploy AMQ Broker in the second cluster
- Attach the broker to the interconnect routers
- Running the demo
The first cluster will be called amq-cluster1. The AMQ Interconnect Operator will deploy two routers which forms a mesh.
-
Create a amq-cluster1 project
$ oc new-project amq-cluster1 -
Install AMQ Interconnect Operator
- Web Console -> Operators -> OperatorHub -> AMQ Interconnect -> Install
-
Deploy the AMQ Interconnect Routing layer
-
From the amq-cluster1 namespace, Operators -> Installed Operators -> AMQ Interconnect -> AMQ Interconnect -> Create Interconnect:
apiVersion: interconnectedcloud.github.io/v1alpha1 kind: Interconnect metadata: name: cluster1-router-mesh namespace: amq-cluster1 spec: deploymentPlan: size: 2 role: interior placement: Any -
End result should be as follows:
$ oc get pods -n amq-cluster1 NAME READY STATUS RESTARTS AGE cluster1-router-mesh-688bfdc477-5jnvp 1/1 Running 0 79m cluster1-router-mesh-688bfdc477-f2lsz 1/1 Running 0 79m interconnect-operator-5c8f464bc4-48n7h 1/1 Running 0 92m
-
-
Install AMQ Certificate Manager Operator to secure the connection between the two routers.
-
Web Console -> Operators -> OperatorHub -> AMQ Certificate Manager -> Install -> Subscribe
-
Create certificate to link both regions, Web Console -> Operators -> Installed Operators -> Certificate -> Create Certificate, E.g:
apiVersion: certmanager.k8s.io/v1alpha1 kind: Certificate metadata: name: cluster2-inter-router-tls spec: commonName: cluster1-router-mesh-myproject.cluster2.openshift.com issuerRef: name: cluster1-router-mesh-inter-router-ca secretName: cluster2-inter-router-tls- Extract the certificate for use when deploying the second cluster
oc extract secret/cluster2-inter-router-tls -
-
Expose AMQPS port so the interconnect routers between the two clusters can communicate with one another.
- From amq-cluster1 namespace, navigate to Web Console -> Operators -> Installed Operators -> AMQ Interconnect -> AMQ Interconnect -> cluster1-interconnect -> YAML
- Set expose: true for port 5671
- port: 5671 sslProfile: default expose: true
-
To create simulate a second cluster, create another namespace, amq-cluster2
$ oc new-project amq-cluster2 -
Create secret from the previous cluster's certificate:
$ oc create secret generic cluster2-inter-router-tls -
Install AMQ's Interconnect Operator
- Web Console -> Operators -> OperatorHub -> AMQ Interconnect -> Install
-
Deploy the AMQ Interconnect Routing layer
-
From the amq-cluster2 namespace, Operators -> Installed Operators -> AMQ Interconnect -> AMQ Interconnect -> Create Interconnect
-
The YAML should include the router connector to connect to the first region
apiVersion: interconnectedcloud.github.io/v1alpha1 kind: Interconnect metadata: name: cluster2-router-mesh namespace: amq-cluster2 spec: deploymentPlan: size: 2 role: interior placement: Any sslProfiles: - name: inter-cluster-tls credentials: cluster2-inter-router-tls caCert: cluster2-inter-router-tls interRouterConnectors: - host: <URL OF amq-cluster1 PORT 55671> port: 443 verifyHostname: false sslProfile: inter-cluster-tls
Note that the URL can be retrieved by running:
$ oc get routes -n amq-cluster1 -
-
Expose AMQPS port to allow communciation from the first cluster.
- From amq-cluster2 namespace, navigate to Web Console -> Operators -> Installed Operators -> AMQ Interconnect -> AMQ Interconnect -> cluster2-interconnect -> YAML
- Set expose: true for port 5671
- port: 5671 sslProfile: default expose: true
-
Validate the links between the two clusters has been established
-
Navigate to cluster2-router-mesh-8080 route and enter the following:
Address: (default) Port: 443 User Name: guest@cluster2-router-mesh Password: (obtain from the Secret generated by Operator)- You can get the password by running:
$ oc get secret cluster2-router-mesh-users -o=jsonpath={.data.guest} | base64 -d
- You can get the password by running:
-
You should see the following:
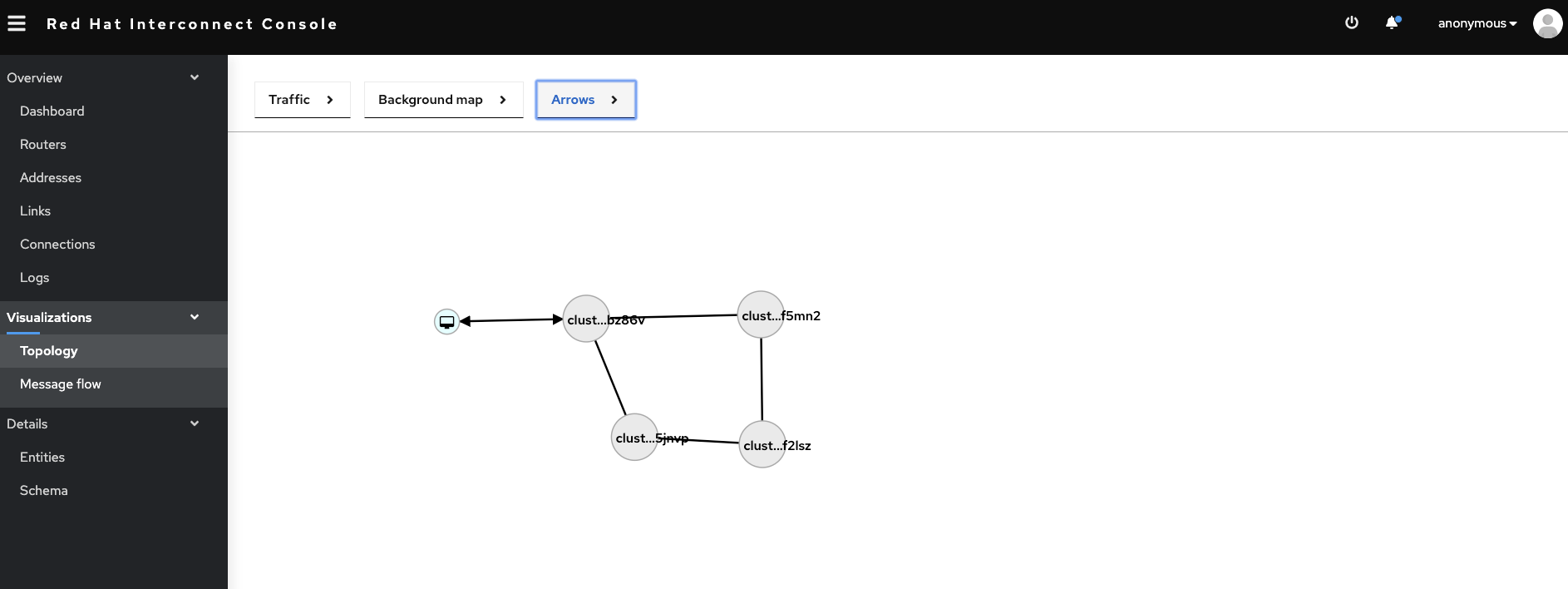 On the Interconnect console, it shows that the 4 routers across the regions are connected.
On the Interconnect console, it shows that the 4 routers across the regions are connected.
- From the amq-cluster2 namespace, Operators -> Installed Operators -> AMQ Broker -> AMQ Broker -> Create Active MQArtemis:
apiVersion: broker.amq.io/v2alpha1 kind: ActiveMQArtemis metadata: name: broker1 namespace: amq-cluster2 spec: deploymentPlan: size: 1 image: 'registry.redhat.io/amq7/amq-broker:7.6' acceptors: - name: amqp port: 5672 protocols: amqp
Once the broker is created successfully, attach the broker to the routers, Web Console -> Operators -> Installed Operators -> AMQ Interconnect -> AMQ Interconnect -> cluster2-router-mesh -> YAML:
- Add the following into the YAML:
spec:
connectors:
- name: my-broker
host: broker1-hdls-svc.amq-cluster2.svc.cluster.local
port: 5672
routeContainer: true
linkRoutes:
- prefix: test
direction: in
connection: my-broker
- prefix: test
direction: out
connection: my-broker
The test prefix indicates for which addresses the Routing layer should forward messages to the broker. The address test matches the address of the Fuse AMQP clients used to produce/consume messages.
To run the demo, need to start the producer and consumer to begin the sending and receiving of messages. You can do so by running maven command locally:
$ mvn
- Once the AMQ clients are running, you should be able to see the whole traffic flow on the Interconnect web console:

